An Adaptive Routing Algorithm Based on Relation Tree in DTN
Abstract
:1. Introduction
- We propose a new method for constructing the Relation Trees, which is based on the fact that in most application scenarios of DTN, nodes exhibit social attributes.
- We propose a sub-policy forwarding method based on the Relation Tree, which is capable of more targeted forwarding based on the social attributes of each node.
- We propose an adaptive replication method based on node cache occupancy that can adapt to the dynamically changing network environment.
2. Related Work
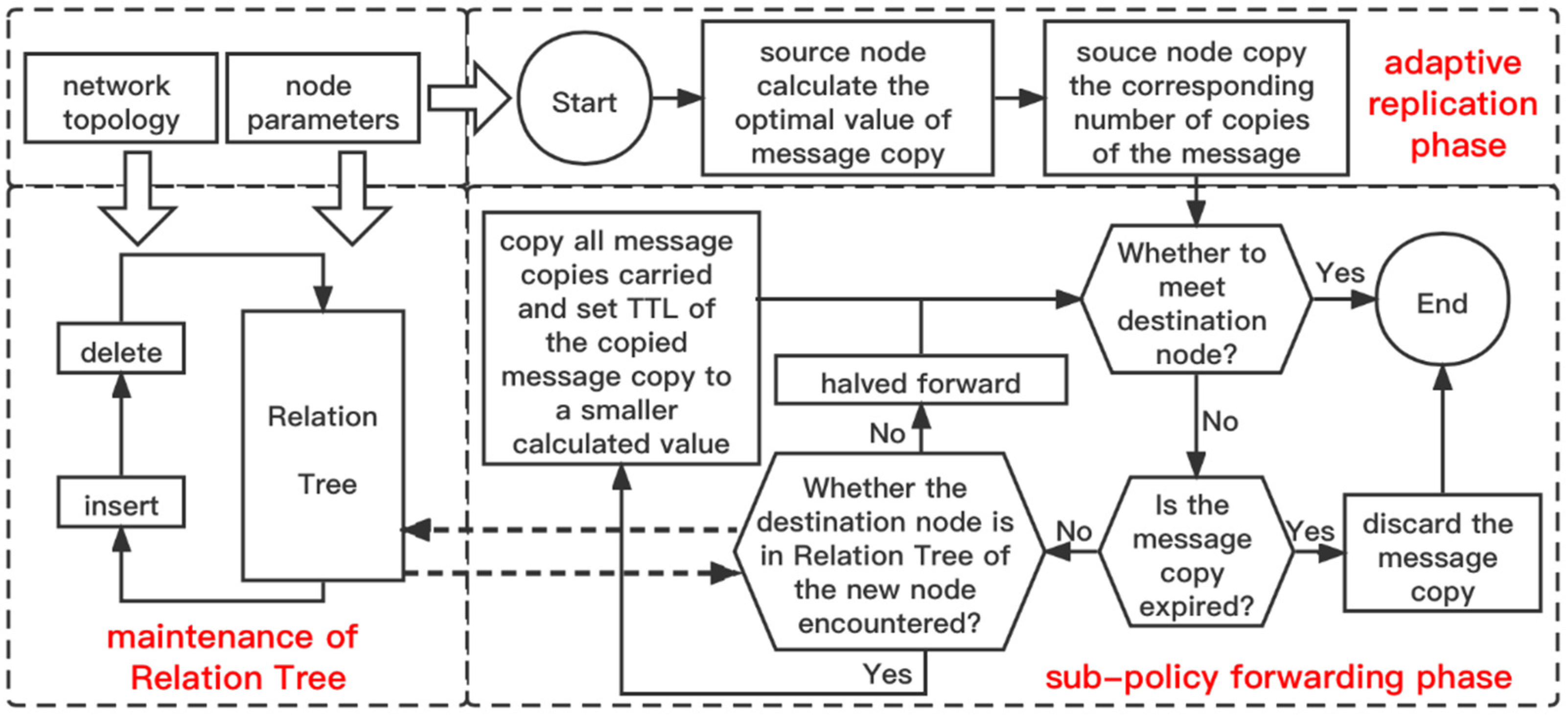
3. Overview
4. Relation Tree
4.1. Maintenance of the Relation Tree
| Algorithm1. Updating Relation Tree |
| Input: , set of nodes in the network , the number of times and meet in a memory cycle T , the relation tree of node , the relation tree of node M, relationship threshold 1: if encounters and then 2: add as a child node of in 3: for each child node of in do 4: if then 5: add as a child node of in 6: end if 7: end for 8: end if 9: for each child node of in do 10: if then 11: remove from 12: end if 13: end for |
4.1.1. Tree Insertion
- Add the new node B to become a child of the root node A.
