The Internet of Drones: Requirements, Taxonomy, Recent Advances, and Challenges of Research Trends
Abstract
:1. Introduction
- Investigate the main requirements of IoD (Section 3).
- Provide the main parameters-based thematic taxonomy (Section 4).
- Discuss the most commonly used commercial case studies of IoD (Section 5).
- Investigate the progress recently described in the literature (Section 6).
- Discuss the IoD open challenges and prospective study directions (Section 7).
2. Related Works
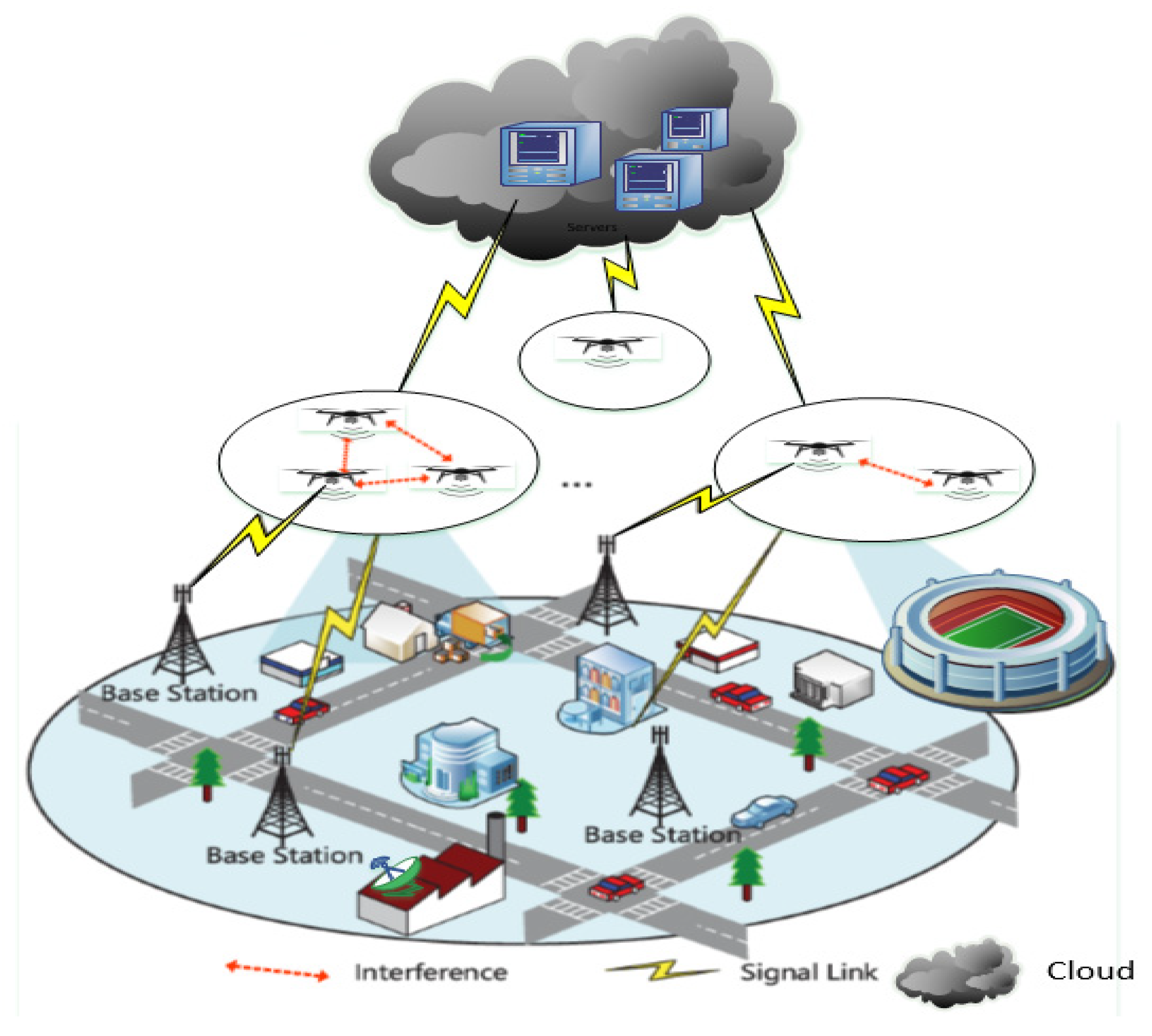
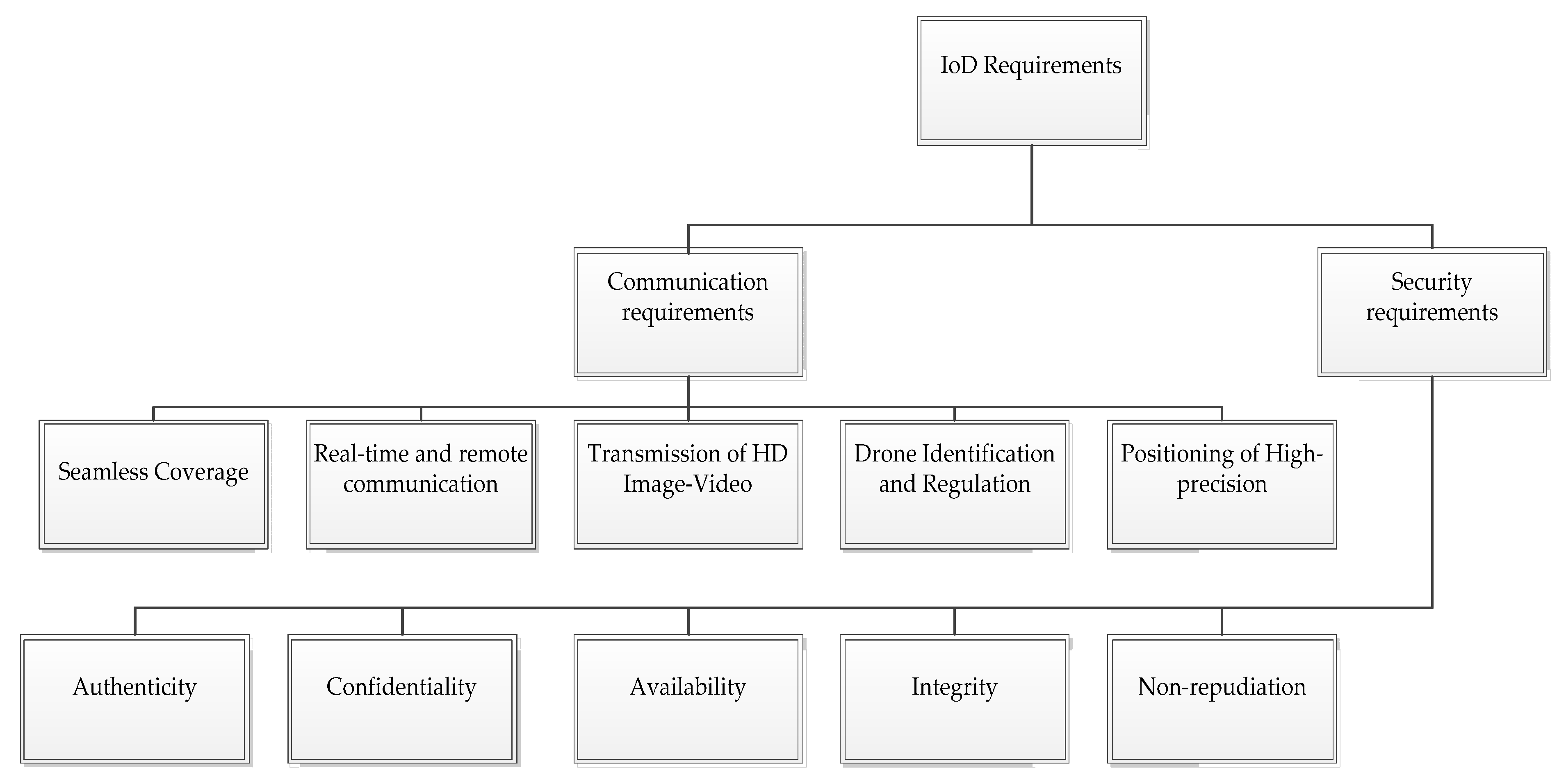
3. Requirements of Internet of Drones (IoD)
3.1. Communication Requirements
3.1.1. Seamless Coverage
3.1.2. Real-Time and Remote Communication
3.1.3. Transmission of HD Image/Video
3.1.4. Drone Identification and Regulation
- Registration: Identifying but standardizing the drone equipment number, serial number, and flight control serial number helps track the whole process orderly from initial drone production to in-use. Through standardizing registration of drone users, owners and mobile networks, drone users and owners can be legally monitored.
- Monitoring: Drone connections and data communications can be detected and monitored through mobile networks. Drone implementations can be completely tracked in real-time with additional regulatory protocols.
- Forecast: Flight situations can be dynamically evaluated and early warning of possible risks can be achieved by tracking drone positions and monitoring the flight traffic and path.
- Coordination: Knowledge exchange between industries and different companies can be carried out by approved oversight of all vertical industries involved.
3.1.5. Positioning of High-Precision
3.2. Security Requirements
3.2.1. Authenticity
3.2.2. Confidentiality
3.2.3. Availability
3.2.4. Integrity
3.2.5. Non-Repudiation
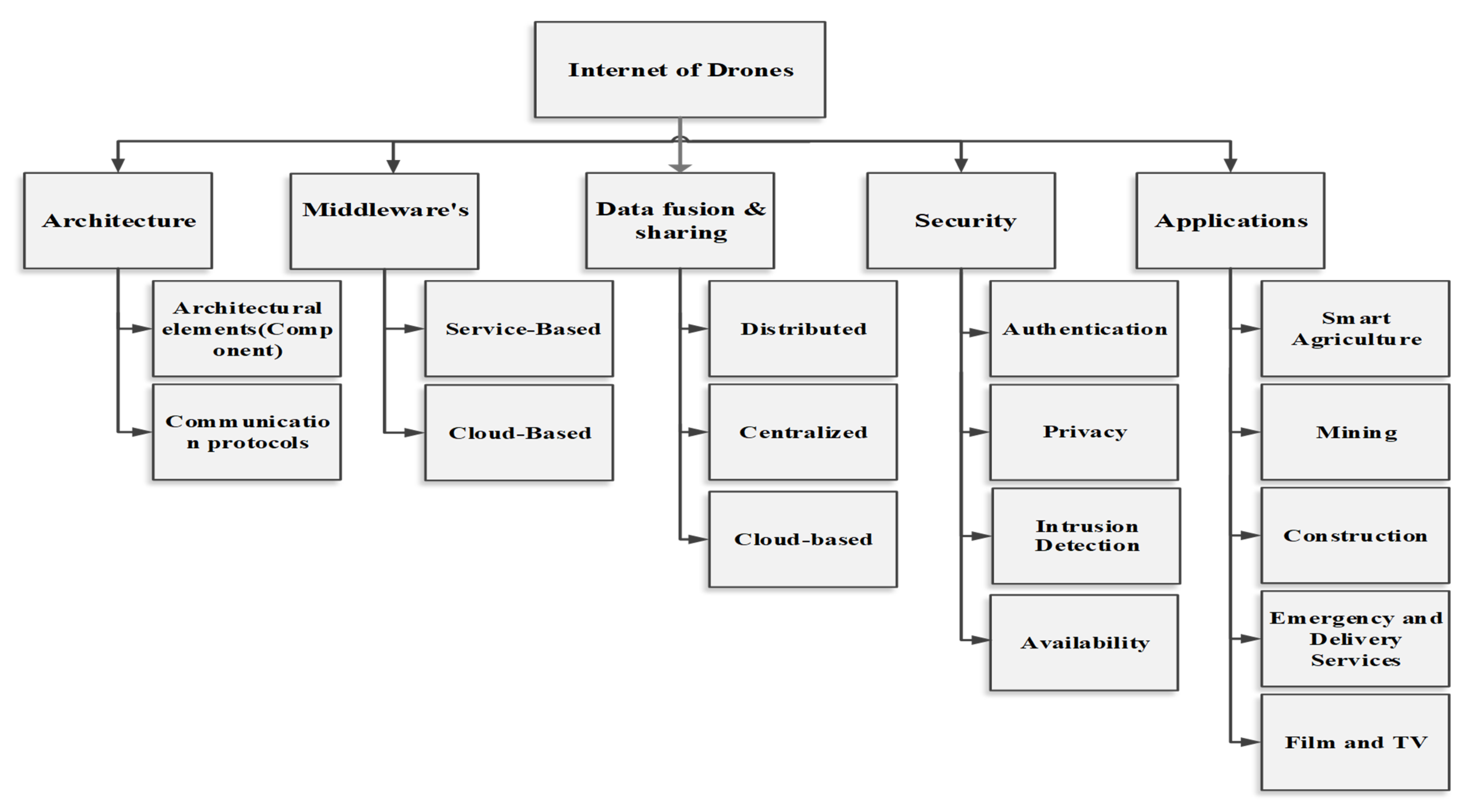
4. Taxonomy of IoD
4.1. Architecture
4.1.1. Architecture Elements (Component)
4.1.2. Communication Protocols
4.2. Middlewares
4.2.1. Service-Based
4.2.2. Cloud-Based
4.3. Data Fusion and Sharing
4.3.1. Distributed
4.3.2. Centralized
4.3.3. Cloud-Based
4.4. Security
4.4.1. Authentication
4.4.2. Privacy
4.4.3. Intrusion Detection
4.4.4. Availability
4.5. Applications
4.5.1. Smart Agriculture
4.5.2. Mining
4.5.3. Construction
| Applications | Modern Usage Areas | Reference |
|---|---|---|
| Smart Agriculture | Soil and Field Analysis Crop Monitoring Irrigation Pathogen detection Drought stress Weed detection Nutrient status Yield prediction | https://www.microdrones.com/en/content/drones-and-precision-agriculture-the-future-of-farming/ (accessed on 10 December 2020). [47,49] |
| Mining | Field measurements Water sampling Stockpile management Site description Mine or quarry monitoring Sediment flow Hazard identification | https://wingtra.com/drone-mapping-applications/mining-and-aggregates/ (accessed on 10 December 2020). [51,53] |
