Epidemic Analysis of Wireless Rechargeable Sensor Networks Based on an Attack–Defense Game Model
Abstract
1. Introduction
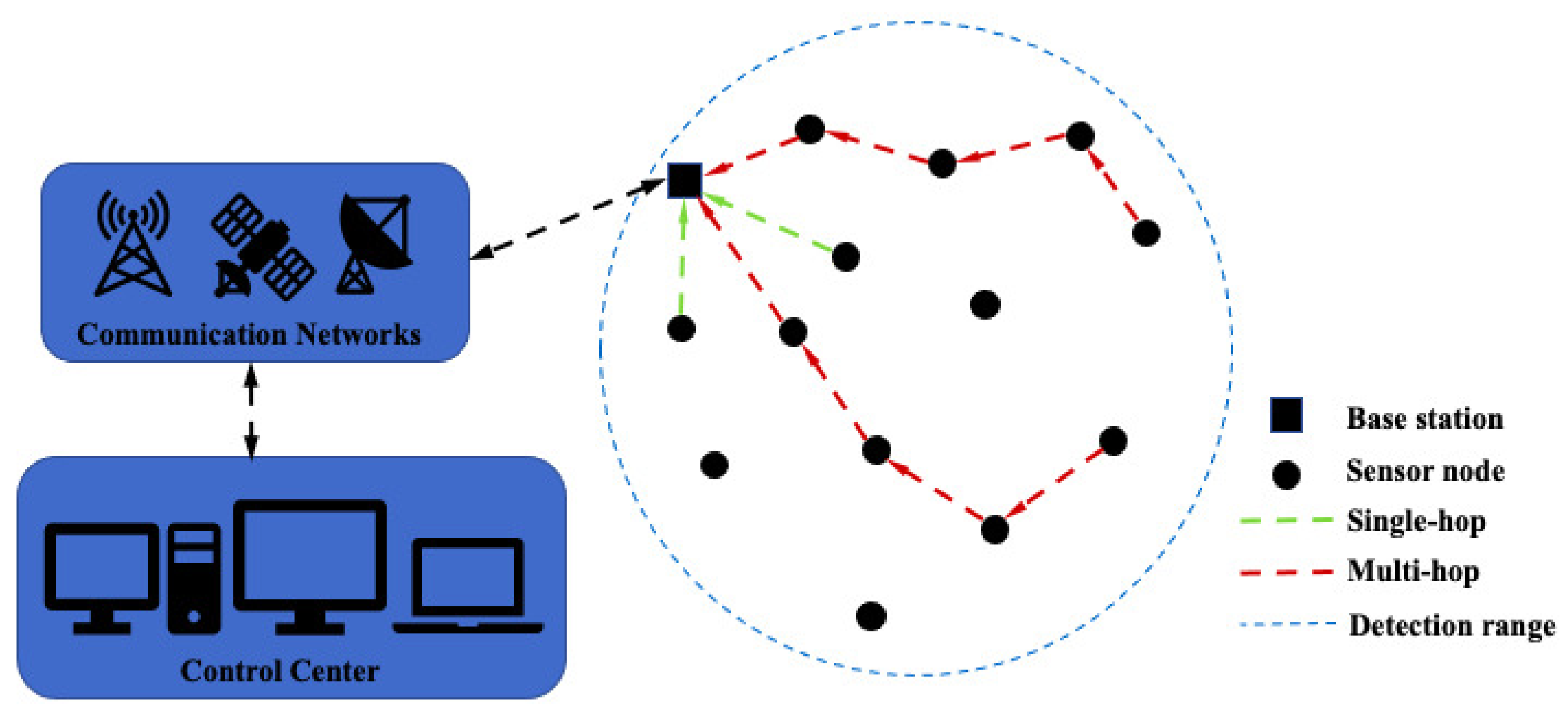
2. Modeling
2.1. Dynamic Equation
- (a)
- Malware propagates by broadcasting. Assuming that the ratio of I nodes successfully infecting S nodes is , where is greater than 0, then the proportion of the new infected in the network is .
- (b)
- Considering mobile chargers and rechargeable modules, after the nodes in A drop to at , anti-malware programs stop running, and the nodes return to S at rate when they are fully charged. and are all greater than 0.
- (c)
- Nodes in S, I, and A drop to low-energy level at different ratios , , and , where . Among them, owing to the running of anti-malware program, is greater than . Due to the software attack launched by malware, is greater than and . , , and are all greater than 0.
- (d)
- Suppose that, except for I, the four remaining compartments S, A, , and have the same mortality . I is different in that malware also launches hardware attacks at rate a to cause damage. and a are all greater than 0.
- (e)
- Regardless of other protective measures, this paper only considers activating anti-malware program to achieve the purpose of clearing malware temporarily.
2.2. Computation of the Steady States and the Basic Reproductive Number
3. Dynamic Analysis and Optimal Strategy
3.1. Analysis of Disease-Free Equilibrium Point
3.2. Analysis of Epidemic Equilibrium Point
- (a)
- , . Then, . The value 0 occurs if and only if .
- (b)
- , . Then, . The value 0 occurs if and only if .