- Add all nodes in the original Relation Tree of B that are not nodes in the Relation Tree of A and whose encounter times with B exceeds M (nodes in the Relation Tree of B with depth 2 and not in the Relation Tree of A) to become children node of B in the Relation Tree of A.
4.1.2. Tree Deletion
4.2. Important Parameters Related to the Relation Tree
5. Algorithm Design
5.1. Adaptive Replication Phase
5.2. Sub-Policy Forwarding Phase
- If the Relation Tree of the new node does not contain the destination node, half of the message copies carried by themselves (rounded down) are forwarded to the new node. This forwarding strategy uses halving propagation to improve the efficiency of breadth-first forwarding among unfamiliar nodes.
- If the Relation Tree of the new node contains the destination node, all the message copies carried are copied and forwarded to the new node, and the survival time () of these newly copied generated message copies is shown in Equation (3). Where , ensuring < , because the destination node is in the Relation Tree of the new node, the encounter expectation is higher, and the message copies generated by the new replication only need a smaller survival time to avoid wasting network resources. This forwarding strategy can effectively accelerate the forwarding efficiency in the final stage of messages by exploiting the flooding effect while keeping the negative impact of the flooding effect in a localized range within a short period of time.
| Algorithm2. Forwarding Phase |
| Input: , set of nodes in the network , the number of times and meet in a memory cycle T , the relation tree of node , the relation tree of node M, relationship threshold T, memory cycle , the number of copies of carried by node 1: if encounters then 2: for each message in do 3: if then 4: destination 5: if then 6: directly forwards to 7: else if then 8: 9: 10: else then 11: 12: 13: end if 14: end if 15: end for 16: end if |
6. Simulation
6.1. Simulation Scenarios and Parameters
6.2. Simulation Results
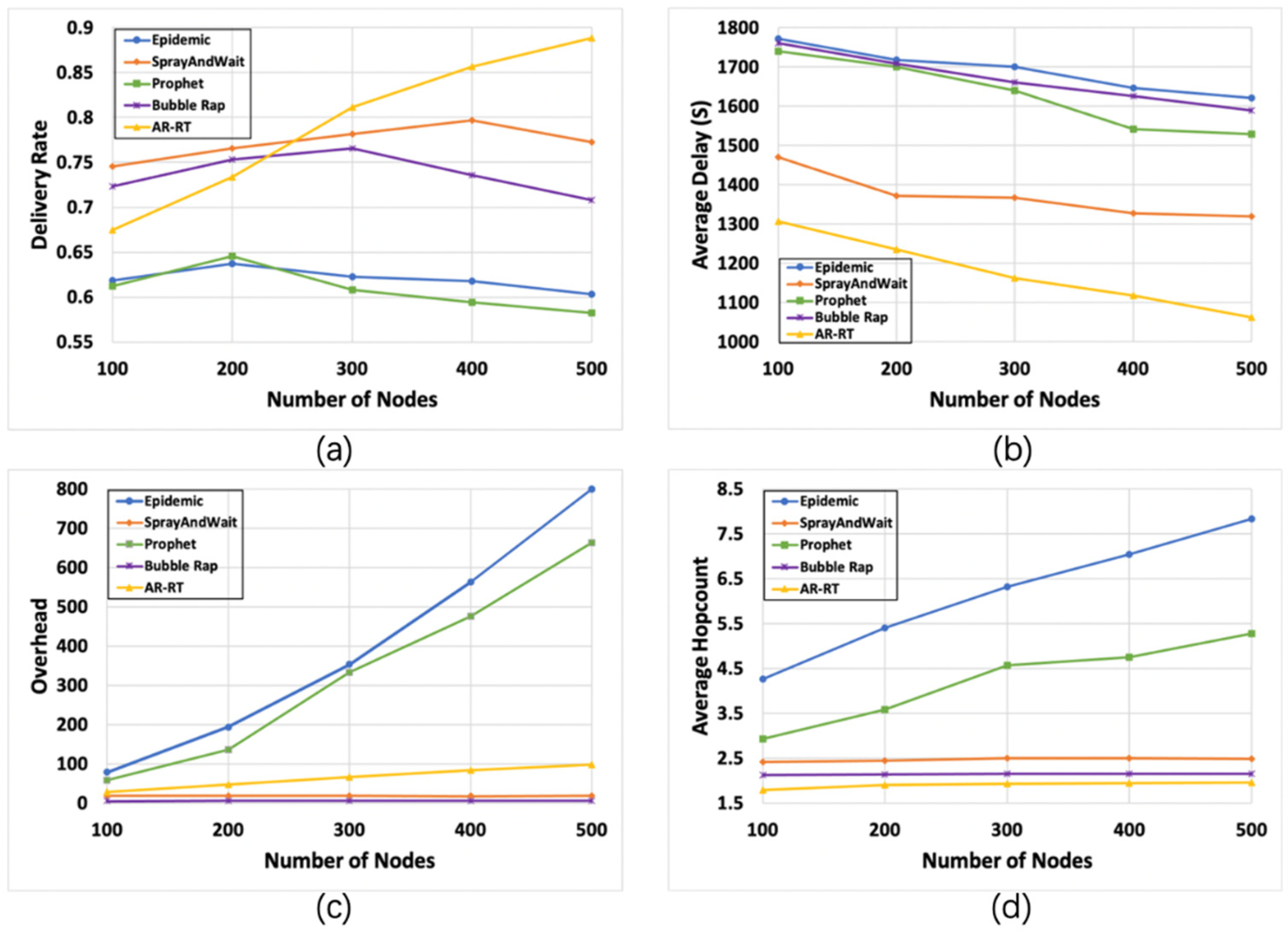
6.2.1. Impact of The Number of Nodes
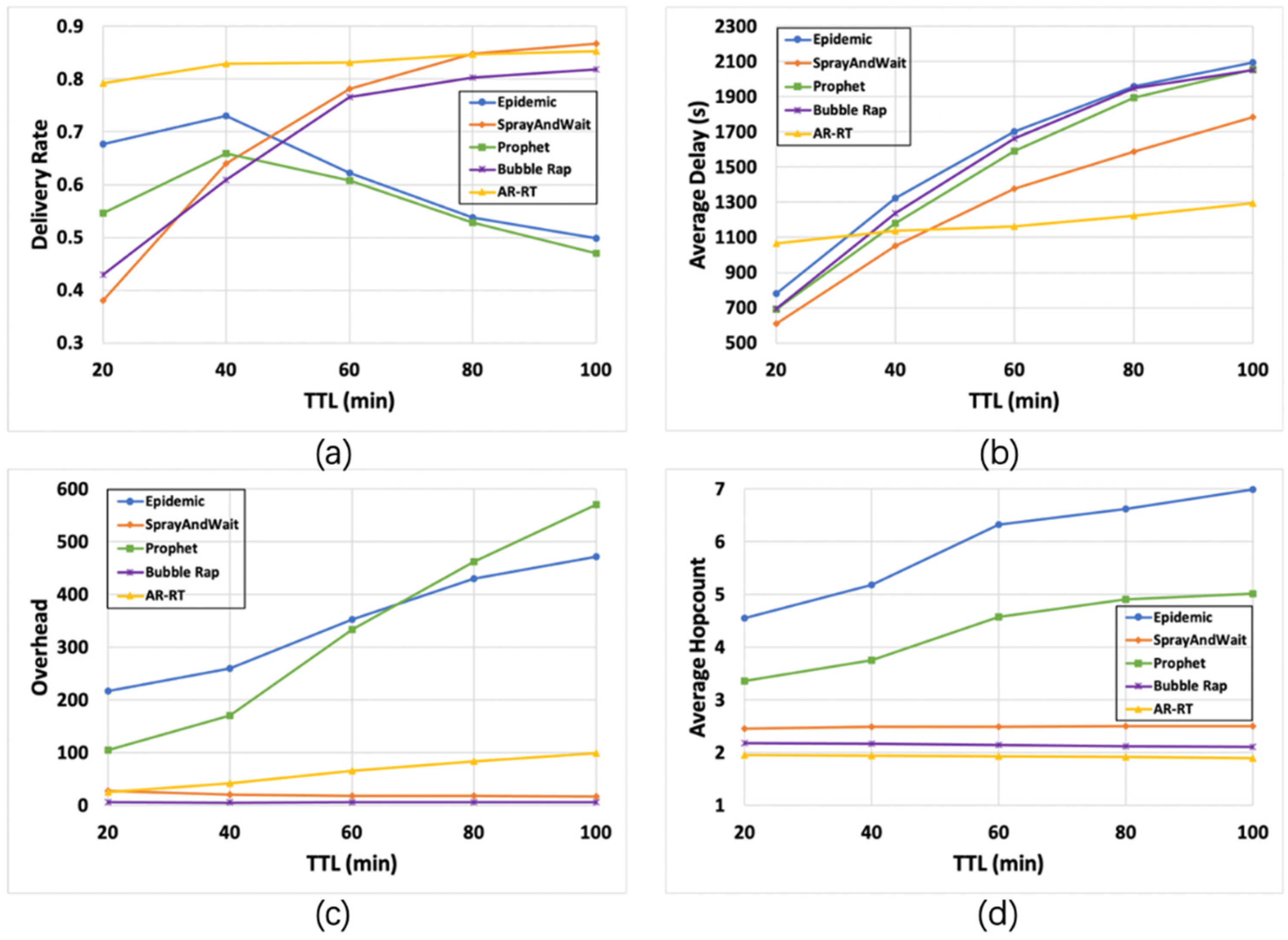
6.2.2. Impact of TTL
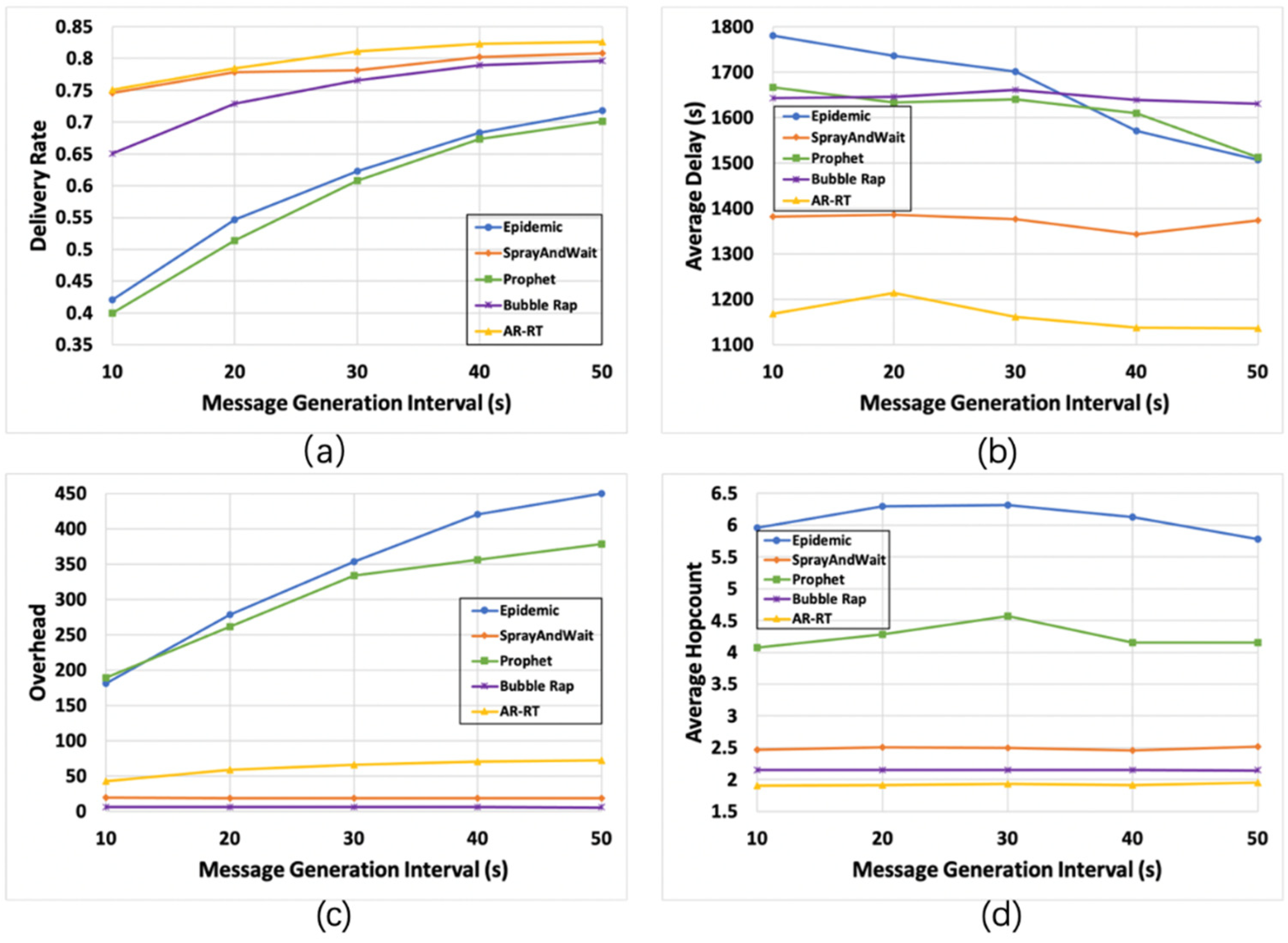
6.2.3. Impact of Message Generation Interval
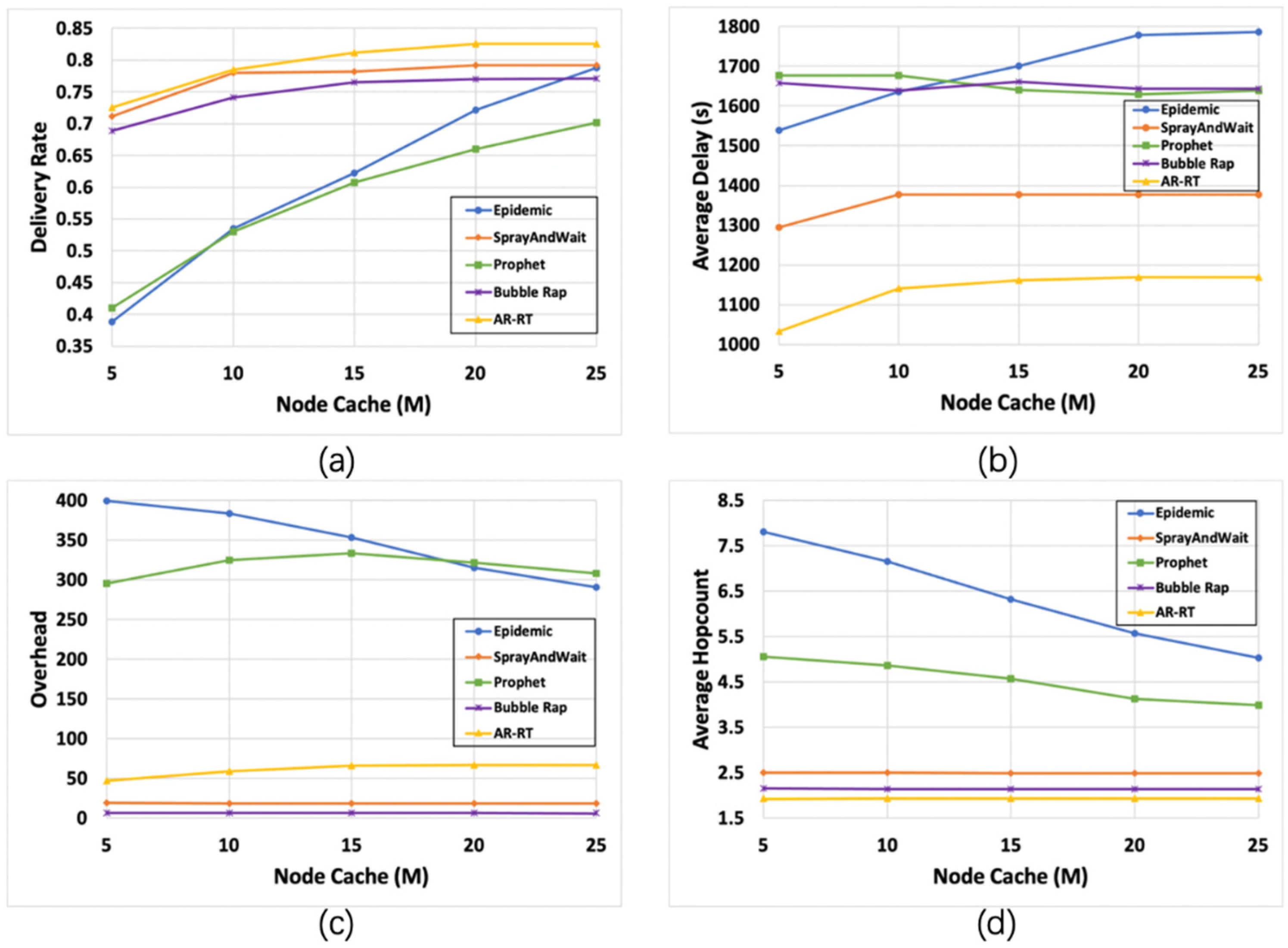
6.2.4. Impact of Buffer Size
7. Summary
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Caini, C.; Cruickshank, H.; Farrell, S.; Marchese, M. Delay- and Disruption-Tolerant Networking (DTN): An alternative solution for future satellite networking applications. Proc. IEEE 2011, 99, 1980–1997. [Google Scholar] [CrossRef]
- Baek, E.C.; Porter, M.A.; Parkinson, C. Social Network analysis for social neuroscientists. Soc. Cogn. Affect. Neurosci. 2021, 16, 883–901. [Google Scholar] [CrossRef] [PubMed]
- Rehman, G.U.; Ghani, A.; Muhammad, S.; Singh, M.; Singh, D. Selfishness in vehicular delay-tolerant networks: A review. Sensors 2020, 20, 3000. [Google Scholar] [CrossRef] [PubMed]
