A Security Scheme Based on Intranal-Adding Links for Integrated Industrial Cyber-Physical Systems
Abstract
1. Introduction
1.1. Interdependent Networks
1.2. Cascading Failure
- (i)
- This node has more than one dependent link from normal working nodes;
- (ii)
- This node belongs to the giant component.
- (i)
- One is that the system is collapsing;
- (ii)
- The other statement is that there are still some nodes working normally. The entire system will be in a stable state.
2. Mathematical Model
2.1. Interdependent Model
2.2. Mathematical Formulation
3. Methodology
4. Results and Discussion
4.1. Parameters
4.2. Reliability Metrics
4.3. Simulation Setup
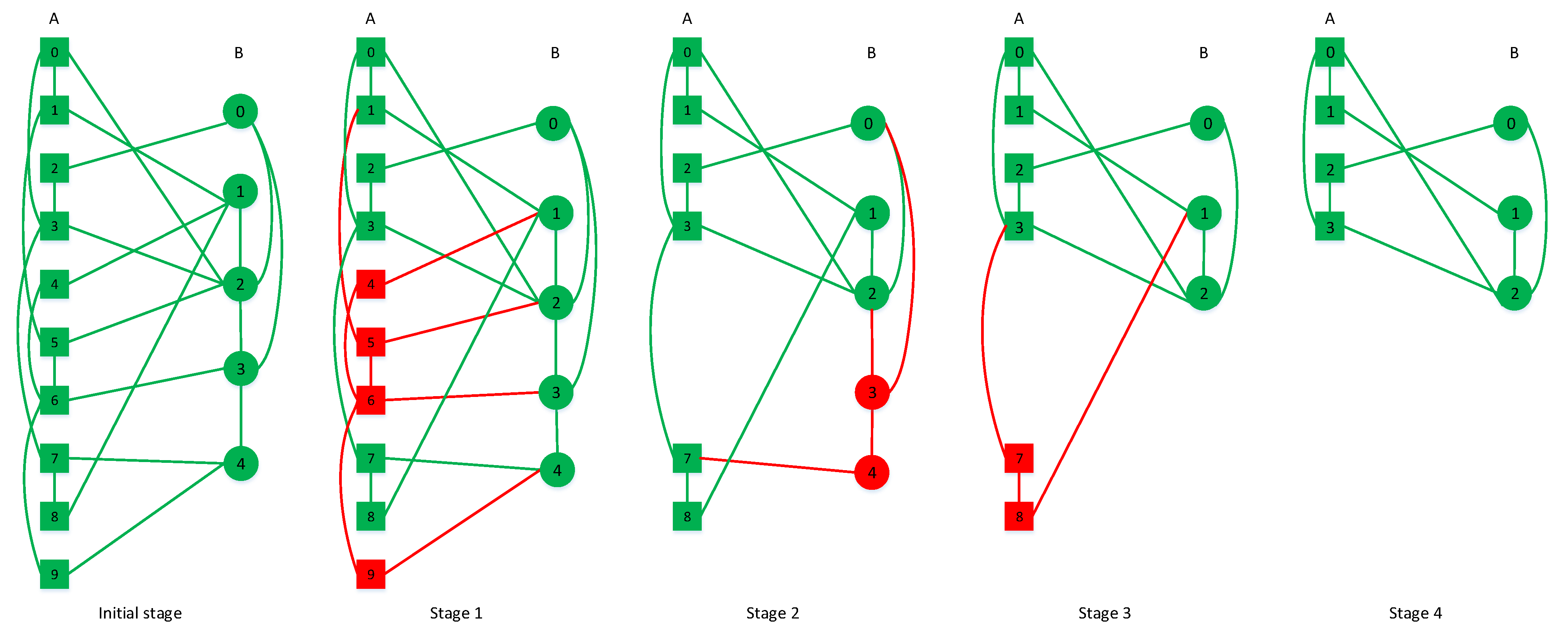
- in the first, we build two complex networks (which are named A and B) to represent an interdependent network. These two networks are selected from the ER and SF network which are generated by binomial distribution and power-law distribution, respectively.
- then, we couple these two networks within the ‘one-to-multiple correspondence’ model. The relationships of inter-links are random connections and the ratio maintains 3:1.
- we apply one adding strategy to one specific model. The relationships of intra-links will change.
