1. Introduction
A Vehicular Ad-hoc Network (VANET) with its variety of protocols (e.g., IEEE 802.11P, IEEE 1609) [
1] and communication types like Vehicle to Vehicle (V2V) and Vehicle to Infrastructure (V2I) [
2] has served as a basis for the promising Internet of Vehicles (IoV) paradigm [
3,
4,
5]. IoV benefits from VANET to extend the usability range by allowing non-conventional communications and applications, e.g., Vehicle to Everything (V2X) communications, to emerge. IoV is an important sub-domain of IoT as well as a clear example of System of Systems domain [
6].
Figure 1 shows V2X external communications and internal equipments. A vehicle using V2X can enhance road-safety by broadcasting a Basic Safety Message (BSM) [
7,
8] beacon message with a 300-m range and a frequency of 1 to 10 BSMs per second from its OBU [
9,
10,
11]. The data included in BSMs are illustrated in
Figure 2. This allows receiving vehicles to be aware of the potential dangers posed by nearby vehicles in addition to managing road-congestion, which is considered a high-level challenge [
5] through the network of Road-Side-Units (RSUs).
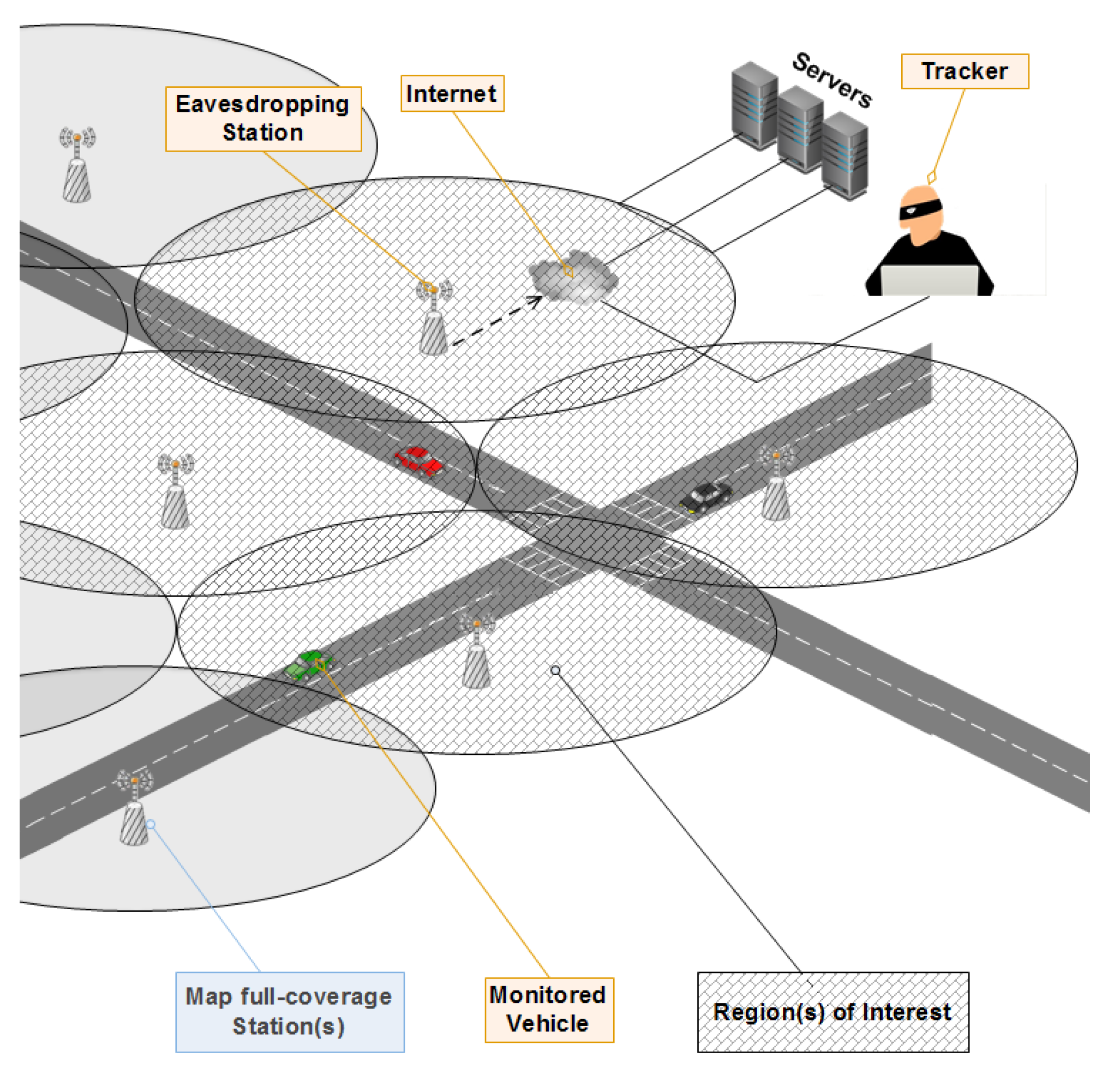
Since BSMs contain fine-grained location data, even though they are useful for road safety, they do open privacy-related issues: Any entity with eavesdropping capability can monitor the whereabouts of IoV users. Smart cars’ safety and infotainment applications may also reveal user private information. Using these data, a system that is ultimately designed to offer safety and comfort applications to drivers can be abused by third parties, such as employers, insurance companies, or criminal organizations to track individuals [
12]. The introduction of mechanisms that can preserve location privacy has become a new research trend that has attracted widespread attention among researchers. Most existing location privacy schemes, e.g., mix-zone, synchronized schemes, etc., are ineffective in achieving a high-level of privacy because of the very precise locations included in BSMs and because of their resource and overhead-consuming characteristics. The better candidate mechanism used is that of the silent period schemes by ceasing BSMs broadcasting until emerging from another location with a new pseudo-identifier. However, the major drawback of such a technique is the sacrifice of safety for the sake of privacy [
13].
