A Survey of Context-Aware Access Control Mechanisms for Cloud and Fog Networks: Taxonomy and Open Research Issues
Abstract
1. Introduction
1.1. The Background
1.2. The Contributions
- We discuss the research challenges with a literature review whose main purpose is to identify the relevant contextual conditions for context-sensitive access to data resources in the cloud and fog networks.
- These dynamically changing conditions are further analyzed to propose a new generation of Fog-Based Context-Aware Access Control (FB-CAAC) model, combining the benefits of the cloud, IoT and context-aware computing along with traditional data integration solutions. Towards this end, we demonstrate different taxonomies and an empirical analysis of existing context-aware access control mechanisms.
- We highlight possible directions for future work that have not been well covered in current state-of-the-art context-aware access control research.
1.3. The Motivation and Scope of the Survey
1.4. The Outline
2. The Traditional Access Control
2.1. Discretionary Access Control
- Access Control List: An access control list contains entries for the subjects, which describe the operations that the subjects can execute on the given objects. For example, a file has an access control list that contains (Mary, read), which gives Mary permission to read the file.
- DAC Policy: In the DAC-based policy, the object owners specify who can access what objects through access control policies.
2.2. Mandatory Access Control
- Security Label: The security label can be seen as an access control mechanism that usually controls access to the objects and the users cannot alter the access permissions.
- MAC Policy: The MAC policy is the type of non-discretionary or mandatory security policy, where the individual owners do not have any choice to specify who can access what objects through access control policies.
2.3. Role-Based Access Control
- User: In the RBAC model, subjects are typically represented by users, who are the human beings.
- Role: Users are assigned to roles based on their credentials or job functions in the organizations along with different sessions.
- Permission: Permissions (i.e., resource access permissions) are assigned to roles based on the authorities and responsibilities conferred on the users assigned to these roles.
- User-Role Assignment Policy: The user and role-specific attributes are used to specify user-role assignment policies. Users can create active sessions to activate roles and users’ assignment in roles can be revoked after the associated sessions.
- Role-Permission Assignment Policy: The role and permission-specific attributes are used to specify role-permission assignment policies. Users acquire resource access permissions by being members of roles.
2.4. Attribute-Based Access Control
- Subject-Specific Attribute: Subject-specific attributes describe the users who attempt to access, such as the age, role, and job title.
- Object-Specific Attribute: Object-specific attributes describe the data or resources being access by the users, such as the granularity or type (the daily medical records, the medical history), the sensitivity (the critical or emergency medical record, the private medical records), the location.
- Action: Action-specific attributes describe the action (on resources) being attempted, such as read, write, update, delete.
- Attribute-Based Policy: In ABAC, the access control policies are used to limiting access to certain resources, based on the attributes, e.g., “user.age = 30”.
2.5. Discussion
3. The Context-Aware Access Control
3.1. Context Information in Pervasive Computing Domain
3.2. Context Information in Access Control Domain
3.3. Context-Aware Access Control
- User-Centric Context: User-centric contexts are the information about representing users. A user can be the resource requester, the resource owner or any other environmental person.
- Resource-Centric Contex: Resource-centric contexts are the information about representing data or information resources.
- Environment-Centric Context: Environment-centric contexts are the information about representing the surrounding environment between user and resource, such as the location from where the access request has been originated.
- User: Users are human-beings interacting with a computing system, whose access requests are being controlled.
- Role: Roles reflect users’ job functions within the organizations (e.g., in the healthcare domain).
- Permission: Permissions are the approvals to perform certain operations on resources, by the users who initiate access requests. The resources are the objects protected by access control that represent the data/information container (e.g., the patients’ medical records). The operations are the actions that can be executed on the resources, for instance, read operation of the patients’ medical records.
- Context: Contexts characterize the situation of entities, such as the users, resources or their environments, e.g., the physical location and the interpersonal relationship between user and resource owner. The expressions are used to express the dynamic contextual conditions (using relevant context and situation information) in order to specify the user-role and role-permission assignment policies.
- Context-aware user-role assignment policy: Context-aware user-role assignment policies are the many-to-many mapping between a set of users and roles, when a set of dynamic contextual conditions are satisfied.
- Context-aware role-permission assignment policy: Context-aware role-permission assignment policies are the many-to-many mapping between a set of roles and permissions when a set of dynamic contextual conditions are sanitised.
3.4. Discussion
4. The Context-Aware Access Control Approaches and Frameworks for Centralized Networks
4.1. The RBAC Approaches with Spatial and Temporal Contexts
4.2. The RBAC Approaches with User, Resource, and Environment-Centric Contexts
4.3. The RBAC Approaches with Relationship Contexts
4.4. The RBAC Approaches with Situational Contexts
4.5. The RBAC Approaches with Fuzzy Contexts
4.6. Discussion on Access Control Mechanisms for Centralized Networks
- John, who is a paramedic, can provide emergency treatments to save a patient’s life from a critical accident situation, by accessing the patient’s medical records, previous historical data and private health records. However, he needs to satisfy the associated contextual conditions (e.g., ‘co-located’ with the patient at the scene of an accident when the patient’s health situation is ‘critical’).
- A patient’s current health condition is derived as “98% critical”, i.e., criticality level is “very high”, from the low-level contextual facts such as heartbeat and body temperature. Due to the dynamic nature of computing technologies, there is still a growing need to exploit further contextual conditions derived from information provided through IoTs and relevant environments, in order to control context-sensitive access to data and information resources at different granularity levels.
- A hospital doctor is allowed to activate an “emergency doctor” role at the emergency department of the hospital when the patient’s health condition is “highly critical”.
5. The Access Control Approaches and Frameworks for Decentralized Cloud and Fog Networks
5.1. The CAAC Approaches for Accessing Data from Edge, IoT and Cloud Networks
5.2. The Privacy-Preserving Protocols and Mechanisms for Distributed Cloud Databases
5.3. The Privacy-Preserving Mechanisms for Cloud Service Providers
5.4. The Policy-Aware Deployment and Management of Cloud Applications
5.5. Discussion on Access Control Mechanisms for Decentralized Networks
6. Towards a New Generation of CAAC Framework: Gains and Open Issues
6.1. Future Research Directions and Real-World Case Studies
- Access management against identity thefts.
- Safeguarding health records against data breaches.
- Protecting banking customers against data breaches.
- Security and privacy of the internet of things.
6.1.1. Access Management against Identity Theft
- Users who did not understand the consequences of such risks.
- Users who knew exactly as well as the consequences.
6.1.2. Safeguarding Health Records against Data Breaches
6.1.3. Protecting Banking Customers against Data Breaches
- Attack attribution.
- Attack forensics.
- Banking malware and fraud detection.
- False positive reduction for incident response.
- Threat intelligence and credential recovery in the dark web.
- Insider threat detection and behavioural analysis.
6.1.4. Security and Privacy of the Internet of Things
- Deducing the daily living activities of elderly people.
- Health data access from IoTs and treatment progress monitoring.
