Efficient and Privacy-Preserving Energy Trading on Blockchain Using Dual Binary Encoding for Inner Product Encryption †
Abstract
:1. Introduction
2. Background and Related Work
2.1. Energy Blockchain
2.2. FHIPE and Integer Comparison
- The map e and the group operations in , and can be efficiently computed.
- The map e is bilinear, such that, for all , the map e satisfies , where q is the order of and , and .
- The map e has non-degeneracy, i.e., if P and Q are not the identity elements in and , respectively.
- Setup(): When a security parameter is given, the setup algorithm samples , , and , and defines e. The generators and are also selected. Then, it samples from a general linear group of square matrices whose elements are selected from , and computes the matrix , where det denotes the determinant of a matrix. Finally, the setup algorithm outputs the public parameters and the secret key , where q is the order of and .
- : When the secret key sk, a random element , and a row vector are given, the left encryption algorithm outputs where and .
- (sk,: When the secret key sk, a random element , and a row vector are given, the right encryption algorithm outputs where and .
- : When the public parameters op and two ciphertexts , are given, the decryption algorithm calculates and . Finally, it seeks a solution for the discrete logarithm problem . In case z exists, the decryption algorithm outputs it, which is equal to the inner product of and , i.e., ; otherwise, it outputs a symbol that implies that there is no valid z.
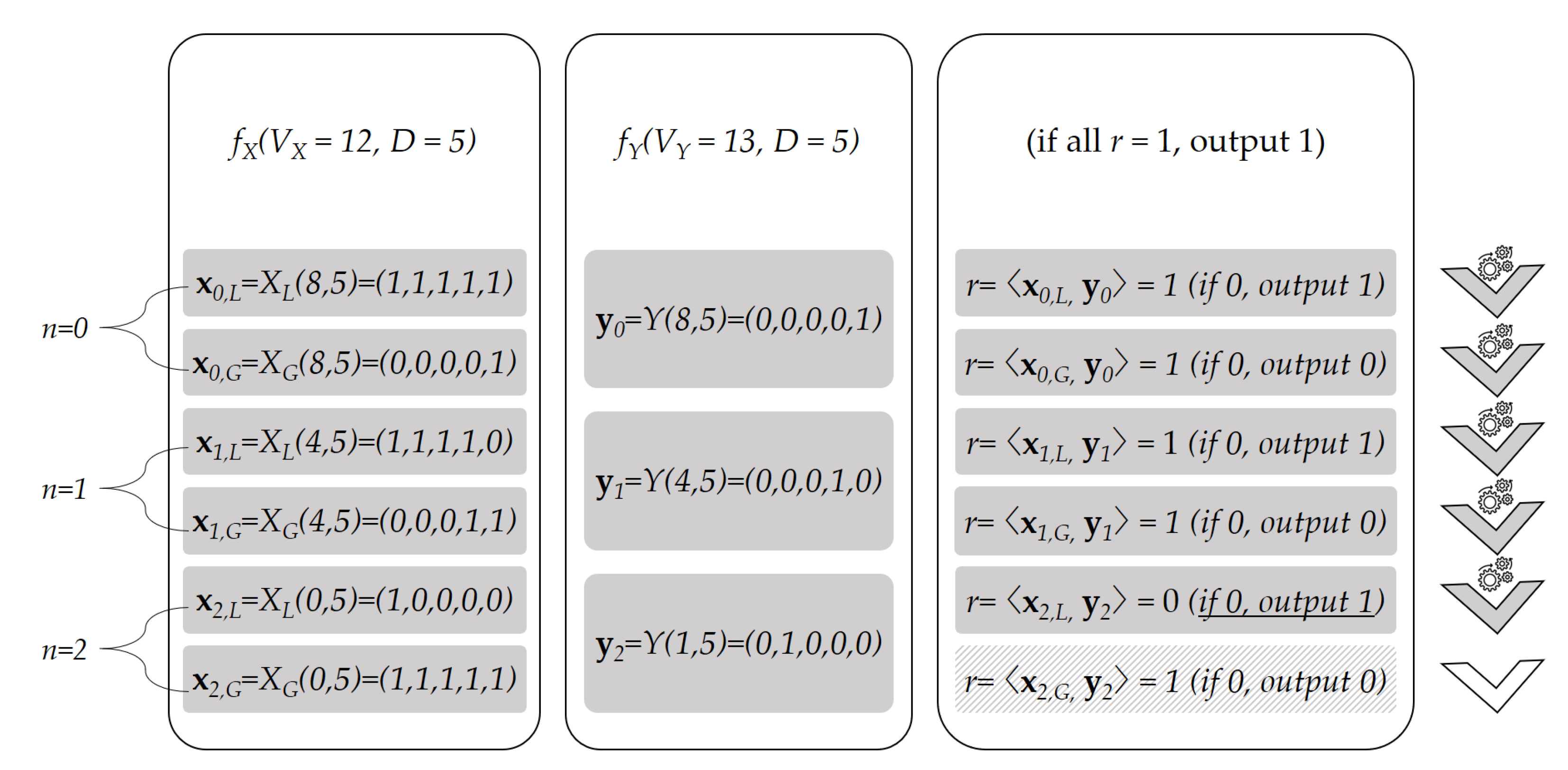
3. Proposed Integer Comparison Method Using Dual Binary Encoding
3.1. Subroutine Y
| 0 | 1 | 2 | 4 | 8 | 16 | 32 | 64 | |
| 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 |
| Algorithm 1: Subroutine to encode 0 or a power of 2 |
|
3.2. Encoding Method
| Algorithm 2: Encoding a value with subroutine Y |
|
3.3. Subroutine
| 0 | 1 | 2 | 4 | 8 | 16 | 32 | 64 | |
| 1 | 1 | 1 | 1 | 1 | 1 | 0 | 0 |
3.4. Subroutine
| 0 | 1 | 2 | 4 | 8 | 16 | 32 | 64 | |
| 0 | 0 | 0 | 0 | 0 | 1 | 1 | 1 |
3.5. Encoding Method
| Algorithm 3: Encoding a value with subroutines and |
|
3.6. Comparing and
- 1.
- means that the nth term of is less than the nth term of .
- 2.
- means that the nth term of is greater than the nth term of .
- 3.
- means that the nth term of equals the nth term of .
| Algorithm4 Comparison of two values encoded in two input vectors |
|
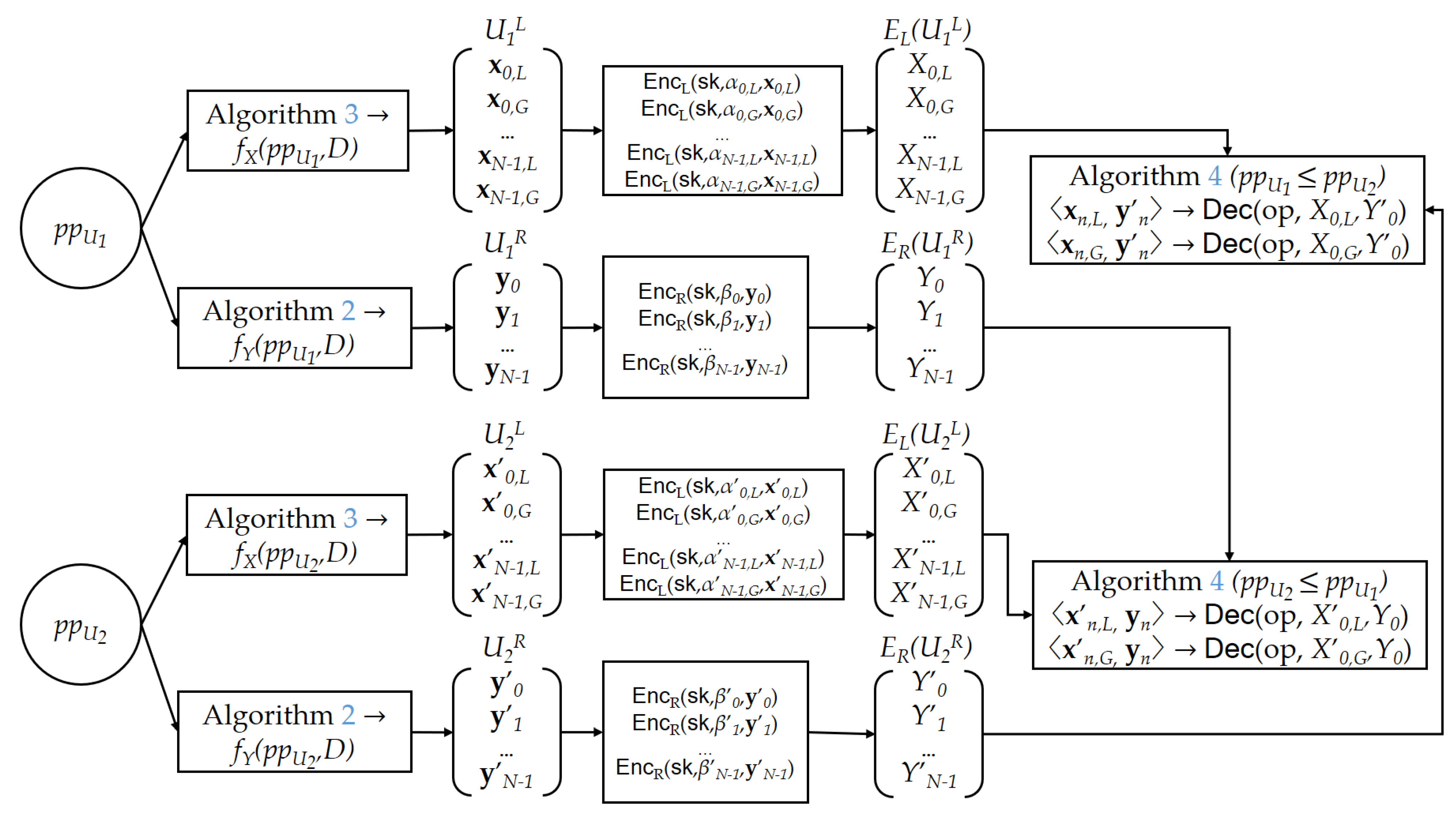
4. Proposed Energy Trading System
4.1. System Components
4.2. Matching Algorithm
| Algorithm 5 INSERT procedure for min-heap [13] |
|
| Algorithm 6 MATCHING procedure to check for possible match [13] |
|
