Abstract
The flourishing of Internet of Things (IoT) applications, characterized by vast transmitter populations and the sporadic transmission of small data units, demands innovative solutions for the sharing of the wireless medium. In this context, satellite connectivity is an important enabler for all scenarios in which terminals are under-served by terrestrial communications and are thus fundamental for providing worldwide coverage. In turn, the design of medium access policies that attain efficient use of the scarce spectrum and can cope with flexible yet unpredictable IoT traffic is of the utmost importance. Starting from these remarks, we investigate in this work the coexistence of a quality of service (QoS)-constrained service with IoT traffic in a shared spectrum as alternative to a more traditional orthogonal allocation among the two services, with an eye on satellite applications. Leaning on analytical tools, we provide achievable rate regions, assuming a slotted ALOHA access method for IoT terminals and accounting for practical aspects, such as the transmission of short packets. Interesting trends emerge, showcasing the benefit of an overlay allocation with respect to segregating the resources for the two services.
1. Introduction
Massive machine-type communications (MMTC) and the Internet of Things (IoT) are attracting steadily growing research and industry attention, emerging as a fundamental component for next-generation wireless systems. Driven by a blooming number of IoT applications, this novel communications paradigm aims at serving vast populations of often low-power, low-complexity terminals that generate sporadic traffic in the form of short data packets. Examples of practical relevance span a wide set of scenarios, ranging from smart agriculture or industry, where sensors may collect data (e.g., temperature, pressure, and presence of chemical substances) and deliver status information to a common gateway, to environmental monitoring or asset tracking [1,2,3].
Support for this multitude of use cases is already provided by terrestrial networks in a number of well-established commercial products [4], e.g., LoRa [5,6,7], SigFox [8], Ingenu [9], as well as by standardized approaches, such as NB-IoT and LTE-M [10]. In parallel to this, satellite-based solutions have recently gained traction as a key enabler to provide global coverage to mMTC services [11]. Favored, among other factors, by the significant reduction in launch cost and by the use of off-the-shelves components, such as reprogrammable software defined radios (SDRs), a revived interest toward the deployment of low-Earth orbit (LEO) satellites has characterized the past few years. From this viewpoint, large constellations such as Starlink, OneWeb or the planned Amazon Kuiper are flanked by a growing number of smaller LEO networks focusing on specialized commercial services, e.g., [12,13,14]. Satellite IoT connectivity is one of the key scenarios included in the non-terrestrial networks (NTN) standardization efforts within the 3GPP ecosystem, and is aimed to become part of the standard already from Release 17.
The increasing interest toward mMTC has spurred significant research efforts to tackle a number of challenges that span the whole communications protocol stack. In particular, the intermittent transmission of short packets from IoT terminals calls for innovative approaches. At the physical layer, for instance, the design of the channel codes that operate efficiently over blocks in the order of a few tens to hundreds of bits and with possibly limited channel state information is fundamental [15]. Moreover, the grant-based medium access control policies encountered in traditional human-centric communication systems is largely ineffective for the traffic profile encountered in machine-type applications. As a matter of fact, the overhead needed to coordinate resource sharing in the presence of a massive population of sporadically active transmitters is highly inefficient. In this perspective, a flourishing line of research is emerging, with the proposal of a number of novel modern random access protocols [16,17,18,19]. These solutions lean on a joint design of coding and medium access, allowing to achieve spectral efficiencies comparable to those of coordinated schemes under a truly grant-free paradigm, and offer a promising way forward for next-generation mMTC systems. At the same time, random access is already at the core of current IoT communications, as variations of the basic ALOHA strategy [20] are employed by many widely used mMTC solutions [5,8,11].
From this standpoint, grant-free and coordinated access policies offer complementary characteristics, and are commonly employed side by side. Indeed, many communications systems host and provide support to a variety of use cases, ranging from sporadic and often lower-priority mMTC traffic to services with more stringent demands in terms of data rate, reliability and quality of service (QoS). This combination is typically achieved by assigning blocks of orthogonal resources (slices)—in time, frequency, or a combination thereof—to applications with distinct requirements. Relevant examples in this direction are the ETSI S-MIM standard for S-band mobile interactive multimedia [21], focusing on the satellite uplink, or the mobile communications standard 5G from 3GPP [22]. In the former case, the transmission of regular or high data rate traffic is served via demand-assignment procedures, whereas delivery of IoT messages can be attempted on dedicated resource blocks via a variation of spread spectrum ALOHA [23]. Similarly, in 5G, a large amount of the spectrum is dedicated to the enhanced mobile broadband (eMBB) traffic, while IoT messages are sent via the NB-IoT waveform in dedicated sub-bands or unused guard bands [24].
By construction, such approaches avoid interference between different services, easing the provision of proper QoS levels and simplifying waveform design. On the other hand, the reservation of orthogonal sets of resources may not be fully efficient in the presence of machine-type communications. In fact, the unpredictable nature of mMTC traffic inherently leads to significant load fluctuations, hindering the precise tuning of the amount of bandwidth to be allocated and often resulting in an either heavily congested or under-utilized channel. From a different angle, instead, a controlled level of interference may be tolerated by non-mMTC services without violating the target QoS requirements. Indeed, information theoretic results on the multiple access channel show that spectrum sharing and interference cancellation allow to achieve the corner points of the capacity region, suggesting that the coexistence of the two services over a shared band may be beneficial.
Starting from these remarks, we explore in this work the possibility to serve different types of traffic over the same set of resources concurrently. Specifically, we tackle the need to provide uplink support to traffic with a specific QoS target as well as to enable transmission for a best-effort service to IoT devices. Leaning on information theoretic tools, we derive the maximum aggregate rate that can be granted to mMTC traffic without violating the rate and reliability requirements of the coexisting service. We then compare the performance of such an overlay configuration to a benchmark setup where resources are orthogonally split, highlighting promising gains.
1.1. Related Work
The first research direction considered spectrum coexistence for geographically spaced systems [25,26]. More recently, the idea of sharing bandwidth among non-homogeneous services has started to receive some attention in the context of 5G cellular systems, aiming to go beyond the inefficiencies of orthogonal slicing. In [27], the possibility to multiplex eMBB and ultra-reliable low-latency communications (URLLC) was studied following an information theoretic approach, pinpointing the potential of the idea in a multi-cell cloud radio access network (C-RAN). Additional insights are provided in [28], where the two aforementioned services are flanked by mMTC traffic. Among other scenarios, the work studied a heterogeneous non-orthogonal multiple access solution for the OFDM 5G uplink, where resources are shared between eMBB and mMTC with different reliability requirements. Assuming packets that are long enough to justify an asymptotic information-theoretic analysis, the authors explored via numerical solutions some key trade-offs in terms of rates that can be granted to the distinct services, showing how an overlay allocation can be beneficial in certain regimes. Providing efficient connectivity while guaranteeing the target QoS among several concurrent services was also thoroughly investigated above layer two, e.g., [29]. Finally, a survey on inter-system spectrum sharing focusing on services with equal access rights to the resources can be found in [30].
1.2. Main Contributions and Structure of the Paper
Within this line of study, we aim to shed light on the potential of a non-orthogonal resource distribution, as well as to trigger additional research on the topic in a satellite-IoT context. In particular, in our work, we do the following:
- We characterize some fundamental trends for the performance of an overlay allocation of a QoS-constrained service and of mMTC traffic, composed of short packets. Based on practical considerations, we assume the receiver to first attempt decoding the former traffic. In the case of success, its contribution is removed (interference cancellation), and retrieval of the underlying mMTC packets is attempted;
- In this setup, we derive the exact analytical expressions for the maximum aggregate rate that can be granted to mMTC traffic as a function of the requirements in terms of the rate and packet error rate set for the QoS-constrained service;
- Going beyond the approach followed in [28], the analysis relies on information theoretic arguments to capture the impact of short packets transmission, as well as the impact of the length of frames in which the uplink communication is organized.
The remainder of this paper is structured as follows. After introducing the system model in Section 2, we provide in Section 3 the initial insight by comparing the performance of the overlay and orthogonal allocations in a setting characterized by packets long enough to justify the use of asymptotic information theoretic tools, considering both an ergodic and a non-ergodic case. The study is then complemented in Section 4 by exploring the impact of transmission of short packets commonly encountered in mMTC applications, relying on the normal approximation [31,32]. The numerical results are presented and discussed in Section 5, highlighting some fundamental trends and comparing the effectiveness of orthogonal and overlay allocations in all of the considered cases. Finally, Section 6 draws the conclusions, offering some relevant open issues and future research directions.
1.3. Notation
We denote random variables (vectors) by uppercase (bold) letters, while we refer to their realizations in lowercase, e.g., X and x; and . The probability mass function (PMF) of a discrete r.v. is denoted as and that of a discrete random vector as . Moreover, we indicate the conditional PMFs as and as . Finally, the expectation operator is denoted as , while is the identity matrix of size k.