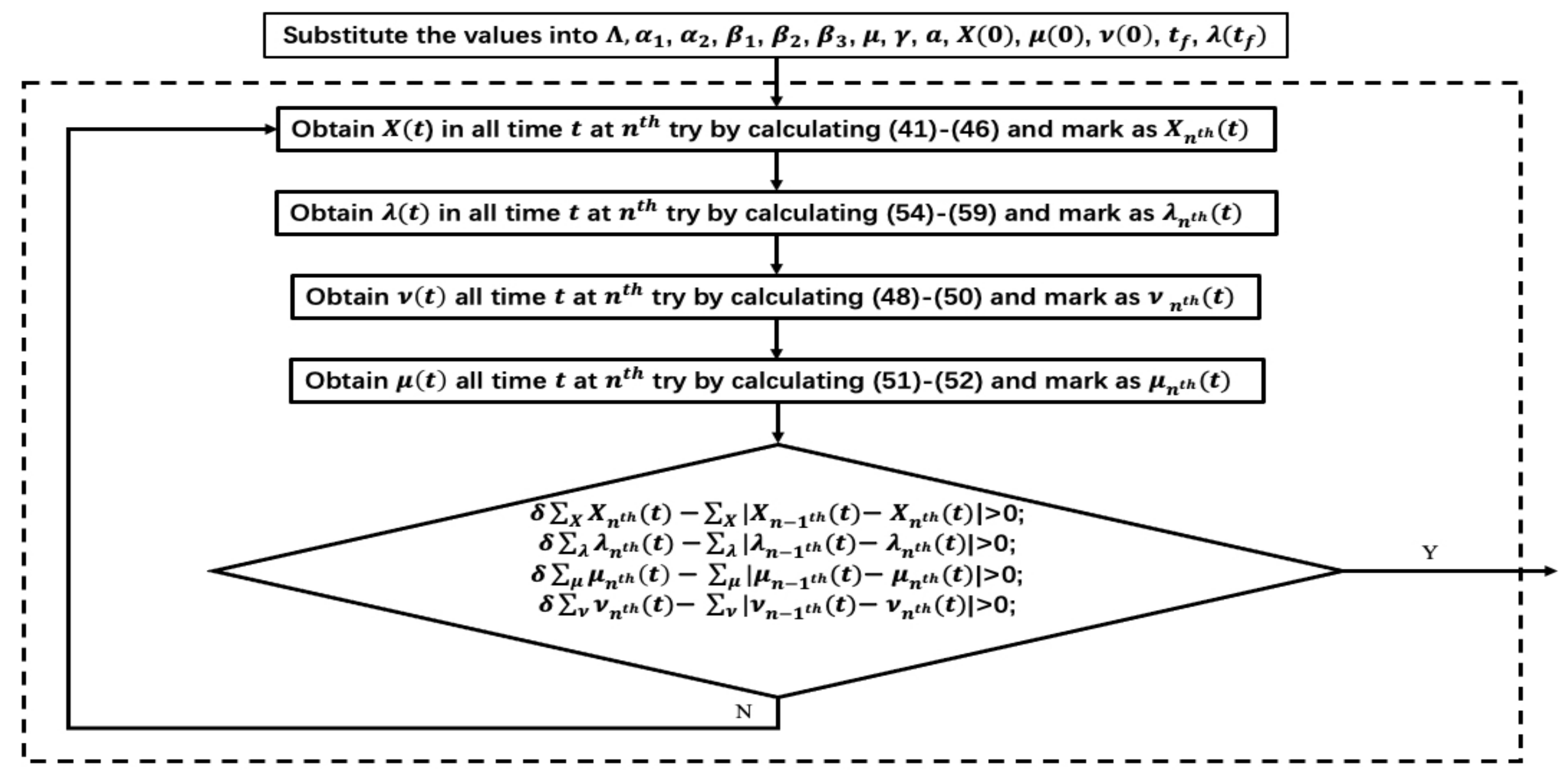
3.3. Optimal Strategies
- is the set of plays in the attack–defense game. is the attacker and is the defender.
- is a set of strategies implemented by the malware. represents the spreading capability of the malware, represents the strength of the attacks on the charging process, and represents the strength of the hardware attack. In particular, the three control strategies are all constrained by the upper and lower bounds.
- is a set of strategies implemented by the WRSNs. represents the strength of activation of the anti-malware program and represents the control of the charging process by WRSNs. Similarly, the two strategies have upper and lower bounds.
- is a set of the state variables on the SIALS model. The denotations of the state variables are the same as the statement in Section 2.1.
- is a set of the adjoint variables of the games
4. Simulation
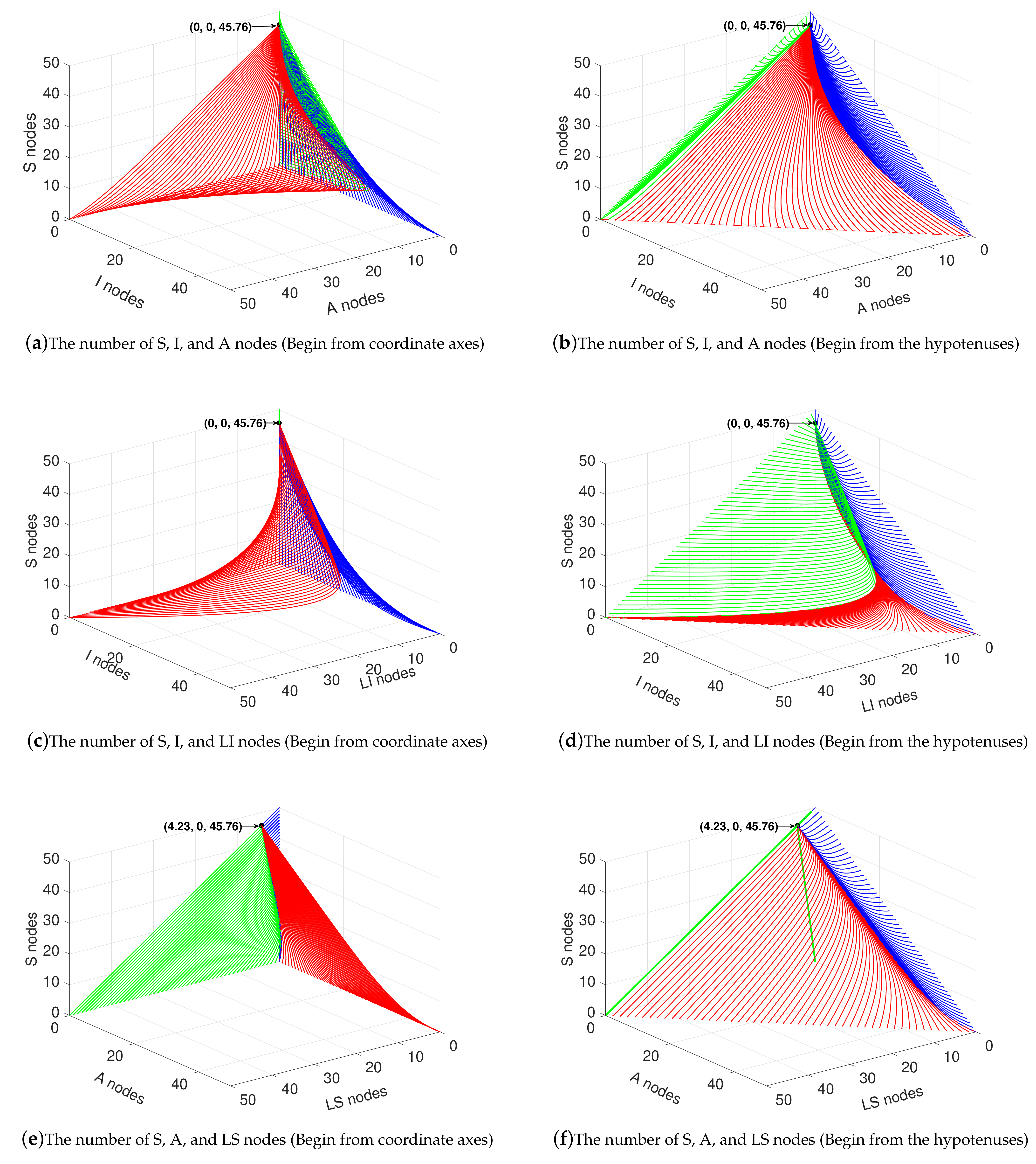
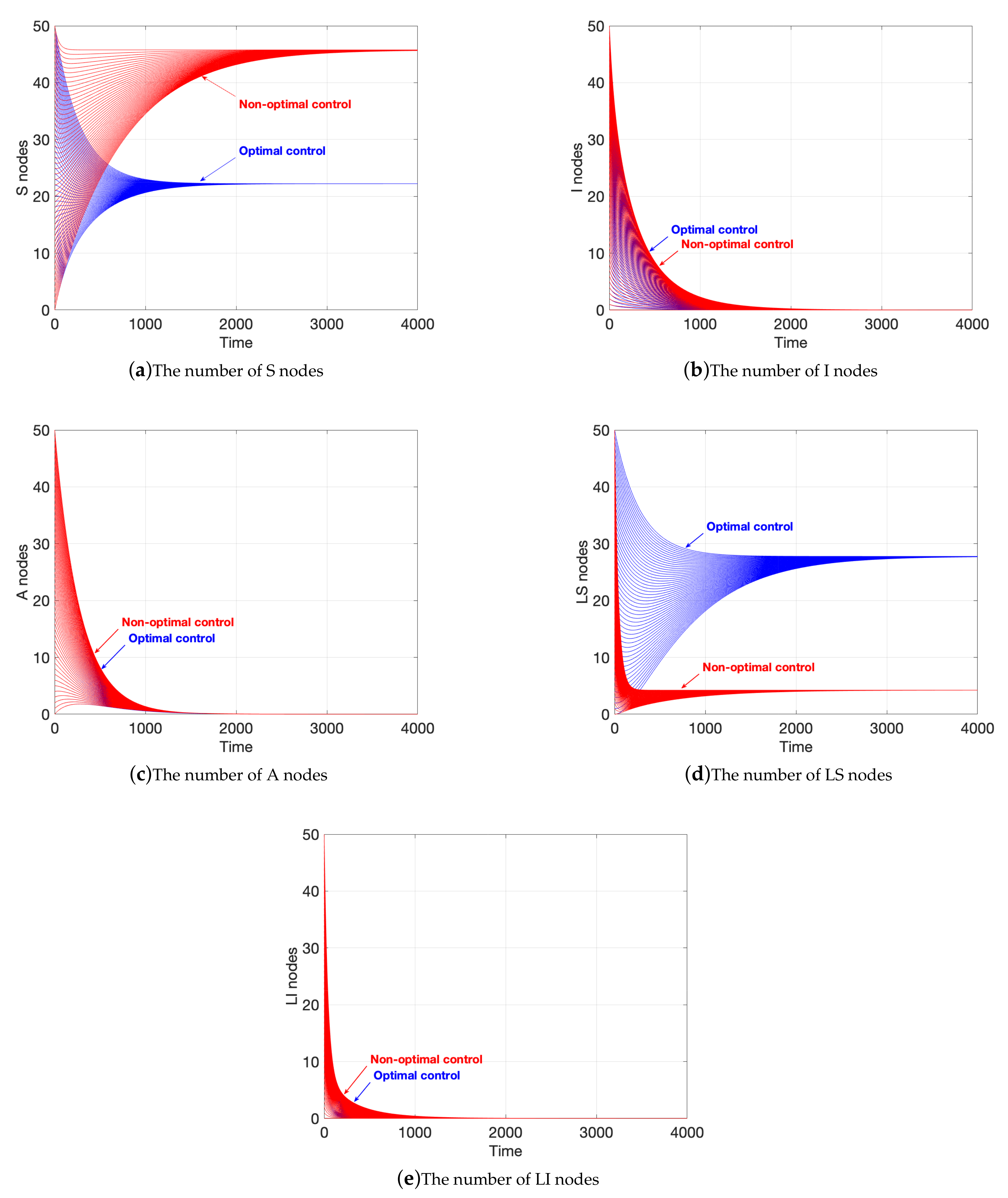
4.1. Stable Analysis When
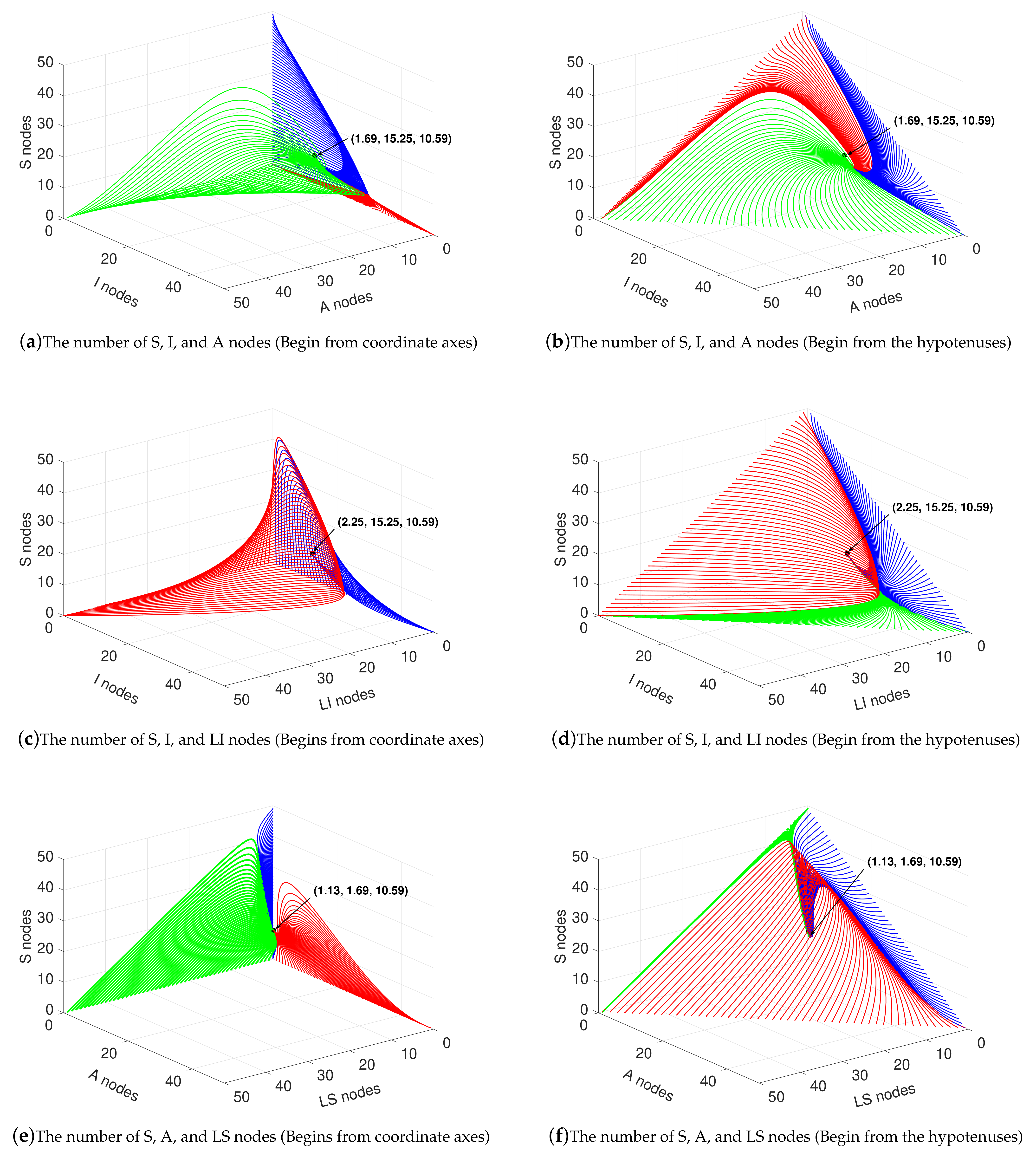
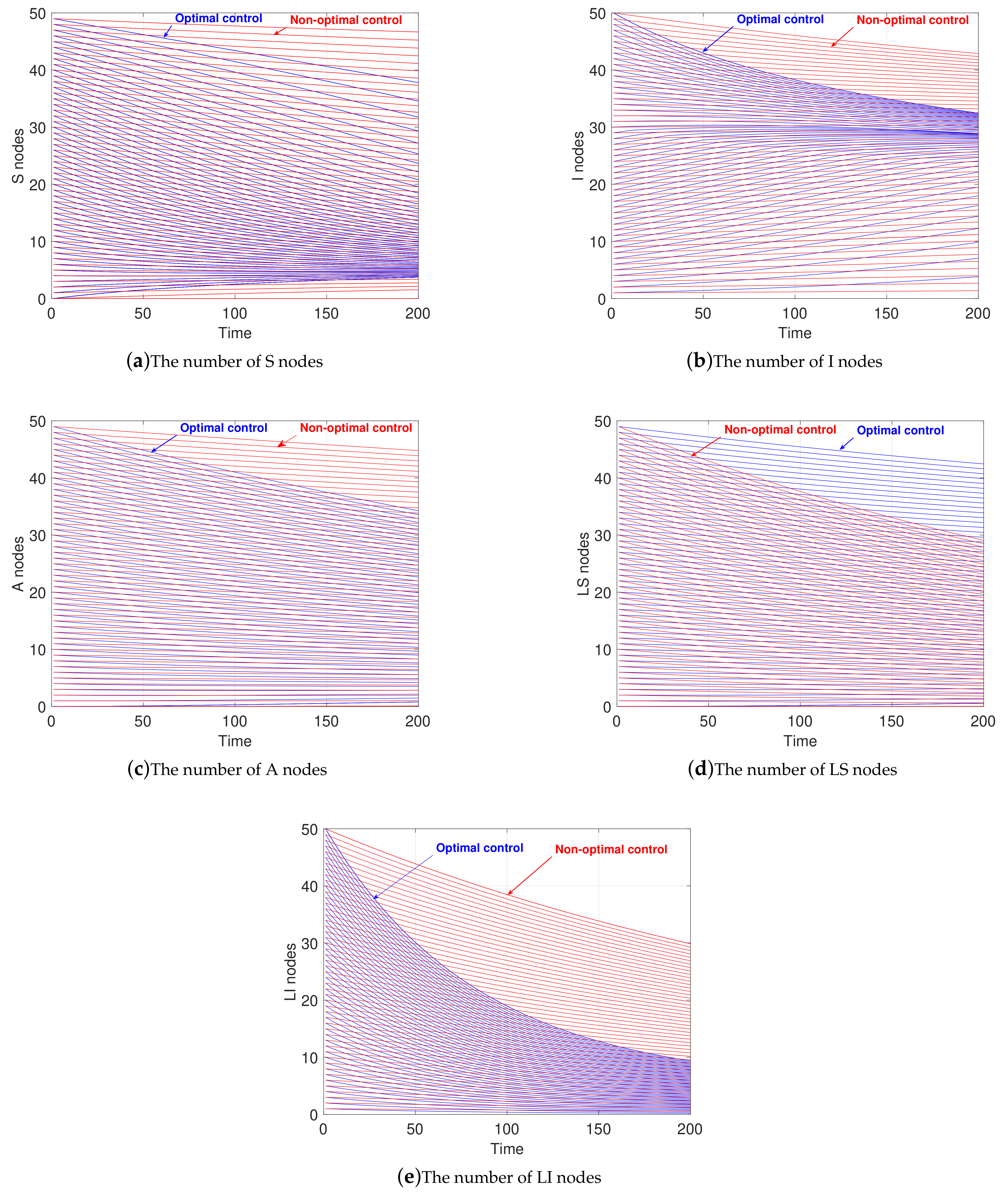
4.2. Stable Analysis when
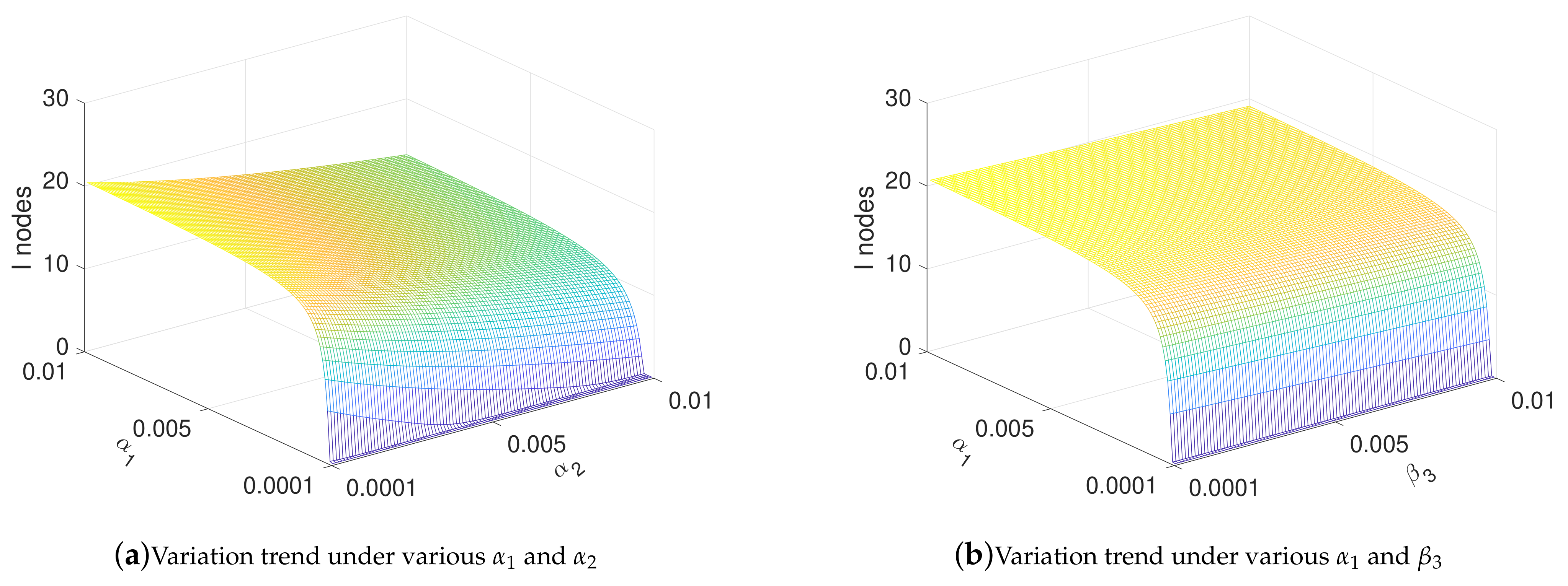
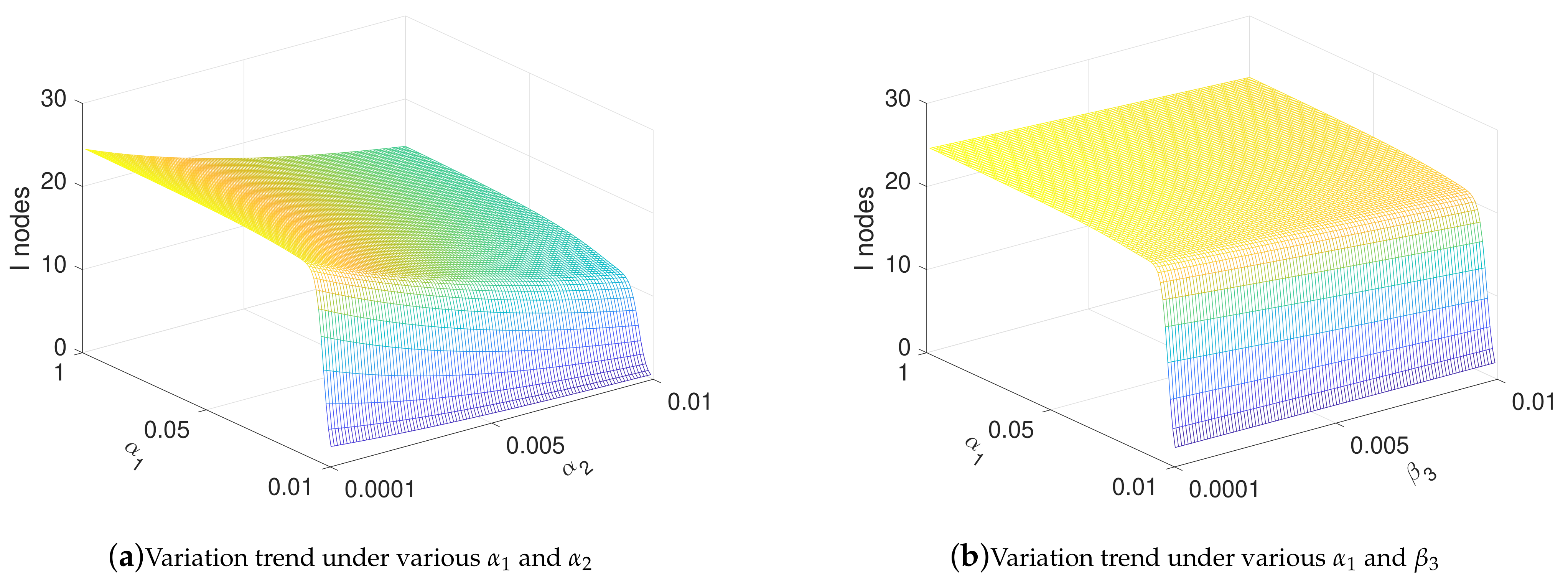
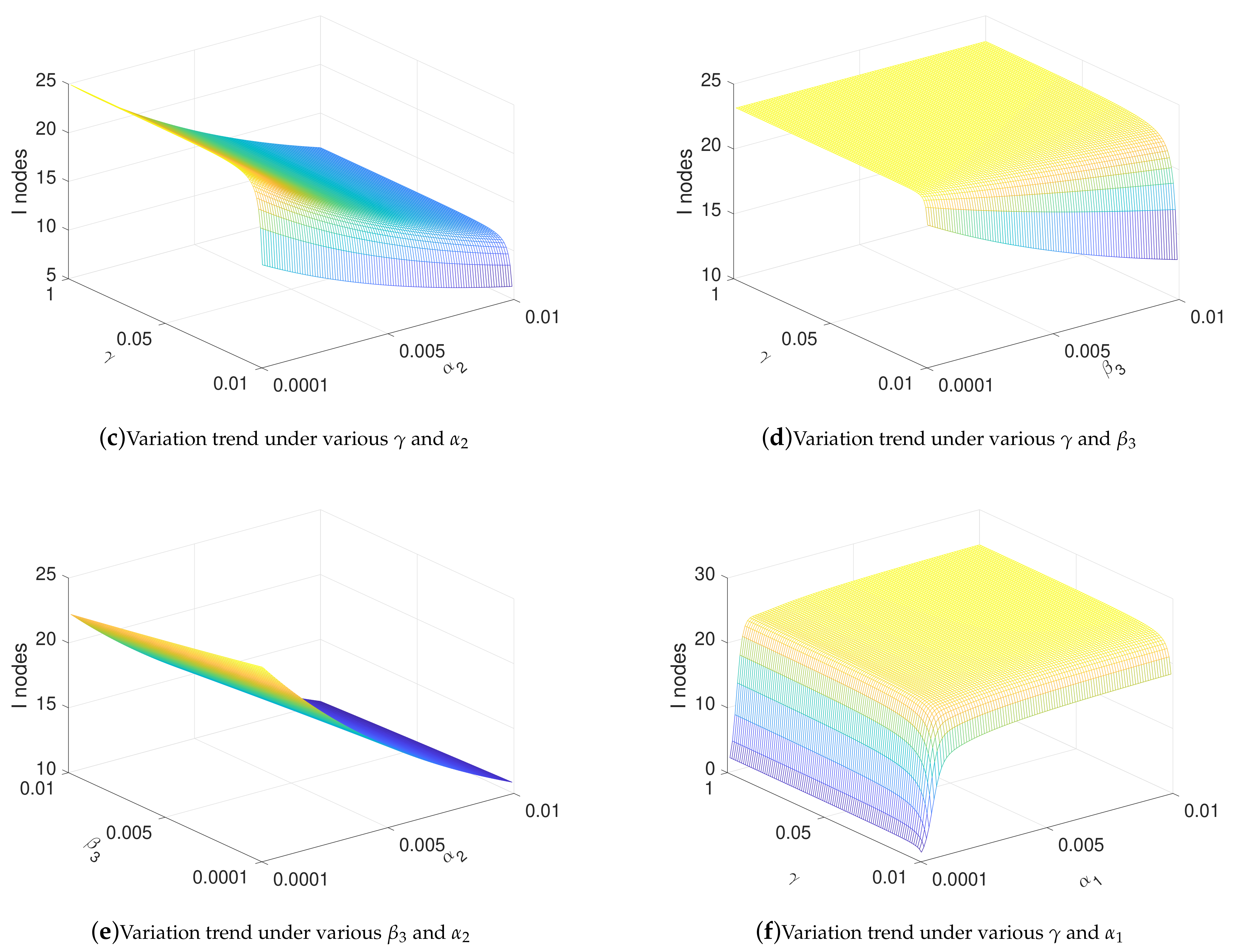
4.3. Influence of Parameters under Stable State
4.4. Variation of State Variables when
4.5. Variation of State Variables when
4.6. Influence of Parameters under Optimal Controls
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Xie, H.M.; Yan, Z.; Yan, Z.; Atiquzzaman, M. Data Collection for Security Measurement in Wireless Sensor Networks: A Survey. IEEE Internet Things J. 2020, 6, 2205–2224. [Google Scholar] [CrossRef]
- Han, G.J.; Jiang, J.F.; Zhang, C.Y.; Duong, T.Q.; Guizani, M.; Karagiannidis, G.K. A Survey on Mobile Anchor Node Assisted Localization in Wireless Sensor Networks. IEEE Commun. Surv. Tutor. 2016, 18, 2220–2243. [Google Scholar] [CrossRef]
- Butun, I.; Osterberg, P.; Song, H.B. Security of the Internet of Things: Vulnerabilities, Attacks, and Countermeasures. IEEE Commun. Surv. Tutor. 2020, 22, 616–644. [Google Scholar] [CrossRef]
- Rashid, B.; Rehmani, M.H. Applications of wireless sensor networks for urban areas: A survey. J. Netw. Comput. Appl. 2016, 60, 192–219. [Google Scholar] [CrossRef]
- Yetgin, H.; Cheung, K.T.K.; El-Hajjar, M.; Hanzo, L. A Survey of Network Lifetime Maximization Techniques in Wireless Sensor Networks. IEEE Commun. Surv. Tutor. 2017, 19, 828–854. [Google Scholar] [CrossRef]