4.3. Proposed Energy Trading Protocol
4.3.1. Setup Stage
4.3.2. Finite State Machine in the Blockchain
4.3.3. Bidding and Matching Operations
4.3.4. Actual Trading
5. Performance Analysis
5.1. Performance Analysis of the Proposed Algorithm
5.2. Performance Analysis of the Proposed System
6. Discussion
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| DER | Distributed Energy Resources |
| DET | Distrubuted Energy Trading |
| DSO | Distributed System Operator |
| FE | Functional Encryption |
| FHIPE | Function-Hiding Inner Product Encryption |
| IEA | International Energy Agency |
| IoE | Internet-of-Energy |
| IPE | Inner Product Encryption |
| OID | One-time identifier |
| P2P | Peer-to-Peer |
| PPT | Probabilistic Polynomial Time |
| PUFs | Physical Unclonable Functions |
| RES | Renewable Energy Systems |
| UID | User identifier |
| UN | United Nations |
References
- Popescu, C.R.G.; Popescu, G.N. An Exploratory Study Based on a Questionnaire Concerning Green and Sustainable Finance, Corporate Social Responsibility, and Performance: Evidence from the Romanian Business Environment. J. Risk Financ. Manag. 2019, 12, 162. [Google Scholar] [CrossRef] [Green Version]
- World Bank. Turn Down the Heat: Why a 4 ∘C Warmer World Must Be Avoided. 2012. Available online: http://hdl.handle.net/10986/11860 (accessed on 1 March 2021).
