Internet of Things for System Integrity: A Comprehensive Survey on Security, Attacks and Countermeasures for Industrial Applications
Abstract
1. Introduction
2. Related Surveys and Contribution
2.1. Surveys on System Integrity for IIoT
2.2. Surveys on IoT System Integrity
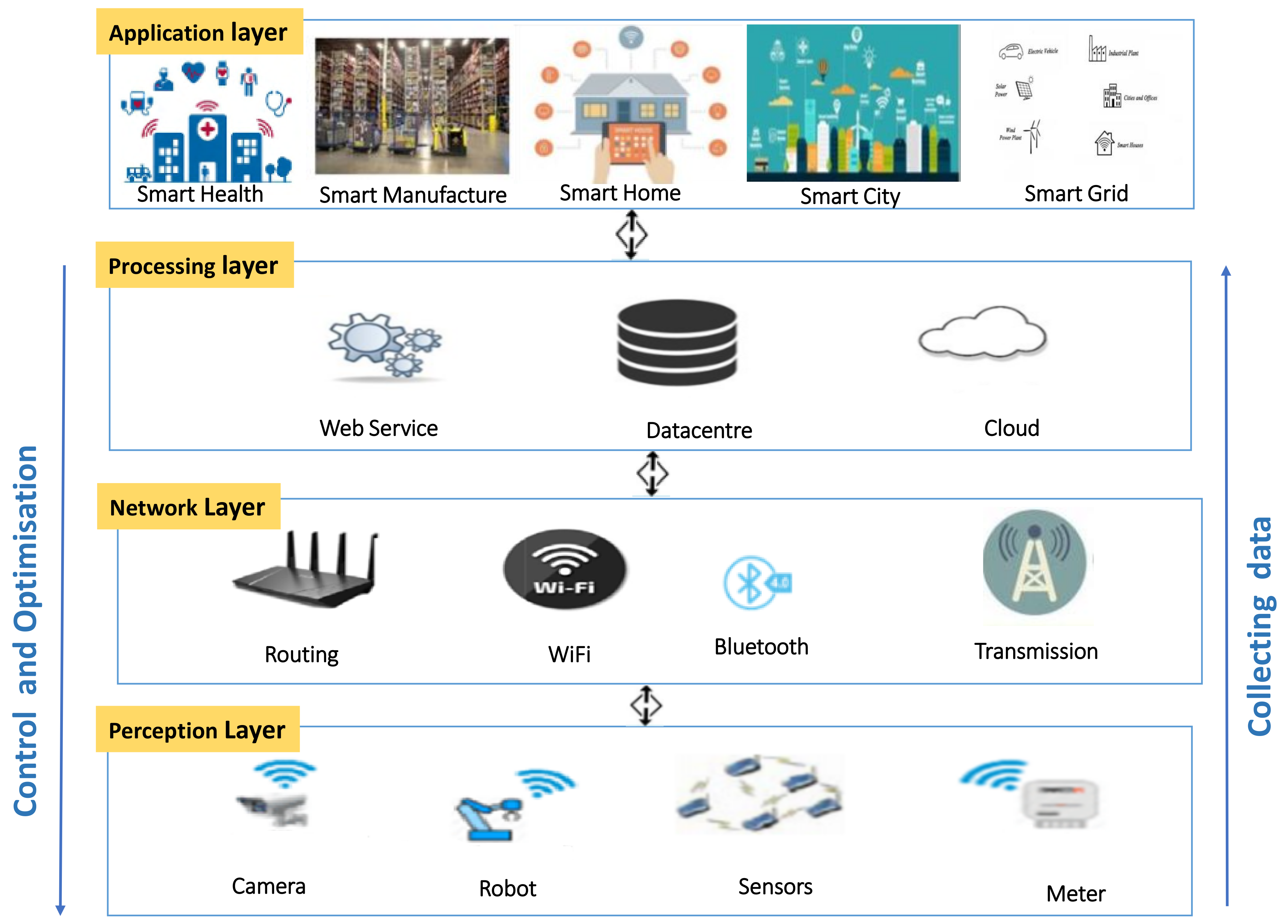
3. Industrial IoT System Integrity
Case Study on IIoT Application: Smart Grid
4. Classification of Security Attacks
4.1. Perception Layer with Security Attacks
4.2. Network Layer with Security Attacks
4.3. Application Layer with Security Attacks
5. Connectivity and System Integrity Approaches
5.1. Communication Security
5.2. Network Security
5.3. Application Security
6. Network Simulations and Operating Systems
6.1. Simulators
6.2. Operating Systems (OSs)
7. Security Solutions for IoT and Industrial Systems
7.1. Communication Layer Security Solutions
7.2. Network Routing Security Solutions
7.3. Transport and Application Layer Security Solutions
8. Open Research Challenges
- The IoT devices have a limited processing capability, memory and storage, which they need to operate at low power. Security methods that demand heavy encryption are not suitable for constrained devices due to the complexity of encryption and decryption operations for transmitting data quickly and securely. Thus, lightweight encryption algorithms are needed for constrained devices, including actuators and sensors. Communication between these devices must be protected and provide integrity and confidentiality using hash functions and the AES.
- The implementation of the IDS in IoT networks presents new challenges, as it generates a large number of false alerts. It is a challenge to provide real-time IoT-IDSs and extend the range of attacks detection and consider the impact of the IDS on IoT devices’ performance regarding overhead, energy consumption and accuracy.
- The new era of Industry 4.0 and industrial IoT requires designing a novel intrusion detection methodology to guarantee the protection of connected systems and provided services.