- Ye, S.; Xu, L.; Li, X. Vehicle-mounted self-organizing network routing algorithm based on deep reinforcement learning. Wirel. Commun. Mob. Comput. 2021, 9, 1–9. [Google Scholar] [CrossRef]
- Wang, H.; Wang, S.; Bu, R.; Zhang, E. A novel cross-layer routing protocol based on network coding for underwater sensor networks. Sensors 2017, 17, 1821. [Google Scholar] [CrossRef] [Green Version]
- Fall, K. A delay-tolerant network architecture for challenged internets. In Proceedings of the 2003 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, Karlsruhe, Germany, 25–29 August 2003; pp. 27–34. [Google Scholar]
- Tuan, L. Multi-hop routing under short contact in delay tolerant networks. Comput. Commun. 2021, 165, 1–8. [Google Scholar]
- Qi, Y.W.; Yang, L.; Pan, C.S.; Li, H.R. CGR-QV: A virtual topology DTN routing algorithm based on queue scheduling. China Commun. 2020, 17, 113–123. [Google Scholar] [CrossRef]
- Sakai, K.; Sun, M.T.; Ku, W.S.; Wu, J.; Alanazi, F.S. Performance and security analyses of onion-based anonymous routing for delay tolerant networks. IEEE Trans. Mob. Comput. 2017, 16, 3473–3487. [Google Scholar] [CrossRef]
- Roy, S.; Bose, T.; Acharya, S. DasBit, social-based energy-aware multicasting in delay tolerant networks. J. Netw. Comput. Appl. 2017, 87, 169–184. [Google Scholar] [CrossRef]
- Yuan, P.; Song, M. MONICA: One simulator for mobile opportunistic networks. In Proceedings of the International Conference on Mobile Multimedia Communications, Qingdao, China, 21–22 June 2018. [Google Scholar]