- United Nations. Transforming Our World: The 2030 Agenda for Sustainable Development; UN General Assembly: New York, NY, USA, 2015. [Google Scholar]
- UNDP Social and Environmental Standards. Available online: https://www.undp.org/content/dam/undp/library/corporate/Social-and-Environmental-Policies-and-Procedures/UNDP%20Social%20and%20Environmental%20Standards_Pre-Launch.pdf (accessed on 1 March 2021).
- OECD. China in a Changing Global Environment. 2015. Available online: https://www.oecd.org/china/china-in-a-changing-global-environment_EN.pdf (accessed on 19 February 2021).
- Kroposki, B.; Johnson, B.; Zhang, Y.; Gevorgian, V.; Denholm, P.; Hodge, B.; Hannegan, B. Achieving a 100% Renewable Grid: Operating Electric Power Systems with Extremely High Levels of Variable Renewable Energy. IEEE Power Energy Mag. 2017, 15, 61–73. [Google Scholar] [CrossRef]
- U.S. Department of Energy Solar Energy Technologies Office. Available online: https://www.energy.gov/eere/solar/enabling-extreme-real-time-grid-integration-solar-energy-energise (accessed on 30 January 2021).
- Demand Response. Available online: https://www.sce.com/business/demand-response (accessed on 30 January 2021).
- Managing Oversupply. Available online: http://www.caiso.com/informed/Pages/ManagingOversupply.aspx (accessed on 30 January 2021).
- Zhou, Y.; Wu, J.; Long, C.; Ming, W. State-of-the-Art Analysis and Perspectives for Peer-to-Peer Energy Trading. Engineering 2020, 6, 739–753. [Google Scholar] [CrossRef]
- Fell, M.J.; Schneiders, A.; Shipworth, D. Consumer Demand for Blockchain-Enabled Peer-to-Peer Electricity Trading in the United Kingdom: An Online Survey Experiment. Energies 2019, 12, 3913. [Google Scholar] [CrossRef] [Green Version]
- Aitzhan, N.Z.; Svetinovic, D. Security and Privacy in Decentralized Energy Trading Through Multi-Signatures, Blockchain and Anonymous Messaging Streams. IEEE Trans. Dependable Secur. Comput. 2018, 15. [Google Scholar] [CrossRef]
- Son, Y.B.; Im, J.H.; Kwon, H.Y.; Jeon, S.Y.; Lee, M.K. Privacy-Preserving Peer-to-Peer Energy Trading in Blockchain-Enabled Smart Grids Using Functional Encryption. Energies 2020, 13, 1321. [Google Scholar] [CrossRef] [Green Version]
- Wang, S.; Taha, A.F.; Wang, J.; Kvaternik, K.; Hahn, A. Energy Crowdsourcing and Peer-to-Peer Energy Trading in Blockchain-Enabled Smart Grids. IEEE Trans. Syst. Man Cybern. B Cybern. 2019, 49, 1612–1623. [Google Scholar] [CrossRef] [Green Version]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 26 January 2021).
- Ethereum. Available online: https://ethereum.org/ (accessed on 26 January 2021).
- Ethereum White Paper. Available online: https://ethereum.org/en/whitepaper/ (accessed on 26 January 2021).
- Wood, G. Ethereum: A Secure Decentralised Generalised Transaction Ledger Petersburg Version. Available online: https://ethereum.github.io/yellowpaper/paper.pdf (accessed on 26 January 2021).