6.2. An Emerging CAAC Mechanism
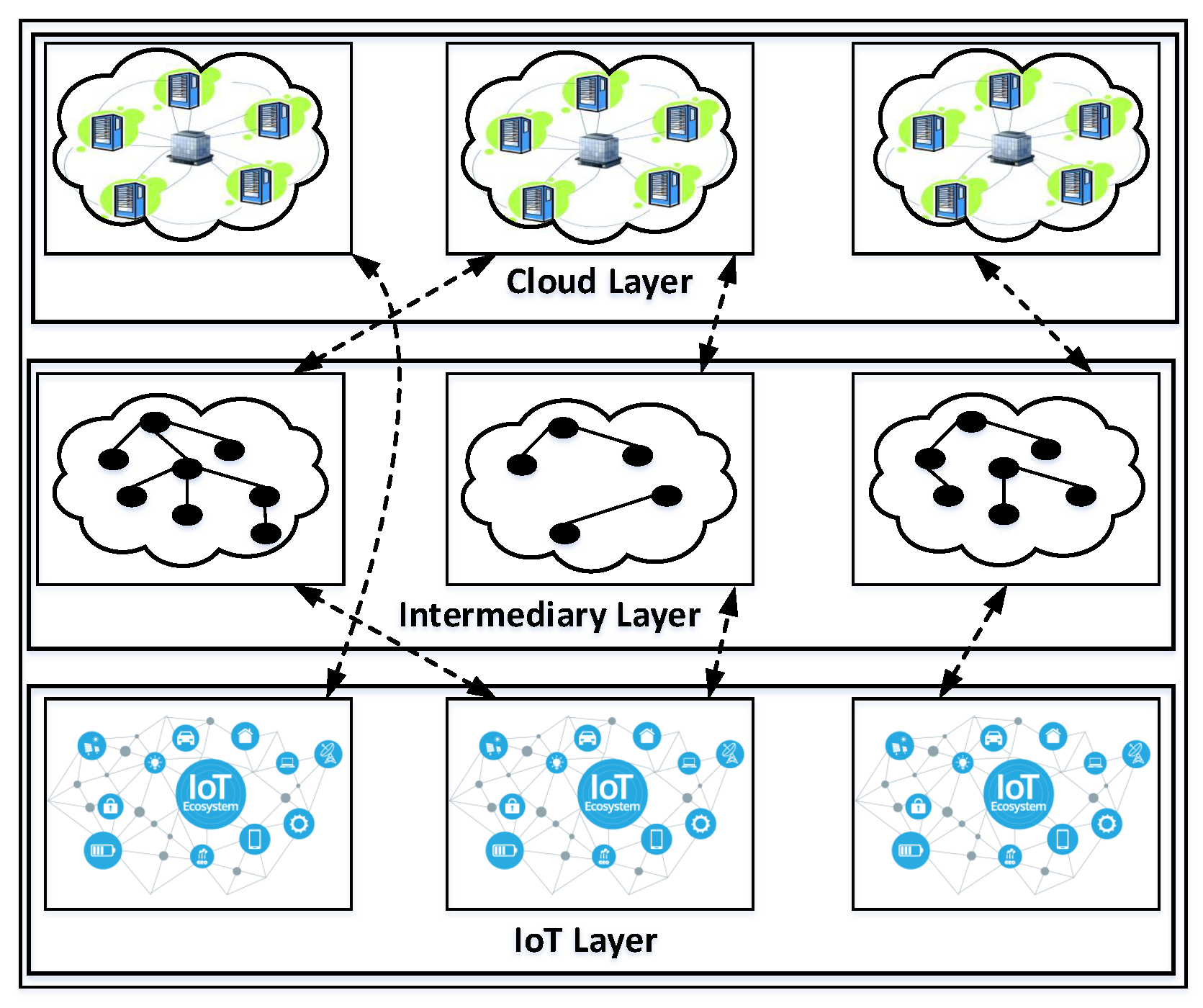
6.2.1. IoT Device Layer
6.2.2. Fog Layer
6.2.3. Cloud Layer
6.2.4. Cloud-Fog Interplay
6.2.5. An Access Request Using FB-CAAC in the IoT Scenario
6.2.6. Discussion and General Requirements
7. Conclusions
- Different taxonomies of contextual conditions and authorization models.
- An empirical analysis of the existing access control mechanisms.
- Opportunities, challenges and new directions of future research for cloud and fog networks.
- A future trend of emerging fog-based context-aware access control model.
Funding
Conflicts of Interest
References
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Sandhu, R.S.; Samarati, P. Access control: Principle and practice. Commun. Mag. IEEE 1994, 32, 40–48. [Google Scholar] [CrossRef]
- Posthumus, S.; Von Solms, R. A framework for the governance of information security. Comput. Secur. 2004, 23, 638–646. [Google Scholar] [CrossRef]
- Dillon, T.S.; Zhuge, H.; Wu, C.; Singh, J.; Chang, E. Web-of-things framework for cyber–physical systems. Concurr. Comput. Pract. Exp. 2011, 23, 905–923. [Google Scholar] [CrossRef]
- Dillon, T.S.; Talevski, A.; Potdar, V.; Chang, E. Web of things as a framework for ubiquitous intelligence and computing. In Proceedings of the International Conference on Ubiquitous Intelligence and Computing, Brisbane, Australia, 7–9 July 2009; Springer: Cham, Switzerland, 2009; pp. 2–13. [Google Scholar]
- Kayes, A.S.M.; Han, J.; Colman, A. OntCAAC: An Ontology-Based Approach to Context-Aware Access Control for Software Services. Comput. J. 2015, 58, 3000–3034. [Google Scholar] [CrossRef]
- Kayes, A.S.M.; Rahayu, W.; Dillon, T.; Chang, E.; Han, J. Context-Aware Access Control with Imprecise Context Characterization Through a Combined Fuzzy Logic and Ontology-Based Approach; Springer: Cham, Switzerland, 2017; pp. 132–153. [Google Scholar]
- Kayes, A.S.M.; Rahayu, W.; Dillon, T. An Ontology-Based Approach to Dynamic Contextual Role for Pervasive Access Control. In Proceedings of the 2018 IEEE 32nd International Conference on Advanced Information Networking and Applications (AINA), Krakow, Poland, 16–18 May 2018. [Google Scholar]
- Weiser, M. Some computer science issues in ubiquitous computing. Commun. ACM 1993, 36, 75–84. [Google Scholar] [CrossRef]
- Kayes, A.S.M.; Han, J.; Colman, A.W. An ontological framework for situation-aware access control of software services. Inf. Syst. 2015, 53, 253–277. [Google Scholar] [CrossRef]
- Corradi, A.; Montanari, R.; Tibaldi, D. Context-Based Access Control for Ubiquitous Service Provisioning. In Proceedings of the COMPSAC, Hong Kong, China, 28–30 September 2004; pp. 444–451. [Google Scholar]
- Schefer-Wenzl, S.; Strembeck, M. Modelling context-aware RBAC models for mobile business processes. IJWMC 2013, 6, 448–462. [Google Scholar] [CrossRef]
- Trnka, M.; Cerný, T. On security level usage in context-aware role-based access control. In Proceedings of the SAC, Symposium on Applied Computing, Pisa, Italy, 4–8 April 2016; pp. 1192–1195. [Google Scholar]
- Hosseinzadeh, S.; Virtanen, S.; Rodríguez, N.D.; Lilius, J. A semantic security framework and context-aware role-based access control ontology for smart spaces. In Proceedings of the International Conference on Management of Data, San Francisco, CA, USA, 26 June–1 July 2016; pp. 1–6. [Google Scholar]
- Bertino, E.; Bonatti, P.A.; Ferrari, E. TRBAC: A temporal role-based access control model. TISSEC 2001, 4, 191–233. [Google Scholar] [CrossRef]
- Zhang, H.; He, Y.; Shi, Z. Spatial Context in Role-Based Access Control. In Proceedings of the ICISC, Busan, Korea, 30 November–1 December 2006; pp. 166–178. [Google Scholar]
- Joshi, J.B.; Bertino, E.; Latif, U.; Ghafoor, A. A generalized temporal role-based access control model. IEEE Trans. Knowl. Data Eng. 2005, 17, 4–23. [Google Scholar] [CrossRef]
- Damiani, M.L.; Bertino, E.; Catania, B.; Perlasca, P. GEO-RBAC: A spatially aware RBAC. TISSEC 2007, 10, 2. [Google Scholar] [CrossRef]
- Kayes, A.S.M.; Han, J.; Colman, A. An Ontology-Based Approach to Context-Aware Access Control for Software Services. In Proceedings of the International Conference on Web Information Systems Engineering, Nanjing, China, 13–15 October 2013; pp. 410–420. [Google Scholar]
- Kayes, A.S.M.; Han, J.; Colman, A.; Islam, M.S. RelBOSS: A Relationship-Aware Access Control Framework for Software Services. In Proceedings of the OTM Confederated International Conferences “On the Move to Meaningful Internet Systems”, Amantea, Italy, 27–31 October 2014; pp. 258–276. [Google Scholar]
- Kayes, A.S.M.; Han, J.; Colman, A. PO-SAAC: A Purpose-Oriented Situation-Aware Access Control Framework for Software Services. In Proceedings of the CAiSE, Thessaloniki, Greece, 16–20 June 2014; pp. 58–74. [Google Scholar]
- Kayes, A.; Rahayu, W.; Dillon, T.; Chang, E. Accessing Data from Multiple Sources Through Context-Aware Access Control. In Proceedings of the 2018 17th IEEE International Conference On Trust, Security And Privacy In Computing And Communications/12th IEEE International Conference On Big Data Science And Engineering, New York, NY, USA, 1–3 August 2018. [Google Scholar]
- Kayes, A.; Rahayu, W.; Watters, P.; Alazab, M.; Dillon, T.; Chang, E. Achieving security scalability and flexibility using Fog-Based Context-Aware Access Control. Future Gener. Comput. Syst. 2020, 107, 307–323. [Google Scholar] [CrossRef]
- Kayes, A.S.M.; Han, J.; Colman, A. A semantic policy framework for context-aware access control applications. In Proceedings of the International Conference on Trust, Security and Privacy in Computing and Communications, Melbourne, Australia, 16–18 July 2013; pp. 753–762. [Google Scholar]
- Kayes, A.; Han, J.; Rahayu, W.; Dillon, T.; Islam, M.S.; Colman, A. A policy model and framework for context-aware access control to information resources. Comput. J. 2018, 62, 670–705. [Google Scholar] [CrossRef]