- Shah, R.C.; Roy, S.; Jain, S.; Brunette, W. Data MULEs: Modeling and analysis of a three-tier architecture for sparse sensor networks. Ad Hoc Netw. 2003, 1, 215–233. [Google Scholar] [CrossRef]
- Vahdat, A.; Becker, D. Epidemic Routing for Partially Connected Ad Hoc Networks; Technical Report CS-200006; Duke University: Durham, NC, USA, 2000. [Google Scholar]
- Spyropoulos, T.; Psounis, K.; Raghavendra, C.S. Spray and wait: An efficient routing scheme for intermittently connected mobile networks. In Proceedings of the 2005 ACM SIGCOMM Workshop on Delay-Tolerant Networking, Philadelphia, PA, USA, 26 August 2005; pp. 252–259. [Google Scholar]
- Zhang, S.; Xue, J.; Hu, C.; Wang, Y. Binary spray and wait routing based on the remaining life time of message in wireless sensor networks. Sens. Lett. 2013, 11, 1586–1590. [Google Scholar]
- Kuronuma, Y.; Suzuki, H.; Koyama, A. An adaptive DTN routing protocol considering replication state. In Proceedings of the International Conference on Advanced Information Networking and Applications Workshops, Taipei, Taiwan, 27–29 March 2017; pp. 421–426. [Google Scholar]
- Raverta, F.D.; Fraire, J.A.; Madoery, P.G.; Demasi, R.A.; Finochietto, J.M.; D’Argenio, P.R. Routing in delay-tolerant networks under uncertain contact plans. Ad Hoc Netw. 2021, 123, 102663. [Google Scholar] [CrossRef]
- Lindgren, A.; Doria, A.; Schelén, O. Probabilistic routing in intermittently connected networks. Acm Sigmobile Mob. Comput. Commun. Rev. 2004, 7, 19–20. [Google Scholar] [CrossRef]