- Ahl, A.; Yarime, M.; Tanaka, K.; Sagawa, D. Review of blockchain-based distributed energy: Implications for institutional development. Renew. Sustain. Energy Rev. 2019, 107, 200–211. [Google Scholar] [CrossRef]
- Mengelkamp, E.; Gärttner, J.; Rock, K.; Kessler, S.; Orsini, L.; Weinhardt, C. Designing microgrid energy markets: A case study: The Brooklyn Microgrid. Appl. Energy 2018, 210, 870–880. [Google Scholar] [CrossRef]
- Sabounchi, M.; Wei, J. Towards resilient networked microgrids: Blockchain-enabled peer-to-peer electricity trading mechanism. In Proceedings of the 2017 IEEE Conference on Energy Internet and Energy System Integration (EI2), Beijing, China, 26–28 November 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Yahaya, A.S.; Javaid, N.; Alzahrani, F.A.; Rehman, A.; Ullah, I.; Shahid, A.; Shafiq, M. Blockchain Based Sustainable Local Energy Trading Considering Home Energy Management and Demurrage Mechanism. Sustainability 2020, 12, 3385. [Google Scholar] [CrossRef] [Green Version]
- Hasankhani, A.; Mehdi Hakimi, S.; Shafie-khah, M.; Asadolahi, H. Blockchain technology in the future smart grids: A comprehensive review and frameworks. Int. J. Electr. Power Energy Syst. 2021, 129, 106811. [Google Scholar] [CrossRef]
- Power Ledger. Available online: https://www.powerledger.io (accessed on 26 January 2021).
- Lo3. Available online: https://lo3energy.com/ (accessed on 26 January 2021).
- Brooklyn Microgrid. Available online: https://www.brooklyn.energy/ (accessed on 26 January 2021).
- SolarCoin. Available online: https://solarcoin.org/ (accessed on 26 January 2021).
- Longo, R.; Podda, A.S.; Saia, R. Analysis of a Consensus Protocol for Extending Consistent Subchains on the Bitcoin Blockchain. Computation 2020, 8, 67. [Google Scholar] [CrossRef]
- Podda, A.; Pompianu, L. An overview of blockchain-based systems and smart contracts for digital coupon. In Proceedings of the IEEE/ACM 42nd International Conference on Software Engineering Workshops 2020, Seoul, Korea, 24 June–16 July 2020; pp. 770–778. [Google Scholar]
- Alizadeh, M.; Andersson, K.; Schelen, O. A Survey of Secure Internet of Things in Relation to Blockchain. J. Internet Serv. Inf. Secur. (JISIS) 2020, 10, 47–75. [Google Scholar]
- Stamatellis, C.; Papadopoulos, P.; Pitropakis, N.; Katsikas, S.; Buchanan, W.J. A Privacy-Preserving Healthcare Framework Using Hyperledger Fabric. Sensors 2020, 20, 6587. [Google Scholar] [CrossRef]
- Ángel Prada-Delgado, M.; Baturone, I.; Dittmann, G.; Jelitto, J.; Kind, A. PUF-derived IoT identities in a zero-knowledge protocol for blockchain. Internet Things 2020, 9, 100057. [Google Scholar] [CrossRef]
- Asif, R.; Ghanem, K.; Irvine, J. Proof-of-PUF Enabled Blockchain: Concurrent Data and Device Security for Internet-of-Energy. Sensors 2021, 21, 28. [Google Scholar] [CrossRef] [PubMed]
- Ben-Sasson, E.; Chiesa, A.; Garman, C.; Green, M.; Miers, I.; Tromer, E.; Virza, M. Zerocash: Decentralized Anonymous Payments from Bitcoin. In Proceedings of the 35th IEEE Symposium on Security and Privacy (SP 2014), Berkeley, CA, USA, 18–21 May 2014; pp. 459–474. [Google Scholar]
- Bünz, B.; Agrawal, S.; Zamani, M.; Boneh, D. Zether: Towards Privacy in a Smart Contract World. Available online: https://crypto.stanford.edu/~buenz/papers/zether.pdf (accessed on 26 January 2021).
