Cyberattack on Flight Safety: Detection and Mitigation Using LoRa
Abstract
:1. Introduction
1.1. Related Works and Motivation
1.2. Flight Safety
1.3. Flight Safety Vulnerabilities
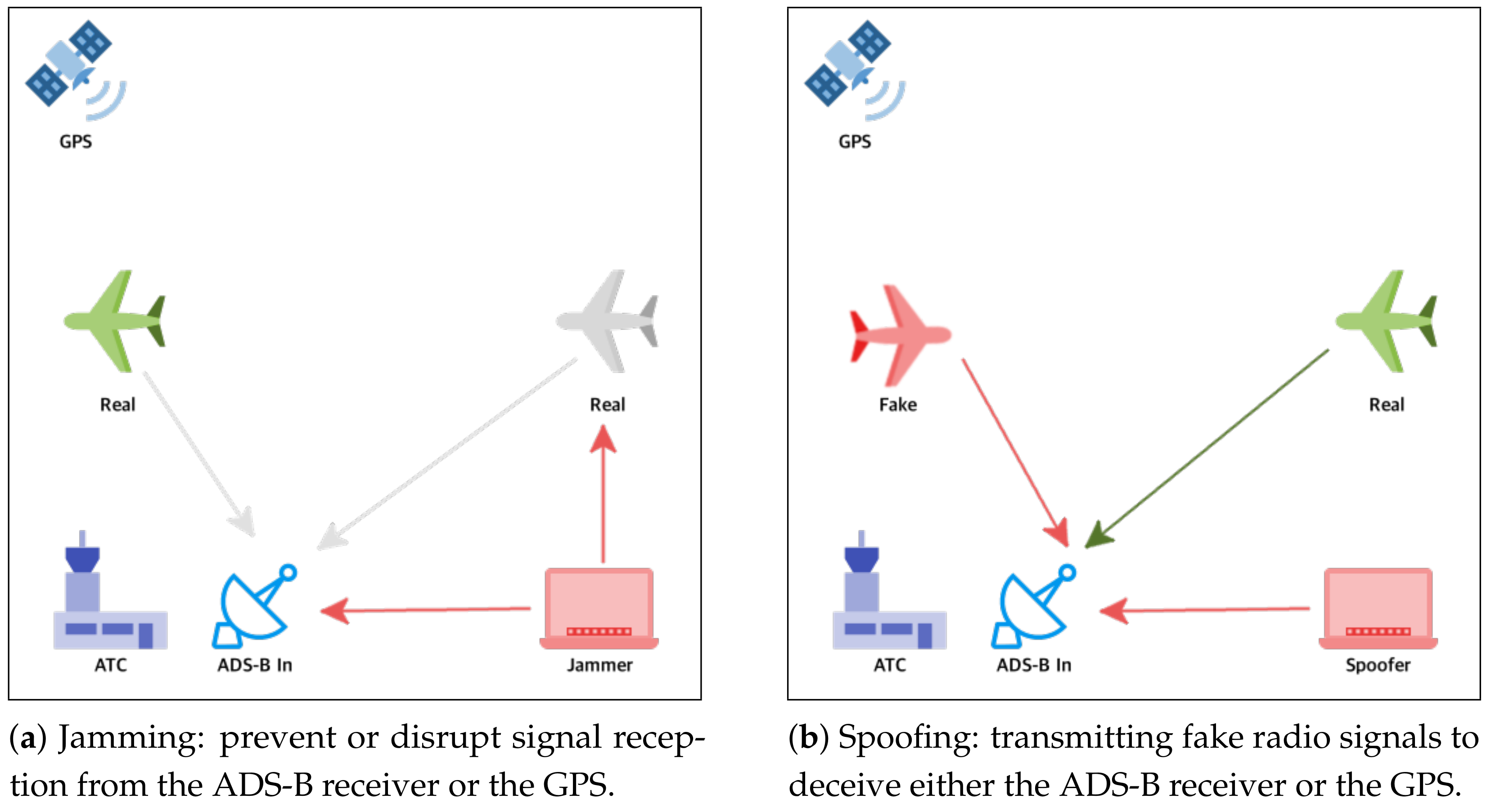
1.4. Jamming
1.5. Spoofing
1.6. Our Contribution
2. Problem of Interest
3. Flight Safety Framework
3.1. Wireless Sensor Networks
3.2. Internet of Things
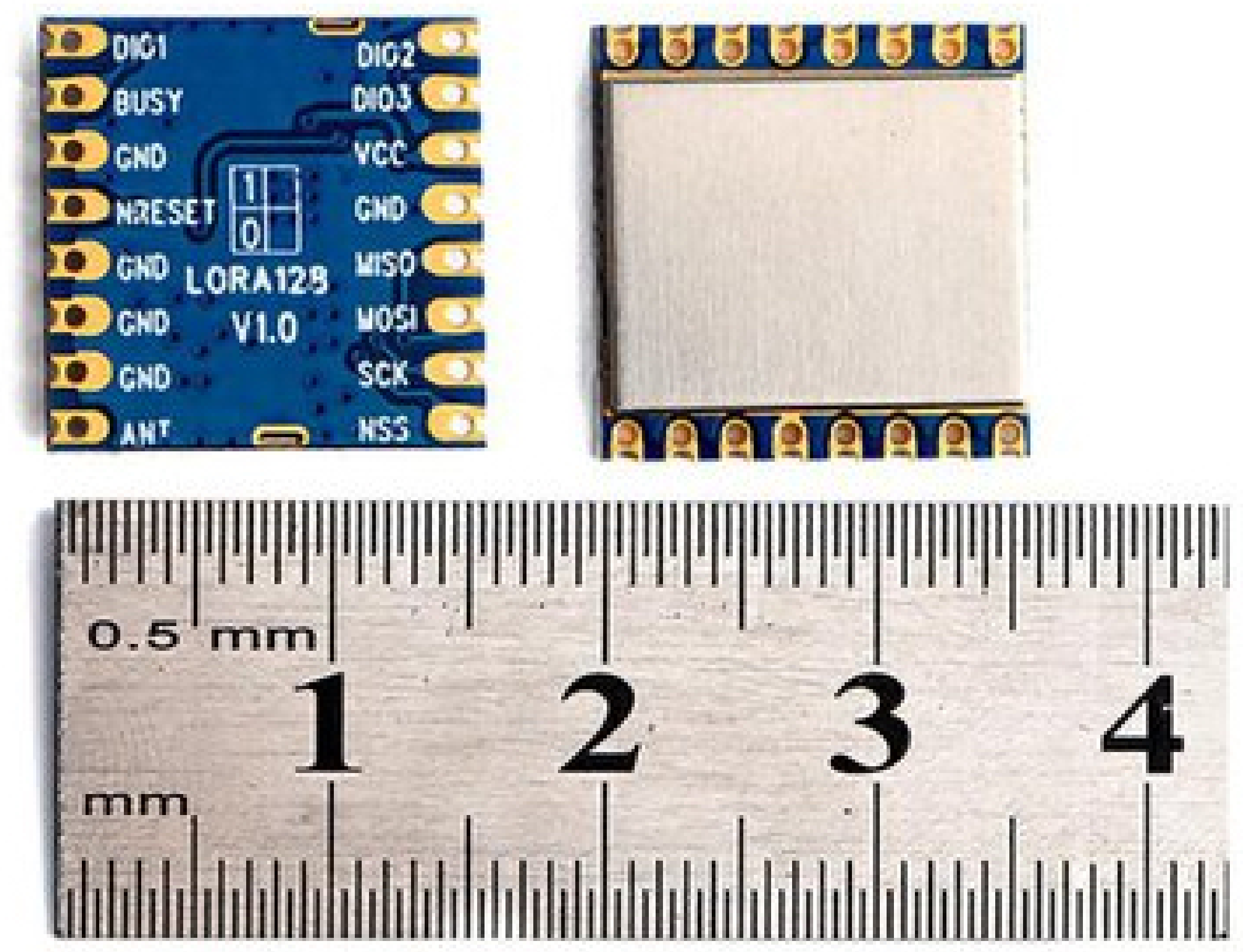
