Interoperable Blockchains for Highly-Integrated Supply Chains in Collaborative Manufacturing
Abstract
:1. Introduction
2. Blockchain for Collaborative Manufacturing: State-of-the-Art and Motivation
2.1. Blockchain Background
2.2. Blockchain in Industry 4.0
- The Industry 4.0 environments are characterized by a significant amount of traffic generated by the applications and devices integrated into the production lines, but blockchain solutions have known scalability limitations due to the adopted consensus algorithms.
- The consensus algorithm determines the provided QoS of the blockchain, and the user is forced to choose between consistency or availability. The selection of a consensus algorithm in place of another may impact the blockchain latency and throughput and has an impact in the case of running blockchain on resource-constraint devices. In Industry 4.0 environments, it is pivotal to make such a selection by optimizing the trade-off among opposing objectives.
- Industry 4.0 environments are ecosystems of companies, and it is not sure that all of them may agree on using the same blockchain solution. Still, it is more reasonable to have various blockchain solutions coexisting and interoperating in a single ecosystem. For this aim, it is important to investigate possible interoperability and standardization means.
2.3. Blockchain Interoperability Related Works
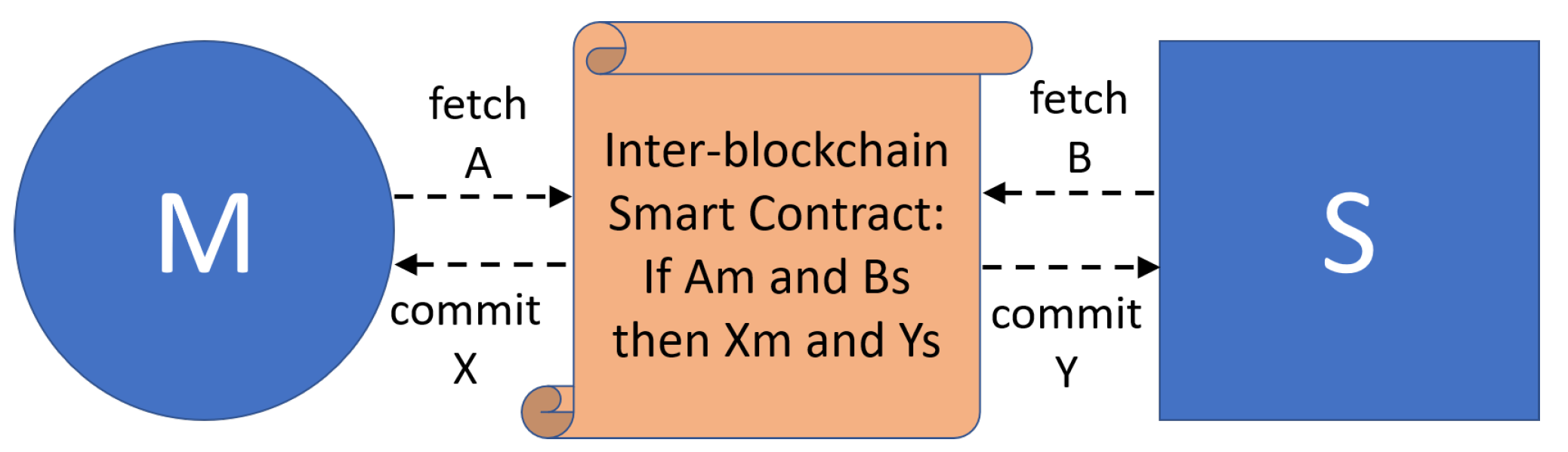
3. Interoperable Blockchains for Collaborative Manufacturing
3.1. Design Highlights
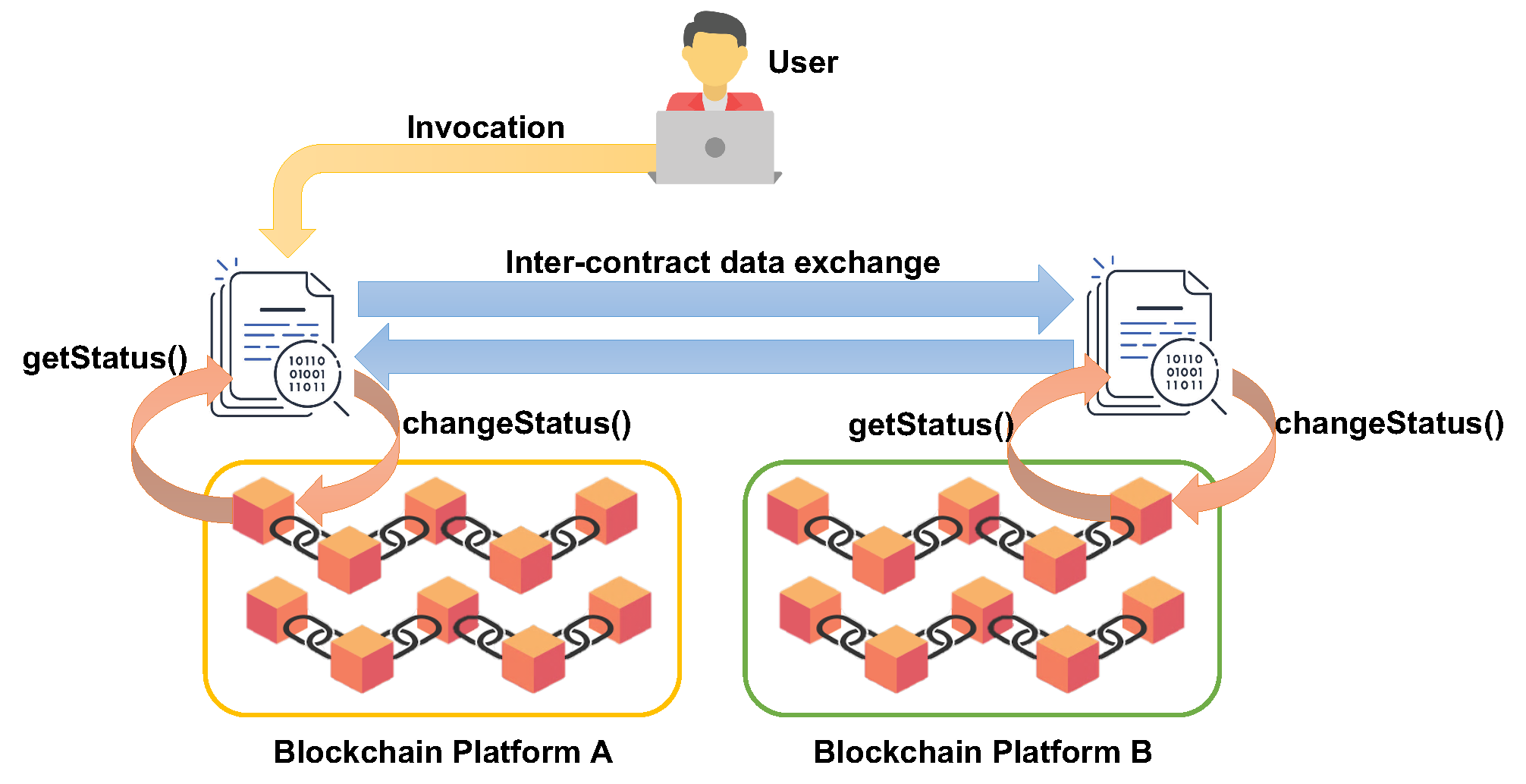
3.2. Distributed Architecture and Interoperable Blockchain
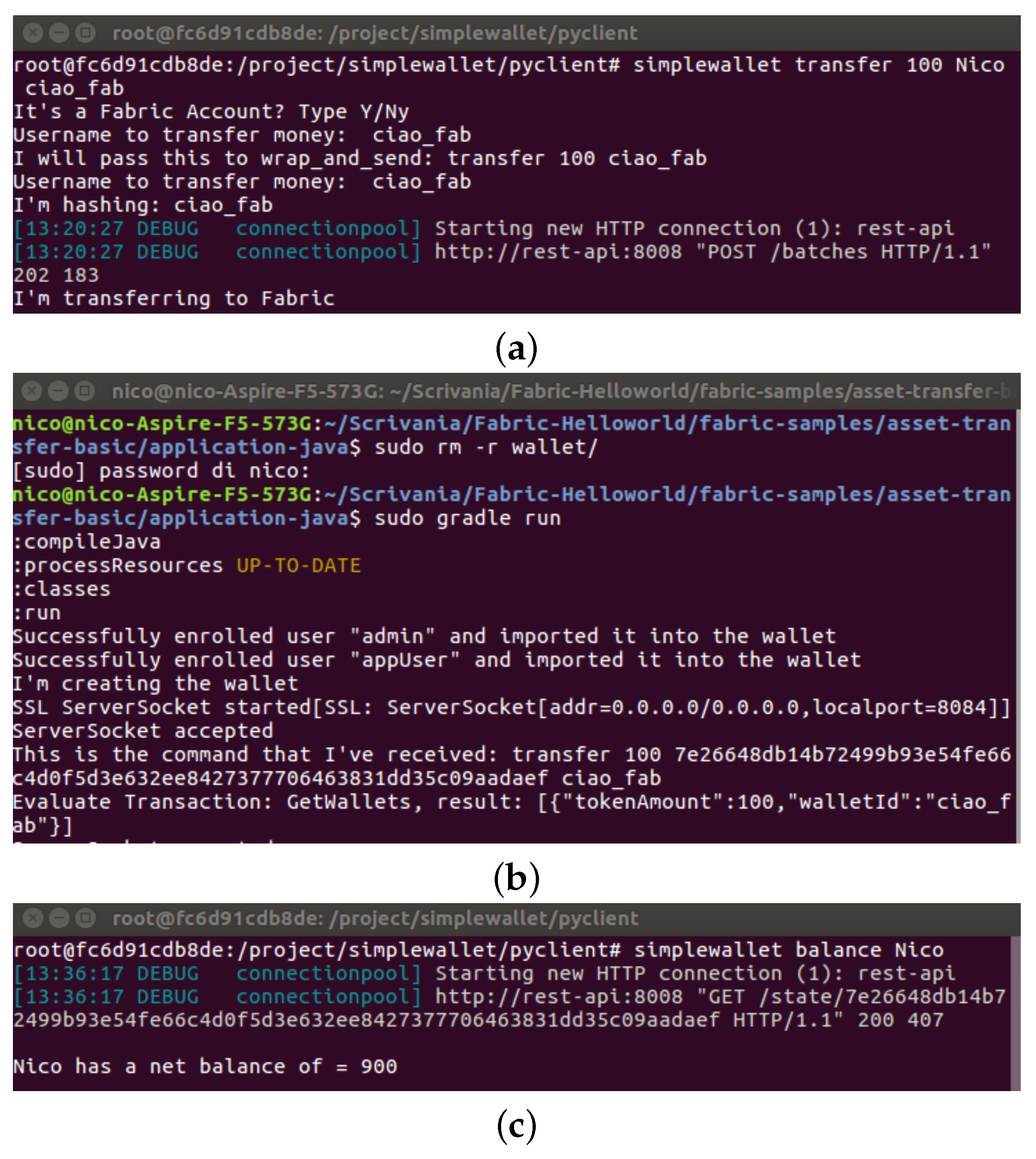
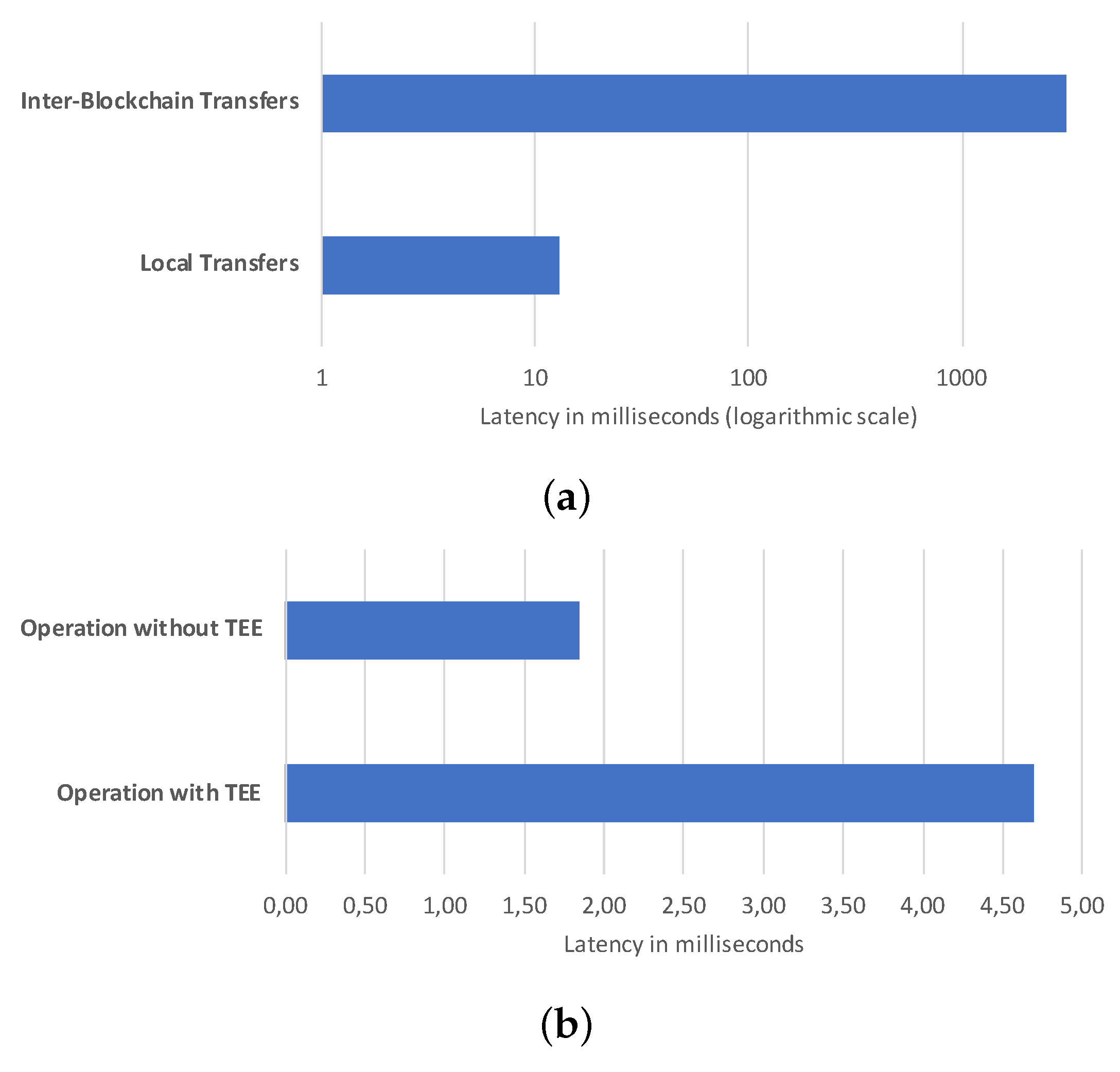
4. Implementation and Experimental Results
4.1. Hyperledger Fabric