- in the further, nodes are chosen at random as failed nodes representing the attacked nodes of the network A.
- cascading failure propagates between network A and B. We simulate each propagate’s stage and record the working node’s number of the system at each step.
- finally, we calculate the steady stage node’s number of this entire interdependent network.
4.4. Network Size and
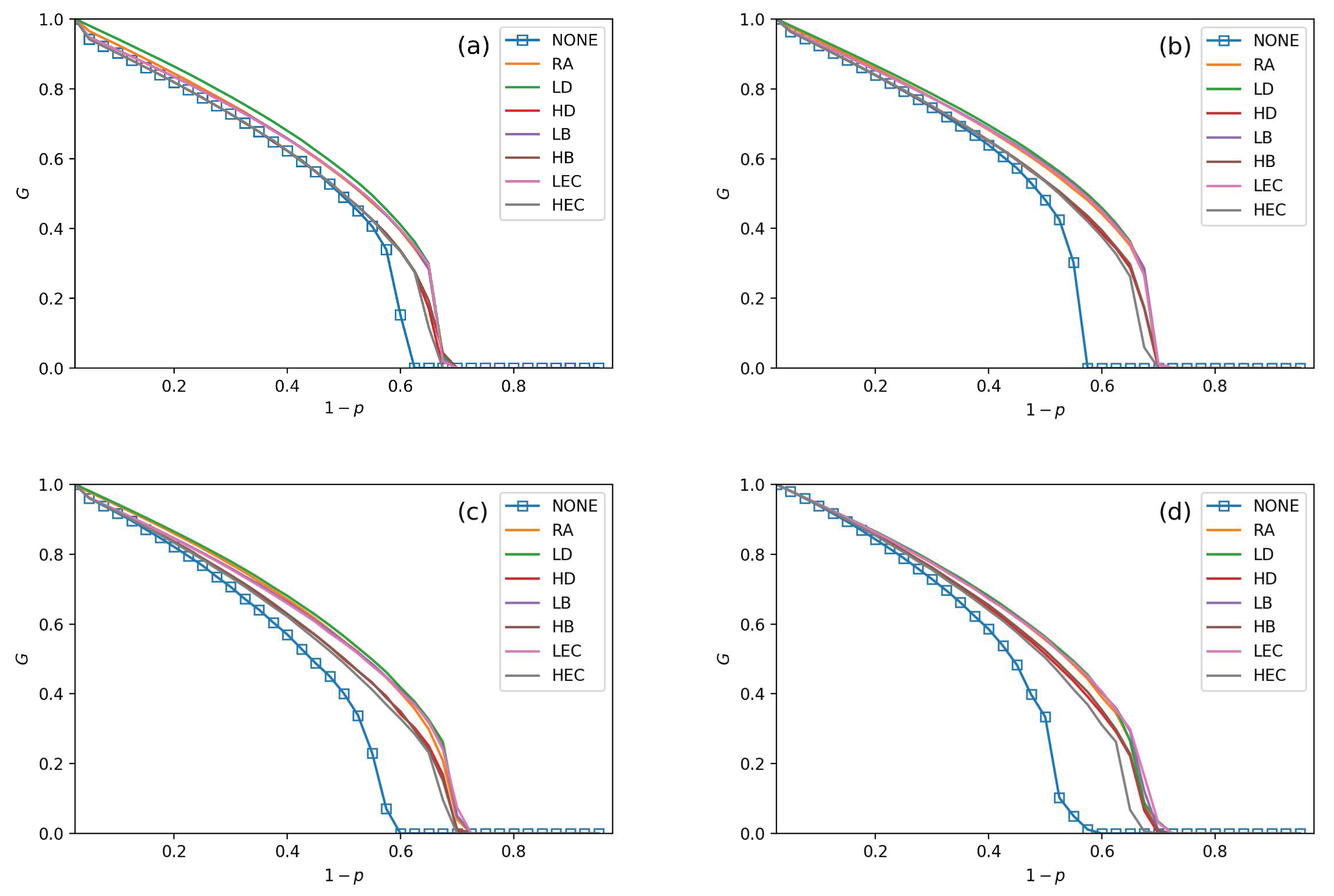
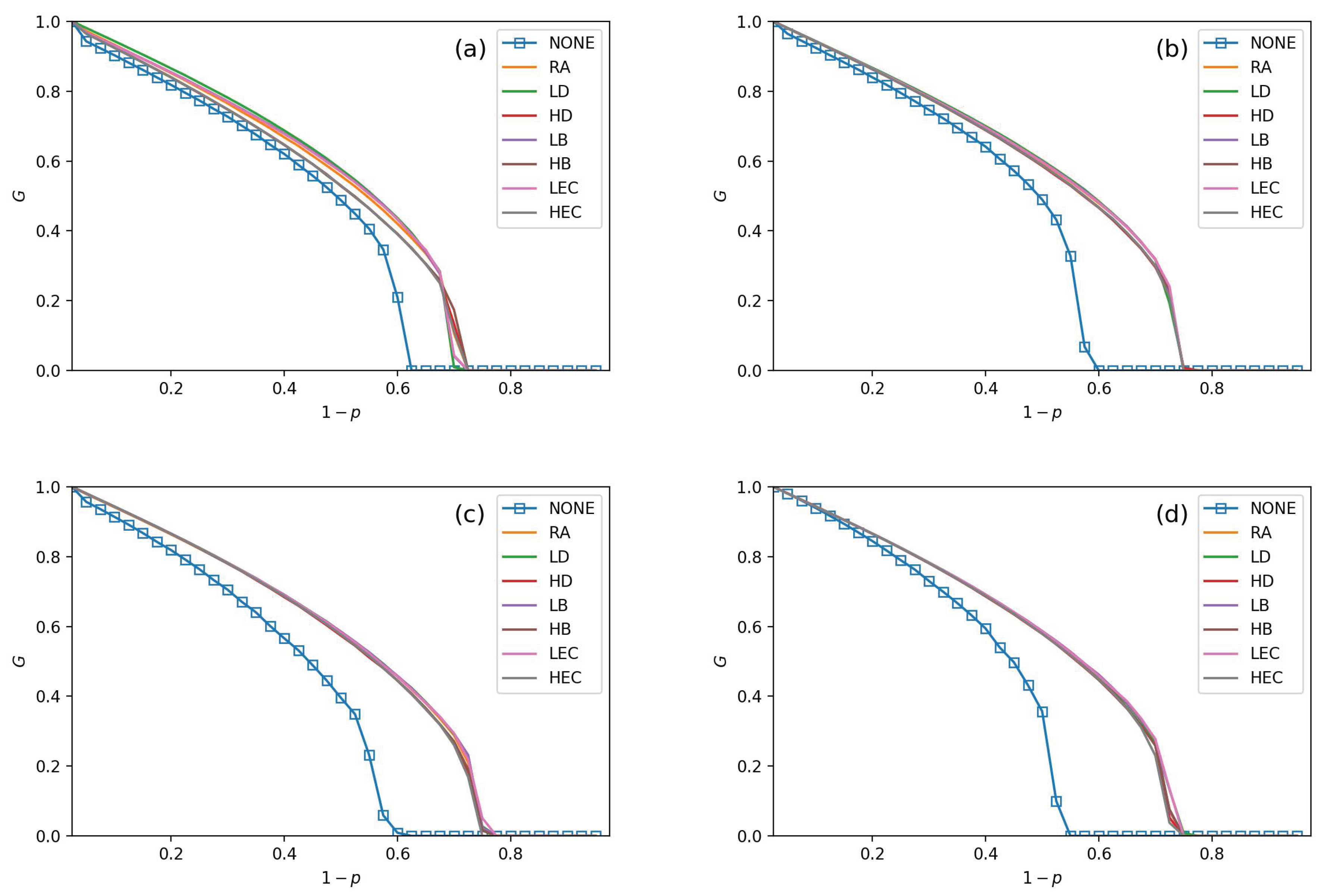
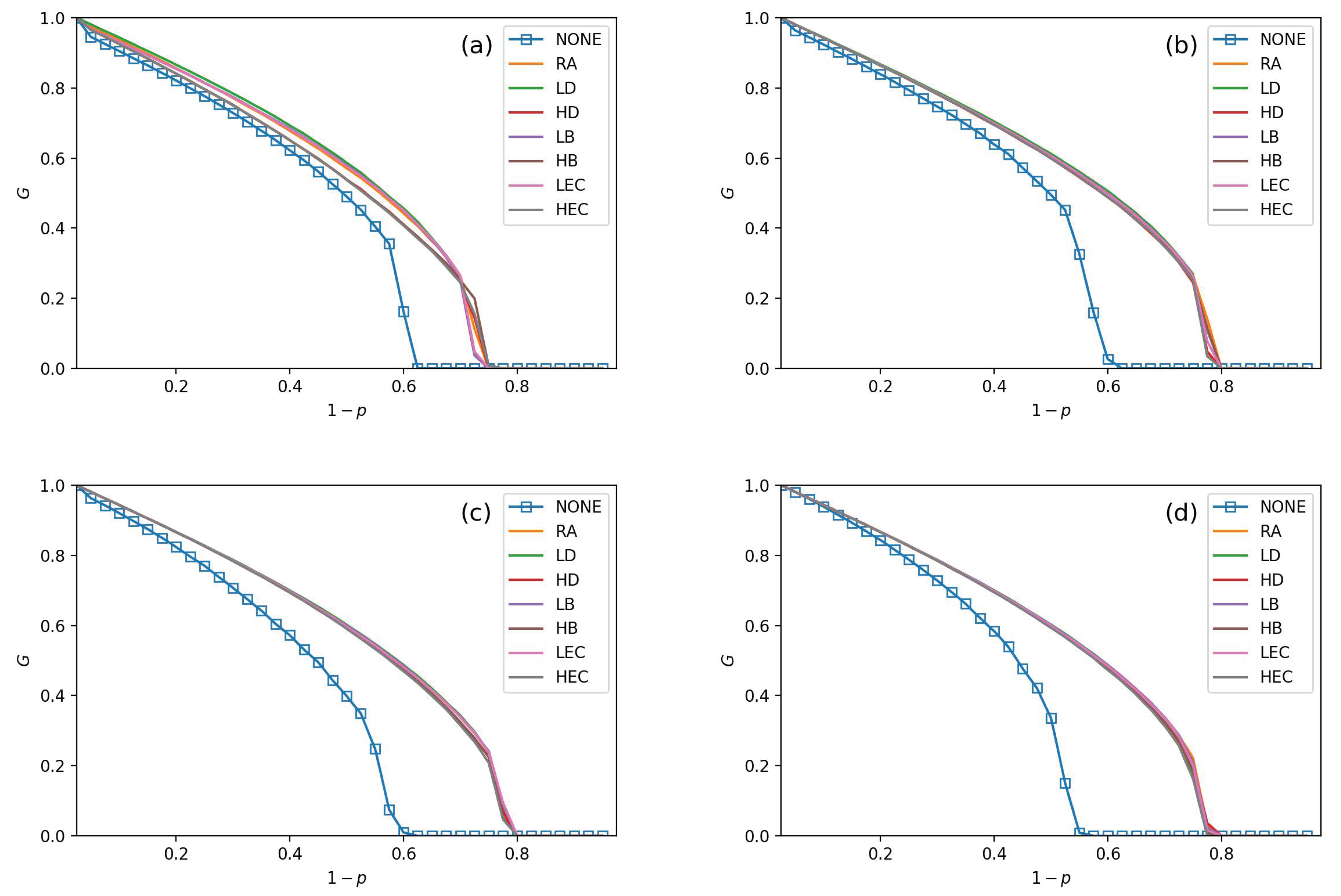
- All strategies make greater robustness of the CPS model. As the value of the increases, one CPS model gets more reliable. All seven adding strategies have higher values of G and than NONE. It means that increasing the number of intra-links can enhance an interdependent network’s reliability. When the number of intra-links increases, the instructions of one network get more complex. The G and values are increasing when increases. The nears 0.7 under LEC in Figure 3d. When gets 45%, the value of is more than 0.8 (in Figure 6d). This conclusion obeys the previous conclusions which are mentioned in [28].
- The LD strategy gets the highest values of G and in the ER-ER CPS model (shown in all subfigure (a) from Figure 3, Figure 4, Figure 5 and Figure 6). The best choice to enhance G and is the LEC strategy in the other models. All strategies achieve a similar influence in both G and values from Figure 4b–d, Figure 5b–d and Figure 6b–d. Adding links by high centrality coincides with low centrality values while . It means that the different system’s structures are getting more similar when the value of increases.
