Machine Learning for Authentication and Authorization in IoT: Taxonomy, Challenges and Future Research Direction
Abstract
:1. Introduction
1.1. Current Issues and Motivation
1.2. Authentication and Authorization in IoT
1.3. Existing Reviews
1.4. Contribution
- An overview of security and privacy issues with a taxonomy related to various authentication and authorization schemes in IoT.
- An overview of various types of attacks in each layer of IoT architecture leveraging a specific IoT AA mechanism.
- Recommendations for enhancing IoT authentication scheme for safe communications based on ML.
- An assessment of countermeasures of IoT security issues with ML for AA.
- Performance evaluation metrics for IoT AA for general and ML-based schemes are identified.
- Open issues, challenges, and future work recommendations for secure IoT system and services.
1.5. Article Organization
2. Machine Learning for IoT Security
2.1. Supervised Learning
2.2. Unsupervised Learning
2.3. Reinforcement Learning
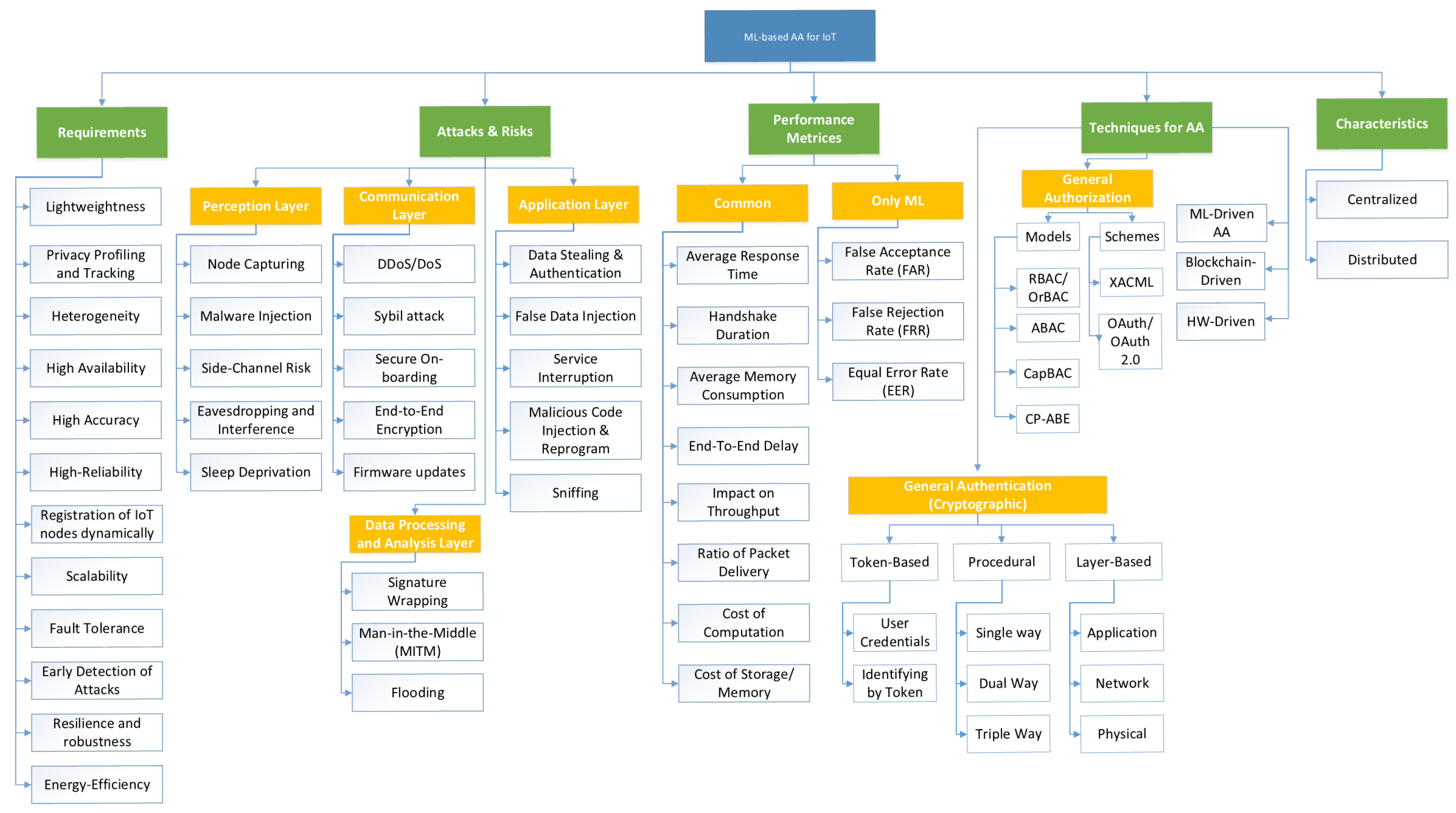
3. Taxonomy of Ml-Based AA for IoT
- AA-based IoT Security Requirements
- Attacks and Risks for AA in IoT
- Performance Evaluation Metrics
- Techniques used for AA
- Characteristics of the AA schemes
3.1. AA-Based IoT Security Requirements
- Privacy Profiling and Tracking: Combining an identification with a specific person is a vulnerability, which may escalate to privacy profiling and tracking [29]. Therefore, one of the critical problems is the dis-allowance of IoT operation, and the security system must be responsible for protecting the clients’ privacy.
- Heterogeneity: Within IoT, nodes and networks are heterogeneous. An essential requirement for the AA scheme must have heterogeneity because of end device characteristics. Heterogeneity in AA schemes will solve issues in multiple types of devices.
- High Availability: The high availability of the AA Scheme confirms that all network services are available to the greatest possible extent, even though threats are occurring within the IoT network [30].
- High Accuracy: A high degree of accuracy level of any AA scheme is required for accessing any IoT node and the network itself [31]. A high degree of accuracy level during authentication and authorization will ensure that the whole system is highly secure.
- High Reliability: One of the key requirements of any authentication and authorization schemes is high reliability. The method relies on its success rate. It confirms that all functions in the IoT network are operating correctly during the specified duration [32].
- Registration of IoT Nodes Dynamically: IoT requires networks with shorter life cycles than general computing networks, while IoT devices can dynamically be added and removed from systems [33].
- Scalability: A range of network scalability approaches is available to provide support to IoT devices, including the publish-subscribe protocols such as MQTT [34]. These scalability features should be combined with the security architecture.
- Fault Tolerance: Fault tolerance is the ability to continue working, even after one or more devices are compromised. If an end-device of the group such as edge node cannot authenticate with the group’s distributor such as cloud, the group loses its identity. This loss of identity causes the authentication failure of the other group devices. Therefore, suitable fault tolerant system architectures should be implemented [35].
- Early Detection of Attacks: The IoT network requires schemes and protocols after an attack is performed to guarantee that the attack is identified as quickly and efficiently before an attack does significant harm and spreads across the network. Moreover, the schemes are also needed to be tolerant to intrusions and various hostile attacks.
- Resilience and Robustness: Due to agility, IoT node faults and the rise in the number of attack vectors, the IoT AA system should be resilient to attacks and must be robust. Security networks should also be able to discover and repair faultiness by immediately taking the necessary steps.
- Energy Efficiency: Energy efficiency is an important metric to assess the lightweightness aspect of an AA system, as it is proportionate to the distance for the communicating nodes [36]. Besides that, lightweight programs with little code or less memory consumption are preferred in an AA system implementation.
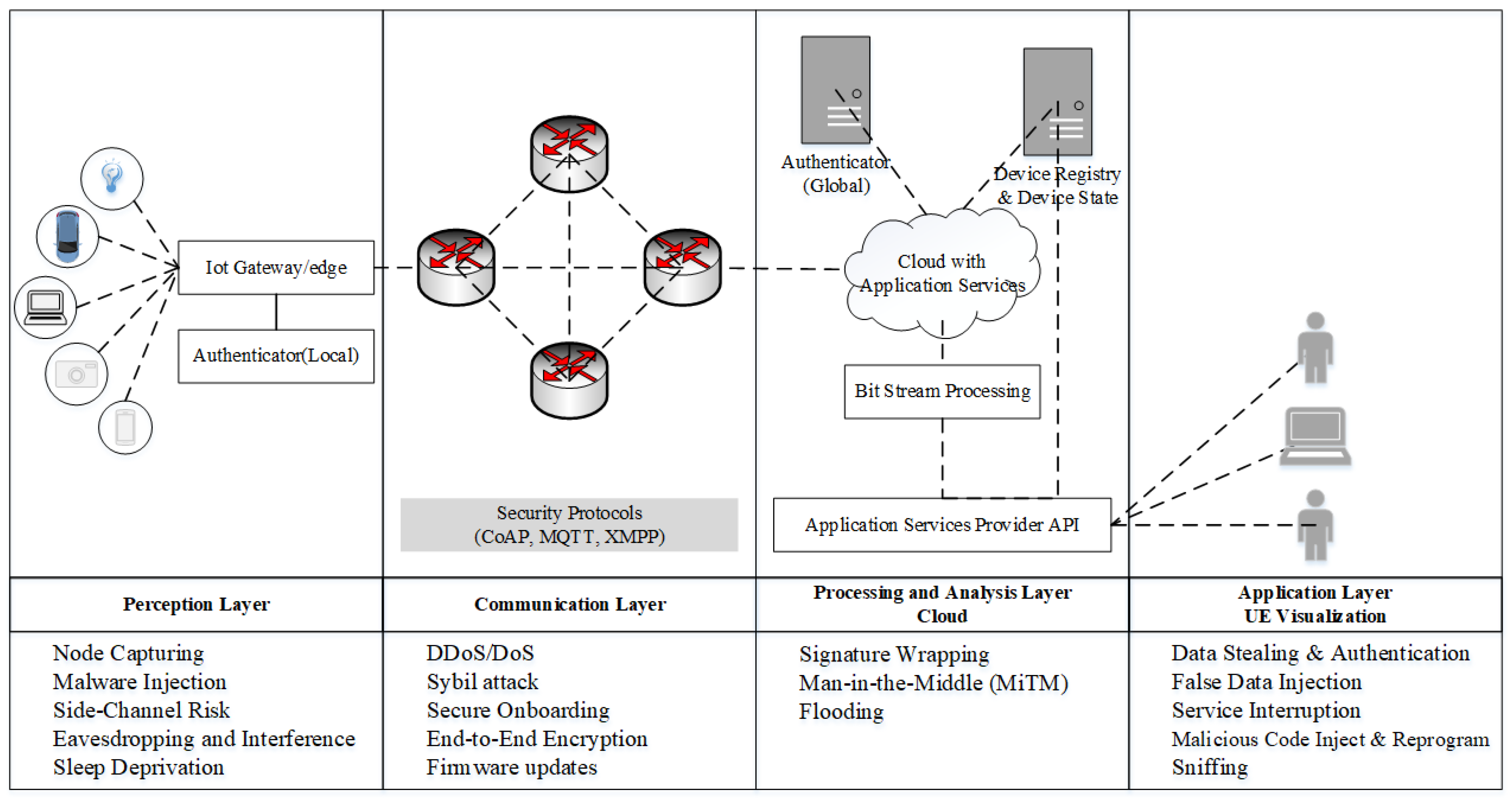
3.2. Attacks and Risks for AA in IoT
3.2.1. Perception Layer
- Node Capturing: IoT systems consist of many limited resource sensor and actuator nodes that are vulnerable to node capture attack. In such an attack, the attacker gains full control over the key node, such as the gateway. The attacker will then leak all information between sender and receiver, exposing the whole network [37].