- Prevention mechanisms for specific attacks to the IIoT environment such as smart grid, transportation, smart industry etc., need further development.
- Developing a lightweight security scheme for the smart grid application based on less computation algorithm suitable for constrained devices.
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Girard, M. Standards for Cybersecure IoT Devices: A Way Forward. JSTOR 2020, 160, 1–13. [Google Scholar]
- Al-Rubaye, S.; Rodriguez, J.; Fragonara, L.Z.; Theron, P.; Tsourdos, A. Unleash Narrowband Technologies for Industrial Internet of Things Services. IEEE Netw. 2019, 33, 16–22. [Google Scholar] [CrossRef]
- Al-Rubaye, S.; Kadhum, E.; Ni, Q.; Anpalagan, A. Industrial Internet of Things Driven by SDN Platform for Smart Grid Resiliency. IEEE Internet Things J. 2019, 6, 267–277. [Google Scholar] [CrossRef]
- Wan, J.; Tang, S.; Shu, Z.; Li, D.; Wang, S.; Imran, M.; Vasilakos, A.V. Software-defined industrial internet of things in the context of industry 4.0. IEEE Sens. J. 2016, 16, 7373–7380. [Google Scholar] [CrossRef]
- Sengupta, J.; Ruj, S.; Bit, S.D. A comprehensive survey on attacks, security issues and blockchain solutions for IoT and IIoT. J. Netw. Comput. Appl. 2020, 149, 102481. [Google Scholar] [CrossRef]
- Lee, I.; Lee, K. The internet of things (iot): Applications, investments, and challenges for enterprises. Bus. Horizons 2015, 58, 431–440. [Google Scholar] [CrossRef]
- Hp News hp Study Reveals 70 Percent of Internet of Things Devices Vulnerable to Attack. Available online: https://www8.hp.com/us/en/hp-news/press-release.html?id=1744676 (accessed on 15 April 2020).
- Flashpoint—Mirai Botnet Linked to Dyn DNS DDoS Attacks. Available online: https://www.flashpoint-intel.com/blog/cybercrime/mirai-botnet-linked-dyn-dns-ddos-attacks/ (accessed on 20 October 2020).
- Agrawal, M.; Zhou, J.; Chang, D. A survey on lightweight authenticated encryption and challenges for securing industrial IoT. In Security and Privacy Trends in the Industrial Internet of Things; Springer: Cham, Switzerland, 2019; pp. 71–94. [Google Scholar]
- Zhang, Y.; Huang, X. Security and privacy techniques for the industrial Internet of Things. In Security and Privacy Trends in the Industrial Internet of Things; Springer: Cham, Switzerland, 2019; pp. 245–268. [Google Scholar]
- Sadeghi, A.-R.; Wachsmann, C.; Waidner, M. Security and privacy challenges in industrial internet of things. In Proceedings of the 52nd ACM/EDAC/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 8–12 June 2015; pp. 1–6. [Google Scholar]
- Li, J.-Q.; Yu, F.R.; Deng, G.; Luo, C.; Ming, Z.; Yan, Q. Industrial internet: A survey on the enabling technologies, applications, and challenges. IEEE Commun. Surv. Tutor. 2017, 19, 1504–1526. [Google Scholar] [CrossRef]
- Hoffman, F. Industrial internet of things vulnerabilities and threats: What stakeholders need to consider. Issues Inf. Syst. 2019, 20, 119–133. [Google Scholar]
- Yu, X.; Guo, H. A survey on IIoT security. In Proceedings of the 2019 IEEE VTS Asia Pacific Wireless Communications Symposium (APWCS), Singapore, 28–30 August 2019; pp. 1–5. [Google Scholar]
- Yadav, G.; Paul, K. Architecture and Security of SCADA Systems: A Review. Int. J. Crit. Infrastruct. Prot. 2021, 34, 100433. [Google Scholar] [CrossRef]
- Sicari, S.; Rizzardi, A.; Grieco, L.A.; CoenPorisini, A. Security, privacy and trust in internet of things: The road ahead. Comput. Netw. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Jing, Q.; Vasilakos, A.V.; Wan, J.; Lu, J.; Qiu, D. Security of the in-ternet of things: Perspectives and challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Frustaci, M.; Pace, P.; Aloi, G.; Fortino, G. Evaluating critical security issues of the iot world: Present and future challenges. IEEE Internet Things J. 2017, 5, 2483–2495. [Google Scholar] [CrossRef]
- Grammatikis, P.I.R.; Sarigiannidis, P.G.; Moscholios, I.D. Securing the internet of things: Challenges, threats and solutions. Internet Things 2019, 5, 41–70. [Google Scholar] [CrossRef]
- Granjal, J.; Monteiro, E.; Silva, J.S. Security for the internet of things: A survey of existing protocols and open research issues. IEEE Commun. Surv. Tutor. 2015, 17, 1294–1312. [Google Scholar] [CrossRef]
- Malina, L.; Hajny, J.; Fujdiak, R.; Hosek, J. On perspective of security and privacy-preserving solutions in the internet of things. Comput. Netw. 2016, 102, 83–95. [Google Scholar] [CrossRef]
- Maple, C. Security and privacy in the internet of things. J. Cyber Policy 2017, 2, 155–184. [Google Scholar] [CrossRef]