| Construction | Construction Safety Autonomous operation Planning and analysis process Site Inspections | [52] |
| Emergency and Delivery Services | Rescue Operations Blood and medicine Transportation Patient Monitoring Disaster relief and Management Find Missing Persons Public safety | [53,54,55] |
| Film and TV | Scouting and planning Location managers Logistics and safety Multiple sensors shooting Visual effects | https://variety.com/2019/artisans/production/film-and-tv-shoots-drones-1203223079/ (accessed on 11 December 2020). [32,56] |
4.5.4. Emergency and Delivery Services
4.5.5. Films and TV
5. Commercial Case Studies
5.1. Matternet
5.2. ARIA
5.3. DroneSmartX
5.4. H3 Dynamics
6. Recent Advancements
7. Challenges and Future Research Trends
7.1. Privacy and Security-Related Challenges
7.2. Global Resource Management-Related Challenges
7.3. Sensor Communication-Related Challenges
7.4. Coordination and Tasks Scheduling-Related Challenges
7.5. Drones Distribution and Deployment-Related Challenges
8. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Gharibi, M.; Boutaba, R.; Waslander, S.L. Internet of drones. IEEE Access 2016, 4, 1148–1162. [Google Scholar] [CrossRef]
- Tian, Y.; Yuan, J.; Song, H. Efficient privacy-preserving authentication framework for edge-assisted Internet of Drones. J. Inf. Secur. Appl. 2019, 48, 102354. [Google Scholar] [CrossRef]
- Ever, Y.K. A secure authentication scheme framework for mobile-sinks used in the Internet of Drones applications. Comput. Commun. 2020, 155, 143–149. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Lee, J.-H. Authentication protocols for the internet of drones: Taxonomy, analysis and future directions. J. Ambient Intell. Humaniz. Comput. 2018, 1–10. [Google Scholar] [CrossRef]
- Motlagh, N.H.; Taleb, T.; Arouk, O. Low-altitude unmanned aerial vehicles-based internet of things services: Comprehensive survey and future perspectives. IEEE Internet Things J. 2016, 3, 899–922. [Google Scholar] [CrossRef]
- Won, J.; Seo, S.-H.; Bertino, E. Certificateless cryptographic protocols for efficient drone-based smart city applications. IEEE Access 2017, 5, 3721–3749. [Google Scholar] [CrossRef]
- Fotouhi, A.; Qiang, H.; Ding, M.; Hassan, M.; Giordano, L.G.; Garcia-Rodriguez, A.; Yuan, J. Survey on UAV cellular communications: Practical aspects, standardization advancements, regulation, and security challenges. IEEE Commun. Surv. Tutor. 2019, 21, 3417–3442. [Google Scholar] [CrossRef] [Green Version]
- Boccadoro, P.; Striccoli, D.; Grieco, L.A. An extensive survey on the Internet of Drones. Ad Hoc Netw. 2021, 122, 102600. [Google Scholar] [CrossRef]
- Rejeb, A.; Rejeb, K.; Simske, S.; Treiblmaier, H. Humanitarian Drones: A Review and Research Agenda. Internet Things 2021, 16, 100434. [Google Scholar] [CrossRef]
