Examining the Performance of Fog-Aided, Cloud-Centered IoT in a Real-World Environment
Abstract
:1. Introduction
- Low latency: The amount of time it takes for data to send from source to destination is known as network latency. In cloud-based IoT environments, latency is typically high due to the distance between the IoT devices and the cloud. This increases the cloud response time, especially as the number of IoT devices increases, making the cloud unable to support the real-time demands of IoT devices. Fog computing decreases the latency by moving data to the edge of the network and nearer to end users to meet the high processing demands;
- Higher scalability: The ability of a system to manage an increasing quantity of work by adding resources to the system is known as scalability. In cloud-based IoT environments, as the number of IoT devices increases, it becomes challenging for the cloud to accommodate the heavy computation and bandwidth demands of the devices. When the number of IoT devices grows, fog computing can solve this problem by distributing several fog nodes, which can reduce the heavy computation demands on the cloud and provide hierarchal scalability;
- Location awareness: The ability of a device to determine its location, either passively or actively, is referred to as location awareness. This feature is important because it allows applications to provide services better suited to the user and device location, thereby lowering latency;
- Mobility: Computing mobility is the ability to perform computing operations while a connected device is able to move, communicating from any location through a wireless channel. This includes the mobility of IoT nodes as well as fog nodes in cloud-based IoT environments;
- Decentralized architecture: A decentralized network is a network of interconnected devices in which no single entity is the sole authority. Workloads in distributed architectures are distributed among several machines instead of relying on a single central server. This is an important feature of fog computing because applications and services on the fog can process and store data from any end devices, whether it is a fog node or a sensor (i.e., IoT node);
- Heterogeneity: Heterogeneity in networking refers to connecting devices made by different manufacturers running different operating systems using multiple network architectures and protocols. Fog computing heterogeneity is a topological feature that is of particular importance in cloud-based IoT environments, as it enables devices to exchange information, meaning the exchanged information can be used without restrictions;
- Bandwidth optimization: Optimization of the network bandwidth refers to the overall inbound and outbound bandwidth improvements in a network. This allows fog nodes to handle the traffic from billions of devices to prevent congestion and latency problems. This is due to the fact that the massive amounts of data collected by IoT devices may be processed locally rather than being sent to the cloud.
- We present two cloud-based IoT environment architectures. The first architecture has a fog layer applied between the IoT devices and the cloud, whereas the second architecture publishes the data directly to the cloud without a fog layer;
- We use two benchmarks to measure the performance of the cloud-based IoT architectures. The first benchmark involves Mosquitto message broker metrics, which are used to measure the performance of the IoT–fog–cloud at the fog computing level. The second benchmark involves AWS message broker metrics, which are used to measure the performance of the two architectures (IoT–cloud and IoT–fog–cloud) to show the impact of the additional middle layer (i.e., the fog layer) on cloud-centered IoT environments;
- We discuss the security and privacy implications of the two architectures presented in this paper, showing what triggers these implications and suggesting methods to address them;
- This study serves as a tutorial reference for fundamental fog computing concepts and aims to walk practitioners through different implementation frameworks for fog-aided IoT and to reveal tradeoffs that inform when to use each implementation based on one’s objectives.
2. Background
- MQTT is a lightweight many-to-many communication protocol for IoT that is designed to be a publish–subscribe messaging transport protocol. MQTT is ideal for connecting remote devices with minimal memory consumption and network bandwidth. MQTT is used in a wide variety of domains, such as in industry, health care, and transportation. Port 1883 is the default MQTT port, whereas port 8883 is the default MQTT port over TLS (i.e., secure-mqtt), both of which are registered with the Internet Assigned Numbers Authority (IANA) for Secure MQTT;
- Constrained Application Protocol (CoAp) is a one-to-one User Datagram Protocol (UDP) protocol for transferring state information between the client and server. Despite its ability to preserve resources, CoAP is best-suited to a state transfer model. Since CoAp uses UDP, it does not guarantee the delivery of datagrams. In addition, CoAp is unencrypted. The default CoAP port registered at IANA is 5683;
- Extensible Messaging and Presence Protocol (XMPP) is a secure and near-real-time communication protocol for message-oriented middleware based on XML that enables the exchange of structured but extensible data between any two or more devices over a network. XMPP is mainly used by instant messaging applications such as WhatsApp [16] and Telegram [17]. XMPP offers persistent decentralized connection between devices. As such, no central XMPP servers are needed to communicate; however, to establish a connection between two devices, one of the devices is considered an xmpp-client and communicates over port 5222, while the other is considered an xmpp-server and uses port 5269. XMPP can also use port 5280 for two-way communication. This is called xmpp-bosh, meaning Bidirectional Streams Over Synchronous HTTP (BOSH). XMPP has been used in the literature to network IoT devices, such as in [18,19]. Despite its features and potential, XMPP has some limitations. First, XMPP does not have a Quality of Service (QoS) mechanism. In addition, XMPP streams data in XML format, which introduces overhead due to the text-based communication. These reasons, among others, make MQTT a more popular protocol for IoT, since it has a mechanism for QoS and uses lightweight binary-based communication;
- MQTT For Sensor Networks (MQTT-SN) [20] is considered a modified version of MQTT that is adapted to the attributes of a wireless connection, such as a lossy wireless network. It is designed specifically for wireless sensor networks with scale in mind. MQTT-SN was developed to support non-TCP networks such as UDP. This is another advantage because it makes the communication lighter by eliminating the TCP handshakes;
- The Advanced Message Queuing Protocol [21] (AMQP) is an open standard application layer protocol for middleware. AMQP is designed with more advanced features that introduce more overhead than when using MQTT. These features include message orientation, queuing, routing, reliability, and security. The registered port number for AMQP at IANA is 5672, while for AMQPS (i.e., TLS/SSL encrypted AMQP) it is 5671. For more information on which protocols function best for IoT networks based on the messaging requirements, see [21].