- Sadeeq, M.A.; Zeebaree, S.R.; Qashi, R.; Ahmed, S.H.; Jacksi, K. Internet of things security: A survey. In Proceedings of the 2018 International Conference on Advanced Science and Engineering (ICOASE), Duhok, Iraq, 9–11 October 2018; pp. 162–166. [Google Scholar]
- Shah, A.; Engineer, M. A survey of lightweight cryptographic algorithms for iot-based applications. In Smart Innovations in Communication and Computational Sciences; Springer: Singapore, 2019; pp. 283–293. [Google Scholar]
- Alaba, F.A.; Othman, M.; Hashem, I.A.T.; Alotaibi, F. Internet of things security: A survey. J. Netw. Comput. Appl. 2017, 88, 10–28. [Google Scholar] [CrossRef]
- Latif, S.; Zafar, N.A. A survey of security and privacy issues in iot for smart cities. In Proceedings of the 2017 Fifth International Conference on Aerospace Science & Engineering (ICASE), Islamabad, Pakistan, 14–16 November 2017; pp. 1–5. [Google Scholar]
- Sfar, A.R.; Natalizio, E.; Challal, Y.; Chtourou, Z. A roadmap for security challenges in the internet of things. Digit. Commun. Netw. 2018, 4, 118–137. [Google Scholar] [CrossRef]
- Hameed, S.; Khan, F.I.; Hameed, B. Understanding security requirements and challenges in internet of things (iot): A review. J. Comput. Netw. Commun. 2019, 2019, 9629381. [Google Scholar] [CrossRef]
- Arıs, A.; Oktug, S.F.; Voigt, T. Security of Internet of Things for a Reliable Internet of Services; Springer: Cham, Switzerland, 2018; pp. 337–370. [Google Scholar]
- Hassan, W.H. Current research on internet of things (iot) security: A survey. Comput. Netw. 2019, 148, 283–294. [Google Scholar]
- Stouffer, K.; Tang, C.; Zimmerman, T.; Powell, M.; McCarthy, J.; Ogunyale, T.; Acierto, L.; Danley, L. Protecting Information and System Integrity in Industrial Control Systems Environments: Cybersecurity for the Manufacturing Sector; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2020; p. 26. [Google Scholar]
- Stouffer, K.; Tang, C.; Zimmerman, T.; Powell, M.; McCarthy, J.; Ogunyale, T.; Acierto, L.; Danley, L. Detecting and Protecting against Data Integrity Attacks in Industrial Control Systems Environments: Cybersecurity for the Manufacturing Sector (Draft); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2019; p. 20. [Google Scholar]
- Elyoenai, E.; Daniel, R.; Jairo, O.; Victor, V.; Luis, T. Smart Grid Security. European Network and Information Security Agency (ENISA). June 2012, pp. 1–71. Available online: https://www.enisa.europa.eu/publications/ENISA-smart-grid-security-recommendations (accessed on 25 March 2021).
- Sarenche, R.; Salmasizadeh, M.; Ameri, M.H.; Aref, M.R. A secure and privacy-preserving protocol for holding double auctions in smart grid. Inf. Sci. 2021, 557, 108–129. [Google Scholar] [CrossRef]
- Khan, A.A.; Kumar, V.; Ahmad, M.; Rana, S. LAKAF: Lightweight authentication and key agreement framework for smart grid network. J. Syst. Archit. 2021, 116, 102053. [Google Scholar] [CrossRef]
- Abdallah, A.; Shen, X.S. A lightweight lattice-based homomorphic privacy-preserving data aggregation scheme for smart grid. IEEE Trans. Smart Grid 2016, 9, 396–405. [Google Scholar] [CrossRef]
- Abbasinezhad-Mood, D.; Nikooghadam, M. An anonymous ECC-based self-certified key distribution scheme for the smart grid. IEEE Trans. Ind. Electron. 2018, 65, 7996–8004. [Google Scholar] [CrossRef]
- Grover, H.S.; Kumar, D. Cryptanalysis and improvement of a three-factor user authentication scheme for smart grid environment. J. Reliab. Intell. Environ. 2020, 6, 249–260. [Google Scholar] [CrossRef]
- Deng, L.; Gao, R. Certificateless two-party authenticated key agreement scheme for smart grid. Inf. Sci. 2021, 543, 143–156. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Alhakami, H.; Baz, A.; Al-Turjman, F. Securing demand response management: A certificate-based access control in smart grid edge computing infrastructure. IEEE Access 2020, 8, 101235–101243. [Google Scholar] [CrossRef]
- Wang, Z.; Liu, Y.; Ma, Z.; Liu, X.; Ma, J. LiPSG: Lightweight Privacy-Preserving Q-Learning-Based Energy Management for the IoT-Enabled Smart Grid. IEEE Internet Things J. 2012, 7, 1437–1443. [Google Scholar] [CrossRef]
- Deogirikar, J.; Vidhate, A. Security attacks in IoT: A survey. In Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud)(I-SMAC), Palladam, India, 10–11 February 2017; pp. 32–37. [Google Scholar]
- Kumar, S.; Sahoo, S.; Mahapatra, A.; Swain, A.K.; Mahapatra, K.K. Security enhancements to system on chip devices for IoT perception layer. In Proceedings of the 2017 IEEE International Symposium on Nanoelectronic and Information Systems (iNIS), Bhopal, India, 18–20 December 2017; pp. 51–156. [Google Scholar]
- Mohite, S.; Kulkarni, G.; Sutar, R.; Mohite, S. RFID security issues. Int. J. Eng. Res. Technol. (IJERT) 2013, 2, 746–748. [Google Scholar]