- Malware Injection: The risks involve the injection of malware into the memory of the node by an external user. In general, IoT node firmware or software is modified to enable adversaries to insert malware to execute such unintended functions or even attempting to access the entire IoT network [38].
- Side-Channel Risk: In addition to direct node attack risks, separate side-channel risks may contribute to sensitive data leakage. These risks may depend on power use, laser attacks, time attacks, or electromagnetic attacks, which are also conceivable [39]. Modern chips take charge of numerous countermeasure steps in the cryptographic modules to avoid risks from this side channel.
- Eavesdropping and Interference: Many IoT systems consist of specific nodes distributed in open environments. An external party may secretly overhear information exchanged via different channels, such as a communication network, or authentication, in certain IoT applications, which might not be allowed [40].
- Sleep Deprivation: The attackers attempt to drain the battery from the low-powered IoT-edge devices during an attack. This can be accomplished by using infinite loops in the edge devices or deliberately increasing the device power consumption by using more power for data transmission [41].
3.2.2. Communication Layer
- DDoS/DoS: Many IoT devices in the IoT network can be used to launch DDoS attacks. This is used to exploit or breach the security of target servers. The Mirai botnet used this attack from numerous distributed nodes to flood the system by persistent transmission [4].
- Sybil Attack: This attack offers many separate identities for an individual node. For example, if there are many Sybil nodes in the same network, several requests from the legitimate nodes are rejected due to Sybil nodes in the same network [13]. Moreover, Sybil attack is possible from every layer of the IoT architecture.
- Secure Onboarding: In case of the installation of a new device in an IoT system, encryption keys must be protected. The gateways can be attacked and searched by the human being, especially during the embedded phase, to catch the encryption keys [42].
- End-to-End Encryption: To ensure the confidentiality of the data, end-to-end protection is required. For example, Zigbee and Zwave protocols allow encryption, but it is not end-to-end encryption. The gateways are needed to decrypt and re-encrypt messages to convert the details from one protocol to another [43]. This gateway stage decryption renders data prone to privacy infringement.
- Firmware Updates: Most IoT devices are resource-limited, so they are unable to access and install software updates with the user interface or computing resources [42]. In this circumstance, gateways are used to download and apply firmware updates by gaining access through authenticating and authorizing.
3.2.3. Data Processing and Analysis Layer
- Signature Wrapping: XML signatures are included in the cloud servers to maintain service integrity [44]. The intruder breaks the signature algorithm during a signature wrapping attack and may execute or change the eavesdropped information, utilizing the Simple Object Access Protocol (SOAP) vulnerabilities.
- Man-in-the-Middle (MiTM): The MQTT protocol employs the MQTT Broker as a publishing subscriber communication model for customers and effectively acts as a proxy. In MITM, the attacker may gain control of the MQTT broker by becoming an intermediary node in the middle and trying to tap the information of other nodes without knowing the potential client nodes [13]. Similarly, many IoT message queueing protocols, such as SMQTT, AMQP, CoAP, M3DA, and XMPP [45], can be exploited using MITM attack.
- Flooding: This flooding is fundamentally the same as the cloud DoS attack, impacting service efficiency (QoS) by submitting numerous queries [13]. The strain on the cloud servers will have a significant effect on cloud-based systems.
3.2.4. Application Layer
- Data Stealing: Many sensitive and private details are protected by IoT applications. Transit data are even more vulnerable to attacks than data at rest. A lot of data movement occurs in IoT applications. When such systems are vulnerable to data stealing threats, individuals would be hesitant to disclose their private data in IoT systems [46].
- False Data Injection: If the node has been captured, the intruder can insert erroneous information into the IoT application that can generate false results and cause IoT application to fail. DDoS attacks may use this critical approach too [47].
- Service Interruption: Such threats are often classified in current literature as unauthorized disruption activities or DDoS attacks. There have been many cases in which IoT systems have been targeted. These threats temporarily blocked legitimate customers from accessing services on IoT infrastructure by deliberately exploiting servers or the network.
- Malicious Code Injection and Reprogram: Attackers are typically used to hacking through an IoT device or network utilizing the fastest or shortest route. An effective XSS attack can cause the device to hijack an IoT account and paralyze the IoT system if it is prone to malicious scripts. Still, the attackers may try to reprogram IoT objects remotely using flaws in the logic of the program [48].
- Sniffing: To access sensitive user data, an intruder can use a sniffer system to monitor network traffic in IoT applications when protection protocols are not enough to prevent it [49].
3.3. Evaluation Metrics for Authentication and Authorization (AA)
3.3.1. General AA Evaluation Metric
- Average Response Time: The time required to reply to the client request is the response time for a server node or gateway node (GWN). Several variables influence this, such as server architecture, the number of clients, the bandwidth of the network, volume of requests, request types and calculation time. Equation (1) can be used to measure first response time.Here, indicates the total time taken for the response, indicates the first response time, and indicates the client’s time of request. The average response time will be determined by the mean of all response times, as seen in Equation (2).where the average response time is , the number of simultaneous users is denoted by . The volume of requests that a server gets is . is the average time of thought (in milliseconds). It is necessary to use think time in the equation to achieve exact response time.
- Handshake Duration: Handshaking is a negotiating mechanism between two parties (e.g., client, actuator, sensor node, server or other nodes) in an IoT network. Handshaking occurs by finishing a two-round trip message. The server identification of the client and the server request recognize [50]. The handshake duration can be denoted by and shall be calculated by Equation (3) at the client-end.where the time taken from a complete session request is denoted by , the response time of the client is indicated by and server processing time denoted as . Random handshakes between the client node and server node are performed to determine the duration of the handshake. Based on the handshake duration, the standard deviation is calculated to observe the variability.
- Average Memory Consumption: IoT is a network of primarily wireless sensors, which are constrained in memory and other resources. Therefore, in specialised and autonomous sensor networks, memory usage optimization is critical [51]. The usage of memory varies at different levels in IoT applications, including the user, sensor, gateway, etc.
- End-to-End Delay: The average time for delivering packets from sending node to the receiving node is defined as an end-to-end delay and denoted by . Using Equation (4), the can be computed.Here, packet number is denoted as i and the number of received packets is denoted as . Similarly, denotes the received timestamp and denotes the sent timestamp for i-th packet. is directly proportional to the number of nodes in an IoT network.
- Impact on Throughput: The throughput can be defined as the amount of data passing in a unit of time through a node. In [36], the authors demonstrated that the output could be represented by Equation (5).Here, the impact on throughput is denoted as , while denotes the received quantity and denotes the length of the i-th packet, and denotes the duration to complete the simulation.
- Ratio of Packet Delivery: Packet delivery ratio denotes the number of packets transmitted by the sending node and the number of packets successfully received at the receiving node. It depends on several variables, such as network setup, system capacity and bandwidth. Equation (6) can be used in the calculation of the packet delivery ratio.where is the packet delivery ratio. The total number sent by the sending node is denoted as and the number of packets received by the receiving node is . When a message is transmitted through the networks, energy is consumed. When more packets are transferred across the nodes, the energy consumption will increase accordingly [36]. So, if the energy level is below a threshold or reaches the node constraints, the packet can be discarded at the edge or cloud.
- Cost of Communication: As stated in the literature, the number of interactions during authentication will differ and depends on the protocols in use. Moreover, it will require different phases and a specific number of messages to establish communication. Furthermore, the scheme involved in the AA process required at least four messages to complete authentication, such as messages transfer between the sensor, GWN, and the user or the central node to establish a secure communication through authentication [36,52,53,54,55,56]. Therefore, the number of messages varies, and different communicating messages carry different information. Due to this, there must be a consideration for communication costs, since multiple standards are subject to varying threshold values. For example, the networking protocol of IEEE 802.15.4 accepts 127 bytes. In comparison, the standards IEEE 802.15.6 carry a limit of 255 bytes of frame length.
