Deep Learning for the Industrial Internet of Things (IIoT): A Comprehensive Survey of Techniques, Implementation Frameworks, Potential Applications, and Future Directions
Abstract
:1. Introduction
1.1. Existing Surveys on DL for IoT and IIoT Applications
1.2. Limitations of Existing Surveys
1.3. Major Contributions
- Discussing the great potential of DL schemes for IIoT.
- Providing a detailed reference architecture of the IIoT with key enabling technologies.
- Presenting a comprehensive survey on the working principle of well-known DL algorithms, their implementation frameworks, and the relevant hardware platforms.
- Covering the real-world applications of DL techniques in IIoT systems.
- Suggesting some potential future research directions.
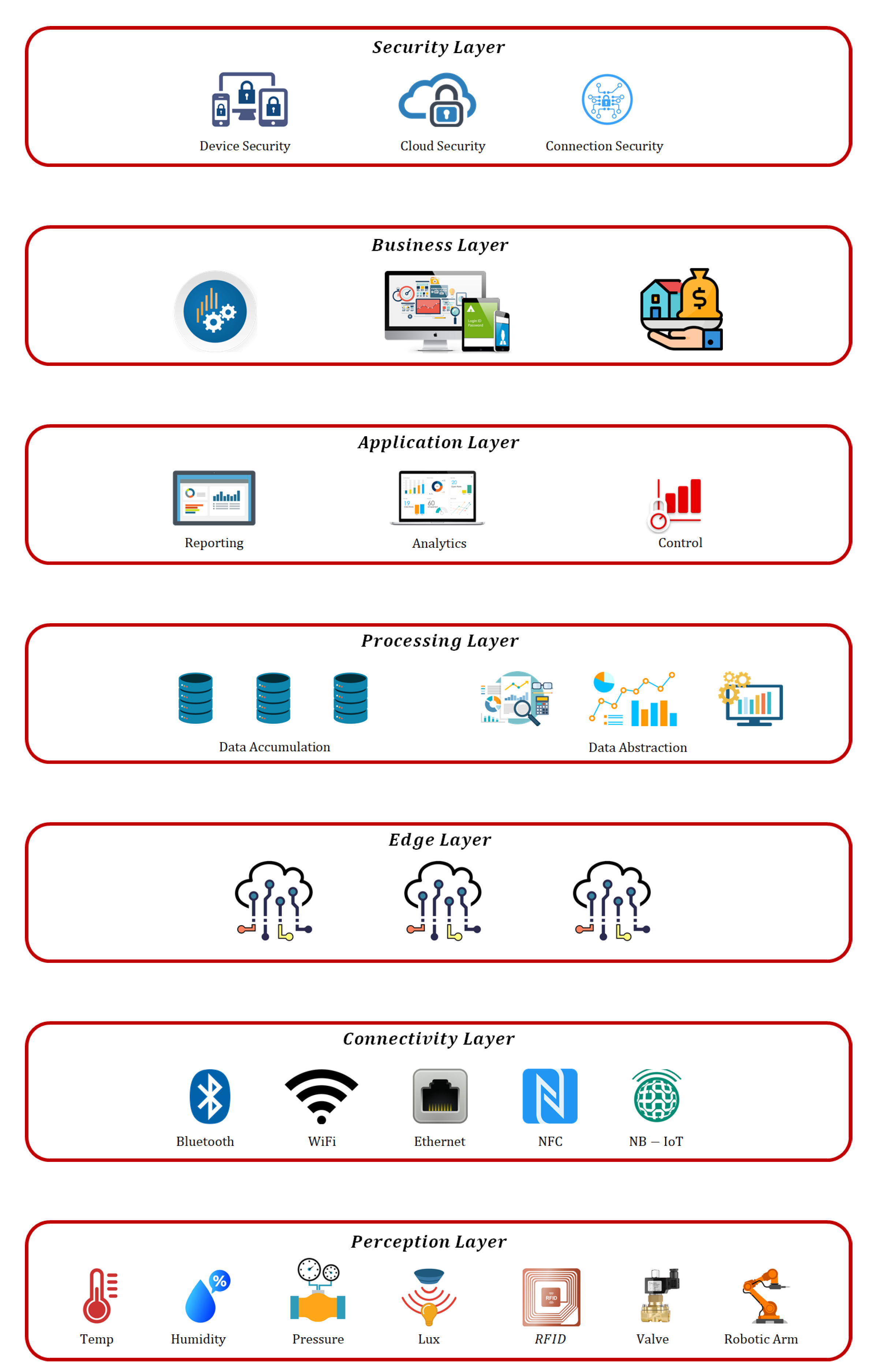
2. Reference Architecture of the Industrial Internet of Things (IIoT)
2.1. Perception Layer
- Sensors: These are small devices that can detect changes in the surrounding environment and extract useful information from the data acquired. Usually, sensors are considered to be resource-constrained devices that have little processing and computational power combined with limited memory resources. However, modern sensors have great capacity to gather environmental signals with a higher level of accuracy. The most commonly used sensors across multiple industries are used to measure temperature, humidity, air pressure, weight, acceleration, position, and many others.
- Actuators: These are usually electromechanical devices that convert electrical signals into physical actions. In an industrial environment, linear and rotary are the two general types of actuators most often used. Linear actuators transform electrical signals into linear motions, which are useful in position adjustment applications. Meanwhile, rotary actuators transform electrical energy into rotational energy. These are usually used for the position control of devices such as conveyor belts.
2.2. Connectivity Layer
- WiFi: This is the most versatile and commonly used scheme across communication technologies. WiFi modems are very suitable for both personal and official uses, delivering smooth communications among LAN and WAN.
- Ethernet: This is an older technology used for connecting devices in a LAN or WAN, which enables them to communicate with each other via a specific communication protocol. Ethernet also enables network communication between different network cables, such as copper to optical fiber and vice versa.
- Bluetooth: This wireless protocol is widely used for information exchange over short distances by creating personal area networks.
- NFC: Near Field Communications (NFC) is a wireless technology that enables secure communication between smart devices at short distances. The communication range of NFC is usually considered to be about 10 cm.
- LPWAN: Low-Power Wide-Area Network (LPWAN) describes a class of radio technologies used for long-distance communication. The top LPWAN technologies are LoRa, Sigfox, and Nwave. As compared to other wireless technologies such as Bluetooth and Wi-Fi, LPWANs are usually used to send smaller amounts of information over longer distances.
- ZigBee: This is a product from the Zigbee alliance that is designed especially for sensor networks on the IEEE 802.15.4 standard. The mostly used data communication protocols for this communication standard are ISA-100.11.a and WirelessHART. These protocols define Media Access Control (MAC) and physical layers to handle several devices at low-data rates.
- LTE-M: Long Term Evolution for Machine is a leading LPWA network technology for IoT applications. It is used for interconnecting objects such as IoT sensors and actuators, or other industrial devices via radio modules.
- NB-IoT: This is a standards-based low-power wide-area (LPWA) technology that enables a wide variety of smart devices and services. NB-IoT improves the power consumption, spectrum efficiency, and system capacity of smart devices.
2.3. Edge Layer
2.4. Processing Layer
- Data Accumulation: Real-time information is acquired through an API and further stored to meet the demands of non-real-time applications. This stage serves as a transient link between query-based data consumption and event-based data generation. This stage also determines the relevance of the data acquired to the stated business requirements.
- Data Abstraction: Once data accumulation and preparation have been completed, consumer applications may use it to produce insights. Several phases are involved in the end-to-end process, including integrating data from multiple sources, reconciliation of formats, and data aggregation in a single place.
- Transmission Control Protocol (TCP): It offers host-to-host communication, breaking large sets of data into individual packets and resending and reassembling packets as needed.
- User Datagram Protocol (UDP): Process-to-process communication is enabled using this protocol, which operates on top of IP. Over TCP, UDP offers faster data transfer speeds, making it the protocol of choice for mission-critical applications.
- Internet Protocol (IP): Many IoT protocols use IPv4, while more recent executions use IPv6. This recent update to IP routes traffic across the Internet and identifies and locates devices on the network.
2.5. Application Layer
- Advanced Message Queuing Protocol (AMQP): It allows messaging middleware to communicate with one another. It enables a variety of systems and applications to communicate with one another, resulting in standardized communications on a large scale.
- Constrained Application Protocol (CoAP): A constrained-bandwidth and constrained-network protocol designed for machine-to-machine communication between devices with limited capacity. CoAP is a document-transfer protocol that operates on the User Datagram Protocol (UDP).
- Data Distribution Service (DDS): A flexible peer-to-peer communication protocol capable of running small devices as well as linking high-performance networks. DDS simplifies deployment, boosts dependability, and minimizes complexity.
- Message Queue Telemetry Transport (MQTT): A messaging protocol developed for low-bandwidth communications to faraway places and mostly used for lightweight machine-to-machine communication. MQTT employs a publisher-subscriber pattern and is suited for tiny devices with limited bandwidth and battery life.
2.6. Business Layer
2.7. Security Layer
- Device Security: This is the beginning point of security in the IIoT framework. Many manufactures and companies integrate both software and hardware-based security schemes in IoT devices.
- Cloud Security: Cloud storage is replacing the traditional data storage servers in modern IoT infrastructures, so in turn new security mechanisms are also adopted to secure that cloud. Cloud security includes encryption schemes and intrusion detection systems, etc., as means of preventing cyberattacks and other malicious activities.
- Connection Security: In an IIoT network, the data must be encrypted before transmission via any communication channel. In this context, different messaging protocols, such as MQTT, DDS, and AMQP, may be implemented to secure valuable information. In modern trends, the use of TSL cryptographic protocol is recommended for communication in industrial applications.