- Feng, L.; Dillon, T.S. Using fuzzy linguistic representations to provide explanatory semantics for data warehouses. IEEE Trans. Knowl. Data Eng. 2003, 15, 86–102. [Google Scholar] [CrossRef]
- Colombo, P.; Ferrari, E. Towards virtual private nosql datastores. In Proceedings of the 2016 IEEE 32nd International Conference on Data Engineering (ICDE), Helsinki, Finland, 16–20 May 2016; pp. 193–204. [Google Scholar]
- Colombo, P.; Ferrari, E. Fine-Grained Access Control Within NoSQL Document-Oriented Datastores. Data Sci. Eng. 2016, 1, 127–138. [Google Scholar] [CrossRef]
- Bellahsène, Z.; Bonifati, A.; Rahm, E. Schema Matching and Mapping; Springer: Cham, Switzerland, 2011. [Google Scholar]
- Kettouch, M.; Luca, C.; Hobbs, M. Schema Matching for Semi-structured and Linked Data. In Proceedings of the 11th International Conference on Semantic Computing, San Diego, CA, USA, 30 January–1 February 2017; pp. 270–271. [Google Scholar]
- Getoor, L.; Machanavajjhala, A. Entity resolution: Theory, practice & open challenges. Proc. VLDB Endow. 2012, 5, 2018–2019. [Google Scholar]
- Koudas, N.; Sarawagi, S.; Srivastava, D. Record linkage: Similarity measures and algorithms. In Proceedings of the 2006 ACM SIGMOD International Conference on Management of Data, ACM, Chicago, IL, USA, 27–29 June 2006; pp. 802–803. [Google Scholar]
- Guo, S.; Dong, X.L.; Srivastava, D.; Zajac, R. Record linkage with uniqueness constraints and erroneous values. Proc. VLDB Endow. 2010, 3, 417–428. [Google Scholar] [CrossRef]
- Liu, X.; Dong, X.L.; Ooi, B.C.; Srivastava, D. Online data fusion. Proc. VLDB Endow. 2011, 4, 932–943. [Google Scholar]
- Castano, S.; De Antonellis, V. Global viewing of heterogeneous data sources. IEEE Trans. Knowl. Data Eng. 2001, 13, 277–297. [Google Scholar] [CrossRef]
- Gagnon, M. Ontology-based integration of data sources. In Proceedings of the 2007 10th International Conference on Information Fusion, Quebec, QC, Canada, 9–12 July 2007; pp. 1–8. [Google Scholar]
- Calbimonte, J.P.; Corcho, O.; Gray, A.J. Enabling ontology-based access to streaming data sources. In Proceedings of the International Semantic Web Conference, Shanghai, China, 7–11 November 2010; pp. 96–111. [Google Scholar]
- Ray, P.P. A survey of IoT cloud platforms. Future Comput. Inf. J. 2016, 1, 35–46. [Google Scholar] [CrossRef]
- Botta, A.; De Donato, W.; Persico, V.; Pescapé, A. On the integration of cloud computing and internet of things. In Proceedings of the 2014 International Conference on Future Internet of Things and Cloud (FiCloud), Barcelona, Spain, 27–29 August 2014; pp. 23–30. [Google Scholar]
- Perera, C.; Zaslavsky, A.; Christen, P.; Georgakopoulos, D. Context aware computing for the internet of things: A survey. IEEE Commun. Surv. Tutor. 2013, 16, 414–454. [Google Scholar] [CrossRef]
- Waingold, E.; Taylor, M.; Srikrishna, D.; Sarkar, V.; Lee, W.; Lee, V.; Kim, J.; Frank, M.; Finch, P.; Barua, R.; et al. Baring it all to software: Raw machines. Computer 1997, 30, 86–93. [Google Scholar] [CrossRef]
- Ylitalo, J.; Nikander, P. A new name space for end-points: Implementing secure mobility and multi-homing across the two versions of IP. In Proceedings of the 5th European Wireless Conference, Barcelona, Spain, 24–27 February 2004; pp. 435–441. [Google Scholar]
- Saurez, E.; Gupta, H.; Mayer, R.; Ramachandran, U. Demo Abstract: Fog Computing for Improving User Application Interaction and Context Awareness. In Proceedings of the Second International Conference on Internet-of-Things Design and Implementation, Pittsburgh, PA, USA, 18–20 April 2017; pp. 281–282. [Google Scholar]
- Fantacci, R.; Nizzi, F.; Pecorella, T.; Pierucci, L.; Roveri, M. False Data Detection for Fog and Internet of Things Networks. Sensors 2019, 19, 4235. [Google Scholar] [CrossRef] [PubMed]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog computing and its role in the Internet of things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing, Helsinki, Finland, 17 August 2012; pp. 13–16. [Google Scholar]
- Stojmenovic, I.; Wen, S. The fog computing paradigm: Scenarios and security issues. In Proceedings of the Federated Conference on Computer Science and Information Systems (FedCSIS), Warsaw, Poland, 7–10 September 2014; pp. 1–8. [Google Scholar]
- Stojmenovic, I.; Wen, S.; Huang, X.; Luan, H. An overview of fog computing and its security issues. Concurr. Comput. Pract. Exp. 2016, 28, 2991–3005. [Google Scholar] [CrossRef]
- Zaghdoudi, B.; Ayed, H.K.B.; Harizi, W. Generic Access Control System for Ad Hoc MCC and Fog Computing. In Proceedings of the International Conference on Cryptology and Network Security, Milan, Italy, 14–16 November 2016; pp. 400–415. [Google Scholar]
- Salonikias, S.; Mavridis, I.; Gritzalis, D. Access control issues in utilizing fog computing for transport infrastructure. In Proceedings of the International Conference on Critical Information Infrastructures Security, Berlin, Germany, 5–7 October 2015; pp. 15–26. [Google Scholar]
- Yu, Z.; Au, M.H.; Xu, Q.; Yang, R.; Han, J. Towards leakage-resilient fine-grained access control in fog computing. Future Gener. Comput. Syst. 2018, 78, 763–777. [Google Scholar] [CrossRef]
- Zhang, P.; Chen, Z.; Liu, J.K.; Liang, K.; Liu, H. An efficient access control scheme with outsourcing capability and attribute update for fog computing. Future Gener. Comput. Syst. 2018, 78, 753–762. [Google Scholar] [CrossRef]
- Wang, H. Anonymous Data Sharing Scheme in Public Cloud and Its Application in E-health Record. IEEE Access 2018, 6, 27818–27826. [Google Scholar] [CrossRef]
- Cadwalladr, C.; Graham-Harrison, E. Revealed: 50 Million Facebook Profiles Harvested for Cambridge Analytica in Major Data Breach. Available online: https://protect-au.mimecast.com/s/EMpWCP7yRZi9ynQqfWivVK?domain=freestudio21.com (accessed on 21 April 2020).
