Trustworthiness and a Zero Leakage OTMP-P2L Scheme Based on NP Problems for Edge Security Access †
Abstract
1. Introduction
- We conduct the study on zero-knowledge proof algorithms and propose a feasible multi algorithms chaining scheme. Since the previous message authentication code needs manual interaction, the content is simple, and the algorithm is single. In the open environment of the IoT, it is necessary to enrich the verification content, increase the complexity of verification codes and the difficulty of production, simplify the verification process, and automate. Thus, we design the enhanced message authentication code, which can limit the time, place, identity and collection members by multifactor zero-knowledge non-interactive verification. We choose a variety of chaining NP problems to achieve verification. The new scheme can exponentially increase the difficulty of crack, thereby reducing the workload.
- We implement an anonymously distributed authorization mechanism that allows users to manage addresses dynamically and choose one autonomously. The centralized authorization has problems such as forgery, single point of failure, user identity, and other data leakage. After removing the user data control right, the authorization center only completes the negotiation and sharing of the common reference string, and the center provides the reservation token service according to the access relationship agreed by the service provider. The provider achieves non-interactive point-to-point verification. So the anonymous mechanism avoids data leakage.
- We make a smart lock prototype system and deploy on MUC and PC equipment to verify the performance of six test cases. The experimental results show that the amount of data required for the proposed scheme is not substantial, and that the resource usage of the verification calculations is within control. The system can be deployed and run stably in existing smart devices and resource-constrained IoT nodes.
2. Related Work
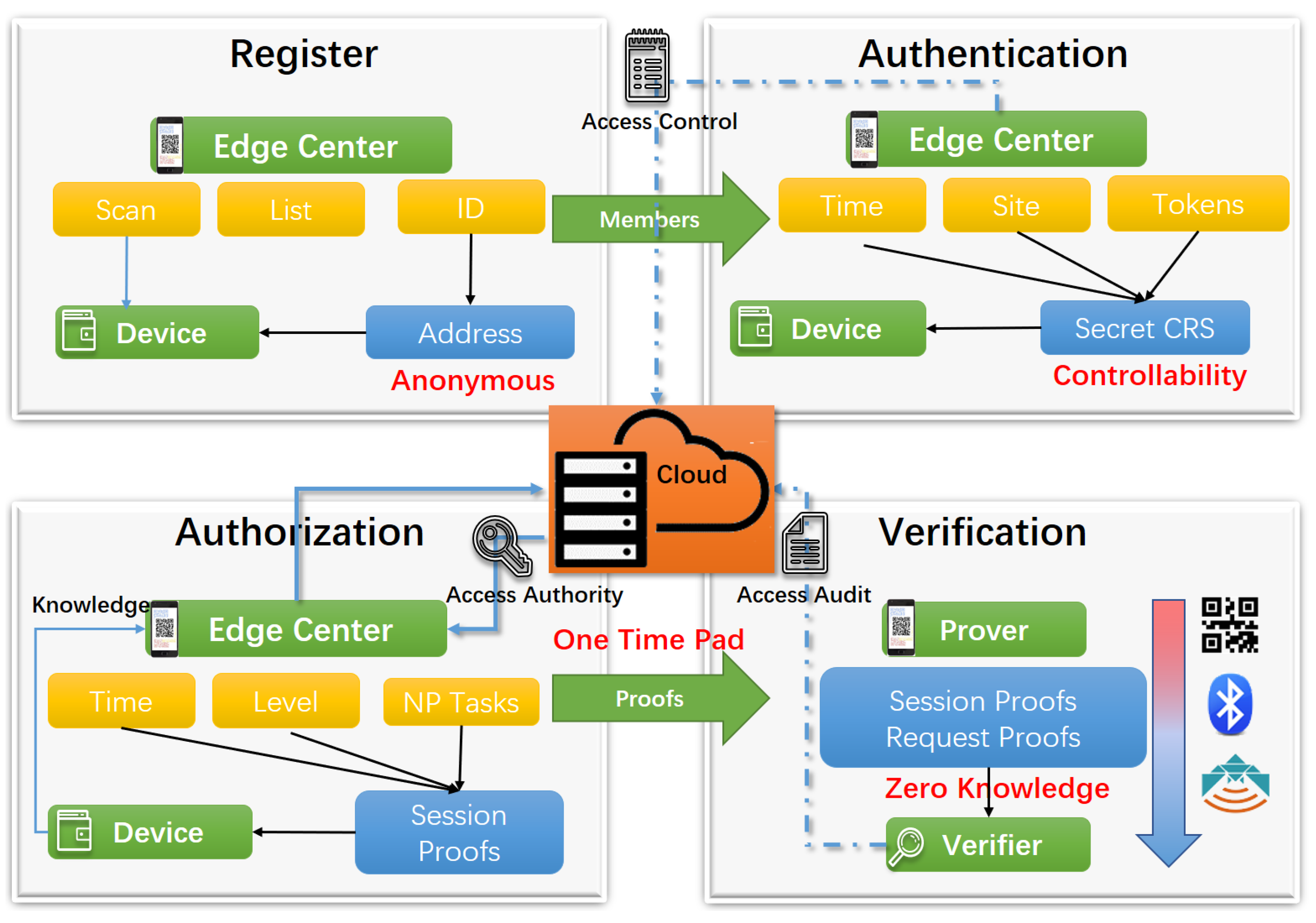
3. OTMP-P2L Architecuture
3.1. Register
3.2. Local Authentication
3.3. Local Authorization
3.4. P2P Verification
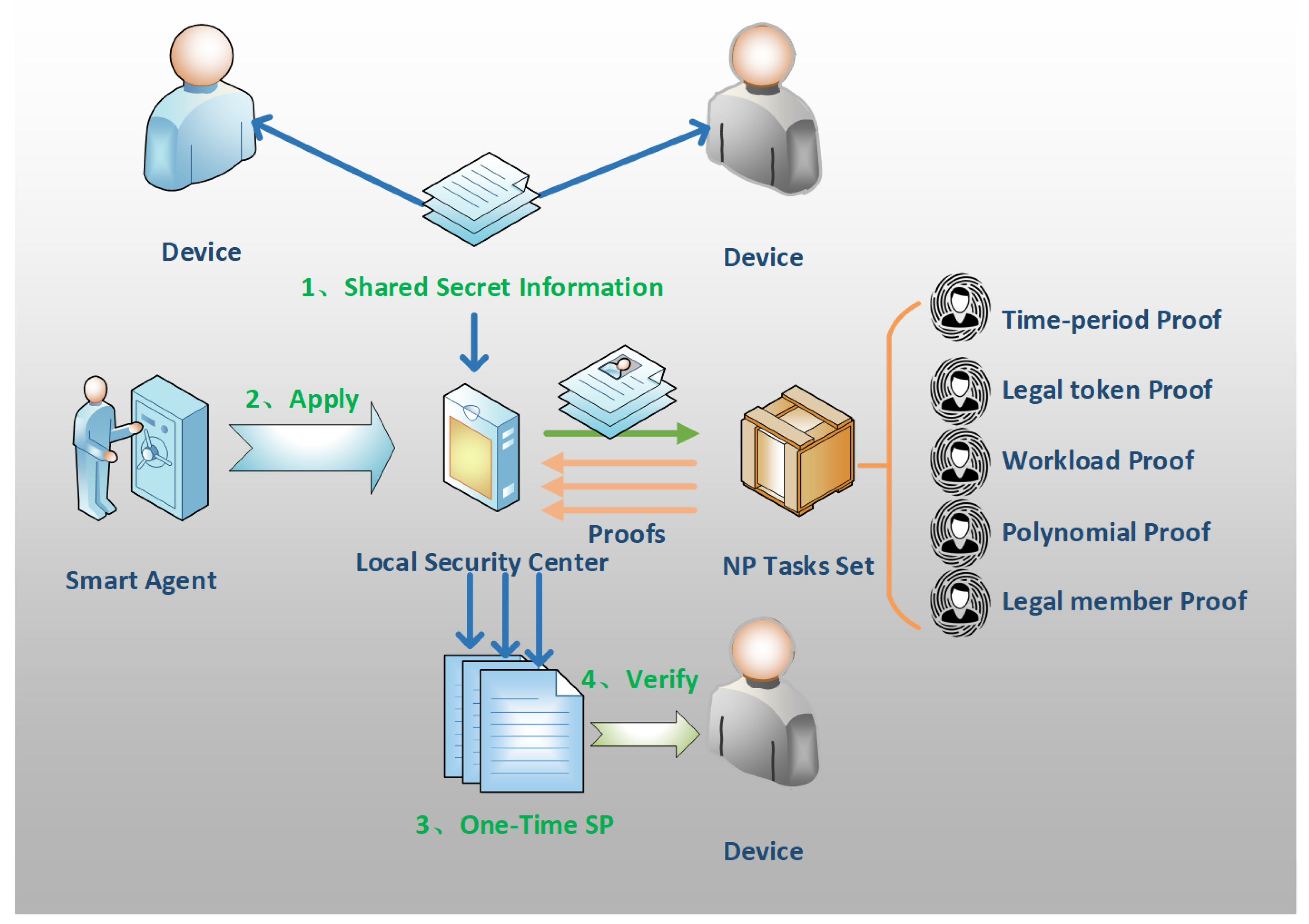
4. OTMP Methodology
4.1. Methodology
4.1.1. Zero Knowledge Proof
- The addition of input values is the output of every hidden transaction.