- Cost of Computation: Computation also relies on protocols within the IoT network. As most network devices are computationally limited, computing large data or information of IoT networks is not feasible. Therefore, protocol architects aim to build lightweight IoT network authentication protocols. In this regard, the principle of hash, XOR, and concatenation has been used by researchers to protect the message across the network [51,57]. In IoT, authentication schemes, such as ECC-based and Fuzzy extractor, are also enforced for authenticating the identity of IoT devices [58].
- Cost of Storage/Memory: Protocols employ various kinds of schemes to implement IoT authentication. One of the common strategies is a smart card. A smart card can store some data, such as sensor information, login credentials, and gateway node information [59,60]. To accomplish authentication, multiple protocols use various functions for improving efficiency, and among them, one of the significant performance metrics is the cost of storage/memory.
3.3.2. ML-Based AA Evaluation Metric
- False Acceptance Rate (FAR): The ML-based AA technique may incorrectly recognize the characteristic of deceivers based on the classification threshold preference. The FAR is the threshold, which depends on falsely accepted characteristics, divided by the number of all deceiver characteristics. It is also known as the false alarm rate. The value will be between 0 and 1. When all the false characteristics are accepted as valid, then the value will be “1”, and the value will be “0” if none of the wrong features are considered valid [61]. Equation (7) presents the formula to calculate FAR.where is the number of false acceptance cases and N is the number of attempts.
- False Rejection Rate (FRR): If an overly high classification criterion is used for the ratings, certain trends for individual characteristics are wrongly denied. Depending on the threshold value, none or all characteristics are denied falsely. The false rejection rate (FRR) is the number of rejected characteristics divided by the total number of individual characteristics [62,63]. Equation (8) presents the formula to calculate FAR.where is the number of false rejection cases and N is the number of attempts.
- False/True Positive: An actual result under which the model accurately forecasts the positive feature vector is truly positive. Likewise, an actual result in which the model wrongly forecasts the positive feature vector is a false positive [24].
3.4. Techniques for AA
3.4.1. General IoT Authentication Schemes
3.4.2. Ml Based Authentication Schemes
3.4.3. General IoT Authorization Schemes
- Attribute-Based Model In the ABAC-based model, the object and the subject are both defined by the attributes function [96]. The client is given a suitable right of access in the ABAC model in compliance with his characteristics. Recent studies mainly concentrated on maintaining user privacy because attributes could include user private information whose leaking significantly hinders ABAC expansion. In [97] the authors introduced a privacy-preserving attribute-based access control (P-ABAC) scheme to avoid data leakage. In P-ABAC user-side manages the critical attributes with homomorphic encoding. With the assistance of stable ciphertext-based homomorphic multi-party computational encoding techniques, the authorization mechanism can also make error-free decisions about access by the received attribute without any knowledge about privacy.
- Role-Based Model The role-based access control (RBAC) offers system permissions that stipulate access for the users to services depending on individual roles and encourages security principles, such as task separation, administrative segregation of administrative roles, and fewer privileges. When the tools extend or access rules span multiple administrative realms, the RBAC model alone has a function eruption dilemma. A service-based RBAC model will be able to run in more IoT scenarios. Moreover, an expanded RBAC model using contextual knowledge, which can be used in detail as constraints to achieve a more scalable, modular, and lightweight access control mechanism. In [98], Barka et al. recommended that RBAC be implemented in smart entities across the Internet as a Web of Things (WoTs) access control mechanism.The organizational role-based access control (ORBAC) model is an extension of the RBAC model. It introduces a new dimension to the concept of “organization”. In the trust-ORBAC model, the ORBAC model uses the concept of trust management. Trust-ORBAC defines two dynamic thrust vectors, one for the organization and the other for users with various parameters. Moreover, the Tr-ORBAC model in which trust is embedded to improve the cooperation of various organizations and avoid malicious behaviour. In the SmartOrBAC scheme, the problem is grouped into smaller functional layers. SmartOrBAC distributes the processing costs between restricted and less restricted equipment to ensure that some users can access data in advance in the context of the task/action plan by restricting access to confidential information beyond the control of the system administrator. In [99], Guesmia et al. suggested an expansion of the OrBAC paradigm with a non-monotonic logic of the temporal representation. This logic may be a centralized plan to reflect the policies formally. The schedule contains a variety of assignments ordered, and in specific situations, make exceptions. The proposed OrBAC model can dynamically evaluate the required action sequence according to the data environment patterns while the access request is generated.In [100], the authors proposed a framework of access control and verification schemes based on location-controlled functions named location-constrained roles-based access control (LCRBAC). The authors describe cyberspace and physical space as a static topology for the LCRBAC scheme by describing cyber objects and physical object dynamic behaviors. The proposed scheme is often focused on the verification findings on a labeled transfer device to allow cyber-physical experiences via the reaction policy and principle.
- Capability Based Model In capability-based access control (CapBAC), users provide access through an authorization sequence and token (such as authorization key, service ticket). Identity management is not a key function that offers tremendous benefits, especially where clients can access interdisciplinary scenarios. The comparison between ACL and CapBAC is that access control depends on the central server in the ACL model. On the other hand, the CapBAC model has leaves access management responsibility to the client. The BlendCAC concept, which is a decentralized CapBAC blockchain operating model, was proposed by Ronghua Xu [101]. A clear identity-based token management approach for access control, which uses a clever contract to register, spread, and revoke the authorization, is proposed within the BlendCAC model. In a cloud-based authentication scheme, users can access IoT services and command multiple smart ubiquitous environments through IoT cloud. In the case of large IoT schemes, Xu et al. [102] introduced the Federated CapBAC Mechanism (FedCAC), which is a token management approach focused on the identification that requires registration, dissemination, and revocation of the entry.
3.4.4. Ml-Based Authorization Schemes
3.5. Characteristics of IoT AA Schemes
3.5.1. Centralized AA
3.5.2. Distributed AA
4. Open Issues, Challenges, and Future Directions
- Resource Constraint and Robustness of Authentication Protocols: Sensors are the end nodes that are limited in resources (limited battery capacity, processing resources). The protocols need to be lightweight and move between resource usage and safety. Moreover, the structure for IoT authentication mechanisms, especially for resource-restricted and the environment of IoT framework, should take into account low computation costs. This reinforces the need for the creation of authentication systems to implement lightweight encryption algorithms and conventions. The authentication protocols must have robustness against potential attacks, including Sybil, node capture, interpret, identification of passwords, message breaches, brute forces, broker, protection, collision, and text selection.
- Authorization for Each Service: User identities are used to access one or more services, but some of these identities can only be used by a specific service. Therefore, a scheme must provide a mechanism to access the device, depending on the different services that claim to access and use identity data. Thus, user information exchange between different system services is not allowed or should follow the authorization policy of individual services.
- Datasets Unavailability: Powerful ML-driven schemes required massive datasets. The performance of different ML algorithms must be evaluated and compared by credible datasets from actual physical environments. The data include personal and vital details that distinguish the individuals and their actions and personality. For example, body area networks (BAN) and other IoT technologies can violate consumer privacy, and smart home data can reveal personal actions and behaviours. It is therefore vital for developers not to jeopardize consumer safety by the data used by ML-driven techniques. To date, the anonymity methods must need to be considered before it is used for analytics as the demonstration showed that the techniques for anonymity are hacked. Training models may be jeopardized by inserting fake data. It may be difficult to gather data while protecting privacy and confidentiality. Questions like how ML algorithms should be implemented, and which degree of privacy ML algorithms can uphold need to be answered. Therefore, it is important to examine data security and user privacy conservation techniques in ML-driven analytics for IoT networks. Actual IoT scenarios cannot completely be encompassed in the data produced by simulations. Production of synthetic data can become quite costly for computing and training.
- Sharing Information to Reduce Overhead: The overhead of authentication protocols is a key factor in communication, particularly in resource-restricted devices. Fewer messages should be shared between communication partners. Owing to the limited capacity of IoT devices, the volume of the message should be as low as possible.
- Trust Relationship among Services: IoT security system needs to be flexible as it has to support multiple nodes and attach additional nodes. All three layers of the IoT system (application, communication, and perception layer) will provide authentication service. The user can have and use different identities to access more IoT services. Therefore, the AA must introduce devices in the authentication phase using a precise selection of identities automatically or semi-automatically. The trust management scheme must manage multiple relationships to select the identities required in the context of access to the service. Therefore, the challenge of authenticating multiple shared devices is expressed by a single user who uses more than one service at a time. The problem can be solved by SSO in SAML, OAuth, etc. The use of devices shared by different users is another important aspect. It is currently addressed through the so-called “sandbox” techniques to differentiate users in the IoT environment. A D2D authentication function is represented as the authentication of multiple devices in an IoT network. An application user device can access all its devices and individual services after performing initial authentication on a single device and authorized access services through trust relationships among related devices. Access to a connected device will allow the collection of contextual metadata and sensor node data in centralized services management.
- Easy, Time & Location Driven Authentication: Throughout the design of IoT authentication frameworks that enable several applications to be accessed from one single sign-on mechanism and thus minimize user interface repetition, the complexity of the application throughout IoT networks must be addressed. Nevertheless, the machine must learn about the ownership of the device and the operator to whom it is linked to enabling efficient contact with this program. Alternatively, it is necessary to reply promptly to the sender, as authentication needs to emerge on time. Protocols often use timestamps and session keys to secure them from attacks. However, the physical context, such as the device’s physical information, temperature, location, behavioural analysis of IoT node, etc., should also need to be considered in developing Context-Aware ML-based AA schemes. Context-awareness in ML-based AA can provide a more robust authentication and authorization and defend against attacks by using the context as AA factor have been discussed in [113]. Moreover, IoT security should rely on centralized and distributed characteristics that consider timing.
