On-Demand Scheduling of Command and Responses for Low-Power Multihop Wireless Networks †
Abstract
1. Introduction
- Identify and demonstrate the problem of severe collisions between command dissemination and response collection because they were not considered “jointly”.
- Design SCoRe, an “on-demand scheme for joint Scheduling of Command and Responses”, on multihop low-power wireless networks to improve both reliability and latency simultaneously.
- Implement SCoRe on a real low-power embedded platform, and evaluate it through simulations and testbed experiments on 31 devices.
2. Related Work
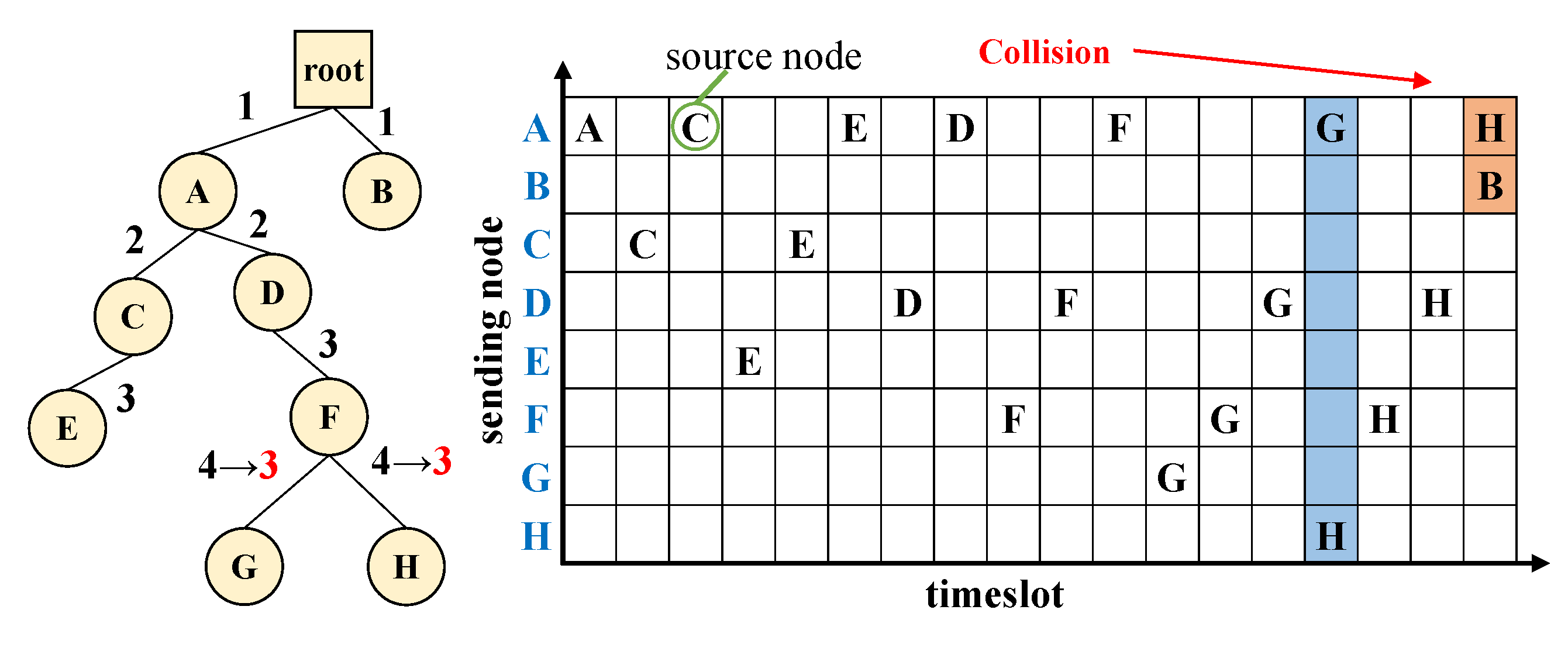
3. Problem
4. SCoRe Design
- Adaptation to network topology: Routing topology in wireless networks are rarely static, and any inconsistency between route and schedule may result in significant performance loss. Therefore, resource scheduling should dynamically adapt to number of devices, physical relocation, and routing topology changes possibly due to link quality variations.
- Little control/memory overhead: Low-power embedded systems with resource constrained devices are typically intolerant of extra packet overhead for energy and bandwidth reasons. Furthermore, multihop routing protocols may take either the storing mode or non-storing mode [24,42] approach depending on the memory constraints for routing tables. Thus, scheduling protocol should generate minimal packet overhead, information exchange should be done locally without a global routing table, and should support both storing and non-storing mode of operation. Furthermore, global time synchronization in a multihop network is a complex task [43,44] and should be avoided if possible.
- Efficient resource assignment over multihop: Because we target multihop, the number of total transmissions required to reach the root (even for same number of devices) depends on the location of each node in the topology. Assigning a dedicated, exclusive transmission slot within the whole network may be a must in a 1-hop TDMA system for fair channel access, but would be too naïve in multihop networks. Nodes that do not interfere with each other should be able to transmit concurrently (spatial re-use) for improved latency and bandwidth.