3. Deep Learning for the IIoT
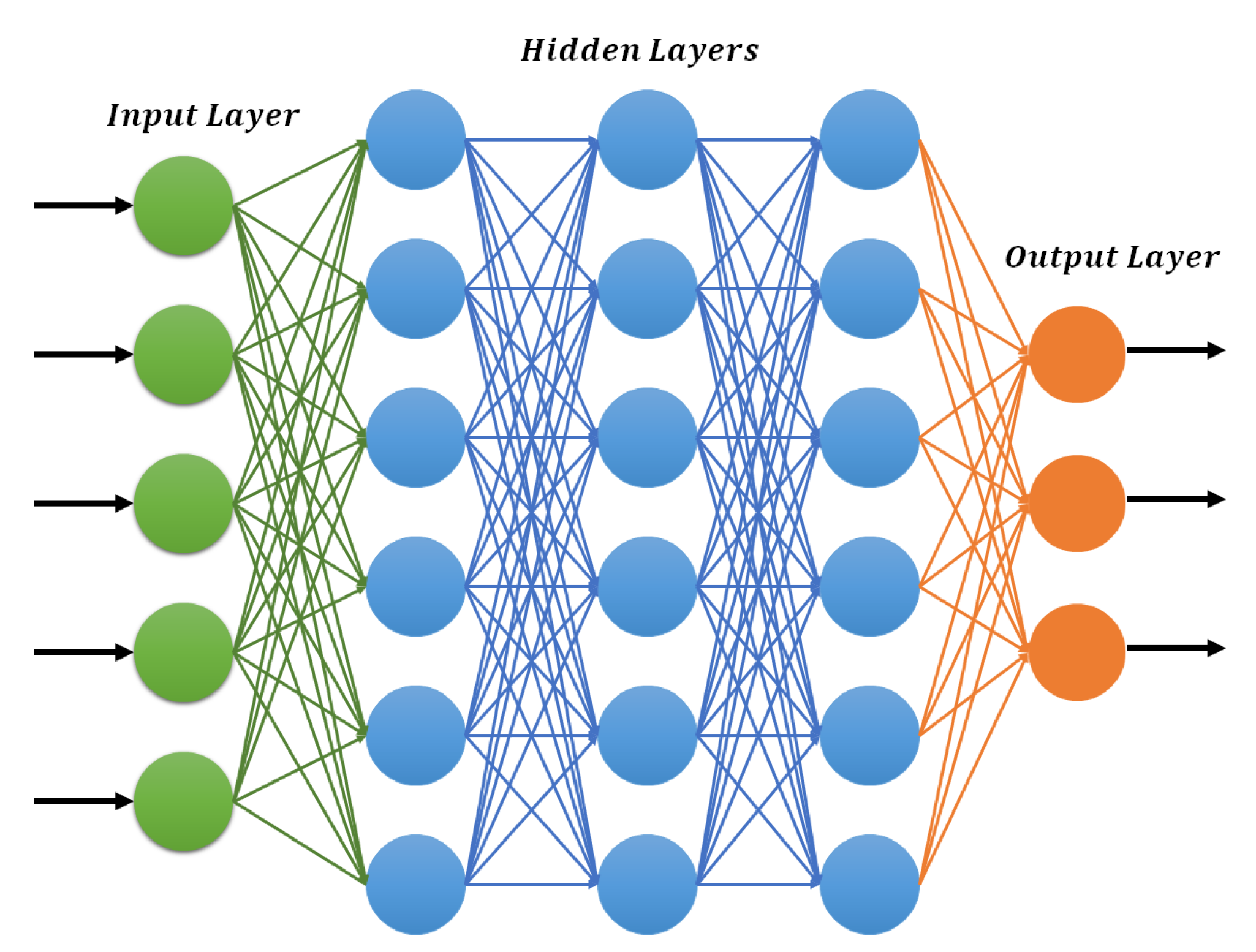
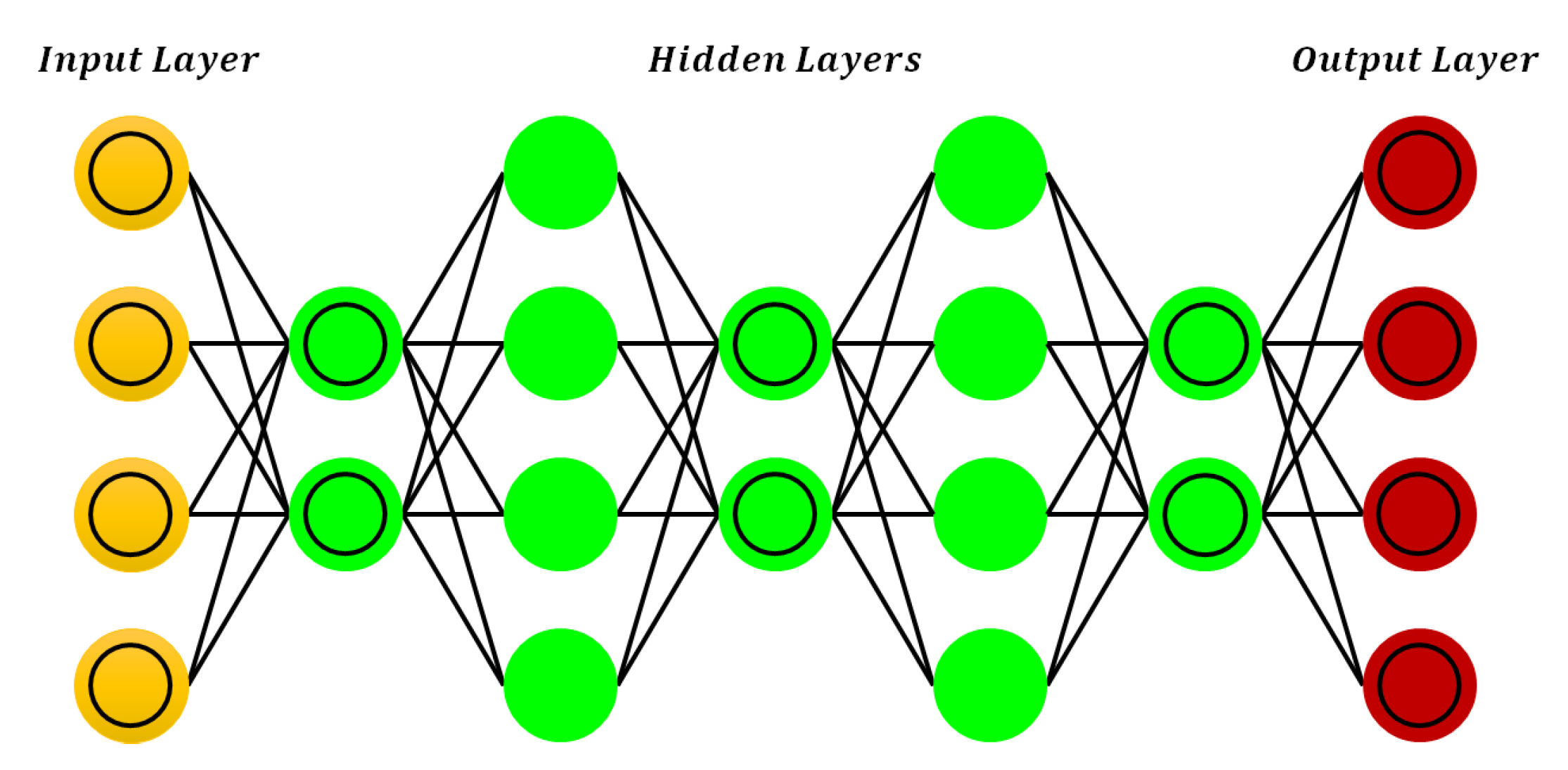
3.1. Deep Feedforward Neural Networks
3.2. Restricted Boltzmann Machines (RBM)
3.3. Deep Belief Networks (DBN)
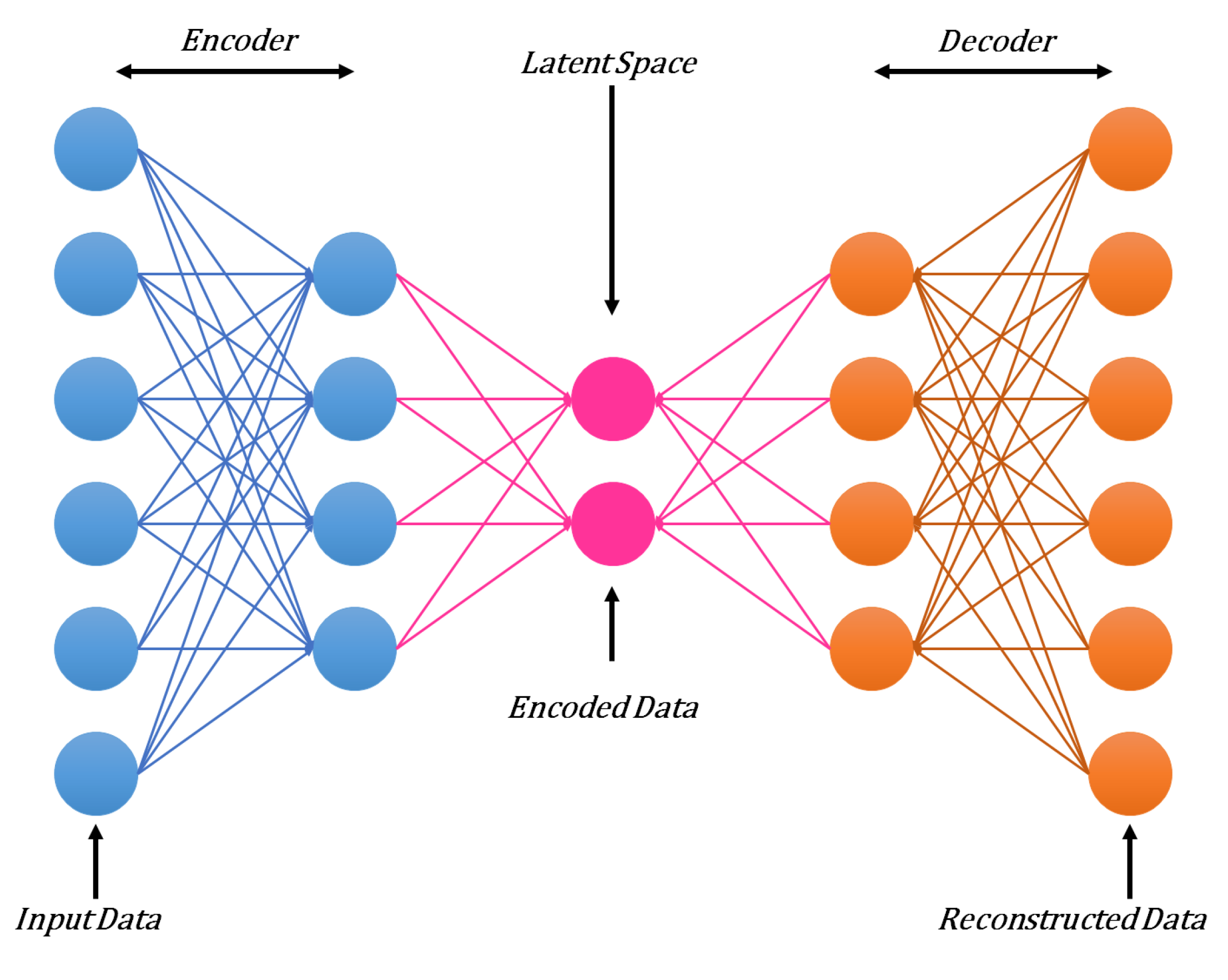
3.4. Autoencoders (AE)
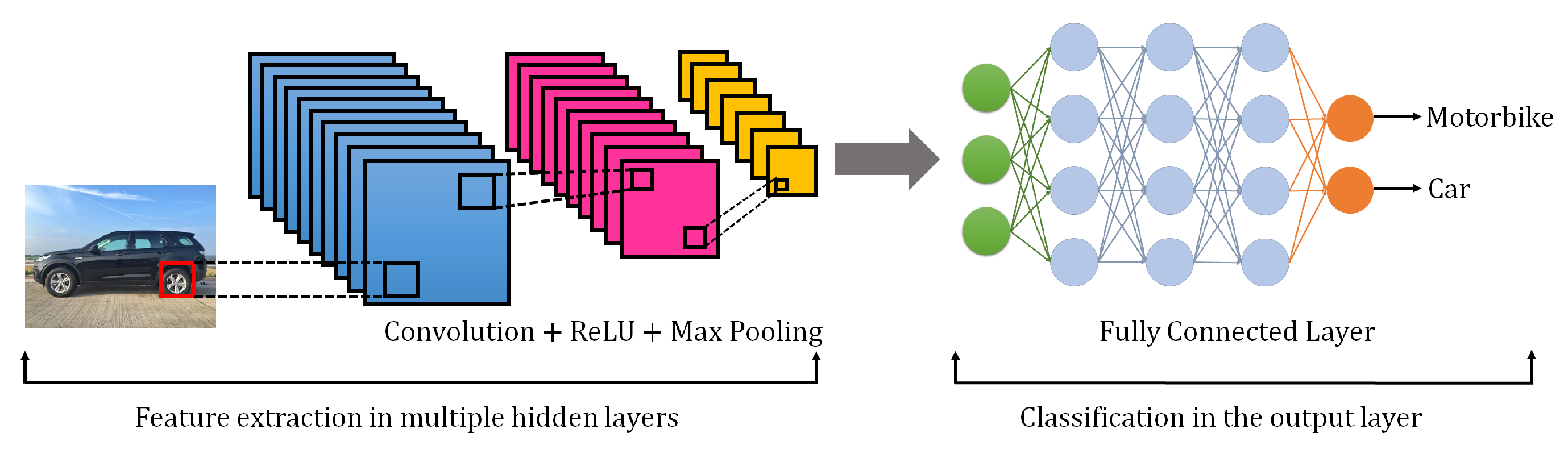
3.5. Convolutional Neural Network (CNN)
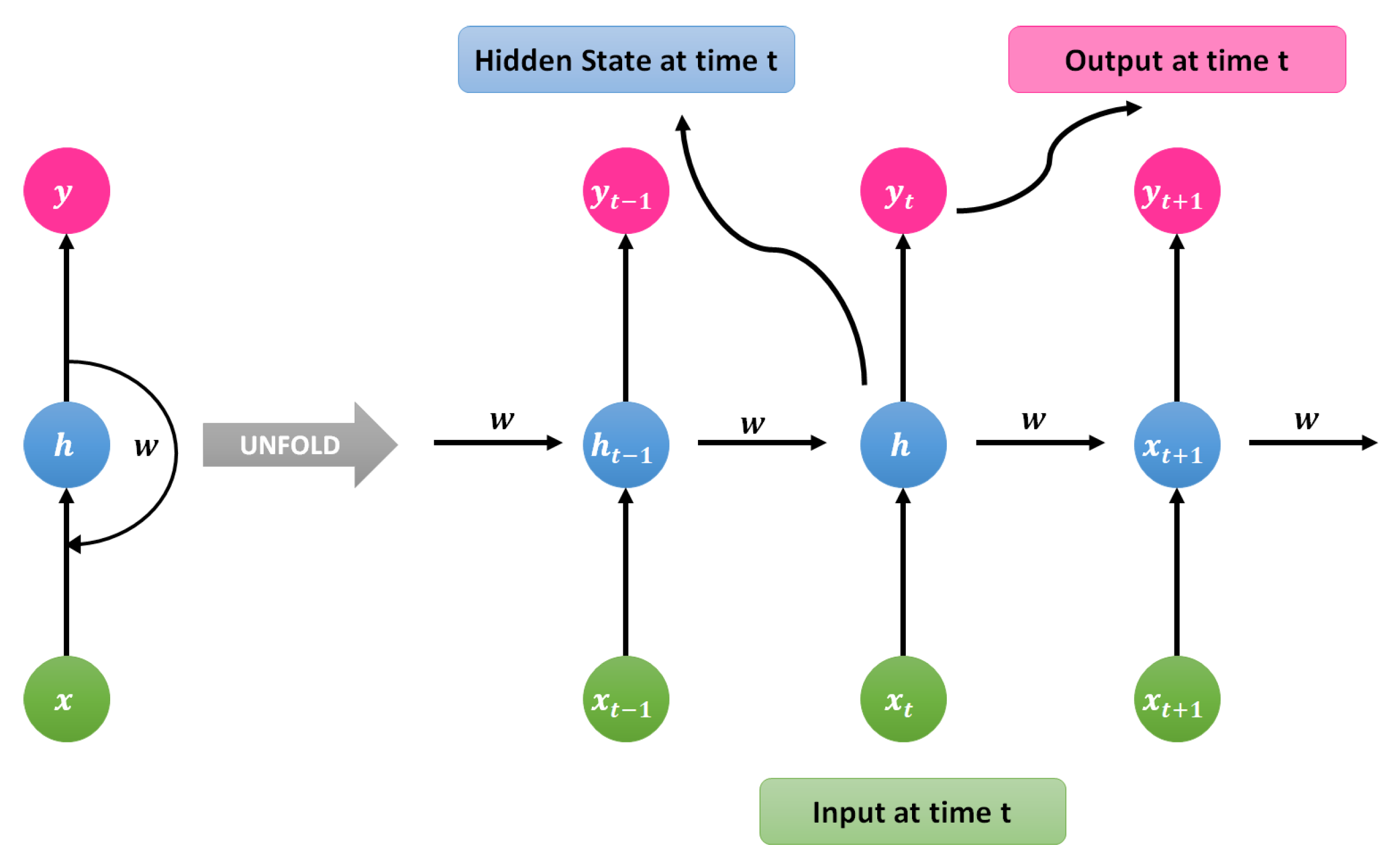
3.6. Recurrent Neural Network (RNN)
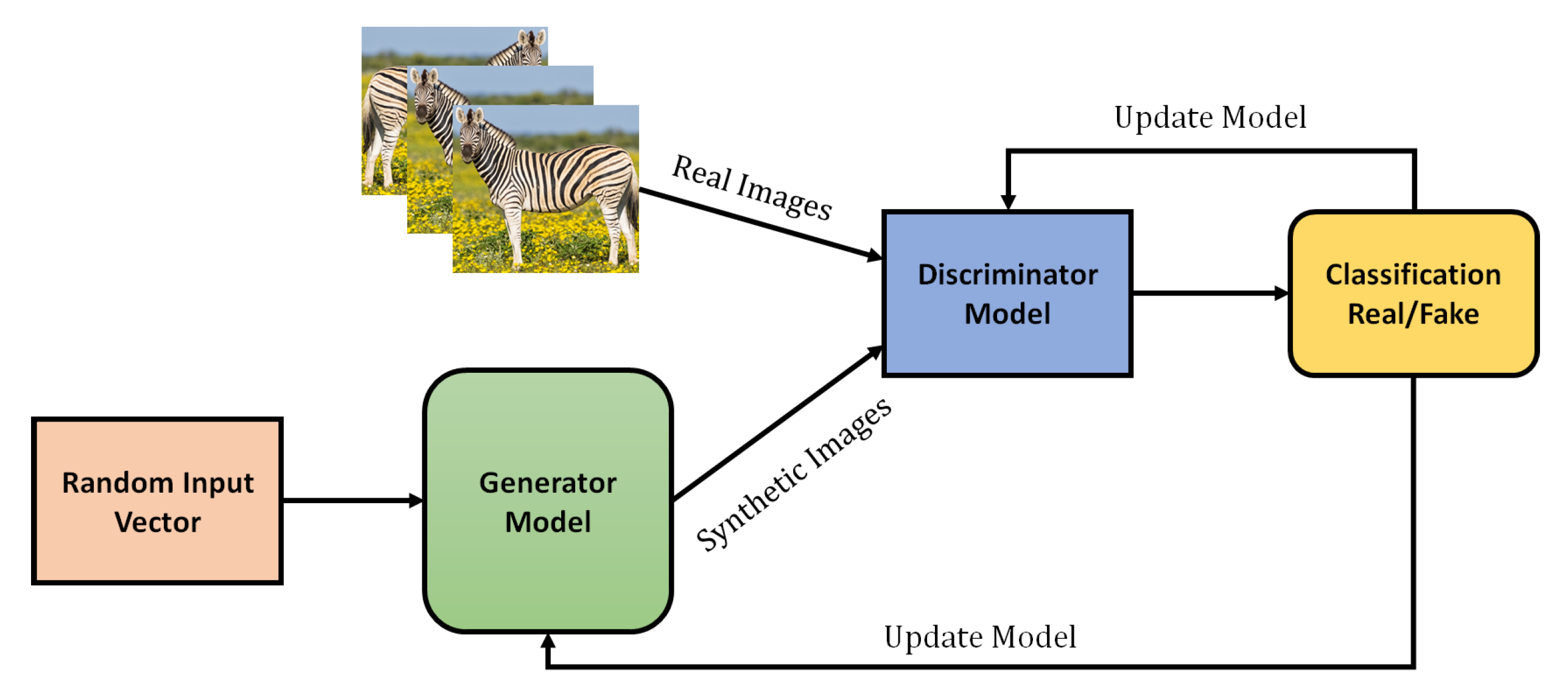
3.7. Generative Adversarial Networks (GAN)
4. Deep Learning Frameworks
4.1. TensorFlow
4.2. Microsoft CNTK
4.3. Keras
- It follows the best practices by offering simple, consistent APIs to reduce cognitive load.