- New & Strong Authentication Schemes: Researchers use XOR-ing and hashing algorithms to render the authentication protocol lightweight. Additionally, protocols require numerous guarantees to maintain authenticated data retention. There are also other opportunities to implement modern authentication methods based on ML. The open issues in IoT security are quantum computation, quantum bit interaction, and quantum cryptography. Considering the attacks in IoT networks are massive, especially at the first step in network access, specific network packets are critical for that device efficiency through their behaviour. Therefore, it is necessary to establish trust in each node to protect the IoT network from all possible attacks using a robust ML-based authentication protocol.
- Anonymity: Anonymity is a significant issue in IoT due to extensive data sharing. An attacker may target the IoT network to collect details regarding IoT nodes, which would reveal critical information, e.g., medical records. Alternatively, an attacker can track down a user or object’s location and harm the devices or device properties, especially in a mobile network. Future work may focus on data anonymization and develop an IoT security process, which illustrates transparency.
- RL for AA: The AA frameworks incorporate artificial learning techniques, such as enhancement of learning and game theory, for understanding and identifying hostile actors through initialization and connectivity, and taking choices regarding protection with greater consistency in a complex operational environment. The operating environment dynamics guarantee different policies (or collections of activities) to optimize node access in every IoT setting. The Markov decision-making processes (MDPs) initially established RL. An agent in RL explores how their behaviors impact the world through trial and error. RL aims to produce long-term outcomes that can be used to answer increasingly technical problems that traditional methods do not address. It is the best option where no training databases are accessible, and learning is done by practice and external contact. In a static stochastic framework, the RL enables a single entity to learn a strategy that maximizes possible late rewards. However, as many agents implement the information sharing process in a collaborative context, it may go beyond the MDP pattern. The optimal strategy in these structures is based not just on the context but also on the other actor’s policies. In this particular instance, game theory is widely used.Nevertheless, RL is afflicted by a dimensionality constraint, and its use in the actual physical environment is constrained. RL also needs data to learn from experience and requires significant computing resources. It is combined with other ML strategies such as Deep Reinforcement Learning (DRL) to address RL shortcomings. In comparison, given the limited amount of data accessible, both RL and DRL algorithms can do better in AA than most ML algorithms. Moreover, the RL can learn from the environment, which will forward the RL-based AA schemes to fight against current threats and upcoming threats.Similarly, malicious nodes may also implement ML methods and initiate attacks during the initialization of the AA process. Thus, in the IoT environment, further studies are needed to be anticipated into the usage of ML in the AA framework and in resolving ML-based attacks.
- Adversarial ML: Most of the ML algorithms are subject to adverse attacks irrespective of the category of the algorithm utilized. The more general inconsistency between an intruder and a protector, an ML-led scheme is designed to protect from attacks [114]. Nonetheless, all schemes are susceptible to both observational and cause-effective attacks.The intruder can affect the ML algorithms training or testing by altering data or a pattern. An intruder applies reverse engineering primarily based on a scheme identification and then exploiting it to avoid detection. Both of these cases can also be launched for IoT protection at the same time. In general, ML-driven schemes involving retraining the scheme very frequently or require the latest data are often more likely to be targeted in these categories. For example, the ML framework dataset can be rendered to various outcomes by slight modifications (e.g., adding a minimal quantity of noise while maintaining the data identified with the actual PHY-Layer signal).Furthermore, it remains vital to build resilient, robust, and reliable ML-driven schemes to cope with complex attacks by intelligent opponents. Adversarial ML analysis requires further attempts to track by adversaries and malware skipping attacks. ML-driven AA systems are prone to attacks of poisoning. An attacker could inject malicious information into an ML training dataset. The learning process is badly impaired in this situation. Therefore, a weak paradigm is enlightened with the learning process. It should be remembered that collusion attacks can be used as an initial step before malware skipping attacks are later initiated. There is also a gap that an intruder might manipulate with the training. An intruder can particularly abuse the vulnerability of different underlying ML algorithms. To illustrate, an Intruder might generate malicious information throughout a malware skipping attack, which purposely causes system errors in the ML algorithm.As a result, these attacks make the system vulnerable in scenarios such as (a) when initial data filtration process is unsuccessful, the intruder may utilize the data which vary considerably from the actual data which will generate the unpredictable actions by ML algorithms; and (b) where the data needed to train the scheme are not always adequate for the function underlying an ML-driven scheme to achieve the ideal learning process [115].
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
List of Acronyms and Abbreviations
| Acronyms | Abbreviations |
| AA | Authentication & Authorization |
| ACL | Access Control List |
| AES | Advance Encryption Standard |
| AI | Artificial Intelligence |
| ABAC | Attribute Based Access Control |
| BAN | Body Area Network |
| BP | Back-Propagation |
| CapBAC | Capability-Based Access Control |
| CA | Certificate Authorities |
| CRP | Challenge Response Pair |
| CIR | Channel Impulsion Responses |
| CSI | Channel State Information |
| CoAP | Constrained Application Protocol |
| XSS | Cross-Site Scripting |
| DTLS | Datagram Transport Layer Security |
| DNN | Deep Neural Network |
| DoS | Denial of Services |
| DDoS | Distributed Denial of Services |
| ERR | Equal Error Rate |
| XMPP | Extensible Messaging and Presence Protocol |
| FAR | False Acceptance Rate |
| FRR | False Rejection Rate |
| DFW | Frank-Wolfe |
| GWN | Gateway Node |
| IAG | Incremental Aggregated Gradient |
| IGMM | Infinite Gaussian Mixture Model |
| I2C | Inter-integrated Circuit |
| IMT | Internet of Medical Things |
| IoT | Internet of Things |
| ID | Intrusion Detection |
| IPHC | IP Header Compression |
| LEAP+ | Localized Encryption and Authentication Protocol |
| MIN | Machine Identification Number |
| ML | Machine Learning |
| MITM | Man in the Middle |
| MDP | Markov Decision-Making Processes |
| MAC | Media Access Control |
| MQTT | Message Queuing Telemetry Transport |
| MLP | Multi-Layer Perceptron |
| NB | Naive Bayes |
| NHC | Next Header Compression |
| PSO | Particle Swarm Optimization |
| PHY-Layer | Phyisical Layer |
| PKI | Public Key Infrastructure |
| QoS | Quality of Services |
| RSS | Received Signal Strength |
| RSSI | Received Signal Strength Indicators |
| RL | Reinforcement Learning |
| RBAC | Roles Based Access Control |
| SMQTT | Secure Message Queue Telemetry Transport |
| SAML | Security Assertion Markup Language |
| SNEP | Sensor Network Encryption Protocol |
| SNSP | Sensor Network Security Protocols |
| SPI | Serial Peripheral Interface |
| SSO | Single Sign-On |
| SVM | Support-Vector Machines |
| TLS | Transport Layer Security |
| TTP | Trusted Third Party |
| WoTs | Web of Things |
| WSN | Wireless Sensor Network |
References
- Statista. Internet of Things—Active Connections Worldwide 2015–2025; Statista Research Department: Hamburg, Germany, 2021. [Google Scholar]
- Li, X.; Lu, R.; Liang, X.; Shen, X.; Chen, J.; Lin, X. Smart community: An internet of things application. IEEE Commun. Mag. 2011, 49, 68–75. [Google Scholar] [CrossRef]
- Ahad, A.; Tahir, M.; Sheikh, M.A.; Ahmed, K.I.; Mughees, A.; Numani, A. Technologies trend towards 5g network for smart health-care using iot: A review. Sensors 2020, 20, 4047. [Google Scholar] [CrossRef]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and other botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Putra, G.D.; Dedeoglu, V.; Kanhere, S.S.; Jurdak, R. Trust management in decentralized iot access control system. In Proceedings of the 2020 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Toronto, ON, Canada, 2–6 May 2020; pp. 1–9. [Google Scholar]