2. System Model and Preliminaries
Throughout our discussion, we focus on the uplink of a wireless satellite system which supports two distinct services, labeled as and . The former grants specific requirements in terms of data-rate and error probability, and is embodied in our setting by a single user, , which sends data to the receiver under an average power constraint, whenever it is granted access to the medium. On the other hand, foresees that a large number of terminals share the wireless channel under a slotted ALOHA contention policy [33] to attempt packet delivery in a best-effort fashion, e.g., for mMTC. Specifically, over any time slot allotted to , a variable number of users U access the channel, each transmitting toward the receiver for the whole slot duration with average power . We note that, while the single user for the transmission of a data packet is subject to an average power constraint , the overall power injected in the system by service varies both with the number of terminals accessing the channel over a single slot and the number of allocated slots. Such a working assumption is representative of the practical implementations of machine-type communications. Following a common approach, U is modeled as a Poisson r.v. of parameter , independent and identically distributed across slots, so that the following holds:
The assumption is especially representative for traffic generated by a multitude of low duty cycle nodes monitoring and/or reporting data generated by heterogeneous systems and phenomena [34], as often encountered in mMTC satellite systems. Furthermore, we consider for no feedback on the outcome of sent packets nor retransmission policies. This approach is in line with the best-effort nature of many IoT applications, where packets losses may be tolerated, awaiting the delivery of a successive update from the monitored devices.
To characterize the performance of the system, we tackle two operation modes, considering an orthogonal and an overlay allocation for and . In both cases, having in mind the uplink of a satellite system, we assume for the link between a transmitter and the receiver a line-of-sight connection with perfect power control. Accordingly, the channel coefficient at the receiver is a constant and known value for all users, assumed to be unitary for the sake of simplicity, and all users of a given service are received with the same power level.
2.1. Orthogonal Allocation
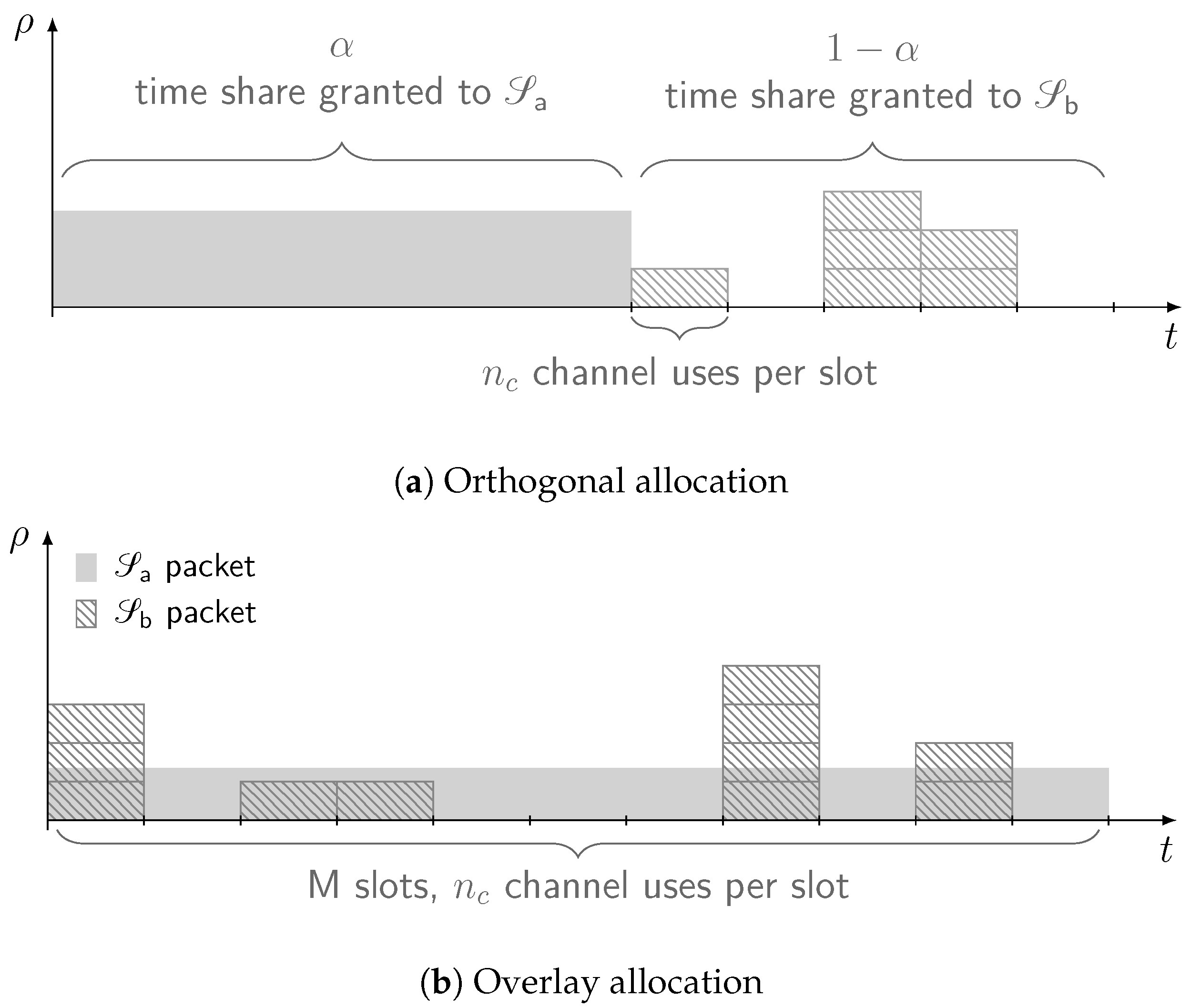
In this configuration, resources are split between services so that no mutual interference between and arises. Without loss of generality, we assume orthogonality to be achieved in time and focus on the setup exemplified by Figure 1a (the reported analysis and results would hold for an orthogonal allocation in the frequency domain as well). Time is divided into successive frames of equal duration. Within each frame, a fraction of the time is granted exclusively to for data delivery. During this period, the channel output at the receiver over the ℓ-th channel use takes the following form:
where is the complex symbol transmitted by the user, and is a zero mean, variance, circularly-symmetric complex Gaussian additive noise component. In view of the fraction of resources available for transmission, the average signal-to-noise ratio (SNR) at the receiver is thus, as follows:
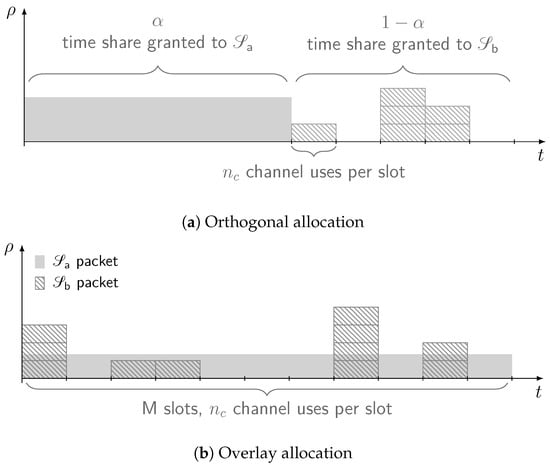
Figure 1.
Reference timeline for the orthogonal and overlay resource allocations.
As for users of the best-effort service , channel access is only permitted during the remaining fraction of the time. To instantiate a slotted ALOHA policy, the corresponding portion of the frame is assumed to be divided in slots of equal duration, each allowing the transmission of a single packet of . Denoting by the number of channel uses over a slot, the input–output relation over the ℓ-th slot conditioned on having users concurrently transmitting can be expressed as follows:
In (2), is the codeword transmitted by the j-th user of active in slot ℓ, whose components are modeled as i.i.d. circularly-symmetric normal r.v. with zero mean and variance , i.e., . In turn, is the additive Gaussian noise, leading to the incoming signal vector at the receiver, . Note that when , no user of transmits over the slot, and the summation in (2) brings no contribution so that solely the noise component is observed. As discussed in Section 1, this event, occurring with probability , represents a waste of resources, as bandwidth granted to mMTC is not employed to attempt data delivery.
2.2. Overlay Allocation
When the system is operated in overlay mode, both services are allowed to access the channel concurrently and without time restrictions, as illustrated in Figure 1b. Such a policy allows and to enjoy the whole share of resources at the cost of suffering from mutual interference, due to the loss of orthogonality. In this case, the whole frame is assumed to be split in slots, each consisting of channel uses. Using all the resources, transmits then a codeword of size channel uses. In turn, users of service can send a packet over any of the available slots. To properly capture the signal model, although encodes its message across all the available channel uses, it is convenient to express as the concatenation of the sub-codewords transmitted over the slots as follows:
where , . Following this notation, the channel output at the receiver over the ℓ-th slot conditioned on having users of access the channel takes the following form:
A packet of a best-effort user is thus always affected by the interference coming from , and possibly by other transmissions of . Conversely, any sub-codeword sent by is received interference-free with probability , i.e., if no mMTC user has transmitted over the corresponding slot. It is worth stressing that the number of interfering packets from is not known a priori, so the coding rate of cannot be dynamically adapted on a slot-by-slot basis.