- Parno, B.; Howell, J.; Gentry, C.; Raykova, M. Pinocchio: Nearly Practical Verifiable Computation. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 19–22 May 2013. Best Paper Award. [Google Scholar]
- Bünz, B.; Bootle, J.; Boneh, D.; Poelstra, A.; Wuille, P.; Maxwell, G. Bulletproofs: Short Proofs for Confidential Transactions and More. In Proceedings of the 39th IEEE Symposium on Security and Privacy (SP 2018), San Francisco, CA, USA, 20–24 May 2018; pp. 315–334. [Google Scholar]
- Li, Z.; Kang, J.; Yu, R.; Ye, D.; Deng, Q.; Zhang, Y. Consortium Blockchain for Secure Energy Trading in Industrial Internet of Things. IEEE Trans. Ind. Inform. 2017, 14, 3690–3700. [Google Scholar] [CrossRef] [Green Version]
- Kang, J.; Yu, R.; Huang, X.; Maharjan, S.; Zhang, Y.; Hossain, E. Enabling Localized Peer-to-Peer Electricity Trading Among Plug-in Hybrid Electric Vehicles Using Consortium Blockchains. IEEE Trans. Ind. Inform. 2017, 13, 3154–3164. [Google Scholar] [CrossRef]
- Gai, K.; Wu, Y.; Zhu, L.; Qiu, M.; Shen, M. Privacy-Preserving Energy Trading Using Consortium Blockchain in Smart Grid. IEEE Trans. Ind. Inform. 2019, 15, 3548–3558. [Google Scholar] [CrossRef]
- Wang, L.; Wu, J.; Yuan, R.; Zhang, D.; Liu, J.; Jiang, S.; Zhang, Y.; Li, M. Dynamic Adaptive Cross-Chain Trading Mode for Multi-Microgrid Joint Operation. Sensors 2020, 20, 6096. [Google Scholar] [CrossRef]
- Guan, Z.; Wang, N.; Fan, X.; Liu, X.; Wu, L.; Wan, S. Achieving Secure Search over Encrypted Data for E-Commerce: A Blockchain Approach. ACM Trans. Internet Technol. 2020, 21. [Google Scholar] [CrossRef]
- Niu, S.; Chen, L.; Wang, J.; Yu, F. Electronic Health Record Sharing Scheme With Searchable Attribute-Based Encryption on Blockchain. IEEE Access 2020, 8, 7195–7204. [Google Scholar] [CrossRef]
- Kim, S.; Lewi, K.; Mandal, A.; Montgomery, H.; Roy, A.; Wu, D.J. Function-Hiding Inner Product Encryption Is Practical. In Proceedings of the International Conference on Security and Cryptography for Networks (SCN 2018), Amalfi, Italy, 5–7 September 2018; pp. 544–562. [Google Scholar]
- Sahai, A.; Seyalioglu, H. Worry-free Encryption: Functional Encryption with Public Keys. In Proceedings of the 17th ACM Conference on Computer and Communications Security (CCS 2017), Chicago, IL, USA, 4–8 October 2010; pp. 463–472. [Google Scholar]
- Boneh, D.; Sahai, A.; Waters, B. Functional encryption: Definitions and challenges. In Proceedings of the Theory of Cryptography Conference, Providence, RI, USA, 28–30 March 2011; pp. 253–273. [Google Scholar]
- Garg, S.; Gentry, C.; Halevi, S.; Raykova, M.; Sahai, A.; Waters, B. Candidate Indistinguishability Obfuscation and Functional Encryption for All Circuits. In Proceedings of the 2013 IEEE 54th Annual Symposium on Foundations of Computer Science, Berkeley, CA, USA, 26–29 October 2013; pp. 40–49. [Google Scholar]
- Bishop, A.; Jain, A.; Kowalczyk, L. Function-Hiding Inner Product Encryption. In Proceedings of the 21st International Conference on Advances in Cryptology (ASIACRYPT 2015), Auckland, New Zealand, 29 November–3 December 2015; pp. 470–491. [Google Scholar]