- Kang, J.J.; Fahd, K.; Venkatraman, S.; Trujillo-Rasua, R.; Haskell-Dowland, P. Hybrid Routing for Man-in-the-Middle (MITM) Attack Detection in IoT Networks. In Proceedings of the 2019 29th International Telecommunication Networks and Applications Conference (ITNAC), Auckland, New Zealand, 27–29 November 2019. [Google Scholar] [CrossRef]
- Hajiheidari, S.; Wakil, K.; Badri, M.; Navimipour, N.J. Intrusion detection systems in the Internet of things: A comprehensive investigation. Comput. Netw. 2019, 160, 165–191. [Google Scholar] [CrossRef]
- Shu, Z.; Wan, J.; Li, D.; Lin, J.; Vasilakos, A.V.; Imran, M. Security in Software-Defined Networking: Threats and Countermeasures. Mob. Netw. Appl. 2016, 21, 764–776. [Google Scholar] [CrossRef]
- Jayasinghe, U.; Lee, G.M.; Um, T.W.; Shi, Q. Machine Learning Based Trust Computational Model for IoT Services. IEEE Trans. Sustain. Comput. 2018, 4, 39–52. [Google Scholar] [CrossRef]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Airehrour, D.; Gutierrez, J.; Ray, S.K. Secure routing for internet of things: A survey. J. Netw. Comput. Appl. 2016, 66, 198–213. [Google Scholar] [CrossRef]
- Ali, I.; Sabir, S.; Ullah, Z. Internet of Things Security, Device Authentication and Access Control: A Review. Int. J. Comput. Sci. Inf. Secur. 2019, 14, 456–466. [Google Scholar]
- Ashraf, Q.M.; Habaebi, M.H. Autonomic schemes for threat mitigation in Internet of Things. J. Netw. Comput. Appl. 2015, 49, 112–127. [Google Scholar] [CrossRef]
- Sicari, S.; Rizzardi, A.; Grieco, L.A.; Coen-Porisini, A. Security, privacy and trust in Internet of things: The road ahead. Comput. Netw. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- El-Hajj, M.; Fadlallah, A.; Chamoun, M.; Serhrouchni, A. A survey of internet of things (IoT) authentication schemes. Sensors 2019, 19, 1141. [Google Scholar] [CrossRef] [Green Version]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A Survey on Security and Privacy Issues in Internet-of-Things. IEEE Internet Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A Survey on Internet of Things: Architecture, Enabling Technologies, Security and Privacy, and Applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Xiao, L.; Wan, X.; Lu, X.; Zhang, Y.; Wu, D. IoT Security Techniques Based on Machine Learning. arXiv 2018, arXiv:1801.06275. [Google Scholar]
- Mishra, P.; Varadharajan, V.; Tupakula, U.; Pilli, E.S. A detailed investigation and analysis of using machine learning techniques for intrusion detection. IEEE Commun. Surv. Tutor. 2019, 21, 686–728. [Google Scholar] [CrossRef]
- Hussain, F.; Hussain, R.; Hassan, S.A.; Hossain, E. Machine Learning in IoT Security: Current Solutions and Future Challenges. IEEE Commun. Surv. Tutor. 2020, 22, 1686–1721. [Google Scholar] [CrossRef] [Green Version]
- Hasan, M.; Islam, M.M.; Zarif, M.I.I.; Hashem, M. Attack and anomaly detection in IoT sensors in IoT sites using machine learning approaches. Internet Things 2019, 7, 100059. [Google Scholar] [CrossRef]
- Sun, P.; Li, J.; Alam Bhuiyan, M.Z.; Wang, L.; Li, B. Modeling and clustering attacker activities in IoT through machine learning techniques. Inf. Sci. 2018, 479, 456–471. [Google Scholar] [CrossRef]
- Park, T.; Abuzainab, N.; Saad, W. Learning How to Communicate in the Internet of Things: Finite Resources and Heterogeneity. IEEE Access 2016, 4, 7063–7073. [Google Scholar] [CrossRef]
- Xiao, L.; Li, Y.; Huang, X.; Du, X. Cloud-based malware detection game for mobile devices with offloading. IEEE Trans. Mob. Comput. 2017, 16, 2742–2750. [Google Scholar] [CrossRef]
- Xiao, L.; Xie, C.; Chen, T.; Dai, H.; Poor, H.V. A Mobile offloading game against smart attacks. IEEE Access 2016, 4, 2281–2291. [Google Scholar] [CrossRef]
- Tahir, M.; Sardaraz, M.; Muhammad, S.; Khan, M.S. A Lightweight Authentication and Authorization Framework for Blockchain-Enabled IoT Network in Health-Informatics. Sustainability 2020, 12, 6960. [Google Scholar] [CrossRef]
- Lee, D.H.; Lee, I.Y. A lightweight authentication and key agreement schemes for IoT environments. Sensors 2020, 20, 5350. [Google Scholar] [CrossRef]
- Lara, E.; Aguilar, L.; Sanchez, M.A.; García, J.A. Lightweight authentication protocol for M2M communications of resource-constrained devices in industrial internet of things. Sensors 2020, 20, 501. [Google Scholar] [CrossRef] [Green Version]
- Nespoli, P.; Zago, M.; Celdrán, A.H.; Pérez, M.G.; Mármol, F.G.; Clemente, F.J. PALOT: Profiling and authenticating users leveraging internet of things. Sensors 2019, 19, 2832. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Yang, H.; Kim, Y. Design and Implementation of High-Availability Architecture for IoT-Cloud Services. Sensors 2019, 19, 3276. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Jayasinghe, U.; Otebolaku, A.; Um, T.W.; Lee, G.M. Data centric trust evaluation and prediction framework for IOT. In Proceedings of the 2017 ITU Kaleidoscope: Challenges for a Data-Driven Society (ITU K), Nanjing, China, 27–29 November 2017; pp. 1–7. [Google Scholar] [CrossRef] [Green Version]
- Fraile, F.; Tagawa, T.; Poler, R.; Ortiz, A. Trustworthy Industrial IoT Gateways for Interoperability Platforms and Ecosystems. IEEE Internet Things J. 2018, 5, 4506–4514. [Google Scholar] [CrossRef]
- Ferreira, C.M.S.; Garrocho, C.T.B.; Oliveira, R.A.R.; Silva, J.S.; Cavalcanti, C.F.M.d.C. IoT registration and authentication in smart city applications with blockchain. Sensors 2021, 21, 1323. [Google Scholar] [CrossRef]
- Banks, A.; Briggs, E.; Borgendale, K.; Gupta, R. MQTT Version 5.0; Standard, O. A. S. I. S, 2019; Available online: https://docs.oasis-open.org/mqtt/mqtt/v5.0/mqtt-v5.0.html (accessed on 20 July 2020).
- Elmouaatamid, O.; Lahmer, M.; Belkasmi, M. Group authentication with fault tolerance for internet of things. In International Symposium on Ubiquitous Networking; Springer: Cham, Switzerland, 2017; Volume 10542 LNCS, pp. 299–307. [Google Scholar] [CrossRef]
- Li, X.; Peng, J.; Niu, J.; Wu, F.; Liao, J.; Choo, K.K.R. A robust and energy efficient authentication protocol for industrial internet of things. IEEE Internet Things J. 2018, 5, 1606–1615. [Google Scholar] [CrossRef]
- Burhan, M.; Rehman, R.A.; Khan, B.; Kim, B.S. IoT elements, layered architectures and security issues: A comprehensive survey. Sensors 2018, 18, 2796. [Google Scholar] [CrossRef] [Green Version]
- Shobana, M.; Rathi, S. IOT Malware: An Analysis of IOT Device Hijacking. Int. J. Sci. Res. Comput. Sci. Eng. Inf. Technol. 2018, 5, 2456–3307. [Google Scholar]
- Argust, G. Side Channel Attacks on IoT Applications. Ph.D. Thesis, University of Bristol, Bristol, UK, 2019. [Google Scholar]
- Li, X.; Hao, W.; Dai, H.N.; Wang, Y.; Zhao, Q. On modeling eavesdropping attacks in wireless networks. Mob. Inf. Syst. 2016, 11, 196–204. [Google Scholar] [CrossRef]
- Brun, O.; Yin, Y.; Augusto-gonzalez, J.; Ramos, M.; Gelenbe, E. IoT Attack Detection with Deep Learning. In Proceedings of the ISCIS Security Workshop, London, UK, 26–27 February 2018. hal- 02062091. [Google Scholar]
- Gupta, H.; Van Oorschot, P.C. Onboarding and Software Update Architecture for IoT Devices. In Proceedings of the 2019 17th International Conference on Privacy, Security and Trust, PST, Fredericton, NB, Canada, 26–28 August 2019. [Google Scholar] [CrossRef]
- Cha, S.C.; Chen, J.F.; Su, C.; Yeh, K.H. A Blockchain Connected Gateway for BLE-Based Devices in the Internet of Things. IEEE Access 2018, 6, 24639–24649. [Google Scholar] [CrossRef]
- Chen, K.; Zhang, S.; Li, Z.; Zhang, Y.; Deng, Q.; Ray, S.; Jin, Y. Internet-of-Things Security and Vulnerabilities: Taxonomy, Challenges, and Practice. J. Hardw. Syst. Secur. 2018, 2, 97–110. [Google Scholar] [CrossRef]
- Celesti, A.; Fazio, M.; Villari, M. Enabling secure XMPP communications in federated IoT clouds through XEP 0027 and SAML/SASL SSO. Sensors 2017, 17, 301. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Mode, G.R.; Calyam, P.; Hoque, K.A. False data injection attacks in internet of things and deep learning enabled predictive analytics. arXiv 2019, arXiv:1910.01716. [Google Scholar]
- Swamy, S.N.; Jadhav, D.; Kulkarni, N. Security Threats in the Application layer in IOT Applications. In Proceedings of the International conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC 2017), Palladam, India, 10–11 February 2017; pp. 477–480. [Google Scholar]
- Abdul-Ghani, H.A.; Konstantas, D.; Mahyoub, M. A comprehensive IoT attacks survey based on a building-blocked reference model. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 355–373. [Google Scholar] [CrossRef]
- Haroon, A.; Akram, S.; Shah, M.A.; Wahid, A. E-lithe: A lightweight secure DTLS for IoT. In Proceedings of the IEEE 86th Vehicular Technology Conference (VTC-Fall), Toronto, ON, Canada, 24–27 September 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Kang, D.; Jung, J.; Kim, H.; Lee, Y.; Won, D. Efficient and Secure Biometric-Based User Authenticated Key Agreement Scheme with Anonymity. Secur. Commun. Netw. 2018, 2018, 9046064. [Google Scholar] [CrossRef] [Green Version]