- Panatik, K.Z.; Kamardin, K.; Shariff, S.A.; Yuhaniz, S.S.; Ahmad, N.A.; Yusop, O.M.; Ismail, S. Energy harvesting in wireless sensor networks: A survey. In Proceedings of the 2016 IEEE 3rd international symposium on Telecommunication Technologies (ISTT), Kuala Lumpur, Malaysia, 28–30 November 2016. [Google Scholar]
- Shu, Y.C.; Yousefi, H.; Cheng, P.; Chen, J.M.; Gu, Y.; He, T.; Shin, K.G. Near-Optimal Velocity Control for Mobile Charging in Wireless Rechargeable Sensor Networks. IEEE. Trans. Mob. Comput. 2016, 15, 1699–1713. [Google Scholar] [CrossRef]
- Wu, P.F.; Xiao, F.; Sha, C.; Huang, H.P.; Sun, L.J. Trajectory Optimization for UAVs’ Efficient Charging in Wireless Rechargeable Sensor Networks. IEEE Trans. Veh. Technol. 2020, 69, 4207–4220. [Google Scholar] [CrossRef]
- Mo, L.; Kritikakou, A.; He, S.B. Energy-Aware Multiple Mobile Chargers Coordination for Wireless Rechargeable Sensor Networks. IEEE Internet Things J. 2019, 6, 8202–8214. [Google Scholar] [CrossRef]
- Lin, C.; Shang, Z.; Du, W.; Ren, J.K.; Wang, L.; Wu, G.W. CoDoC: A novel attack for wireless rechargeable sensor networks through denial of charge. In Proceedings of the IEEE INFOCOM 2019-IEEE Conference on Computer Communications, Paris, France, 29 April–2 May 2019. [Google Scholar]
- Lin, C.; Zhou, J.Z.; Guo, C.Y.; Song, H.B.; Wu, G.W.; Mohammad, S.O. TSCA: A temporal-spatial real-time charging scheduling algorithm for on-demand architecture in wireless rechargeable sensor networks. IEEE. Trans. Mob. Comput. 2018, 17, 211–224. [Google Scholar] [CrossRef]
- Nguyen, A.N.; Vo, V.N.; So-ln, C.; Ha, D.B.; Sanguanpong, S.; Baig, Z.A. On Secure Wireless Sensor Networks With Cooperative Energy Harvesting Relaying. IEEE Access 2019, 7, 139212–139225. [Google Scholar] [CrossRef]
- Jung, J.; Kang, M.; Yoon, I.; Noh, D.K. Adaptive forward error correction scheme to improve data reliability in solar-powered wireless sensor networks. In Proceedings of the 2016 International Conference on Information Science and Security (ICISS), Pattaya, Thailand, 19–22 December 2016. [Google Scholar]
- Vo, V.N.; Nguyen, T.G.; So-ln, C.; Ha, D.B. Secrecy Performance Analysis of Energy Harvesting Wireless Sensor Networks with a Friendly Jammer. IEEE Access 2017, 5, 25196–25206. [Google Scholar] [CrossRef]
- Shafie, A.E.I.; Niyato, D.; Al-Dhahir, N. Security of Rechargeable Energy-Harvesting Transmitters in Wireless Networks. IEEE Wirel. Commun. Lett. 2016, 5, 384–387. [Google Scholar] [CrossRef]
- Bhushan, B.; Sahoo, G. E2SR2: An acknowledgement-based mobile sink routing protocol with rechargeable sensors for wireless sensor networks. Wirel. Netw. 2019, 25, 2697–2721. [Google Scholar] [CrossRef]