- Abdalla, M.; Bourse, F.; De Caro, A.; Pointcheval, D. Simple Functional Encryption Schemes for Inner Products. In Proceedings of the 18th IACR International Workshop on Public Key Cryptography (PKC 2015), Gaithersburg, MD, USA, 30 March–1 April 2015; pp. 733–751. [Google Scholar]
- Datta, P.; Dutta, R.; Mukhopadhyay, S. Functional Encryption for Inner Product with Full Function Privacy. In Proceedings of the 19th IACR International Workshop on Public Key Cryptography (PKC 2016), Taipei, Taiwan, 6–9 March 2016; pp. 164–195. [Google Scholar]
- Kim, S.; Kim, J.; Seo, J.H. A New Approach for Practical Function-Private Inner Product Encryption. Theor. Comput. Sci. 2019, 783, 22–40. [Google Scholar] [CrossRef]
- Gaybullaev, T.; Lee, M.K. Poster: Ternary Encoding Algorithm for Integer Comparison using Multiple Inner Products. In Proceedings of the 21st World Conference on Information Security Applications 2020 (WISA 2020), Jeju Island, Korea, 26–28 August 2020; p. 5. [Google Scholar]
- Han, W.; Xiao, Y. Privacy preservation for V2G networks in smart grid: A survey. Comput. Commun. 2016, 91, 17–28. [Google Scholar] [CrossRef] [Green Version]
- Solidity Documentation. Available online: https://docs.soliditylang.org/en/latest/ (accessed on 26 January 2021).
- Jeon, S.Y.; Im, J.H.; Lee, M.K. Performance improvement of inner product encryption using parallel processing. In Proceedings of the 5th International Conference on Next Generation Computing 2019 (ICNGC 2019), Chiang Mai, Thailand, 19–21 December 2019; pp. 1–4. [Google Scholar]
- Vercauteren, F. Optimal pairings. IEEE Trans. Inf. Theory 2009, 56, 455–461. [Google Scholar] [CrossRef]
- Barreto, P.S.; Naehrig, M. Pairing-friendly elliptic curves of prime order. In Proceedings of the International Workshop on Selected Areas in Cryptography, Kingston, ON, Canada, 11–12 August 2005; pp. 319–331. [Google Scholar]
- Aranha, D.F.; Karabina, K.; Longa, P.; Gebotys, C.H.; Hernandez, J.L. Faster Explicit Formulas for Computing Pairings over Ordinary Curves. In Proceedings of the 30th Annual International Conference on the Theory and Applications of Cryptographic Techniques Advances in Cryptology (EUROCRYPT 2011), Tallinn, Estonia, 15–19 May 2011; pp. 48–68. [Google Scholar]
- Sakemi, Y.; Nogami, Y.; Okeya, K.; Katou, H.; Morikawa, Y. Skew Frobenius Map and Efficient Scalar Multiplication for Pairing-Based Cryptography. In Proceedings of the Cryptology and Network Security, 7th International Conferenc (CANS 2008), Hong Kong, China, 2–4 December 2008; pp. 226–239. [Google Scholar]
- KEPCO Electricity Tariffs. Available online: http://cyber.kepco.co.kr/ckepco/front/jsp/CY/E/E/CYEEHP00102.jsp (accessed on 18 January 2021).
- Foundation, E. The Description of Istanbul Fork from Ethereum Wiki. Available online: https://eth.wiki/en/roadmap/istanbul (accessed on 19 January 2021).
- Antonio Salazar Cardozo, Z.W. EIP1108: Reduce alt_bn128 Precompile Gas Costs. Available online: https://eips.ethereum.org/EIPS/eip-1108 (accessed on 19 January 2021).
- Buterin, V.; Reitwiessner, C. EIP197: Precompiled Contracts for Optimal Ate Pairing Check on The Elliptic Curve alt_bn128. Available online: https://eips.ethereum.org/EIPS/eip-197 (accessed on 30 January 2021).