- Neural layers, optimizers, cost functions, activation functions, initialization schemes, and regularization methods are all separate modules that can be combined to construct new models.
- The addition of new modules is easy and existing modules provide sufficient examples that allow for the reduction of expressiveness.
- It works with Python models that are easy to debug as well as compact and extensible.
4.4. Caffe
4.5. Caffe2
4.6. MXNet
4.7. Torch
4.8. PyTorch
4.9. Theano
4.10. Chainer
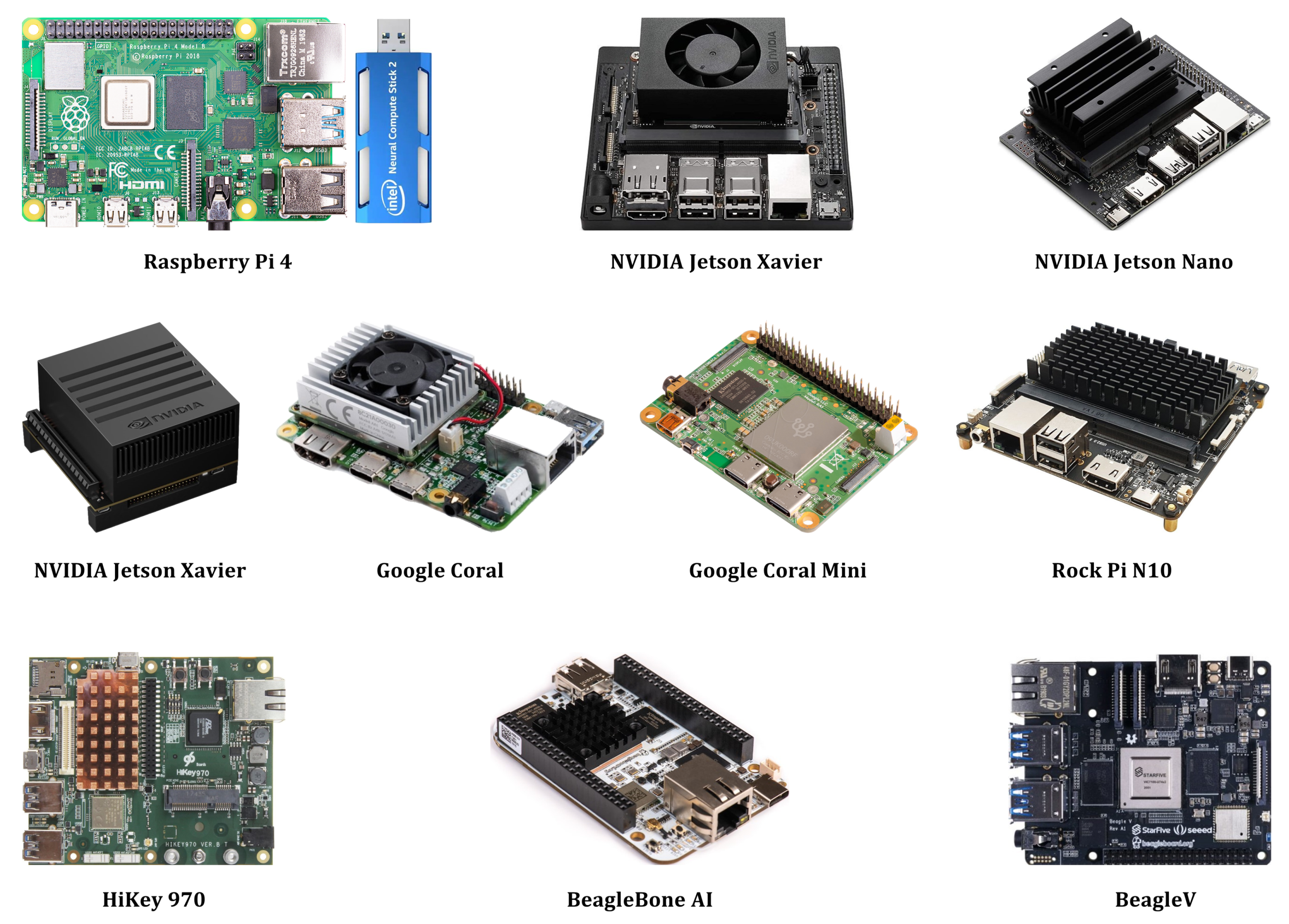
5. Hardware Platforms for the Implementation of Deep Learning Algorithms
5.1. Raspberry Pi 4
5.2. NVIDIA Jetson XavierTM
5.3. NVIDIA Jetson NanoTM
5.4. NVIDIA Jetson AGX XavierTM
5.5. Google Coral
5.6. Google Coral Dev Board Mini
5.7. Rock Pi N10
5.8. HiKey 970
5.9. BeagleBone AI
5.10. BeagleV
6. Applications of Deep Learning in the IIoT
6.1. Agriculture
6.1.1. Weed Detection
6.1.2. Smart Greenhouse
6.1.3. Hydroponics
6.1.4. Soil Nutrient Monitoring
6.1.5. Smart Irrigation
6.1.6. Fruit and Vegetable Plucking
6.1.7. Early Detection of Plant Diseases
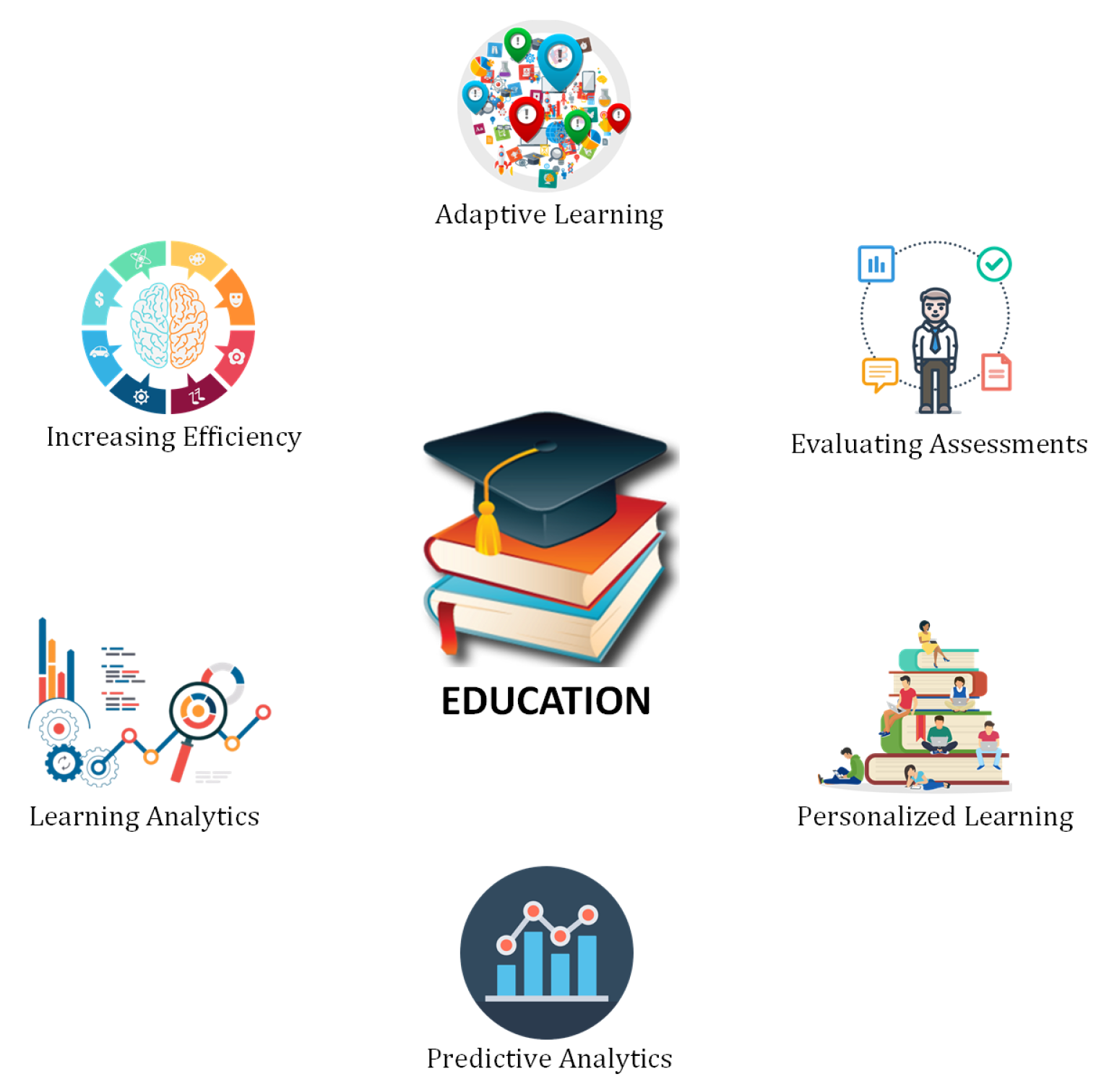
6.2. Education
6.2.1. Adaptive Learning
6.2.2. Increasing Efficiency
6.2.3. Learning Analytics
6.2.4. Predictive Analytics
6.2.5. Personalized Learning
6.2.6. Evaluating Assessments
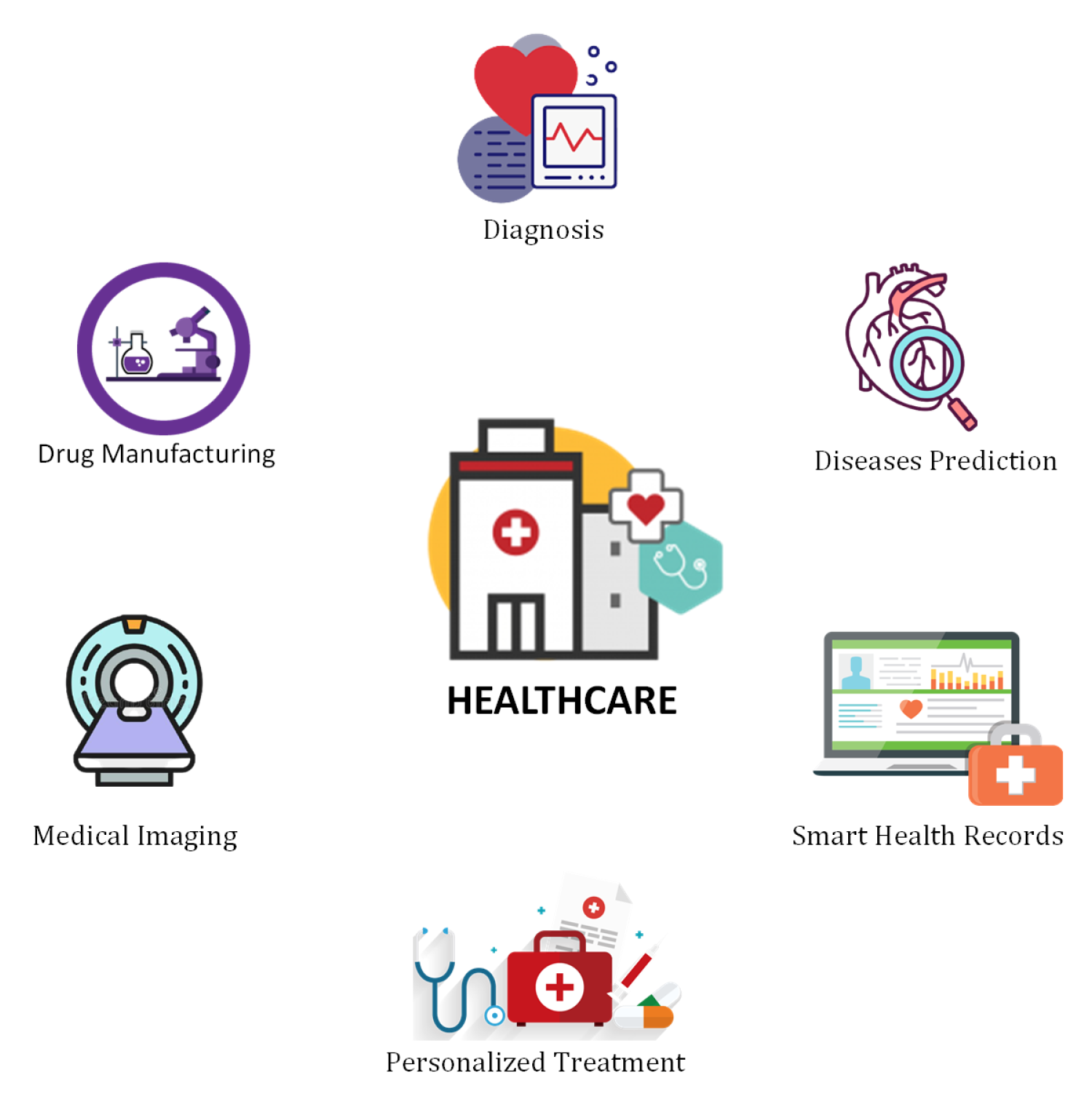
6.3. Healthcare
6.3.1. Diseases Identification and Diagnosis
6.3.2. Drug Discovery and Manufacturing
6.3.3. Medical Imaging
6.3.4. Personalized Medicine/Treatment
6.3.5. Smart Health Records
6.3.6. Diseases Prediction
6.4. Intelligent Transportation Systems
6.4.1. Traffic Characteristics Prediction
6.4.2. Traffic Incidents Inference
6.4.3. Vehicle Detection
6.4.4. Traffic Signal Timing
6.4.5. Visual Recognition Tasks
6.5. Manufacturing Industry
6.5.1. Maintenance
6.5.2. Predictive Analytics
6.5.3. Product Development
6.5.4. Quality Assurance
6.5.5. Robotics
6.5.6. Supply Chain Management
6.5.7. Logistics
6.6. Aviation Industry
6.6.1. Revenue Management
6.6.2. Air Safety and Airplane Maintenance
6.6.3. Feedback Analysis
6.6.4. Messaging Automation
6.6.5. Crew Management
6.6.6. Fuel Efficiency Optimization
6.6.7. In-Flight Food Service Management
6.7. Defense
6.7.1. Warfare Platforms
6.7.2. Cybersecurity
6.7.3. Logistics and Transportation
6.7.4. Target Recognition
6.7.5. Battlefield Healthcare
6.7.6. Combat Simulation and Training
6.8. Sports Industry
6.8.1. Sports Coaching
6.8.2. Analyzing Player Behavior
6.8.3. Refereeing
6.8.4. Health and Fitness Improvement
6.8.5. Streaming and Broadcasting
7. Potential Challenges and Future Research Directions
7.1. Key Challenges
7.1.1. Complexity
7.1.2. Algorithm Selection
7.1.3. Data Selection
7.1.4. Data Preprocessing
7.1.5. Data Labeling
7.2. Future Directions
7.2.1. DL-Enabled Edge/Cloud Computing
7.2.2. Distributed Deep Learning
7.2.3. Low Latency and Improved Reliability
7.2.4. Intelligent Sensing and Decision-Making
7.2.5. Lightweight Learning Frameworks
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Sisinni, E.; Saifullah, A.; Han, S.; Jennehag, U.; Gidlund, M. Industrial internet of things: Challenges, opportunities, and directions. IEEE Trans. Ind. Inform. 2018, 14, 4724–4734. [Google Scholar] [CrossRef]
- Saeed, N.; Alouini, M.S.; Al-Naffouri, T.Y. Toward the internet of underground things: A systematic survey. IEEE Commun. Surv. Tutor. 2019, 21, 3443–3466. [Google Scholar] [CrossRef] [Green Version]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of things: A survey on enabling technologies, protocols, and applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Liang, F.; Yu, W.; Liu, X.; Griffith, D.; Golmie, N. Toward edge-based deep learning in industrial Internet of Things. IEEE Internet Things J. 2020, 7, 4329–4341. [Google Scholar] [CrossRef]
- Statista. Industrial Internet of Things Market Size Worldwide from 2017 to 2025. 2020. Available online: https://www.statista.com/statistics/611004/global-industrial-internet-of-things-market-size/ (accessed on 1 August 2021).
- Khalil, R.A.; Saeed, N.; Masood, M.; Fard, Y.M.; Alouini, M.S.; Al-Naffouri, T.Y. Deep Learning in the Industrial Internet of Things: Potentials, Challenges, and Emerging Applications. IEEE Internet Things J. 2021, 8, 11016–11040. [Google Scholar] [CrossRef]
- Zhu, S.; Ota, K.; Dong, M. Green AI for IIoT: Energy Efficient Intelligent Edge Computing for Industrial Internet of Things. IEEE Trans. Green Commun. Netw. 2021. [Google Scholar] [CrossRef]
- Ullah, F.; Naeem, H.; Jabbar, S.; Khalid, S.; Latif, M.A.; Al-Turjman, F.; Mostarda, L. Cyber security threats detection in internet of things using deep learning approach. IEEE Access 2019, 7, 124379–124389. [Google Scholar] [CrossRef]
- Zhang, Q.; Yang, L.T.; Chen, Z.; Li, P.; Bu, F. An adaptive dropout deep computation model for industrial IoT big data learning with crowdsourcing to cloud computing. IEEE Trans. Ind. Inform. 2018, 15, 2330–2337. [Google Scholar] [CrossRef]
- Mohammadi, M.; Al-Fuqaha, A.; Sorour, S.; Guizani, M. Deep learning for IoT big data and streaming analytics: A survey. IEEE Commun. Surv. Tutor. 2018, 20, 2923–2960. [Google Scholar] [CrossRef] [Green Version]
- Ma, X.; Yao, T.; Hu, M.; Dong, Y.; Liu, W.; Wang, F.; Liu, J. A survey on deep learning empowered IoT applications. IEEE Access 2019, 7, 181721–181732. [Google Scholar] [CrossRef]
- Boulila, W.; Sellami, M.; Driss, M.; Al-Sarem, M.; Safaei, M.; Ghaleb, F.A. RS-DCNN: A novel distributed convolutional-neural-networks based-approach for big remote-sensing image classification. Comput. Electron. Agric. 2021, 182, 106014. [Google Scholar] [CrossRef]
- Ambika, P. Machine learning and deep learning algorithms on the Industrial Internet of Things (IIoT). Adv. Comput. 2020, 117, 321–338. [Google Scholar]
- Saleem, T.J.; Chishti, M.A. Deep learning for the internet of things: Potential benefits and use-cases. Digit. Commun. Netw. 2020. [Google Scholar] [CrossRef]
- Deepan, P.; Sudha, L. Deep Learning Algorithm and Its Applications to IoT and Computer Vision. Artif. Intell. IOT Smart Converg. Eco-Friendly Topogr. 2021, 85, 223. [Google Scholar]
- Boyes, H.; Hallaq, B.; Cunningham, J.; Watson, T. The industrial internet of things (IIoT): An analysis framework. Comput. Ind. 2018, 101, 1–12. [Google Scholar] [CrossRef]
- Lin, S.W.; Miller, B.; Durand, J.; Joshi, R.; Didier, P.; Chigani, A.; Torenbeek, R.; Duggal, D.; Martin, R.; Bleakley, G.; et al. Industrial Internet Reference Architecture; Technical Reports; Industrial Internet Consortium (IIC): Boston, MA, USA, 2015. [Google Scholar]