As safety is a substantial requirement underpinning the introduction of V2X communication, silent period schemes have been received with reservations by the research community. Our motivation is to find a solution to allow nearby vehicles to be aware (providing safety) and reduce an adversary opportunity to employ eavesdropping attacks. The purpose of protecting user location privacy in an IoV context is related to the risk of user private information being disclosed. Location privacy is directly connected to other types of privacy. Location privacy leaks can reveal the home and work address of the driver, some visits to sensitive places, travel habits, times of absence from home, etc. The correlation of this spatio-temporal information with other data allows an adversary to come to conclusions about health habits, social contacts, religious beliefs, etc. Protecting user location privacy has many benefits both to the users and the system. First of all privacy preservation improves the performance of the IoV system and reduces users’ concerns about security and privacy. Thus IoVs can attract more users to use their functions and applications, especially those that are related to safety, promoting further innovation and development in the automobile industry. In this paper, we propose a mechanism that reduces the transmission range occasionally to just inform nearby vehicles and prevent the adversary from tracking users through BSMs. The design of a pseudonym change scheme that exploits such a transmission range adjustment feature is inspired by our previous work [
9] where we studied the effect of changing the transmission range using existing strategies. The novel method that is proposed in the current article, entitled “WHISPER”, maintains road-safety since vehicles are only hidden from the tracker (occasionally) and not from close vehicles (always), which makes the use of WHISPER an advantageous feature that comes in favor of safety and privacy.
The main contributions of this paper are as follows:
- -
We propose a novel location privacy-preserving scheme, entitled WHISPER, that maintains privacy without sacrificing safety;
- -
We detail the techniques and protocols used by WHISPER for adjusting the transmission range and performing a pseudonym change;
- -
We compare WHISPER to well-known location privacy-preserving schemes such as cooperative pseudonym change (CPN) [
14], Random Silent Period (RSP) [
15], and SLOW [
16] in a manhattan-grid model with various densities using location privacy and QoS as metrics in addition to a comparative table.
The remainder of this paper is organized as follows: In
Section 2, we review and discuss existing techniques to address the problem of location privacy in V2X. Then, we give our proposed system model in
Section 3. Next, the proposed WHISPER scheme with its techniques and protocols are presented in
Section 4. After that, WHISPER performances are analyzed in
Section 5. Later in
Section 6, we discuss the schemes in the obtained results perspective. Finally,
Section 7 concludes the paper and gives future work.
2. Related Work
The location privacy problem is being considered as one of the crucial parameters for the adoption of a successful IoV system. There are a number of efficient privacy preservation techniques for location based ervices (LBS), however, they are using location obfuscating [
17], hiding, anonymizing, and making dummies. These techniques are explained in [
18], however, they are not recommended in the context of achieving safety via BSMs broadcasting and this is because of the safety-related requirements that do not recommend risking drivers’ safety for the sake of privacy as using such techniques implies tricking the adversary alongside the nearby vehicles.
Beresford and Stajano (2003) [
19] introduce the mix-group concept, defined as a group region where vehicles are mixed within that region. However, broadcast beacons that contain high precision locations still represent a problem for drivers’ privacy. Based on the mix-group concept, Freudiger et al. (2007) proposed CMIX [
20], a location privacy scheme that uses symmetric key-based cryptography to ensure that beacons are not readable by the adversary. This approach uses a key shared by RSUs to encrypt BSMs. Their approach did not consider the internal attacker scenario in addition to heavy infrastructure reliance.
The silent period, a concept that was firstly introduced in the field of wireless LANs by Huang et al. (2005) [
15], ceases any BSM broadcasts for a specific period of time in order to achieve a good level of privacy. The strategy works well against correlation attacks [
21]. However the silent periods introduce a reduction in safety relevant data being shared within the IoV – reducing the safety properties of the system and potentially invalidating safety requirements of (“ETSI TR 103 415” [
22] and “ETSI TS 103 601” [
23] standards). This safety-privacy trade-off is addressed in our work on WHISPER.