3. Related Works
4. Experiment Setup
4.1. Hardware
4.1.1. First Architecture
4.1.2. Second Architecture
4.2. Software
4.2.1. First Architecture
| Algorithm 1. Gather data generated from the IoT device and forward it to the fog node. First architecture/*. This algorithm authenticates the IoT device to the fog device, generates temperature and humidity data via DHT11 sensors, and publishes them to the Mosquitto MQTT broker on the fog device |
| 1: Define the Type of DHT Sensor, which is DHT11 2: Define the Input/Output Pins of the Raspberry Pi to which the DHT11 is Connected 3: Define an Object of the Sensor with Two Arguments: DHT Pin and DHT Type 4: Define the Name of the Network 5: Define the Password of the Network 6: Define the Variable of MQTT Broker 7: Define only Two Variables of Humidity Topic and Temperature Topic for each IoT Device (DHT11 + Raspberry Pi) in Each Experiment 8: Create Two Instances of Clients, One used to Connect to the Internet and the other used to Connect to the MQTT Broker 9: Run MQTT Connection, Setup, Loop 10: Function: MQTT Connection 11: Connect to Internet 12: If (the Connection is Established) then 13: Print “Connected” 14: Connect to MQTT Broker on Fog Device 15: Else (the Connection isn’t Established) then 16: Try Reconnecting to Internet 17: Function: Setup 18: Start a Serial Communication at 9600 Board Rates 19: Initialize the DHT11 Sensor 20: While (MQTT Connection is True): 21: Read Humidity 22: Read Temperature 23: Print Humidity 24: Print Temperature 25: Publish Humidity Topic with Its Read Value to MQTT Broker on Fog Device 26: Publish Temperature Topic with Its Read Value to MQTT Broker on Fog Device 27: End while |
- Bridging
| Algorithm 2. Bridge every message received from the IoT devices based on the topics of the messages to the AWS broker on the cloud/*. This algorithm authenticates the IoT device to the MQTT broker on the fog device, bridges to the data received from the sensors via the MQTT broker, filters them based on topics, authenticates to the AWS via certificates, and then publishes the filtered data to the AWS IoT core service |
| 1: Define the Variable of the Endpoint of Amazon Web Service with Port Number 8883 2: Determine which Topics of the Messages to Bridge to AWS 3: Define the Version of the Protocol to be used between the MQTT Broker and the AWS Broker 4: Create One Instance of the Client to be used Over the MQTT Protocol 5: Define the Name of the Bridge Connection 6: Start Connection 7: Configure the Bridge using SSL/TLS Support 8: Define Bridge_Cafile to Hold the Path of Amazon Root CA Certificate 9: Define Bridge_Certfile to Hold the Path of Amazon Certificate 10: Define Bridge_Keyfile to Hold the Path of Private Key |
- Python Script
| Algorithm 3. Receive data from the IoT devices and forward it to the cloud/*. This algorithm authenticates the IoT device to the MQTT broker on the fog device, subscribes to the data received from the sensors via the MQTT broker, filters the data based on topics, authenticates to the AWS via certificates, and then publishes the filtered data to the AWS IoT core service |
| 1: Define Two Variables (Humidity Topic and Temperature Topic) for each IoT Device in Each Experiment 2: Define the Variables of MQTT Broker and MQTT Port 3: Create Two Instances of Clients, one used for the MQTT Broker and the other used for the AWS Broker 4: Connect the First Client to the MQTT Broker using the IP Address of the Fog Device and MQTT Port 5: Create a Loop_Start () Method to Start a New Thread for the First Client 6: Set the Transport Layer Security (TLS) for the Second Client using the Three Paths of AWS Certificates and the Current Version of MQTT Protocol 7: Connect the Second client to AWS Broker using AWS Endpoint and AWS Port 8: Create a Loop_Start () Method to Start a New Thread for the Second Client 9: While True do 10: Define a Connection Function 11: Subscribe for All Topics in each IoT Device 12: Print “Connected” when the Connection is Established 13: Print “Error” when the Connection is Disconnected 14: Define a Message Function 15: Get Topic of The Message 16: Get Payload of the Message 17: Print Topic of the Message 18: Print Payload of the Message 19: Publish Topic and Payload of the Message to AWS Cloud 20: Make the First Client Execute the Two Functions: (1) Connection, and (2) Message 21: Make the Second Client Execute the Message Function to Publish the Recovered Data to AWS Cloud 22: End while |
4.2.2. Second Architecture
| Algorithm 4. Gather data generated from the IoT device and forward it to the cloud—Second architecture/*. This algorithm authenticates the IoT device to the AWS cloud via certificates, generates temperature and humidity data via the DHT11 sensors, and publishes them to the AWS cloud |
| 1: Define the Type of DHT Sensor, which is DHT11 2: Define the Input/Output Pins of the Raspberry Pi to which the DHT11 is Connected 3: Define an Object of the Sensor with Two Arguments, DHT Pin and DHT Type 4: Define the Name of the Network 5: Define the Password of the Network 6: Define the Variable of Endpoint of Amazon Web Service 7: Define only Two Variables (Humidity Topic and Temperature Topic) for each IoT Device (DHT11 + Raspberry Pi) in Each Experiment 8: Create a client to Connect to AWS using AWS Endpoint and Port Number 8883 9: Run Connection, Setup, Loop 10: Function: Connection 11: Connect to Internet 12: If (the Connection is Established) then 13: Print “Connected” 14: Else (the Connection isn’t Established) then 15: Try Reconnecting to Internet 16: Function: Setup 17: Start a Serial Communication at 9600 Board Rates 18: Initialize the DHT11 Sensor 19: Run a Connection Function 20: Convert the AWS Certificates to der Format 21: Open Certificate 22: If (Certificate is Existing) 23: Load Certificate 24: Else 25: Print “Certificate is not Existing” 26: Open Amazon Root CA Certificate 27: If (Amazon Root CA Certificate is Existing) 28: Load Amazon Root CA Certificate 29: Else 30: Print “Amazon Root CA Certificate is not Existing” 31: Open Private Key 32: If (Private Key is Existing) 33: Load Private Key 34: Else 35: Print “Private Key is Not Existing” 36: While (Connection is True): 37: Read Humidity 38: Read Temperature 39: Print Humidity 40: Print Temperature 41: Publish Humidity Topic with its Read Value to MQTT Broker on Fog Device 42: Publish Temperature Topic with its Read Value to MQTT Broker on Fog Device 43: End while |
| Algorithm 5. Monitoring script on fog device/*. This algorithm connects to the MQTT broker, subscribes to SYS-Topics via the MQTT broker to monitor and provide benchmark metrics of the Mosquitto broker, and publishes the results based on these metrics |
| 1: Create One Instance of Clients to Connect to Mosquitto Broker 2: Connect the Client to MQTT Broker using the IP Address of Fog Device and MQTT Port 3: Define a Connection Function 4: Print “Connected” when the Connection is Established 5: Print “Error” when the Connection is Disconnected 6: Subscribe To $SYS/# Topics to Monitor the Mosquito MQTT Broker (Print the Metrics Results Of Mosquitto Broker On Fog Device 7: Make the Client Execute the Connection Function 8: Create a Loop Forever () Method for the Client to Remain Monitoring the Mosquitto |
5. Descriptions of Metrics
5.1. Cloud Layer: AWS IoT Metrics
- Connect Success: This metric is used to collect the number of successful connections from our IoT nodes or fog nodes to the AWS message broker.
- Ping Success: This metric is used to collect the number of ping messages received by the AWS message broker. These ping messages are received from the fog node(s) in the first architecture and from the IoT node(s) in the second architecture.
- PublishIn Success: This metric is used to collect the number of publish requests successfully processed by the AWS message broker. As with the ping messages, these messages are received from the fog node(s) in the first architecture and from the IoT node(s) in the second architecture.
- PublishOut Success: This metric is used to collect the number of publish requests successfully made by the AWS message broker to the fog nodes in the first architecture and to the IoT nodes in the second architecture.