- Cheng, C.F.; Chen, Y.C.; Lin, J.C.W. A Carrier-Based Sensor Deployment Algorithm for Perception Layer in the IoT Architecture. IEEE Sens. J. 2020, 20, 10295–10305. [Google Scholar] [CrossRef]
- Kaur, H.; Kumar, R. A survey on Internet of Things (IoT): Layer-specific, domain-specific and industry-defined architectures. In Advances in Computational Intelligence and Communication Technology; Springer: Berlin/Heidelberg, Germany, 2021; pp. 265–275. [Google Scholar]
- HaddadPajouh, H.; Khayami, R.; Dehghantanha, A.; Choo, K.K.R.; Parizi, R.M. AI4SAFE-IoT: An AI-powered secure architecture for edge layer of Internet of things. Neural Comput. Appl. 2020, 32, 16119–16133. [Google Scholar] [CrossRef]
- Abdullah, A.; Kaur, H.; Biswas, R. Universal Layers of IoT Architecture and Its Security Analysis. In New Paradigm in Decision Science and Management; Springer: Berlin/Heidelberg, Germany, 2020; pp. 293–302. [Google Scholar]
- Mrabet, H.; Belguith, S.; Alhomoud, A.; Jemai, A. A survey of IoT security based on a layered architecture of sensing and data analysis. Sensors 2020, 20, 3625. [Google Scholar] [CrossRef]
- Alidoosti, M.; Nowroozi, A.; Nickabadi, A. Evaluating the web-application resiliency to business-layer DoS attacks. ETRI J. 2020, 42, 433–445. [Google Scholar] [CrossRef]
- Patnaik, R.; Padhy, N.; Raju, K.S. A systematic survey on IoT security issues, vulnerability and open challenges. In Intelligent System Design; Springer: Berlin/Heidelberg, Germany, 2021; pp. 723–730. [Google Scholar]
- Chen, B.; Wan, J. Emerging trends of ml-based intelligent services for industrial internet of things (iiot). In Proceedings of the 2019 Computing, Communications and IoT Applications (ComComAp), Shenzhen, China, 26–28 October 2019; pp. 135–139. [Google Scholar]
- Ozanich, E.; Gerstoft, P.; Niu, H. A feedforward neural network for direction-of-arrival estimation. J. Acoust. Soc. Am. 2020, 147, 2035–2048. [Google Scholar] [CrossRef]
- Orimoloye, L.O.; Sung, M.C.; Ma, T.; Johnson, J.E. Comparing the effectiveness of deep feedforward neural networks and shallow architectures for predicting stock price indices. Expert Syst. Appl. 2020, 139, 112828. [Google Scholar] [CrossRef]
- Zhang, N.; Sun, S. Multiview Graph Restricted Boltzmann Machines. IEEE Trans. Cybern. 2021. [Google Scholar] [CrossRef] [PubMed]
- Gu, L.; Zhou, F.; Yang, L. Towards the representational power of restricted Boltzmann machines. Neurocomputing 2020, 415, 358–367. [Google Scholar] [CrossRef]
- Deshwal, D.; Sangwan, P. A Comprehensive Study of Deep Neural Networks for Unsupervised Deep Learning. In Artificial Intelligence for Sustainable Development: Theory, Practice and Future Applications; Springer: Berlin/Heidelberg, Germany, 2021; pp. 101–126. [Google Scholar]
- Chen, C.; Ma, Y.; Ren, G. Hyperspectral classification using deep belief networks based on conjugate gradient update and pixel-centric spectral block features. IEEE J. Sel. Top. Appl. Earth Obs. Remote Sens. 2020, 13, 4060–4069. [Google Scholar] [CrossRef]
- Hong, C.; Zeng, Z.Y.; Fu, Y.Z.; Guo, M.F. Deep-Belief-Networks Based Fault Classification in Power Distribution Networks. IEEJ Trans. Electr. Electron. Eng. 2020, 15, 1428–1435. [Google Scholar] [CrossRef]
- Chu, H.; Wei, J.; Wu, W.; Jiang, Y.; Chu, Q.; Meng, X. A classification-based deep belief networks model framework for daily streamflow forecasting. J. Hydrol. 2021, 595, 125967. [Google Scholar] [CrossRef]
- Zhuang, X.; Guo, H.; Alajlan, N.; Zhu, H.; Rabczuk, T. Deep autoencoder based energy method for the bending, vibration, and buckling analysis of Kirchhoff plates with transfer learning. Eur. J. Mech. -A/Solids 2021, 87, 104225. [Google Scholar] [CrossRef]
- Pawar, K.; Attar, V.Z. Assessment of autoencoder architectures for data representation. In Deep Learning: Concepts and Architectures; Springer: Berlin/Heidelberg, Germany, 2020; pp. 101–132. [Google Scholar]
- Deng, Z.; Li, Y.; Zhu, H.; Huang, K.; Tang, Z.; Wang, Z. Sparse stacked autoencoder network for complex system monitoring with industrial applications. Chaos Solitons Fractals 2020, 137, 109838. [Google Scholar] [CrossRef]
- LeCun, Y.; Bottou, L.; Bengio, Y.; Haffner, P. Gradient-based learning applied to document recognition. Proc. IEEE 1998, 86, 2278–2324. [Google Scholar] [CrossRef] [Green Version]
- Krizhevsky, A.; Sutskever, I.; Hinton, G.E. Imagenet classification with deep convolutional neural networks. Adv. Neural Inf. Process. Syst. 2012, 25, 1097–1105. [Google Scholar] [CrossRef]
- Redmon, J.; Divvala, S.; Girshick, R.; Farhadi, A. You only look once: Unified, real-time object detection. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Las Vegas, NV, USA, 27–30 June 2016; pp. 779–788. [Google Scholar]
- Zhang, Y.; Wang, Y.; Luo, G. A new optimization algorithm for non-stationary time series prediction based on recurrent neural networks. Future Gener. Comput. Syst. 2020, 102, 738–745. [Google Scholar] [CrossRef]
- Boulila, W.; Ghandorh, H.; Khan, M.A.; Ahmed, F.; Ahmad, J. A novel CNN-LSTM-based approach to predict urban expansion. Ecol. Inform. 2021, 101325. [Google Scholar] [CrossRef]
- Kousik, N.; Natarajan, Y.; Raja, R.A.; Kallam, S.; Patan, R.; Gandomi, A.H. Improved salient object detection using hybrid Convolution Recurrent Neural Network. Expert Syst. Appl. 2021, 166, 114064. [Google Scholar] [CrossRef]
- Aggarwal, A.; Mittal, M.; Battineni, G. Generative adversarial network: An overview of theory and applications. Int. J. Inf. Manag. Data Insights 2021, 100004. [Google Scholar] [CrossRef]
- Yoon, J.; Drumright, L.N.; Van Der Schaar, M. Anonymization through data synthesis using generative adversarial networks (ads-gan). IEEE J. Biomed. Health Inform. 2020, 24, 2378–2388. [Google Scholar] [CrossRef]
- Fekri, M.N.; Ghosh, A.M.; Grolinger, K. Generating energy data for machine learning with recurrent generative adversarial networks. Energies 2020, 13, 130. [Google Scholar] [CrossRef] [Green Version]
- Nguyen, G.; Dlugolinsky, S.; Bobák, M.; Tran, V.; García, Á.L.; Heredia, I.; Malík, P.; Hluchỳ, L. Machine learning and deep learning frameworks and libraries for large-scale data mining: A survey. Artif. Intell. Rev. 2019, 52, 77–124. [Google Scholar] [CrossRef] [Green Version]
- Pang, B.; Nijkamp, E.; Wu, Y.N. Deep learning with tensorflow: A review. J. Educ. Behav. Stat. 2020, 45, 227–248. [Google Scholar] [CrossRef]
- TensorFlow: An End-to-End Open Source Machine Learning Platform. Available online: https://www.tensorflow.org/ (accessed on 4 August 2021).