Buttyán et al. (2009) proposed the SLOW strategy [
16]. SLOW aims at letting vehicles choose the best moment to update their pseudonyms. This decision is based on a threshold of the vehicles speed, assuming that for low speeds the risk of crashes will be low and the vehicle is allowed to stay silent for a period of time. SLOW, does not necessarily respect the beaconing frequency of once per second at minimum [
9] and this occurs in congested areas. Eckhoff et al. (2011) proposed Slotswap [
24], a strategy that uses a time-slotted pool to manage pseudonyms by each vehicle. Each slot is used for a period of time with the possibility to re-use pseudonyms after reaching the last time-slot. The exchange of pseudonyms between time-slots of different vehicles is also an option of their approach.
Lu et al. (2012) leveraged the feature of social spots [
25] for privacy enhancement. Social spots are places where vehicles meet more frequently and are characterized with high densities such as intersections and parking lots. An adversary will be more confused in such dense areas because the probability to successfully match the old changed pseudonym with the new one inside a set of vehicles
n will be tied inversely with the size of
n. In the same social context, Babaghayou et al. (2019) proposed the Extreme Points Privacy (EPP) [
18] scheme. EPP exploits the feature that IoV users are generally situated in district (where they live) and since turning the vehicle’s engine results in beaconing, this gives an indication to the adversary that the user is about to leave their home, thus, the authors propose to cease beaconing until leaving the district. The probability of leaving a district under different scenarios are evaluated.
Tomandl et al. (2012) [
26] investigated the effects of both mix-zones and silent periods. The work was also implemented by Emmara et al. (2016) in their privacy extension PREXT [
27] under the name of Coordinated Silent Period (CSP). Emmara et al. (2015) also proposed their own privacy scheme: Context-Aware Privacy Scheme (CAPS) [
28]. CAPS lets vehicles choose the best opportunity to enter a silence period and to change their pseudonyms.
Pan and Li (2013) proposed the Cooperative Pseudonym Change (CPN) [
14] scheme that exploits the best opportunity to achieve a synchronous pseudonym change with the help of neighbors. This way, the adversary loses tracking since vehicles are considered as the target and are indistinguishable. Yet, vehicles are not fully indistinguishable due to the fact that they broadcast fine-grained location. This means that an attacker is still able to identify the vehicles based on their precise location.
Emmara et al. (2016) also apply the silent period mechanism [
15] to propose the Random Silent Period (RSP) scheme [
27]. RSP is based on entering silence for a random range of time, then, it performs the pseudonym change. The scheme’s nature is considered as a spatial mix-zone because when vehicles enter the silence period and leave it after some time this implies disappearing from a point and emerging from another point which is the same idea with spatial mix-zones.
Another scheme was proposed by Zidani et al. (2018) [
29] which is the Estimation of Neighbors Position privacy scheme with an Adaptive Beaconing approach (ENeP-AB) strategy that uses the number of neighbors and the predicted positions
d as a pseudonym change trigger. Zidani et al. had also compared ENeP-AB to some other strategies like CAPs and the mix-context enhanced.
The effect of pseudonym change is mostly beneficial to privacy, however, Schoch et al. (2006) [
30] shed light on some adverse consequences of intense pseudonym changes on the overall network performances and geo-routing protocols. Their results show that high pseudonym change frequencies negatively affect the system performances. Following a different direction, Zhang et al. (2019) [
7] had touched upon the problem of collisions that occur while sending BSMs with high frequency, more precisely the problems occurring on the Medium Access Control (MAC) layer. They demonstrated the issue and proposed a hybrid MAC Protocol and showed its effectiveness via analysis and simulation means.
Goudarzi and Asgari (2018) proposed a congestion control mechanisms algorithm called (NOPC) [
31] that is based on the beacon transmission power control. The scheme performs well in the bandwidth usage and fairness, nevertheless, its influence was not evaluated versus the achieved location privacy. In the same area, SAB Mussa et al. (2014) [
32] shed light on the challenging issues that have to be addressed in the beaconing and transmission range control in the vehicular domain but without mentioning the privacy requirement [
33]. A summary of recent location privacy-preserving schemes for the Internet of Vehicles is presented in
Table 1. In the same table the major advantages and drawbacks of all these methods are also presented.
Based on the methods that were analyzed in the previous paragraphs and the ones presented in
Table 1, it is obvious that the reviewed schemes have serious limitations. The silent period schemes are the most promising solutions but at the cost of road-safety which does not make them welcomed by the research community. Moreover, pseudonym schemes on the other hand cannot reassure privacy preservation since an adversary can still track vehicles that are broadcasting their locations even if they change pseudonyms by performing the so-called linking attack. The proposed idea in this research paper (WHISPER) comes to fill these limitations, by ensuring privacy along with a high road-safety level, by acting as a silent period scheme on some occasions.
4. The Proposed WHISPER Strategy
WHISPER uses the change of transmission power to preserve or at least augment the level of location privacy in addition to ensuring road-safety while driving. Vehicles monitor the neighborhood and their proper speeds on-the-fly in order to adjust their beacons transmission range. This is because the adversary, in our assumptions, distributes eavesdropping stations intelligently and economically according to the standardization (that vehicles transmit with 300 m of range). Thus, when driving in low speeds the vehicle (i.g., ) may reduce, according to the value of its speed (and the surrounding vehicles’ speeds), its own range to ensure that:
The safety of its neighbor vehicle(s) (e.g., ) is preserved unlike the case of the silent period schemes that do not make much safety-considerations when going to enter silent. This is fulfilled by continuously checking its own speed. Thus, when in high speeds, the risk of a sudden crash will be high, which is why ought to be visible earlier to the surrounding vehicles ().