- Subscribe Success: This metric is used to collect the number of successful subscribe requests processed by the AWS message broker. These requests are made by the fog node in the first architecture and made directly by the IoT devices in the second architecture.
- PublishIn Clienterror: This metric is used to collect the number of publish requests rejected because they did not meet the AWS IoT requirements.
- Unsubscribe Success: This metric is used to collect the number of unsubscribe requests that were successfully processed by the AWS message broker. These unsubscribe requests are made by the fog node in the first architecture and made directly by the IoT devices in the second architecture.
- Throttle Exceeded: This metric is used to collect the number of requests that have been throttled because the client (i.e., the IoT node or fog node) has sent too many messages and exceeded the allowed message rate.
- PublishOut Throttle: This metric is used to collect the number of publish requests that have been throttled because the client (i.e., IoT node or fog node) has exceeded the allowed message rate.
5.2. Fog Layer: Eclipse Mosquitto Broker Metrics
- $SYS/broker/uptime: This metric is used to measure the amount of time in seconds the broker has been online.
- $SYS/broker/load/messages/received: This metric is used to measure the moving average of the number of all types of MQTT messages received by the broker over different time intervals.
- $SYS/broker/load/messages/sent: This metric is used to measure the moving average of the number of all types of MQTT messages sent by the broker over different time intervals.
- $SYS/broker/load/publish/received: This metric is used to measure the moving average of the number of publish messages received by the broker over different time intervals.
- $SYS/broker/load/publish/sent: This metric is used to measure the moving average of the number of publish messages sent by the broker over different time intervals.
- $SYS/broker/load/bytes/received: This metric is used to measure the moving average of the number of bytes received by the broker over different time intervals.
- $SYS/broker/load/bytes/sent: This metric is used to measure the moving average of the number of bytes sent by the broker over different time intervals.
- $SYS/broker/load/sockets: This metric is used to measure the moving average of the number of socket connections opened to the broker over different time intervals.
- $SYS/broker/load/connections: This metric is used to measure the moving average of the number of CONNECT packets received by the broker over different time intervals.
- $SYS/broker/messages/stored: This metric is used to measure the number of messages currently held in the message store. This includes retained messages and messages queued for durable clients.
- $SYS/broker/store/messages/bytes: This metric is used to measure the number of bytes currently held by message payloads in the message store. This includes retained messages and messages queued for durable clients.
- $SYS/broker/subscriptions/count: This metric is used to measure the total number of subscriptions active on the broker.
- $SYS/broker/heap/current: This metric is used to measure the current size of the heap memory in use by Mosquitto.
- $SYS/broker/messages/received: This metric is used to measure the total number of messages of any type received since the broker started.
- $SYS/broker/messages/sent: This metric is used to measure the total number of messages of any type sent since the broker started.
- $SYS/broker/publish/messages/received: This metric is used to measure the total number of PUBLISH messages received since the broker started.
- $SYS/broker/publish/messages/sent: This metric is used to measure the total number of PUBLISH messages sent since the broker started.
- $SYS/broker/bytes/received: This metric is used to measure the total number of bytes received since the broker started.
- $SYS/broker/bytes/sent: This metric is used to measure the total number of bytes sent since the broker started.
- $SYS/broker/publish/bytes/received: This metric is used to measure the total number of PUBLISH bytes received since the broker started.
- $SYS/broker/publish/bytes/sent: This metric is used to measure the total number of PUBLISH bytes sent since the broker started.
6. Analysis Methods
6.1. Architecture 1 vs. Architecture 2
6.2. Architecture 1 Implementation: Python Script vs. Bridging
6.3. Architecture 1 Measurement: Mosquitto Metrics vs. AWS Metrics
7. Results and Description of Experiments
7.1. Descriptions of the Three Experiments on the First Architecture with One, Two, or Three IoT Devices Using AWS Benchmark Metrics (Cloud Layer)
7.2. Descriptions of the Three Experiments on the Second Architecture with One, Two, or Three IoT Devices Using AWS Benchmark Metrics (Cloud Layer)
7.3. Descriptions of the Three Experiments on the First Architecture with One, Two, or Three IoT Devices Using Mosquitto Benchmark Metrics (Fog Layer)
8. Evaluation of Results
8.1. First Architecture vs. Second Architecture
8.2. Architecture 1 Implementation: Python Script vs. Bridging
8.3. Architecture 1 Measurement: Mosquitto Metrics vs. AWS Metrics
9. Threats to Validity
10. Discussion and Limitations
11. Conclusions and Future Works
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Aleisa, M.A.; Abuhussein, A.; Sheldon, F.T. Access Control in Fog Computing: Challenges and Research Agenda. IEEE Access 2020, 8, 83986–83999. [Google Scholar] [CrossRef]
- Aleisa, M.; Hussein, A.A.; Alsubaei, F.; Sheldon, F.T. Performance Analysis of Two Cloud-Based IoT Implementations: Empirical Study. In Proceedings of the 2020 7th IEEE International Conference on Cyber Security and Cloud Computing (CSCloud)/2020 6th IEEE International Conference on Edge Computing and Scalable Cloud (EdgeCom), New York, NY, USA, 1–3 August 2020; IEEE: New York, NY, USA, 2020; pp. 276–280. [Google Scholar]
- F.Computing. Fog Computing and the Internet of Things: Extend the Cloud to Where the Things Are. 2015. Available online: https://www.cisco.com/c/dam/en_us/solutions/trends/iot/docs/computing-overview.pdf (accessed on 9 October 2021).
- Ni, J.; Zhang, K.; Lin, X.; Shen, X. Securing Fog Computing for Internet of Things Applications: Challenges and Solutions. IEEE Commun. Surv. Tutor. 2018, 20, 601–628. [Google Scholar] [CrossRef]
- What Is an IoT Platform & What Role Does It Play In Your Business? Available online: /content/attbusiness/en/learn/research-reports/whats-an-iot-platform-and-what-role-does-it-play.html (accessed on 13 February 2021).
- AWS IoT Core Overview—Amazon Web Services. Available online: https://aws.amazon.com/iot-core/ (accessed on 13 February 2021).
- Azure IoT—Internet of Things Platform|Microsoft Azure. Available online: https://azure.microsoft.com/en-us/overview/iot/ (accessed on 13 February 2021).
- Internet of Things|IBM. Available online: https://www.ibm.com/cloud/internet-of-things (accessed on 13 February 2021).
- Cloud IoT Core. Available online: https://cloud.google.com/iot-core (accessed on 13 February 2021).
- Home|IoTivity. Available online: https://iotivity.org/ (accessed on 13 February 2021).
- Zetta—An API-First Internet of Things (IoT) Platform—Free and Open Source Software. Available online: https://www.zettajs.org/ (accessed on 13 February 2021).
- What Is Arduino? Available online: https://www.arduino.cc/en/Guide/Introduction (accessed on 13 February 2021).