- TensorFlow Lite. Available online: https://www.tensorflow.org/lite/guide (accessed on 4 August 2021).
- Yapici, M.M.; Topaloğlu, N. Performance comparison of deep learning frameworks. Comput. Inform. 2021, 1, 1–11. [Google Scholar]
- Microsoft. The Microsoft Cognitive Toolkit. Available online: https://docs.microsoft.com/en-us/cognitive-toolkit/ (accessed on 4 August 2021).
- Gulli, A.; Pal, S. Deep Learning with Keras; Packt Publishing Ltd.: Birmingham, UK, 2017. [Google Scholar]
- Keras: The Python Deep Learning API. Available online: https://keras.io/about/ (accessed on 4 August 2021).
- Bahrampour, S.; Ramakrishnan, N.; Schott, L.; Shah, M. Comparative Study of Caffe, Neon, Theano, and Torch for Deep Learning 2016. Available online: https://openreview.net/pdf/q7kEN7WoXU8LEkD3t7BQ.pdf (accessed on 6 August 2021).
- Caffe: Deep Learning Framework. Available online: https://caffe.berkeleyvision.org/ (accessed on 8 August 2021).
- Wang, Z.; Liu, K.; Li, J.; Zhu, Y.; Zhang, Y. Various frameworks and libraries of machine learning and deep learning: A survey. Arch. Comput. Methods Eng. 2019, 1–24. [Google Scholar] [CrossRef]
- Caffe2: A New Lightweight, Modular, and Scalable Deep Learning Framework. Available online: https://caffe2.ai/docs/caffe-migration.html (accessed on 8 August 2021).
- Hodnett, M.; Wiley, J.F. R Deep Learning Essentials: A Step-by-Step Guide to Building Deep Learning Models Using Tensorflow, Keras, and MXNet; Packt Publishing Ltd.: Birmingham, UK, 2018. [Google Scholar]
- Apache MXNet: A Flexible and Efficient Library for Deep Learning. Available online: https://mxnet.apache.org/versions/1.8.0/ (accessed on 8 August 2021).
- Kabakuş, A.T. A Comparison of the State-of-the-Art Deep Learning Platforms: An Experimental Study. Sak. Univ. J. Comput. Inf. Sci. 2020, 3, 169–182. [Google Scholar] [CrossRef]
- Torch: A Scientific Computing Framewotk for LuaJIT. Available online: http://torch.ch/ (accessed on 8 August 2021).
- Paszke, A.; Gross, S.; Massa, F.; Lerer, A.; Bradbury, J.; Chanan, G.; Killeen, T.; Lin, Z.; Gimelshein, N.; Antiga, L.; et al. Pytorch: An imperative style, high-performance deep learning library. Adv. Neural Inf. Process. Syst. 2019, 32, 8026–8037. [Google Scholar]
- Stevens, E.; Antiga, L.; Viehmann, T. Deep learning with PyTorch; Manning Publications Company: Shelter Island, NY, USA, 2020. [Google Scholar]
- Bourez, C. Deep Learning with Theano; Packt Publishing Ltd.: Birmingham, UK, 2017. [Google Scholar]
- Brownlee, J. Introduction to the Python Deep Learning Library Theano. 2016. Available online: https://machinelearningmastery.com/introduction-python-deep-learning-library-theano/ (accessed on 8 August 2021).
- Tokui, S.; Okuta, R.; Akiba, T.; Niitani, Y.; Ogawa, T.; Saito, S.; Suzuki, S.; Uenishi, K.; Vogel, B.; Yamazaki Vincent, H. Chainer: A deep learning framework for accelerating the research cycle. In Proceedings of the 25th ACM SIGKDD International Conference on Knowledge Discovery & Data Mining, Anchorage, AK, USA, 4–8 August 2019; pp. 2002–2011. [Google Scholar]
- Chainer: A Powerful, Flexible, and Intuitive Framework for Neural Networks. Available online: https://chainer.org/ (accessed on 8 August 2021).
- Hattersley, L. Learn Artificial Intelligence with Raspberry Pi. 2019. Available online: https://magpi.raspberrypi.org/articles/learn-artificial-intelligence-with-raspberry-pi (accessed on 12 August 2021).
- Hattersley, L. Raspberry Pi 4. Available online: https://www.raspberrypi.org/products/raspberry-pi-4-model-b/ (accessed on 12 August 2021).
- Developer, N. Jetson Xavier NX Developer Kit. Available online: https://developer.nvidia.com/embedded/jetson-xavier-nx-devkit (accessed on 12 August 2021).
- Developer, N. Jetson Nano: Deep Learning Inference Benchmarks. Available online: https://developer.nvidia.com/embedded/jetson-nano-dl-inference-benchmarks (accessed on 12 August 2021).
- Developer, N. NVIDIA Jetson AGX Xavier: The AI Platform for Autonomous Machines. Available online: https://www.nvidia.com/en-us/autonomous-machines/jetson-agx-xavier/ (accessed on 12 August 2021).
- Dev Board: Coral. Available online: https://coral.ai/products/dev-board/ (accessed on 12 August 2021).
- Dev Board Mini: Coral. Available online: https://coral.ai/products/dev-board-mini/ (accessed on 12 August 2021).
- Yida. Introducing the Rock Pi N10 RK3399Pro—SBC for AI and Deep Learning. 2019. Available online: https://www.seeedstudio.com/blog/2019/12/04/introducing-the-rock-pi-n10-rk3399pro-sbc-for-ai-and-deep-learning/ (accessed on 13 August 2021).
- Synced. Huawei Introduces AI Development Board HiKey 970. 2018. Available online: https://medium.com/syncedreview/huawei-introduces-ai-development-board-hikey-970-763ac996b29a (accessed on 13 August 2021).
- BeagleBone AI: Fast Track to Embedded Artificial Intelligence. Available online: https://beagleboard.org/ai (accessed on 13 August 2021).
- Cloudware, O. BeagleV Development Board Features RISC-V Architecture. 2021. Available online: https://opencloudware.com/beaglev-development-board-features-risc-v-architecture/ (accessed on 13 August 2021).