For both the orthogonal and overlay configurations, we are interested in the maximum sum rate that the system can offer to the best-effort service while granting the QoS requirements of . Specifically, denoting by the rate in bits per channel use of and by the average aggregate number of bits per channel use decoded at the receiver for , we aim at deriving the rate region given by all pairs that allow to experience an error probability that is less than or equal to a target value.
3. Asymptotic Analysis
In order to gather preliminary insight on the performance of the system, we first consider an asymptotic setting in which the codewords transmitted by , as well as those by users of over a slot, can be made long enough to approach the classical information theoretic results.
3.1. Orthogonal Allocation
When resources are orthogonally split among services, delivers data over an additive white gaussian noise (AWGN) channel with SNR defined in (1), yet is allowed to transmit only for a fraction of the time. In this setting, the user can then communicate with vanishing small error probability for any rate as follows:
Let us focus instead on the share granted to , and indicate as the communication rate achieved by the service over the ℓ-th slot. If no user accesses the channel (i.e., ), then clearly . Conversely, if a single transmission is performed (, with probability ), data are sent over an AWGN channel with capacity as follows:
Finally, when more than one user becomes active over the slot, a collision takes place, and the channel output at the receiver takes the general form of (2). As will be discussed later (see Remark 1), we assume terminals of to encode information at a rate approaching , as would be done in the absence of interference. Accordingly, in the event of a collision, the actual channel capacity falls below the employed rate, and we regard all packets sent over the slot of interest to be lost. In other words, following a common modeling approach for random access schemes (e.g., [20]), collisions are of a destructive nature, and whenever more than one user accesses the channel concurrently (). In summary, (i) for , , and (ii) for , . Combining these observations, the average rate for in bits per channel use over a slot readily follows:
Equation (6) clarifies how, for any given power level , the slotted ALOHA best-effort channel shall be operated at a load (pkt/slot) in order to maximize the average aggregate rate. Recalling that only a fraction of the resources can be leveraged, the achievable sum-rates for are then characterized as follows:
Remark 1.
The widely-employed assumption of destructive collisions reflected in (6) is of practical relevance for the considered mMTC setting. Indeed, given that the number of competing terminals over a slot cannot generally be predicted before transmission, a coding scheme that effectively and dynamically takes into account interfering packets may be difficult to develop and goes beyond the complexity of the available terminals. On the other hand, a backoff on the transmission rate to increase resiliency to interference may not be efficient in lightly loaded channels, where sporadic access may lead to having many slots without contention, resulting in significance performance loss for the tight link budget configurations that are typical of mMTC links. Finally, we note that many machine-type applications attempt the delivery of updates that are often repeated or very much correlated in content over time (e.g., reporting of sensed data), positively trading off higher packet loss rates due to interference for a larger aggregate channel sum rate achieved in the absence of coordination among nodes.
3.2. Overlay Allocation
When the system is operated in overlay configuration, the incoming signal at the receiver is the superposition of transmissions performed by both services. Throughout our study, we assume decoding to start from the message sent by , treating the interference component of packets as noise. In the case of successful decoding, ideal interference cancellation is performed, removing the contribution of from the overall waveform and presenting to the receiver the -slot frame populated by packets of alone for further processing. Ideal interference cancellation of the packet of user can be regarded as a reasonable assumption, especially taking into account that its transmission can enjoy a large number of channel uses, and the data-aided channel estimation can be properly tuned. Moreover, we also note that non-ideal interference cancellation would yield a minor impact on the model by effectively increasing the noise power suffered by the transmissions of service since both the signal and the noise are modeled as Gaussian distributed r.vs..
Remark 2.
The assumption on the order of decoding for the supported services stems from two practical considerations. First, as will be further discussed in Section 4 and Section 5, mMTC traffic is typically composed of very short packets—often in the order of a few hundreds of bits— confining pilot symbols to few channel uses per transmitted message in order to avoid excessive overhead. Accurate channel estimation needed for decoding packets of , especially in the presence of interference from , may thus not be viable. On the other hand, the longer data units that characterize render the cost of stronger pilot sequences manageable, and, together with its more regular and predictable traffic patterns, can lead to estimates of the channel parameters that are good enough to retrieve information and perform accurate interference cancellation. In addition to this, the choice of initiating decoding from is driven by QoS arguments. It is indeed reasonable to overlay best-effort mMTC traffic to an existing service only as long as the latter does not experience a significant loss in performance. Along this line of reasoning, the receiver shall be able to decode even in the presence of underlying interference, i.e., treating the whole of traffic as noise.
Under this assumption, experiences the block-interference channel described in (3), with the interference level remaining constant over a coherence period of one slot duration, and changing to an independent realization during the subsequent channel uses. Specifically, conditioned on the number of users of accessing the channel over the ℓ-th slot, the r.v. describing the signal-to-interference and noise ratio (SINR) seen at the receiver for takes the following form:
Within this framework, to better grasp the effect of the bursty overlaid mMTC traffic, we first analyze an ergodic setting, later extending our results to the more practically-relevant non-ergodic setup.
3.2.1. Ergodic Case
When the number of slots within a frame is sufficiently large (i.e., ), the codeword of experiences, in the limit, all the possible interference values, making it possible to define the ergodic channel capacity.
In this case, a vanishingly small error probability can still be granted to the user for any rate . Clearly, from a system design perspective, the overlay operation mode becomes meaningful—and possibly convenient—if the QoS requirements of in terms of data rate are met, even in the presence of interference. We are thus interested in configurations for which the achievable rate in overlay matches the one of an orthogonal allocation, i.e., for which, leaning on (4) and (8),
In particular, for any value of employed to configure a dedicated-resource allocation, (9) imposes a constraint on the tolerable level of interference from in overlay mode, limiting the average number of transmissions per slot and thus the intensity of the mMTC traffic. Denoting this value as , the message of is retrieved and its contribution on the incoming waveform is perfectly canceled with probability approaching one for any channel load of service . We note that, while a closed-form expression of is elusive due to the transcendental nature of (9), its value can easily be determined numerically. If the system is operated satisfying this constraint, the receiver can then process packets sent by mMTC users via slotted ALOHA after having performed interference cancellation, and the average aggregate rate for is once again captured by (6). In order to maximize performance while meeting the requirements of the QoS-driven user, shall thus be operated at a channel load as follows:
We recall indeed that values of larger than 1 [pkt/slot], even if tolerable by the QoS requirements of , would be ineffective from a throughput perspective for the mMTC traffic in view of the detrimental effect of destructive collisions.
Combining these remarks, and recalling that both services have now access to the whole set of resources, the rate region for the ergodic case finally evaluates to the following:
3.2.2. Non-Ergodic Case
Albeit insightful in pinpointing a fundamental trade-off between the achievable rate for and the amount of mMTC traffic that can be served, the ergodic setup fails to capture some important aspects of practical relevance. In particular, the assumption of having an asymptotically large number of slots over which user can encode its message can become highly inaccurate for typical systems, characterized by frames of a length of few hundreds of slots, e.g., [21]. In such conditions, each codeword of service experiences a finite number of interference realizations, and a vanishingly small error probability can no longer be granted. The QoS requirements of the service are therefore more appropriately characterized by a rate-reliability pair, where is complemented by a tolerable error probability for the sent codeword. In the non-ergodic setting, the latter is captured using information theory tools by the outage probability . Specifically, for the block-interference channel under study, the two quantities are related as follows:
where denotes the instantaneous capacity for over the ℓ-th slot, and can be expressed as a function of the number of users transmitting over the slot as follows:
Due to the discrete levels of interference that can be experienced, the r.v. takes values in the alphabet as follows:
and its PMF can readily be derived from (11), leading to the following:
where the final expression resorts to the ancillary quantity as follows:
Leaning on this, let us define for compactness the r.v. as follows:
taking values in the set . Observing that the instantaneous capacity values over different slots are i.i.d., the PMF of V can simply be computed as the -fold convolution of (12), to obtain for any the following:
Accordingly, an exact expression of the outage probability in (10) can finally be derived as follows:
This result offers a useful system design tool. Indeed, for any pair , (12) and (13) provide an exact characterization of the maximum channel load that can be granted to mMTC traffic without violating the QoS requirements of .