Its own safety. This is fulfilled by the neighbor vehicle(s) that are using the same behavior as while driving in different speeds. They aim, as a consequence, to inform earlier when they are driving in high speeds. Once it has received a BSM with a powerful transmission range, takes that as a parameter and adjusts, in its role, its own transmission range based on that parameter and on its own speed. By doing so, will be visible to the other neighbors, as well.
The two aforementioned points lead to a collective awareness that will ensure the safety of both and its neighbor .
To benefit and exploit the already deployed eavesdropping mode, as these eavesdropping stations will not be able to collect BSMs all the time even if the vehicles are inside the area of the eavesdropping station. This is because each eavesdropping station is placed at the aim of intercepting every sent BSM in the range of 300 m.
4.1. System Initialization
Each vehicle is equipped with M certificates and each one of them is defined as () where j represents the i-th certificate of . Thus, each vehicle has a set of certificates defined as follows: . When referring to a pseudonym change, this implies the use of another certificate.
Before we dive into the detailed modus-operandi of WHISPER, we define the set of concepts (find them in
Table 2) that are key-parameters used to determine the exact behavior of WHISPER.
Generally speaking, in WHISPER, every vehicle can be in one of the following main states:
Vehicle ON: Is the state when a vehicle is turned on (to be ready for driving).
Listening: Once on, keeps monitoring the transmission medium to detect any transmitted BSM. Both its neighbor(s) status (found in their transmitted BSMs) and its own speed.