- Yahuza, M.; Idris, M.Y.I.; Ahmedy, I.B.; Wahab, A.W.A.; Nandy, T.; Noor, N.M.; Bala, A. Internet of Drones Security and Privacy Issues: Taxonomy and Open Challenges. IEEE Access 2021, 9, 57243–57270. [Google Scholar]
- Ayamga, M.; Akaba, S.; Nyaaba, A.A. Multifaceted applicability of drones: A review. Technol. Forecast. Soc. Chang. 2021, 167, 120677. [Google Scholar] [CrossRef]
- Merkert, R.; Bushell, J. Managing the drone revolution: A systematic literature review into the current use of airborne drones and future strategic directions for their effective control. J. Air Transp. Manag. 2020, 89, 101929. [Google Scholar] [CrossRef] [PubMed]
- Zaidi, S.; Atiquzzaman, M.; Calafate, C.T. Internet of Flying Things (IoFT): A survey. Comput. Commun. 2020, 165, 53–74. [Google Scholar] [CrossRef]
- Yaacoub, J.-P.; Salman, O. Security Analysis of Drones Systems: Attacks, Limitations, and Recommendations. Internet Things 2020, 11, 100218. [Google Scholar] [CrossRef]
- Al-Turjman, F.; Abujubbeh, M.; Malekloo, A.; Mostarda, L. UAVs assessment in software-defined IoT networks: An overview. Comput. Commun. 2020, 150, 519–536. [Google Scholar] [CrossRef]
- Alsamhi, S.H.; Ma, O.; Ansari, M.S.; Almalki, F.A. Survey on collaborative smart drones and internet of things for improving smartness of smart cities. IEEE Access 2019, 7, 128125–128152. [Google Scholar] [CrossRef]
- Bagloee, S.A.; Tavana, M.; Asadi, M.; Oliver, T. Autonomous vehicles: Challenges, opportunities, and future implications for transportation policies. J. Mod. Transp. 2016, 24, 284–303. [Google Scholar] [CrossRef] [Green Version]
- Sharma, A.; Vanjani, P.; Paliwal, N.; Basnayaka, C.M.W.; Jayakody, D.N.K.; Wang, H.-C.; Muthuchidambaranathan, P. Communication and networking technologies for UAVs: A survey. J. Netw. Comput. Appl. 2020, 168, 102739. [Google Scholar] [CrossRef]
- Yang, G.; Lin, X.; Li, Y.; Cui, H.; Xu, M.; Wu, D.; Rydén, H.; Redhwan, S.B. A telecom perspective on the internet of drones: From LTE-advanced to 5G. arXiv 2018, arXiv:1803.11048. [Google Scholar]
- Lin, C.; He, D.; Kumar, N.; Choo, K.-K.R.; Vinel, A.; Huang, X. Security and privacy for the internet of drones: Challenges and solutions. IEEE Commun. Mag. 2018, 56, 64–69. [Google Scholar] [CrossRef]
- Rahman, M.F.B.A. Smart CCTVS for Secure Cities: Potentials and Challenges, S. Rajaratnam School of International Studies; Rajaratnam School of International Studies: Singapore, 2017. [Google Scholar]
- Bera, B.; Saha, S.; Das, A.K.; Kumar, N.; Lorenz, P.; Alazab, M. Blockchain-envisioned secure data delivery and collection scheme for 5g-based iot-enabled internet of drones environment. IEEE Trans. Veh. Technol. 2020, 69, 9097–9111. [Google Scholar] [CrossRef]
- Nikooghadam, M.; Amintoosi, H.; Islam, S.H.; Moghadam, M.F. A provably secure and lightweight authentication scheme for Internet of Drones for smart city surveillance. J. Syst. Archit. 2021, 115, 101955. [Google Scholar] [CrossRef]