- Lim, S.; Huie, L. Hop-by-hop cooperative detection of selective forwarding attacks in energy harvesting wireless sensor networks. In Proceedings of the 2015 International Conference on Computing, Networking and Communications, Anaheim, CA, USA, 16–19 February 2015. [Google Scholar]
- Kommuru, K.J.S.R.; Kadari, K.K.Y.; Alluri, B.K.S.P.K.R. A novel approach to balance the trade-off between security and energy consumption in WSN. In Proceedings of the 2018 2nd International Conference on Micro-Electronics and Telecommunication Engineering, Ghaziabad, India, 20–21 September 2018. [Google Scholar]
- Mauro, A.D.; Fafoutis, X.; Dragoni, N. Adaptive Security in ODMAC for Multihop Energy Harvesting Wireless Sensor Networks. Int. J. Distrib. Sens. Netw. 2015, 11, 760302. [Google Scholar] [CrossRef]
- Hu, X.; Huang, K.Z.; Chen, Y.J.; Xu, X.M.; Liang, X.H. Secrecy analysis of UL transmission for SWIPT in WSNs with densely clustered eavesdroppers. In Proceedings of the 2017 9th International Conference on Wireless Communications and Signal Processing (WCSP 2017), Nanjing, China, 11–13 October 2017. [Google Scholar]
- Bouachir, O.; Mnaouer, A.B.; Touati, F.; Crescini, D. Opportunistic routing and data dissemination protocol for energy harvesting wireless sensor networks. In Proceedings of the 2016 8th IFIP International Conference on New Technologies, Mobility and Security (NTMS 2016), Larnaca, Cyprus, 21–23 November 2016. [Google Scholar]
- Huang, S.Y.; Chen, F.D.; Chen, L.J. Global dynamics of a network-based SIQRS epidemic model with demographics and vaccination. Commun. Nonlinear Sci. Numer. Simul. 2017, 43, 296–310. [Google Scholar] [CrossRef]
- Srivastava, P.K.; Pandey, S.P.; Gupta, N.; Singh, S.P.; Ojha, R.P. Modeling and analysis of antimalware effect on wireless sensor network. In Proceedings of the 2019 IEEE 4th International Conference on Computer and Communication Systems (ICCCS), Singapore, 23–25 February 2019. [Google Scholar]
- Zhu, L.H.; Guan, G. Dynamical analysis of a rumor spreading model with self-discrimination and time delay in complex networks. Phys. A 2019, 533, 121953. [Google Scholar] [CrossRef]
- Liu, G.Y.; Peng, B.H.; Zhong, X.J. A Novel Epidemic Model for Wireless Rechargeable Sensor Network Security. Sensors 2020, 21, 123. [Google Scholar] [CrossRef]
- Hosseini, S.; Azgomi, M.A. The dynamics of an SEIRS-QV malware propagation model in heterogeneous networks. Phys. A 2018, 512, 803–817. [Google Scholar] [CrossRef]
- Ojha, R.P.; Srivastava, P.K.; Sanyal, G.; Gupta, N. Improved Model for the Stability Analysis of Wireless Sensor Network Against Malware Attacks. Wirel. Pers. Commun. 2020, 1–24. [Google Scholar] [CrossRef]