Receiving BSMs: When receiving a BSM from , proceeds into diverse calculations at the aim of knowing the status of .
Adjusting the transmission power: In this status, takes as parameters its own speed and the neighbors’ speed and may, accordingly, adjust its transmission range in order to ensure road-safety and preserve location-privacy of the present vehicles.
Checking pseudonym change condition: This status comes after the expires. will check its eligibility for a pseudonym (and certificate) change. When favorable, moves into the next status.
Pseudonym change: In this status, a pseudonym change takes place and the BSM will be sent right after.
Sending a BSM: This status happens after the Pseudonym change action. Sometimes, the pseudonym change trigger will not be satisfied, thus, just sends the BSM. In both scenarios, returns to the next status (Listening) afterwards.
Vehicle OFF: The status where a vehicle is turned off and thus the ending status.
A state diagram is presented in
Figure 6 which gives a better illustration and understanding on the aforementioned states and the existing transitions.
4.2. Receiving Beacon Messages Protocol
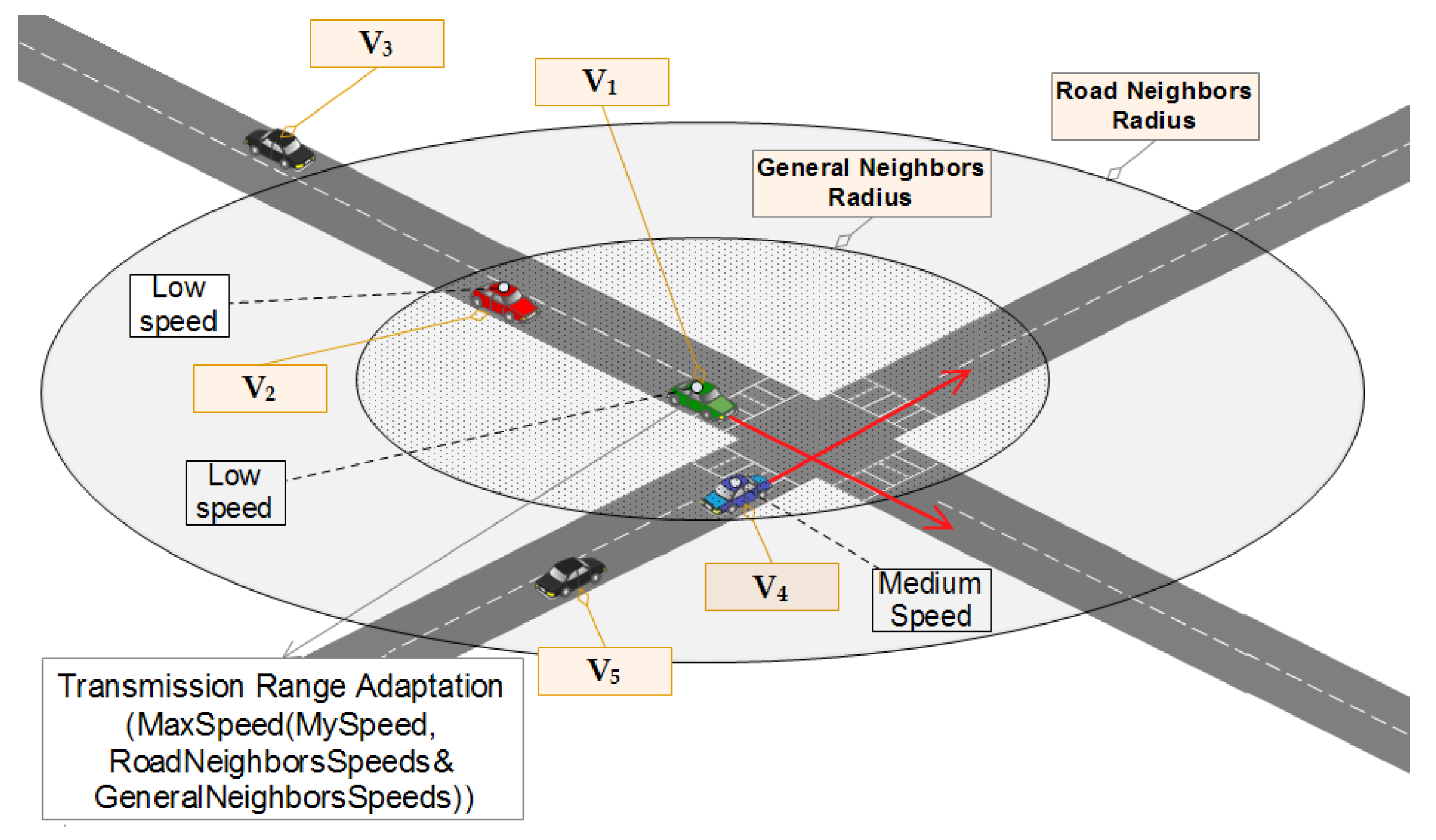
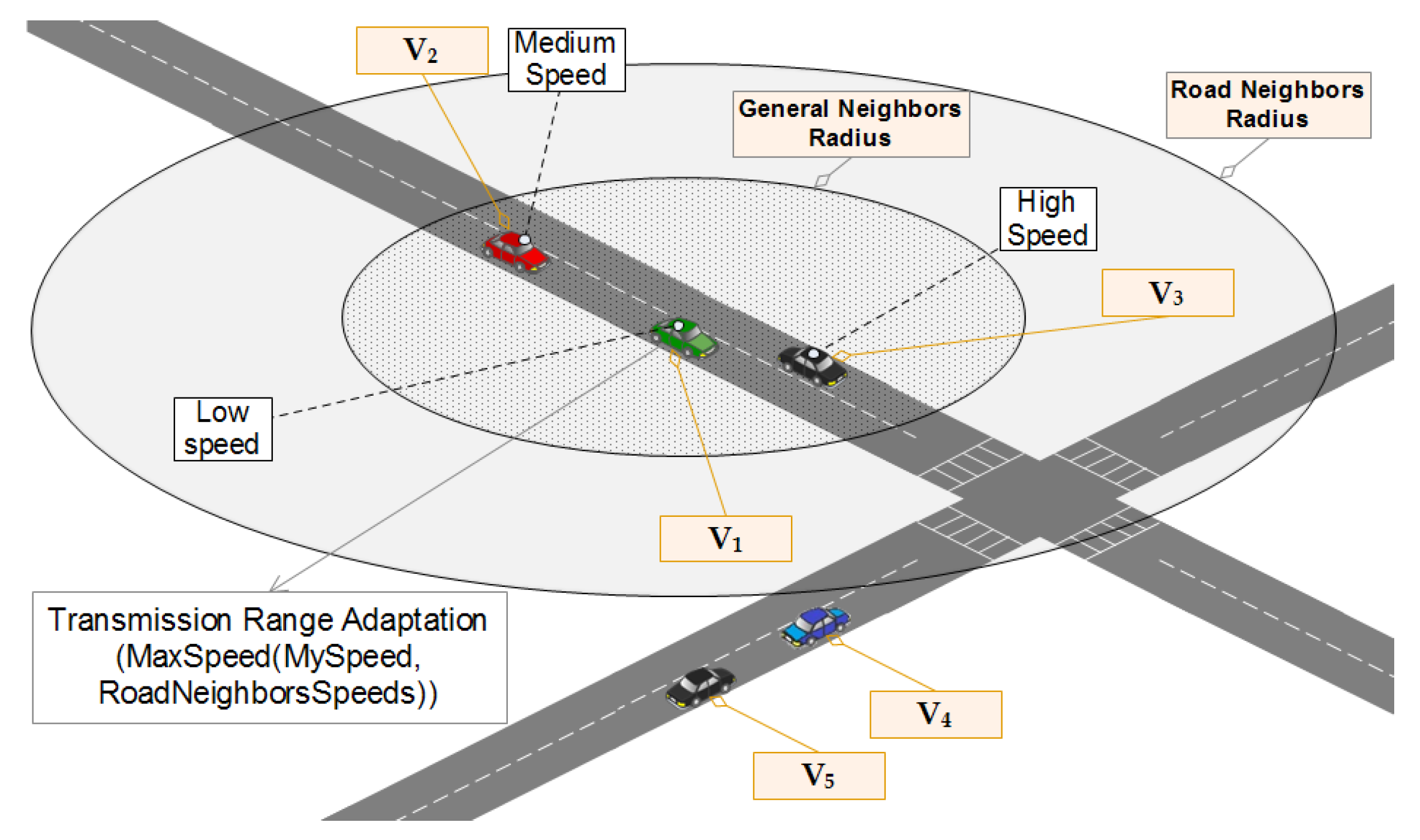
Vehicles are always ready to receive BSMs. When receiving a BSM, the receiving vehicle considers the sender’s position and calculates the distance between itself and the sender. By doing this simple calculation, will be able to get a set of useful information that will determine its behavior. The pseudo-code of receiving a beacon message in WHISPER is illustrated in Algorithm 1. The main conclusions that is going to have after parsing the BSM sent by are the following:
Knowing the distance between itself and .