3.3. LoRa Technology
3.4. LoRa 2.4 GHz Band
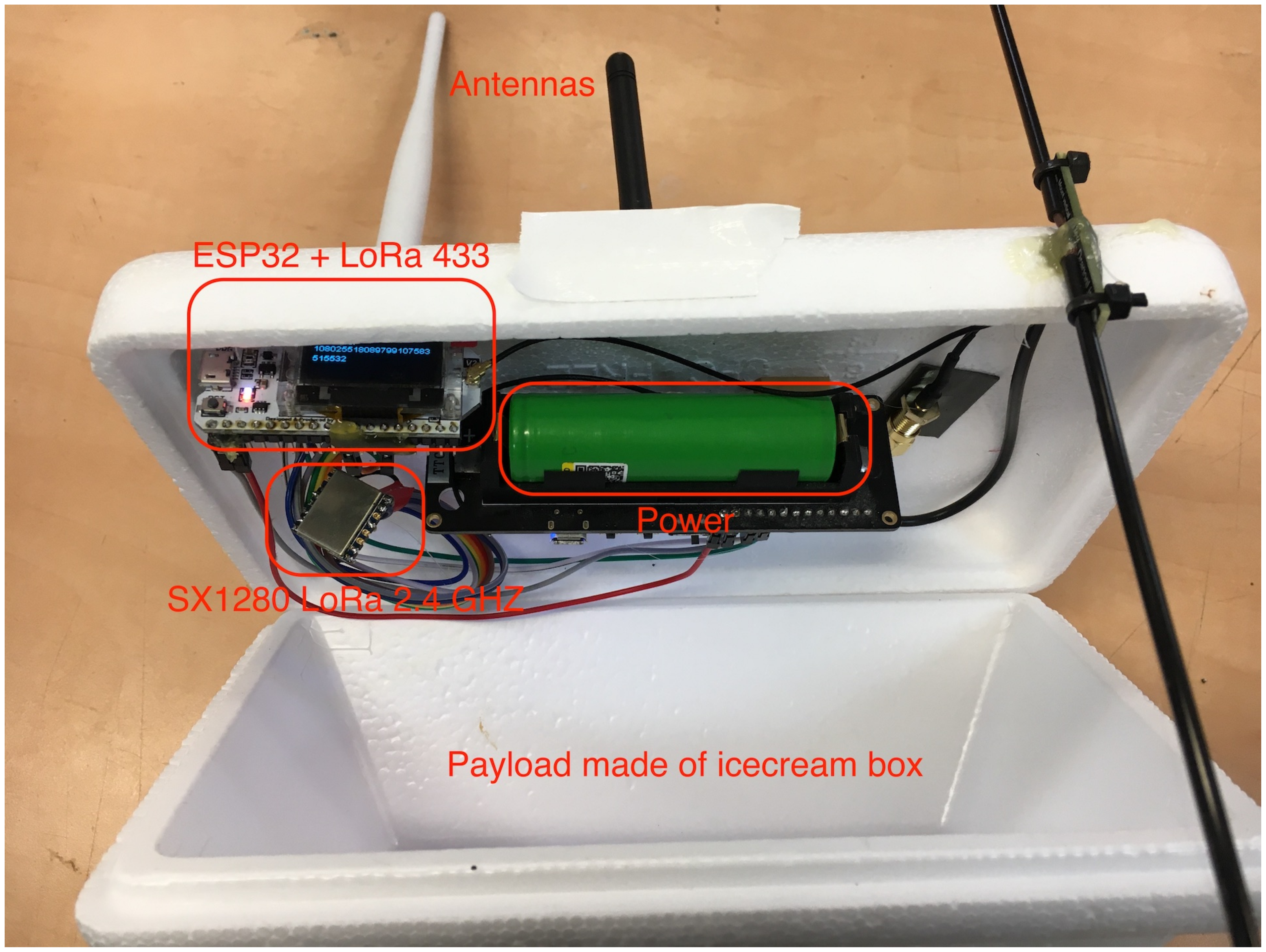
3.5. Setup Implementation
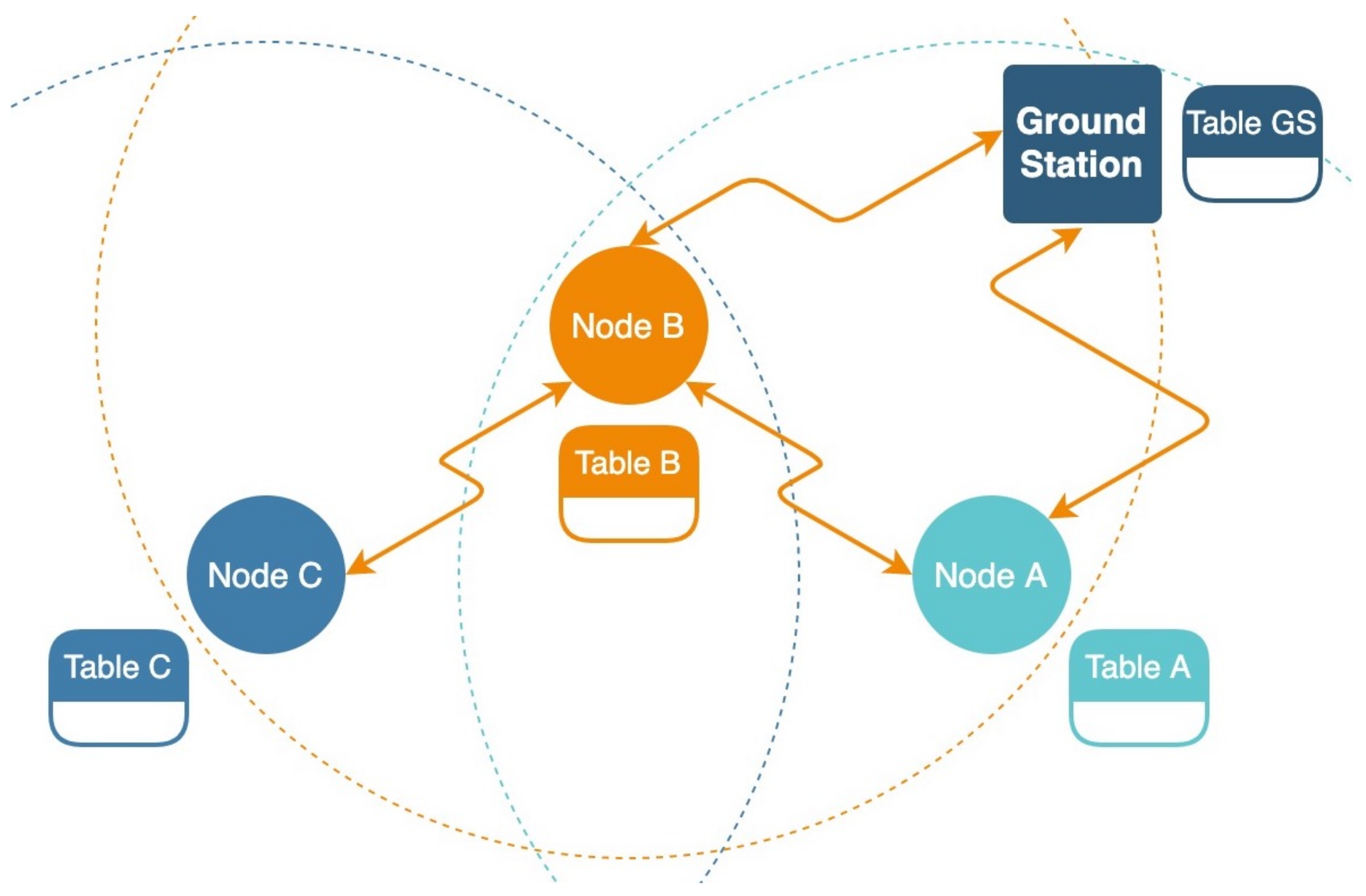
3.6. Wireless Sensor Network Protocol
3.7. Sense and Avoid Protocol
3.8. Message Authentication
4. Simulator and Field Experiment
4.1. Wireless Sensor Network Experiments
4.2. Finding Relative Position Experiments
4.3. Sense and Avoid Experiments
4.4. Doppler Effect
5. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| ADS-B | Automatic Dependent Surveillance-Broadcast |
| ATC | Air Traffic Control |
| FAA | Federal Aviation Administration |
| GNSS | Global Navigation Satellite System |
| ISM | Industrial, Scientific, Medical |
| IoT | Internet of Things |
| RSSI | Received Signal Strength Indicator |
| SNR | Signal-to-Noise Ratio |
| TCAS | Traffic Collision Avoidance System |
| TIS-B | Traffic Information Services-Broadcast |
| ToF | Time-of-Flight |
| UAV | Unmanned Aerial Vehicle |
| WSN | Wireless Sensor Network |
References
- ADS-B and Other Means of Surveillance Implementation Status, in SEASAR. Available online: https://ec.europa.eu/transport/sites/transport/files/20180515-sesar-ads-b-report.pdf (accessed on 15 May 2018).