- Sehgal, G.; Gupta, B.; Paneri, K.; Singh, K.; Sharma, G.; Shroff, G. Crop planning using stochastic visual optimization. In Proceedings of the 2017 IEEE Visualization in Data Science (VDS), Phoenix, AZ, USA, 1 October 2017; pp. 47–51. [Google Scholar]
- Song, X.; Zhang, G.; Liu, F.; Li, D.; Zhao, Y.; Yang, J. Modeling spatio-temporal distribution of soil moisture by deep learning-based cellular automata model. J. Arid Land 2016, 8, 734–748. [Google Scholar] [CrossRef] [Green Version]
- Douarre, C.; Schielein, R.; Frindel, C.; Gerth, S.; Rousseau, D. Deep learning based root-soil segmentation from X-ray tomography images. bioRxiv 2016, 071662. [Google Scholar] [CrossRef]
- Aliev, K.; Pasero, E.; Jawaid, M.M.; Narejo, S.; Pulatov, A. Internet of plants application for smart agriculture. Int. J. Adv. Comput. Sci. Appl 2018, 9, 421–429. [Google Scholar] [CrossRef]
- Huang, H.; Deng, J.; Lan, Y.; Yang, A.; Deng, X.; Zhang, L. A fully convolutional network for weed mapping of unmanned aerial vehicle (UAV) imagery. PLoS ONE 2018, 13, e0196302. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Rahnemoonfar, M.; Sheppard, C. Deep count: Fruit counting based on deep simulated learning. Sensors 2017, 17, 905. [Google Scholar] [CrossRef] [Green Version]
- Jiang, Z.; Liu, C.; Hendricks, N.P.; Ganapathysubramanian, B.; Hayes, D.J.; Sarkar, S. Predicting county level corn yields using deep long short term memory models. arXiv 2018, arXiv:1805.12044. [Google Scholar]
- Ferentinos, K.P. Deep learning models for plant disease detection and diagnosis. Comput. Electron. Agric. 2018, 145, 311–318. [Google Scholar] [CrossRef]
- Toda, Y.; Okura, F. How convolutional neural networks diagnose plant disease. Plant Phenomics 2019, 2019, 9237136. [Google Scholar] [CrossRef]
- Grinblat, G.L.; Uzal, L.C.; Larese, M.G.; Granitto, P.M. Deep learning for plant identification using vein morphological patterns. Comput. Electron. Agric. 2016, 127, 418–424. [Google Scholar] [CrossRef] [Green Version]
- Bhardwaj, P.; Gupta, P.; Panwar, H.; Siddiqui, M.K.; Morales-Menendez, R.; Bhaik, A. Application of Deep Learning on Student Engagement in e-learning environments. Comput. Electr. Eng. 2021, 93, 107277. [Google Scholar] [CrossRef]
- Han, Z.; Xu, A. Ecological evolution path of smart education platform based on deep learning and image detection. Microprocess. Microsyst. 2021, 80, 103343. [Google Scholar] [CrossRef]
- Tsai, S.C.; Chen, C.H.; Shiao, Y.T.; Ciou, J.S.; Wu, T.N. Precision education with statistical learning and deep learning: A case study in Taiwan. Int. J. Educ. Technol. High. Educ. 2020, 17, 1–13. [Google Scholar] [CrossRef]
- Fok, W.W.; He, Y.; Yeung, H.A.; Law, K.; Cheung, K.; Ai, Y.; Ho, P. Prediction model for students’ future development by deep learning and tensorflow artificial intelligence engine. In Proceedings of the 2018 4th International Conference on Information Management (ICIM), Oxford, UK, 25–27 May 2018; pp. 103–106. [Google Scholar]
- Nandal, P. Deep Learning in diverse Computing and Network Applications Student Admission Predictor using Deep Learning. In Proceedings of the International Conference on Innovative Computing & Communications (ICICC), Delhi, India, 20–22 February 2020. [Google Scholar]
- Khaleel, M.F.; Sharkh, M.A.; Kalil, M. A Cloud-based Architecture for Automated Grading of Computer-Aided Design Student Work Using Deep Learning. In Proceedings of the 2020 IEEE Canadian Conference on Electrical and Computer Engineering (CCECE), London, ON, Canada, 30 August–2 September 2020; pp. 1–5. [Google Scholar]
- Choi, E.; Biswal, S.; Malin, B.; Duke, J.; Stewart, W.F.; Sun, J. Generating multi-label discrete patient records using generative adversarial networks. In Proceedings of the Machine Learning for Healthcare Conference, PMLR, Boston, MA, USA, 18–19 August 2017; pp. 286–305. [Google Scholar]
- Nie, D.; Trullo, R.; Lian, J.; Wang, L.; Petitjean, C.; Ruan, S.; Wang, Q.; Shen, D. Medical image synthesis with deep convolutional adversarial networks. IEEE Trans. Biomed. Eng. 2018, 65, 2720–2730. [Google Scholar] [CrossRef]
- Sha, Y.; Wang, M.D. Interpretable predictions of clinical outcomes with an attention-based recurrent neural network. In Proceedings of the 8th ACM International Conference on Bioinformatics, Computational Biology, and Health Informatics, Boston, MA, USA, 20–23 August 2017; pp. 233–240. [Google Scholar]
- Verma, H.; Kumar, S. An accurate missing data prediction method using LSTM based deep learning for health care. In Proceedings of the 20th International Conference on Distributed Computing and Networking, Bangalore, India, 4–7 January 2019; pp. 371–376. [Google Scholar]
- Sun, M.; Min, T.; Zang, T.; Wang, Y. CDL4CDRP: A collaborative deep learning approach for clinical decision and risk prediction. Processes 2019, 7, 265. [Google Scholar] [CrossRef] [Green Version]
- Najdi, S.; Gharbali, A.A.; Fonseca, J.M. Feature transformation based on stacked sparse autoencoders for sleep stage classification. In Proceedings of the Doctoral Conference on Computing, Electrical and Industrial Systems, Costa de Caparica, Portugal, 3–5 May 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 191–200. [Google Scholar]
- Nguyen, M.; Sun, N.; Alexander, D.C.; Feng, J.; Yeo, B.T. Modeling Alzheimer’s disease progression using deep recurrent neural networks. In Proceedings of the 2018 International Workshop on Pattern Recognition in Neuroimaging (PRNI), Singapore, 12–14 June 2018; pp. 1–4. [Google Scholar]
- Xue, Q.; Wang, X.; Meehan, S.; Kuang, J.; Gao, J.A.; Chuah, M.C. Recurrent neural networks based obesity status prediction using activity data. In Proceedings of the 2018 17th IEEE International Conference on Machine Learning and Applications (ICMLA), Orlando, FL, USA, 17–20 December 2018; pp. 865–870. [Google Scholar]
- Amin, S.U.; Hossain, M.S.; Muhammad, G.; Alhussein, M.; Rahman, M.A. Cognitive smart healthcare for pathology detection and monitoring. IEEE Access 2019, 7, 10745–10753. [Google Scholar] [CrossRef]
- Wang, L.; Zhou, X. Detection of congestive heart failure based on LSTM-based deep network via short-term RR intervals. Sensors 2019, 19, 1502. [Google Scholar] [CrossRef] [Green Version]
- Alhussein, M.; Muhammad, G. Voice pathology detection using deep learning on mobile healthcare framework. IEEE Access 2018, 6, 41034–41041. [Google Scholar] [CrossRef]
- Maragatham, G.; Devi, S. LSTM model for prediction of heart failure in big data. J. Med. Syst. 2019, 43, 111. [Google Scholar] [CrossRef]
- Kim, J.; Kang, U.; Lee, Y. Statistics and deep belief network-based cardiovascular risk prediction. Healthc. Inform. Res. 2017, 23, 169–175. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Xu, W.; Feng, X.; Wang, J.; Luo, C.; Li, J.; Ming, Z. Energy harvesting-based smart transportation mode detection system via attention-based lstm. IEEE Access 2019, 7, 66423–66434. [Google Scholar] [CrossRef]
- Song, X.; Kanasugi, H.; Shibasaki, R. Deeptransport: Prediction and simulation of human mobility and transportation mode at a citywide level. In Proceedings of the Twenty-Fifth International Joint Conference on Artificial Intelligence, New York, NY, USA, 9–15 July 2016; pp. 2618–2624. [Google Scholar]
- Mohammadi, M.; Al-Fuqaha, A.; Oh, J.S. Path planning in support of smart mobility applications using generative adversarial networks. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 878–885. [Google Scholar]
- Camero, A.; Toutouh, J.; Stolfi, D.H.; Alba, E. Evolutionary deep learning for car park occupancy prediction in smart cities. In Proceedings of the International Conference on Learning and Intelligent Optimization, Kalamata, Greece, 10–15 June 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 386–401. [Google Scholar]
- Singh, D.; Mohan, C.K. Deep spatio-temporal representation for detection of road accidents using stacked autoencoder. IEEE Trans. Intell. Transp. Syst. 2018, 20, 879–887. [Google Scholar] [CrossRef]
- Lv, Z.; Xu, J.; Zheng, K.; Yin, H.; Zhao, P.; Zhou, X. Lc-rnn: A deep learning model for traffic speed prediction. In Proceedings of the Twenty-Seventh International Joint Conference on Artificial Intelligence (IJCAI-18), Stockholm, Sweden, 13–19 July 2018; pp. 3470–3476. [Google Scholar]
- Ma, X.; Yu, H.; Wang, Y.; Wang, Y. Large-scale transportation network congestion evolution prediction using deep learning theory. PLoS ONE 2015, 10, e0119044. [Google Scholar] [CrossRef]
- Pérez, J.L.; Gutierrez-Torre, A.; Berral, J.L.; Carrera, D. A resilient and distributed near real-time traffic forecasting application for Fog computing environments. Future Gener. Comput. Syst. 2018, 87, 198–212. [Google Scholar] [CrossRef]
- Xiangxue, W.; Lunhui, X.; Kaixun, C. Data-driven short-term forecasting for urban road network traffic based on data processing and LSTM-RNN. Arab. J. Sci. Eng. 2019, 44, 3043–3060. [Google Scholar] [CrossRef]
- Goudarzi, S.; Kama, M.N.; Anisi, M.H.; Soleymani, S.A.; Doctor, F. Self-organizing traffic flow prediction with an optimized deep belief network for internet of vehicles. Sensors 2018, 18, 3459. [Google Scholar] [CrossRef] [Green Version]
- Park, S.T.; Li, G.; Hong, J.C. A study on smart factory-based ambient intelligence context-aware intrusion detection system using machine learning. J. Ambient Intell. Humaniz. Comput. 2020, 11, 1405–1412. [Google Scholar] [CrossRef]
- Tao, W.; Lai, Z.H.; Leu, M.C.; Yin, Z. Worker activity recognition in smart manufacturing using IMU and sEMG signals with convolutional neural networks. Procedia Manuf. 2018, 26, 1159–1166. [Google Scholar] [CrossRef]
- Ren, L.; Sun, Y.; Cui, J.; Zhang, L. Bearing remaining useful life prediction based on deep autoencoder and deep neural networks. J. Manuf. Syst. 2018, 48, 71–77. [Google Scholar] [CrossRef]
- Yan, H.; Wan, J.; Zhang, C.; Tang, S.; Hua, Q.; Wang, Z. Industrial big data analytics for prediction of remaining useful life based on deep learning. IEEE Access 2018, 6, 17190–17197. [Google Scholar] [CrossRef]
- Jiang, L.; Ge, Z.; Song, Z. Semi-supervised fault classification based on dynamic Sparse Stacked auto-encoders model. Chemom. Intell. Lab. Syst. 2017, 168, 72–83. [Google Scholar] [CrossRef]
- Yuan, Y.; Ma, G.; Cheng, C.; Zhou, B.; Zhao, H.; Zhang, H.T.; Ding, H. Artificial intelligent diagnosis and monitoring in manufacturing. arXiv 2018, arXiv:1901.02057. [Google Scholar]
- Li, L.; Ota, K.; Dong, M. Deep learning for smart industry: Efficient manufacture inspection system with fog computing. IEEE Trans. Ind. Inform. 2018, 14, 4665–4673. [Google Scholar] [CrossRef] [Green Version]
- Wang, J.; Wang, K.; Wang, Y.; Huang, Z.; Xue, R. Deep Boltzmann machine based condition prediction for smart manufacturing. J. Ambient Intell. Humaniz. Comput. 2019, 10, 851–861. [Google Scholar] [CrossRef]
- Zhang, W.; Guo, W.; Liu, X.; Liu, Y.; Zhou, J.; Li, B.; Lu, Q.; Yang, S. LSTM-based analysis of industrial IoT equipment. IEEE Access 2018, 6, 23551–23560. [Google Scholar] [CrossRef]
- Alkhamisi, A.O.; Mehmood, R. An ensemble machine and deep learning model for risk prediction in aviation systems. In Proceedings of the 2020 6th Conference on Data Science and Machine Learning Applications (CDMA), Riyadh, Saudi Arabia, 4–5 March 2020; pp. 54–59. [Google Scholar]
- Acuna-Agost, R.; Thomas, E.; Lhéritier, A. Price elasticity estimation for deep learning-based choice models: An application to air itinerary choices. J. Revenue Pricing Manag. 2021, 20, 213–226. [Google Scholar] [CrossRef]
- Barakat, H.; Yeniterzi, R.; Martín-Domingo, L. Applying deep learning models to twitter data to detect airport service quality. J. Air Transp. Manag. 2021, 91, 102003. [Google Scholar] [CrossRef]
- Wu, E.Q.; Deng, P.Y.; Qu, X.Y.; Tang, Z.; Zhang, W.M.; Zhu, L.M.; Ren, H.; Zhou, G.R.; Sheng, R.S. Detecting fatigue status of pilots based on deep learning network using EEG signals. IEEE Trans. Cogn. Dev. Syst. 2020, 13, 575–585. [Google Scholar] [CrossRef]
- Dong, T.; Yang, Q.; Ebadi, N.; Luo, X.R.; Rad, P. Identifying Incident Causal Factors to Improve Aviation Transportation Safety: Proposing a Deep Learning Approach. J. Adv. Transp. 2021, 2021, 5540046. [Google Scholar] [CrossRef]
- Yazdi, M.F.; Kamel, S.R.; Chabok, S.J.M.; Kheirabadi, M. Flight delay prediction based on deep learning and Levenberg-Marquart algorithm. J. Big Data 2020, 7, 106. [Google Scholar] [CrossRef]