Whether to consider ’s BSM for transmission power adjustment or just ignore it.
It considers
’s BSM for transmission power adjustment if
is less than or equal to
(shown in the scenario that is illustrated in
Figure 7).
It considers
’s BSM for transmission power adjustment if
is less than or equal to
but also share the same road segment with each other (shown in the scenario that is illustrated in
Figure 8).
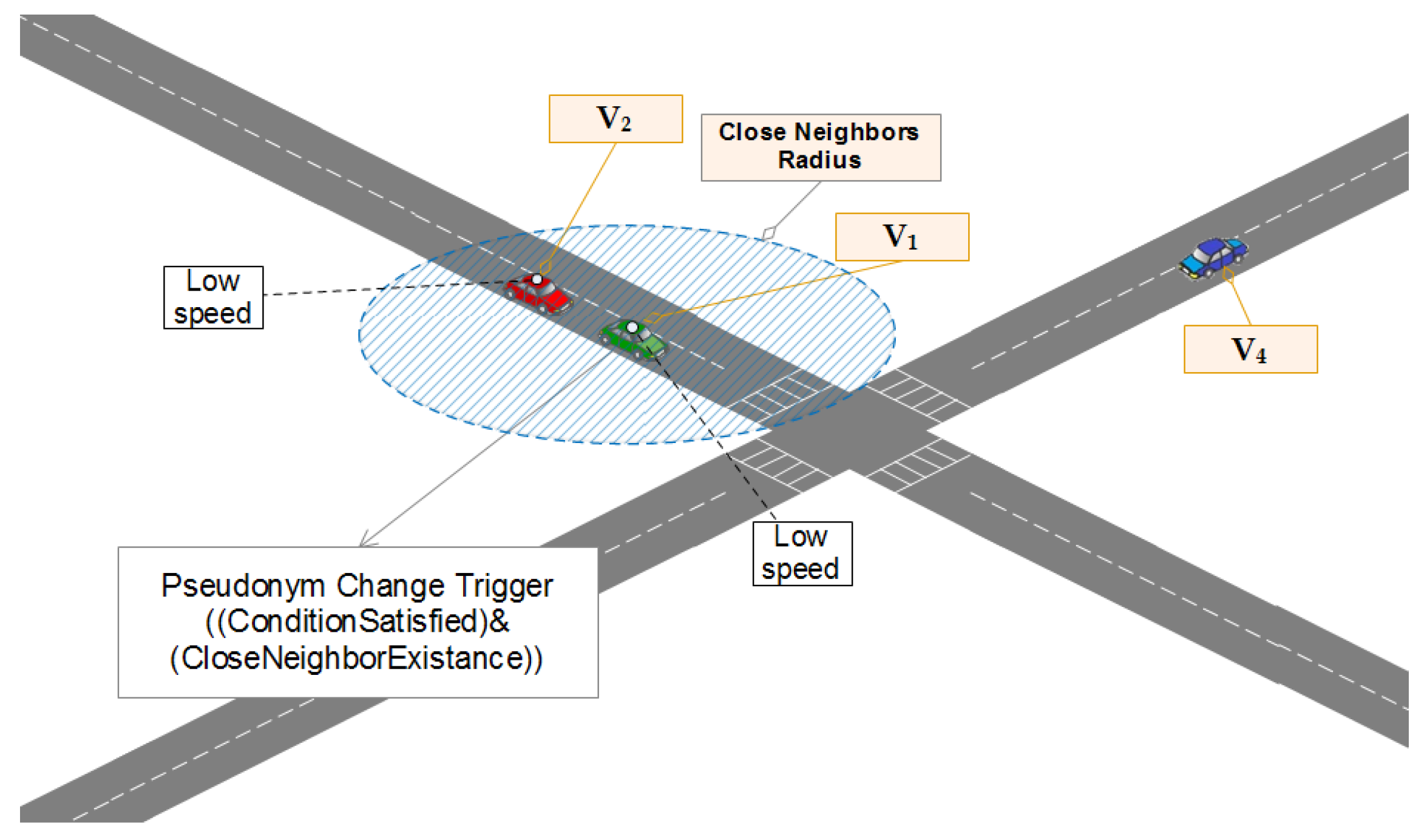
It considers itself eligible for the pseudonym change if is less than or equal to . It does change to as a consequence.