Taking such a constraint into account, let us now focus on , aiming to derive the aggregate rate that can be achieved for the maximum arrival intensity sustainable by . In this perspective, we observe that two conditions have to be met for an mMTC packet to be retrieved over a slot in a non-ergodic setup: (i) the packet of is decoded, and (ii) no other user of concurrently accesses the channel over the slot of interest. Note that condition (i) is consistent with the system model assumptions. Indeed, should the message of not be decoded, its interference contribution cannot be removed, affecting any underlying mMTC packet. Recalling the discussion of Remark 1, this would prevent the successful retrieval of information for users of . Furthermore, let us denote by W the r.v. taking values in and counting the number of slots characterized by the transmission of a single user (named also singleton slots) of , which, for the Poisson traffic under study, follows a binomial distribution of parameters and . Following this notation, for any arrival intensity , the aggregate rate of can be conveniently expressed as follows:
where, recalling (10), the term within square brackets takes into account how all w singleton slots bring a contribution of bits per channel use if, and only if, is not in outage. To complete the calculation, we therefore need to derive the outage probability for conditioned on the r.v. W. To this aim, it is useful to rearrange the conditional expression as follows:
where the first addend on the right-hand side of (15) accounts for the sum of the instantaneous capacity of all w slots with a single transmission of service , whereas the summation takes into consideration the contributions of all other slots (i.e., those with ). In turn, the PMF of the instantaneous capacity over a non-singleton slot can be directly derived from (12), to obtain for any value in the alphabet ,
where the normalization factor readily follows from the Poisson distribution of the mMTC traffic. Recalling now that also the r.v. over non-singleton slots are i.i.d., the PMF of the sum of such values can be once more derived by taking the -fold convolution of (17), allowing to compute (16). Leaning on this result, and plugging the binomial distribution of W into (14), can be finally computed for any value of as follows:
The presented approach provides thus the sought pairs of sustainable rates. As discussed, the maximum sustainable arrival intensity for can be computed from (13) for any target QoS requirements (). In turn, mMTC traffic can be operated effectively at any channel load lower than , with the corresponding aggregate rate obtained by evaluating (18) for .
4. Finite Blocklength Analysis
Going beyond the asymptotic setting discussed in Section 3, we complement our study by delving into a more practical scenario that closely relates to mMTC applications, where packets transmitted by users can be in the order of few hundreds bits. To capture this aspect we leverage tools of finite-length information theory, and focus in particular on the normal approximation [31,32] to characterize the rates achievable by and .
4.1. Orthogonal Allocation
Let us first focus on the orthogonal configuration, and denote by n the (finite) number of channel uses available over the whole transmission frame. Following the notation of Section 2, the transmission of spans channel uses, and takes place over an AWGN channel of SNR defined in (1), i.e., we implicitly focus on values of such that . In this case, a vanishingly small error probability cannot be granted, even in the absence of interference, and the performance of is properly described by the couple , where denotes the maximum rate that can be supported for a codeword error probability . Specifically, the two quantities are related as follows [31]:
where the channel capacity and channel dispersion are defined by the following expressions:
and denotes the inverse Q function. If we now recall that the user transmits only for a fraction of the time, and approximates (19) by disregarding the terms of order , the set of rates achievable by for a target error probability can be characterized as follows:
Consider now service . In line with what was discussed in Section 3, collisions are once more regarded as destructive, so slots in which more than one user transmits lead to the loss of all the packets sent. In the setup under study, however, a non-vanishing error probability is to be expected for any transmission rate even over a singleton slot, in view of the finite number of available channel uses. Accordingly, introducing the channel dispersion,
and recalling the channel capacity in (5), the maximum rate that can be granted to under a codeword error probability can be approximated as follows:
In terms of system design, (21) allows then to tune the rate-reliability requirements of . From this standpoint, we assume within our study mMTC traffic to be of the best-effort nature, i.e., without stringent requirements in terms of reliability, and select the transmission rate in order to maximize the attained spectral efficiency. Specifically, we consider to be operated at an error rate that maximizes the information bits per channel use retrieved over a singleton slot:
Finally, recalling that mMTC traffic can enjoy a share of the resources and that the fraction of singleton slots is bounded by (achieved for ), the set of aggregate rates achievable by in the orthogonal configuration can be described as follows:
4.2. Overlay Allocation
As discussed in Section 2, when the system is operated in overlay mode, the total number of channel uses, n, available over a frame is split into time slots of channel uses each, i.e., . Let us denote by the random vector whose components describe the number of users of that transmit over each of the slots. Recalling the i.i.d. Poisson distribution of the r.v. , the joint PMF of can be expressed for any arrival intensity as follows:
Consider now the transmission of , and condition on a specific realization . In this case, each portion of the sent message experiences a distinct (and independent) interference level, allowing to model the problem as the transmission of an n channel uses codeword over parallel AWGN channels. Following the approach presented in [35] in the context of block-fading, the relation between maximum sustainable rate and codeword error probability we can then be approximated as follows:
where
and we introduce for convenience the SINR experienced by over the ℓ-th slot as follows:
Solving (24) with respect to , we can easily obtain the error probability when a given rate is employed by and a specific realization of the interference pattern is experienced:
We now observe that, in view of the random nature of the interference of service , it is more meaningful to evaluate the average error probability as follows:
by employing (23) and (25). The QoS requirements of are properly specified in this case by the pair .
In this perspective, the result in (26) offers a relevant system design tool. Indeed, for any targeted rate , an inspection of the equation allows to derive the maximum traffic intensity of that can be supported without violating the average error probability .
Taking the lead from this, let us then focus on for which we need to compute the maximum aggregate rate that can be achieved under the constraint on . In this case, three conditions have to be met for a mMTC message to be retrieved: (i) the message of has to be decoded and its interference canceled; (ii) the packet of has to be sent over a singleton slot; and (iii) the -channel use codeword has to be decoded. To account for all these conditions, we follow an approach similar to the one discussed in Section 3.2.2, and condition on the number of singleton slots W that take place over the observed frame, writing the aggregate average rate achieved for a traffic intensity as follows:
where we assume that the coding scheme employed by has been tuned following (22), so that each of the w singleton slots brings a contribution of information bits per channel use. Recalling that W follows a binomial distribution of parameters , the complete evaluation of (27) simply requires to specify the joint PMF of the number of users of that transmitted over each of the slots, conditioned on having singleton ones. The distribution can be computed by considering two cases. First, for any vector whose number of components with value 1 (i.e., the number of singleton slots in the considered frame realization) is different from w, we clearly have . For any other , instead.
where the numerator follows from the i.i.d. Poisson distribution of the number of transmissions over a slot, whereas the normalization factor accounts for the probability of having exactly w singleton slots out of the available .
In conclusion, the set of admissible rates for can be computed by taking into account the constraint imposed by the QoS requirements of , and by evaluating (27) for all traffic intensities smaller than .
5. Numerical Results
In this section, we present and discuss some numerical results obtained from the general framework developed in Section 3 and Section 4. Bearing in mind the uplink of a satellite IoT system, we target two relevant scenarios. In the former, packets of both service and reach the receiver with the same power level so that dB. This setting reflects the coexistence of two services whose transmitters have a similar hardware (amplifier, antenna) and thus are received with comparable signal strength. In the latter, the QoS-constrained traffic of is transmitted with higher power, and we consider the configuration dB, dB. The second setting, instead, assumes that the QoS-constrained service features transmitting units equipped with a better and possibly more costly hardware, thus resulting in a more favorable link budget. The selected configurations are in line with LEO satellite systems targeting IoT applications, e.g., [36].