- Wallgren, L.; Raza, S.; Voigt, T. Routing attacks and countermeasures in the RPL-based internet of things. Int. J. Distrib. Sens. Netw. 2013, 9, 794326. [Google Scholar] [CrossRef]
- Pongle, P.; Chavan, G. A survey: Attacks on RPL and 6LoWPAN in IoT. In Proceedings of the 2015 International Conference on Pervasive Computing (ICPC), Pune, India, 8–10 January 2015; pp. 1–6. [Google Scholar]
- Nawir, M.; Amir, A.; Yaakob, N.; Lynn, O.B. Internet of Things (IoT): Taxonomy of security attacks. In Proceedings of the 2016 3rd International Conference on Electronic Design (ICED), Phuket, Thailand, 11–12 August 2016; pp. 321–326. [Google Scholar]
- Abdul-Ghani, H.A.; Konstantas, D.; Mahyoub, M. A comprehensive IoT attacks survey based on a building-blocked reference model. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 355–373. [Google Scholar]
- Karlof, C.; Wagner, D. Secure routing in wireless sensor networks: Attacks and countermeasures. Ad Hoc Netw. 2003, 1, 293–315. [Google Scholar] [CrossRef]
- Gautam, S.; Malik, A.; Singh, N.; Kumar, S. Recent Advances and Countermeasures Against Various Attacks in IoT Environment. In Proceedings of the 2019 2nd International Conference on Signal Processing and Communication (ICSPC), Coimbatore, India, 29–30 March 2019; pp. 315–319. [Google Scholar]
- Rizvi, S.; Kurtz, A.; Pfeffer, J.; Rizvi, M. Securing the internet of things (iot): A security taxonomy for iot. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 163–168. [Google Scholar]
- Hari, P.B.; Singh, S.N. Security issues in wireless sensor networks: Current research and challenges. In Proceedings of the 2016 International Conference on Advances in Computing, Communication, & Automation (ICACCA)(Spring), Dehradun, India, 8–9 April 2016; pp. 1–6. [Google Scholar]
- Ali, W.; Dustgeer, G.; Awais, M.; Shah, M.A. Iot based smart home: Security challenges, security requirements and solutions. In Proceedings of the 2017 23rd International Conference on Automation and Computing (ICAC), Huddersfield, UK, 7–8 September 2017; pp. 1–6. [Google Scholar]
- Hossain, M.M.; Fotouhi, M.; Hasan, R. Towards an analysis of security issues, challenges, and open problems in the internet of things. In Proceedings of the 2015 IEEE World Congress on Services, New York, NY, USA, 27 June–2 July 2015; pp. 21–28. [Google Scholar]
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A survey on internet of things: Architecture, enabling technologies, security and privacy, and applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Vashi, S.; Ram, J.; Modi, J.; Verma, S.; Prakash, C. Internet of things (iot): A vision, architectural elements, and security issues. In Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud)(I-SMAC), Palladam, India, 10–11 February 2017; pp. 492–496. [Google Scholar]
- Liu, X.; Zhao, M.; Li, S.; Zhang, F.; Trappe, W. A security framework for the internet of things in the future internet architecture. Future Internet 2017, 9, 27. [Google Scholar] [CrossRef]
- Andrea, I.; Chrysostomou, C.; Hadjichristofi, G. Internet of things: Security vulnerabilities and challenges. In Proceedings of the 2015 IEEE Symposium on Computers and Communication (ISCC), Larnaca, Cyprus, 6–9 July 2015; pp. 180–187. [Google Scholar]
- Yousuf, T.; Mahmoud, R.; Aloul, F.; Zualkernan, I. Internet of things (iot) security: Current status, challenges and countermeasures. Int. J. Inf. Secur. Res. (IJISR) 2015, 5, 608–616. [Google Scholar] [CrossRef]
- Dragomir, D.; Gheorghe, L.; Costea, S.; Radovici, A. A survey on secure communication protocols for iot systems. In Proceedings of the 2016 International Workshop on Secure Internet of Things (SIoT), Heraklion, Greece, 26–30 September 2016; pp. 47–62. [Google Scholar]
- Naoui, S.; Elhdhili, M.E.; Saidane, L.A. Enhancing the security of the IoT LoraWAN architecture. In Proceedings of the 2016 International Conference on Performance Evaluation and Modeling in Wired and Wireless Networks (PEMWN), Paris, France, 22–25 November 2016; pp. 1–7. [Google Scholar]
- Aras, E.; Ramachandran, G.S.; Lawrence, P.; Hughes, D. Exploring the security vulnerabilities of LoRa. In Proceedings of the 2017 3rd IEEE International Conference on Cybernetics (CYBCONF), Exeter, UK, 21–23 June 2017; pp. 1–6. [Google Scholar]
- Keoh, S.L.; Kumar, S.S.; Tschofenig, H. Securing the internet of things: A standardization perspective. IEEE Internet Things J. 2014, 1, 265–275. [Google Scholar] [CrossRef]
- Raza, S.; Duquennoy, S.; Voigt, T.; Roedig, U. Demo abstract: Securing communication in 6lowpan with compressed ipsec. In Proceedings of the 2011 International Conference on Distributed Computing in Sensor Systems and Workshops (DCOSS), Barcelona, Spain, 27–29 June 2011; pp. 1–2. [Google Scholar]