- Huang, D.W.; Yang, L.X.; Yang, X.F.; Wu, Y.B.; Tang, Y.Y. Towards understanding the effectiveness of patch injection. Phys. A 2019, 526, 120956. [Google Scholar] [CrossRef]
- Zhu, L.H.; Zhou, M.T.; Zhang, Z.D. Dynamical Analysis and Control Strategies of Rumor Spreading Models in Both Homogeneous and Heterogeneous Networks. J. Nonlinear Sci. 2020, 30, 2545–2576. [Google Scholar] [CrossRef]
- Guillén, J.D.H.; del Rey, A.M. A mathematical model for malware spread on WSNs with population dynamics. Phys. A 2020, 545, 123609. [Google Scholar]
- Shen, S.G.; Zhou, H.P.; Feng, S.; Liu, J.H.; Zhang, H.; Cao, Q.Y. An Epidemiology-Based Model for Disclosing Dynamics of Malware Propagation in Heterogeneous and Mobile WSNs. IEEE Access 2020, 8, 43876–43887. [Google Scholar] [CrossRef]
- Eshghi, S.; Khouzani, M.H.R.; Sarkar, S. Optimal Patching in Clustered Malware Epidemics. IEEE ACM Trans. Netw. 2016, 24, 283–298. [Google Scholar] [CrossRef]
- Khouzani, M.H.R.; Sarkar, S.; Altman, E. Optimal Dissemination of Security Patches in Mobile Wireless Networks. IEEE Trans. Inf. Theory 2012, 58, 4714–4732. [Google Scholar] [CrossRef]
- Zhang, L.T.; Xu, J. Differential Security Game in Heterogeneous Device-to-Device Offloading Network under Epidemic Risks. IEEE Trans. Netw. Sci. Eng. 2020, 7, 1852–1861. [Google Scholar] [CrossRef]
- Al-Tous, H.; Barhumi, I. Differential game for resource allocation in energy harvesting sensor networks. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018. [Google Scholar]
- Huang, Y.H.; Zhu, Q.Y. A Differential Game Approach to Decentralized Virus-Resistant Weight Adaptation Policy over Complex Networks. IEEE Trans. Control Netw. Syst. 2020, 7, 944–955. [Google Scholar] [CrossRef]
- Sun, Y.; Li, Y.B.; Chen, X.H.; Li, J. Optimal defense strategy model based on differential game in edge computing. J. Intell. Fuzzy Syst. 2020, 39, 1449–1459. [Google Scholar] [CrossRef]
- Shen, S.G.; Li, H.J.; Han, R.S.; Vasilakos, A.V.; Wang, Y.H.; Cao, Q.Y. Differential Game-Based Strategies for Preventing Malware Propagation in Wireless Sensor Networks. IEEE Trans. Inf. Forensics Secur. 2014, 9, 1962–1973. [Google Scholar] [CrossRef]
- Hu, J.H.; Qian, Q.; Fang, A.; Fang, S.Z.; Xie, Y. Optimal Data Transmission Strategy for Healthcare-Based Wireless Sensor Networks: A Stochastic Differential Game Approach. Wirel. Pers. Commun. 2016, 89, 1295–1313. [Google Scholar] [CrossRef]
- Sarkar, S.; Khouzani, M.H.R.; Kar, K. Optimal Routing and Scheduling in Multihop Wireless Renewable Energy Networks. IEEE Trans. Autom. Control 2013, 58, 1792–1798. [Google Scholar] [CrossRef]