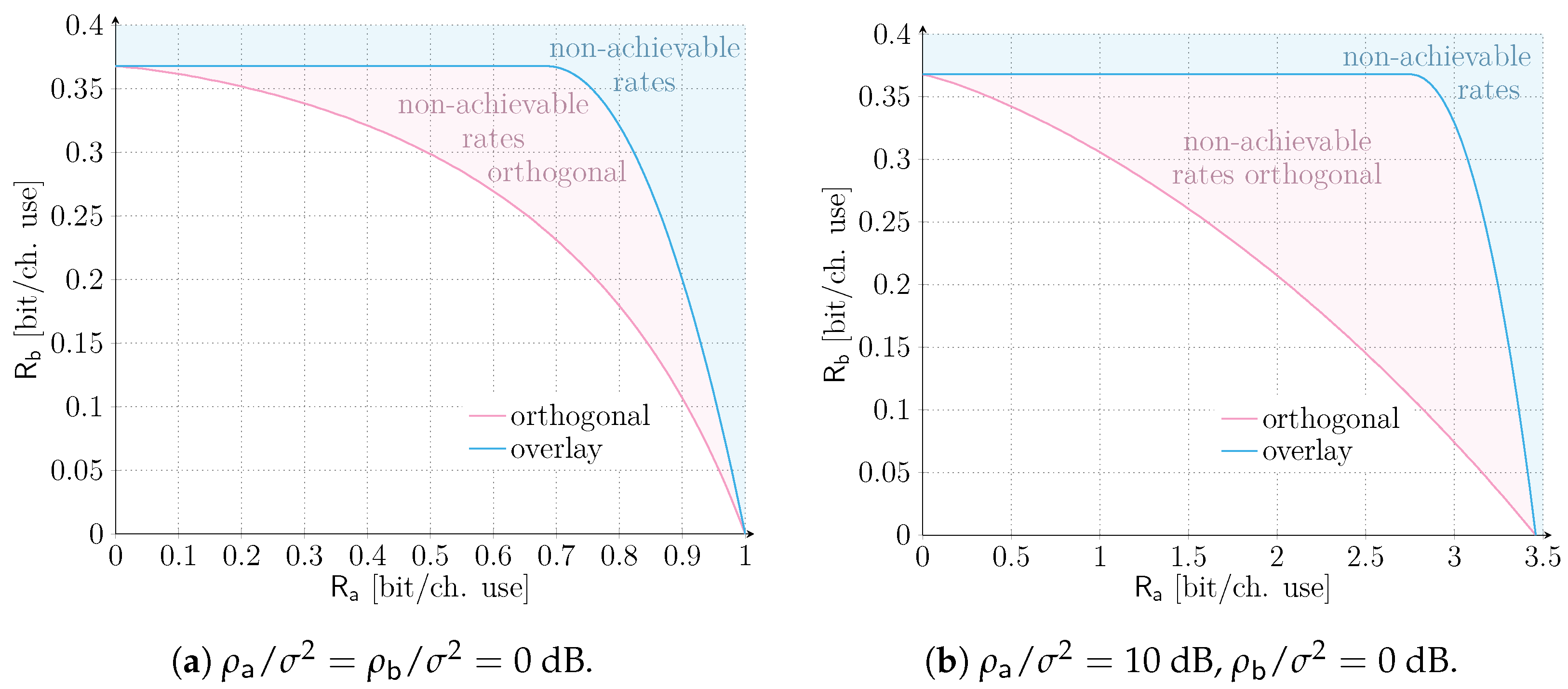
As a starting point, let us focus on the asymptotic, ergodic setting introduced in Section 3. In this case, a vanishingly small error probability can always be granted to , whose QoS requirements are solely specified in terms of a target data rate . The corresponding results are reported in Figure 2. The two solid lines represent the boundary of the rate pairs achievable by orthogonal and overlay allocations respectively, according to (4), (7) and (8). The shadowed light-red area comprises rate pairs achievable only with an overlay allocation, whereas the shadowed light-blue area denotes rates that are non-achievable by any of the two schemes. The two SNR scenarios, i.e., dB and dB, dB are depicted in Figure 2a,b, respectively. In both configurations, irrespective of the target rate of user , an overlay allocation is always beneficial to service in terms of maximum achievable rates. Incidentally, we note that a slightly different trend was observed in [28], where, even in the asymptotic setting, orthogonal allocation may be beneficial for a small rate region. The discrepancy stems from two main factors. First, different channel models, i.e., AWGN with perfect power control vs. Rayleigh fading, are considered. Second, distinct decoding condition on the mMTC service are assumed. Indeed, while in our case we consider destructive collisions, ref. [28] relies on capture effect and interference cancellation (IC) also for service data units.
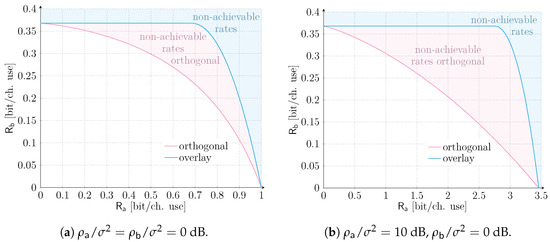
Figure 2.
Asymptotic ergodic rate regions for an orthogonal and overlay allocation of resources of services and . Two scenarios are considered: dB and dB, dB.
From Figure 2, we can also infer that, when the two services are operated in overlay, can achieve its maximum rate of (bit/ch. use) up to (bit/ch. use) for dB, and up to (bit/ch. use) for dB. In other words, increasing the target rate for the QoS-constrained service does not impact service in this region. Especially for the setting of Figure 2b, there is a very large range of rates for service , where the IoT traffic is limited by the poor performance of a slotted ALOHA access method. Indeed, the channel code protection of the data unit of user could allow a larger channel traffic of service , beyond , but cannot be reaped due to the limitation in the medium access. Such a remark hints at how advanced alternatives relying on packet repetition, e.g., [37], can be beneficial to expand the achievable rate region, fostering the need for additional research in this direction. Finally, for (bit/ch. use), or (bit/ch. use) the maximum rate achievable for service sees a larger and steeper degradation with respect to the orthogonal allocation as . As a consequence, more caution on the tuning of the traffic intensity for service shall be devoted for such rates.
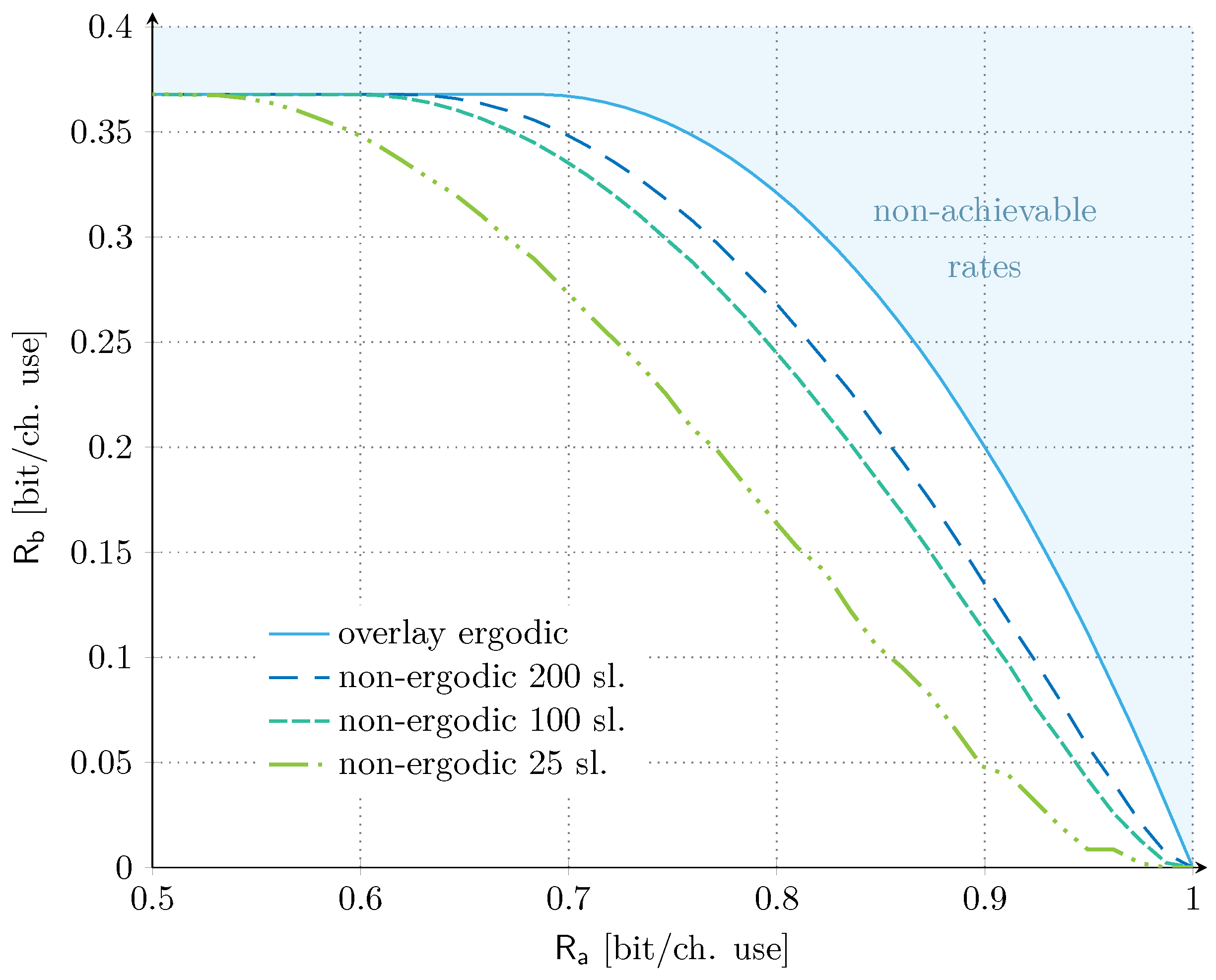
Let us now take a further step and consider the practical constraint imposed by having a finite number of slots within the communications frames (Section 3.2.2). Under these conditions, the transmission of service fails to experience all possible interference levels from service , and a non-ergodic setting has to be considered for the overlay allocation. The corresponding results for a number of time slots in the set are shown in Figure 3 together with the ergodic benchmark as reference. The set of time slots considered is in line with the literature on random access targeting satellite uplink scenarios, e.g., [37,38]. For our discussion, we set the target (average) codeword error probability for service to , and focus on the dB scenario. Similar trends were also found for the unbalanced SNR scenario, and are not reported here for the sake of compactness. The impact of finite-length frames is clearly visible already for a moderately large number of slots, and the reduction of the achievable rate region becomes even more pronounced as the system operates with smaller values of . For example, if user targets a rate of (bit/ch. use), the maximum achievable rate for service is reduced by ∼51% with respect to the ergodic setting, when . The rate contraction becomes even more relevant for larger values of . Conversely, increasing the number of time slots to 100 or 200 mitigates the trend. For the same target rate of (bit/ch. use), the maximum achievable rate for service is reduced by only ∼18% with respect to the asymptotic setting, when 200 slots are considered. On the other hand, it is relevant to remark that, also in the non-ergodic setting, there exists a significant range of rate values for service that allows to operate at the maximum aggregate rate. Such a result confirms the potential of the overlay approach.