- Ko, Y.; Kim, J.; Duguma, D.G.; Astillo, P.V.; You, I.; Pau, G. Drone Secure Communication Protocol for Future Sensitive Applications in Military Zone. Sensors 2021, 21, 2057. [Google Scholar] [CrossRef] [PubMed]
- Choudhary, G.; Sharma, V.; You, I. Sustainable and secure trajectories for the military Internet of Drones (IoD) through an efficient Medium Access Control (MAC) protocol. Comput. Electr. Eng. 2019, 74, 59–73. [Google Scholar] [CrossRef]
- Lagkas, T.; Argyriou, V.; Bibi, S.; Sarigiannidis, P. UAV IoT framework views and challenges: Towards protecting drones as “Things”. Sensors 2018, 18, 4015. [Google Scholar] [CrossRef] [Green Version]
- Zhang, P.; Wang, C.; Qin, Z.; Cao, H. A multidomain virtual network embedding algorithm based on multiobjective optimization for Internet of Drones architecture in Industry 4.0. Softw. Pract. Exp. 2020. [Google Scholar] [CrossRef]
- Koubâa, A.; Qureshi, B.; Sriti, M.-F.; Allouch, A.; Javed, Y.; Alajlan, M.; Cheikhrouhou, O.; Khalgui, M.; Tovar, E. Dronemap planner: A service-oriented cloud-based management system for the internet-of-drones. Ad Hoc Netw. 2019, 86, 46–62. [Google Scholar] [CrossRef]
- Sánchez-García, J.; García-Campos, J.; Arzamendia, M.; Reina, D.G.; Toral, S.; Gregor, D. A survey on unmanned aerial and aquatic vehicle multi-hop networks: Wireless communications, evaluation tools and applications. Comput. Commun. 2018, 119, 43–65. [Google Scholar] [CrossRef]
- Bousbaa, F.Z.; Kerrache, C.A.; Mahi, Z.; Tahari, A.E.K.; Lagraa, N.; Yagoubi, M.B. GeoUAVs: A new geocast routing protocol for fleet of UAVs. Comput. Commun. 2020, 149, 259–269. [Google Scholar] [CrossRef]
- Ahmed, A.I.A.; Gani, A.; Ab Hamid, S.H.; Abdelmaboud, A.; Syed, H.J.; Mohamed, R.A.A.H.; Ali, I. Service Management for IoT: Requirements, Taxonomy, Recent Advances and Open Research Challenges. IEEE Access 2019, 7, 155472–155488. [Google Scholar] [CrossRef]
- Vallejo, D.; Castro-Schez, J.; Glez-Morcillo, C.; Albusac, J. Multi-agent architecture for information retrieval and intelligent monitoring by UAVs in known environments affected by catastrophes. Eng. Appl. Artif. Intell. 2020, 87, 103243. [Google Scholar] [CrossRef]
- López, J.; Royo, P.; Pastor, E.; Barrado, C.; Santamaria, E. A middleware architecture for unmanned aircraft avionics. In Proceedings of the 2007 ACM/IFIP/USENIX International Conference on Middleware Companion, Newport Beach, CA, USA, 26–30 November 2007; pp. 1–6. [Google Scholar]
- Sharma, V.; Kumar, R.; Patiala, P. Service-oriented middleware for multi-UAV guided ad hoc networks. IT Converg. Pract. 2014, 2, 24–33. [Google Scholar]
- Ribeiro, J.P.; Fontes, H.; Lopes, M.; Silva, H.; Campos, R.; Almeida, J.M.; Silva, E. UAV cooperative perception based on DDS communications network. In Proceedings of the OCEANS 2017-Anchorage, Anchorage, AK, USA, 18–27 September 2017; pp. 1–8. [Google Scholar]