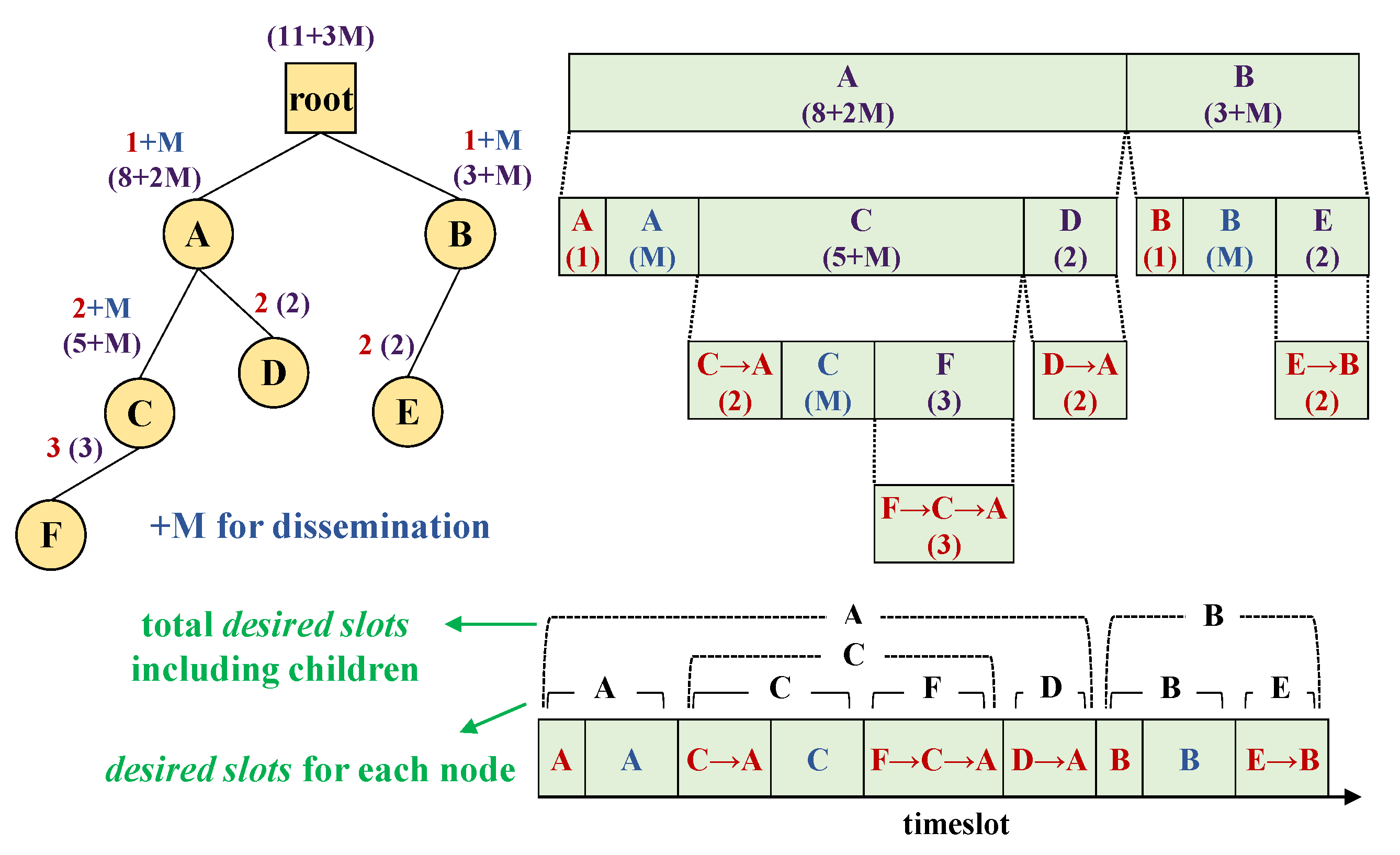
4.1. Recursive Gathering
4.2. Recursive Scheduling
4.3. Concurrent Transmissions for Spatial Reuse
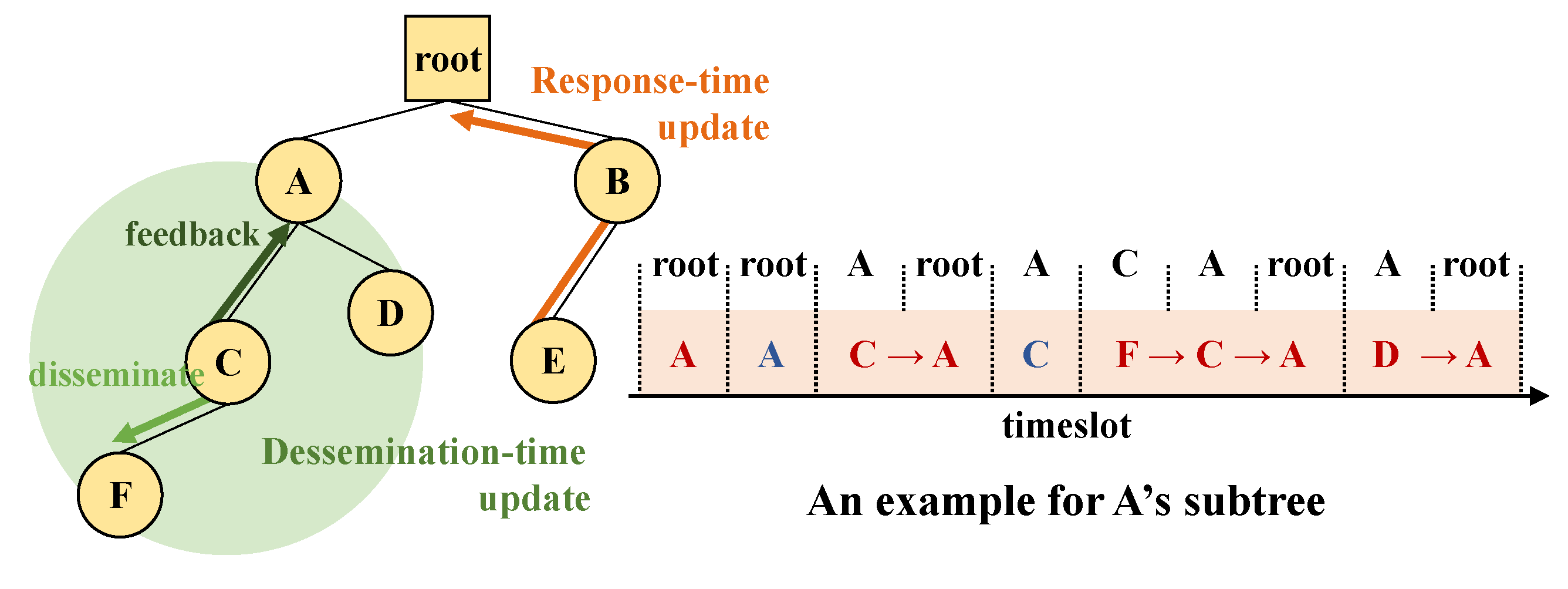
4.4. Faster Updates
- Response time update. Because SCoRe’s timeslot scheduling is up to each parent and all response messages must pass through the parent of a sender, this is a great opportunity to resolve inconsistency. An SCoRe node piggybacks its in the response messages so that its parent can check/update its . When the parent forwards the message to its parent, it modifies the value of field to its own demand. Through this recursive process, newly updated information from a response source is aggregated and reaches the root at response time.
- Dissemination time update. SCoRe’s command messages are based on link broadcast, and a parent also belongs to a child’s 1-hop neighbors. Thus, a parent is also able to hear the command messsage transmission from its child, although it is meant to go downwards. SCoRe uses this characteristic to update any inconsistency. An SCoRe node embeds its into command messages also, and its parent can overhear and update of that node.