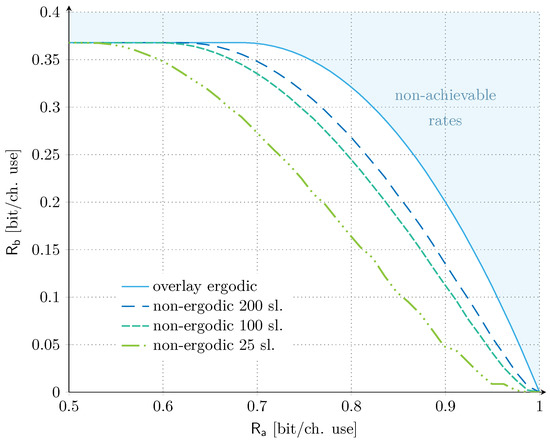
Figure 3.
Asymptotic non-ergodic rate regions for overlay allocation. We fix dB. The number of time slots are in the set and the target outage probability for service is . The asymptotic ergodic rate region for the overlay allocation is also provided for reference.
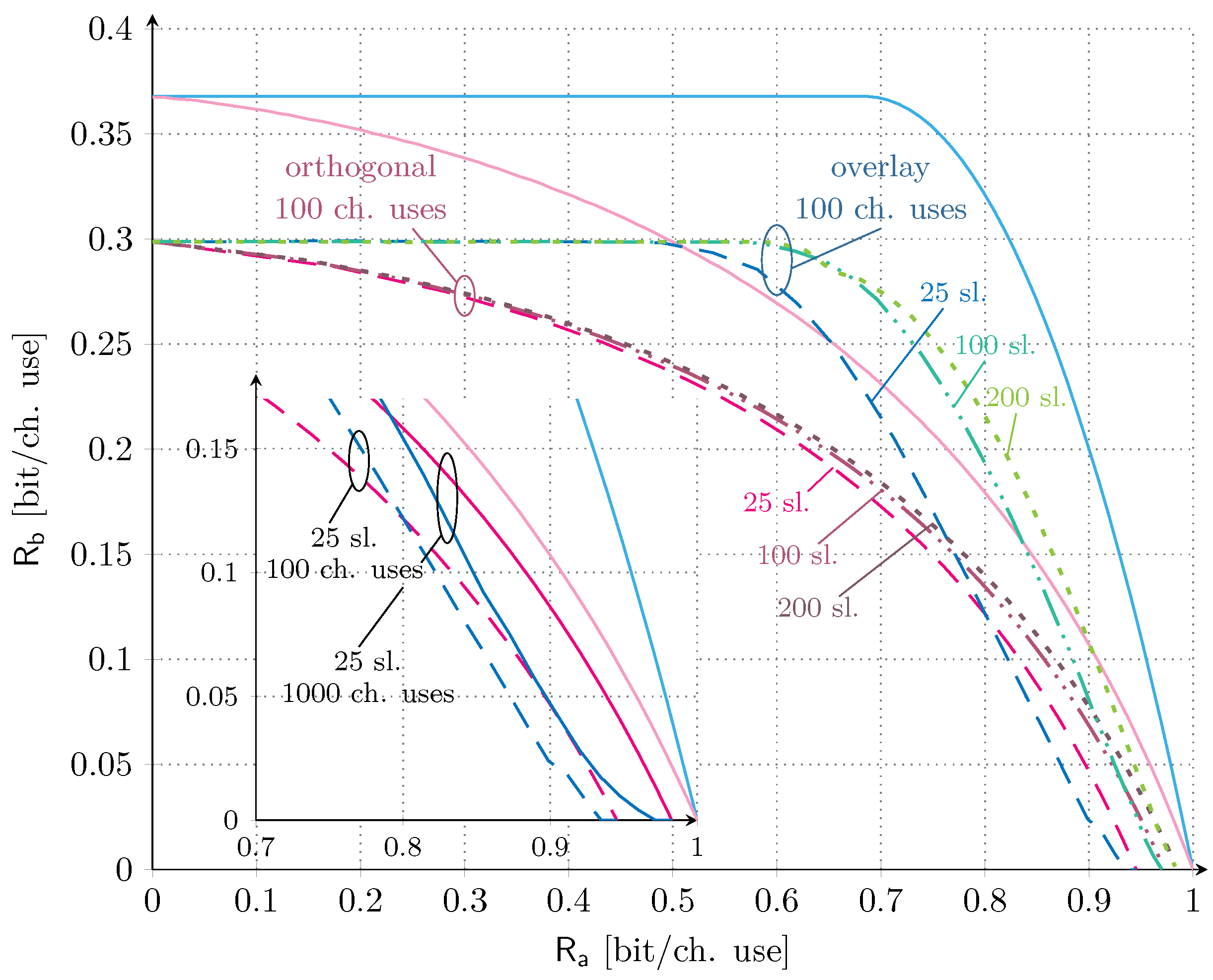
We also investigate the trends under finite codeword length in Figure 4. In this case, not only the time slots, but also the number of channel uses per time slot are finite and we thus rely on the analysis provided in Section 4. As for the previous scenario, we set the target average codeword error probability of service to , and consider dB. The set of time slots is and the set of channel uses per time slot . The latter choice is representative of practical mMTC applications, e.g., LoRa [5] and SigFox [8], which enable the transmission of payloads of up to 96 and 2000 bits, respectively. Accordingly, the set of total channel uses in the orthogonal allocation evaluates to . In the main plot of Figure 4, the orthogonal allocation and the overlay allocation for and channel uses per time slot are compared. As we can observe, increasing the number of time slots has a more beneficial impact on the overlay allocation than on the orthogonal one. In the former case, the increase in the number of time slots allows supporting a larger channel load for service for the same target outage probability. In the latter case instead, it only impacts the correction term in (20) with respect to capacity, and thus results in a minor benefit on the achievable rate pairs. It is also worth noting that, as expected, the finite number of channel uses strongly affects the maximum achievable rate of service , reducing it by ∼18% with respect to the asymptotic case. More interestingly, in contrast with what was discussed in the asymptotic setting, a region where an orthogonal allocation is superior to the overlay configuration emerges. Focusing on the case, such a region is well highlighted in the subplot, where both scenarios with are depicted. Although rather limited and only for rates of service larger than (bit/ch. use), such inversion suggests that reserving a portion of time for the IoT service alone is beneficial instead of letting the two services compete completely.
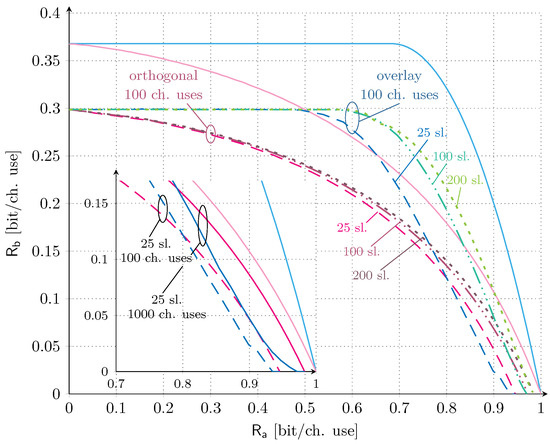
Figure 4.
Finite length results for orthogonal and overlay allocations. We fix dB. The number of time slots are in the set , the number of channel uses per time slot are and the target average codeword error probability for service is . The asymptotic ergodic rate region for the both orthogonal and overlay allocations are also provided for reference.