- Aggarwal, S.; Shojafar, M.; Kumar, N.; Conti, M. A new secure data dissemination model in internet of drones. In Proceedings of the ICC 2019–2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Xu, S.; Doğançay, K.; Hmam, H. Distributed pseudolinear estimation and UAV path optimization for 3D AOA target tracking. Signal. Process. 2017, 133, 64–78. [Google Scholar] [CrossRef]
- Patra, A.N.; Regis, P.A.; Sengupta, S. Distributed allocation and dynamic reassignment of channels in UAV networks for wireless coverage. Pervasive Mob. Comput. 2019, 54, 58–70. [Google Scholar] [CrossRef]
- Mohamed, N.; Al-Jaroodi, J.; Jawhar, I.; Idries, A.; Mohammed, F. Unmanned aerial vehicles applications in future smart cities. Technol. Forecast. Soc. Chang. 2018, 153, 119293. [Google Scholar] [CrossRef]
- Fotohi, R. Securing of Unmanned Aerial Systems (UAS) against security threats using human immune system. Reliab. Eng. Syst. Saf. 2020, 193, 106675. [Google Scholar] [CrossRef]
- Zhi, Y.; Fu, Z.; Sun, X.; Yu, J. Security and Privacy Issues of UAV: A Survey. Mob. Netw. Appl. 2019, 25, 1–7. [Google Scholar] [CrossRef]
- Manesh, M.R.; Kaabouch, N. Cyber Attacks on Unmanned Aerial System Networks: Detection, Countermeasure, and Future Research Directions. Comput. Secur. 2019, 85, 386–401. [Google Scholar] [CrossRef]
- Volovelsky, U. Civilian uses of unmanned aerial vehicles and the threat to the right to privacy–An Israeli case study. Comput. Law Secur. Rev. 2014, 30, 306–320. [Google Scholar] [CrossRef]
- Condomines, J.-P.; Zhang, R.; Larrieu, N. Network intrusion detection system for UAV ad-hoc communication: From methodology design to real test validation. Ad Hoc Netw. 2019, 90, 101759. [Google Scholar] [CrossRef]
- Amanullah, M.A.; Habeeb, R.A.A.; Nasaruddin, F.H.; Gani, A.; Ahmed, E.; Nainar, A.S.M.; Akim, N.M.; Imran, M. Deep learning and big data technologies for IoT security. Comput. Commun. 2020, 151, 495–517. [Google Scholar] [CrossRef]
- Besada, J.A.; Bernardos, A.M.; Bergesio, L.; Vaquero, D.; Campaña, I.; Casar, J.R. Drones-as-a-service: A management architecture to provide mission planning, resource brokerage and operation support for fleets of drones. In Proceedings of the 2019 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kyoto, Japan, 11–15 March 2019; pp. 931–936. [Google Scholar]
- Abdallah, A.; Ali, M.Z.; Mišić, J.; Mišić, V.B. Efficient Security Scheme for Disaster Surveillance UAV Communication Networks. Information 2019, 10, 43. [Google Scholar] [CrossRef] [Green Version]
- Eng-Wilmot, G.L. Universal People: Audiovisual Experiments in Black Science Fiction, 1980–1986; University of California: Irvine, CA, USA, 2017. [Google Scholar]
- Radoglou-Grammatikis, P.; Sarigiannidis, P.; Lagkas, T.; Moscholios, I. A Compilation of UAV Applications for Precision Agriculture. Comput. Netw. 2020, 172, 107148. [Google Scholar] [CrossRef]