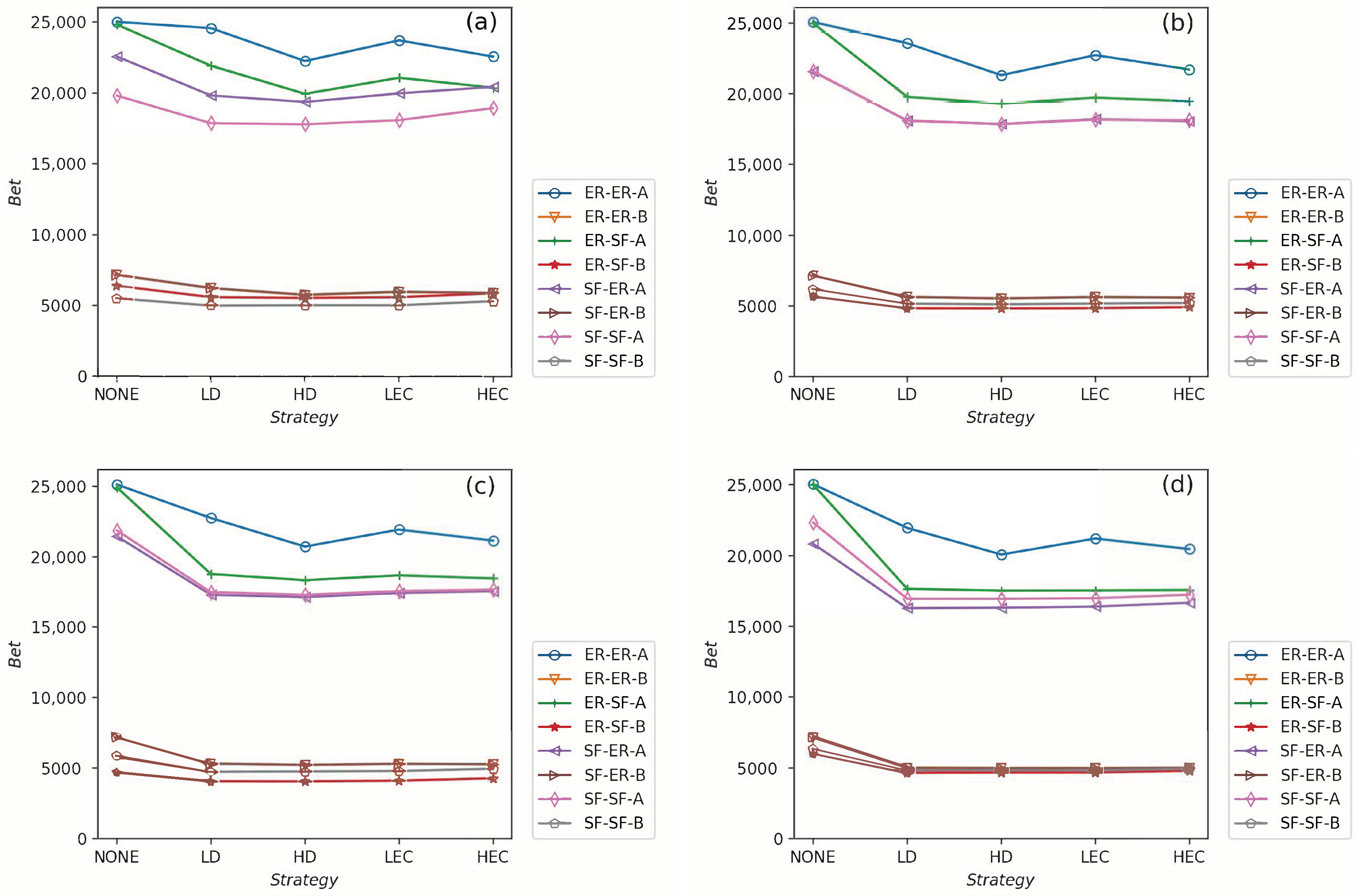
- In Figure 7, we graph the relationship of betweenness values and different strategies. We use the form X-Y-Z to illustrate the interdependent networks after adding intra-links [28]. X and Y denote the types of the network of interdependent networks. Z represents the single network of the CPS. We find that the betweenness values of strategies are lower than the original networks (NONE). Gaps between betweennesses among ER-SF, SF-ER, and SF-SF interdependent networks are getting smaller when increases. The betweenness values of the A network in the ER-ER model are highest under all .In Figure 8, we plot the eigenvector centrality values of different strategies. Eigenvector centrality values of LEC are lower than the other strategies when . When , and , HD and HEC display a tendency to decay compared to their adjacent values. All strategies’ eigenvector centrality values are more closed with getting bigger. The eigenvector centrality values of the A network are smaller than its correspondence B network. The ER network has higher eigenvector centrality values. In Figure 8, the eigenvector centrality values of all strategies are not lower than NONE.According to Figure 7 and Figure 8, we can obtain that decreasing the network’s betweenness value and increasing the network’s eigenvector centrality value could enhance network reliability. Nevertheless, a too high or too low cost cannot get the largest G and . Betweenness values and eigenvector centrality values of different interdependent networks are not the same, even if their topologies are similar.