- DeviceHive—Open Source IoT Data Platform with the Wide Range of Integration Options. Available online: https://devicehive.com/ (accessed on 13 February 2021).
- OpenRemote|The 100% Open Source IoT Platform. Available online: https://openremote.io/ (accessed on 13 February 2021).
- Alsubaei, F.; Abuhussein, A.; Shiva, S. An Overview of Enabling Technologies for the Internet of Things. In Internet of Things A to Z; John Wiley & Sons, Ltd.: Hoboken, NJ, USA, 2018; pp. 77–112. ISBN 978-1-119-45673-5. [Google Scholar]
- WhatsApp. Available online: https://www.whatsapp.com/?lang=en (accessed on 13 February 2021).
- Telegram—A New Era of Messaging. Available online: https://telegram.org/?setln=en (accessed on 14 February 2021).
- Wang, H.; Xiong, D.; Wang, P.; Liu, Y. A Lightweight XMPP Publish/Subscribe Scheme for Resource-Constrained IoT Devices. IEEE Access 2017, 5, 16393–16405. [Google Scholar] [CrossRef]
- Bendel, S.; Springer, T.; Schuster, D.; Schill, A.; Ackermann, R.; Ameling, M. A Service Infrastructure for the Internet of Things Based on XMPP. In Proceedings of the 2013 IEEE International Conference on Pervasive Computing and Communications Workshops (PERCOM Workshops), Kassel, Germany, 18–22 March 2013; IEEE: San Diego, CA, USA, 2013; pp. 385–388. [Google Scholar]
- Stanford-Clark, A.; Truong, H.L. MQTT For Sensor Networks (MQTT-SN) Protocol Specification. 2013. Available online: https://www.oasis-open.org/committees/download.php/66091/MQTT-SN_spec_v1.2.pdf (accessed on 9 October 2021).
- Naik, N. Choice of Effective Messaging Protocols for IoT Systems: MQTT, CoAP, AMQP and HTTP. In Proceedings of the 2017 IEEE International Systems Engineering Symposium (ISSE), Vienna, Austria, 11–13 October 2017; pp. 1–7. [Google Scholar]
- AWS IoT—Amazon Web Services. Available online: https://aws.amazon.com/iot/ (accessed on 20 November 2020).
- Amazon Web Services, Inc. AWS IoT—Developer Guide. 2020. Available online: https://docs.aws.amazon.com/iot/latest/developerguide/iot-dg.pdf (accessed on 15 May 2020).
- Amazon Web Services, Inc. Amazon CloudWatch—User Guide. 2020. Available online: https://docs.aws.amazon.com/AmazonCloudWatch/latest/monitoring/acw-ug.pdf (accessed on 15 May 2020).
- Eclipse Mosquitto. Available online: https://mosquitto.org/ (accessed on 20 November 2020).
- Messaging That Just Works—RabbitMQ. Available online: https://www.rabbitmq.com/ (accessed on 13 February 2021).
- ActiveMQ. Available online: https://activemq.apache.org/ (accessed on 13 February 2021).
- Mosquitto Man Page. Available online: https://mosquitto.org/man/mosquitto-8.html (accessed on 21 November 2020).
- SPEC—Standard Performance Evaluation Corporation. Available online: https://www.spec.org/ (accessed on 9 September 2021).
- TPC-Homepage. Available online: http://www.tpc.org/ (accessed on 9 September 2021).
- Transaction Processing Performance Council (TPC). TPC Express Benchmark IoT (TPCx-IoT) Standard Specification Version 2.0.0. 2021. Available online: http://tpc.org/tpc_documents_current_versions/pdf/tpcx-iot_v2.0.0.pdf (accessed on 15 May 2020).
- Poess, M.; Nambiar, R.; Kulkarni, K.; Narasimhadevara, C.; Rabl, T.; Jacobsen, H.-A. Analysis of TPCx-IoT: The First Industry Standard Benchmark for IoT Gateway Systems. In Proceedings of the 2018 IEEE 34th International Conference on Data Engineering (ICDE), Paris, France, 16–19 April 2018; IEEE: Paris, France, 2018; pp. 1519–1530. [Google Scholar]
- Arlitt, M.; Marwah, M.; Bellala, G.; Shah, A.; Healey, J.; Vandiver, B. IoTAbench: An Internet of Things Analytics Benchmark. In Proceedings of the 6th ACM/SPEC International Conference on Performance Engineering—ICPE ’15, Austin, TX, USA, 31 January–4 February 2015; ACM Press: Austin, TX, USA, 2015; pp. 133–144. [Google Scholar]
- Vanneback, E. Using the Mosquitto Implementation in an Embedded Environment; Umea University: Umeå, Sweden, 2018; pp. 1–39. [Google Scholar]
- Maksuti, S.; Schluga, O.; Settanni, G.; Tauber, M.; Delsing, J. Self-Adaptation Applied to MQTT via a Generic Autonomic Management Framework. In Proceedings of the 2019 IEEE International Conference on Industrial Technology (ICIT), Melbourne, Australia, 13–15 February 2019; IEEE: Melbourne, Australia, 2019; pp. 1179–1185. [Google Scholar]
- Ismail, A.A.; Hamza, H.S.; Kotb, A.M. Performance Evaluation of Open Source IoT Platforms. In Proceedings of the 2018 IEEE Global Conference on Internet of Things (GCIoT), Alexandria, Egypt, 5–7 December 2018; IEEE: Alexandria, Egypt, 2018; pp. 1–5. [Google Scholar]
- Lee, S.; Kim, H.; Hong, D.K.; Ju, H. Correlation Analysis of MQTT Loss and Delay According to QoS Level. In Proceedings of the International Conference on Information Networking 2013 (ICOIN), Bangkok, Thailand, 28–30 January 2013; IEEE: Bangkok, Thailand, 2013; pp. 714–717. [Google Scholar]
- Aazam, M.; Zeadally, S.; Harras, K.A. Fog Computing Architecture, Evaluation, and Future Research Directions. IEEE Commun. Mag. 2018, 56, 46–52. [Google Scholar] [CrossRef]
- Alsubaei, F.; Abuhussein, A.; Shandilya, V.; Shiva, S. IoMT-SAF: Internet of Medical Things Security Assessment Framework. Internet Things 2019, 8, 100123. [Google Scholar] [CrossRef]
- El Kafhali, S.; Salah, K.; Ben Alla, S. Performance Evaluation of IoT-Fog-Cloud Deployment for Healthcare Services. In Proceedings of the 2018 4th International Conference on Cloud Computing Technologies and Applications (Cloudtech), Brussels, Belgium, 26–28 November 2018; pp. 1–6. [Google Scholar]
- Vilela, P.H.; Rodrigues, J.J.P.C.; Solic, P.; Saleem, K.; Furtado, V. Performance Evaluation of a Fog-Assisted IoT Solution for e-Health Applications. Future Gener. Comput. Syst. 2019, 97, 379–386. [Google Scholar] [CrossRef]
- Das, A.; Patterson, S.; Wittie, M. EdgeBench: Benchmarking Edge Computing Platforms. In Proceedings of the 2018 IEEE/ACM International Conference on Utility and Cloud Computing Companion (UCC Companion), Zurich, Switzerland, 17–20 December 2018; IEEE: Zurich, Switzerland, 2018; pp. 175–180. [Google Scholar]
- McChesney, J.; Wang, N.; Tanwer, A.; de Lara, E.; Varghese, B. DeFog: Fog Computing Benchmarks. In Proceedings of the 4th ACM/IEEE Symposium on Edge Computing, New York, NY, USA, 7 November 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 47–58. [Google Scholar]
- Industries, A. DHT11 Basic Temperature-Humidity Sensor + Extras. Available online: https://www.adafruit.com/product/386 (accessed on 20 November 2020).