- Clients: This requires creating a new transaction based on a specific endorsement policy, detailing how to select nodes involved in a transaction creation procedure. To this purpose, clients (i) contact a subset of endorser peers as specified by the endorsement policy, e.g., at least one for each organization involved in the transaction; (ii) wait for a given amount of transaction endorsements, again as specified by the endorsement policy, e.g., majority or all; and (iii) finally send the new transaction to orderers.
- Peers: multi-role nodes executing smart contracts, validating transactions provided by clients, and maintaining a local copy of the ledger by committing transactions;
- Committers, nodes with the only role of maintaining the ledger and updating it whenever they receive a new block.
- Endorsers: nodes actually executing a smart contract whenever they receive a proposal of transaction. During the endorsement of a new transaction, endorsers securely sign so-called endorsement messages (also containing transaction output, transaction id, endorser id, and endorser signature) and send them to the client requiring the new transaction.
- Orderers: nodes are collecting requests of new transactions creations, grouping multiple transactions in a block, e.g., sorting concurrent transaction requests coming from different clients and issuing commands to peers to add new blocks on top of the ledger. Note that orderers are unaware of transaction semantics and exploit cryptographic signatures of endorsers to create new blocks.
4.2. Hyperledger Sawtooth
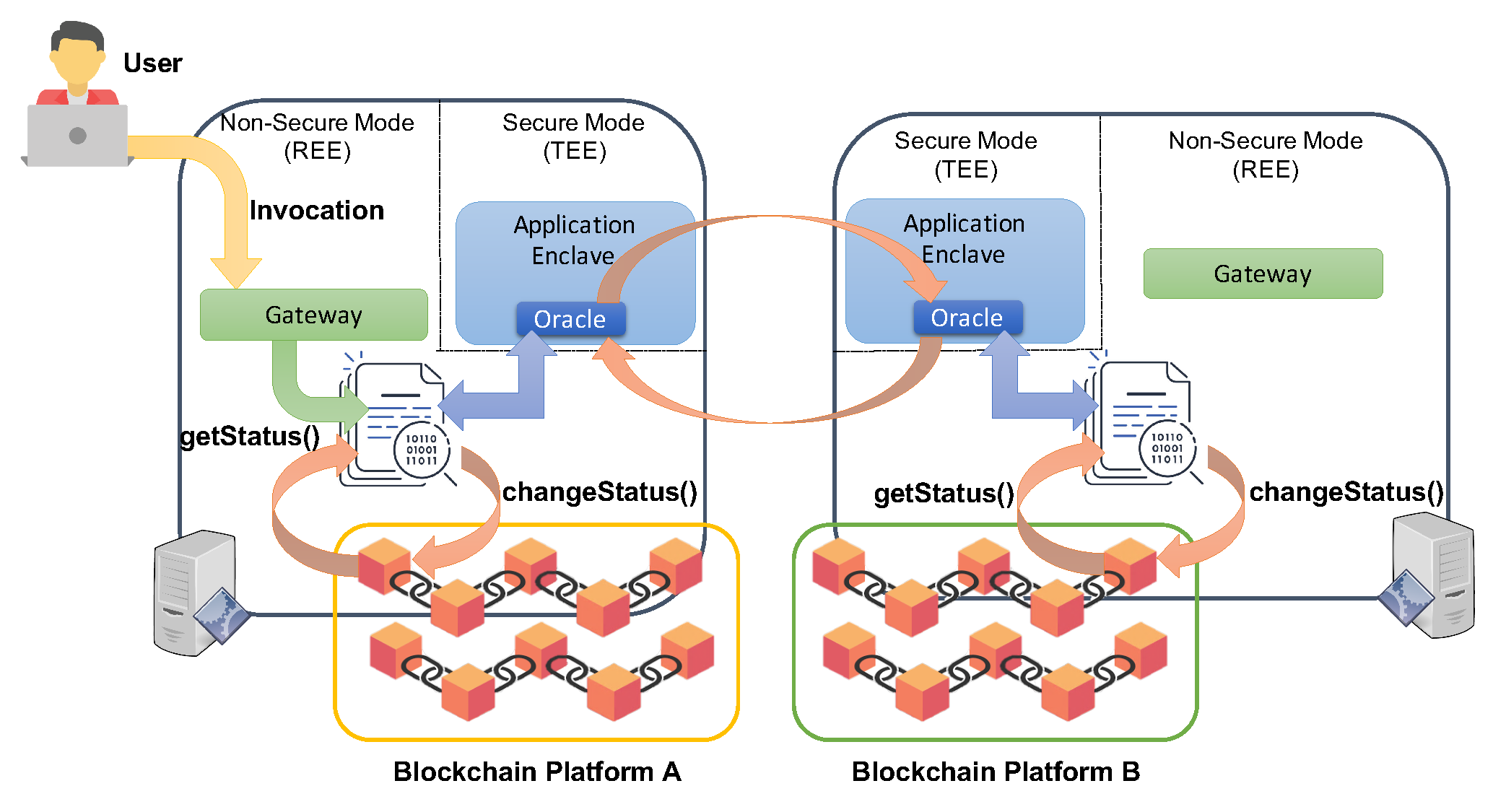
4.3. Open Enclave
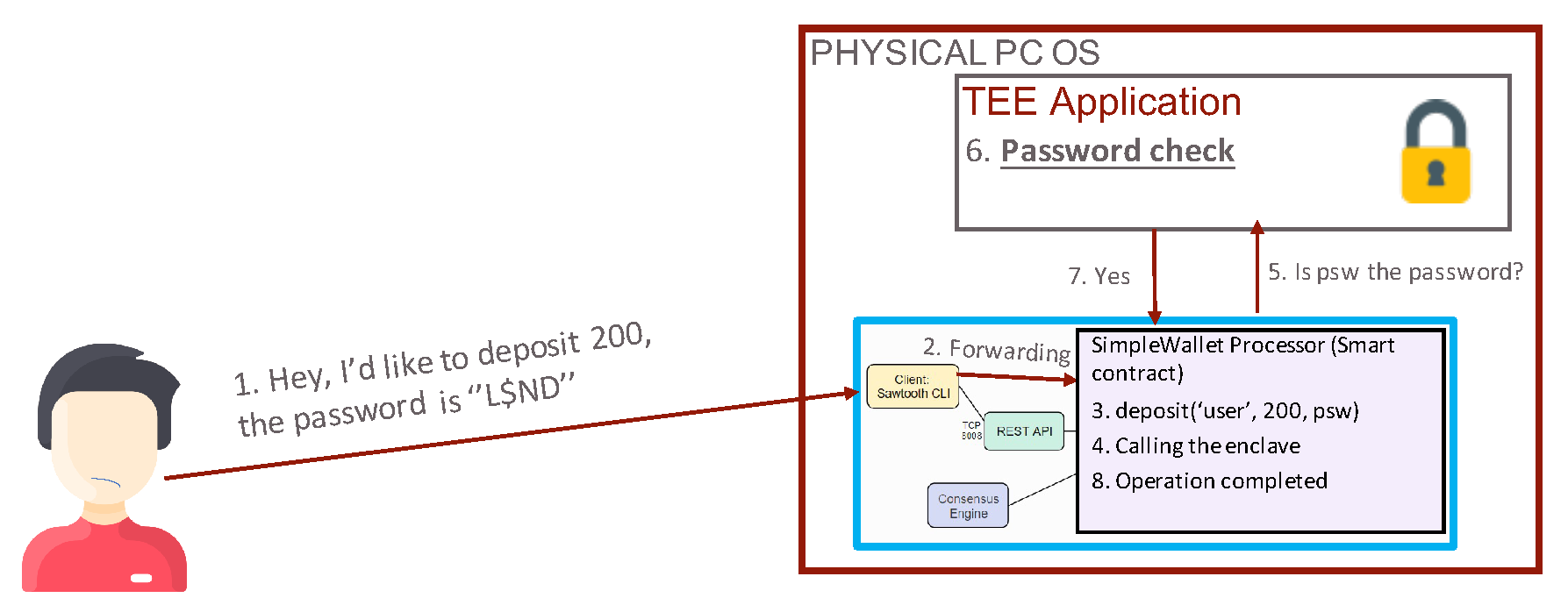
4.4. Prototype Realization
4.5. Experimental Results
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Cimini, C.; Pinto, R.; Pezzotta, G.; Gaiardelli, P. The Transition Towards Industry 4.0: Business Opportunities and Expected Impacts for Suppliers and Manufacturers; Advances in Production Management Systems. The Path to Intelligent, Collaborative and Sustainable Manufacturing; Springer: Cham, Switzerland, 2017; pp. 119–126. [Google Scholar]
- Corradi, A.; Foschini, L.; Giannelli, C.; Lazzarini, R.; Stefanelli, C.; Tortonesi, M.; Virgilli, G. Smart Appliances and RAMI 4.0: Management and Servitization of Ice Cream Machines. IEEE Trans. Ind. Inform. 2018, 15, 1007–1016. [Google Scholar] [CrossRef]
- Dombrowski, U.; Dombrowski, S. Servitization as a key driver for Digital Transformation of manufacturing companies’ Spare Parts Service. In Proceedings of the IEEE International Conference on Service Operations and Logistics, and Informatics (SOLI), Piscataway, NJ, USA, 31 July–2 August 2018; pp. 291–296. [Google Scholar]
- Industrial Internet Consortium. Industrial Internet Reference Architecture. v 1.9. 2020. Available online: https://www.iiconsortium.org/IIRA.htm (accessed on 2 July 2021).