- Amin, R.; Kumar, N.; Biswas, G.P.; Iqbal, R.; Chang, V. A light weight authentication protocol for IoT-enabled devices in distributed Cloud Computing environment. Future Gener. Comput. Syst. 2018, 78, 1005–1019. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X.; Shen, J.; Choo, K.K.R.; Wazid, M.; Das, A.K. An efficient authentication and key agreement scheme for multi-gateway wireless sensor networks in IoT deployment. J. Netw. Comput. Appl. 2017, 89, 72–85. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Bhuiyan, M.Z.A.; Wu, F.; Karuppiah, M.; Kumari, S. A robust ECC-Based provable secure authentication protocol with privacy preserving for industrial internet of things. IEEE Trans. Ind. Inform. 2018, 14, 3599–3609. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Kumari, S.; Wu, F.; Sangaiah, A.K.; Choo, K.K.R. A three-factor anonymous authentication scheme for wireless sensor networks in internet of things environments. J. Netw. Comput. Appl. 2018, 103, 194–204. [Google Scholar] [CrossRef]
- Roy, S.; Chatterjee, S.; Das, A.K.; Chattopadhyay, S.; Kumari, S.; Jo, M. Chaotic map-based anonymous user authentication scheme with user biometrics and fuzzy extractor for crowdsourcing internet of things. IEEE Internet Things J. 2018, 5, 2884–2895. [Google Scholar] [CrossRef]
- Ahmed, A.A.; Ahmed, W.A. An effective multifactor authentication mechanism based on combiners of hash function over internet of things. Sensors 2019, 19, 3663. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Sebbah, A.; Kadri, B. A Privacy and Authentication Scheme for IoT Environments Using ECC and Fuzzy Extractor. In Proceedings of the 2020 International Conference on Intelligent Systems and Computer Vision, ISCV 2020, Fez, Morocco, 9–11 June 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Amin, R.; Biswas, G.P. A secure light weight scheme for user authentication and key agreement in multi-gateway based wireless sensor networks. Ad Hoc Netw. 2016, 36, 58–80. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Biswas, G.P.; Khan, M.K.; Leng, L.; Kumar, N. Design of an anonymity-preserving three-factor authenticated key exchange protocol for wireless sensor networks. Comput. Netw. 2016, 101, 42–62. [Google Scholar] [CrossRef]
- Xiao, L.; Wan, X.; Han, Z. PHY-Layer Authentication with Multiple Landmarks with Reduced Overhead. IEEE Trans. Wirel. Commun. 2018, 17, 1676–1687. [Google Scholar] [CrossRef]
- Xiao, L.; Li, Y.; Han, G.; Liu, G.; Zhuang, W. PHY-Layer Spoofing Detection with Reinforcement Learning in Wireless Networks. IEEE Trans. Veh. Technol. 2016, 65, 10037–10047. [Google Scholar] [CrossRef]
- Ozay, M.; Esnaola, I.; Yarman Vural, F.T.; Kulkarni, S.R.; Poor, H.V. Machine Learning Methods for Attack Detection in the Smart Grid. IEEE Trans. Neural Netw. Learn. Syst. 2016, 27, 1773–1786. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Punithavathi, P.; Geetha, S.; Karuppiah, M.; Islam, S.H.; Hassan, M.M.; Choo, K.K.R. A lightweight machine learning-based authentication framework for smart IoT devices. Inf. Sci. 2019, 484, 255–268. [Google Scholar] [CrossRef]
- Noor, M.B.M.; Hassan, W.H. Current research on Internet of Things (IoT) security: A survey. Comput. Netw. 2018, 148, 283–294. [Google Scholar] [CrossRef]
- Jan, M.A.; Khan, F.; Alam, M.; Usman, M. A payload-based mutual authentication scheme for Internet of Things. Future Gener. Comput. Syst. 2019, 92, 1028–1039. [Google Scholar] [CrossRef]
- Alizai, Z.A.; Tareen, N.F.; Jadoon, I. Improved IoT Device Authentication Scheme Using Device Capability and Digital Signatures. In Proceedings of the 2018 International Conference on Applied and Engineering Mathematics (ICAEM), Taxila, Pakistan, 4–5 September 2018; pp. 115–119. [Google Scholar] [CrossRef]
- Hamidi, H. An approach to develop the smart health using Internet of Things and authentication based on biometric technology. Future Gener. Comput. Syst. 2019, 91, 434–449. [Google Scholar] [CrossRef]
- Hammi, M.T.; Hammi, B.; Bellot, P.; Serhrouchni, A. Bubbles of Trust: A decentralized blockchain-based authentication system for IoT. Comput. Secur. 2018, 78, 126–142. [Google Scholar] [CrossRef]
- Zhou, L.; Li, X.; Yeh, K.H.; Su, C.; Chiu, W. Lightweight IoT-based authentication scheme in cloud computing circumstance. Future Gener. Comput. Syst. 2019, 91, 244–251. [Google Scholar] [CrossRef]
- Souissi, I.; Ben Azzouna, N.; Ben Said, L. A multi-level study of information trust models in WSN-assisted IoT. Comput. Netw. 2019, 151, 12–30. [Google Scholar] [CrossRef]
- Hu, H.; Ahn, G.J.; Kulkarni, K. Detecting and resolving firewall policy anomalies. IEEE Trans. Dependable Secur. Comput. 2012, 9, 318–331. [Google Scholar] [CrossRef]
- Saâdaoui, A.; Ben Youssef Ben Souayeh, N.; Bouhoula, A. FARE: FDD-based firewall anomalies resolution tool. J. Comput. Sci. 2017, 23, 181–191. [Google Scholar] [CrossRef]
- Xiao, L.; Wan, X.; Lu, X.; Zhang, Y.; Wu, D. IoT Security Techniques Based on Machine Learning: How Do IoT Devices Use AI to Enhance Security? IEEE Signal Process. Mag. 2018, 35, 41–49. [Google Scholar] [CrossRef]
- Gong, B.; Zhang, Y.; Wang, Y. A remote attestation mechanism for the sensing layer nodes of the Internet of Things. Future Gener. Comput. Syst. 2018, 78, 867–886. [Google Scholar] [CrossRef]
- Caminha, J.; Perkusich, A.; Perkusich, M. A Smart Trust Management Method to Detect On-Off Attacks in the Internet of Things. Secur. Commun. Netw. 2018, 2018, 6063456. [Google Scholar] [CrossRef]
- Zhang, Y.; Wu, X. Access Control in Internet of Things: A Survey. In Proceedings of the Asia-Pacific Engineering and Technology Conference (APETC 2017), Kuala Lumpur, Malaysia, 25–26 May 2017; pp. 1544–1557. [Google Scholar]
- Bernal Bernabe, J.; Hernandez Ramos, J.L.; Skarmeta Gomez, A.F. TACIoT: Multidimensional trust-aware access control system for the Internet of Things. Soft Comput. 2016, 20, 1763–1779. [Google Scholar] [CrossRef]
- Karthikeyan, S.; Patan, R.; Balamurugan, B. Enhancement of Security in the Internet of Things (IoT) by Using X.509 Authentication Mechanism. In Recent Trends in Communication, Computing, and Electronics; Springer: Singapore, 2019; pp. 217–225. [Google Scholar] [CrossRef]
- Xu, H.; Ding, J.; Li, P.; Zhu, F.; Wang, R. A lightweight rfid mutual authentication protocol based on physical unclonable function. Sensors 2018, 18, 760. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Modadugu, N.; Rescorla, E. The Design and Implementation of Datagram TLS. In Proceedings of the NDSS, San Diego, CA, USA, 5–6 February 2004. [Google Scholar]
- Raza, S.; Shafagh, H.; Hewage, K.; Hummen, R.; Voigt, T. Lithe: Lightweight secure CoAP for the internet of things. IEEE Sens. J. 2013, 13, 3711–3720. [Google Scholar] [CrossRef]
- Gope, P.; Lee, J.; Quek, T.Q. Lightweight and Practical Anonymous Authentication Protocol for RFID Systems Using Physically Unclonable Functions. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2831–2843. [Google Scholar] [CrossRef]
- Alotaibi, M. An enhanced symmetric cryptosystem and biometric-based anonymous user authentication and session key establishment scheme for WSN. IEEE Access 2018, 6, 70072–70087. [Google Scholar] [CrossRef]
- Buczak, A.L.; Guven, E. A Survey of Data Mining and Machine Learning Methods for Cyber Security Intrusion Detection. IEEE Commun. Surv. Tutor. 2016, 18, 1153–1176. [Google Scholar] [CrossRef]
- Tan, Z.; Jamdagni, A.; He, X.; Nanda, P.; Liu, R.P. A system for denial-of-service attack detection based on multivariate correlation analysis. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 447–456. [Google Scholar] [CrossRef]
- Choudhary, S.; Kesswani, N. Analysis of KDD-Cup’99, NSL-KDD and UNSW-NB15 Datasets using Deep Learning in IoT. Procedia Comput. Sci. 2020, 167, 1561–1573. [Google Scholar] [CrossRef]
- Branch, J.W.; Giannella, C.; Szymanski, B.; Wolff, R.; Kargupta, H. In-network outlier detection in wireless sensor networks. Knowl. Inf. Syst. 2013, 34, 23–54. [Google Scholar] [CrossRef] [Green Version]
- Xiao, L.; Yan, Q.; Lou, W.; Chen, G.; Hou, Y.T. Proximity-based security techniques for mobile users in wireless networks. IEEE Trans. Inf. Forensics Secur. 2013, 8, 2089–2100. [Google Scholar] [CrossRef] [Green Version]
- Gwon, Y.; Dastangoo, S.; Fossa, C.; Kung, H. Competing mobile network game: Embracing anti-jamming and jamming strategies with reinforcement learning. In Proceedings of the 2013 IEEE Conference on Communications and Network Security (CNS), National Harbor, MD, USA, 14–16 October 2013; pp. 28–36. [Google Scholar]
- Aref, M.A.; Jayaweera, S.K.; Machuzak, S. Multi-agent reinforcement learning based cognitive anti-jamming. In Proceedings of the 2017 IEEE Wireless Communications and Networking Conference (WCNC), San Francisco, CA, USA, 19–22 March 2017. [Google Scholar] [CrossRef]