- Dey, K.; Mondal, P. Social Networking Websites and Privacy Concern: A User Study. Asian J. Inf. Sci. Technol. 2018, 8, 33–38. [Google Scholar]
- Lampson, B.W. Protection. ACM SIGOPS Oper. Syst. Rev. 1974, 8, 18–24. [Google Scholar] [CrossRef]
- Qiu, L.; Zhang, Y.; Wang, F.; Kyung, M.; Mahajan, H.R. Trusted computer system evaluation criteria. In National Computer Security Center; Citeseer: Philadelphia, PA, USA, 1985. [Google Scholar]
- Saltzer, J.H. Protection and the control of information sharing in Multics. Commun. ACM 1974, 17, 388–402. [Google Scholar] [CrossRef]
- Sandhu, R.S.; Coyne, E.J.; Feinstein, H.L.; Youman, C.E. Role-Based Access Control Models. IEEE Comput. 1996, 29, 38–47. [Google Scholar] [CrossRef]
- Wang, L.; Wijesekera, D.; Jajodia, S. A logic-based framework for attribute based access control. In Proceedings of the 2004 ACM Workshop on Formal Methods in Security Engineering, Washington, DC, USA, 25–29 October 2004; pp. 45–55. [Google Scholar]
- Dey, A.K. Understanding and Using Context. Pers. Ubiquitous Comput. 2001, 5, 4–7. [Google Scholar] [CrossRef]
- Dey, A.K.; Abowd, G.D.; Salber, D. A Conceptual Framework and a Toolkit for Supporting the Rapid Prototyping of Context-Aware Applications. Hum. Comput. Interact. 2001, 16, 97–166. [Google Scholar] [CrossRef]
- Kayes, A.S.M.; Han, J.; Colman, A. ICAF: A Context-Aware Framework for Access Control. In Proceedings of the Australasian Conference on Information Security and Privacy, Wollongong, Australia, 9–11 July 2012; pp. 442–449. [Google Scholar]
- Kayes, A.; Rahayu, W.; Dillon, T.; Chang, E.; Han, J. Context-aware access control with imprecise context characterization for cloud-based data resources. Future Gener. Comput. Syst. 2019, 93, 237–255. [Google Scholar] [CrossRef]
- Wang, X.H.; Zhang, D.Q.; Gu, T.; Pung, H.K. Ontology Based Context Modeling and Reasoning using OWL. In Proceedings of the Second Annual Conference on Pervasive Computing and Communications Workshops, Orlando, FL, USA, 14–17 March 2004; pp. 18–22. [Google Scholar]
- Bettini, C.; Brdiczka, O.; Henricksen, K.; Indulska, J.; Nicklas, D.; Ranganathan, A.; Riboni, D. A survey of context modelling and reasoning techniques. Pervasive Mob. Comput. 2010, 6, 161–180. [Google Scholar] [CrossRef]
- Riboni, D.; Bettini, C. OWL 2 modeling and reasoning with complex human activities. Pervasive Mob. Comput. 2011, 7, 379–395. [Google Scholar] [CrossRef]
- Bertino, E.; Catania, B.; Damiani, M.L.; Perlasca, P. GEO-RBAC: A spatially aware RBAC. In Proceedings of the 10th Symposium on Access Control Models and Technologies, Stockholm, Sweden, 1–3 June 2005; pp. 29–37. [Google Scholar]
- Chandran, S.M.; Joshi, J.B. LoT-RBAC: A location and time-based RBAC model. In Proceedings of the International Conference on Web Information Systems Engineering, New York, NY, USA, 20–22 November 2005; pp. 361–375. [Google Scholar]
- Bhatti, R.; Ghafoor, A.; Bertino, E.; Joshi, J. X-GTRBAC: An XML-based policy specification framework and architecture for enterprise-wide access control. ACM Trans. Inf. Syst. Secur. 2005, 8, 187–227. [Google Scholar] [CrossRef]
- Figueroa-Lorenzo, S.; Añorga, J.; Arrizabalaga, S. A Role-Based Access Control Model in Modbus SCADA Systems. A Centralized Model Approach. Sensors 2019, 19, 4455. [Google Scholar] [CrossRef]
- Al-Kahtani, M.A.; Sandhu, R. A model for attribute-based user-role assignment. In Proceedings of the 18th Annual Computer Security Applications Conference, Las Vegas, NV, USA, 9–13 December 2002; pp. 353–362. [Google Scholar]
- Kern, A.; Walhorn, C. Rule support for role-based access control. In Proceedings of the 10th ACM Symposium on Access Control Models and Technologies, Stockholm, Sweden, 1–3 June 2005; pp. 130–138. [Google Scholar]
- Zheng, J.; Zhang, K.Q.; Zheng, W.S.; Tan, A.Y. Dynamic Role-Based Access Control Model. JSW 2011, 6, 1096–1102. [Google Scholar] [CrossRef]
- Zhang, R.; Giunchiglia, F.; Crispo, B.; Song, L. Relation-Based Access Control: An Access Control Model for Context-Aware Computing Environment. Wirel. Pers. Commun. 2010, 55, 5–17. [Google Scholar] [CrossRef]
- Fong, P.W.; Siahaan, I. Relationship-based access control policies and their policy languages. In Proceedings of the 16th ACM Symposium on Access Control Models and Technologies, Innsbruck, Austria, 15–17 June 2011; pp. 51–60. [Google Scholar]
- Endsley, M.R. Design and evaluation for situation awareness enhancement. In Proceedings of the Human Factors Society Annual Meeting; SAGE Publications: Los Angeles, CA, USA, 1988; Volume 32, pp. 97–101. [Google Scholar]
- Kim, Y.G.; Lim, J. Dynamic activation of role on rbac for ubiquitous applications. In Proceedings of the International Conference on Convergence Information Technology, Gyeongju, Korea, 21–23 November 2007; pp. 1148–1153. [Google Scholar]
- Garcia-Morchon, O.; Wehrle, K. Modular context-aware access control for medical sensor networks. In Proceedings of the 15th ACM Symposium on Access Control Models and Technologies, Pittsburgh, PA, USA, 9–11 June 2010; pp. 129–138. [Google Scholar]