- Arfaoui, A.; Kribeche, A.; Senouci, S.M.; Hamdi, M. Game-based adaptive remote access VPN for IoT: Application to e-Health. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–7. [Google Scholar]
- Khan, M.A.; Salah, K. Iot security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Assiri, B.; Almagwashi, H. Iot security and privacy issues. In Proceedings of the 2018 1st International Conference on Computer Applications Information Security (ICCAIS), Riyadh, Saudi Arabia, 4–6 April 2018; pp. 1–5. [Google Scholar]
- Bilal, M. A review of internet of things architecture, technologies and analysis smartphone-based attacks against 3d printers. arXiv 2017, arXiv:1708.04560. [Google Scholar]
- Airehrour, D.; Gutierrez, J.; Ray, S.K. Secure routing for internet of things: A survey. J. Netw. Comput. Appl. 2016, 66, 198–213. [Google Scholar] [CrossRef]
- Krishna, B.S.; Gnanasekaran, T. A systematic study of security issues in internet-of-things (iot). In Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud)(I-SMAC), Palladam, India, 10–11 February 2017; pp. 107–111. [Google Scholar]
- Singh, D.; Tripathi, G.; Jara, A. Secure layers based architecture for internet of things. In Proceedings of the 2015 IEEE 2nd World Forum on Internet of Things (WF-IoT), Milan, Italy, 14–16 December 2015; pp. 321–326. [Google Scholar]
- Benkhelifa, E.; Welsh, T.; Hamouda, W. A critical review of practices and challenges in intrusion detection systems for iot: Toward universal and resilient systems. IEEE Commun. Surv. Tutor. 2018, 20, 3496–3509. [Google Scholar] [CrossRef]
- Ammar, M.; Russello, G.; Crispo, B. Internet of things: A survey on the security of iot frameworks. J. Inf. Secur. Appl. 2018, 38, 8–27. [Google Scholar] [CrossRef]
- Chernyshev, M.; Baig, Z.; Bello, O.; Zeadally, S. Internet of things (iot): Research, simulators, and testbeds. IEEE Internet Things J. 2017, 5, 1637–1647. [Google Scholar] [CrossRef]
- Ani, U.D.; Watson, J.M.; Carr, M.; Cook, A.; Nurse, J.R.C. A review of the use and utility of industrial network-based open source simulators: Functionality, security, and policy viewpoints. J. Def. Model. Simul. 2020, 1–24. [Google Scholar] [CrossRef]
- Al-Kashoash, H. Congestion Control for 6LoWPAN Wireless Sensor Networks: Toward the Internet of Things; Springer: Berlin/Heidelberg, Germany, 2019. [Google Scholar]
- Varga, A.; Hornig, R. An overview of the omnet++ simulation environment. In Proceedings of the 1st International Conference on Simulation Tools and Techniques for Communications, Networks and Systems & Workshops, ICST (Institute for Computer Sciences, Social-Informatics), Marseille, France, 3–7 March 2008; p. 60. [Google Scholar]
- Choi, H.-Y.; Min, S.-G.; Han, Y.-H.; Park, J.; Kim, H. Implementation and evaluation of proxy mobile ipv6 in ns-3 network simulator. In Proceedings of the 2010 5th International Conference on Ubiquitous Information Technologies and Applications, Sanya, China, 16–18 December 2010; pp. 1–6. [Google Scholar]
- Siraj, S.; Gupta, A.; Badgujar, R. Network simulation tools survey. Int. J. Adv. Res. Comput. Commun. Eng. 2012, 1, 199–206. [Google Scholar]
- Queiroz, C.; Mahmood, A.; Tari, Z. SCADASim—A framework for building SCADA simulations. IEEE Trans. Smart Grid 2011, 2, 589–597. [Google Scholar] [CrossRef]
- Zikria, Y.B.; Kim, S.W.; Hahm, O.; Afzal, M.K.; Aalsalem, M.Y. Internet of things (iot) operating systems management: Opportunities, challenges, and solution. Sensors 2019, 19, 1793. [Google Scholar] [CrossRef] [PubMed]
- Kumar, G.S.; Paul, T. Safe contiki os: Type and memory safety for contiki os. In Proceedings of the International Conference on Advances in Recent Technologies in Communication and Computing, Kottayam, India, 27–28 October 2009. [Google Scholar]
- Saadallah, B.; Lahmadi, A.; Festor, O. Ccnx for Contiki: Implementation Details, Inria Nancy—Grand Est, LORIA—NSS: HAL-Inria; [Technical Report] RT-0432; INRIA: Rocquencourt, France, 2012; p. 52. Available online: https://hal.inria.fr/hal-00755482/document (accessed on 15 April 2020).
- Samal, N.; Dalai, P. A Performance survey of operating systems in iot environment. Int. J. Comput. Sci. Mob. Appl. 2018, 6, 1–6. [Google Scholar]
- Raspberry pi 4 Review: The New Gold Standard for Single-Board Computing-Tom’s hArdware Tom’s Hardware. USA. Available online: https://www.tomshardware.com/reviews/raspberry-pi-4-b,6193.html (accessed on 2 April 2021).
- Top 10 IoT Operating Systems For IoT Devices In 2021—Solace Infotech Pvt Ltd. USA. Available online: https://solaceinfotech.com/blog/top-10-iot-operating-systems-for-iot-devices-in-2021/ (accessed on 29 April 2021).