- Mao, Y.; Zhou, C.; Ling, Y.; Lloret, J. An optimized probabilistic Delay Tolerant Network (DTN) routing protocol based on scheduling mechanism for Internet of Things (IoT). Sensors 2019, 19, 243. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Derakhshanfard, N.; Sabaei, M.; Rahmani, A.M. Sharing spray and wait routing algorithm in opportunistic networks. Wirel. Netw. 2016, 22, 2403–2414. [Google Scholar] [CrossRef]
- Spaho, E.; Dhoska, K.; Barolli, L.; Kolici, V.; Takizawa, M. Enhancement of binary spray and wait routing protocol for improving delivery probability and latency in a delay tolerant network. In International Conference on Broadband and Wireless Computing, Communication and Applications; Springer: Berlin/Heidelberg, Germany, 2019; pp. 105–113. [Google Scholar]
- Yang, H. Geography-Based Adaptive Spray Routing Algorithm in Delay Tolerant Network. Master’s Thesis, Central China Normal University, Wuhan, China, 2018. [Google Scholar]
- Hui, P.; Crowcroft, J.; Yoneki, E. Bubble rap: Social-based forwarding in delay-tolerant networks. IEEE Trans. Mob. Comput. 2010, 10, 1576–1589. [Google Scholar] [CrossRef] [Green Version]
- Jain, S.; Verma, A. Bubble rap incentive scheme for prevention of node selfish- ness in delay-tolerant networks. In Smart Innovations in Communication and Computational Sciences; Springer: Berlin/Heidelberg, Germany, 2019; pp. 289–303. [Google Scholar]
- Bulut, E.; Szymanski, B. Exploiting friendship relations for efficient routing in mobile social networks. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 2254–2265. [Google Scholar] [CrossRef]