- Yau, S.S.; Huang, D. Development of Situation-Aware Applications in Services and Cloud Computing Environments. Int. J. Softw. Inf. 2013, 7, 21–39. [Google Scholar]
- Yau, S.S.; Karim, F.; Wang, Y.; Wang, B.; Gupta, S.K. Reconfigurable context-sensitive middleware for pervasive computing. IEEE Pervasive Comput. 2002, 1, 33–40. [Google Scholar] [CrossRef]
- Yau, S.S.; Liu, J. A situation-aware access control based privacy-preserving service matchmaking approach for service-oriented architecture. In Proceedings of the International Conference on Web Services (ICWS 2007), Salt Lake City, UT, USA, 9–13 July 2007; pp. 1056–1063. [Google Scholar]
- Jones, R.E.; Connors, E.S.; Mossey, M.E.; Hyatt, J.R.; Hansen, N.J.; Endsley, M.R. Using fuzzy cognitive mapping techniques to model situation awareness for army infantry platoon leaders. Comput. Math. Organ. Theory 2011, 17, 272–295. [Google Scholar] [CrossRef]
- Almenárez, F.; Marín, A.; Campo, C.; García, C. TrustAC: Trust-based access control for pervasive devices. In Proceedings of the International Conference on Security in Pervasive Computing, Boppard, Germany, 6–8 April 2005; pp. 225–238. [Google Scholar]
- Chang, E.; Hussain, F.; Dillon, T. Trust and Reputation for Service-Oriented Environments: Technologies for Building Business Intelligence and Consumer Confidence; John Wiley & Sons: New York, NY, USA, 2006. [Google Scholar]
- Takabi, H.; Amini, M.; Jalili, R. Trust-based user-role assignment in role-based access control. In Proceedings of the International Conference on Computer Systems and Applications, Amman, Jordan, 13–16 May 2007; pp. 807–814. [Google Scholar]
- Martínez-García, C.; Navarro-Arribas, G.; Borrell, J. Fuzzy role-based access control. Inf. Process. Lett. 2011, 111, 483–487. [Google Scholar] [CrossRef]
- Roberts, D.W. Ordination on the basis of fuzzy set theory. Vegetatio 1986, 66, 123–131. [Google Scholar] [CrossRef]
- Botta, A.; De Donato, W.; Persico, V.; Pescapé, A. Integration of cloud computing and internet of things: A survey. Future Gener. Comput. Syst. 2016, 56, 684–700. [Google Scholar] [CrossRef]
- Covington, M.J.; Long, W.; Srinivasan, S.; Dev, A.K.; Ahamad, M.; Abowd, G.D. Securing context-aware applications using environment roles. In Proceedings of the 6th ACM Symposium on Access Control Models and Technologies, Chantilly, VI, USA, 3–4 May 2001; pp. 10–20. [Google Scholar]
- Zhang, H.; He, Y.; Shi, Z. A formal model for access control with supporting spatial context. Sci. China Ser. F Inf. Sci. 2007, 50, 419–439. [Google Scholar] [CrossRef]
- Zhou, Z.; Wu, L.; Hong, Z.; Liang, Z.; Jun, L.; Xu, S.-J.; Chen, D.; Xiao, P.; Qu, P.; Qu, X.; et al. Context-aware access control model for cloud computing. Int. J. Grid Distrib. Comput. 2013, 6, 1–12. [Google Scholar] [CrossRef]
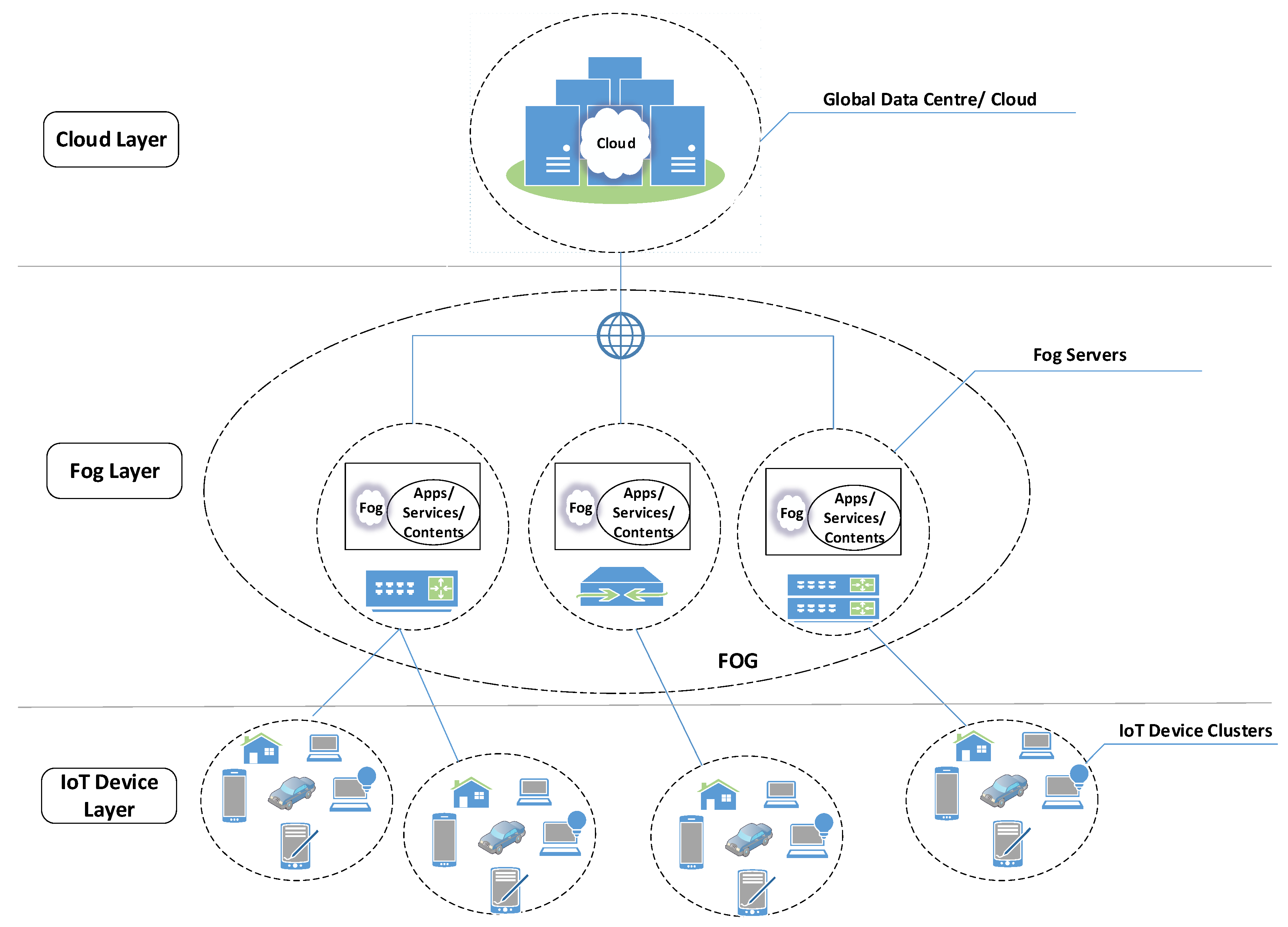
- Atlam, H.F.; Walters, R.J.; Wills, G.B. Fog computing and the internet of things: A review. Big Data Cogn. Comput. 2018, 2, 10. [Google Scholar] [CrossRef]
- Yi, S.; Qin, Z.; Li, Q. Security and privacy issues of fog computing: A survey. In Proceedings of the International Conference on Wireless Algorithms, Systems, and Applications, Qufu, China, 10–12 August 2015; pp. 685–695. [Google Scholar]
- Mukherjee, M.; Matam, R.; Shu, L.; Maglaras, L.; Ferrag, M.A.; Choudhury, N.; Kumar, V. Security and privacy in fog computing: Challenges. IEEE Access 2017, 5, 19293–19304. [Google Scholar] [CrossRef]
- Pierleoni, P.; Concetti, R.; Belli, A.; Palma, L. Amazon, Google and Microsoft Solutions for IoT: Architectures and a Performance Comparison. IEEE Access 2019, 8, 5455–5470. [Google Scholar] [CrossRef]
- Jiang, B.; Huang, G.; Wang, T.; Gui, J.; Zhu, X. Trust based energy efficient data collection with unmanned aerial vehicle in edge network. In Transactions on Emerging Telecommunications Technologies; Wiley: New York, NY, USA, 2020. [Google Scholar]
- Liu, X.; Liu, A.; Wang, T.; Ota, K.; Dong, M.; Liu, Y.; Cai, Z. Adaptive data and verified message disjoint security routing for gathering big data in energy harvesting networks. J. Parallel Distrib. Comput. 2020, 135, 140–155. [Google Scholar] [CrossRef]
- Huang, M.; Liu, A.; Xiong, N.N.; Wang, T.; Vasilakos, A.V. An Effective Service-Oriented Networking Management Architecture for 5G-Enabled Internet of Things. Comput. Netw. 2020, 173, 107208. [Google Scholar] [CrossRef]
- Saha, R.; Kumar, G.; Rai, M.K.; Thomas, R.; Lim, S.J. Privacy Ensured e-Healthcare for Fog-Enhanced IoT Based Applications. IEEE Access 2019, 7, 44536–44543. [Google Scholar] [CrossRef]
- Siow, E.; Tiropanis, T.; Hall, W. PIOTRe: Personal Internet of Things Repository. In Proceedings of the International Semantic Web Conference Posters & Demos, Kobe, Japan, 17–21 October 2016. [Google Scholar]
- Agrawal, R.; Srikant, R. Privacy-preserving data mining. In Proceedings of the ACM International Conference on Management of Data and Symposium on Principles of Database Systems, Dallas, TX, USA, 14–19 May 2000; pp. 439–450. [Google Scholar]
- Doganay, M.C.; Pedersen, T.B.; Saygin, Y.; Savaş, E.; Levi, A. Distributed privacy preserving k-means clustering with additive secret sharing. In Proceedings of the 2008 International Workshop on Privacy and Anonymity in Information Society, Nantes, France, 29 March 2008; pp. 3–11. [Google Scholar]