5. Evaluation
5.1. Evaluation Setup
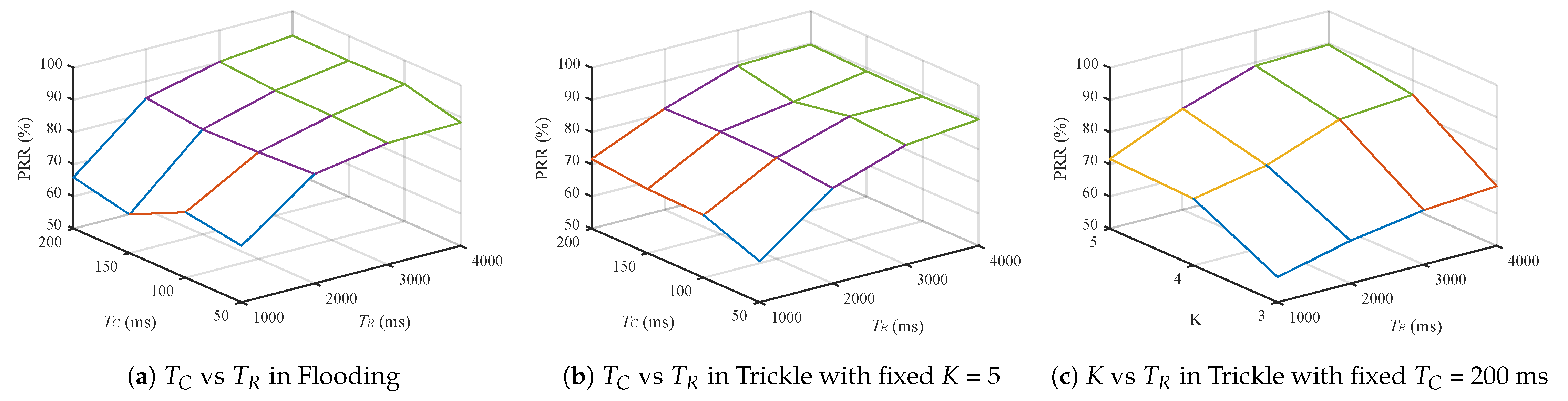
5.2. Parameter Selection for Legacy Schemes
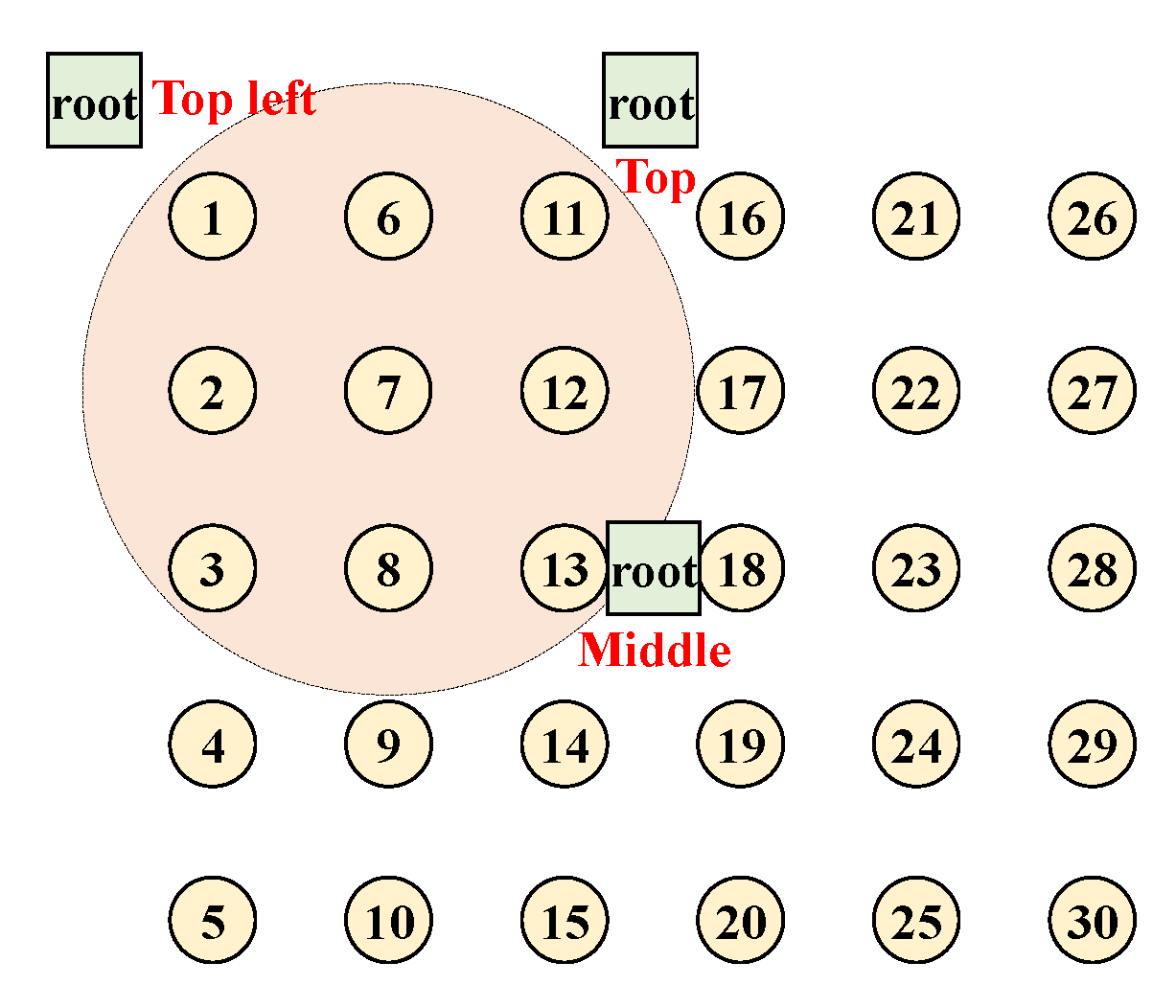
5.3. Simulation on Various Topology
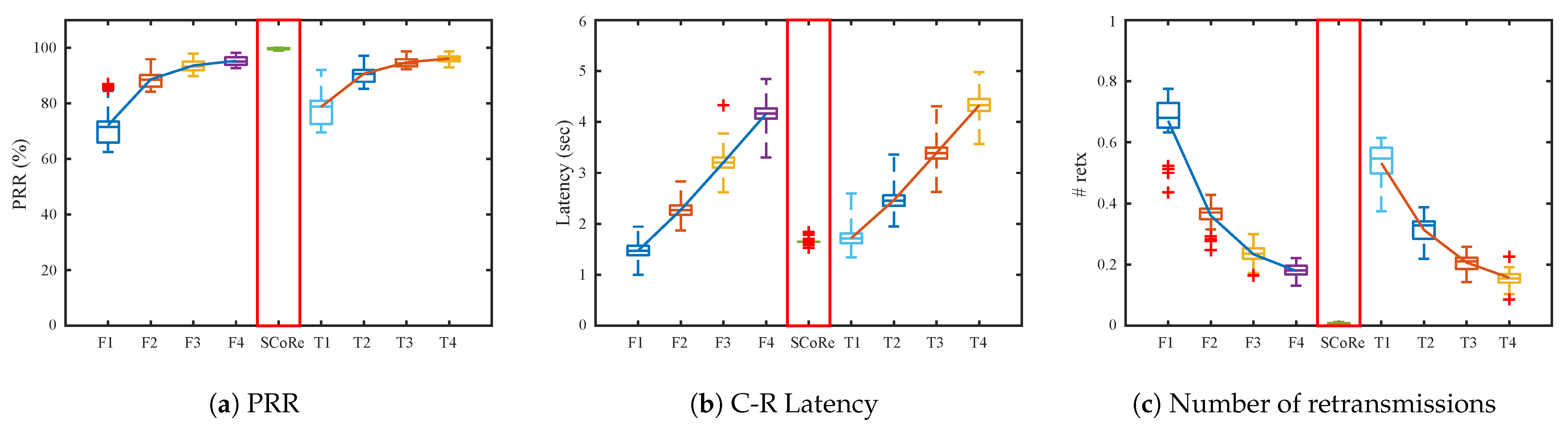
5.4. Testbed Experiment
6. Discussion and Future Work
6.1. Packet Fragmentation
6.2. Coping with Packet Losses
- Recurrent slot assignment. When a SCoRe root generates a command message, it can set a recurrent bit and omit the scheduling info if the routing topology and information has not changed since last command dissemination. A node receiving this command can use timeslots in the same way as the previous command. This method enables each node to be able to receive a command not only from its parent but also neighbors, and thus reduces overhead and improves downward PRR. As a result, recurrent slot assignment makes SCoRe more efficient.