- Foundation, T.R.P. Buy a Raspberry Pi 3 Model B. Available online: https://www.raspberrypi.org/products/raspberry-pi-3-model-b/?resellerType=home (accessed on 20 November 2020).
- Software. Available online: https://www.arduino.cc/en/software (accessed on 13 February 2021).
- How to Bridge Mosquitto MQTT Broker to AWS IoT. Available online: https://aws.amazon.com/blogs/iot/how-to-bridge-mosquitto-mqtt-broker-to-aws-iot/ (accessed on 13 February 2021).
- Birje, M.N.; Bulla, C. Commercial and Open Source Cloud Monitoring Tools: A Review. In Advances in Decision Sciences, Image Processing, Security and Computer Vision; Satapathy, S.C., Raju, K.S., Shyamala, K., Krishna, D.R., Favorskaya, M.N., Eds.; Springer International Publishing: Cham, Swizerland, 2020; Volume 3, pp. 480–490. ISBN 978-3-030-24321-0. [Google Scholar]
- Aslanpour, M.S.; Gill, S.S.; Toosi, A.N. Performance Evaluation Metrics for Cloud, Fog and Edge Computing: A Review, Taxonomy, Benchmarks and Standards for Future Research. Internet Things 2020, 12, 100273. [Google Scholar] [CrossRef]
- Stephen, A.; Benedict, S.; Kumar, R.P.A. Monitoring IaaS Using Various Cloud Monitors. Clust. Comput. 2019, 22, 12459–12471. [Google Scholar] [CrossRef]
- Jutadhamakorn, P.; Pillavas, T.; Visoottiviseth, V.; Takano, R.; Haga, J.; Kobayashi, D. A Scalable and Low-Cost MQTT Broker Clustering System. Int. Conf. Inf. Technol. 2017, 5, 1–5. [Google Scholar]
- Peng, K.; Huang, H.; Wan, S.; Leung, V.C.M. End-Edge-Cloud Collaborative Computation Offloading for Multiple Mobile Users in Heterogeneous Edge-Server Environment. Wirel. Netw. 2020, 1–12. [Google Scholar] [CrossRef]


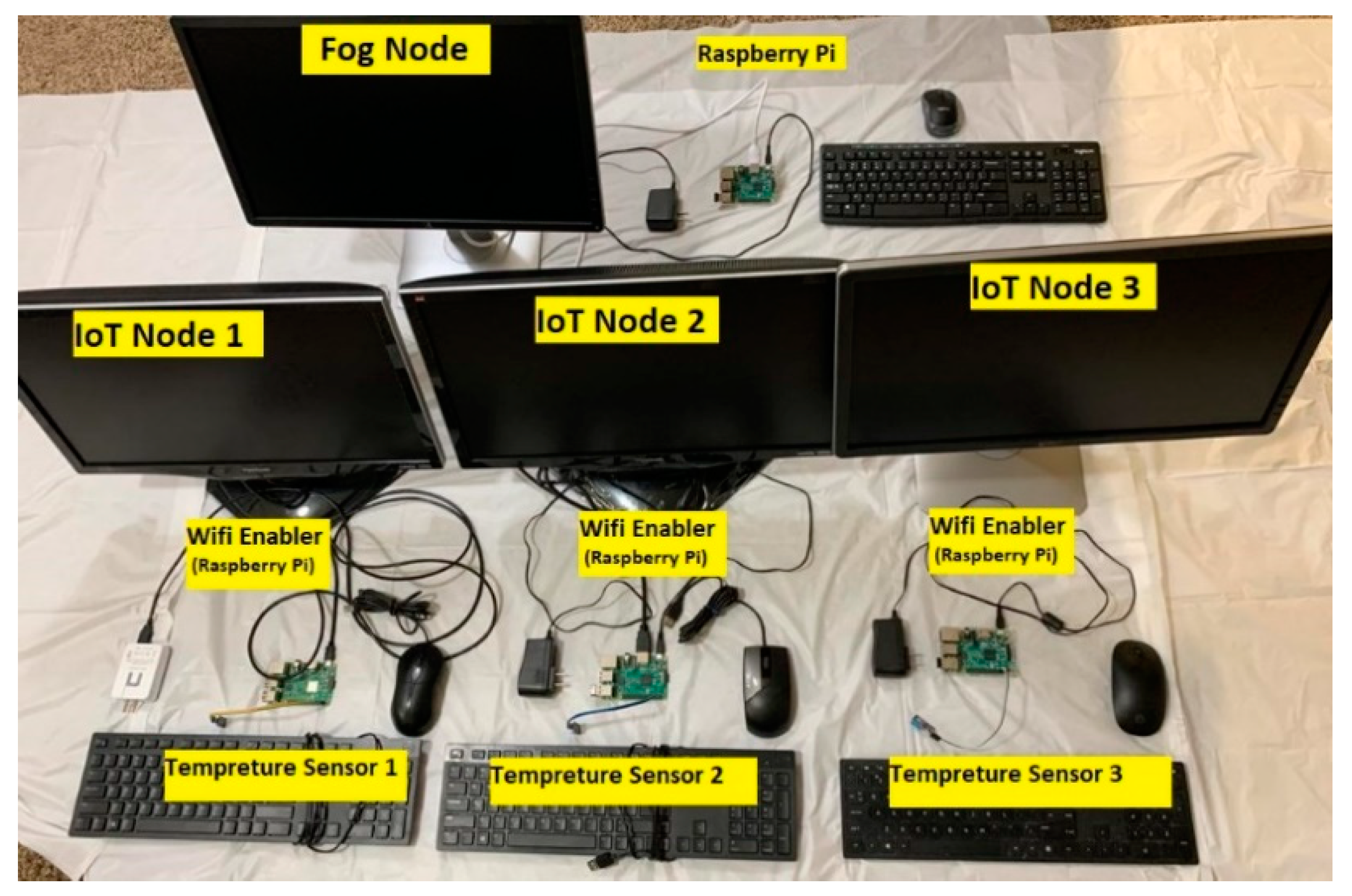












| Equipment Name | Equipment Type | Quantity | Purpose |
|---|---|---|---|
| DHT11 | Temperature-Humidity Sensor | 3 | Generate Real Life Data |
| Raspberry Pi | Version 3 Model B | 4 | Enable WiFi and Provide Huge Processing Power and Storage |
| Micro SD Card | 32GB ImageMate Plus 130 MB/s Read | 4 | Initial Storage for The Operating System and Files |
| Monitor | HP | 4 | Provide a Visual Display |
| Keyboard and Mouse | HP | 4 | Useful for Working on a Raspberry Pi |
| Power Supply/Adapter | CanaKit | 4 | Supply the Power for the Raspberry Pi |
| HDMI Cable | onn | 4 | Connect the Raspberry Pi to a Monitor |
| AWS IoT Message Broker Metrics on N. Virginia Datacenter (Cloud Layer) Using Bridge—First Architecture | AWS IoT Message Broker Metrics on N. Virginia Datacenter (Cloud Layer)—Second Architecture | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Number of IoT Devices | 1 | Number of IoT Devices | 1 | ||||||||
| Number of subscribing and Publishing | 2 | Number of Subscribing and Publishing | 2 | ||||||||
| AWS IoT Metrics in Minutes (m) | 0.5 | 1 | 5 | 15 | 60 | AWS IoT Metrics in Minutes (m) | 0.5 | 1 | 5 | 15 | 60 |
| Connect Success | 2 | 2 | 2 | 2 | 2 | Connect Success | 2 | 2 | 2 | 2 | 2 |
| Ping Success | 2 | 2 | 8 | 29 | 120 | Ping Success | 5 | 5 | 25 | 75 | 297 |
| PublishIn Success | 44 | 44 | 206 | 586 | 2360 | PublishIn Success | 60 | 60 | 300 | 900 | 3580 |
| PublishOut Success | 44 | 44 | 206 | 586 | 2360 | PublishOut Success | 60 | 60 | 300 | 900 | 3580 |
| Subscribe Success | 2 | 2 | 2 | 2 | 2 | Subscribe Success | 2 | 2 | 2 | 2 | 2 |
| Unsubscribe Success | 2 | 2 | 2 | 2 | 2 | Unsubscribe Success | 2 | 2 | 2 | 2 | 2 |
| AWS IoT Message Broker Metrics on N. Virginia Datacenter (Cloud Layer) using Bridge—First Architecture | AWS IoT Message Broker Metrics on N. Virginia Datacenter (Cloud Layer)—Second Architecture | ||||||||||
| Number of IoT Devices | 2 | Number of IoT Devices | 2 | ||||||||
| Number of Subscribing and Publishing | 4 | Number of Subscribing and Publishing | 4 | ||||||||
| AWS IoT Metrics in Minutes | 0.5 | 1 | 5 | 15 | 60 | AWS IoT Metrics in Minutes | 0.5 | 1 | 5 | 15 | 60 |
