Obfuscation of Malicious Behaviors for Thwarting Masquerade Detection Systems Based on Locality Features
Abstract
1. Introduction
2. Background
3. Design Principles
3.1. Motivation and Objectives
3.2. Experimental Research
- The selected classifiers were applied upon the reference dataset to set up a baseline of accuracy measurements.
- The evasion tactics introduced in this research were applied on the raw observations (e.g., system call sequences, file navigation patterns, log entries, and so on) to generate adversarial datasets with the same features presented in the reference repository.
- The classification algorithms were applied upon the adversarial datasets and the variation on accuracy results was measured to cross-validate the masquerading effectiveness achieved by the obfuscation methods. To this end, different calibrations were exercised in the generation of the adversarial samples.
3.3. Reference Dataset
3.4. Machine-Learning Base Classifiers
4. Obfuscation of Locality-Based Evidences
- As indicated by Tapiador et al. [35], and regardless of the level of obfuscation of malicious actions, they will always present a small invariant trait that shall allow to recognize their true malicious nature.
- The adversary knows the detection method and all the relevant information about its operation. However, it is unaware of the reference datasets considered for training the classifiers and outlier detection capabilities inherent in modern IDS.
- The adversary has the capability of conducting padding/noise activities within the time interval in which each observation is defined. They will impact on the values calculated for the behavioral metrics that model the legitimate usage pattern.
- The detection system applies ideal models of legitimate and malicious system usage. Therefore, neither their poisoning, nor improvement is possible [35].
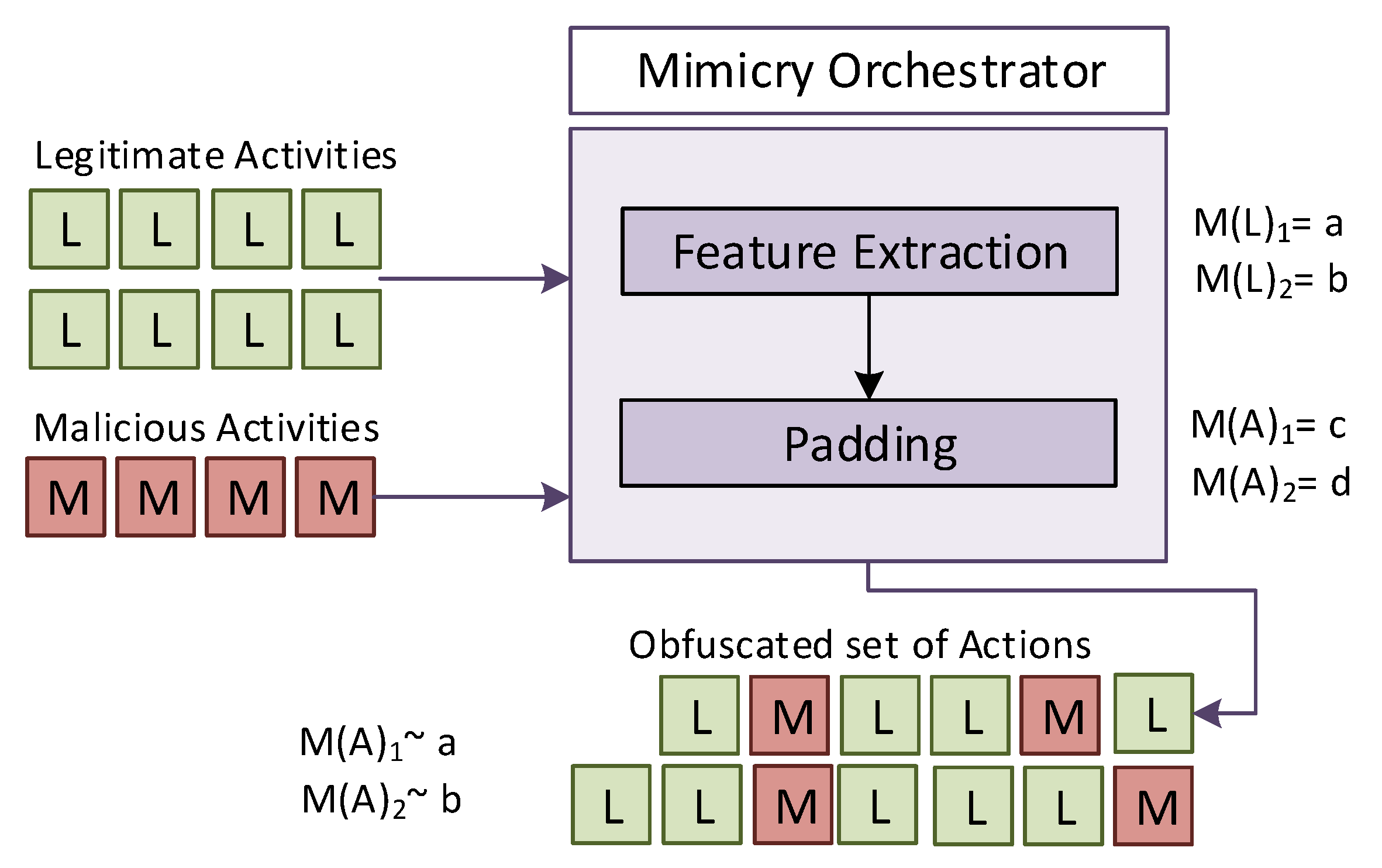
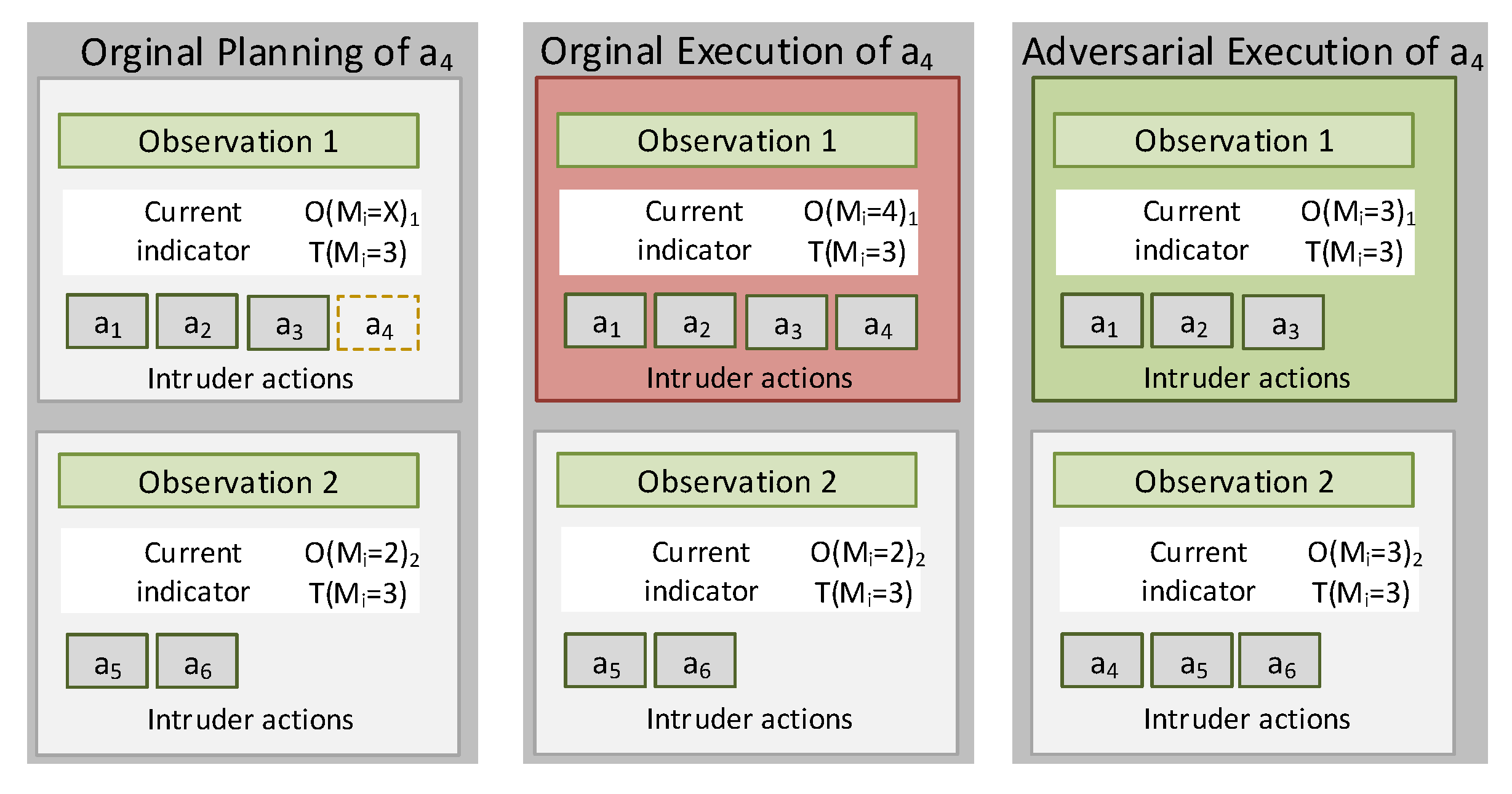
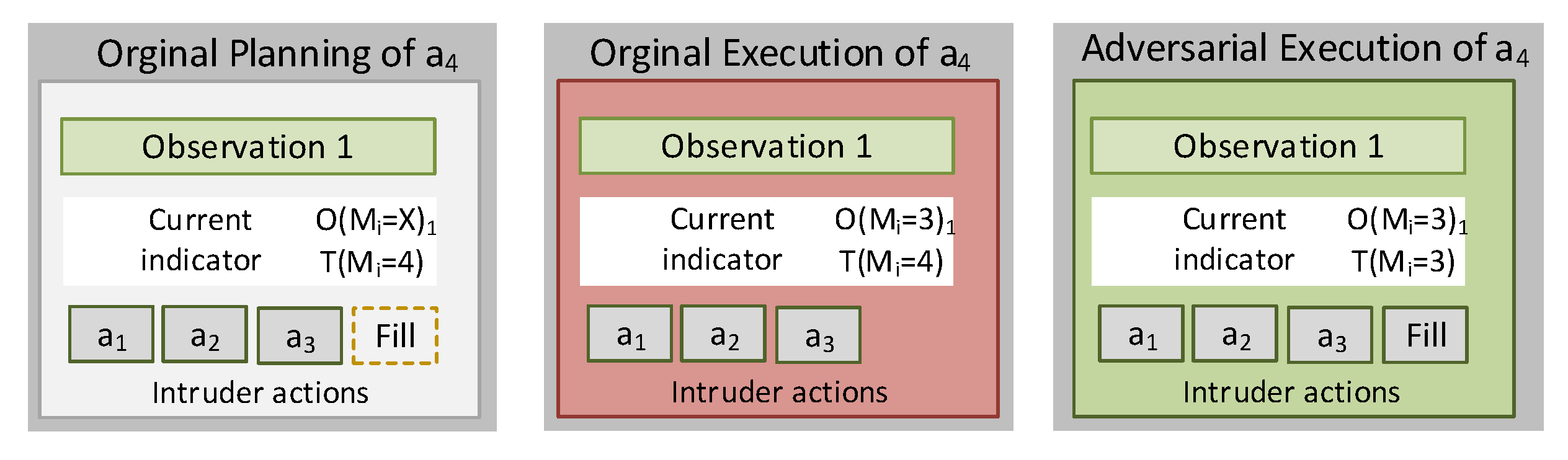
4.1. Locality-Based Mimicry by Action Pruning
4.2. Locality-Based Mimicry by Noise Generation
4.3. Adversarial Model and Thresholds
- The m size of the reference dataset is small, since it is not possible to pretend that the adversary spends long periods of inactivity capturing information without being discovered. To avoid this, actions like privilege gain, hiding (bulletproof), or vulnerability exploitation may be conducted within the victim’s system. Consequently, any implemented modeling tool based on machine learning should present sufficient effectiveness when dealing with small training datasets.
- The machine learning enablers behind the modeling must be agile enough to allow the valuation of the observations in real time. From the models they built, it must be possible to specify a set of upper/lower thresholds for guiding the actions inherent in the obfuscation process.
5. Experimental Results
5.1. Baseline Scenario: WUIL Dataset
5.2. Locality-Based Scenario: WUIL dataset with Action Pruning
5.3. Locality-Based Scenario: WUIL Dataset with Noise Generation
6. Discussion
- There are no preliminary studies about the feasibility of locality-based masquerade detectors concerning the specific adversarial tactics able to evade them.
- There is no functional standard adopted by the research community for assessing locality-based classifiers. Although, to the best of these authors knowledge, WUIL (Windows-Users and Intruder simulations) is one of the most complete and well documented collections, there are no preliminary studies on WUIL with focus on evasion.
- There are no standardized measures of performance (MOPs) and measures of effectiveness (MOEs) concerning mimicry-based obfuscation tactics.
- The proposal introduces pioneering adversarial methods against locality-based analytics.
- Unlike most of the state-of-the-art contributions, the proposed techniques can be applied at run time. Note that most of the previous, related publications already conducted static modifications on predefined datasets. The introduced tactics are able to step-wise guide the insider when operating in the compromised environment, which make them more applicable in real uses cases.
- Locality-based mimicry by action pruning prevents the insider from conducting highly detectable actions by suggesting their avoidance or delay to the beginning of a new IDS observation gathering cycle.