- ETX based timeslot. A SCoRe node demands H, its hop count, for its own response packet transmissions since this is the number of transmissions required to reach the root assuming 100% successful link PRR. However, link retransmissions due to losses may extend beyond its assigned slot, resulting in invading and violating other’s timeslots which will again cause packet collisions. Therefore, careful estimation of the number of retransmissions can help SCoRe to avoid such collisions. ETX [55], expected transmission count, is a very well-known network metric, and RPL also supports ETX based routing called ETXOF [56]. SCoRe can use this metric to request and allocate rather than hop count.
- Permeate into lower-layer protocol. SCoRe’s packet can collide with other protocol’s packets because its on-demand scheduling accounts for only the commands and responses within SCoRe protocol without considering, for example, routing control packets. In fact, most of SCoRe’s packet losses in our evaluations come from packet collisions with RPL routing protocol, the DIO and DAO packets. To avoid this collision, SCoRe may be implemented “jointly” together with the lower-layer protocols. For example, SCoRe can reserve an extra slot within its schedule for other control messages (such as routing) to use. We leave this as our future work.
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Voigt, T.; Osterlind, F. CoReDac: Collision-free command-response data collection. In Proceedings of the 2008 IEEE International Conference on Emerging Technologies and Factory Automation, Hamburg, Germany, 15–18 September 2008; pp. 967–973. [Google Scholar]
- Fan, Z.; Kulkarni, P.; Gormus, S.; Efthymiou, C.; Kalogridis, G.; Sooriyabandara, M.; Zhu, Z.; Lambotharan, S.; Chin, W.H. Smart grid communications: Overview of research challenges, solutions, and standardization activities. IEEE Commun. Surv. Tutor. 2013, 15, 21–38. [Google Scholar] [CrossRef]
- Cisco. Connected Grid Networks for Smart Grid—Field Area Network. Available online: http://www.cisco.com/web/strategy/energy/field_area_network.html (accessed on 21 January 2021).