- Wang, L.; Mykityshyn, A.; Johnson, C.M.; Marple, B.D. Deep Learning for Flight Demand and Delays Forecasting. In Proceedings of the AIAA Aviation 2021 Forum, Virtual, 2–6 August 2021; p. 2399. [Google Scholar]
- Corrado, S.J.; Puranik, T.G.; Pinon-Fischer, O.J.; Mavris, D.; Rose, R.; Williams, J.; Heidary, R. Deep Autoencoder for Anomaly Detection in Terminal Airspace Operations. In Proceedings of the AIAA Aviation 2021 Forum, Virtual, 2–6 August 2021; p. 2405. [Google Scholar]
- Hasib, K.M.; Habib, M.A.; Towhid, N.A.; Showrov, M.I.H. A Novel Deep Learning based Sentiment Analysis of Twitter Data for US Airline Service. In Proceedings of the 2021 International Conference on Information and Communication Technology for Sustainable Development (ICICT4SD), Dhaka, Bangladesh, 27–28 February 2021; pp. 450–455. [Google Scholar]
- Das, L.B.; Lijiya, A.; Jagadanand, G.; Aadith, A.; Gautham, S.; Mohan, V.; Reuben, S.; George, G. Human Target Search and Detection using Autonomous UAV and Deep learning. In Proceedings of the 2020 IEEE International Conference on Industry 4.0, Artificial Intelligence, and Communications Technology (IAICT), Bali, Indonesia, 7–8 July 2020; pp. 55–61. [Google Scholar]
- Calderón, M.; Aguilar, W.G.; Merizalde, D. Visual-Based Real-Time Detection Using Neural Networks and Micro-UAVs for Military Operations. In Developments and Advances in Defense and Security; Springer: Berlin/Heidelberg, Germany, 2020; p. 55. [Google Scholar]
- Krishnaveni, P.; Sutha, J. Novel deep learning framework for broadcasting abnormal events obtained from surveillance applications. J. Ambient Intell. Humaniz. Comput. 2020, 1–15. [Google Scholar] [CrossRef]
- Sharma, D.Y.K.; Pradeep, S. Deep Learning based Real Time Object Recognition for Security in Air Defense. In Proceedings of the 13th INDIACom, New Delhi, India, 13–15 March 2019; pp. 64–67. [Google Scholar]
- Shi, Y.; Sagduyu, Y.E.; Erpek, T.; Davaslioglu, K.; Lu, Z.; Li, J.H. Adversarial deep learning for cognitive radio security: Jamming attack and defense strategies. In Proceedings of the 2018 IEEE International Conference on Communications Workshops (ICC Workshops), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Wang, F.; Zhong, C.; Gursoy, M.C.; Velipasalar, S. Defense strategies against adversarial jamming attacks via deep reinforcement learning. In Proceedings of the 2020 54th Annual Conference on Information Sciences and Systems (CISS), Princeton, NJ, USA, 18–20 March 2020; pp. 1–6. [Google Scholar]
- Chen, C.Y.; Lai, W.; Hsieh, H.Y.; Zheng, W.H.; Wang, Y.S.; Chuang, J.H. Generating defensive plays in basketball games. In Proceedings of the 26th ACM international conference on Multimedia, Seoul, Korea, 22–26 October 2018; pp. 1580–1588. [Google Scholar]
- Chung, J.; Kastner, K.; Dinh, L.; Goel, K.; Courville, A.C.; Bengio, Y. A recurrent latent variable model for sequential data. Adv. Neural Inf. Process. Syst. 2015, 28, 2980–2988. [Google Scholar]
- Baccouche, M.; Mamalet, F.; Wolf, C.; Garcia, C.; Baskurt, A. Action classification in soccer videos with long short-term memory recurrent neural networks. In Proceedings of the International Conference on Artificial Neural Networks, Thessaloniki, Greece, 15–18 September 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 154–159. [Google Scholar]
- Theagarajan, R.; Pala, F.; Zhang, X.; Bhanu, B. Soccer: Who has the ball? Generating visual analytics and player statistics. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition Workshops, Salt Lake City, UT, USA, 18–22 June 2018; pp. 1749–1757. [Google Scholar]
- Le, H.M.; Carr, P.; Yue, Y.; Lucey, P. Data-driven ghosting using deep imitation learning. In Proceedings of the MIT Sloan Sports Analytics Conference, Boston, MA, USA, 3–4 March 2017. [Google Scholar]
- Kautz, T.; Groh, B.H.; Hannink, J.; Jensen, U.; Strubberg, H.; Eskofier, B.M. Activity recognition in beach volleyball using a deep convolutional neural network. Data Min. Knowl. Discov. 2017, 31, 1678–1705. [Google Scholar] [CrossRef]
- Qiao, F. Application of deep learning in automatic detection of technical and tactical indicators of table tennis. PLoS ONE 2021, 16, e0245259. [Google Scholar] [CrossRef]
- Cao, Z.; Liao, T.; Song, W.; Chen, Z.; Li, C. Detecting the shuttlecock for a badminton robot: A YOLO based approach. Expert Syst. Appl. 2021, 164, 113833. [Google Scholar] [CrossRef]
- Li, H.; Ota, K.; Dong, M. Learning IoT in edge: Deep learning for the Internet of Things with edge computing. IEEE Netw. 2018, 32, 96–101. [Google Scholar] [CrossRef] [Green Version]
- Roopaei, M.; Rad, P.; Jamshidi, M. Deep learning control for complex and large scale cloud systems. Intell. Autom. Soft Comput. 2017, 23, 389–391. [Google Scholar] [CrossRef]
- Rymarczyk, T.; Kłosowski, G.; Kozłowski, E.; Tchórzewski, P. Comparison of selected machine learning algorithms for industrial electrical tomography. Sensors 2019, 19, 1521. [Google Scholar] [CrossRef] [Green Version]
- Wang, Y.; Pan, Z.; Yuan, X.; Yang, C.; Gui, W. A novel deep learning based fault diagnosis approach for chemical process with extended deep belief network. ISA Trans. 2020, 96, 457–467. [Google Scholar] [CrossRef]
- Latif, S.; Zou, Z.; Idrees, Z.; Ahmad, J. A novel attack detection scheme for the industrial internet of things using a lightweight random neural network. IEEE Access 2020, 8, 89337–89350. [Google Scholar] [CrossRef]
- Khan, M.A.; Khan, M.A.; Latif, S.; Shah, A.A.; Rehman, M.U.; Boulila, W.; Driss, M.; Ahmad, J. Voting Classifier-based Intrusion Detection for IoT Networks. arXiv 2021, arXiv:2104.10015. [Google Scholar]
- Zhou, L.; Wu, D.; Chen, J.; Dong, Z. When computation hugs intelligence: Content-aware data processing for industrial IoT. IEEE Internet Things J. 2017, 5, 1657–1666. [Google Scholar] [CrossRef]
- Ai, Y.; Peng, M.; Zhang, K. Edge computing technologies for Internet of Things: A primer. Digit. Commun. Netw. 2018, 4, 77–86. [Google Scholar] [CrossRef]
- Latif, S.; Idrees, Z.; Zou, Z.; Ahmad, J. DRaNN: A deep random neural network model for intrusion detection in industrial IoT. In Proceedings of the 2020 International Conference on UK-China Emerging Technologies (UCET), Glasgow, UK, 20–21 August 2020; pp. 1–4. [Google Scholar]
- Savaglio, C.; Gerace, P.; Di Fatta, G.; Fortino, G. Data mining at the IoT edge. In Proceedings of the 2019 28th International Conference on Computer Communication and Networks (ICCCN), Valencia, Spain, 29 July–1 August 2019; pp. 1–6. [Google Scholar]
- Hatcher, W.G.; Yu, W. A survey of deep learning: Platforms, applications and emerging research trends. IEEE Access 2018, 6, 24411–24432. [Google Scholar] [CrossRef]
- Chen, J.; Li, K.; Deng, Q.; Li, K.; Philip, S.Y. Distributed deep learning model for intelligent video surveillance systems with edge computing. IEEE Trans. Ind. Inform. 2019. [Google Scholar] [CrossRef] [Green Version]
- Latif, S.; Idrees, Z.; Ahmad, J.; Zheng, L.; Zou, Z. A blockchain-based architecture for secure and trustworthy operations in the industrial Internet of Things. J. Ind. Inf. Integr. 2021, 21, 100190. [Google Scholar] [CrossRef]
- Luckow, A.; Cook, M.; Ashcraft, N.; Weill, E.; Djerekarov, E.; Vorster, B. Deep learning in the automotive industry: Applications and tools. In Proceedings of the 2016 IEEE International Conference on Big Data (Big Data), Washington, DC, USA, 5–8 December 2016; pp. 3759–3768. [Google Scholar]
- Yang, H.; Alphones, A.; Zhong, W.D.; Chen, C.; Xie, X. Learning-based energy-efficient resource management by heterogeneous RF/VLC for ultra-reliable low-latency industrial IoT networks. IEEE Trans. Ind. Inform. 2019, 16, 5565–5576. [Google Scholar] [CrossRef]
- Huma, Z.E.; Latif, S.; Ahmad, J.; Idrees, Z.; Ibrar, A.; Zou, Z.; Alqahtani, F.; Baothman, F. A Hybrid Deep Random Neural Network for Cyberattack Detection in the Industrial Internet of Things. IEEE Access 2021, 9, 55595–55605. [Google Scholar] [CrossRef]
- Bennis, M.; Debbah, M.; Poor, H.V. Ultrareliable and low-latency wireless communication: Tail, risk, and scale. Proc. IEEE 2018, 106, 1834–1853. [Google Scholar] [CrossRef] [Green Version]
- Gungor, V.C.; Hancke, G.P. Industrial wireless sensor networks: Challenges, design principles, and technical approaches. IEEE Trans. Ind. Electron. 2009, 56, 4258–4265. [Google Scholar] [CrossRef] [Green Version]
- Popescu, G.H. The economic value of the industrial internet of things. J. Self-Gov. Manag. Econ. 2015, 3, 86–91. [Google Scholar]
- Banaie, F.; Hashemzadeh, M. Complementing IIoT Services through AI: Feasibility and Suitability. In AI-Enabled Threat Detection and Security Analysis for Industrial IoT; Springer: Berlin/Heidelberg, Germany, 2021; pp. 7–19. [Google Scholar]
- Latif, S.; Idrees, Z.; e Huma, Z.; Ahmad, J. Blockchain technology for the industrial Internet of Things: A comprehensive survey on security challenges, architectures, applications, and future research directions. Trans. Emerg. Telecommun. Technol. 2021, e4337. [Google Scholar] [CrossRef]
- Cantor, B.; Grant, P.; Johnston, C. Automotive Engineering: Lightweight, Functional, and Novel Materials; CRC Press: Boca Raton, FL, USA, 2008. [Google Scholar]
- Alvarez-Gonzalez, F.; Griffo, A.; Sen, B.; Wang, J. Real-time hardware-in-the-loop simulation of permanent-magnet synchronous motor drives under stator faults. IEEE Trans. Ind. Electron. 2017, 64, 6960–6969. [Google Scholar] [CrossRef] [Green Version]
- Idrees, Z.; Granados, J.; Sun, Y.; Latif, S.; Gong, L.; Zou, Z.; Zheng, L. IEEE 1588 for Clock Synchronization in Industrial IoT and Related Applications: A Review on Contributing Technologies, Protocols and Enhancement Methodologies. IEEE Access 2020, 8, 155660–155678. [Google Scholar] [CrossRef]
- Abbas, A.; Khan, M.A.; Latif, S.; Ajaz, M.; Shah, A.A.; Ahmad, J. A New Ensemble-Based Intrusion Detection System for Internet of Things. Arab. J. Sci. Eng. 2021, 1–15. [Google Scholar] [CrossRef]
- Huerta, F.; Gruber, J.K.; Prodanovic, M.; Matatagui, P. Power-hardware-in-the-loop test beds: Evaluation tools for grid integration of distributed energy resources. IEEE Ind. Appl. Mag. 2016, 22, 18–26. [Google Scholar] [CrossRef]
- Mai, X.H.; Kwak, S.K.; Jung, J.H.; Kim, K.A. Comprehensive electric-thermal photovoltaic modeling for power-hardware-in-the-loop simulation (PHILS) applications. IEEE Trans. Ind. Electron. 2017, 64, 6255–6264. [Google Scholar] [CrossRef]
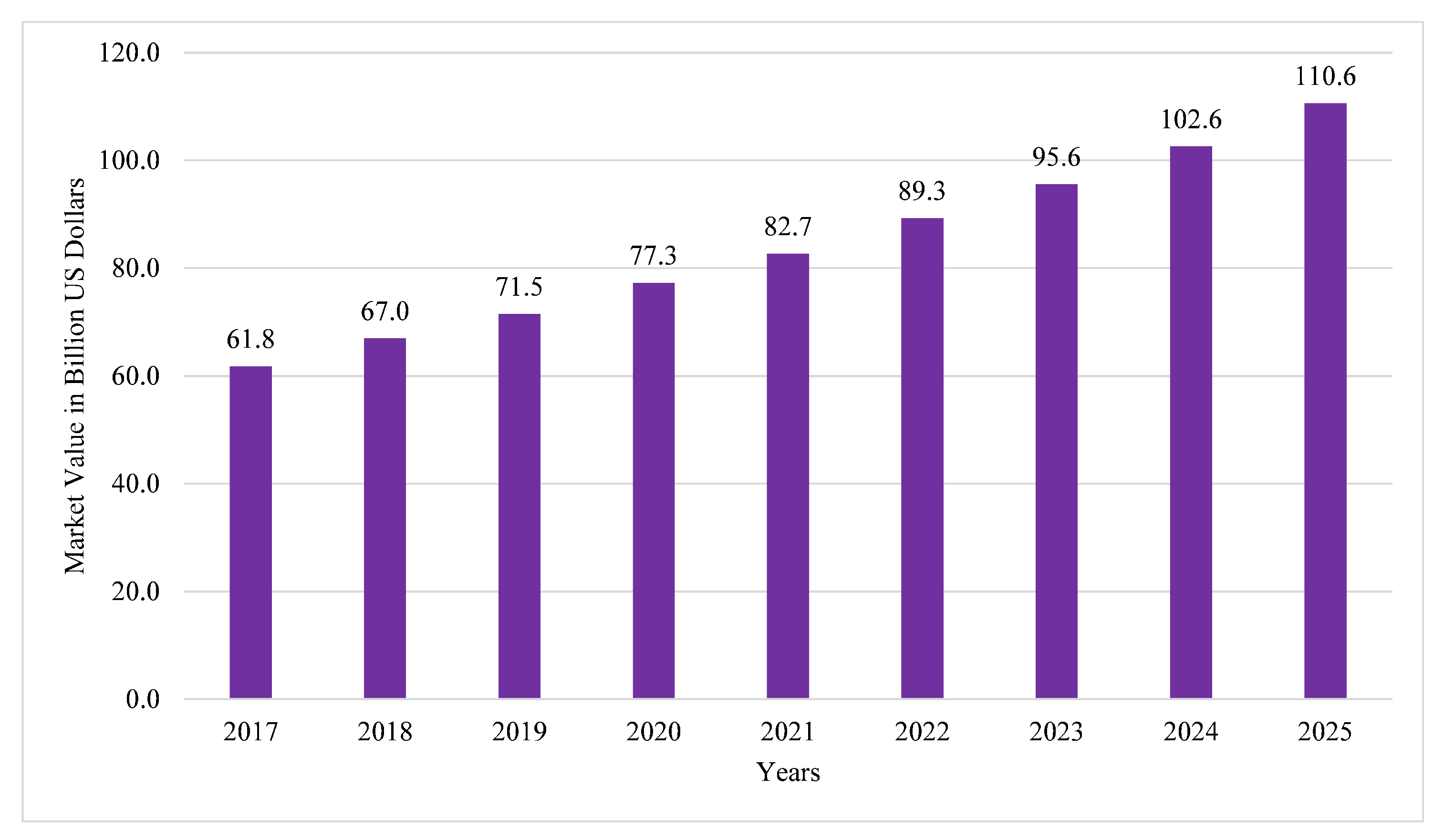




| Authors | Year | Contributions of Survey Articles | |||||
|---|---|---|---|---|---|---|---|
| IIoT Architecture | Algorithms | Frameworks | Hardware | Applications | Future Directions | ||
| Mohammadi et al. [10] | 2018 | √ | √ | √ | × | √ | √ |
| Ma et al. [11] | 2019 | × | √ | × | × | √ | √ |
| Sengupta et al. [12] | 2020 | × | √ | × | × | √ | √ |
| Ambika et al. [13] | 2020 | √ | √ | × | × | √ | × |
| Saleem et al. [14] | 2020 | × | √ | × | × | √ | × |
| Deepan et al. [15] | 2021 | × | √ | √ | × | √ | × |
| Khalil et al. [6] | 2021 | √ | √ | × | × | √ | √ |
| Our Study | 2021 | √ | √ | √ | √ | √ | √ |
| Author | DL Algorithm | Dataset | Application | Purpose of DL Technique |
|---|---|---|---|---|
| Sehgal et al. [79] | LSTM | Dataset from Syngeta crop challenge (2016) | Weather prediction | Weather prediction according to the conditions of preceding year |
| Song et al. [80] | DBN | Data gathered from corn field (irrigated) in China | Soil moisture content prediction | Prediction of moisture content in the soil |
| Douarre et al. [81] | CNN | X-ray tomographic images of soil | Root and soil segmentation | Image categorization into two classes root and soil |
| Aliev et al. [82] | RNN | Sensory data | Internet of plants-based system | To envisage the minimum and temperature records for ten days |
| Huang et al. [83] | CNN | Data collected using multirotor UAV | Weed mapping in smart agriculture | Classification of input images into three categories: weed, rice and others |
| Rahnemoonfar et al. [84] | CNN | Dataset consisting of 24,000 images | Tomato counting | Prediction of tomatoes quantity |
| Jiang et al. [85] | LSTM | Data obtained from the National Agricultural Statistics Service (NASS) Quick Stats | Crop yield prediction | Corn yield prediction |
| Ferentinos et al. [86] | CNN | Leaf images of plants | Plant disease detection | Image classification into health and diseased categories |