- Raza, S.; Duquennoy, S.; Höglund, J.; Roedig, U.; Voigt, T. Secure communication for the internet of things a comparison of link-layer security and ipsec for 6lowpan. Secur. Commun. Netw. 2014, 7, 2654–2668. [Google Scholar] [CrossRef]
- Ndibanje, B.; Lee, H.-J.; Lee, S.-G. Security analysis and improvements of authentication and access control in the internet of things. Sensors 2014, 14, 14786–14805. [Google Scholar] [CrossRef]
- Lee, T.H.; Wen, C.H.; Chang, L.-H.; Chiang, H.S.; Hsieh, M.C. A lightweight intrusion detection scheme based on energy consumption analysis in 6lowpan. In Advanced Technologies, Embedded and Multimedia for Human-Centric Computing; Springer: Dordrecht, The Netherlands, 2014; pp. 1205–1213. [Google Scholar]
- Oh, D.; Kim, D.; Ro, W. A malicious pattern detection engine for embedded security systems in the internet of things. Sensors 2014, 14, 24188–24211. [Google Scholar] [CrossRef]
- Cervantes, C.; Poplade, D.; Nogueira, M.; Santos, A. Detection of sinkhole attacks for supporting secure routing on 6lowpan for internet of things. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; pp. 606–611. [Google Scholar]
- Raza, S.; Wallgren, L.; Voigt, T. Svelte: Real-time intrusion detection in the internet of things. Ad Hoc Netw. 2013, 11, 2661–2674. [Google Scholar] [CrossRef]
- Deshmukh-Bhosale, S.; Sonavane, S.S. A real-time intrusion detection system for wormhole attack in the rpl based internet of things. Procedia Manuf. 2019, 32, 840–847. [Google Scholar] [CrossRef]
- Le, A.; Loo, J.; Luo, Y.; Lasebae, A. Specification-based ids for securing rpl from topology attacks. In Proceedings of the 2011 IFIP Wireless Days (WD), Niagara Falls, ON, Canada, 10–12 October 2011; pp. 1–3. [Google Scholar]
- Le, A.; Loo, J.; Chai, K.; Aiash, M. A specification-based ids for detecting attacks on rpl-based network topology. Information 2016, 7, 25. [Google Scholar] [CrossRef]
- Shin, D.; Sharma, V.; Kim, J.; Kwon, S.; You, I. Secure and efficient protocol for route optimization in pmipv6-based smart home iot networks. IEEE Access 2017, 5, 11100–11117. [Google Scholar] [CrossRef]
- Airehrour, D.; Gutierrez, J.A.; Ray, S.K. Sectrust-rpl: A secure trust-aware rpl routing protocol for internet of things. Future Gener. Comput. Syst. 2019, 93, 860–876. [Google Scholar] [CrossRef]
- Pongle, P.; Chavan, G. Real time intrusion and wormhole attack detection in internet of things. Int. J. Comput. Appl. 2015, 121, 1–9. [Google Scholar] [CrossRef]
- Mirshahjafari, S.M.H.; Ghahfarokhi, B.S. Sinkhole+ cloneid: A hybrid attack on rpl performance and detection method. Inf. Secur. J. Glob. Perspect. 2019, 28, 107–119. [Google Scholar] [CrossRef]
- Patel, H.B.; Jinwala, D.C. Blackhole detection in 6lowpan based internet of things: An anomaly based approach. In Proceedings of the TENCON 2019-2019 IEEE Region 10 Conference (TENCON), Kochi, India, 17–20 October 2019; pp. 947–954. [Google Scholar]
- Aydogan, E.; Yilmaz, S.; Sen, S.; Butun, I.; Forsström, S.; Gidlund, M. A central intrusion detection system for rpl-based industrial internet of things. In Proceedings of the 2019 15th IEEE International Workshop on Factory Communication Systems (WFCS), Sundsvall, Sweden, 27–29 May 2019; pp. 1–5. [Google Scholar]
- Ghaeini, H.R.; Tippenhauer, N.O. Hamids: Hierarchical monitoring intrusion detection system for industrial control systems. In Proceedings of the 2nd ACM Workshop on Cyber-Physical Systems Security and Privacy, Vienna, Austria, 28 October 2016; pp. 103–111. [Google Scholar]
- Faisal, M.A.; Cardenas, A.A.; Wool, A. Profiling communications in industrial ip networks: Model complexity and anomaly detection. In Security and Privacy Trends in the Industrial Internet of Things; Springer: Cham, Switzerland, 2019; pp. 139–160. [Google Scholar]
- Zamfir, S.; Balan, T.; Iliescu, I.; Sandu, F. A Security Analysis on Standard IoT Protocols. In Proceedings of the 2016 International Conference on Applied and Theoretical Electricity (ICATE), Craiova, Romania, 6–8 October 2016; pp. 1–6. [Google Scholar]
- Anthraper, J.J.; Kotak, J. Security, Privacy and Forensic Concern of MQTT Protocol. SSRN Electron. J. 2019, 876–883. [Google Scholar] [CrossRef]
- Kothmayr, T.; Schmitt, C.; Hu, W.; Brunig, M.; Carle, G. A dtls based end-to-end security architecture for the internet of things with two-way authentication. In Proceedings of the 37th Annual IEEE Conference on Local Computer Networks-Workshops, Clearwater, FL, USA, 22–25 October 2012; pp. 956–963. [Google Scholar]
- Kothmayr, T.; Schmitt, C.; Hu, W.; Brunig, M.; Carle, G. Dtls based security and two-way authentication for the internet of things. Ad Hoc Netw. 2013, 11, 2710–2723. [Google Scholar] [CrossRef]
- Granjal, J.; Monteiro, E.; Silva, J.S. End-to-end transport-layer security for internet-integrated sensing applications with mutual and delegated ecc public-key authentication. In Proceedings of the 2013 IFIP Networking Conference, Brooklyn, NY, USA, 22–24 May 2013; pp. 1–9. [Google Scholar]
- Raza, S.; Shafagh, H.; Hewage, K.; Hummen, R.; Voigt, T. Lithe: Lightweight secure coap for the internet of things. IEEE Sens. J. 2013, 13, 3711–3720. [Google Scholar] [CrossRef]
- Haroon, A.; Akram, S.; Shah, M.A.; Wahid, A. E-lithe: A lightweight secure DTLS for IoT. In Proceedings of the IEEE Vehicular Technology Conference, Toronto, ON, Canada, 24–27 September 2017; pp. 1–5. [Google Scholar]
- Salami, S.A.; Baek, J.; Salah, K.; Damiani, E.; Motivation, A. Lightweight Encryption for Smart Home. In Proceedings of the 2016 11th International Conference on Availability, Reliability and Security (ARES), Salzburg, Austria, 31 August–2 September 2016; pp. 382–388. [Google Scholar]