5. Conclusions and Future Works
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Arafsha, F.; Laamarti, F.; El Saddik, A. Development of a wireless CPS for gait parameters measurement and analysis. In Proceedings of the 2018 IEEE International Instrumentation and Measurement Technology Conference (I2MTC), Houston, TX, USA, 14–17 May 2018; pp. 1–5. [Google Scholar]
- Xuhong, L.; Muhai, L. Application of CPS in the Complex Network. In Proceedings of the 2011 Fourth International Conference on Intelligent Computation Technology and Automation, Shenzhen, China, 28–29 March 2011; Volume 2, pp. 1067–1069. [Google Scholar]
- Rana, M.; Shafiq, A.; Altaf, I.; Alazab, M.; Mahmood, K.; Chaudhry, S.A.; Zikria, Y.B. A secure and lightweight authentication scheme for next generation IoT infrastructure. Comput. Commun. 2021, 165, 85–96. [Google Scholar] [CrossRef]
- Wang, W.; Xia, F.; Nie, H.; Chen, Z.; Gong, Z.; Kong, X.; Wei, W. Vehicle trajectory clustering based on dynamic representation learning of internet of vehicles. IEEE Trans. Intell. Transp. Syst. 2020. [Google Scholar] [CrossRef]
- Wang, T.; Liang, Y.; Yang, Y.; Xu, G.; Peng, H.; Liu, A.; Jia, W. An intelligent edge-computing-based method to counter coupling problems in cyber-physical systems. IEEE Netw. 2020, 34, 16–22. [Google Scholar] [CrossRef]
- Wang, W.; Zhao, X.; Gong, Z.; Chen, Z.; Zhang, N.; Wei, W. An attention-based deep learning framework for trip destination prediction of sharing bike. IEEE Trans. Intell. Transp. Syst. 2020. [Google Scholar] [CrossRef]
- Zhang, J.; Yeh, E.; Modiano, E. Robustness of interdependent random geometric networks. IEEE Trans. Netw. Sci. Eng. 2018, 6, 474–487. [Google Scholar] [CrossRef]
- Huang, Z.; Wang, C.; Nayak, A.; Stojmenovic, I. Small cluster in cyber physical systems: Network topology, interdependence and cascading failures. IEEE Trans. Parallel Distrib. Syst. 2014, 26, 2340–2351. [Google Scholar] [CrossRef]
- Peng, H.; Liu, C.; Zhao, D.; Han, J. Reliability analysis of CPS systems under different edge repairing strategies. Phys. A Stat. Mech. Appl. 2019, 532, 121865. [Google Scholar] [CrossRef]
- Wang, W.; Kumar, N.; Chen, J.; Gong, Z.; Kong, X.; Wei, W.; Gao, H. Realizing the Potential of Internet of Things for Smart Tourism with 5G and AI. IEEE Netw. 2020, 34, 295–301. [Google Scholar] [CrossRef]
- Peng, H.; Liu, C.; Zhao, D.; Hu, Z.; Han, J.; Lu, J. Reliability Analysis of Heterogeneous CPS under Different Swapping Inter-links Strategies. In International Symposium on Security and Privacy in Social Networks and Big Data; Springer: Berlin/Heidelberg, Germany, 2020; pp. 329–339. [Google Scholar]
- Buldyrev, S.V.; Parshani, R.; Paul, G.; Stanley, H.E.; Havlin, S. Catastrophic cascade of failures in interdependent networks. Nature 2010, 464, 1025–1028. [Google Scholar] [CrossRef]
- Wu, P.; Ling, Z.; Liu, L.; Jiang, Y.; Wu, H.; Dai, L. End-to-End Emotional Speech Synthesis Using Style Tokens and Semi-Supervised Training. In Proceedings of the 2019 Asia-Pacific Signal and Information Processing Association Annual Summit and Conference (APSIPA ASC), Lanzhou, China, 18–21 November 2019; pp. 623–627. [Google Scholar]
- Huang, Z.; Wang, C.; Stojmenovic, M.; Nayak, A. Characterization of cascading failures in interdependent cyber-physical systems. IEEE Trans. Comput. 2014, 64, 2158–2168. [Google Scholar] [CrossRef]