- Erkin, Z.; Veugen, T.; Toft, T.; Lagendijk, R.L. Privacy-preserving distributed clustering. EURASIP J. Inf. Secur. 2013, 2013, 4. [Google Scholar] [CrossRef]
- Oliveira, S.R.; Zaiane, O.R. Privacy preserving clustering by data transformation. J. Inf. Data Manag. 2010, 1, 37. [Google Scholar]
- Badsha, S.; Yi, X.; Khalil, I.; Liu, D.; Nepal, S.; Bertino, E.; Lam, K.Y. Privacy preserving location-aware personalized web service recommendations. IEEE Trans. Serv. Comput. 2018. [Google Scholar] [CrossRef]
- Badsha, S.; Yi, X.; Khalil, I.; Liu, D.; Nepal, S.; Lam, K.Y. Privacy preserving user based web service recommendations. IEEE Access 2018, 6, 56647–56657. [Google Scholar] [CrossRef]
- Badsha, S.; Yi, X.; Khalil, I. A practical privacy-preserving recommender system. Data Sci. Eng. 2016, 1, 161–177. [Google Scholar] [CrossRef]
- Badsha, S.; Khalil, I.; Yi, X.; Atiquzzaman, M. Designing privacy-preserving protocols for content sharing and aggregation in content centric networking. IEEE Access 2018, 6, 42119–42130. [Google Scholar] [CrossRef]
- Badsha, S.; Vakilinia, I.; Sengupta, S. Privacy Preserving Cyber Threat Information Sharing and Learning for Cyber Defense. In Proceedings of the IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 7–9 January 2019; pp. 708–714. [Google Scholar]
- Wang, C.; Chow, S.S.; Wang, Q.; Ren, K.; Lou, W. Privacy-preserving public auditing for secure cloud storage. IEEE Trans. Comput. 2011, 62, 362–375. [Google Scholar] [CrossRef]
- Alabdulatif, A.; Kumarage, H.; Khalil, I.; Yi, X. Privacy-preserving anomaly detection in cloud with lightweight homomorphic encryption. J. Comput. Syst. Sci. 2017, 90, 28–45. [Google Scholar] [CrossRef]
- Alabdulatif, A.; Khalil, I.; Yi, X. Towards secure big data analytic for cloud-enabled applications with fully homomorphic encryption. J. Parallel Distrib. Comput. 2019, 137, 192–204. [Google Scholar] [CrossRef]
- Van Dijk, M.; Juels, A. On the impossibility of cryptography alone for privacy-preserving cloud computing. HotSec 2010, 10, 1–8. [Google Scholar]
- Malina, L.; Hajny, J. Efficient security solution for privacy-preserving cloud services. In Proceedings of the 36th International Conference on Telecommunications and Signal Processing (TSP), Rome, Italy, 2–4 July 2013; pp. 23–27. [Google Scholar]
- Xu, R.; Joshi, J.B. An integrated privacy preserving attribute based access control framework. In Proceedings of the IEEE 9th International Conference on Cloud Computing (CLOUD), San Francisco, CA, USA, 27 June–2 July 2016; pp. 68–76. [Google Scholar]
- Waizenegger, T.; Wieland, M.; Binz, T.; Breitenbücher, U.; Haupt, F.; Kopp, O.; Leymann, F.; Mitschang, B.; Nowak, A.; Wagner, S. Policy4TOSCA: A policy-aware cloud service provisioning approach to enable secure cloud computing. In Proceedings of the OTM Confederated International Conferences “On the Move to Meaningful Internet Systems”, Graz, Austria, 9–13 September 2013; pp. 360–376. [Google Scholar]
- Breitenbücher, U.; Binz, T.; Fehling, C.; Kopp, O.; Leymann, F.; Wieland, M. Policy-Aware Provisioning and Management of Cloud Applications. Int. J. Adv. Secur. 2014, 7, 15–36. [Google Scholar]
- Yussupov, V.; Falkenthal, M.; Kopp, O.; Leymann, F.; Zimmermann, M. Secure collaborative development of cloud application deployment models. In Proceedings of the 12th International Conference on Emerging Security Information, Systems and Technologies, Venice, Italy, 16–20 September 2018. [Google Scholar]
- Yussupov, V.; Falazi, G.; Falkenthal, M.; Leymann, F. Protecting Deployment Models in Collaborative Cloud Application Development. Int. J. Adv. Secur. 2019, 79–94. [Google Scholar]
- Wurster, M.; Breitenbücher, U.; Kopp, O.; Leymann, F. Modeling and Automated Execution of Application Deployment Tests. In Proceedings of the IEEE 22nd International Enterprise Distributed Object Computing Conference (EDOC), Stockholm, Sweden, 16–19 October 2018; pp. 171–180. [Google Scholar]
- Zimmermann, M.; Breitenbücher, U.; Krieger, C.; Leymann, F. Deployment Enforcement Rules for TOSCA-based Applications. In Proceedings of the 12th International Conference on Emerging Security Information, Systems and Technologies, Venice, Italy, 16–20 September 2018; pp. 114–121. [Google Scholar]
- Fischer, M.P.; Breitenbücher, U.; Képes, K.; Leymann, F. Towards an Approach for Automatically Checking Compliance Rules in Deployment Models. In Proceedings of the 11th International Conference on Emerging Security Information, Systems and Technologies, Rome, Italy, 10–14 September 2017; pp. 150–153. [Google Scholar]
- Képes, K.; Breitenbücher, U.; Leymann, F.; Saatkamp, K.; Weder, B. Deployment of Distributed Applications Across Public and Private Networks. In Proceedings of the IEEE 23rd International Enterprise Distributed Object Computing Conference (EDOC), Paris, France, 28–31 October 2019; pp. 236–242. [Google Scholar]
- Hardt, D. The OAuth 2.0 Authorization Framework. Available online: https://protect-au.mimecast.com/s/zNjQCQnzV0igzL7mivocg6?domain=hjp.at (accessed on 21 April 2020).