- Ying, X.; Mazer, J.; Bernieri, G.; Conti, M.; Bushnell, L.; Poovendran, R. Detecting ADS-B Spoofing Attacks Using Deep Neural Networks. In Proceedings of the 2019 IEEE Conference on Communications and Network Security (CNS), Washington, DC, USA, 10–12 June 2019; pp. 187–195. [Google Scholar] [CrossRef] [Green Version]
- Strohmeier, M.; Niedbala, A.K.; Schäfer, M.; Lenders, V.; Martinovic, I. Surveying aviation professionals on the security of the air traffic control system. In Security and Safety Interplay of Intelligent Software Systems; Springer: Basel, Switzerland, 2019; pp. 135–152. [Google Scholar] [CrossRef]
- Leonardi, M.; Strohmeier, M.; Lenders, V. On Jamming Attacks in Crowdsourced Air Traffic Surveillance. IEEE Aerosp. Electron. Syst. Mag. 2021, 36, 44–54. [Google Scholar] [CrossRef]
- Wu, Z.; Shang, T.; Guo, A. Security Issues in Automatic Dependent Surveillance-Broadcast (ADS-B): A Survey. IEEE Access 2020, 8, 122147–122167. [Google Scholar] [CrossRef]
- Innovative 787 Flight Deck Designed for Efficiency, Comfort, and Commonality, Boeing. Available online: https://www.boeing.com/commercial/aeromagazine/articles/2012_q1/3/ (accessed on 27 June 2021).
- Boeing: ADSB Out Certification, Boeing. Available online: http://www.boeing.com/commercial/services/adsb-out-certification.page (accessed on 27 June 2021).
- Mirzaei, K.F.; de Carvalho, B.; Pschorn, P. Security of ADS-B: Attack Scenarios. EasyChair. 2019. Available online: file:///C:/Users/MDPI/AppData/Local/Temp/EasyChair-Preprint-851.pdf (accessed on 4 March 2021).
- Harris, M. FAA Files Reveal a Surprising Threat to Airline Safety: The U.S. Military’s GPS Tests in IEEE Spectrum. Available online: https://spectrum.ieee.org/aerospace/aviation/faa-files-reveal-a-surprising-threat-to-airline-safety-the-us-militarys-gps-tests (accessed on 4 February 2021).
- Goward, D. NASA Report: Passenger Aircraft Nearly Crashes Due GPS Disruption, GPS World. Available online: https://www.gpsworld.com/nasa-report-passenger-aircraft-nearly-crashes-due-gps-disruption (accessed on 8 July 2019).
- Strohmeier, M.; Lenders, V.; Martinovic, I. On the Security of the Automatic Dependent Surveillance-Broadcast Protocol. IEEE Commun. Surv. Tutorials 2015, 17, 1066–1087. [Google Scholar] [CrossRef] [Green Version]
- Airborne Collision Avoidance System (ACAS), SKYbrary. Available online: https://www.skybrary.aero/index.php/Airborne_Collision_Avoidance_System_(ACAS)#Complying_with_RAs (accessed on 6 May 2021).