- Maes, W.H.; Steppe, K. Perspectives for remote sensing with unmanned aerial vehicles in precision agriculture. Trends Plant Sci. 2019, 24, 152–164. [Google Scholar] [CrossRef] [PubMed]
- Ren, H.; Zhao, Y.; Xiao, W.; Hu, Z. A review of UAV monitoring in mining areas: Current status and future perspectives. Int. J. Coal Sci. Technol. 2019, 6, 1–14. [Google Scholar] [CrossRef] [Green Version]
- Gheisari, M.; Esmaeili, B. Applications and requirements of unmanned aerial systems (UASs) for construction safety. Saf. Sci. 2019, 118, 230–240. [Google Scholar] [CrossRef]
- Manickavasagam, B.; Amutha, B. Analysis of efficient unmanned aerial vehicles to handle medical emergency data transmission surveillance system by using wireless body area network. Comput. Commun. 2020, 152, 19–33. [Google Scholar] [CrossRef]
- Mukherjee, A.; Dey, N.; De, D. EdgeDrone: QoS aware MQTT middleware for mobile edge computing in opportunistic Internet of Drone Things. Comput. Commun. 2020, 152, 93–108. [Google Scholar] [CrossRef]
- Chamola, V.; Hassija, V.; Gupta, V.; Guizani, M. A comprehensive review of the COVID-19 pandemic and the role of IoT, drones, AI, blockchain, and 5G in managing its impact. IEEE Access 2020, 8, 90225–90265. [Google Scholar] [CrossRef]
- Karakostas, I.; Mademlis, I.; Nikolaidis, N.; Pitas, I. Shot type constraints in UAV cinematography for autonomous target tracking. Inf. Sci. 2020, 506, 273–294. [Google Scholar] [CrossRef]
- Matternet Launches Operations in Berlin. Available online: https://mttr.net/ (accessed on 22 December 2020).
- Lacey, J. Technology for Good: Stratus Information Systems Helps Matternet Drones Deliver Critical Medical Supplies. Available online: https://blogs.cisco.com/partner/stratus-information-systems-helps-matternet-drones-deliver-critical-medical-supplies (accessed on 22 December 2020).
- HiveMQ‘s Reliable IoT Communication Enables Real-Time Monitoring of Matternet’s Autonomous Drones. Available online: https://www.hivemq.com/case-studies/matternet/ (accessed on 22 December 2020).
- Insights, A. New Company ‘Aria Insights’ Turns Drone Collected Data into Actionable Intelligence. Available online: https://www.officer.com/command-hq/technology/security-surveillance/uav-uas/press-release/21041425/aria-insights-formerly-known-as-cyphy-works-inc-persistent-aerial-solutions-aria-insights-uses-ai-to-turn-drone-collected-data-into-actionable-intelligence (accessed on 22 December 2020).
- Lillian, B. DroneSmartX Develops Cloud-Based UAV Attachment for Data Collection. Available online: https://unmanned-aerial.com/dronesmartx-develops-cloud-based-uav-attachment-for-data-collection (accessed on 20 December 2020).
- Dynamics, H. DBX Automates Various Professional Drones. Available online: https://www.h3dynamics.com/security (accessed on 23 December 2020).