- Watters, P.; Scolyer-Gray, P.; Kayes, A.; Chowdhury, M.J.M. This would work perfectly if it weren’t for all the humans: Two factor authentication in late modern societies. First Monday 2019, 24, 7. [Google Scholar] [CrossRef]
- Taylor, M.J.; Whitton, T. Public Interest, Health Research and Data Protection Law: Establishing a Legitimate Trade-Off between Individual Control and Research Access to Health Data. Laws 2020, 9, 6. [Google Scholar] [CrossRef]
- Chiang, M.; Zhang, T. Fog and IoT: An overview of research opportunities. IEEE Internet Things J. 2016, 3, 854–864. [Google Scholar] [CrossRef]
- Delgrossi, L.; Zhang, T. Vehicle Safety Communications: Protocols, Security, and Privacy; Wiley: New York, NY, USA, 2012; Volume 103. [Google Scholar]
- Bruschi, R.; Davoli, F.; Lago, P.; Pajo, J.F. Move with me: Scalably keeping virtual objects close to users on the move. In Proceedings of the IEEE International Conference on Communications, Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Baek, J.; Vu, Q.H.; Liu, J.K.; Huang, X.; Xiang, Y. A secure cloud computing based framework for big data information management of smart grid. IEEE Trans. Cloud Comput. 2014, 3, 233–244. [Google Scholar] [CrossRef]

| Scope | Description |
|---|---|
| S1 | We first cover the background of the traditional access control and context-aware access control literature. |
| S2 | We then present different taxonomies of contextual conditions and authorization models according to the access control-specific contextual entities. |
| S3 | We cover the existing context-sensitive access control approaches, including the Role-Based Access Control (RBAC) mechanisms and Context-Aware Access Control (CAAC) approaches for IoT sensor networks, privacy-preserving techniques and applications for distributed cloud databases and the policy-aware deployment and management of cloud applications. |
| S4 | We divide the context-aware access control literature into main two categories: the access control mechanisms for centralized networks and the access control mechanisms for decentralized cloud and fog networks. |
| S5 | We provide a comparative analysis of the existing context-aware access control mechanisms. We highlight the limitations and shortcomings of these mechanisms that motivate us to develop a new CAAC framework for cloud and fog networks. |
| S6 | We discuss the directions of future research along with practical case studies, including access management against identify thefts, safeguarding health data against data breaches, protecting banking customers against data breaches, and security and privacy of the internet of things. We also include the research challenges and opportunities in these directions. |
| S7 | In addition, we propose a new generation of fog-based CAAC model for today’s cloud and fog networks, including a layer-based framework. |
| S8 | From our analysis of the state-of-the-art access control literature and open research issues, finally we identify the general requirements of an emerging fog-based CAAC mechanism. |
| Research | Context Definition | Entity |
|---|---|---|
| Dey et al. [60] | The context information can be seen as any information that can be used to characterize the situation of an entity (an entity is a person, a place or an object). | Person, Place and Object |
| Kayes et al. [62] | The context information can be seen as any information that can be used to characterize the state of the relevant access control-specific entities and the state of the relevant relationships between different entities (an access control-specific entity is a user, a resource or an environment). | User, Resource and Environment |
| Research | Context Definition |
|---|---|
| Dey et al. [60] | General Context Definition in Pervasive Domain: Focusing the pervasive computing domain, the general context information can be categorized into three types: person, place and object-specific. |
| Kayes et al. [62] | General Context Definition in CAAC Domain: Focusing the access control domain, the context information can be categorized into three types: user, resource and environment-specific. Based on the access control literature, the context information also can be categorized into two types: basic context and derived context. |
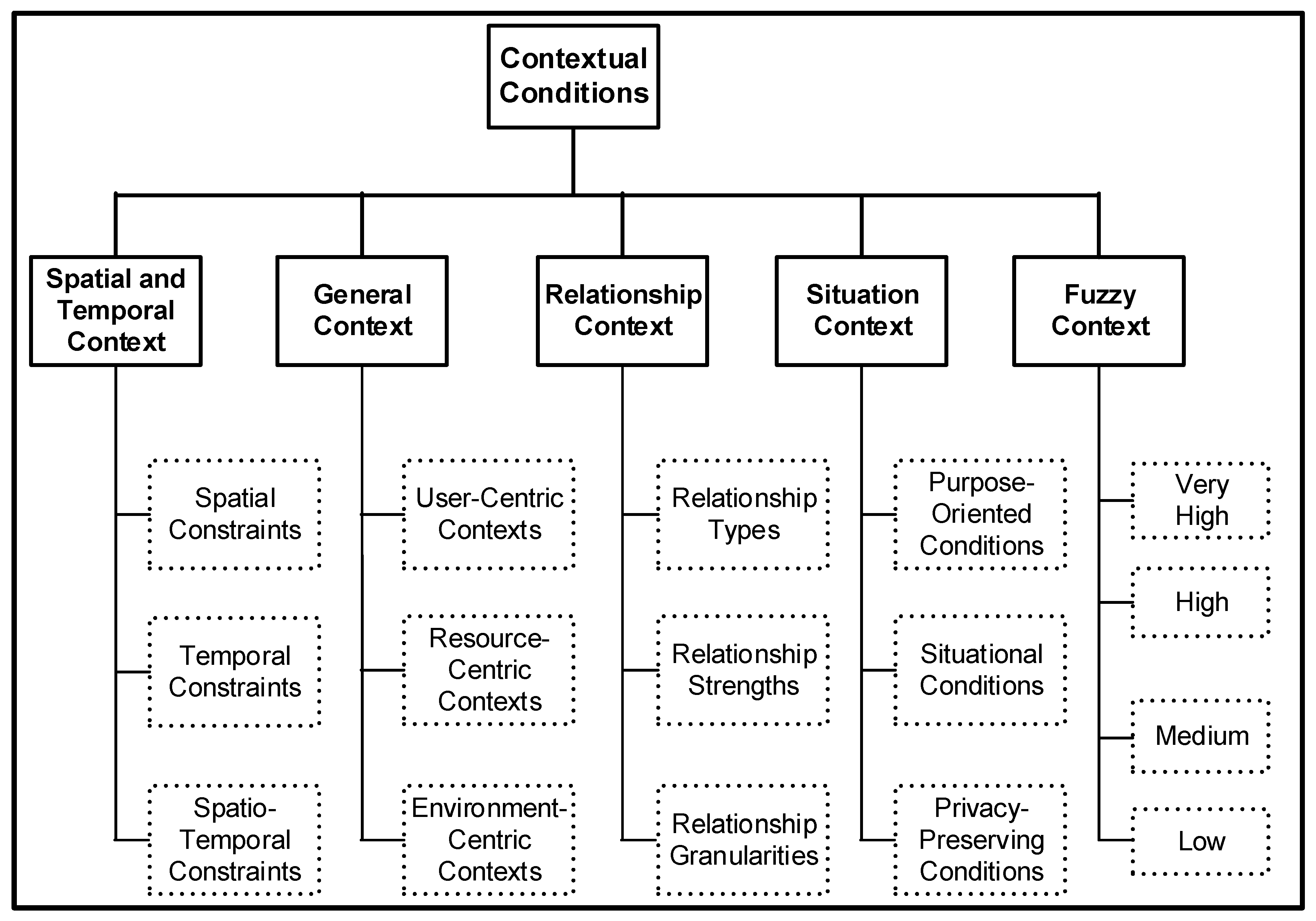
| Kayes et al. [19] | Basic Context Definition in CAAC Domain: The basic context can be captured or sensed directly from the raw contextual facts, such as the location context can be captured from the raw location coordinates. |
| Kayes et al. [6] | Derived Context Definition in CAAC domain: The derived context can be inferred from the basic context information, such as derived or inferred contexts can be relationship-based, situational and fuzzy context. |