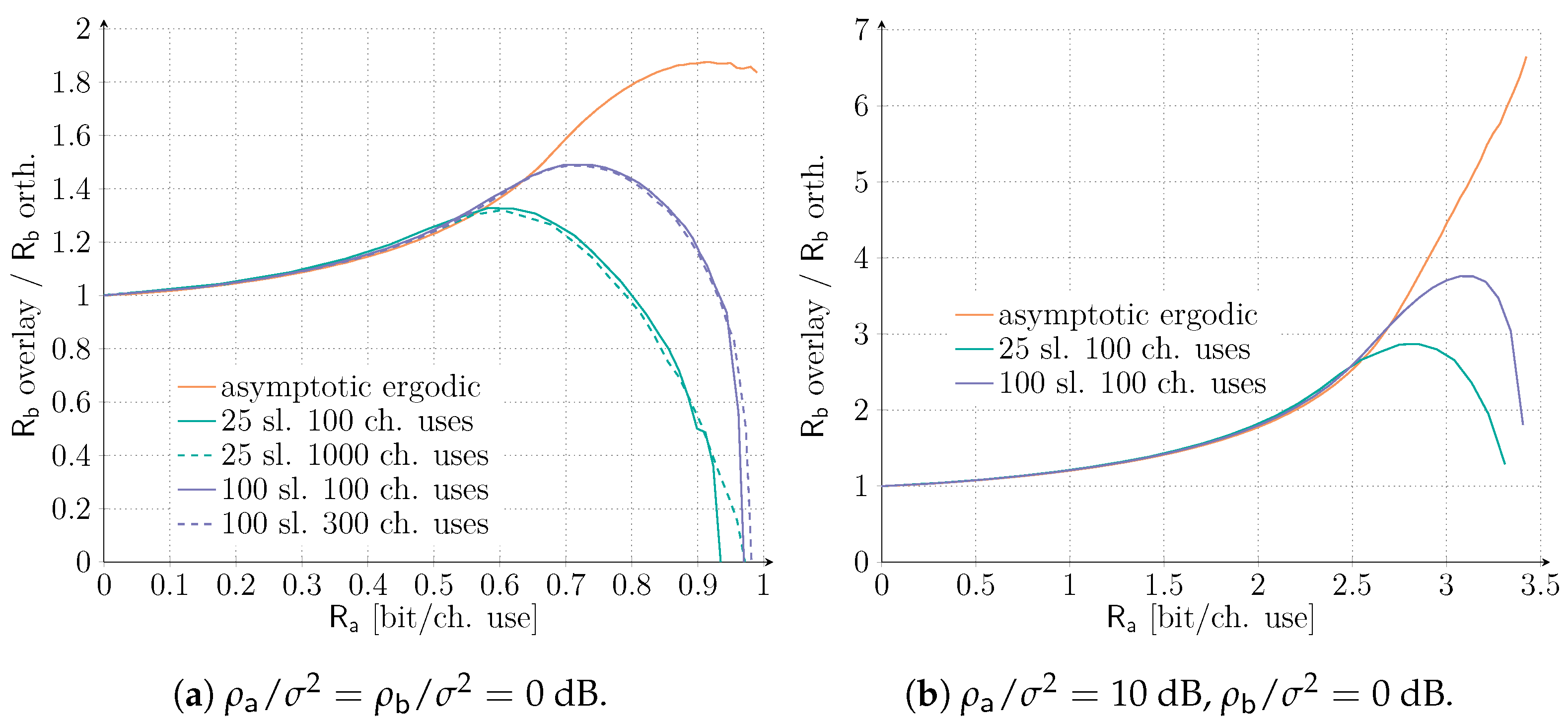
In order to further investigate this aspect, we provide in Figure 5a different angle on the considered results. In particular, we analyze the ratio of the maximum rate achievable by service with an overlay allocation to the one obtained in the orthogonal case as a function of . Values larger than 1 thus identify regions of where an overlay allocation can outperform the orthogonal one, so that a more aggregate mMTC rate is achieved while granting the same performance to the QoS-constrained service. To highlight the impact of short-packet transmissions, we compare the asymptotic, ergodic setting with finite length scenarios. In the latter case, we set the target average codeword error probability of service to . Let us focus first on the setting dB. As already shown in Figure 2, under the asymptotic, ergodic setting, the overlay allocation is always beneficial. However, Figure 5a reveals the presence of an optimal operating point at (bit/ch. use) for which the benefit achieved by the overlay allocation is maximized. A similar trend can also be observed for both and , although for progressively smaller values of rate . Moreover, the improvement reduces as well with the number of available time slots, going from a peak increase in rate for the overlay allocation with respect to the orthogonal one in the asymptotic setting, to a improvement for and for . The plot also confirms that, in practical finite-length setups, there exist values of for which an orthogonal allocation is convenient (i.e., the ratio falls below 1). Nonetheless, such a region drastically reduces by increasing the number of slots available over a frame. Finally, the effect of the number of channel uses appears to have a minor impact. Taking the lead from this, we explore in Figure 5b the configuration dB, dB, focusing only on . Increasing the SNR enjoyed by the QoS-constrained service drastically increases the advantage perceived by the IoT traffic when an overlay allocation is adopted. Rate exceeding a six-fold improvement for the IoT traffic can be achieved in the asymptotic ergodic setting, while, even for as few as 25 slots, more than a two-fold increase in is expected when in overlay allocation. Interestingly, the region where the orthogonal allocation is superior for the equal SNR scenario appears to vanish in this scenario.
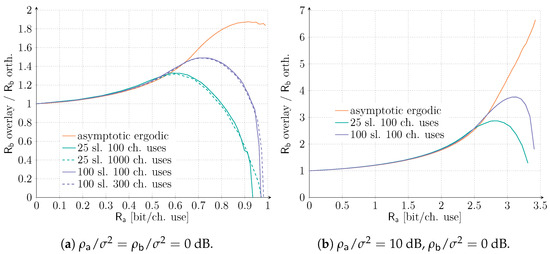
Figure 5.
Ratio of the maximum rate achievable by service with an overlay allocation ( overlay) over the one with an orthogonal allocation ( orth.) as a function of . Both the ergodic asymptotic setting and the finite length scenarios are presented. In the latter, we set the target average codeword error probability of service to 10−3 for both SNR setups. M = 25 and M = 100 slots together with ns = 100 and ns = 300 channel uses are investigated for dB, while only ns = 100 channel uses for are shown.
6. Conclusions and Outlook
In this paper, we investigated the potential of letting two services, a QoS-constrained () and a mMTC (), share a common spectrum by overlaying their transmissions in an AWGN scenario modeling the uplink of a satellite communication system. The receiver attempts decoding of and, if successful, removes its contribution by means of IC, possibly allowing to retrieve data units of the mMTC traffic transmitted with a slotted ALOHA policy. Leveraging analytical tools, we have shown that an overlay allocation is beneficial in most situations, compared to a more traditional orthogonal allocation among the two services. Starting with an asymptotic scenario, where both the codewords and the number of time slots are very large, we delved into a non-ergodic setting (finite number of time slots) and the more practical finite-length regime (both time slots and codewords are finite). Achievable rate regions and expected gains for the IoT aggregate rate when the overlay allocation is adopted are presented for all scenarios. Furthermore, a rate tuple maximizing the improvement on the aggregate rate for the mMTC service is identified, showcasing a possible optimal operating point for the overlay system.
The presented work aims at stimulating further research in the context of the spectral coexistence between mMTC and QoS-constrained traffic in satellite scenarios. The possibility to upgrade the medium access policy of the mMTC service to more advanced solutions and exploring the benefits of modern random access schemes is an interesting direction. For example, the use of repetition-based solutions, e.g., [37], may unleash further benefits of the overlay allocation for low enough rates of the QoS-constrained service. In particular, when strong forward error correction is adopted on service , the mMTC service is not able to fully exploit it since high channel load values are detrimental in slotted ALOHA (cf. Figure 2 and Figure 4, for example). A repetition-based scheme instead, can reap the rewards of a stronger interference rejection in (lower rate) by heavily loading the physical layer with packet copies. Furthermore, we focused in this paper on perfect power control, i.e., all terminals of service are received with the same power. In practical scenarios, in turn, fading and topology trigger variability in the received power levels so that the capture of packets is viable at the receiver. The impact of this aspect is also worth exploring, as it may trigger other relevant benefits and trade-offs, all the more so when coupled with IC, becoming especially relevant in the context of modern random access policies for IoT. The decoding order of services—first , then IC and subsequently —can also be further investigated when power variability is present, along the lines of [28]. Finally, the applicability of the overlay allocation shall be investigated in a real-world scenario, entailing details such as the link budget, topology of the transmitters and effective error correcting code, among others.