- Dong, G.; Chen, Y.; Wang, F.; Du, R.; Tian, L.; Stanley, H.E. Robustness on interdependent networks with a multiple-to-multiple dependent relationship. Chaos Interdiscip. J. Nonlinear Sci. 2019, 29, 073107. [Google Scholar] [CrossRef]
- Chen, L.; Yue, D.; Dou, C.; Cheng, Z.; Chen, J. Robustness of cyber-physical power systems in cascading failure: Survival of interdependent clusters. Int. J. Electr. Power Energy Syst. 2020, 114, 105374. [Google Scholar] [CrossRef]
- Chen, L.; Yue, D.; Dou, C. Optimization on vulnerability analysis and redundancy protection in interdependent networks. Phys. A Stat. Mech. Appl. 2019, 523, 1216–1226. [Google Scholar] [CrossRef]
- Shao, J.; Buldyrev, S.V.; Havlin, S.; Stanley, H.E. Cascade of failures in coupled network systems with multiple support-dependence relations. Phys. Rev. E 2011, 83, 036116. [Google Scholar] [CrossRef]
- Jiang, J.; Xia, Y.; Xu, S.; Shen, H.L.; Wu, J. An asymmetric interdependent networks model for cyber-physical systems. Chaos Interdiscip. J. Nonlinear Sci. 2020, 30, 053135. [Google Scholar] [CrossRef]
- Peng, H.; Kan, Z.; Zhao, D.; Han, J. Security assessment for interdependent heterogeneous cyber physical systems. Mob. Netw. Appl. 2019. [Google Scholar] [CrossRef]
- Ruj, S.; Pal, A. Analyzing cascading failures in smart grids under random and targeted attacks. In Proceedings of the 2014 IEEE 28th International Conference on Advanced Information Networking and Applications, Victoria, BC, Canada, 13–16 May 2014; pp. 226–233. [Google Scholar]
- Nguyen, D.T.; Shen, Y.; Thai, M.T. Detecting critical nodes in interdependent power networks for vulnerability assessment. IEEE Trans. Smart Grid 2013, 4, 151–159. [Google Scholar] [CrossRef]
- Cui, P.; Zhu, P.; Wang, K.; Xun, P.; Xia, Z. Enhancing robustness of interdependent network by adding connectivity and dependence links. Phys. A Stat. Mech. Appl. 2018, 497, 185–197. [Google Scholar] [CrossRef]
- Parshani, R.; Rozenblat, C.; Ietri, D.; Ducruet, C.; Havlin, S. Inter-similarity between coupled networks. Europhys. Lett. 2011, 92, 68002. [Google Scholar] [CrossRef]
- Chattopadhyay, S.; Dai, H.; Hosseinalipour, S. Designing optimal interlink patterns to maximize robustness of interdependent networks against cascading failures. IEEE Trans. Commun. 2017, 65, 3847–3862. [Google Scholar] [CrossRef]
- Zhou, D.; Stanley, H.E.; D’Agostino, G.; Scala, A. Assortativity decreases the robustness of interdependent networks. Phys. Rev. E 2012, 86, 066103. [Google Scholar] [CrossRef] [PubMed]
- Kamran, K.; Zhang, J.; Yeh, E.; Modiano, E. Robustness of interdependent geometric networks under inhomogeneous failures. In Proceedings of the 2018 16th International Symposium on Modeling and Optimization in Mobile, Ad Hoc, and Wireless Networks (WiOpt), Shanghai, China, 7–11 May 2018; pp. 1–6. [Google Scholar]
- Ji, X.; Wang, B.; Liu, D.; Chen, G.; Tang, F.; Wei, D.; Tu, L. Improving interdependent networks robustness by adding connectivity links. Phys. A Stat. Mech. Appl. 2016, 444, 9–19. [Google Scholar] [CrossRef]
- Jiang, Z.; Liang, M.; Guo, D. Enhancing network performance by edge addition. Int. J. Mod. Phys. C 2011, 22, 1211–1226. [Google Scholar] [CrossRef]