- Kim, H.S.; Cho, H.; Lee, M.S.; Paek, J.; Ko, J.; Bahk, S. MarketNet: An Asymmetric Transmission Power-based Wireless System for Managing e-Price Tags in Markets. In Proceedings of the 13th ACM International Conference on Embedded Networked Sensor Systems, Seoul, Korea, 3 November 2015; pp. 281–294. [Google Scholar]
- Ock, J.; Kim, H.; Kim, H.S.; Paek, J.; Bahk, S. Low-power Wireless with Denseness: The Case of an Electronic Shelf Labeling System - Design and Experience. IEEE Access 2019, 7, 163887–163897. [Google Scholar] [CrossRef]
- Park, J.; Nam, W.; Kim, T.; Choi, J.; Lee, S.; Yoon, D.; Paek, J.; Ko, J. Glasses for the Third Eye: Improving Clinical Data Analysis with Motion Sensor-based Filtering. In Proceedings of the 15th ACM Conference on Embedded Network Sensor Systems, Delft, The Netherlands, 6 November 2017; pp. 1–14. [Google Scholar]
- Paek, J.; Greenstein, B.; Gnawali, O.; Jang, K.Y.; Joki, A.; Vieira, M.; Hicks, J.; Estrin, D.; Govindan, R.; Kohler, E. The Tenet Architecture for Tiered Sensor Networks. ACM Trans. Sens. Netw. 2010, 6, 34:1–34:44. [Google Scholar] [CrossRef]
- Han, D.; Lim, J. Smart home energy management system using IEEE 802.15.4 and zigbee. IEEE Trans. Consum. Electron. 2010, 56, 1403–1410. [Google Scholar] [CrossRef]
- Lin, J.C.; Paul, S. RMTP: A reliable multicast transport protocol. In Proceedings of the IEEE INFOCOM ’96. Conference on Computer Communications, San Francisco, CA, USA, 24–28 March 1996; pp. 1414–1424. [Google Scholar]
- DeLucia, D.; Obraczka, K. Multicast feedback suppression using representatives. In Proceedings of the INFOCOM ’97, Kobe, Japan, 7–11 April 1997; pp. 463–470. [Google Scholar]
- Levine, B.N.; Garcia-Luna-Aceves, J.J. A comparison of known classes of reliable multicast protocols. In Proceedings of the 1996 International Conference on Network Protocols (ICNP-96), Columbus, OH, USA, 29 October–1 November 1996; pp. 112–121. [Google Scholar]
- Ferrari, F.; Zimmerling, M.; Thiele, L.; Saukh, O. Efficient network flooding and time synchronization with glossy. In Proceedings of the 10th ACM/IEEE International Conference on Information Processing in Sensor Networks, Chicago, IL, USA, 12–14 April 2011. [Google Scholar]
- Levis, P.; Patel, N.; Culler, D.; Shenker, S. Trickle: A Self-regulating Algorithm for Code Propagation and Maintenance in Wireless Sensor Networks. In Proceedings of the First USENIX/ACM Symposium on Network Systems Design and Implementation, San Francisco, CA, USA, 29–31 March 2004. [Google Scholar]
- Bedewy, A.M.; Sun, Y.; Shroff, N.B. Age-optimal information updates in multihop networks. In Proceedings of the 2017 IEEE International Symposium on Information Theory (ISIT), Aachen, Germany, 25–30 June 2017; pp. 576–580. [Google Scholar]
- Lu, J.; Whitehouse, K. Flash Flooding: Exploiting the Capture Effect for Rapid Flooding in Wireless Sensor Networks. In Proceedings of the IEEE INFOCOM 2009, Rio de Janeiro, Brazil, 19–25 April 2009. [Google Scholar]
- Kulkarni, S.S.; Arumugam, M. Infuse: A TDMA Based Data Dissemination Protocol For Sensor Networks. Int. J. Distrib. Sens. Netw. 2006, 2, 55–78. [Google Scholar] [CrossRef]
- Ye, F.; Luo, H.; Cheng, J.; Lu, S.; Zhang, L. Hexagonal Two Tier Data Dissemination model for large scale wireless sensor networks. In Proceedings of the 2012 Japan-Egypt Conference on Electronics, Communications and Computers, Alexandria, Egypt, 6–9 March 2012. [Google Scholar]
- Hui, J.W.; Culler, D. The Dynamic Behavior of a Data Dissemination Protocol for Network Programming at Scale. In Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems (SenSys), Baltimore, MD, USA, 3 November 2004; pp. 81–94. [Google Scholar]
- Chen, J.; Guan, Y.; Pooch, U. An Efficient Data Dissemination Method in Wireless Sensor Networks. In Proceedings of the IEEE Global Telecommunications Conference, Dallas, TX, USA, 29 November–3 December 2004. [Google Scholar]
- Nail, V.; Arora, A.; Sinha, P. Sprinkler: A Reliable and Energy Efficient Data Dissemination Service for Wireless Embedded Devices. In Proceedings of the 26th IEEE International Real-Time Systems Symposium (RTSS’05), Miami, FL, USA, 5–8 December 2005. [Google Scholar]
- Shu, T.; Liu, W.; Wang, T.; Deng, Q.; Zhao, M.; Xiong, N.N.; Li, X.; Liu, A. Broadcast Based Code Dissemination Scheme for Duty Cycle Based Wireless Sensor Networks. IEEE Access 2019, 7, 105258–105286. [Google Scholar] [CrossRef]
- Jeong, G.; Park, M.; Paek, J. A2-Trickle: Adaptive & Aligned Trickle for Rapid and Reliable Dissemination in Low-Power Wireless Networks. IEEE Access 2020, 8, 214374–214382. [Google Scholar] [CrossRef]
- Gnawali, O.; Fonseca, R.; Jamieson, K.; Moss, D.; Levis, P. Collection Tree Protocol. In Proceedings of the 7th ACM Conference on Embedded Networked Sensor Systems, Berkeley, CA, USA, 4–6 November 2009; pp. 1–14. [Google Scholar]
- Winter, T.; Thubert, P.; Brandt, A.; Hui, J.; Kelsey, R.; Levis, P.; Pister, K.; Struik, R.; Vasseur, J.; Alexander, R. RPL: IPv6 Routing Protocol for Low-Power and Lossy Networks. Available online: https://tools.ietf.org/id/draft-ietf-roll-rpl-13.html (accessed on 21 January 2021).