- Yu, G.; Chen, Z.; Wu, J.; Wu, J. Predicted encounter probability based on dynamic programming proposed probability algorithm in opportunistic social network. Comput. Netw. 2020, 181, 107456. [Google Scholar] [CrossRef]
- Li, F.; Jiang, H.; Li, H.; Cheng, Y.; Wang, Y. SEBAR: Social-energy-based routing for mobile social delay-tolerant networks. IEEE Trans. Veh. Technol. 2017, 66, 7195–7206. [Google Scholar] [CrossRef]
- Zhou, Y.J.; Ma, C.G.; Miao, J.F.; Qi, F. Community level based opportunity network mobility model. Inf. Netw. Secur. 2014, 8, 45–49. [Google Scholar]
- Boc, M.; Fladenmuller, A.; de Amorim, M.D.; Galluccio, L.; Palazzo, S. Price: Hybrid geographic and co-based forwarding in delay-tolerant networks. Comput. Netw. 2011, 55, 2352–2360. [Google Scholar] [CrossRef]
- Keranen, A.; Karkkainen, T.; Ott, J. Simulating mobility and DTN with the ONE. J. Comput. Appl. 2010, 5, 92–105. [Google Scholar]

| Notation | Explanation |
|---|---|
| Memory cycle | |
| Relationship threshold | |
| Set of nodes in the network | |
| Number of times and meet in a memory cycle | |
| Relation Tree of node | |
| Number of copies of carried by node | |
| Current cache occupancy of node | |
| Optimal cache occupancy of node | |
| The actual number of copies | |
| The initial number of copies | |
| The lifetime of the newly generated message copy | |
| The original lifetime of the message copy |
| Parameter | Default Value | Variation Range |
|---|---|---|
| Scenario Size (m2) | 4500 × 3400 | - |
| Simulation Time (h) | 10 | - |