- OPC Foundation. 2020. Available online: https://opcfoundation.org (accessed on 2 July 2021).
- Salah, K.; Nizamuddin, N.; Jayaraman, R.; Omar, M. Blockchain-Based Soybean Traceability in Agricultural Supply Chain; IEEE Access: Piscataway, NJ, USA, 2019; Volume 7. [Google Scholar]
- Kshetri, N. Blockchain and the Economics of Food Safety; IT Professional (IEEE): Piscataway, NJ, USA, 2019; Volume 21. [Google Scholar]
- Alzahrani, N.; Bulusu, N. Block-Supply Chain: A New Anti- Counterfeiting Supply Chain Using NFC and Blockchain. In Proceedings of the 1st Workshop on Cryptocurrencies and Blockchains for Distributed Systems (ACM CryBlock’18), Munich, Germany, 15 June 2018; pp. 30–35. [Google Scholar]
- Hyperledger Fabric. Available online: https://www.hyperledger.org/use/fabric (accessed on 2 July 2021).
- Hyperledger Sawtooth. Available online: https://www.hyperledger.org/use/sawtooth (accessed on 2 July 2021).
- Open Enclave SDK. Available online: https://openenclave.io/sdk/ (accessed on 2 July 2021).
- Open SSL. Available online: https://www.openssl.org/ (accessed on 2 July 2021).
- Proof of Elapsed Time (PoET) Consensus in Hyperledger Sawtooth. Available online: https://sawtooth.hyperledger.org/docs/core/releases/latest/introduction.html (accessed on 2 July 2021).
- Hyperledger Avaloin. Available online: https://www.hyperledger.org/use/avalon (accessed on 2 July 2021).
- Monrat, A.A.; Schelén, O.; Andersson, K. A survey of blockchain from the perspectives of applications, challenges, and opportunities. IEEE Access 2019, 7, 117134–117151. [Google Scholar] [CrossRef]
- Gilbert, S.; Lynch, N. Perspectives on the cap theorem. Computer 2012, 45, 30–36. [Google Scholar] [CrossRef] [Green Version]
- Wang, X.; Zha, X.; Ni, W.; Liu, R.P.; Guo, Y.J.; Niu, X.; Zheng, K. Survey on blockchain for internet of things. Comput. Commun. 2019, 136, 10–29. [Google Scholar] [CrossRef]
- Xiao, Y.; Zhang, N.; Lou, W.; Hou, Y.T. A survey of distributed consensus protocols for blockchain networks. IEEE Commun. Surv. Tutorials 2020, 22, 1432–1465. [Google Scholar] [CrossRef] [Green Version]
- Bahga, A.; Madisetti, V.K. Blockchain platform for industrial internet of things. J. Softw. Eng. Appl. 2016, 9, 533–546. [Google Scholar] [CrossRef] [Green Version]
- Esposito, C.; Castiglione, A.; Martini, B.; Choo, K.-K.R. Cloud Manufacturing: Security, Privacy, and Forensic Concerns. IEEE Cloud Comput. 2016, 3, 16–22. [Google Scholar] [CrossRef]
- Li, Z.; Barenji, A.V.; Huang, G.Q. Toward a blockchain cloud manufacturing system as a peer to peer distributed network platform. Robot. Comput. Integr. Manuf. 2018, 54, 133–144. [Google Scholar] [CrossRef]
- Kumar, T.; Harjula, E.; Ejaz, M.; Manzoor, A.; Porambage, P.; Ahmad, I.; Liyanage, M.; Braeken, A.; Ylianttila, M. BlockEdge: Blockchain-Edge Framework for Industrial IoT Networks. IEEE Access 2020, 8, 154166–154185. [Google Scholar] [CrossRef]
- Cinque, M.; Esposito, C.; Russo, S.; Tamburis, O. Blockchain-empowered decentralised trust management for the Internet of Vehicles security. Comput. Electr. Eng. 2020, 86, 106722. [Google Scholar] [CrossRef]