- The sender proves that they have a private key for each entry and therefore has the power to consume.
- The cost private key of the input item is linked to the signature of the entire transaction in an encrypted way, and it is difficult for anyone can modify the transaction without knowing these private keys.
- For most x, it is usually difficult to solve x at a given .
- Different inputs will get different outputs, so if , then .
- If someone knows and , and can be used to calculate .
- For each exponential of s, Bob calculates and sends them to Alice.
- Alice knows all the coefficients of the polynomial and can calculate using the homomorphic property and send it back to Bob.
- A set of polynomials over a finite field F: ;
- The target polynomial t on the finite field F;
- The injective function .
- If , then ; (where is the i-th bit of u);
- If , then ;
- The target polynomial t can be divisible by .
4.1.2. Proof of Work
4.1.3. ECC Algorithm
- While encrypting with the public key Q, find the random number M and calculate and (M is randomly selected, x is the number to be encrypted).
- While decrypting with the private key k, the ciphertexts and are obtained, calculate , and the plaintext x is decrypted.
- Even though other attackers know and G, they cannot directly calculate M by division. They also cannot directly calculate x with and Q. Random number M can make the values of and different each time.
- While signing with the private key k, find the random number M, the hash value h of the message x, the coordinate position of the G, and calculate and .
- While verifying the signature with the public key Q, the message x and the signature are obtained, use the hash value h of the message x, and calculate . If the calculation result is the same as the received signature , the verification is successful.
4.2. Tasks Set
4.2.1. Proof of the Period
4.2.2. Proof of the Legal Token
4.2.3. Proof of Work
4.2.4. Proof of zk-SNARK
4.2.5. Proof of Legal Members
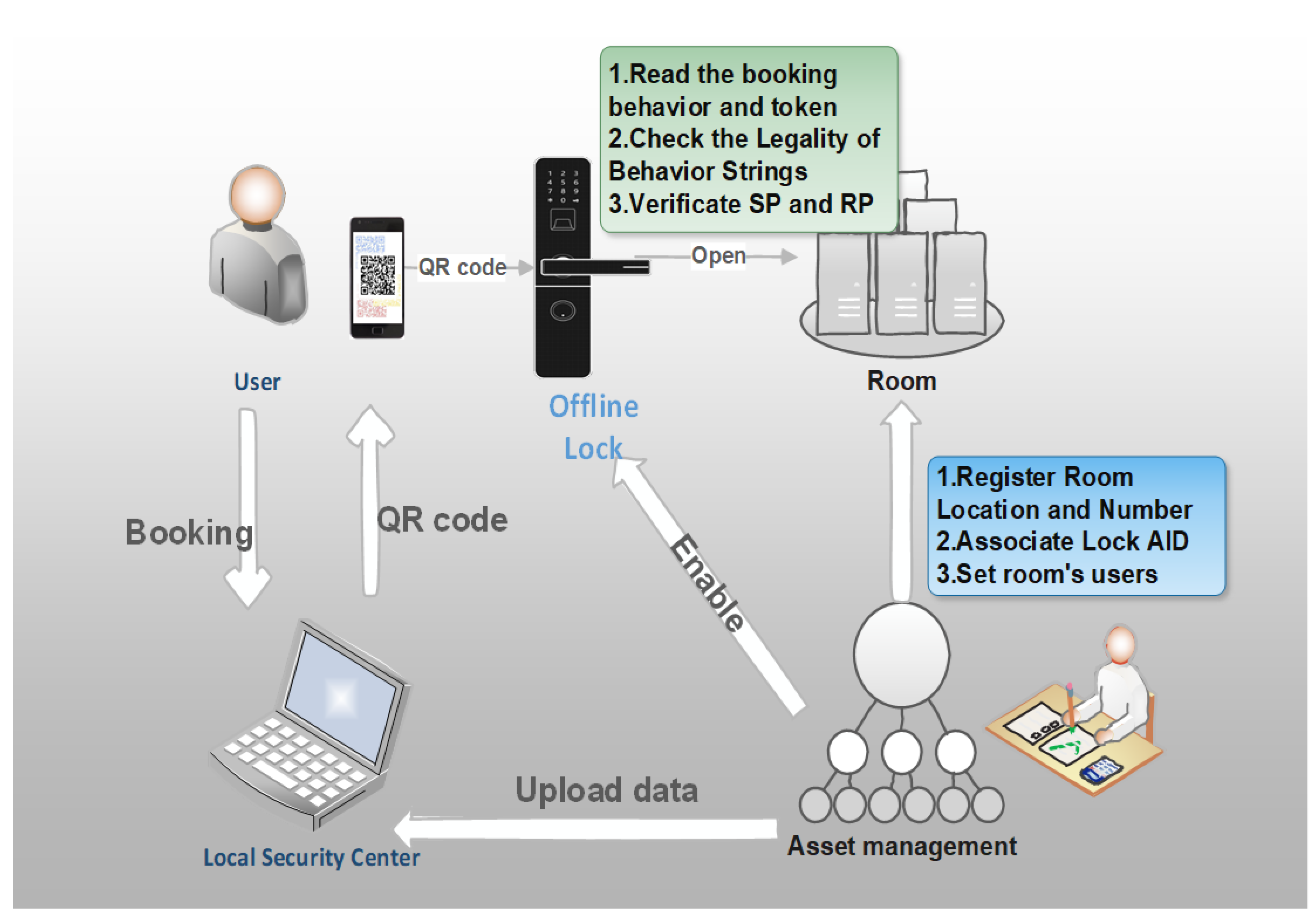
4.3. Verification
4.3.1. SP Reservation
4.3.2. SP Authentication
- After receiving the data, the device uses the internally stored elliptic curve parameter and the private key to decrypt the token, so obtains the hash data HCBS. The algorithm guarantees that only the specified device can decrypt and find the HCBS.