- Almulhem, A. Threat modeling of a multi-UAV system. Transp. Res. Part A Policy Pract. 2020, 142, 290–295. [Google Scholar] [CrossRef]
- Zhang, Y.; He, D.; Li, L.; Chen, B. A lightweight authentication and key agreement scheme for Internet of Drones. Comput. Commun. 2020, 154, 455–464. [Google Scholar] [CrossRef]
- Deebak, B.; Al-Turjman, F. A smart lightweight privacy preservation scheme for IoT-based UAV communication systems. Comput. Commun. 2020, 162, 102–117. [Google Scholar] [CrossRef]
- Wang, E.K.; Chen, C.-M.; Wang, F.; Khan, M.K.; Kumari, S. Joint-learning segmentation in Internet of drones (IoD)-based monitor systems. Comput. Commun. 2020, 152, 54–62. [Google Scholar] [CrossRef]
- Nouacer, R.; Hussein, M.; Espinoza, H.; Ouhammou, Y.; Ladeira, M.; Castiñeira, R. Towards a Framework of Key Technologies for Drones. Microprocess. Microsyst. 2020, 77, 103142. [Google Scholar] [CrossRef]
- Sharma, B.; Srivastava, G.; Lin, J.C.-W. A bidirectional congestion control transport protocol for the internet of drones. Comput. Commun. 2020, 153, 102–116. [Google Scholar] [CrossRef]
- Bera, B.; Das, A.K.; Sutrala, A.K. Private blockchain-based access control mechanism for unauthorized UAV detection and mitigation in Internet of Drones environment. Comput. Commun. 2020, 166, 91–109. [Google Scholar] [CrossRef]
- Weng, L.; Zhang, Y.; Yang, Y.; Fang, M.; Yu, Z. A mobility compensation method for drones in SG-eIoT. Digit. Commun. Netw. 2020, 7, 196–200. [Google Scholar] [CrossRef]
- Dawaliby, S.; Aberkane, A.; Bradai, A. Blockchain-based IoT platform for autonomous drone operations management. In Proceedings of the 2nd ACM MobiCom Workshop on Drone Assisted Wireless Communications for 5G and Beyond, London, UK, 25 September 2020; pp. 31–36. [Google Scholar]
- Gallego-Madrid, J.; Molina-Zarca, A.; Sanchez-Iborra, R.; Bernal-Bernabe, J.; Santa, J.; Ruiz, P.M.; Skarmeta-Gómez, A.F. Enhancing Extensive and Remote LoRa Deployments through MEC-Powered Drone Gateways. Sensors 2020, 20, 4109. [Google Scholar] [CrossRef] [PubMed]
- Rehman, A.; Paul, A.; Ahmad, A.; Jeon, G. A novel class based searching algorithm in small world internet of drone network. Comput. Commun. 2020, 157, 329–335. [Google Scholar] [CrossRef]
- Chang, Y. An enhanced rerouting cost estimation algorithm towards internet of drone. J. Supercomput. 2020, 76, 1–14. [Google Scholar] [CrossRef]
- Huang, H.; Savkin, A.V.; Ding, M.; Kaafar, M.A. Optimized deployment of drone base station to improve user experience in cellular networks. J. Netw. Comput. Appl. 2019, 144, 49–58. [Google Scholar] [CrossRef]
- Yao, J.; Ansari, N. QoS-aware power control in internet of drones for data collection service. IEEE Trans. Veh. Technol. 2019, 68, 6649–6656. [Google Scholar] [CrossRef]
- Alladi, T.; Chamola, V.; Sahu, N.; Guizani, M. Applications of blockchain in unmanned aerial vehicles: A review. Veh. Commun. 2020, 23, 100249. [Google Scholar] [CrossRef]
- Faughnan, M.S.; Hourican, B.J.; MacDonald, G.C.; Srivastava, M.; Wright, J.-P.A.; Haimes, Y.Y.; Andrijcic, E.; Guo, Z.; White, J.C. Risk analysis of unmanned aerial vehicle hijacking and methods of its detection. In Proceedings of the 2013 IEEE Systems and Information Engineering Design Symposium, Charlottesville, VA, USA, 26 April 2013; pp. 145–150. [Google Scholar]
- Idries, A.; Mohamed, N.; Jawhar, I.; Mohamed, F.; Al-Jaroodi, J. Challenges of developing UAV applications: A project management view. In Proceedings of the 2015 International Conference on Industrial Engineering and Operations Management (IEOM), Dubai, United Arab Emirates, 3–5 March 2015; pp. 1–10. [Google Scholar]
- Nikolic, J.; Burri, M.; Rehder, J.; Leutenegger, S.; Huerzeler, C.; Siegwart, R. A UAV system for inspection of industrial facilities. In Proceedings of the 2013 IEEE Aerospace Conference, Big Sky, MT, USA, 6 January 2013; pp. 1–8. [Google Scholar]
- Mohamed, N.; Al-Jaroodi, J. Service-oriented middleware for collaborative UAVs. In Proceedings of the 2013 IEEE 14th International Conference on Information Reuse & Integration (IRI), San Francisco, CA, USA, 14–16 August 2013; pp. 185–192. [Google Scholar]
- Kriz, V.; Gabrlik, P. Uranuslink-communication protocol for uav with small overhead and encryption ability. IFAC-PapersOnLine 2015, 48, 474–479. [Google Scholar] [CrossRef]
- Liu, Y.; Dai, H.-N.; Wang, Q.; Shukla, M.K.; Imran, M. Unmanned aerial vehicle for internet of everything: Opportunities and challenges. Comput. Commun. 2020, 155, 66–83. [Google Scholar] [CrossRef] [Green Version]
- Tran, T.X.; Hajisami, A.; Pandey, P.; Pompili, D. Collaborative mobile edge computing in 5G networks: New paradigms, scenarios, and challenges. IEEE Commun. Mag. 2017, 55, 54–61. [Google Scholar] [CrossRef] [Green Version]
- Stergiou, C.; Psannis, K.E.; Kim, B.-G.; Gupta, B. Secure integration of IoT and cloud computing. Future Gener. Comput. Syst. 2018, 78, 964–975. [Google Scholar] [CrossRef]
| Survey Paper | Year of Publication | Highlight | Comparison of Current Research Works in Terms of | Domain |
|---|---|---|---|---|
| This work | 2021 | Comprehensive study covering requirements, taxonomy, recent advances, and challenges of future research trends | Drone applications Commercial case studies Recent advances in IoD | IoD |
| Boccadoro et al. [8] | 2021 | Drone adoption for the economy and society | Drone applications | IoD |
| Rejeb et al. [9] | 2021 | Humanitarian drones | The humanitarian drone’s capabilities and performance | Drones |
| Yahuza et al. [10] | 2021 | Evaluate IoD network security and privacy | Drones classification | IoD |
| Ayamga et al. [11] | 2021 | Review the advancements in agricultural, military, and medical drones | No comparison table | Drones |