This protocol is called whenever
receives a BSM generated by
and with each call, less than 10 instructions are executed thus a linear complexity per each call
. With this said, by receiving
BSM, the complexity of the whole protocol will be as in Equation (
5):
This indicates that the
protocol is neither time nor resources consumer.
| Algorithm 1 Receiving Beacon |
- 1:
procedureReceiving_Beacon(beacon* bsm) - 2:
- 3:
- 4:
if then - 5:
- 6:
- 7:
if then - 8:
- 9:
end if - 10:
end if - 11:
Process_Beacon(BSM); - 12:
end procedure
|
4.3. Transmission Range Adjustment Protocol
Each vehicle , and after the expires, will send a BSM to inform the nearby vehicles about its location. Particularly, WHISPER adjusts the transmission range prior to the final BSM broadcast. The adjustment is done each time a BSM is received by as explained before. When going to broadcast, uses the value of to decide the appropriate transmission range (between all of the four levels: Low, Medium, beyond-Medium, and High). Algorithm 2 shows the pseudo-code of sending a BSM after making the transmission range adjustment step. Additionally, is reinitialized to 0 after that and is called during this protocol and that is to see the eligibility of changing ’s pseudonym (and certificate respectively). Moreover, is decreased depending on the value of and this is to trigger the pseudonym change (will be seen in the next point). However, if is at max level, there will be no meaning for changing the pseudonym and that is because the attacker is able to collect every sent beacon (the maximum transmission range is used) and that is why is reinitialized to its default value .
This protocol is called whenever
expires and thus, one time per call. However, it calls, in its role, the
protocol. In total, there are 7 instructions without counting the called protocol (
). With this said, the complexity of the
protocol is defined as in Equation (
6):
This indicates that the
protocol does depend on the
protocol.
| Algorithm 2 Sending Beacon |
- 1:
procedureSending_Beacon - 2:
while do - 3:
; - 4:
Prepare_Beacon(BSM); - 5:
- 6:
if then - 7:
- 8:
- 9:
else if then - 10:
- 11:
- 12:
else if then - 13:
- 14:
else - 15:
- 16:
- 17:
end if - 18:
- 19:
Checking_Pseudonym_Change_Trigger(); - 20:
Send_Beacon(BSM); - 21:
end while - 22:
end procedure
|
4.4. Pseudonym Change Trigger Protocol
In order to avoid wasting pseudonyms (certificates) in an inappropriate opportunity, finding an almost good opportunity requires that the pseudonym change trigger must be implemented delicately. Algorithm 3 shows, in a pseudo-code, the way vehicles perform a check to see the eligibility for changing their pseudonyms. When the trigger
Counter reaches or drops below (0) (which is an indicator that
was sending BSMs with a short range for some important period of time)
changes its pseudonym then initializes the trigger
Counter. This whole process provides high confusion chances since the pseudonym change is performed not in the favor of the tracker (see the scenario illustrated in
Figure 9). The
protocol is used each time the
is executed. Its complexity depends on a small and fixed number of instructions (5), thus, can be defined as in Equation (
7):
The
protocol has
as a complexity.
| Algorithm 3 Checking Pseudonym Change Trigger |
- 1:
procedureChecking_Pseudonym_Change_Trigger - 2:
if then - 3:
- 4:
Pseudonym_Change(); - 5:
else if then - 6:
- 7:
Pseudonym_Change(); - 8:
end if - 9:
- 10:
end procedure
|
5. Performance Evaluation
To validate the performances of WHISPER, we use simulation runs in a manhattan grid model created using the NETEDIT script included in SUMO; the mobility simulator [
43]. SUMO is considered as one of the most credible and realistic mobility simulators. The mobility and environment information used for the simulation are presented in
Table 3. The manhattan grid model consists of 9 intersected roads with attached segments where each segment has a length of 200 m.
Concerning the network simulator, we use OMNeT++ [
44]; the component is c++ based and discrete events simulator. OMNet++ allows the integration of diverse frameworks depending on the simulation nature like Veins [
45], which is the vehicular network simulator. Veins acts as a bridge between the mobility simulator SUMO and the network simulator OMNet++. We also employ the PREXT extension [
27] that is developed by Emmara et al.; a Veins extension that integrates a set of (1) location privacy schemes, (2) some privacy metrics such as the traceability and the normalized traceability (described in [
46]), and (3) a Quality of Service (QoS) metric (the consumption of pseudonyms/certificates). A block diagram is elaborated in order to facilitate the comprehension of the interaction between the different simulation tools (shown in
Figure 10). Based on PREXT, WHISPER is evaluated and compared against some other schemes under the same environmental condition using the aforementioned metrics. The schemes’ parameters and the evaluation metrics are also presented in
Table 3.
5.1. The Adversary’s Achieved Traceability
Traceability, the location privacy metric used in this study, is defined as the correctness of an adversary to build the target vehicle’s traces using its eavesdropped beacons [
46]. The results, provided in
Figure 11 show that WHISPER outperformed SLOW, RSP, and CPN in the traceability metric with a clear difference (ranging in the interval of
to
). An important remark is that at dense situations (e.g., with the density of 200 vehicle), the traceability gets augmented a bit. The reason behind the decrease in the privacy level is due to the higher density of vehicles, which can help the attacked collect BSMs from the legitimate cars.