- Kim, H.S.; Paek, J.; Bahk, S. QU-RPL: Queue Utilization based RPL for Load Balancing in Large Scale Industrial Applications. In Proceedings of the 2015 12th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), Seattle, WA, USA, 22–25 June 2015. [Google Scholar]
- Lorincz, K.; Malan, D.; Fulford-Jones, T.R.F.; Nawoj, A.; Clavel, A.; Shnayder, V.; Mainland, G.; Moulton, S.; Welsh, M. Sensor Networks for Emergency Response: Challenges and Opportunities. IEEE Pervasive Comput. 2004, 3, 16–23. [Google Scholar] [CrossRef]
- Duquennoy, S.; Al Nahas, B.; Landsiedel, O.; Watteyne, T. Orchestra: Robust mesh networks through autonomously scheduled TSCH. In Proceedings of the 13th ACM Conference on Embedded Networked Sensor Systems, Seoul, Korea, 4 November 2015; pp. 337–350. [Google Scholar]
- Jeong, S.; Paek, J.; Kim, H.S.; Bahk, S. TESLA: Traffic-aware Elastic Slotframe Adjustment in TSCH Networks. IEEE Access 2019, 7, 130468–130483. [Google Scholar] [CrossRef]
- Kim, H.S.; Paek, J.; Culler, D.E.; Bahk, S. PC-RPL: Joint Control of Routing Topology and Transmission Power in Real Low-Power Lossy Network. ACM Trans. Sens. Netw. 2020, 16. [Google Scholar] [CrossRef]
- Jeong, S.; Park, E.; Woo, D.; Kim, H.S.; Paek, J.; Bahk, S. MAPLE: Mobility Support using Asymmetric Transmit Power in Low-power and Lossy Networks. J. Commun. Netw. 2018, 20, 414–424. [Google Scholar] [CrossRef]
- Paek, J.; Govindan, R. RCRT: Rate-controlled Reliable Transport Protocol for Wireless Sensor Networks. ACM Trans. Sens. Netw. 2010, 7, 20:1–20:45. [Google Scholar] [CrossRef]
- Polastre, J.; Szewczyk, R.; Culler, D. Telos: Enabling Ultra-Low Power Wireless Research. In Proceedings of the (IPSN 2005) Fourth International Symposium on Information Processing in Sensor Networks, Boise, ID, USA, 15 April 2005. [Google Scholar]
- Aijaz, A.; Raza, U. DeAMON: A decentralized adaptive multi-hop scheduling protocol for 6TiSCH wireless networks. IEEE Sens. J. 2017, 17, 6825–6836. [Google Scholar] [CrossRef]
- Thubert, P.; Watteyne, T.; Struik, R.; Richardson, M. An Architecture for IPv6 over the TSCH mode of IEEE 802.15.4. Available online: https://tools.ietf.org/id/draft-ietf-6tisch-architecture-15.html (accessed on 21 January 2021).
- Accettura, N.; Vogli, E.; Palattella, M.R.; Grieco, L.A.; Boggia, G.; Dohler, M. Decentralized Traffic Aware Scheduling in 6TiSCH Networks: Design and Experimental Evaluation. IEEE Internet Things J. 2015, 2, 455–470. [Google Scholar] [CrossRef]
- Jeong, S.; Kim, H.S.; Paek, J.; Bahk, S. OST: On-Demand TSCH Scheduling with Traffic-awareness. In Proceedings of the IEEE INFOCOM, Toronto, ON, Canada, 8 July 2020; pp. 69–78. [Google Scholar]
- Zhang, H.; Soldati, P.; Johansson, M. Performance bounds and latency-optimal scheduling for convergecast in WirelessHART networks. IEEE Trans. Wirel. Commun. 2013, 12, 2688–2696. [Google Scholar] [CrossRef]
- Kim, H.S.; Ko, J.; Culler, D.E.; Paek, J. Challenging the IPv6 Routing Protocol for Low-Power and Lossy Networks (RPL): A Survey. IEEE Commun. Surv. Tutor. 2017, 19, 2502–2525. [Google Scholar] [CrossRef]
- Hill, J.; Szewczyk, R.; Woo, A.; Hollar, S.; Culler, D.; Pister, K. System architecture directions for network sensors. In Proceedings of the ninth international conference on Architectural support for programming languages and operating systems, Cambridge, MA, USA, 15 November 2000; pp. 93–104. [Google Scholar]
- Österlind, F.; Dunkels, A.; Eriksson, J.; Finne, N.; Voigt, T. Cross-level sensor network simulation with COOJA. In Proceedings of the 2006 31st IEEE Conference on Local Computer Networks, Tampa, FL, USA, 14–16 November 2006. [Google Scholar]
- Ko, J.; Dawson-Haggerty, S.; Gnawali, O.; Culler, D.; Terzis, A. Evaluating the Performance of RPL and 6LoWPAN in TinyOS. In Proceedings of the Workshop on Extending the Internet to Low power and Lossy Networks (IP+SN 2011), Chicago, IL, USA, 11 April 2011. [Google Scholar]
- Ko, J.; Jeong, J.; Park, J.; Jun, J.A.; Gnawali, O.; Paek, J. DualMOP-RPL: Supporting Multiple Modes of Downward Routing in a Single RPL Network. ACM Trans. Sens. Netw. 2015, 11, 39:1–39:20. [Google Scholar] [CrossRef]
- Marot, M.; Kusy, B.; Simon, G.; Ledeczi, A. The flooding time synchronization protocol. In Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems (SenSys), Baltimore, MD, USA, 3 November 2004; pp. 39–49. [Google Scholar]
- Gutiérrez, M.; Steiner, W.; Dobrin, R.; Punnekkat, S. Synchronization Quality of IEEE 802.1AS in Large-Scale Industrial Automation Networks. In Proceedings of the 2017 IEEE Real-Time and Embedded Technology and Applications Symposium (RTAS), Pittsburgh, PA, USA, 18–21 April 2017; pp. 273–282. [Google Scholar]
- Clausen, T.H.; Verdière, A.C.D. The LLN On-demand Ad hoc Distance-vector Routing Protocol - Next Generation (LOADng). Available online: https://hal.inria.fr/inria-00611181/document (accessed on 21 January 2021).