| D = 8 | 0 | 1 | 2 | 4 | 8 | 16 | 32 | 64 |
|---|---|---|---|---|---|---|---|---|
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | |
| 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | |
| 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | |
| 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | |
| 0 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | |
| 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 |
| D = 8 | 0 | 1 | 2 | 4 | 8 | 16 | 32 | 64 |
|---|---|---|---|---|---|---|---|---|
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | |
| 1 | 1 | 1 | 1 | 1 | 0 | 0 | 0 | |
| 1 | 1 | 1 | 1 | 1 | 1 | 0 | 0 | |
| 1 | 1 | 1 | 1 | 1 | 1 | 1 | 0 | |
| 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 |
| D = 8 | 0 | 1 | 2 | 4 | 8 | 16 | 32 | 64 |
|---|---|---|---|---|---|---|---|---|
| 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | |
| 0 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | |
| 0 | 0 | 1 | 1 | 1 | 1 | 1 | 1 | |
| 0 | 0 | 0 | 1 | 1 | 1 | 1 | 1 | |
| 0 | 0 | 0 | 0 | 1 | 1 | 1 | 1 | |
| 0 | 0 | 0 | 0 | 0 | 1 | 1 | 1 | |
| 0 | 0 | 0 | 0 | 0 | 0 | 1 | 1 | |
| 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 |
| ConsumedGas | (A) Heap Node Creation in [13] | (B) Heap Node Creation (proposed) | (C) Ratio (A)/(B) | (D)COMP in [13] | (E)COMP (proposed) | (F) Ratio (D)/(E) | (G) Norm. Ratio (F)/2.35 | |
| Range of Price | ||||||||
| 2,293,360 | 3,369,742 | 0.68 | 1,340,000 | 1,121,414 | 1.19 | 0.51 | ||
| 4,428,144 | 5,097,334 | 0.87 | 2,620,000 | 1,405,418 | 1.86 | 0.79 | ||
| 8,697,712 | 7,157,309 | 1.21 | 5,180,000 | 1,423,967 | 3.63 | 1.55 | ||
| 17,236,848 | 9,549,645 | 1.80 | 10,300,000 | 1,636,989 | 6.29 | 2.68 | ||
| 34,315,120 | 12,274,426 | 2.80 | 20,540,000 | 2,121,623 | 9.68 | 4.12 | ||
| 68,471,664 | 15,331,680 | 4.47 | 41,020,000 | 2,161,902 | 18.97 | 8.07 | ||
| 136,784,752 | 18,721,328 | 7.31 | 81,980,000 | 2,315,035 | 35.41 | 15.07 | ||
| 273,410,928 | 22,443,544 | 12.18 | 163,900,000 | 2,329,521 | 70.36 | 29.94 | ||
| 546,663,280 | 26,498,268 | 20.63 | 327,740,000 | 3,416,721 | 95.92 | 40.82 | ||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gaybullaev, T.; Kwon, H.-Y.; Kim, T.; Lee, M.-K. Efficient and Privacy-Preserving Energy Trading on Blockchain Using Dual Binary Encoding for Inner Product Encryption. Sensors 2021, 21, 2024. https://doi.org/10.3390/s21062024
Gaybullaev T, Kwon H-Y, Kim T, Lee M-K. Efficient and Privacy-Preserving Energy Trading on Blockchain Using Dual Binary Encoding for Inner Product Encryption. Sensors. 2021; 21(6):2024. https://doi.org/10.3390/s21062024
Chicago/Turabian StyleGaybullaev, Turabek, Hee-Yong Kwon, Taesic Kim, and Mun-Kyu Lee. 2021. "Efficient and Privacy-Preserving Energy Trading on Blockchain Using Dual Binary Encoding for Inner Product Encryption" Sensors 21, no. 6: 2024. https://doi.org/10.3390/s21062024
APA StyleGaybullaev, T., Kwon, H.-Y., Kim, T., & Lee, M.-K. (2021). Efficient and Privacy-Preserving Energy Trading on Blockchain Using Dual Binary Encoding for Inner Product Encryption. Sensors, 21(6), 2024. https://doi.org/10.3390/s21062024