- The device uses the received user public key, the internal center public key, decrypts the signature data twice, and then verifies that it is consistent with the above HCBS signature.
- The device uses the user public key, HCBS, start and end timestamps, four known random numbers, and also needs to find the remaining four random numbers, and calculates the consensus hash string HPC of the PoW mechanism with the specified difficulty requirement. If it is consistent with the HPC obtained by the scan, it is verified that both the server and the device have paid the corresponding difficulty work, and the authentication is passed.
4.3.3. RP Generation and Verification
4.4. Challenges
- The attacker collects data by eavesdropping. The SP token is a one-time evidence of encryption that cannot be solved to obtain the pre-made shared information CRS and forge a new token. Due to the timestamp control mechanism, each request message and signature token RP are different. Moreover, messages are encrypted by a secure ECC algorithm.
- Man-in-the-middle attack. When masquerading, there is no trust relationship with the security center. When applying for a legal token SP, an attacker cannot pretend to be a requester to send a message. When replaying a message, it is necessary to update the timestamp, so the token RP also needs to be regenerated.
- DDoS attack. There is no centralized authentication service, or direct point-to-point authentication. When a device is attacked, it does not affect other devices.
- Physical hijacking. It is impossible to pass the multifactor authentication and release the original binding relationship, so the pre-made shared information CRS cannot be read and decrypted. When a forged CRS is transmitted to the device through a secure channel, it also cannot pass the authentication.
- Fictional legal user. Due to the lack of trust with the security center, an attacker cannot apply for legal token SP in a batch. The accumulated value A is generated by using the Nyberg one-way accumulator as the shared information CRS generated by the identity authentication, and the accumulated function can quickly verify whether the opponent is an accumulated item of the accumulated value A.
- Privacy query. Only the smart device that becomes the security center can query corresponding devices according to the anonymous ID, can check resources, and can audit logs. All the devices use the AID in the verification phase.
- The multiple proofs will increase program complexity and length of verification strings.
- Important is also the tradeoff between chain more algorithms and reduce the workload of each one, we should define the security level of each combination before its employment in practical.
- The static CRS are the keys to hiding knowledge in these algorithms, it is also a potential risk.
- The batch reservation method places restrictions on the service capabilities of edge devices, and the pre-made tokens cannot bind and protect dynamic real-time data.