- Hammi, M.T.; Hammi, B.; Bellot, P.; Serhrouchni, A. Bubbles of trust: A decentralized blockchain-based authentication system for IoT. Comput. Secur. 2018, 78, 126–142. [Google Scholar] [CrossRef]
- Fernández-Caramés, T.M.; Fraga-Lamas, P. A Review on the Application of Blockchain to the Next Generation of Cybersecure Industry 4.0Smart Factories. IEEE Access 2019, 7, 45201–45218. [Google Scholar] [CrossRef]
- Leng, J.; Ye, S.; Zhou, M.; Zhao, J.L.; Liu, Q.; Guo, W.; Cao, W.; Fu, L. Blockchain-Secured Smart Manufacturing in Industry4.0: A Survey. IEEE Trans. Syst. Man, Cybern. 2021, 51, 237–252. [Google Scholar] [CrossRef]
- Fraga-Lamas, P.; Fernández-Caramés, T.M. Review on Blockchain Technologies for an Advanced and Cyber-Resilient Automotive Industry. IEEE Access 2019, 7, 17578–17598. [Google Scholar] [CrossRef]
- Balistri, E.; Casellato, F.; Giannelli, C.; Lazzarini, R.; Keyi, C.F.N.; Stefanelli, C. Servitization in the Era of Blockchain: The IceCream Supply Chain Business Case. In Proceedings of the 2020 International Conference on Technology and Entrepreneurship (ICTE), Bologna, Italy, 19–22 April 2020; pp. 1–8. [Google Scholar]
- Geiger, S.; Schall, D.; Meixner, S.; Egger, A. Process traceability in distributed manufacturing using blockchains. In Proceedings of the 34th ACM/SIGAPP Symposium on Applied Computing (SAC 19), New York, NY, USA, 4 April 2019; pp. 417–420. [Google Scholar]
- Kaynak, B.; Kaynak, S.; Uygun, O. Cloud Manufacturing Architecture Based on Public Blockchain Technology. IEEE Access 2020, 8, 2163–2177. [Google Scholar] [CrossRef]
- Loukil, F.; Ghedira-Guegan, C.; Boukadi, K.; Benharkat, A.N.; Benkhe-lifa, E. Data Privacy Based on IoT Device Behavior Control Using Blockchain. ACM Trans. Internet Technol. 2021, 21, 1. [Google Scholar] [CrossRef]
- Bai, L.; Hu, M.; Liu, M.; Wang, J. BPIIoT: A Light-Weighted Blockchain-Based Platform for Industrial IoT. IEEE Access 2019, 7, 58381–58393. [Google Scholar] [CrossRef]
- Shen, M.; Liu, H.; Zhu, L.; Xu, K.; Yu, H.; Du, X.; Guizani, M. Blockchain-Assisted Secure Device Authentication for Cross-Domain Industrial IoT. IEEE J. Sel. Areas Commun. 2020, 38, 942–954. [Google Scholar] [CrossRef]
- Lafourcade, P.; Lombard-Platet, M. About blockchain interoperability. Inf. Process. Lett. 2020, 161, 105976. [Google Scholar] [CrossRef]
- Liu, Z.; Xiang, Y.; Shi, J.; Gao, P.; Wang, H.; Xiao, X.; Wen, B.; Hu, Y.-C. HyperService: Interoperability and Programmability across Heterogeneous Blockchains. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 549–566. [Google Scholar]
- Scheid, E.J.; Hegnauer, T.; Rodrigues, B.; Stiller, B. Bifröst: A Modular Blockchain Interoperability API. In Proceedings of the IEEE 44th Conference on Local Computer Networks (LCN), Osnabrueck, Germany, 14–17 October 2019; pp. 332–339. [Google Scholar]
- Pillai, B.; Biswas, K.; Muthukkumarasamy, V. Cross-chain interoperability among blockchain-based systems using transactions. Knowl. Eng. Rev. 2020, 35, E23. [Google Scholar] [CrossRef]
- Koens, T.; Poll, E. Assessing interoperability solutions for distributed ledgers. Pervasive Mob. Comput. 2019, 59, 101079. [Google Scholar] [CrossRef]
- Hyperledger Fabric EVM Chaincode. Available online: https://github.com/hyperledger/fabric-chaincode-evm (accessed on 2 July 2021).