- Liu, G.Y.; Peng, B.H.; Zhong, X.J.; Cheng, L.F.; Li, Z.F. Attack-Defense Game between Malicious Programs and Energy-Harvesting Wireless Sensor Networks Based on Epidemic Modeling. Complexity 2020, 2020, 3680518. [Google Scholar] [CrossRef]
- Van den Diressche, P.; Watmough, J. Further notes on the basic reproduction number. In Mathematical Epidemiology; Brauer, F., van den Driessche, P., Wu, J., Eds.; Springer: Berlin, Germany, 2008; pp. 159–178. [Google Scholar]
- Lyapunov, A.M. The general problem of the stability of motion. Int. J. Control 1992, 55, 531–534. [Google Scholar] [CrossRef]
- Lasalle, J.P. The Stability of Dynamical Systems; SIAM: Philadelphia, PA, USA, 1976. [Google Scholar]
- Merkin, D.R. Introduction to the Theory of the Stability; Springer: New York, NY, USA, 2012; Volume 24. [Google Scholar]
- Robinson, R.C. An Introduction to Dynamical Systems: Continous and Discrete; Pearson Education; Prentice Hall: Upper Saddle River, NJ, USA, 2004. [Google Scholar]


| Authors | Problems | Methods | Results |
|---|---|---|---|
| A.N. Nguyen et al. [12] | Securing the physical layer | Time-switching power-splitting (TSPS) mechanism | The secrecy performance under TSPS is higher than the traditional scheme |
| J. Jung et al. [13] | Excessive energy consumption in the forward error correction(FEC) method | Energy-aware FEC method | The developed method performs better than the former one. |
| V.N. Vo et al. [14] | Securing energy harvesting wireless sensor networks(EH-WSNs) under eavesdropping and signal interception | An optimization scheme that uses a wirelessly powered friendly jammer | The hypotheses are supported. |
| A. EI Shafie et al. [15] | Securing a single-antenna rechargeable source node in the presence of a multi-antenna rechargeable cooperative jammer and a potential single-antenna eavesdropper | An efficient scheme which can optimize the transmission times of the source node | The average secrecy rate gain of the scheme is demonstrated significantly |
| B. Bhushan et al. [16] | Securing the mobile sinks position information | Energy Efficient Secured Ring Routing (E2SR2) protocol | E2SR2 achieves improved performance than the existing protocols |
| S. Lim et al. [17] | Securing EH-WSNs under the Denial-of-Service (DoS) attacks | Hop-by-hop Cooperative Detection (HCD) scheme | HCD scheme can significantly reduce the number of forwarding misbehaviors and achieve higher packet delivery ratio |