- Locality-based mimicry by noise generation guides the insider towards conducting locality-based padding actions in order to resemble the targeted legitimate usage model.
- The effectiveness of the evasion tactics was compared with the results presented in the original WUIL [38] publication, which includes well-known classification algorithms like SVM, REPTree, Bagging, or Naive Bayes. This sets the grounds for further research, as well as facilitates the definition of a benchmark for future related research actions.
- As presented in Table 3, when the number of legitimate preliminary observations observed by the attacker is significant, the accuracy of the detection methods decreases considerably. For example, the 94.24% accuracy of Naive Bayes was reduced to 75.35% by adversarial action pruning, and to 47.53% by adversarial noise generation.
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- ENISA. Threat Landscape Report 2018. Available online: https://www.enisa.europa.eu/publications (accessed on 18 January 2020).
- General Data Protection Regulation (GDPR). Available online: https://gdpr-info.eu (accessed on 14 March 2020).
- Salem, M.B.; Hershkop, S.; Stolfo, S.J. A survey of insider attack detection research. In Insider Attack and Cyber Security; Springer: Berlin/Heidelberg, Germany, 2008; pp. 69–90. [Google Scholar]
- Voris, J.; Jermyn, J.; Boggs, N.; Stolfo, S. Fox in the trap: Thwarting masqueraders via automated decoy document deployment. In Proceedings of the Eighth European Workshop on System Security, Bordeaux, France, 21 April 2015; ACM: New York, NY, USA, 2015; p. 3. [Google Scholar]
- Wang, C.; Lu, Z. Cyber deception: Overview and the road ahead. IEEE Secur. Privacy 2018, 16, 80–85. [Google Scholar] [CrossRef]
- Maestre Vidal, J.; Orozco, A.; Villalba, L. Online masquerade detection resistant to mimicry. Expert Syst. Appl. 2016, 61, 162–180. [Google Scholar] [CrossRef]
- Balozian, P.; Leidner, D.; Warkentin, M. Managers’ and employees’ differing responses to security approaches. J. Comput. Inf. Syst. 2019, 59, 197–210. [Google Scholar] [CrossRef]
- Alzubaidi, A.; Kalita, J. Authentication of smartphone users using behavioral biometrics. IEEE Commun. Surv. Tutorials 2016, 18, 1998–2026. [Google Scholar] [CrossRef]
- Maestre Vidal, J.; Sotelo Monge, M. Framework for Anticipatory Self-Protective 5G Environments. In Proceedings of the 14th International Conference on Availability, Reliability and Security, Canterbury, UK, 26–29 August 2019; ACM: New York, NY, USA, 2019; pp. 1–6. [Google Scholar]
- Biggio, B.; Roli, F. Wild patterns: Ten years after the rise of adversarial machine learning. Pattern Recogn. 2018, 48, 317–331. [Google Scholar] [CrossRef]
- Camiña, J.B.; Medina-Pérez, M.A.; Monroy, R.; Loyola-González, O.; Villanueva, L.A.P.; Gurrola, L.C.G. Bagging-RandomMiner: A one-class classifier for file access-based masquerade detection. Mach. Vision Appl. 2019, 30, 959–974. [Google Scholar] [CrossRef]
- Maestre Vidal, J.; Meja Castro, J.; Sandoval Orozco, A.; García Villalba, L. Evolutions of evasion techniques aigainst network intrusion detection systems. In Proceedings of the 6th International conference on Information Technology, Amman, Jordan, 8–10 May 2013; ACM: New York, NY, USA, 2013. [Google Scholar]
- Schonlau, M.; DuMouchel, W.; Ju, W.H.; Karr, A.F.; Theusan, M.; Vardi, Y. Computer intrusion: Detecting masquerades. Stat. Sci. 2001, 16, 58–74. [Google Scholar]
- Wang, K.; Stolfo, S. One-class training for masquerade detection. In Proceedings of the 3rd IEEE Conference Data Mining Workshop on Data Mining for Computer Security, Melbourne, FL, USA, 19–22 November 2003; Springer: Berlin/Heidelberg, Germany, 2003. [Google Scholar]
- Liu, L.; De Vel, O.; Han, Q.L.; Zhang, J.; Xiang, Y. Detecting and preventing cyber insider threats: A survey. IEEE Commun. Surv. Tutorials 2018, 20, 1397–1417. [Google Scholar] [CrossRef]