- The IEEE Standards Association. IEEE Recommended Practice for Routing Packets in IEEE 802.15.4 Dynamically Changing Wireless Networks. IEEE Std 802.15.10-2017 2017, 1–143. [CrossRef]
- Bharghavan, V.; Demers, A.; Shenker, S.; Zhang, L. MACAW: Media Access Protocol for Wireless LANs. ACM SIGCOMM Comput. Commun. Rev. 1994, 24. [Google Scholar] [CrossRef]
- Levis, P.; Clausen, T.; Hui, J.; Gnawali, O.; Ko, J. The Trickle Algorithm. Available online: https://tools.ietf.org/html/rfc6206 (accessed on 21 January 2021).
- Levis, P.; Culler, D. Maté: A Tiny Virtual Machine for Sensor Networks. In Proceedings of the 10th International Conference on Architectural Support for Programming Languages and Operating Systems (ASPLOS X), San Jose, CA, USA, 5–9 October 2002; pp. 85–95. [Google Scholar]
- Ancillotti, E.; Bruno, R.; Conti, M.; Mingozzi, E.; Vallati, C. Trickle-L2: Lightweight link quality estimation through Trickle in RPL networks. In Proceedings of the IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks 2014, Sydney, NSW, Australia, 19 June 2014; pp. 1–9. [Google Scholar]
- Hui, J.; Kelsey, R. Multicast Protocol for Low-Power and Lossy Networks (MPL). Available online: https://tools.ietf.org/html/rfc7731 (accessed on 21 January 2021).
- Thubert, P. Objective Function Zero for the Routing Protocol for Low-Power and Lossy Networks (RPL). Available online: https://www.hjp.at/doc/rfc/rfc6552.html (accessed on 21 January 2021).
- Hithnawi, A.; Shafagh, H.; Duquennoy, S. Understanding the impact of cross technology interference on IEEE 802.15.4. In Proceedings of the 9th ACM International Workshop on Wireless Network Testbeds, Experimental Evaluation and Characterization, Maui, HI, USA, 7 September 2014; pp. 49–56. [Google Scholar]
- Yang, P.; Yan, Y.; Li, X.Y.; Zhang, Y.; Tao, Y.; You, L. Taming cross-technology interference for Wi-Fi and ZigBee coexistence networks. IEEE Trans. Mob. Comput. 2015, 15, 1009–1021. [Google Scholar] [CrossRef]
- Couto, D.S.J.D.; Aguayo, D.; Bicket, J.; Morris, R. A High-Throughput Path Metric for Multi-Hop Wireless Routing. In Proceedings of the 9th Annual International Conference on Mobile Computing and Networking, San Diego, CA, USA, 17 September 2003; pp. 134–146. [Google Scholar]
- Gnawali, O.; Levis, P. The ETX Objective Function for RPL. Available online: https://tools.ietf.org/id/draft-gnawali-roll-etxof-01.html (accessed on 21 January 2021).





Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Park, M.; Paek, J. On-Demand Scheduling of Command and Responses for Low-Power Multihop Wireless Networks. Sensors 2021, 21, 738. https://doi.org/10.3390/s21030738
Park M, Paek J. On-Demand Scheduling of Command and Responses for Low-Power Multihop Wireless Networks. Sensors. 2021; 21(3):738. https://doi.org/10.3390/s21030738
Chicago/Turabian StylePark, Mingyu, and Jeongyeup Paek. 2021. "On-Demand Scheduling of Command and Responses for Low-Power Multihop Wireless Networks" Sensors 21, no. 3: 738. https://doi.org/10.3390/s21030738
APA StylePark, M., & Paek, J. (2021). On-Demand Scheduling of Command and Responses for Low-Power Multihop Wireless Networks. Sensors, 21(3), 738. https://doi.org/10.3390/s21030738