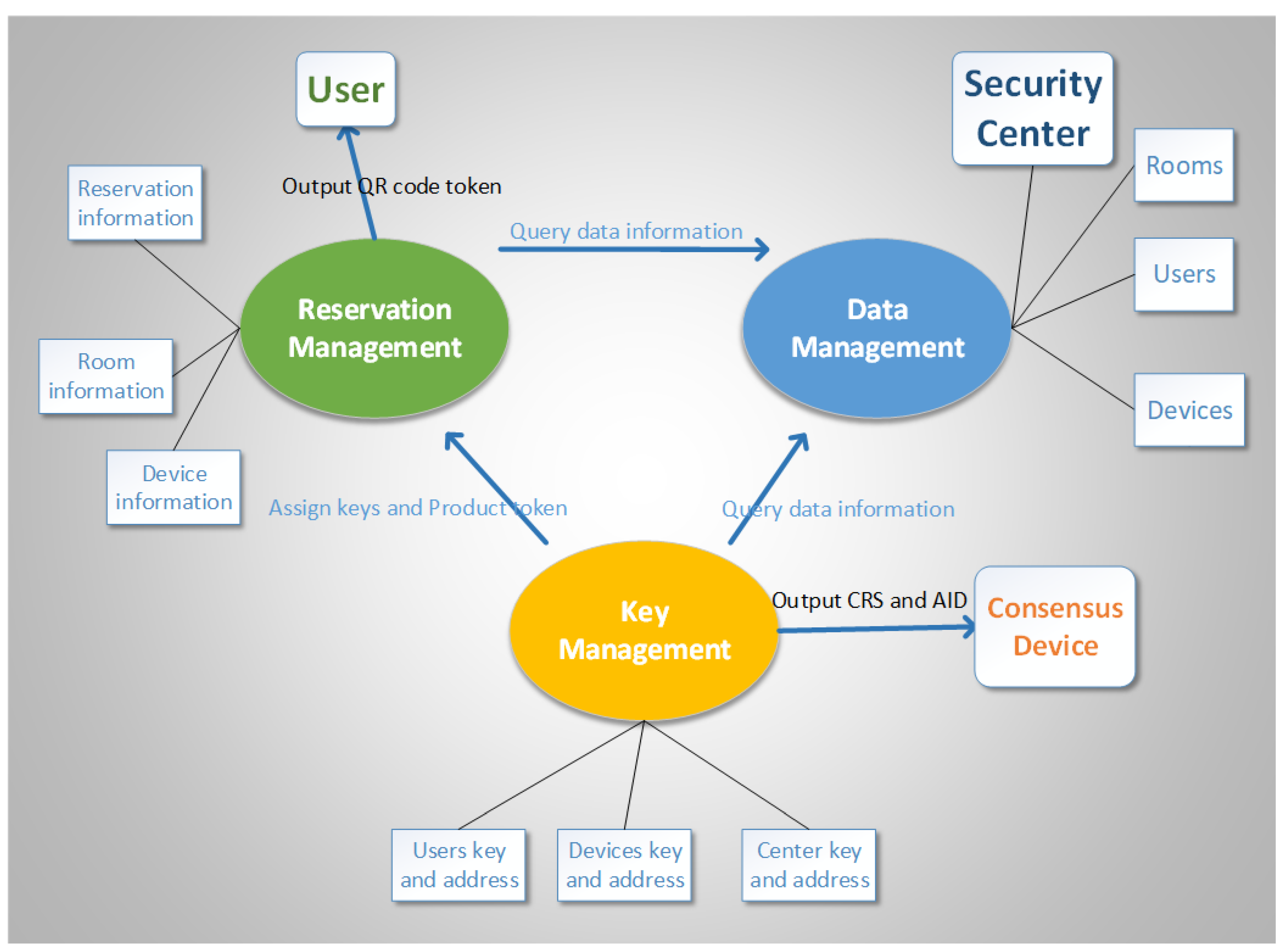
5. P2L Methodology
6. Evaluation
6.1. Implementation
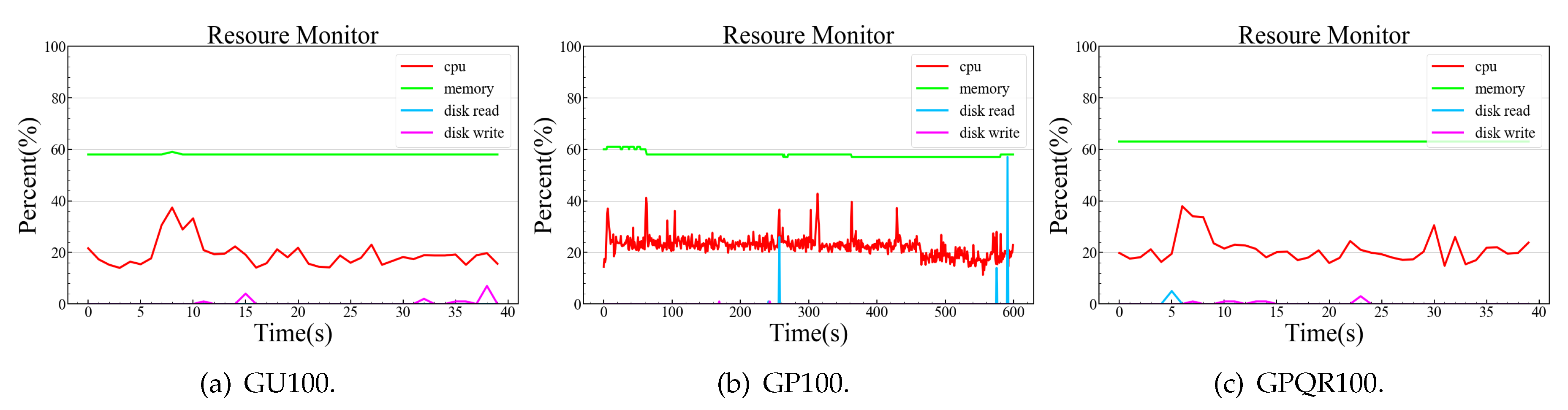
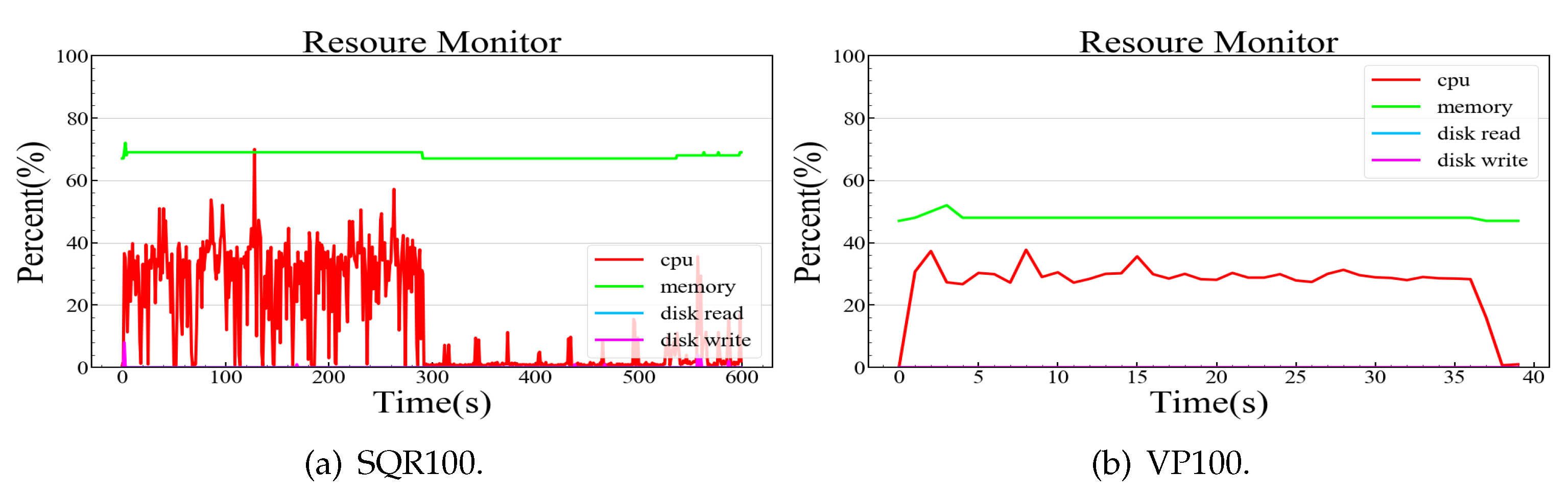
6.2. Complexity and Experiments
- QR codes should be quickly scanned by light intensity, proper distance sweeping. It will be necessary to design a reasonable operating environment specification for the scheme or to study the dynamic adjustment mechanism of smartphones.
- Sleep and activation controls of the ARM system can minimize their power consumption. A sonar sensor, or the addition of a button for manual activation of the system, is required to detect the users’ scanning motions.
- The scheme should provide user-friendly prompts and verification results. For example, the system could use a speaker to output prompt sounds or integrate a digital screen for interactions.
- In a heterogeneous IoT environment, there are many types of devices, and more device to device communication modes need to be integrated, such as Bluetooth and sound waves. The process of automatic identification between devices is also absent. Further research should focus on possible cracking methods to find vulnerabilities.
6.3. Comparsion and Analysis of Schemes