- Shi, C.; Liu, J.; Liu, H.; Chen, Y. Smart User authentication through actuation of daily activities leveraging wifi-enabled IoT. In Proceedings of the 18th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Chennai, India, 10–14 July 2017. Part F1291. [Google Scholar] [CrossRef]
- Han, G.; Xiao, L.; Poor, H.V. Two-dimensional anti-jamming communication based on deep reinforcement learning. In Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), New Orleans, LA, USA, 5–9 March 2017; pp. 2087–2091. [Google Scholar] [CrossRef]
- Li, Y.; Quevedo, D.E.; Dey, S.; Shi, L. SINR-Based DoS attack on remote state estimation: A game-theoretic approach. IEEE Trans. Control Netw. Syst. 2017, 4, 632–642. [Google Scholar] [CrossRef] [Green Version]
- Alsheikh, M.A.; Lin, S.; Niyato, D.; Tan, H.P. Machine learning in wireless sensor networks: Algorithms, strategies, and applications. IEEE Commun. Surv. Tutor. 2014, 16, 1996–2018. [Google Scholar] [CrossRef] [Green Version]
- Ouaddah, A.; Mousannif, H.; Abou Elkalam, A.; Ait Ouahman, A. Access control in the Internet of Things: Big challenges and new opportunities. Comput. Netw. 2017, 112, 237–262. [Google Scholar] [CrossRef]
- Xu, Y.; Zeng, Q.; Wang, G.; Zhang, C.; Ren, J.; Zhang, Y. A Privacy-Preserving Attribute-Based Access Control Scheme. In Proceedings of the Security, Privacy and Anonymity in Computation, Communication and Storage 11th International Conference Satell. Work. SpaCCS 2018, Melbourne, NSW, Australia, 11–13 December 2018; Springer International Publishing: Cham, Switzerland, 2018; Volume 11342, pp. 361–370. [Google Scholar] [CrossRef]
- Barka, E.; Mathew, S.S.; Atif, Y. Securing the web of things with role-based access control. In International Conference on Codes, Cryptology, and Information Security; Springer: Cham, Switzerland, 2015; Volume 9084, pp. 14–26. [Google Scholar] [CrossRef] [Green Version]
- Guesmia, K.; Boustia, N. OrBAC from access control model to access usage model. Appl. Intell. 2018, 48, 1996–2016. [Google Scholar] [CrossRef]
- Baseri, Y.; Hafid, A.; Cherkaoui, S. Privacy preserving fine-grained location-based access control for mobile cloud. Comput. Secur. 2018, 73, 249–265. [Google Scholar] [CrossRef]
- Xu, R.; Chen, Y.; Blasch, E.; Chen, G. Blendcac: A blockchain-enabled decentralized capability-based access control for iots. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 1027–1034. [Google Scholar] [CrossRef] [Green Version]
- Xu, R.; Chen, Y.; Blasch, E.; Chen, G. A federated capability-based access control mechanism for internet of things (iots). In Sensors and Systems for Space Applications XI; International Society for Optics and Photonics: Orlando, FL, USA, 2018; Volume 10641, p. 106410U. [Google Scholar] [CrossRef] [Green Version]
- Yunchuan, G.; Han, Z.; Lingcui, Z.; Liang, F.; Fenghua, L. Incentive Mechanism for Cooperative Intrusion Detection: An Evolutionary Game Approach. In International Conference on Computational Science; Springer International Publishing: Cham, Switzerland, 2018; Volume 10860, pp. 83–97. [Google Scholar] [CrossRef]
- Göynügür, E.; Bernardini, S.; De Mel, G.; Talamadupula, K.; Şensoy, M. Policy conflict resolution in iot via planning. In Advances in Artificial Intelligence: 30th Canadian Conference on Artificial Intelligence, Canadian AI 2017; Springer: Cham, Switzerland, 2017; Volume 10233 LNAI, pp. 169–175. [Google Scholar] [CrossRef]
- Paci, F.; Squicciarini, A.; Zannone, N. Survey on access control for community-centered collaborative systems. ACM Comput. Surv. 2018, 51, 1–38. [Google Scholar] [CrossRef] [Green Version]
- Kulkarni, R.V.; Venayagamoorthy, G.K. Neural network based secure media access control protocol for wireless sensor networks. In Proceedings of the 2009 International Joint Conference on Neural Networks, Atlanta, GA, USA, 14–19 June 2009; pp. 1680–1687. [Google Scholar] [CrossRef]
- Awan, K.A.; Ud Din, I.; Almogren, A.; Guizani, M.; Altameem, A.; Jadoon, S.U. RobustTrust—A Pro-Privacy Robust Distributed Trust Management Mechanism for Internet of Things. IEEE Access 2019, 7, 62095–62106. [Google Scholar] [CrossRef]
- Awan, K.A.; Din, I.U.; Zareei, M.; Talha, M.; Guizani, M.; Jadoon, S.U. HoliTrust-A holistic cross-domain trust management mechanism for service-centric internet of things. IEEE Access 2019, 7, 52191–52201. [Google Scholar] [CrossRef]
- Kim, H.; Lee, E.A. Trusting Internet of Things: Authentication and Authorization for the Internet of Things. IT Prof. 2017, 19, 27–33. [Google Scholar] [CrossRef]
- Li, R.; Asaeda, H.; Li, J.; Fu, X. A distributed authentication and authorization scheme for in-network big data sharing. Digit. Commun. Netw. 2017, 3, 226–235. [Google Scholar] [CrossRef]
- Jiang, J.; Han, G.; Wang, F.; Shu, L.; Guizani, M. An Efficient Distributed Trust Model for Wireless Sensor Networks. IEEE Trans. Parallel Distrib. Syst. 2015, 26, 1228–1237. [Google Scholar] [CrossRef]
- Tedeschi, S.; Mehnen, J.; Tapoglou, N.; Roy, R. Secure IoT Devices for the Maintenance of Machine Tools. Procedia CIRP 2017, 59, 150–155. [Google Scholar] [CrossRef]
- Väisänen, T.; Farar, A.; Pissanidis, N.; Braccini, C.; Blumbergs, B.; Diez, E. Defending Mobile Devices for High Level Officials and Decision-Makers; NATO Cooperative Cyber Defence Centre of Excellence: Tallinn, Estonia, 2015; pp. 1–107. [Google Scholar]
- Papernot, N.; McDaniel, P.; Goodfellow, I.; Jha, S.; Celik, Z.B.; Swami, A. Practical black-box attacks against machine learning. In Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security, Abu Dhabi, United Arab Emirates, 2–6 April 2017; pp. 506–519. [Google Scholar] [CrossRef] [Green Version]
- Munoz Gonzalez, L.; Lupu, E. The Secret of Machine Learning; Oxford University Press (OUP): Oxford, UK, 2018. [Google Scholar]
| References | Authors Contribution(s) | Limitation(s) |
|---|---|---|
| Yang et al. [16] | Discussing IoT attacks, surveying the most critical limitations of IoT devices and their solutions, analyzing the security issues in different IoT layers, and exploring IoT access control schemes and architectures. | The survey mainly focuses on battery life and computational lightweightness without any taxonomy, while other essential IoT security requirements are neglected. |
| Lin et al. [17] | Overview of the safety and privacy problems, and challenges of fog/edge computing and IoT applications. | Available security and privacy control schemes are neglected in this survey. Moreover, the requirements are not specified appropriately. |
| Xiao et al. [18] | Addressing the importance of the ML-driven methods for IoT security and privacy by showing the implementation of ML-driven security solutions for IoT networks. | Lacks taxonomy and little discussion on the attack detection schemes. |
| Hajiheidari et al. [7] | Discussing the security issues in the IoT environment and categorize the types, characteristics, attacks and respective simulation, and the theoretical solution by illustrating the advantages and disadvantages of the selected mechanisms. | Focuses on IDS in IoT without emphasis on vital IoT security requirements and a minimal discussion on AA. |
| El-hajj et al. [15] | This paper gives a near-complete and up-to-date view of the IoT authentication field. It provides a summary of a large range of authentication protocols proposed in the literature. | A limited number of related works considered. Moreover, the author covered generic authentication schemes for the survey. |
| Preeti et al. [19] | This paper explored the viability of ML-driven schemes to identify intruders in IoT networks by applying these methods in intrusion detection systems, either by irregularities or traffic classification | The IoT security requirements are not appropriately considered. The metrics required to measure ML-based IDS performance are not presented. |
| Hussain et al. [20] | Discussing in-depth protection and privacy analysis of the layers (physical, network, and application). Extensively describe shortcomings of the current ML-driven approaches. | IoT attacks are not specified systematically and metrics needed to measure ML-based security schemes are not discussed. |
| References | Benefit(s) | Limitation(s) |
|---|---|---|
| Jan et al. [66] | A centralized lightweight key-based Authentication scheme over CoAP. Able to detect DoS and eavesdropping attack. | Require more than four message exchange before establishing communication. Moreover, the end-to-end delay is not considered for benchmarking the performance, and it is not sufficient to tackle Sybil, MiTM, node capturing, and flooding attack. |
| Hamidi et al. [68] | A heterogeneous biometric authentication system that considered privacy profiling and tracking over the application layer. | Attacks are not considered, and performance metrics have not been properly considered for benchmarking. Moreover, the analysis of results is not adequately shown. |
| Zhou et al. [70] | A lightweight two-factor authentication scheme using RFID tag with the one-way hashing and XOR-ing in the cloud computing environment. Moreover, costs and computational efficiency are also considered and demonstrated for the low-resource environment. | The cost of communication and the computation cost at the cloud are higher. Moreover, the attacks are not considered during authentication. |