| K J.S.R. Kommuru et al. [18] | Balancing the trade-off between improving security and reducing energy consumption | Low complexity XOR technique and Hybrid LEACH-PSO algorithm | The proposed approach performs better than the existing approaches. |
| A. DI Mauro et al. [19] | Securing the communications under energy constraints | Adaptive approach which allows nodes to dynamically choose the most appropriate parameters | Adaptive solution performs better |
| X. Hu et al. [20] | Securing the up-link (UL) transmission | Establishing the communication model; deriving the energy outage probabilities (EOP), connection outage probabilities (COP) and secrecy outage probabilities (SOP) through comprehensive analysis | The theoretical derivations are verified |
| O. Bouachir et al. [21] | Securing the transmission between sensor nodes and base stations | A novel strategy to select cluster heads and implement the non-orthogonal multiple access (NOMA) technique in the transmission | The secrecy performance can be improved |
| Authors | Characteristics | Model | Stability |
|---|---|---|---|
| S.Y. Huang et al. [22] | Heterogeneity | Susceptible-Infected-Quarantined- Recovered-Susceptible (SIQRS) | 1 |
| P.K. Srivastava et al. [23] | Anti-malware process | Susceptible-Exposed-Infectious- Antimalware-Recovered (SEIAR) | 2 |
| L.H. Zhu et al. [24] | Time delay | Susceptible-Believed-Denied (SBD) | 2 |
| G.Y. Liu et al. [25] | Low-energy | Susceptible-Infected-Low-energy-Susceptible(SILS) | 1 |
| S. Hosseini et al. [26] | User awareness, network delay and diverse configuration of nodes | Susceptible–Exposed–Infected–Recovered-Susceptible with Vaccination and Quarantine state | 2 |
| R.P. Ojha et al. [27] | Quarantine and vaccination techniques | Susceptible–Exposed–Infectious–Quarantined–Recovered–Vaccinated (SEIQRV) | 2 |
| D.W. Huang et al. [28] | Patch injection mechanism | Susceptible–Infected–Patched–Susceptible (SIPS) | 3 |
| L.H. Zhu et al. [29] | Time delay in homogeneous and heterogeneous networks | Ignorants–Spreaders1–Spreaders2–Stiflers1–Stiflers2 (I2S2R) | 1 |
| J.D. Hernández Guillén et al. [30] | Carrier state | Susceptible–Carrier–Infectious–Recovered–Susceptible (SCIRS) | 1 |
| S.G. Shen et al. [31] | Heterogeneity and Mobility | Vulnerable–Compromised–Quarantined–Patched–Scrapped (VCQPS) | 2 |
| Authors | Players | Goal | Strategies |
|---|---|---|---|
| S. Eshghi et al. [32] | Malware and mobile WSNs | Leverage the heterogeneity of malware propagation | Optimal patching policies |
| M.H.R. Khouzani et al. [33] | Malware and Mobile WSNs | Attain desired tradeoffs between security risks and bandwidth consumption | Optimal control in activating dispatchers and selecting their transmission rate |