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge computing: Vision and challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Su, J.; Lin, F.; Zhou, X.; Lu, X. Steiner tree based optimal resource caching scheme in fog computing. Chin. Commun. 2015, 12, 161–168. [Google Scholar] [CrossRef]
- Lin, F.; Lü, X.; You, I.; Zhou, X. A novel utility based resource management scheme in vehicular social edge computing. IEEE Access 2018, 6, 66673–66684. [Google Scholar] [CrossRef]
- Al Ridhawi, I.; Otoum, S.; Aloqaily, M.; Jararweh, Y.; Baker, T. Providing secure and reliable communication for next generation networks in smart cities. Sustain. Cities Soc. 2020, 56, 102080. [Google Scholar] [CrossRef]
- Panetta, K. Gartner’s Top 10 Strategic Technology Trends for 2017. Available online: https://www.gartner.com/smarterwithgartner/gartners-top-10-technology-trends-2017/ (accessed on 1 February 2019).
- Review, M.T. 10 Breakthrough Technologies. Available online: https://www.technologyreview.com/lists/technologies/2018/ (accessed on 1 February 2019).
- Lin, F.; Zhou, Y.; Pau, G.; Collotta, M. Optimization-oriented resource allocation management for vehicular fog computing. IEEE Access 2018, 6, 69294–69303. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 1 February 2019).