| Merkert and Bushell et al. [12] | 2020 | Need for more policy and management response to drone usage | Countries and regions contributing | Airborne drones |
| Zaidi et al. [13] | 2020 | State of the art of IoFT | IoT, FANET, and IoFT MANET, VANET, UANET, and FANET UAV system, multi-UAV system, and FANET | IoFT |
| Yaacoub et al. [14] | 2020 | Analysis to assist ethical hackers in recognizing the current vulnerabilities of UAVs | Frequencies of drones communication Drones cyber-attacks Analytical drone review | Unmanned Aerial Vehicles |
| Al-Turjman et al. [15] | 2020 | Review the performance assessment techniques and cybersecurity applications | Flight stacks Objective, constraint, area, and assessment approach Mass simulators Testbeds | IoT networks |
| Alsamhi et al. [16] | 2019 | Improve smart cities’ real-time implementation | Surveys and current work Drone and IoT for smart cities | Smart cities |
| Fotouhi et al. [7] | 2019 | Overview of advancements supporting compatibility of UAVs into mobile networks | Characteristics of drones Comparison of aerial placement | UAV Cellular |
| Wazid et al. [4] | 2018 | Define the strengths and limitations of user authentication of IoD | Authentication schemes Communication overheads Security features and functionality | IoD |
| Bagloee et al. [17] | 2016 | Vehicles’ connection and infrastructure of future growth of AV | No comparison table | Autonomous vehicles |
| Gharibi et al. [1] | 2016 | Investigate and extract key concepts of networks | No comparison table | IoD |
| Case Study | Middleware Strategy | Data Sharing | Supported Applications and Services |
|---|---|---|---|
| Matternet | Cloud-based | Cloud-based | Healthcare and logistics |
| Aria Insights | Service-based | Distributed | Oil and Gas |
| DroneSmartX | Cloud-based | Cloud-based | Agriculture Energy Manufacturing Oil and Gas |
| H3 Dynamics | Cloud-based | Cloud-based | Real Estate Mining Oil and Gas |
| References | Architectural Organization | Middleware Strategies | Solution Type | Proposed Solution | Supported Applications and Services |
|---|---|---|---|---|---|
| Almulhem [63] | Communication protocol | Cloud-based | Model | Provide a holistic view of threats affecting an IoD scheme | IoD system |
| Zhang et al. [64] | Component | Service-based | Scheme | Attain security and withstand various attacks | IoD architecture |
| Nikooghadam et al. [23] | Communication protocol | Service-based | Scheme | Develop authentication for drones to ensure surveillance of smart city | Smart City Surveillance |
| Deebak and Al-Turjman [65] | Communication protocol | Service-based | Scheme | Reduce the computation expense of the authentication protocol | IoD infrastructure |
| Bera et al. [22] | Communication protocol | Service-based | Scheme | Secure data management system between entities of IoD communication | IoD environment |
| Wang et al. [66] | Communication protocol | Service-based | Scheme | Improve the accuracy of object segmentation | IoD |
| Tian [2] | Communication protocol | Service-based | Framework | Secure authentication to protect privacy of UAV | IoD communication |
| Ever [3] | Communication protocol | Service-based | Framework | Secure authentication of UAV environment | IoD applications |
| Choudhary et al. [25] | Communication protocol | Service-based | Framework | Enhance IoD security aspects | Military IoD |
| Nouacer et al. [67] | Component | Cloud-based | Framework | Secure architectures based drone for software and hardware | IoD architecture |
| Sharma et al. [68] | Communication protocol | Service-based | Protocol | Minimize packet drops, to maintain fairness and boost energy quality | Wireless Sensor Network |
| Mukherjee et al. [54] | Communication protocol | Cloud-based | Mechanism | Enhance protocol | EdgeDrone |
| Bera et al. [69] | Communication protocol | Cloud-based | Mechanism | Access control for unauthorized UAV | IoD environment |
| Weng et al. [70] | Communication protocol | Service-based | Method | Improve mobility compensation of drones | IoT drone |
| Dawaliby et al. [71] | Component | Cloud-based | Architecture | Handle IoT drone operations | IoT drone |
| Gallego-Madrid et al. [72] | Component | Cloud-based | Architecture | Provide an intermediate processing layer running (VNF) | Drone Gateways |
| Koubâa et al. [28] | Communication protocol | Cloud-based | Architecture | Control, monitor, and communicate over Internet with drones | IoD |
| Rehman et al. [73] | Communication protocol | Service-based | Algorithm | Enable information search to explore the ranking of services | Drone network |
| Chang et al. [74] | Communication protocol | Service-based | Algorithm | Improve cost estimation for multiple in-flight rerouting | IoD |
| Huang et al. [75] | Communication protocol | Cloud-based | Algorithm | Support analysis of computational complexity | IoD |
| Yao et al. [76] | Communication protocol | Service-based | Algorithm | Minimize the energy consumption of the drone | IoD |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abdelmaboud, A. The Internet of Drones: Requirements, Taxonomy, Recent Advances, and Challenges of Research Trends. Sensors 2021, 21, 5718. https://doi.org/10.3390/s21175718
Abdelmaboud A. The Internet of Drones: Requirements, Taxonomy, Recent Advances, and Challenges of Research Trends. Sensors. 2021; 21(17):5718. https://doi.org/10.3390/s21175718
Chicago/Turabian StyleAbdelmaboud, Abdelzahir. 2021. "The Internet of Drones: Requirements, Taxonomy, Recent Advances, and Challenges of Research Trends" Sensors 21, no. 17: 5718. https://doi.org/10.3390/s21175718
APA StyleAbdelmaboud, A. (2021). The Internet of Drones: Requirements, Taxonomy, Recent Advances, and Challenges of Research Trends. Sensors, 21(17), 5718. https://doi.org/10.3390/s21175718