- Beygelzimer, A.; Grinstein, G.; Linsker, R.; Rish, I. Improving network robustness by edge modification. Phys. A Stat. Mech. Appl. 2005, 357, 593–612. [Google Scholar] [CrossRef]
- Zhang, F.; Shi, Z.; Mukhopadhyay, S. Robustness analysis for battery-supported cyber-physical systems. ACM Trans. Embed. Comput. Syst. 2013, 12, 69. [Google Scholar] [CrossRef]
- Wang, Z.; Scaglione, A.; Thomas, R.J. Generating statistically correct random topologies for testing smart grid communication and control networks. IEEE Trans. Smart Grid 2010, 1, 28–39. [Google Scholar] [CrossRef]
- Derler, P.; Lee, E.A.; Vincentelli, A.S. Modeling cyber–physical systems. Proc. IEEE 2011, 100, 13–28. [Google Scholar] [CrossRef]
- Newman, M. Networks; Oxford University Press: Oxford, UK, 2018. [Google Scholar]
- Peng, H.; Liu, C.; Zhao, D.; Ye, H.; Fang, Z.; Wang, W. Security Analysis of CPS Systems Under Different Swapping Strategies in IoT Environments. IEEE Access 2020, 8, 63567–63576. [Google Scholar] [CrossRef]
- Kumari, P.; Singh, A. Approximation and Updation of Betweenness Centrality in Dynamic Complex Networks. In Computational Intelligence: Theories, Applications and Future Directions-Volume I; Springer: Berlin/Heidelberg, Germany, 2019; pp. 25–37. [Google Scholar]
- Hesse, M.; Dann, D.; Braesemann, F.; Teubner, T. Understanding the Platform Economy: Signals, Trust, and Social Interaction. In Proceedings of the Proceedings of the 53rd Hawaii International Conference on System Sciences, Maui, HI, USA, 7–10 January 2020. [Google Scholar]


| Symbol | Meaning |
|---|---|
| p | The fraction of nodes which is not failed after initial attacks |
| , | The fraction of normal nodes of network A, B in stage i |
| , | The nodes’ number in network A, B in stage i |
| The fraction of () and () | |
| The fraction of () and () | |
| , | The generating functions of network A, B |
| Network A | Network B | |
|---|---|---|
| Stage 1 | ||
| Stage 2 | ||
| Stage 3 | ||
| Stage 4 | ||
| … | … | … |
| Stage 2i | ||
| Stage 2 |
| Symbol | Meaning |
|---|---|
| The nodes’ number in network A, B | |
| The average degree of the network | |
| The parameter of the SF network | |
| The fraction of adding intra-links | |
| The intra-links number of network A, B | |
| G | The functions of normal working nodes after cascading failures |
| The ability of the network to fight random attacks |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhao, D.; Liu, C.; Peng, H.; Yu, J.; Han, J. A Security Scheme Based on Intranal-Adding Links for Integrated Industrial Cyber-Physical Systems. Sensors 2021, 21, 2794. https://doi.org/10.3390/s21082794
Zhao D, Liu C, Peng H, Yu J, Han J. A Security Scheme Based on Intranal-Adding Links for Integrated Industrial Cyber-Physical Systems. Sensors. 2021; 21(8):2794. https://doi.org/10.3390/s21082794
Chicago/Turabian StyleZhao, Dandan, Can Liu, Hao Peng, Juan Yu, and Jianmin Han. 2021. "A Security Scheme Based on Intranal-Adding Links for Integrated Industrial Cyber-Physical Systems" Sensors 21, no. 8: 2794. https://doi.org/10.3390/s21082794
APA StyleZhao, D., Liu, C., Peng, H., Yu, J., & Han, J. (2021). A Security Scheme Based on Intranal-Adding Links for Integrated Industrial Cyber-Physical Systems. Sensors, 21(8), 2794. https://doi.org/10.3390/s21082794