| Connect Success | 4 | 4 | 4 | 4 | 4 | Connect Success | 6 | 6 | 35 | 111 | 432 |
| Ping Success | 2 | 2 | 8 | 29 | 120 | Ping Success | 1 | 1 | 8 | 20 | 85 |
| PublishIn Success | 70 | 70 | 350 | 1110 | 4590 | PublishIn Success | 62 | 62 | 322 | 965 | 3850 |
| PublishOut Success | 70 | 70 | 350 | 1110 | 4590 | PublishOut Success | 51 | 51 | 322 | 965 | 3850 |
| Subscribe Success | 4 | 4 | 4 | 4 | 4 | Subscribe Success | 6 | 6 | 35 | 111 | 432 |
| Unsubscribe Success | 4 | 4 | 4 | 4 | 4 | Unsubscribe Success | 4 | 4 | 4 | 4 | 4 |
| AWS IoT Message Broker Metrics on N. Virginia Datacenter (Cloud Layer) using Bridge—First Architecture | AWS IoT Message Broker Metrics on N. Virginia Datacenter (Cloud Layer)—Second Architecture | ||||||||||
| Number of IoT Devices | 3 | Number of IoT Devices | 3 | ||||||||
| Number of Subscribing and Publishing | 6 | Number of Subscribing and Publishing | 6 | ||||||||
| AWS IoT Metrics in Minutes | 0.5 | 1 | 5 | 15 | 60 | AWS IoT Metrics in Minutes | 0.5 | 1 | 5 | 15 | 60 |
| Connect Success | 6 | 6 | 6 | 6 | 6 | Connect Success | 12 | 12 | 76 | 228 | 893 |
| Ping Success | 2 | 2 | 9 | 29 | 119 | Ping Success | 2 | 1 | 5 | 14 | 60 |
| PublishIn Success | 115 | 115 | 548 | 1660 | 6510 | PublishIn Success | 68 | 68 | 359 | 1050 | 4240 |
| PublishOut Success | 115 | 115 | 548 | 1660 | 6510 | PublishOut Success | 58 | 68 | 359 | 1050 | 4240 |
| Subscribe Success | 6 | 6 | 6 | 6 | 6 | Subscribe Success | 12 | 12 | 76 | 228 | 893 |
| Unsubscribe Success | 6 | 6 | 6 | 6 | 6 | Unsubscribe Success | 6 | 6 | 6 | 6 | 6 |
| AWS IoT Message Broker Metrics on N. Virginia Datacenter (Cloud Layer) Using Python Script—First Architecture | AWS IoT Message Broker Metrics on N. Virginia Datacenter (Cloud Layer) Using Bridge—First Architecture | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Number of IoT Devices | 1 | Number of IoT Devices | 1 | ||||||||
| Number of Subscribing and Publishing | 2 | Number of Subscribing and Publishing | 2 | ||||||||
| AWS IoT Metrics in Minutes | 0.5 | 1 | 5 | 15 | 60 | AWS IoT Metrics in Minutes | 0.5 | 1 | 5 | 15 | 60 |
| Connect Success | 2 | 2 | 2 | 2 | 2 | Connect Success | 2 | 2 | 2 | 2 | 2 |
| Ping Success | 2 | 2 | 10 | 30 | 119 | Ping Success | 2 | 2 | 8 | 29 | 120 |
| IoT PublishIn Success | 46 | 46 | 206 | 590 | 2360 | IoT PublishIn Success | 44 | 44 | 206 | 586 | 2360 |
| IoT PublishOut Success | 46 | 46 | 206 | 590 | 2360 | IoT PublishOut Success | 44 | 44 | 206 | 586 | 2360 |
| Subscribe Success | 2 | 2 | 2 | 2 | 2 | Subscribe Success | 2 | 2 | 2 | 2 | 2 |
| IoT Unsubscribe Success | 2 | 2 | 2 | 2 | 2 | IoT Unsubscribe Success | 2 | 2 | 2 | 2 | 2 |
| AWS IoT Message Broker Metrics on N. Virginia Datacenter (Cloud Layer) using Python Script—First Architecture | AWS IoT Message Broker Metrics on N. Virginia Datacenter (Cloud Layer) using Bridge—First Architecture | ||||||||||
| Number of IoT Devices | 2 | Number of IoT Devices | 2 | ||||||||
| Number of Subscribing and Publishing | 4 | Number of Subscribing and Publishing | 4 | ||||||||
| AWS IoT Metrics in Minutes | 0.5 | 1 | 5 | 15 | 60 | AWS IoT Metrics in Minutes | 0.5 | 1 | 5 | 15 | 60 |
| Connect Success | 4 | 4 | 4 | 4 | 4 | Connect Success | 4 | 4 | 4 | 4 | 4 |
| Ping Success | 2 | 2 | 9 | 29 | 118 | Ping Success | 2 | 2 | 8 | 29 | 120 |
| IoT PublishIn Success | 76 | 76 | 359 | 1170 | 4680 | IoT PublishIn Success | 70 | 70 | 350 | 1110 | 4590 |
| IoT PublishOut Success | 76 | 76 | 359 | 1170 | 4680 | IoT PublishOut Success | 70 | 70 | 350 | 1110 | 4590 |
| Subscribe Success | 4 | 4 | 4 | 4 | 4 | Subscribe Success | 4 | 4 | 4 | 4 | 4 |
| IoT Unsubscribe Success | 4 | 4 | 4 | 4 | 4 | IoT Unsubscribe Success | 4 | 4 | 4 | 4 | 4 |
| AWS IoT Message Broker Metrics on N. Virginia Datacenter (Cloud Layer) using Python Script—First Architecture | AWS IoT Message Broker Metrics on N. Virginia Datacenter (Cloud Layer) using Bridge—First Architecture | ||||||||||