| Karthikeyan et al. [79] | A lightweight, energy-efficient authentication scheme for a centralized IoT environment using X.509 PKI certificates is presented. | The practical analysis of security and scalability requirements for PKI-based IoT authentication systems are not considered. Moreover, attacks are not considered, and performance metrics have not considered properly for benchmarking. |
| Gope et al. [83] | A scalable, lightweight Authentication scheme with privacy profiling and tracking for IoT application layer is presented. A PUF key is shared as security credentials and provide tolerance against DoS and eavesdropping attacks. Moreover, the cost of communication and storage is minimal. | The end-to-end delay is not considered for benchmarking the performance, and it is not sufficient to tackle Sybil, MiTM, node capturing, and flooding attack. |
| Alizai et al. [67] | A lightweight multi-factor authentication using digital signature and device capacity is presented. It can be utilized to authenticate both the end node and the server node from the application layer and physical layer perspective. Able to defence against MITM attacks and replay attacks. | The server node validates the signatures and the outcomes from the function during device authentication. At the same time, DoS/DDoS, Sybil attacks can take advantage, and considerable performance metrics are not discussed. |
| Hammi et al. [69] | A blockchain-driven new authentication scheme for IoT systems aims to create bubbles by dividing devices into virtual zones to identify and trust each other through grouping. | To validate a transaction, this consensus protocol takes a considerable amount of time which is not feasible for real-time applications. Moreover, the transaction fee in the public blockchain is considered to be inefficient. |
| Haroon et al. [50] | An enhanced lightweight authentication scheme over DTLS by sharing a pre-shared key between the server and the trusted third party (TTP) is discussed. It uses NHC and IPHC as compression schemes. As a result, it decreases DoS attack and computational overhead. | Despite the benefits of reducing DoS attacks and computational overhead compared to other Lithe and DTLS methods, the multiple create requests and multiple handshake requests from various requesters can cause drainage problems, as it needs to control numerous computations. |
| Reference | [66] | [68] | [70] | [79] | [83] | [67] | [69] | [50] | |
|---|---|---|---|---|---|---|---|---|---|
| Requirement | Lightweightness | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| Privacy Profiling and Tracking | ✓ | ✓ | ✓ | ||||||
| Heterogeneity | ✓ | ✓ | |||||||
| High Availability | ✓ | ||||||||
| Dynamic Registration | ✓ | ✓ | |||||||
| Scalability | ✓ | ✓ | |||||||
| Fault Tolerance | ✓ | ✓ | ✓ | ✓ | ✓ | ||||
| Early Detection of Attacks | ✓ | ||||||||
| Resilience and robustness | ✓ | ✓ | ✓ | ✓ | |||||
| Energy-Efficiency | ✓ | ✓ | ✓ | ||||||
| Deployment Flexibility | |||||||||
| Layer | Application | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| Network | ✓ | ||||||||
| Physical | ✓ | ✓ | |||||||
| Perception | |||||||||
| Token | User Credentials | ✓ | ✓ | ||||||
| Key | ✓ | ✓ | ✓ | ✓ | ✓ | ||||
| Procedural | Single | ✓ | |||||||
| Dual | ✓ | ✓ | ✓ | ✓ | |||||
| Triple | |||||||||
| Characteristics | Centralized | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| Distributed | ✓ | ✓ | |||||||
| HW-driven | ✓ | ✓ | |||||||
| Certificate-driven | ✓ | ||||||||
| Blockchain-driven | ✓ |
| Reference | [66] | [68] | [70] | [79] | [83] | [67] | [69] | [50] | |
|---|---|---|---|---|---|---|---|---|---|
| Evaluation metrics | Average Response Time | ✓ | ✓ | ✓ | |||||
| Handshake duration | ✓ | ✓ | |||||||
| Average memory consumption | ✓ | ||||||||
| End-to-End delay | |||||||||
| Impact on Throughput | |||||||||
| Ratio of Packet delivery | ✓ | ||||||||
| Cost of communication | ✓ | ✓ | |||||||
| Cost of computation | ✓ | ||||||||
| Cost of storage/memory | ✓ | ✓ | |||||||
| Energy-Consumption | ✓ | ✓ | ✓ | ||||||
| Attacks | DoS/DDoS | ✓ | ✓ | ✓ | ✓ | ||||
| MiTM | ✓ | ||||||||
| Spoofing | ✓ | ||||||||
| Sybil | ✓ | ||||||||
| Off-Line Guessing | ✓ | ✓ | |||||||
| Forgery | ✓ | ✓ | |||||||
| On-Off | ✓ | ||||||||
| Eavesdropping | ✓ | ✓ |
| Techniques | Benefit(s) with Performance Accuracy | Limitations(s) |
|---|---|---|
| Q-Learning [24,25,62,90,91,94] | Able to detect Jamming, Spoofing, Eavesdropping, DoS/DDoS, Malware attacks using optimal authentication threshold while the mis-detection of spoofing minimized by 61.72% and false positive by 93.33%. | Classfication Accuracy, Miss-detection, False/True Positive, False/True Negative has not analyzed. Morever DoS/DDoS, Jamming and Malware attacks have not been formulated. |
| KNN [88] | Detects Intrusion attacks. Accuracy has not been specified. | FAR, FRR, EER, False/True Positive, False/True Negative have not analyzed. Moreover, only designed to detect intrusion from sequential request. |
| SVM [63,95] | Detects Intrusion attack and also able to classify Spoofing attack. Accuracy has not been specified. | Only algorithms, strategies, and application discussed with limited analysis on spoofing. |
| Naïve Bayes [95] | Detects Intrusion attack. Accuracy has not been specified. | |
| Dyna-Q [24,62] | Detects Intrusion attack. Moreover, the mis-detection rate of Dyna-Q is 6.9% lower and false positive rate is 5% lower than Q-Learning. | The applications are Limited to Malware Attack only. |
| DQN [93] | Detects Jamming attack. Accuracy has not been specified. | The attack design Limited to Jamming without analyzing FAR, FRR, EER, False/True Positive, False/True Negative metrics. |
| DNN [92] | Detects Spoofing attack with accuracy more than 94.5% and user identification accuracy is 93%. | No considerations on low-resource devices and limited to WiFi enabled devices. |
| Distributed Frank Wolfe [61] | Detects Spoofing attack and saves communication overhead by 37.4%. | DoS/DDoS, Eavesdropping attacks have not been considered to be formulated. |
| Incremental Aggregated function [61] | Detects Spoofing attack and saves the computational overhead by 71.3%. | DoS/DDoS, Eavesdropping attacks have not been considered to be formulated. |
| Techniques | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Q-Learning [90] | KNN [88] | Nonparametric Bayesian [89] | Multivariate correlation analysis [86] | SVM [95] | Naïve Bayes [95] | Q-Learning [62] | Dyna-Q [62] | SVM [63] | Q-Learning [25] | Q-Learning [94] | Q-Learning [91] | DQN [93] | DNN [92] | Q/Dyna-Q/PDS [24] | Distributed Frank-Wolfe [61] | Incremental aggregated gradient [61] | ||
| PerformanceMetric | Detection Accuracy | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |||||
| Root Mean Error | ✓ | ✓ | ✓ | ✓ | ✓ | |||||||||||||
| Energy Consumption | ✓ | ✓ | ✓ | |||||||||||||||
| SINR | ✓ | ✓ | ✓ | |||||||||||||||
| Average Error | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||||||||
| Classification Accuracy | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||||
| False Alarm | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |||||||||||
| Miss-Detection | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||||||||
| False/True Positive | ✓ | |||||||||||||||||
| False/True Negative | ✓ | |||||||||||||||||
| Detection Latency | ✓ | |||||||||||||||||
| Proximity latency | ✓ | ✓ | ||||||||||||||||
| Data Secrecy | ✓ | ✓ | ||||||||||||||||
| Attacks | DoS | ✓ | ✓ | |||||||||||||||
| Jamming | ✓ | ✓ | ✓ | |||||||||||||||
| Spoofing | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||||||||
| Intrusion | ✓ | ✓ | ✓ | |||||||||||||||
| Malware | ✓ | |||||||||||||||||
| Eavesdropping | ✓ | ✓ | ||||||||||||||||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Istiaque Ahmed, K.; Tahir, M.; Hadi Habaebi, M.; Lun Lau, S.; Ahad, A. Machine Learning for Authentication and Authorization in IoT: Taxonomy, Challenges and Future Research Direction. Sensors 2021, 21, 5122. https://doi.org/10.3390/s21155122
Istiaque Ahmed K, Tahir M, Hadi Habaebi M, Lun Lau S, Ahad A. Machine Learning for Authentication and Authorization in IoT: Taxonomy, Challenges and Future Research Direction. Sensors. 2021; 21(15):5122. https://doi.org/10.3390/s21155122
Chicago/Turabian StyleIstiaque Ahmed, Kazi, Mohammad Tahir, Mohamed Hadi Habaebi, Sian Lun Lau, and Abdul Ahad. 2021. "Machine Learning for Authentication and Authorization in IoT: Taxonomy, Challenges and Future Research Direction" Sensors 21, no. 15: 5122. https://doi.org/10.3390/s21155122
APA StyleIstiaque Ahmed, K., Tahir, M., Hadi Habaebi, M., Lun Lau, S., & Ahad, A. (2021). Machine Learning for Authentication and Authorization in IoT: Taxonomy, Challenges and Future Research Direction. Sensors, 21(15), 5122. https://doi.org/10.3390/s21155122