- Zhang, Z.K.; Cho, M.C.Y.; Wang, C.W.; Hsu, C.W.; Chen, C.K.; Shieh, S. IoT security: Ongoing challenges and research opportunities. In Proceedings of the 2014 IEEE 7th international conference on service-oriented computing and applications, Matsue, Japan, 17–19 November 2014; pp. 230–234. [Google Scholar]
- Kim, H.; Lee, E.A. Authentication and Authorization for the Internet of Things. IT Prof. 2017, 19, 27–33. [Google Scholar] [CrossRef]
- Luk, M.; Perrig, A.; Whillock, B. Seven cardinal properties of sensor network broadcast authentication. In Proceedings of the fourth ACM workshop on Security of ad hoc and sensor networks, Alexandria, VA, USA, 30 October 2006; pp. 147–156. [Google Scholar]
- Yao, X.; Han, X.; Du, X.; Zhou, X. A lightweight multicast authentication mechanism for small scale IoT applications. IEEE Sens. J. 2013, 13, 3693–3701. [Google Scholar] [CrossRef]
- An, X.; Su, J.; Lü, X.; Lin, F. Hypergraph clustering model-based association analysis of DDOS attacks in fog computing intrusion detection system. EURASIP J. Wirel. Commun. Netw. 2018, 2018, 249. [Google Scholar] [CrossRef]
- An, X.; Zhou, X.; Lü, X.; Lin, F.; Yang, L. Sample selected extreme learning machine based intrusion detection in fog computing and MEC. Wirel. Commun. Mob. Comput. 2018, 2018. [Google Scholar] [CrossRef]
- Lin, F.; Zhou, Y.; An, X.; You, I.; Choo, K.K.R. Fair resource allocation in an intrusion-detection system for edge computing: Ensuring the security of Internet of Things devices. IEEE Consum. Electron. Mag. 2018, 7, 45–50. [Google Scholar] [CrossRef]
- Hui, H.; Zhou, C.; Xu, S.; Lin, F. A novel secure data transmission scheme in industrial internet of things. Chin. Commun. 2020, 17, 73–88. [Google Scholar]
- Courtois, N.T.; Grajek, M.; Naik, R. Optimizing SHA256 in Bitcoin Mining. In International Conference on Cryptography and Security Systems; Springer: Berlin/Heidelberg, Germany, 2014; pp. 131–144. [Google Scholar]
- Koblitz, N.; Menezes, A.; Vanstone, S. The state of elliptic curve cryptography. Des. Codes Cryptogr. 2000, 19, 173–193. [Google Scholar] [CrossRef]
- Jiang, X.; Liu, M.; Yang, C.; Liu, Y.; Wang, R. A Blockchain-Based Authentication Protocol for WLAN Mesh Security Access. CMC 2019, 58, 45–59. [Google Scholar] [CrossRef]
- Zhao, Y.; Zhang, S.; Yang, M.; He, P.; Wang, Q. Research on Architecture of Risk Assessment System Based on Block Chain. CMC 2019, 61, 677–686. [Google Scholar] [CrossRef]
- Li, C.; Xu, G.; Chen, Y.; Ahmad, H.; Li, J. A New Anti-Quantum Proxy Blind Signature for Blockchain-Enabled Internet of Things. CMC 2019, 61, 711–726. [Google Scholar] [CrossRef]
- Wang, B.; Kong, W.; Guan, H.; Xiong, N.N. Air Quality Forecasting Based on Gated Recurrent Long Short Term Memory Model in Internet of Things. IEEE Access 2019, 7, 69524–69534. [Google Scholar] [CrossRef]
- Wang, T.; Bhuiyan, M.Z.A.; Wang, G.; Qi, L.; Wu, J.; Hayajneh, T. Preserving Balance between Privacy and Data Integrity in Edge-Assisted Internet of Things. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Tseng, L.; Wong, L.; Otoum, S.; Aloqaily, M.; Othman, J.B. Blockchain for managing heterogeneous internet of things: A perspective architecture. IEEE Netw. 2020, 34, 16–23. [Google Scholar] [CrossRef]
- Goldwasser, S.; Micali, S.; Rackoff, C. The knowledge complexity of interactive proof systems. SIAM J. Comput. 1989, 18, 186–208. [Google Scholar] [CrossRef]
- Gervais, A.; Karame, G.O.; Wüst, K.; Glykantzis, V.; Ritzdorf, H.; Capkun, S. On the security and performance of proof of work blockchains. In Proceedings of the 2016 ACM SIGSAC conference on computer and communications security, Vienna, Austria, 24–28 October 2016; pp. 3–16. [Google Scholar]
- Gebotys, C.H.; White, B.A.; Mateos, E. Preaveraging and carry propagate approaches to side-channel analysis of HMAC-SHA256. ACM Trans. Embedded Comput. Syst. 2016, 15, 4. [Google Scholar] [CrossRef]
- Gennaro, R.; Gentry, C.; Parno, B.; Raykova, M. Quadratic span programs and succinct NIZKs without PCPs. In Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2013; pp. 626–645. [Google Scholar]
- Ben-Sasson, E.; Chiesa, A.; Tromer, E.; Virza, M. Scalable zero knowledge via cycles of elliptic curves. Algorithmica 2017, 79, 1102–1160. [Google Scholar] [CrossRef]
- Zcash. A Privacy-Protecting, Digital Currency. Available online: https://z.cash/technology/ (accessed on 1 February 2019).