| Number of IoT Devices | 3 | Number of IoT Devices | 3 | ||||||||
| Number of Subscribing and Publishing | 6 | Number of Subscribing and Publishing | 6 | ||||||||
| AWS IoT Metrics in Minutes | 0.5 | 1 | 5 | 15 | 60 | AWS IoT Metrics in Minutes | 0.5 | 1 | 5 | 15 | 60 |
| Connect Success | 6 | 6 | 6 | 6 | 6 | Connect Success | 6 | 6 | 6 | 6 | 6 |
| Ping Success | 1 | 2 | 10 | 30 | 118 | Ping Success | 2 | 2 | 9 | 29 | 119 |
| IoT PublishIn Success | 117 | 117 | 534 | 1680 | 6650 | IoT PublishIn Success | 115 | 115 | 548 | 1660 | 6510 |
| IoT PublishOut Success | 117 | 117 | 534 | 1680 | 6650 | IoT PublishOut Success | 115 | 115 | 548 | 1660 | 6510 |
| Subscribe Success | 6 | 6 | 6 | 6 | 6 | Subscribe Success | 6 | 6 | 6 | 6 | 6 |
| IoT Unsubscribe Success | 6 | 6 | 6 | 6 | 6 | IoT Unsubscribe Success | 6 | 6 | 6 | 6 | 6 |
| Number of IoT Devices | One IoT Device | ||||||
|---|---|---|---|---|---|---|---|
| Number of Subscribing and Publishing | Two Subscribing and Two Publishing | ||||||
| Mosquitto Message Broker Metrics as $SYS Topics | 30 (S) | 1 (Min) | 5 (Min) | 15 (Min) | 30 (Min) | 45 (Min) | 1 (H) |
| $SYS/Broker/Load/Messages/Received 1(m) | 25.31 | 36.26 | 27.43 | 46.25 | 47.81 | 25.96 | 44.70 |
| $SYS/Broker/Load/Messages/Sent 1(m) | 137.87 | 177.35 | 179.52 | 215.36 | 199.56 | 188.81 | 213.35 |
| $SYS/Broker/Load/Publish/Received 1(m) | 22.68 | 33.07 | 23.95 | 43.88 | 45.38 | 23.43 | 42.69 |
| $SYS/Broker/Load/Publish/Sent 1(m) | 135.23 | 174.15 | 176.03 | 213.00 | 197.14 | 186.28 | 211.34 |
| $SYS/Broker/Load/Bytes/Received 1(m) | 802.93 | 1135.98 | 849.26 | 1478.98 | 1524.90 | 791.00 | 1439.38 |
| $SYS/Broker/Load/Bytes/Sent 1(m) | 5315.03 | 6898.23 | 7230.76 | 8637.79 | 8029.54 | 7694.46 | 8610.21 |
| $SYS/Broker/Load/Sockets 1(m) | 1.05 | 0.61 | 0.92 | 0.09 | 0.12 | 0.94 | 0.12 |
| $SYS/Broker/Load/Connections 1(m) | 1.05 | 0.61 | 0.92 | 0.09 | 0.12 | 0.94 | 0.12 |
| $SYS/Broker/Subscriptions/Count | 2 | 2 | 2 | 2 | 2 | 2 | 2 |
| $SYS/Broker/Heap/Current | 30,224 | 30,232 | 30,360 | 30,148 | 30,084 | 29,744 | 30,132 |
| $SYS/Broker/Messages/Received | 37 | 65 | 225 | 663 | 1285 | 1885 | 2515 |
| $SYS/Broker/Messages/Sent | 202 | 329 | 1144 | 3250 | 6356 | 9416 | 12,552 |
| $SYS/Broker/Publish/Messages/Received | 32 | 58 | 209 | 625 | 1213 | 1787 | 2375 |
| $SYS/Broker/Publish/Messages/Sent | 197 | 322 | 1128 | 3212 | 6284 | 9310 | 12,412 |
| $SYS/Broker/Bytes/Received | 1154 | 2029 | 7149 | 21,219 | 41,165 | 60374 | 80,633 |
| $SYS/Broker/Bytes/Sent | 7730 | 12,711 | 45,329 | 129,895 | 255,029 | 378,636 | 505,171 |
| $SYS/Broker/Publish/Bytes/Received | 160 | 290 | 1045 | 3125 | 6065 | 8935 | 11,875 |
| $SYS/Broker/Publish/Bytes/Sent | 806 | 1400 | 5505 | 16,551 | 33,192 | 49,748 | 66,818 |
| Number of IoT Devices | Two IoT Devices | ||||||
|---|---|---|---|---|---|---|---|
| Number of Subscribing and Publishing | Four Subscribing and Four Publishing | ||||||
| Mosquitto Message Broker Metrics as $SYS Topics | 30 (S) | 1 (Min) | 5 (Min) | 15 (Min) | 30 (Min) | 45 (Min) | 1 (H) |
| $SYS/Broker/Load/Messages/Received 1(m) | 59.48 | 79.02 | 109.81 | 119.86 | 109.03 | 123.12 | 114.70 |
| $SYS/Broker/Load/Messages/Sent 1(m) | 175.38 | 226.02 | 296.83 | 312.57 | 296.21 | 307.21 | 298.85 |
| $SYS/Broker/Load/Publish/Received 1(m) | 38.21 | 53.18 | 73.62 | 79.78 | 74.34 | 82.05 | 78.49 |
| $SYS/Broker/Load/Publish/Sent 1(m) | 154.11 | 200.18 | 260.63 | 272.49 | 261.52 | 266.13 | 262.63 |
| $SYS/Broker/Load/Bytes/Received 1(m) | 2124.60 | 2767.93 | 3916.20 | 4291.54 | 3854.92 | 4393.78 | 4074.59 |
| $SYS/Broker/Load/Bytes/Sent 1(m) | 5981.40 | 7807.80 | 10,344.23 | 10,803.61 | 10,424.09 | 10,568.27 | 10,457.24 |
| $SYS/Broker/Load/Sockets 1(m) | 19.69 | 23.40 | 33.62 | 37.64 | 32.03 | 38.43 | 34.27 |