| L.T. Zhang, et al. [34] | Malware and device to Device (D2D) offloading-enabled mobile network | Understand the malware propagation process in D2D offloading-enabled mobile network | Optimal dynamic defense and attack strategies |
| H. Al-Tous et al. [35] | An energy-harvesting multi-hop WSN | Balance the normalized buffer states of all sensor nodes and minimize the amount of energy used for data transmission. | An online power control and data scheduling algorithm |
| Y.H. Huang et al. [36] | Virus and sensor nodes | Mitigate virus spreading | Virus-resistant weight adaptation policies |
| Y. Sun et al. [37] | Edge nodes (ENs) | Realize the balance between reward and energy consumption cost of ENs in the deployment of defense measures | Optimal defense strategy |
| S.G. Shen et al. [38] | malware and WSNs | Limit malware in WSNs | Optimal dynamic strategies for the system and malware |
| J.H. Hu et al. [39] | A healthcare-based wireless sensor network (HWSN) | Minimize the transmission cost | Optimal data transmission strategies |
| S. Sarkar et al. [40] | Multi-hop wireless networks | Optimize network throughput | Optimal routing and scheduling policies |
| Symbol | Description |
|---|---|
| Birth rate | |
| The rate of charging sensor nodes from low-energy to high-energy | |
| Depletion rate determined by the working strength of susceptible nodes | |
| Depletion rate determined by the working strength of anti-malware nodes | |
| Depletion rate determined by malware | |
| Transmission rate of malware | |
| The rate of activating anti-malware | |
| Death rate | |
| a | The rate of hardware attack determined by malware |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, G.; Peng, B.; Zhong, X. Epidemic Analysis of Wireless Rechargeable Sensor Networks Based on an Attack–Defense Game Model. Sensors 2021, 21, 594. https://doi.org/10.3390/s21020594
Liu G, Peng B, Zhong X. Epidemic Analysis of Wireless Rechargeable Sensor Networks Based on an Attack–Defense Game Model. Sensors. 2021; 21(2):594. https://doi.org/10.3390/s21020594
Chicago/Turabian StyleLiu, Guiyun, Baihao Peng, and Xiaojing Zhong. 2021. "Epidemic Analysis of Wireless Rechargeable Sensor Networks Based on an Attack–Defense Game Model" Sensors 21, no. 2: 594. https://doi.org/10.3390/s21020594
APA StyleLiu, G., Peng, B., & Zhong, X. (2021). Epidemic Analysis of Wireless Rechargeable Sensor Networks Based on an Attack–Defense Game Model. Sensors, 21(2), 594. https://doi.org/10.3390/s21020594