- Han, D.; Lu, Y.; Du, X.; Gan, J. Offline Authentication Scheme Based on Blockchain Technology for Smart Lock. In Proceedings of the 2nd International Conference on Telecommunications and Communication Engineering; Association for Computing Machinery, New York, NY, USA, 28–30 November 2018; pp. 384–390. [Google Scholar] [CrossRef]

| Symbol | Notation |
|---|---|
| CRS | Common reference strings set |
| SP | Service proof |
| RP | Request proof |
| NPs | One-time associated multitasks set based on nondeterministic polynomial time problems |
| AID | Anonymous IDs associate multiple addresses and key pairs |
| E(x) | Homomorphic encryption algorithms |
| P(x) | Polynomials |
| zk-SNARKs | Zero-knowledge succinct non-interactive arguments of knowledge algorithms |
| R1CS | Rank-1 constraint system is composed of a set of mathematical form of Verification Rules like is a triple vector |
| QAP | Quadratic arithmetic programs |
| QSP | Quadratic span programs |
| CBS | Contents of the behavior string |
| H | Nyberg’s fast one-way accumulate function |
| A | Accumulated value |
| HCBS | Hash contents of the behavior string |
| HPC | Hash proof of work (PoW) contents |
| QRP | Quick response (QR) code picture |
| Simulation Role | Device | Specification | Case |
|---|---|---|---|
| Security center and Provider | PC | 2.6 G(MAX 3.5) Intel i7-6700HQ 4C/8T 16 G DDR3 RAM | GU100 GP100 GPQR100 |
| Verifier | ARM | 1.6 G ARM Cortex-A7 4C 1G DDR3 RAM AD703_G2J1 Scanner | SQR100 VP100 |
| Case | Device | Total Time (s) | Average Time (s) |
|---|---|---|---|
| GU100 | PC | 5.568 | 0.057 |
| GP100 | PC | 514.027 | 5.14 |
| GPQR100 | PC | 6.852 | 0.069 |
| SQR100 | ARM | 200–500 | 2–5 |
| VP100 | ARM | 33.851 | 0.339 |
| VP100 | PC | 3.55 | 0.036 |
| Scheme | Resistance Against Node Compromise | Computation Overhead | Communication Overhead | Advantage |
|---|---|---|---|---|
| OAuth | High | <50 ms | >2 K | Remote center, fine-grained policy control. |
| DB+HMAC | Low | <50 ms | >1 K | Centralized management, the MAC address of the device is used as a unique ID. |
| One-Time Signature | Middle | 268 ms | >1 K | Lightweight IBE-ECC algorithm, OTP is generated in the cloud. |
| Public-key based signature | High | >1 s | >1 K | Mature PKI system and CA center, CA unified manage certificate. |
| One-way accumulator | Middle | <32 ms | <132 B | Lightweight to adapt resource constraints. |
| Verification Phase of OTMP-P2L | High | <400 ms | 593 B | One-time multitasking and local security center. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Han, D.; Du, X.; Lu, Y. Trustworthiness and a Zero Leakage OTMP-P2L Scheme Based on NP Problems for Edge Security Access. Sensors 2020, 20, 2231. https://doi.org/10.3390/s20082231
Han D, Du X, Lu Y. Trustworthiness and a Zero Leakage OTMP-P2L Scheme Based on NP Problems for Edge Security Access. Sensors. 2020; 20(8):2231. https://doi.org/10.3390/s20082231
Chicago/Turabian StyleHan, Daoqi, Xiaofeng Du, and Yueming Lu. 2020. "Trustworthiness and a Zero Leakage OTMP-P2L Scheme Based on NP Problems for Edge Security Access" Sensors 20, no. 8: 2231. https://doi.org/10.3390/s20082231
APA StyleHan, D., Du, X., & Lu, Y. (2020). Trustworthiness and a Zero Leakage OTMP-P2L Scheme Based on NP Problems for Edge Security Access. Sensors, 20(8), 2231. https://doi.org/10.3390/s20082231