- Thomas, S.; Schwartz, E. A Protocol for Interledger Payments. 2015. Available online: https://interledger.org/interledger.pdf (accessed on 9 November 2020).
- Hyperledger Cactus. Available online: https://www.hyperledger.org/use/cactus (accessed on 2 July 2021).
- Polkadot. Available online: https://polkadot.network/ (accessed on 2 July 2021).
- Cosmos. Available online: https://cosmos.network (accessed on 2 July 2021).
- Chainlink. Available online: https://chain.link/ (accessed on 2 July 2021).
- Interledger. Available online: https://interledger.org/ (accessed on 2 July 2021).
- Lightning. Available online: https://lightning.network/ (accessed on 2 July 2021).
- Substrate. Available online: https://substrate.dev/ (accessed on 2 July 2021).
- Liu, X.; Muhammad, K.; Lloret, J.; Chen, Y.-W.; Yuan, S.-M. Elastic and cost-effective data carrier architecture for smart contract in blockchain. Future Gener. Comput. Syst. 2019, 100, 590–599. [Google Scholar] [CrossRef]
- Sabt, M.; Achemlal, M.; Bouabdallah, A. Trusted Execution Environment: What It is, and What It is Not. In Proceedings of the IEEE Trustcom/BigDataSE/ISPA Conference, Helsinki, Finland, 20–22 August 2015; pp. 57–64. [Google Scholar]
- Jones, M.; Campbell, B.; Mortimore, C. JSON Web Token (JWT) Profile for OAuth 2.0 Client Authentication and Authorization Grants. 2015. Available online: https://tools.ietf.org/html/rfc7523 (accessed on 9 November 2020).
- A Simple Sawtooth “Simplewallet” Transaction family Example. Available online: https://github.com/askmish/sawtooth-simplewallet (accessed on 2 July 2021).
- IFTTT. Available online: https://ifttt.com/ (accessed on 2 July 2021).
- Ganache. Available online: https://www.trufflesuite.com/ganache (accessed on 2 July 2021).
- Hyperledger Besu. Available online: https://www.hyperledger.org/use/besu (accessed on 2 July 2021).
- Bakshi, S.; Yarmosh, Y.; Zhang, L. Enterprise Ethereum Alliance Off-Chain Trusted Compute Specification. Available online: https://entethalliance.github.io/trusted-computing/spec.html (accessed on 24 March 2020).




| Solution | Approach | Security Mechanisms | Cons | |
|---|---|---|---|---|
| Hyperledger Cactus [41] | Notary Scheme | Details Missing | Centralized Cactus Node Server, which can be compromised | |
| Polkadot [42] | Sidechain + Relay Nodes | Shared state between the relay chain and connected parachains | Validators can be compromised, use of costly BFT consensus among blockchains | |
| Cosmos [43] | Sidechain + Relay Nodes | Tendermint Core BFT consensus mechanism and 100-validator node network maintain security | Validators can be compromised, use of costly BFT consensus among blockchains and the deployment of a centralized hub | |
| ChainLink [44] | Network of Relay Nodes | TEE-based connector between on-chain and off-chain systems, with secured adapters towards various blockchains | ERC-20 tokens provide data to any connected blockchain, with no support to shared state | |
| Interledger [45] | Network of Relay Nodes | Conditional transfers to secure payments | Interledger connectors can be compromised | |
| Lightning Network [46] | Hash-locking scheme | Multiple multi-signature channels established among heterogeneous blockchains | Validators can be compromised, only for micropayments |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bellavista, P.; Esposito, C.; Foschini, L.; Giannelli, C.; Mazzocca, N.; Montanari, R. Interoperable Blockchains for Highly-Integrated Supply Chains in Collaborative Manufacturing. Sensors 2021, 21, 4955. https://doi.org/10.3390/s21154955
Bellavista P, Esposito C, Foschini L, Giannelli C, Mazzocca N, Montanari R. Interoperable Blockchains for Highly-Integrated Supply Chains in Collaborative Manufacturing. Sensors. 2021; 21(15):4955. https://doi.org/10.3390/s21154955
Chicago/Turabian StyleBellavista, Paolo, Christian Esposito, Luca Foschini, Carlo Giannelli, Nicola Mazzocca, and Rebecca Montanari. 2021. "Interoperable Blockchains for Highly-Integrated Supply Chains in Collaborative Manufacturing" Sensors 21, no. 15: 4955. https://doi.org/10.3390/s21154955
APA StyleBellavista, P., Esposito, C., Foschini, L., Giannelli, C., Mazzocca, N., & Montanari, R. (2021). Interoperable Blockchains for Highly-Integrated Supply Chains in Collaborative Manufacturing. Sensors, 21(15), 4955. https://doi.org/10.3390/s21154955