Author Contributions
Conceptualization, A.M. and F.C.; methodology, A.M. and F.C.; software, A.M. and F.C.; validation, A.M. and F.C.; formal analysis, A.M. and F.C.; investigation, A.M. and F.C.; writing–original draft preparation, A.M. and F.C.; writing–review and editing, A.M. and F.C.; visualization, A.M. and F.C.; supervision, A.M. and F.C. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
The authors would like to thank Gianlugi Liva, German Aerospace Center (DLR), for the insightful discussions.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Villa-Henriksen, A.; Edwards, G.; Pesonen, L.; Green, O.; Sorensen, C. Internet of Things in arable farming: Implementation, applications, challenges and potential. Biosyst. Eng. 2020, 191, 60–84. [Google Scholar] [CrossRef]
- Aceto, G.; Persico, V.; Pescapé, A. A Survey on Information and Communication Technologies for Industry 4.0: State-of-the-Art, Taxonomies, Perspectives, and Challenges. IEEE Commun. Surv. Tuts. 2019, 21, 3467–3501. [Google Scholar] [CrossRef]
- Dhingra, S.; Madda, R.; Gandomi, A.; Patan, R.; Daneshmand, M. Internet of Things Mobile-Air Pollution Monitoring System (IoT-Mobair). IEEE Internet Things J. 2019, 6, 5577–5584. [Google Scholar] [CrossRef]
- Raza, U.; Kulkarni, P.; Sooriyabandara, M. Low Power Wide Area Networks: An Overview. IEEE Commun. Surv. Tuts. 2017, 19, 855–873. [Google Scholar] [CrossRef] [Green Version]
- LoRa Alliance. The LoRa Alliance Wide Area Networks for Internet of Things. Available online: www.lora-alliance.org (accessed on 2 July 2021).
- Georgiou, O.; Raza, U. Low Power Wide Area Network Analysis: Can LoRa Scale? IEEE Wirel. Commun. Lett. 2017, 6, 162–165. [Google Scholar] [CrossRef] [Green Version]
- Adelantado, F.; Vilajosana, X.; Tuset-Peiro, P.; Martinez, B.; Melia-Segui, J.; Watteyne, T. Understanding the Limits of LoRaWAN. IEEE Commun. Mag. 2017, 55, 34–40. [Google Scholar] [CrossRef] [Green Version]
- Sigfox. SIGFOX: The Global Communications Service Provider for the Internet of Things. Available online: www.sigfox.com (accessed on 2 July 2021).
- Ingenu. Available online: www.ingenu.com (accessed on 2 July 2021).
- Höglund, A.; Lin, X.; Liberg, O.; Behravan, A.; Yavuz, E.; Van der Zee, M.; Sui, Y.; Tirronen, T.; Ratilainen, A.; Eriksson, D. Overview of 3GPP Release 14 Enhanced NB-IoT. IEEE Netw. 2017, 31, 16–22. [Google Scholar] [CrossRef]
- Marchese, M.; Moheddine, A.; Patrone, F. IoT and UAV integration in 5G hybrid terrestrial-satellite networks. Sensors 2019, 19, 3704. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- exactEarth. Available online: www.exactearth.com (accessed on 2 July 2021).
- KLEO. KLEO Connect Gmbh. Available online: www.kleo-connect.com (accessed on 2 July 2021).
- Kepler Communications Inc. Available online: www.keplercommunications.com (accessed on 2 July 2021).
- Coşkun, M.; Durisi, G.; Jerkovits, T.; Liva, G.; Ryan, W.; Stein, B.; Steiner, F. Efficient error-correcting codes in the short blocklength regime. Elsevier Phys. Commun. 2019, 34, 66–79. [Google Scholar] [CrossRef] [Green Version]
- Berioli, M.; Cocco, G.; Liva, G.; Munari, A. Modern Random Access Protocols; NOW Publisher: Boston, MA, USA; Delft, The Netherlands, 2016. [Google Scholar]
- Polyanskiy, Y. A Perspective on Massive Random-Access. In Proceedings of the 2017 IEEE International Symposium on Information Theory (ISIT), Aachen, Germany, 25–30 June 2017. [Google Scholar]
- Fengler, A.; Jung, P.; Caire, G. SPARCs and AMP for unsourced random access. In Proceedings of the 2019 IEEE International Symposium on Information Theory (ISIT), Maison de la Mutualit, Paris, France, 7–19 July 2019. [Google Scholar]
- Amalladinne, V.; Chamberland, J.F.; Narayanan, K. A coded compressed sensing scheme for unsourced multiple access. IEEE Trans. Inf. Theory 2020, 66, 6509–6533. [Google Scholar] [CrossRef]
- Abramson, N. The throughput of packet broadcasting channels. IEEE Trans. Commun. 1977, 25, 117–128. [Google Scholar] [CrossRef] [Green Version]
- ETSI. TS 102 721-3: Satellite Earth Stations and Systems; Air Interface for S-band Mobile Interactive Multimedia (S-MIM); Part 3: Physical Layer Specification, Return Link Asynchronous Access; Technical Report; ETSI: Sophia Antipolis, France, 2012. [Google Scholar]
- Lien, S.; Shieh, S.; Huang, Y.; Su, B.; Hsu, Y.; Wei, H. 5G new radio: Waveform, frame structure, multiple access, and initial access. IEEE Commun. Mag. 2017, 55, 64–71. [Google Scholar] [CrossRef]
- del Rio Herrero, O.; De Gaudenzi, R. High efficiency satellite multiple access scheme for machine-to-machine communications. IEEE Trans. Aerosp. Electron. Syst. 2012, 48, 2961–2989. [Google Scholar] [CrossRef]
- Wang, Y.; Lin, X.; Adhikary, A.; Grovlen, A.; Sui, Y.; Blankenship, Y.; Bergman, J.; Razaghi, H. A primer on 3GPP narrowband internet of things. IEEE Commun. Mag. 2017, 55, 117–123. [Google Scholar] [CrossRef]
- Gastpar, M. On capacity under receive and spatial spectrum-sharing constraints. IEEE Trans. Inf. Theory 2007, 53, 471–487. [Google Scholar] [CrossRef]
- Lee, J.; Andrews, J.; Hong, D. Spectrum-sharing transmission capacity. IEEE Trans. Wirel. Commun. 2011, 10, 3053–3063. [Google Scholar] [CrossRef]
- Kassab, R.; Simeone, O.; Popovski, P. Coexistence of URLLC and eMBB services in the C-RAN uplink: An information-theoretic study. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018. [Google Scholar]
- Popovski, P.; Trillingsgaard, K.F.; Simeone, O.; Durisi, G. 5G wireless network slicing for eMBB, URLLC, and mMTC: A communication-theoretic view. IEEE Access 2018, 6, 55765–55779. [Google Scholar] [CrossRef]
- Trakadas, P.; Karkazis, P.; Leligou, H.; Zahariads, T.; Vicens, F.; Zurita, A.; Alemany, P.; Soenen, T.; Parada, C.; Bonnet, J.; et al. Comparison of management and orchestration solutions for the 5G era. J. Sens. Actuator Netw. 2020, 9, 4. [Google Scholar] [CrossRef] [Green Version]
- Voicu, A.; Simic, L.; Petrova, M. Survey of spectrum sharing for inter-technology coexistence. IEEE Commun. Surv. Tuts. 2019, 21, 1112–1144. [Google Scholar] [CrossRef] [Green Version]
- Polyanskiy, Y.; Poor, H.; Verdu, S. Channel coding rate in the finite blocklength regime. IEEE Trans. Inf. Theory 2010, 56, 2307–2359. [Google Scholar] [CrossRef]
- Durisi, G.; Koch, T.; Popovski, P. Toward massive, ultrareliable, and low-latency wireless communication with short packets. Proc. IEEE 2016, 104, 1711–1726. [Google Scholar] [CrossRef] [Green Version]
- Roberts, L. ALOHA packet systems with and without slots and capture. ACM SIGCOMM Comput. Commun. Rev. 1975, 2, 28–42. [Google Scholar] [CrossRef]
- Metzger, F.; Hoßfeld, T.; Bauer, A.; Kounev, S.; Heegaard, P.E. Modeling of aggregated IoT traffic and its application to an IoT cloud. Proc. IEEE 2019, 107, 679–694. [Google Scholar] [CrossRef] [Green Version]
- Lancho, A.; Koch, T.; Durisi, G. On single-antenna Rayleigh block-fading channels at finite blocklength. IEEE Trans. Inf. Theory 2020, 66, 496–519. [Google Scholar] [CrossRef] [Green Version]
- Conti, M.; Guidotti, A.; Amatetti, C.; Vanelli-Coralli, A. NB-IoT over non-terrestrial networks: Link budget analysis. In Proceedings of the 2020 IEEE Global Communications Conference (GLOBECOM), Taipei, Taiwan, 7–11 December 2020. [Google Scholar]
- Liva, G. Graph-based analysis and optimization of contention resolution diversity slotted ALOHA. IEEE Trans. Commun. 2011, 59, 477–487. [Google Scholar] [CrossRef]
- Casini, E.; Gaudenzi, R.D.; del Rio Herrero, O. Contention Resolution Diversity Slotted ALOHA (CRDSA): An Enhanced Random Access Scheme for Satellite Access Packet Networks. IEEE Trans. Wirel. Commun. 2007, 6, 1408–1419. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).