In general, as presented in
Figure 11, WHISPER performs better in terms of the level of privacy that it offered since it achieves a traceability ranging in the interval of
to
. We interpret this as being WHISPER reducing the vehicle’s transmission range according to its and/or the neighbor vehicles’ speeds (according to the safety situation) followed by CPN, RSP, then SLOW, in addition we observe that the traceability decreases when augmenting the number of vehicles in SLOW. The reason is that, in high densities, vehicles would drive with lower speeds, thus, SLOW performs better.
5.2. The Adversary’s Achieved Normalized Traceability
As some vehicles may not perform the pseudonym change, building their traces becomes easy, thus, excluding them gives more fairness to the real level of privacy [
46]; that is the normalized traceability. With this definition, our conducted simulation under the normalized traceability aims to give a more credible and better privacy-reflecting metric to quantify the achieved privacy level of WHISPER, SLOW, RSP, and CPN (shown in
Figure 12).
As stated above, by taking the case of just the vehicles which did change their pseudonyms, we get the achieved normalized traceability as shown in
Figure 12. The results always give WHISPER the leading position since it outperforms the other schemes but this time by achieving an even higher privacy level represented in a lower than
of normalized traceability. The same order of performance remains: CPN, RSP, then SLOW. However, SLOW has achieved better-normalized traceability of about
due to removing vehicles that did not change their pseudonyms at all from the calculation.
5.3. Pseudonym Consumption
Also considered is the QoS metric. The pseudonym consumption has multiple effects and impacts like the use of different pseudonyms (thus, certificates), extra-communications with the corresponding authorities to refill pseudonyms, affecting the routing algorithms [
30], etc. For this reason, the pseudonym consumption metric is crucial. With a clear view,
Figure 13 shows that SLOW is the less-pseudonym consuming scheme followed by RSP and WHISPER respectively, while CPN had a considerable high pseudonyms consumption level. We argue this by the scheme’s nature, when the trigger of
k neighbors is satisfied, a pseudonym change is performed and as
k was taken as 2 by the default parameters, a lot of pseudonym changes occurred.
6. Discussion
For an overall investigation, the performances of CPN, RSP, SLOW, and WHISPER were evaluated in terms of (1) location privacy that gives WHISPER the leading in both (a) traceability and (b) normalized traceability and (2) QoS comes in the favor of SLOW. CPN, under the default parameters (i.e., ), has resulted in a very high pseudonym consumption, thus, considered as a non-wise choice for a deployed pseudonym scheme. The results, clearly show that WHISPER has a very good level of privacy since it achieves traceability ranging in the interval of 10% to 20%. In terms of normalized traceability, WHISPER outperformed the other schemes achieving an even higher privacy level.
Despite WHISPER consuming more pseudonyms (with a remarkably low amount in general) than SLOW and RSP, having it a very high location privacy level represented in the traceability and the normalized traceability gives it the leading position. Thus, we can say that WHISPER, as also compared and summarized in
Table 4, has outperformed the other schemes especially in both the safety and location privacy that are known to be on the top of the security requirements.
Except for the evaluation comparison, WHISPER is an important solution that offers privacy preservation while maintaining at the same time road-safety. This is achieved since vehicles are only hidden from the tracker (occasionally) and not from the close vehicles (always), which makes the use of WHISPER an advantageous method that comes in favor of safety and privacy.
7. Conclusions and Future Work
In this paper, WHISPER, a novel location privacy-preserving scheme that is based on reducing the transmission range while sending the safety beacons was proposed. We presented WHISPER protocols, techniques, and algorithms and compared them against other methods, namely CPN, RSP, and SLOW in terms of the location privacy level (traceability, normalized traceability) and QoS (pseudonyms consumption) metrics. WHISPER clearly outperformed the other schemes in location privacy evaluation, which is an important security requirement, but consumed, lightly, more pseudonyms than SLOW and RSP as the QoS evaluation demonstrated. Furthermore, WHISPER showed its robustness during the evaluation and also provided (1) road safety that is missed by all other silent period schemes in conjunction with (2) location privacy.
The reason why WHISPER is a road-safety mechanism is that the vehicle is only hidden from the tracker (occasionally) and not from close vehicles (always) which made the use of WHISPER (or at least, the change of transmission range protocol) an advantageous feature that works in favor of safety and privacy alike.
As this new technique has not been exploited before in the privacy field, we intend on evaluating the achieved location privacy level versus an internal attacker i.e., when vehicles act as malicious eavesdropping stations in order to bypass the reduction of transmission range and increase the coverage of the attacker. Also, some of the values (e.g., existing in Algorithm 2) are set heuristically, evaluating the performance by optimally adjusting those values dynamically would certainly enhance the obtained privacy level of WHISPER. Moreover technologies like blockchain [
47], cryptography [
48], IDSs [
49], and Edge Computing [
50] which are widely recognized as key enablers for IoV could be integrated or used in parallel with our solution. Finally, using other metrics like the number of sent BSMs, the number of verified signatures, and evaluating WHISPER’s performance under different scenarios like the free-way model are some of our future plans.