| $SYS/Broker/Load/Connections 1(m) | 19.69 | 23.40 | 33.64 | 37.65 | 32.12 | 38.43 | 34.27 |
| $SYS/Broker/Subscriptions/Count | 4 | 4 | 4 | 4 | 4 | 4 | 4 |
| $SYS/Broker/Heap/Current | 30,268 | 30,268 | 30,252 | 30,268 | 30,252 | 30,260 | 30,204 |
| $SYS/Broker/Messages/Received | 84 | 143 | 593 | 1747 | 3433 | 5194 | 6954 |
| $SYS/Broker/Messages/Sent | 253 | 416 | 1632 | 4686 | 9154 | 13,704 | 18,242 |
| $SYS/Broker/Publish/Messages/Received | 53 | 94 | 398 | 1157 | 2283 | 3451 | 4618 |
| $SYS/Broker/Publish/Messages/Sent | 222 | 367 | 1437 | 4096 | 8004 | 11961 | 15906 |
| $SYS/Broker/Bytes/Received | 2976 | 5015 | 21,111 | 62,781 | 123,353 | 186,822 | 250,274 |
| $SYS/Broker/Bytes/Sent | 8609 | 14,285 | 56,570 | 162,328 | 318,376 | 476,257 | 633,619 |
| $SYS/Broker/Publish/Bytes/Received | 265 | 470 | 1990 | 5785 | 11,415 | 17,255 | 23,090 |
| $SYS/Broker/Publish/Bytes/Sent | 942 | 1650 | 7159 | 21,442 | 42,979 | 65,025 | 87076 |
| Number of Iot Devices | Three IoT Devices | ||||||
|---|---|---|---|---|---|---|---|
| Number of Subscribing and Publishing | Six Subscribing and Six Publishing | ||||||
| Mosquitto Message Broker Metrics as $SYS Topics | 30 (S) | 1 (Min) | 5 (Min) | 15 (Min) | 30 (Min) | 45 (Min) | 1 (H) |
| $SYS/Broker/Load/Messages/Received 1(m) | 90.09 | 129.50 | 172.49 | 163.15 | 163.81 | 172.50 | 179.13 |
| $SYS/Broker/Load/Messages/Sent 1(m) | 207.44 | 279.24 | 359.50 | 357.54 | 353.60 | 352.41 | 369.72 |
| $SYS/Broker/Load/Publish/Received 1(m) | 55.43 | 81.41 | 109.62 | 99.23 | 98.21 | 107.07 | 115.52 |
| $SYS/Broker/Load/Publish/Sent 1(m) | 172.78 | 231.14 | 296.63 | 293.61 | 287.99 | 286.97 | 306.10 |
| $SYS/Broker/Load/Bytes/Received 1(m) | 3329.39 | 4744.07 | 6384.79 | 6124.10 | 6170.40 | 6480.58 | 6627.83 |
| $SYS/Broker/Load/Bytes/Sent 1(m) | 6672.01 | 8948.99 | 11,686.44 | 11,697.09 | 11,528.00 | 11,394.30 | 12,088.13 |
| $SYS/Broker/Load/Sockets 1(m) | 33.08 | 45.51 | 60.27 | 61.48 | 63.11 | 63.81 | 61.52 |
| $SYS/Broker/Load/Connections 1(m) | 33.08 | 45.51 | 60.29 | 61.49 | 63.11 | 63.82 | 61.63 |
| $SYS/Broker/Subscriptions/Count | 6 | 6 | 6 | 6 | 6 | 6 | 6 |
| $SYS/Broker/Heap/Current | 30,376 | 30,320 | 30,268 | 30,312 | 30,376 | 30,240 | 30,252 |
| $SYS/Broker/Messages/Received | 129 | 228 | 951 | 2689 | 5310 | 7915 | 10,503 |
| $SYS/Broker/Messages/Sent | 299 | 505 | 1992 | 5639 | 11,077 | 16,495 | 21,823 |
| $SYS/Broker/Publish/Messages/Received | 79 | 142 | 603 | 1699 | 3333 | 4973 | 6612 |
| $SYS/Broker/Publish/Messages/Sent | 249 | 419 | 1644 | 4649 | 9100 | 13,553 | 17,932 |
| $SYS/Broker/Bytes/Received | 4736 | 8349 | 35210 | 100,003 | 197,975 | 295,130 | 391,395 |
| $SYS/Broker/Bytes/Sent | 9603 | 16202 | 64301 | 183,194 | 359,880 | 536,549 | 710,168 |
| $SYS/Broker/Publish/Bytes/Received | 395 | 710 | 3015 | 8495 | 16,665 | 24,865 | 33,060 |
| $SYS/Broker/Publish/Bytes/Sent | 1082 | 1920 | 8315 | 24,546 | 49,094 | 73,862 | 98,359 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Aleisa, M.A.; Abuhussein, A.; Alsubaei, F.S.; Sheldon, F.T. Examining the Performance of Fog-Aided, Cloud-Centered IoT in a Real-World Environment. Sensors 2021, 21, 6950. https://doi.org/10.3390/s21216950
Aleisa MA, Abuhussein A, Alsubaei FS, Sheldon FT. Examining the Performance of Fog-Aided, Cloud-Centered IoT in a Real-World Environment. Sensors. 2021; 21(21):6950. https://doi.org/10.3390/s21216950
Chicago/Turabian StyleAleisa, Mohammed A., Abdullah Abuhussein, Faisal S. Alsubaei, and Frederick T. Sheldon. 2021. "Examining the Performance of Fog-Aided, Cloud-Centered IoT in a Real-World Environment" Sensors 21, no. 21: 6950. https://doi.org/10.3390/s21216950
APA StyleAleisa, M. A., Abuhussein, A., Alsubaei, F. S., & Sheldon, F. T. (2021). Examining the Performance of Fog-Aided, Cloud-Centered IoT in a Real-World Environment. Sensors, 21(21), 6950. https://doi.org/10.3390/s21216950