- Halabi, D.; Hamdan, S.; Almajali, S. Enhance the security in smart home applications based on IOT-CoAP protocol. In Proceedings of the 6th International Conference on Digital Information, Networking, and Wireless Communications, DINWC, Beirut, Lebanon, 25–27 April 2018; pp. 81–85. [Google Scholar]
- Abosata, N.R.A.; Kemp, A.H.; Razavi, M. Secure smart-home application based on iotcoap protocol. In Proceedings of the 2019 Sixth International Conference on Internet of Things: Systems, Management and Security (IOTSMS), Granada, Spain, 22–25 October 2019; pp. 13–17. [Google Scholar]
- Granjal, J.; Monteiro, E. End-to-end transparent transport-layer security for internet-integrated mobile sensing devices. In Proceedings of the 2016 IFIP Networking Conference (IFIP Networking) and Workshops, Vienna, Austria, 17–19 May 2016; pp. 306–314. [Google Scholar]

| Ref | Year | Objective | Comparison with Our Survey |
|---|---|---|---|
| [16] | 2019 | Highlights the relevant security solutions regarding the middle layer and mobile device | This survey highlights classifications of security attacks and countermeasures in respect to each layer of IoT/IIoT layers |
| [17] | 2015 | Analyses and discusses the security issues of the IoT layers | This survey provides a critical evaluation of the existing security issues and countermeasures regarding IoT/IIoT layers |
| [18] | 2018 | Highlights the security and issues of the IoT layers | This survey presents a comprehensive evaluation of the security issues, attacks and solutions with respect to the IoT/IIoT layers |
| [19] | 2019 | Analyses the possible threats to the communication protocols on each layer | This study highlights the IIoT system integrity along with a case study discussing the existing security solutions for the important industrial IoT application of smart grids |
| [20] | 2015 | Investigates the security and issues related to the MAC layer and physical layer, IEEE802.15.4 | This survey highlights classifications of security attacks and countermeasures with respect to each IoT/IIoT layer |
| [21] | 2018 | Reviews the most used cryptography algorithms on the IoT constrained deceives | This survey overviews various security solutions approaches mapped to each IoT/IIoT layer |
| [22] | 2017 | Details the various types of IoT application and discuss security and privacy in the IoT | This survey highlights classifications of security attacks and countermeasures mapped to each IoT/IIoT layer |
| [23] | 2018 | Highlights an appropriate cryptography algorithm covering the aspects of energy consumption and execution time | This survey reviews various security solutions approaches mapped to each layer of IoT/IIoT layer with their corresponding countermeasure proposed in the literature |
| [24] | 2019 | Examine and compare several lightweight algorithms that implemented on different tools and software | This work presents lightweight and non-lightweight algorithms and their possible solutions proposed in the literature. |
| [25] | 2017 | Compare possible attacks on IoT in the aspects of communication and application architecture | This survey highlights a comprehensive evaluation of the security issues, attacks and solutions with respect to each IoT/IIoT layer |
| [26] | 2017 | Analyse the security issues in IoT application based on smart cities | This survey reviews various security solutions approaches mapped to each layer of IoT layers with their corresponding countermeasure proposed in the literature |
| [27] | 2018 | Discuss the security and issues related to data privacy, trust and identification and authentication: uses smart manufacturing as case study | This study highlights system integrity of each layer of IoT/IIoT along with a case study discussing the existing security solutions for the most important industrial IoT application, the smart grid |
| [28] | 2019 | Highlights the vulnerabilities and solutions related to the privacy and routing attacks, mainly DoS | This survey highlight classifications of security attacks and countermeasures mapped to each layer of IoT/IIoT layers |
| [29] | 2018 | Highlights the characteristic of IoT and discuss the D/DoS attacks targeting the network and MAC layer | This survey highlights a comprehensive evaluation of the security issues, attacks and solutions with respect to IoT/IIoT layers |
| [30] | 2019 | Highlights and discusses the recent studies in the IoT security and issues from 2016 to 2018 | This survey highlights a comprehensive evaluation of the security issues, attacks and solutions with respect to IoT/IIoT layers |
| Our Contribution | - | - | IIoT system integrity has been highlighted along with a case study discussing the existing security solutions for for an important IoT application, the smart grid; the taxonomy of IoT layers, attacks, and security countermeasures have been presented; provides a critical analysis of the practical implementation regarding IoT/IIoT; highlights several simulation tools and operating systems (OS) used to investigate security solutions; discusses potential future research directions |
| IoT Layers | Protocols | Security Solution |
|---|---|---|
| Application layer | CoAP, MQTT | CoAPs, MQTTs |
| Transport layer | UDP, TCP | DTLS, TLS |
| Network layer | IPv6, RPL | IDS, Secure RPL, IPsec |
| Perception layer | IEEE 802.14.5 | IEEE 802.24.5 security |
| Ref | Detection Technique | Security Threats | Validation | Advantages | Disadvantages |
|---|---|---|---|---|---|
| [89] | Lightweight IDS | DoS attack | Simulation (Qualnet) | Evaluates the energy consumption. | Does not evaluate the accuracy.Use only one metric and one attack. |