| Toda et al. [87] | CNN | Plant Village dataset | Plant disease diagnosis | Leaf image classification into healthy and diseased categories and diagnosis of disease type |
| Grinblat et al. [88] | CNN | Dataset consisting of vein leaf images of soybean, red beans, and white beans | Plant identification | Legume’s classification into three categories: red beans, soybean, and white beans |
| Author | DL Algorithm | Dataset | Application | Purpose of DL Technique |
|---|---|---|---|---|
| Bhardwaj et al. [89] | CNN | FER-2013, MES dataset | Student engagement | Monitoring the student’s emotions in real time such as anger, fear, disgust, sadness, happiness, and surprise |
| Han et al. [90] | DNN | Amazon | Smart education platform | Designing an intelligent educational environment |
| Tsai et al. [91] | MLP | University’s institutional research database | Precision education | To help universities to more precisely understand student backgrounds |
| Fok et al. [92] | CNN | Self-generated dataset | Prediction model for students’ future development | Analyzing students’ performance and prediction of their future program of studies |
| Nandal et al. [93] | DNN | Self-generated dataset | Student admission predictor | Development of student admission predictor program for students to find the chances of gaining admission to a university |
| Khaleel et al. [94] | DCNN | Self-generated dataset | Automated grading | Automatic grade prediction system for the students of computer-aided drawing |
| Author | DL Algorithm | Dataset | Application | Purpose of DL Technique |
|---|---|---|---|---|
| Choi et al. [95] | AE + GAN | Sutter PAMF, IMIC-III, Sutter Heart Failure | Generating patient records | Patient’s, record synthesis |
| Nie et al. [96] | GAN | Brain data from ADNI dataset, Pelvic dataset | Medical image synthesis | Synthetization of CT image from MRI |
| Sha et al. [97] | RNN | Medical Information Mart for Intensive Care (MIMIC) dataset | Clinical outcome prediction | Mortality prediction |
| Verma et al. [98] | LSTM | MIT-BIH dataset | Missing data prediction in healthcare | Prediction of missing data in healthcare scenarios |
| Sun et al. [99] | RBM | Chronic kidney disease (CKD) and dermatology datasets | Clinical decision and risk prediction | Capturing high-level features from the clinical data and predict missing values |
| Najdi et al. [100] | AE | ISRUC-Sleep dataset | Sleep stage classification | Dimensionality reduction, feature extraction, and classification |
| Nguyen et al. [101] | RNN | Alzheimer’s Disease Neuroimaging Initiative (ADNI) dataset | Alzheimer’s disease recognition | Modeling the succession of Alzheimer’s disease for seven years |
| Xue et al. [102] | RNN | Electronic medical records, Sensory data from wearables | Obesity status prediction | Prediction of improvement in obesity status based on blood demographics, pressure, and step count |
| Amin et al. [103] | CNN | Temple University Hospital dataset | Pathology detection and monitoring | Classification of EEG signals into two categories, normal and pathological |
| Wang et al. [104] | LSTM | Normal Sinus Rhythm (NSR), Fantasia Database (FD), | Congestive heart failure | Detection of congestive heart failure |
| Alhussein et al. [105] | CNN | SVD database, MEEI database | Voice pathology detection | Classification of voice signals into normal and pathological categories |
| Maragatham et al. [106] | LSTM | Electronic Health Records | Heart failure prediction | Modeling the risk prediction of heart failure |
| Kim et al. [107] | DBN | Sixth Korea National Health and Nutrition Examination Survey (KNHANES-VI) 2013 dataset | Cardiovascular risk prediction | Development of cardiovascular risk prediction model |
| Author | DL Algorithm | Dataset | Application | Purpose of DL Technique |
|---|---|---|---|---|
| Su et al. [108] | LSTM | 38.6 h of transportation data | Mode detection system | Identification of mode of transport based on kinetic energy harvester |
| Song et al. [109] | LSTM | GPS data and transportation network data | Human mobility and transportation mode prediction | Prediction of human movements |
| Mohammadi et al. [110] | GAN | Localization dataset, Path planning dataset | Path planning | Safe and reliable paths generation |
| Camero et al. [111] | RNN | Data from 29 Parking slots in Birmingham | Car Park occupancy prediction | Prediction of occupancies rate of car parks |
| Singh et al. [112] | AE | Traffic videos | Road Accident detection | Extraction of Spatio-temporal features from the surveillance video |
| Lv et al. [113] | RNN + CNN | Trajectory data from Beijing and Shanghai | Traffic speed prediction | Traffic speed prediction |
| Ma et al. [114] | RBM + RNN | GPS data | Congestion Evolution Prediction in the transportation network | Traffic congestion evolution from GPS data |
| Pérez et al. [115] | RBM | Floating car data gathered in Barcelona | Real-time traffic forecasting | Traffic prediction in real time |
| Xiangxue et al. [116] | LSTM | Floating Car Data | Short-term traffic prediction | Modeling of traffic flow in urban road networks |
| Goudarzi et al. [117] | DBN | Data containing historical road traffic flow | Traffic flow prediction | Traffic flows prediction |
| Author | DL Algorithm | Dataset | Application | Purpose of DL Technique |
|---|---|---|---|---|
| Park et al. [118] | AE | Sensory data, network traffic data | Intrusion detection system | Development of IDS |
| Tao et al. [119] | CNN | Sensory data | Worker activity recognition | Classification of worker’s activities into 6 groups: screwdriver, used power, grab tool, hammer, rest arm, turn a screwdriver, and wrench usage |
| Ren et al. [120] | AE | IEEE PHM2012 data provided by the FEMTO-ST Institute in France | Remaining useful life prediction of bearings | Features extraction that is important for the remaining bearings’ life prediction |
| Yan et al. [121] | AE | Data collected from CNC machining centers | Remaining useful life prediction in machines | Features extraction that is important for the remaining machine’s life prediction |
| Jiang et al. [122] | AE | Process data samples | Fault classification | Feature learning from a wide variety of faults |
| Yuan et al. [123] | CNN | Bearing data offered by Case Western Reserve University (CWRU) | Diagnosis and monitoring in manufacturing | Identification and prediction of machine faults |
| Li et al. [124] | CNN | Sensory data | Manufacture inspection system | Classification of production items into two categories: defected and non-defected. |
| Wang et al. [125] | DBN | Sensory data gathered from a centrifugal compressor | Condition prediction | Prediction of machine’s condition in manufacturing systems |
| Zhang et al. [126] | LSTM | Sensory data obtained from 33 sensors deployed on a pump in power station | Industrial IoT equipment analysis | Prediction of the working condition of industrial equipment to enhance operation quality |
| Author | DL Algorithm | Dataset | Application | Purpose of DL Technique |
|---|---|---|---|---|
| Alkhamisi et al. [127] | RNN | Aviation Safety Reporting System (ASRS) dataset | Risk prediction in Aviation Systems | Improvements of risks prediction in aviation systems |
| Rodrigo et al. [128] | PCMC-Net | Data extracted from a global distribution system (GDS) | Price elasticity estimation | Differentiate the price elasticity between business and leisure trips |
| Barakat et al. [129] | CNN + LSTM | Twitter US Airline Sentiment dataset | Airport service quality | Measurement of airport service quality using passengers’ tweets about airports |
| Wu et al. [130] | CSAE | Self-generated EEG dataset | Detecting fatigue status of pilots | Development of fatigue recognition system based on EEG signals and DL algorithms |
| Dong et al. [131] | LSTM | Aviation Safety Reporting System (ASRS) | Aviation transportation safety | Identification of incident causal factors for aviation transportation safety improvement. |
| Yazdi et al. [132] | SAE-LM + SDA | U.S flight dataset | Flight delay prediction | Development of flight delays prediction system. |
| Wang et al. [133] | LSTM | ASPM datasets | Flight demand and delays forecasting | Prediction of flight departure demand in a multiple-stage time horizon |
| Corrado et al. [134] | DAE | Flight data collected from San Francisco International Airport | Anomaly detection | Development of an anomaly detection system to identify deviated trajectories |
| Hasib et al. [135] | DNN + CNN | US airline service dataset | Sentiment analysis | Evaluation of six major US airlines and multi-class sentiment analysis |
| Author | DL Algorithm | Dataset | Application | Purpose of DL Technique |
|---|---|---|---|---|
| Das et al. [136] | R-CNN | Self-generated dataset | Target detection | Development of a new search algorithm for object detection through UAV |
| Calderón et al. [137] | CNN | Self-generated dataset | Real-time object detection | Development of a vision-based object detection system for a micro-UAV |
| Krishnaveni et al. [138] | DCNN | Data collected from wildlife television. | Surveillance applications | Identification of abnormal events and the data streaming by creating a multipath routing in WSN |
| Pradeep et al. [139] | CNN | Self-generated dataset | Real-time object recognition in air defense systems | Accurate identification of definite target with DL algorithm and real-time camera of FWN aircraft |
| Shi et al. [140] | FNN | Self-generated | Cognitive radio security | Launching of jamming attacks on wireless communications and development of a defense strategy |
| Wang et al. [141] | DRL | Self-generated dataset | Defense strategies against adversarial jamming attacks | Design and development of defense strategies against DRL-based jamming attackers on a multichannel access agent |
| Author | DL Algorithm | Dataset | Application | Purpose of DL Technique |
|---|---|---|---|---|
| Chen et al. [142] | GAN | NBA SportVu | Basketball | Development of realistic defensive plays conditioned on the ball and offensive term movements |
| Chung et al. [143] | GAN | STATS SportVu | Basketball | Simulation of offensive tactic sketched by coaches |
| Baccouche et al. [144] | LSTM + RNN | MICC-Soccer-Actions-4 dataset | Football | Classifying four football actions |
| Theagarajan et al. [145] | CNN | 3 different soccer matches | Football | Generation of sports highlights |
| Le et al. [146] | RNN | STATS | Football | Ghost modeling in football. |
| Kautz et al. [147] | DCNN | Video Recordings from GoPro Hero 3 action camera | Volleyball | Activity recognition in volleyball |
| Qiao et al. [148] | DCNN + LSTM | Self-built video dataset | Table Tennis | Recognition and tracking of table tennis’s real-time trajectories in complex environments |
| Cao et al. [149] | Tiny YOLOv2 | Self-generated shuttlecock detection dataset | Badminton | Precise and detection of the shuttlecock with badminton robot |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Latif, S.; Driss, M.; Boulila, W.; Huma, Z.e.; Jamal, S.S.; Idrees, Z.; Ahmad, J. Deep Learning for the Industrial Internet of Things (IIoT): A Comprehensive Survey of Techniques, Implementation Frameworks, Potential Applications, and Future Directions. Sensors 2021, 21, 7518. https://doi.org/10.3390/s21227518
Latif S, Driss M, Boulila W, Huma Ze, Jamal SS, Idrees Z, Ahmad J. Deep Learning for the Industrial Internet of Things (IIoT): A Comprehensive Survey of Techniques, Implementation Frameworks, Potential Applications, and Future Directions. Sensors. 2021; 21(22):7518. https://doi.org/10.3390/s21227518
Chicago/Turabian StyleLatif, Shahid, Maha Driss, Wadii Boulila, Zil e Huma, Sajjad Shaukat Jamal, Zeba Idrees, and Jawad Ahmad. 2021. "Deep Learning for the Industrial Internet of Things (IIoT): A Comprehensive Survey of Techniques, Implementation Frameworks, Potential Applications, and Future Directions" Sensors 21, no. 22: 7518. https://doi.org/10.3390/s21227518
APA StyleLatif, S., Driss, M., Boulila, W., Huma, Z. e., Jamal, S. S., Idrees, Z., & Ahmad, J. (2021). Deep Learning for the Industrial Internet of Things (IIoT): A Comprehensive Survey of Techniques, Implementation Frameworks, Potential Applications, and Future Directions. Sensors, 21(22), 7518. https://doi.org/10.3390/s21227518