| Message Generation Interval (s) | 30 | 10–50 |
| Message Size (KB) | 1250 | 1000–1500 |
| Buffer Size (MB) | 15 | 5–25 |
| TTL (min) | 60 | 20–100 |
| Number of Nodes | 300 | 100–500 |
| 8 | - | |
| 0.6 | - | |
| 2 | - | |
| 3 | - | |
| (min) | 30 | - |
| Group Number | Parameter | Value |
|---|---|---|
| Group 1 (Pedestrians) | movement speed (m/s) | 0.5–1.5 |
| communication rate (Kbps) | 250 | |
| communication range (m) | 30 | |
| Group 2 (Bus) | movement speed (m/s) | 2.7–13.9 |
| communication rate (Kbps) | 250 | |
| communication range (m) | 30 | |
| Group 3 (Taxi) | movement speed (m/s) | 3–12 |
| communication rate (Kbps) | 250 | |
| communication range (m) | 30 | |
| Group 4 (Tram) | movement speed (m/s) | 7–10 |
| communication rate (Mbps) | 10 | |
| communication range (m) | 150 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, D.; Cui, H.; Welsch, R.E. An Adaptive Routing Algorithm Based on Relation Tree in DTN. Sensors 2021, 21, 7847. https://doi.org/10.3390/s21237847
Chen D, Cui H, Welsch RE. An Adaptive Routing Algorithm Based on Relation Tree in DTN. Sensors. 2021; 21(23):7847. https://doi.org/10.3390/s21237847
Chicago/Turabian StyleChen, Diyue, Hongyan Cui, and Roy E. Welsch. 2021. "An Adaptive Routing Algorithm Based on Relation Tree in DTN" Sensors 21, no. 23: 7847. https://doi.org/10.3390/s21237847
APA StyleChen, D., Cui, H., & Welsch, R. E. (2021). An Adaptive Routing Algorithm Based on Relation Tree in DTN. Sensors, 21(23), 7847. https://doi.org/10.3390/s21237847