| [90] | Centralised | Malicious attacks | RaspberryPi | High accuracy rate. Much faster than Wu-Manber. | High overhead. |
| [91] | Distributed | Snikhole attack | - | High accuracy rate. | High false-positive.Does not address the impact of their IDS on energy consumption. |
| [92] | Hybrid | Snikhole and Selective forwarding attacks | Cooja-ContikiOS | High accuracy rate and Low overhead. | High false alarm rate 38% |
| [93] | Centralised | Wormhole attack | Cooja-ContikiOS | High true-positive when the network size small. | the true-positive significantly decreases by the increase of network size.Evaluates only one metric and one attack. |
| [94] | Distributed | Repair and rank attack | Not available | Effectively detects rank and repair attacks. | Does not validate their approach on a simulation. |
| [95] | Centralised | Rank local repair, and sinkhole attacks | Cooja-ContikiOS | High detection accuracy Low false-positive. | Slight overhead. |
| [96] | - | Authentication key exchange and privacy | AVISSPA | Reduces latency and packet delay. | - |
| [97] | Distributed | Sybil and rank attack | Cooja-ContikiOS | Capable of detecting sybil and rank attacks. | Does not evaluate the impact of their approach in terms of performance. |
| [98] | Hybrid | Wormhole attack | Cooja-ContikiOS | High detection rate sufficient for constrained resources. | Detects only one attack. |
| [99] | Hybrid | Sinkhole-CloneID attacks | Cooja-ContikiOS | High detection rate. | High energy and power consumption. |
| [100] | Anomaly | Blackhole attack | Cooja-ContikiOS | Improves detection rate. | Packet delivery ratio decreases when the network size increases. |
| [101] | centralised | Version number and hello flood attacks | Cooja-ContikiOS | High accuracy detection.Low false-positive alarms | Evaluates only one metric which detection accuracy.Does not evaluate the impact of the IDs on performance. |
| [102] | Network behaviour anomaly | Outsider attacks ARP posing and MITM attacks | NS3 and Python script | Detects outsider attacks with zero false-positive. | Not able to detect insider attacks. |
| [103] | Anomaly | Malicious traffic | Discrete Markov Chain models (DTMC) | Evaluates the DTMC on different industrial datasets. | High number of unknown transactions and states. |
| Ref | Security Objective | Proposed Solution | Simulation/Testbed | Advantages | Disadvantages |
|---|---|---|---|---|---|
| [104,105] | Security analysis for MQTT-TLS and CoAP with DTLS | Authentication key exchange and security privacy | - | Compares the security mechanisms for MQTT and CoAP protocols. | |
| [106] | Provides message integrity and confidentiality with low overhead and latency | DTLS based on x.509 certificate containing RSA keys | TinyOS | Provides message integrity and confidentiality with energy efficiency | - |
| [107] | Provides data confidentiality, integrity with low overhead and high interoperability | integrated DTLS handshake and RSA key, and DTLS with ECC | Real IoT system | - | - |
| [108] | Provides authentication security and secure communication | DTLS with ECC public key authentication | TinyOS | Consumes higher energy due to the complexity computation of ECC algorithm | |
| [109] | Reduces the energy consumption for the integration of CoAP with DTLS | Using tinyOS DTLS based on pre-shared keys | Cooja-ContikiOS | significantly reduces the overhead | Does not compromise end-to-end security |
| [110] | Lightweight security against DoS attack | Uses Trusted Third Party between the constrained node and CoAP server | Cooja-ContikOS | Reduce the energy and respond time | - |
| [111] | Lightweight encryption for smart-home based on public key | Cryptography solution based on stateful Diffie Hellman key and identity-based encryption scheme | - | Reduce the computational cost of encryption implementation | - |
| [112] | Message integrity security for smart-home application | integrated hash functions with CoAP protocol | Cooja-ContikiOS | Provides integrity protection | Does not provide data confidentiality. In the terminology of smart-home system, the data transactions being leaked |
| [113] | Data confidentiality, integrity, and authentication for smart-home application | Cryptography solution based on integrated CoAP-AES and CoAP-ShA2 | Cooja-ContikiOS | Provides data confidentiality, integrity, and authentication protection | Does not evaluate their solution performance with DTLS |
| [114] | end-to-end security for mobile devices | Integrated DTLS with ECC authentication | TniyOS | - | - |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abosata, N.; Al-Rubaye, S.; Inalhan, G.; Emmanouilidis, C. Internet of Things for System Integrity: A Comprehensive Survey on Security, Attacks and Countermeasures for Industrial Applications. Sensors 2021, 21, 3654. https://doi.org/10.3390/s21113654
Abosata N, Al-Rubaye S, Inalhan G, Emmanouilidis C. Internet of Things for System Integrity: A Comprehensive Survey on Security, Attacks and Countermeasures for Industrial Applications. Sensors. 2021; 21(11):3654. https://doi.org/10.3390/s21113654
Chicago/Turabian StyleAbosata, Nasr, Saba Al-Rubaye, Gokhan Inalhan, and Christos Emmanouilidis. 2021. "Internet of Things for System Integrity: A Comprehensive Survey on Security, Attacks and Countermeasures for Industrial Applications" Sensors 21, no. 11: 3654. https://doi.org/10.3390/s21113654
APA StyleAbosata, N., Al-Rubaye, S., Inalhan, G., & Emmanouilidis, C. (2021). Internet of Things for System Integrity: A Comprehensive Survey on Security, Attacks and Countermeasures for Industrial Applications. Sensors, 21(11), 3654. https://doi.org/10.3390/s21113654