- Ahmad, M.; Farid, M.A.; Ahmed, S.; Saeed, K.; Asharf, M.; Akhtar, U. Impact and Detection of GPS Spoofing and Countermeasures against Spoofing. In Proceedings of the 2019 2nd International Conference on Computing, Mathematics and Engineering Technologies (iCoMET), Sukkur, Pakistan, 30–31 January 2019; pp. 1–8. [Google Scholar] [CrossRef]
- UAS Remote Identification Overview, FAA. Available online: https://www.faa.gov/uas/getting_started/remote_id/ (accessed on 6 February 2021).
- Sengupta, J.; Ruj, S.; Bit, S.D. A Comprehensive Survey on Attacks, Security Issues and Blockchain Solutions for IoT and IIoT. J. Netw. Comput. Appl. 2020, 149, 102481. [Google Scholar] [CrossRef]
- Bahashwan, A.A.; Anbar, M.; Abdullah, N.; Hanshi, S.M. Review on Common IoT Communication Technologies for Both Long-Range Network (LPWAN) and Short-Range Network. In Advances on Smart and Soft Computing; Springer: Singapore, 2021; pp. 341–353. [Google Scholar]
- Long Range, Long Power, 2.4 GHz Transceiver with Ranging Capability, Semtech. Available online: https://www.semtech.com/ (accessed on 14 February 2021).
- Smith, M.; Strohmeier, M.; Lenders, V.; Martinovic, I. Understanding Realistic Attacks on Airborne Collision Avoidance Systems. arXiv 2020, arXiv:2010.01034. [Google Scholar]
- Doroshkin, A.A.; Zadorozhny, A.M.; Kus, O.N.; Prokopyev, V.Y.; Prokopyev, Y.M. Experimental Study of LoRa Modulation Immunity to Doppler Effect in CubeSat Radio Communications. IEEE Access 2019, 7, 75721–75731. [Google Scholar] [CrossRef]
- Liando, J.C.; Gamage, A.; Tengourtius, A.W.; Li, M. Known and Unknown Facts of LoRa: Experiences from a Large-scale Measurement Study. ACM Trans. Sens. Netw. 2019, 15, 16. [Google Scholar] [CrossRef]