| Kayes et al. [20] | Relationship Context Definition in CAAC domain: The relationship context can be categorized as social or interpersonal relationship and location-specific or co-located relationship. The interpersonal relationship context can be inferred from the users’ profile context and the colocated relationship context can be derived from the users’ location context. |
| Kayes et al. [10] | Situational Context Definition in CAAC domain: A situational context is defined as the states of the access control-specific entities and the states of the relationships between such entities at a particular time that are relevant to a certain goal or purpose of a resource access request. The situation value can be obtained based on the access request (i.e., from the sensed contexts, and/or inferred contexts). |
| Kayes et al. [63] | Fuzzy Context Definition in CAAC domain: The fuzzy context information cannot be obtained directly from the raw contextual facts, which are the crisp sets, where the value can be ranged either 0 or 1. Such information can be obtained based on the degree of membership function, where the value can be ranged from 0 to 1, or based on another type of measure like low, medium or high. A patient’s health status is “70% critical with a critically level of 0.7 or high”, which is a fuzzy context. |
| Research | Contribution Areas |
|---|---|
| [15,16,17,67,68,69] | The RBAC Approaches with Spatial and Temporal Contexts |
| [6,19,25,62,71,72,73] | The RBAC Approaches with User, Resource, and Environment-Centric Contexts |
| [20,74,75] | The RBAC Approaches with Relationship Contexts |
| [8,10,21,64,76,77,78,79,80,81] | The RBAC Approaches with Situational Contexts |
| [7,63,82,83,84,85,86] | The RBAC Approaches with Fuzzy Contexts |
| Research | Contribution Areas |
|---|---|
| [22,23,91,95,96,97,98] | The CAAC Approaches for Accessing Data from Edge, IoT and Cloud Networks |
| [99,100,101,102,103,104,105,106,107,108,109] | The Privacy-Preserving Protocols and Mechanisms for Distributed Cloud Databases |
| [110,111,112,113,114,115] | The Privacy-Preserving Mechanisms for Cloud Service Providers |
| [116,117,118,119,121,122,123] | The Policy-Aware Deployment and Management of Cloud Applications |
| Requirement | Description |
|---|---|
| R1 | How to capture and derive the relevant contextual conditions from the IoT, fog and cloud environments? Thus, there is a need for a generic context model to capture and represent relevant contextual conditions using information provided through IoT devices and the associated fog and cloud environments. |
| R2 | How to effectively specify the context-aware access control policies to manage and control data from distributed cloud sources by means of reducing computational overheads? Towards this goal, we can model a single set of access control policies instead of multiple sets of policies for different data sources. |
| R3 | In order to reduce the overheads, how to build a global data model to map the identical attributes (e.g., the contextual conditions) from the relevant data sources and apply the same set of policy in the intermediary fog layer for accessing data from multiple sources? |
| R4 | Focusing on the privacy requirements of the multiple stakeholders, how the end-users can prevent unauthorized entities and can ensure the privileges to access only certain information except sensitive and personally identifiable information? |
| R5 | In order to limit the permissions to data from multiple cloud centres and achieve trust among all peers (e.g., users and other stakeholders), how to build an appropriate data sharing mechanism for all the entities involved, like IoT devices, fog servers and cloud data centres. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kayes, A.S.M.; Kalaria, R.; Sarker, I.H.; Islam, M.S.; Watters, P.A.; Ng, A.; Hammoudeh, M.; Badsha, S.; Kumara, I. A Survey of Context-Aware Access Control Mechanisms for Cloud and Fog Networks: Taxonomy and Open Research Issues. Sensors 2020, 20, 2464. https://doi.org/10.3390/s20092464
Kayes ASM, Kalaria R, Sarker IH, Islam MS, Watters PA, Ng A, Hammoudeh M, Badsha S, Kumara I. A Survey of Context-Aware Access Control Mechanisms for Cloud and Fog Networks: Taxonomy and Open Research Issues. Sensors. 2020; 20(9):2464. https://doi.org/10.3390/s20092464
Chicago/Turabian StyleKayes, A. S. M., Rudri Kalaria, Iqbal H. Sarker, Md. Saiful Islam, Paul A. Watters, Alex Ng, Mohammad Hammoudeh, Shahriar Badsha, and Indika Kumara. 2020. "A Survey of Context-Aware Access Control Mechanisms for Cloud and Fog Networks: Taxonomy and Open Research Issues" Sensors 20, no. 9: 2464. https://doi.org/10.3390/s20092464
APA StyleKayes, A. S. M., Kalaria, R., Sarker, I. H., Islam, M. S., Watters, P. A., Ng, A., Hammoudeh, M., Badsha, S., & Kumara, I. (2020). A Survey of Context-Aware Access Control Mechanisms for Cloud and Fog Networks: Taxonomy and Open Research Issues. Sensors, 20(9), 2464. https://doi.org/10.3390/s20092464