- ExpressLRS. Available online: https://github.com/ExpressLRS/ExpressLRS (accessed on 22 June 2021).






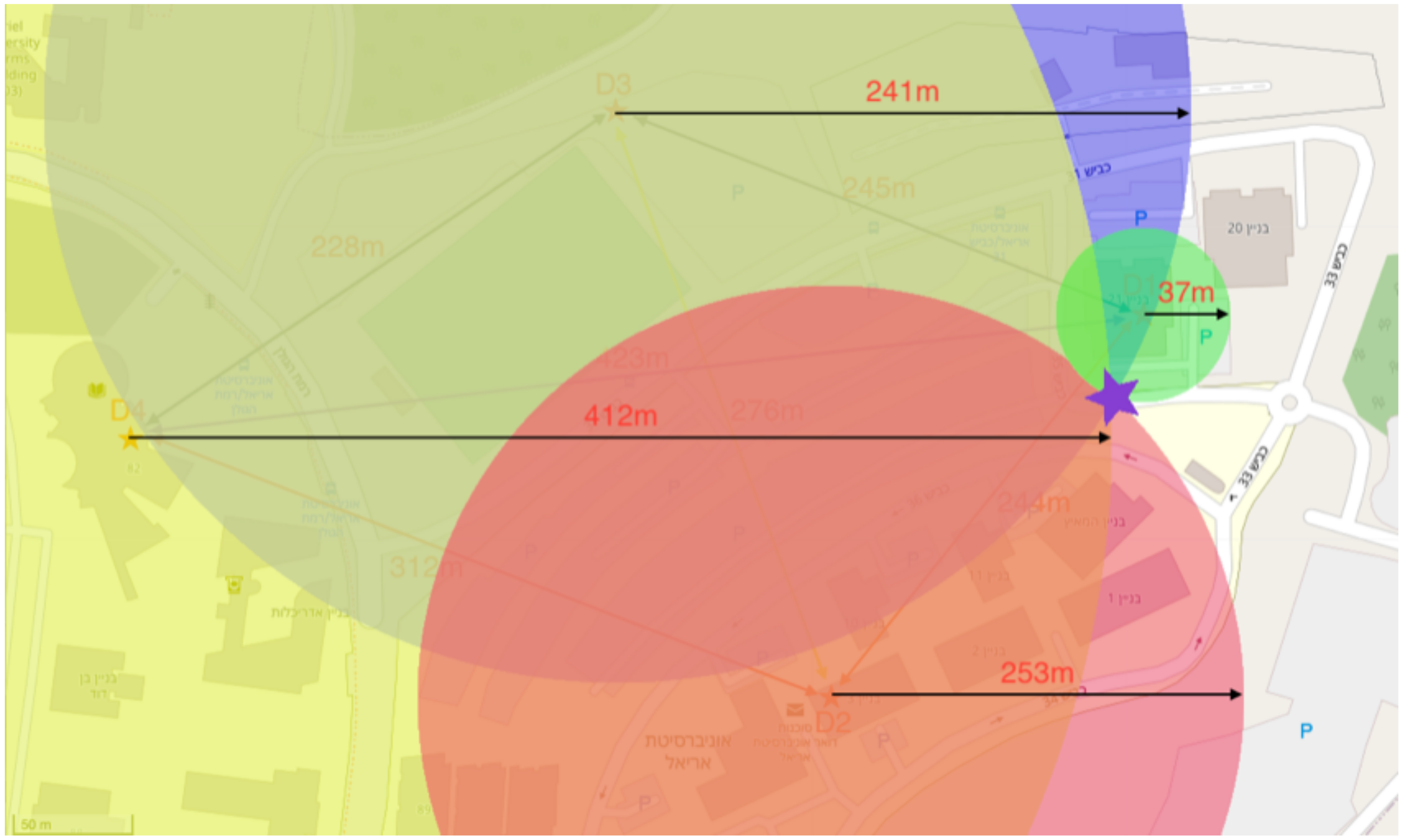
| Device | D1 | D2 | D3 | D4 |
|---|---|---|---|---|
| D1 | - | 250.2 | 252.8 | 416.2 |
| D2 | 248.4 | - | 230.2 | 344.8 |
| D3 | 242.9 | 242.9 | - | 219.2 |
| D4 | 431.8 | 288.7 | 312.0 | - |
| Device | D1 | D2 | D3 | D4 |
|---|---|---|---|---|
| D1 | - | 244.0 | 245.0 | 423.0 |
| D2 | 244.0 | - | 276.0 | 312.0 |
| D3 | 245.0 | 276.0 | - | 228.0 |
| D4 | 423.0 | 312.0 | 228.0 | - |
| GPS | LoRa SX1280 | Difference | Time Shift | Accuracy |
|---|---|---|---|---|
| (Meters) | (Meters) | (Meters) | (Seconds) | |
| 1780 | 1980 | 200 | 12 | 92.93% |
| 2130 | 2404.6 | 274.6 | 29 | 91.26% |
| 13,210 | 13,453.7 | 243.7 | 17 | 98.75% |
| 21,530 | 21,698.8 | 168.8 | 11 | 99.64% |
| 22,170 | 22,325.1 | 155.1 | 11 | 99.70% |
| Device | D1 | D2 | D3 | D4 |
|---|---|---|---|---|
| A1 | 36.7 | 253.1 | 241.3.0 | 412.0 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ronen, R.; Ben-Moshe, B. Cyberattack on Flight Safety: Detection and Mitigation Using LoRa. Sensors 2021, 21, 4610. https://doi.org/10.3390/s21134610
Ronen R, Ben-Moshe B. Cyberattack on Flight Safety: Detection and Mitigation Using LoRa. Sensors. 2021; 21(13):4610. https://doi.org/10.3390/s21134610
Chicago/Turabian StyleRonen, Rony, and Boaz Ben-Moshe. 2021. "Cyberattack on Flight Safety: Detection and Mitigation Using LoRa" Sensors 21, no. 13: 4610. https://doi.org/10.3390/s21134610
APA StyleRonen, R., & Ben-Moshe, B. (2021). Cyberattack on Flight Safety: Detection and Mitigation Using LoRa. Sensors, 21(13), 4610. https://doi.org/10.3390/s21134610