- Homoliak, I.; Toffalini, F.; Guarnizo, J.; Elovici, Y.; Ochoa, M. Insight into insiders and it: A survey of insider threat taxonomies, analysis, modeling, and countermeasures. ACM Comput. Surv. (CSUR) 2019, 52, 30. [Google Scholar] [CrossRef]
- Peng, J.; Choo, K.K.R.; Ashman, H. User profiling in intrusion detection: A review. J. Network Comput. Appl. 2016, 72, 14–27. [Google Scholar] [CrossRef]
- Shen, C.; Zhang, Y.; Guan, X.; Maxion, R.A. Performance analysis of touch-interaction behavior for active smartphone authentication. IEEE Trans. Inf. Forensics Secur. 2015, 11, 498–513. [Google Scholar] [CrossRef]
- Fadolalkarim, D.; Bertino, E. A-PANDDE: Advanced Provenance-based ANomaly Detection of Data Exfiltration. Comput. Secur. 2019, 84, 276–287. [Google Scholar] [CrossRef]
- Salem, M.B.; Stolfo, S.J. Modeling User Search Behavior for Masquerade Detection. In Recent Advances in Intrusion Detection; Springer: Berlin/Heidelberg, Germany, 2011; pp. 181–200. [Google Scholar]
- Happa, J. Insider-threat detection using gaussian mixture models and sensitivity profiles. Comput. Secur. 2018, 77, 838–859. [Google Scholar]
- Yuan, F.; Cao, Y.; Shang, Y.; Liu, Y.; Tan, J.; Fang, B. Insider threat detection with deep neural network. In International Conference on Computational Science; Springer: Berlin/Heidelberg, Germany, 2018; pp. 43–54. [Google Scholar]
- Sallam, A.; Bertino, E.; Hussain, S.R.; Landers, D.; Lefler, R.M.; Steiner, D. DBSAFE—An anomaly detection system to protect databases from exfiltration attempts. IEEE Syst. J. 2015, 11, 483–493. [Google Scholar] [CrossRef]
- Roman, R.; Lopez, J.; Mambo, M. Mobile edge computing, fog et al.: A survey and analysis of security threats and challenges. Future Gener. Comput. Syst. 2018, 78, 680–698. [Google Scholar] [CrossRef]
- Maestre Vidal, J.; Sotelo Monge, M.; Martinez Monterrubio, M. EsPADA: Enhanced Payload Analyzer for malware Detection robust against Adversarial threats. Future Gener. Comput. Syst. 2020, 104, 159–173. [Google Scholar] [CrossRef]
- Maestre Vidal, J.; Sotelo Monge, M. Adversarial Communication Networks Modeling for Intrusion Detection Strengthened against Mimicry. In Proceedings of the 14th International Conference on Availability, Reliability and Security, Canterbury, UK, 26–29 August 2019; ACM: New York, NY, USA, 2019; pp. 1–6. [Google Scholar]
- Sotelo Monge, M.; Maestre Vidal, J. Entropy-based economic denial of sustainability detection. Entropy 2019, 19, 649. [Google Scholar] [CrossRef]
- Sotelo Monge, M.; Maestre Vidal, J.; Martinez Pérez, G. Detection of economic denial of sustainability (EDoS) threats in self-organizing networks. Comput. Commun. 2019, 145, 284–308. [Google Scholar] [CrossRef]
- Sohal, A.S.; Sandhu, R.; Sood, S.K.; Chang, V. A cybersecurity framework to identify malicious edge device in fog computing and cloud-of-things environments. Comput. Secur. 2018, 74, 340–354. [Google Scholar] [CrossRef]
- Sotelo Monge, M.; Herranz Gonzalez, A.; Lorenzo Fernandez, B.; Maestre Vidal, D.; Rius Garcia, G.; Maestre Vidal, J. Traffic-flow analysis for source-side DDoS recognition on 5G environments. J. Network Comput. Appl. 2019, 136, 114–131. [Google Scholar] [CrossRef]
- Kim, D.; Solomon, M.G. Fundamentals of Information Systems Security; Jones & Bartlett Learning: Burlington, MA, USA, 2016. [Google Scholar]
- Maloof, M.A.; Stephens, G.D. Elicit: A system for detecting insiders who violate need-to-know. In Proceedings of the 10th International Workshop on Recent Advances in Intrusion Detection, Gold Goast, QLD, Australia, 5–7 September 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 146–166. [Google Scholar]
- Ackerman, D.; Mehrpouyan, H. Modeling human behavior to anticipate insider attacks via system dynamics. In Proceedings of the Symposium on Theory of Modeling & Simulation, Pasadena, CA, USA, 3–6 April 2016. [Google Scholar]
- Giffin, J.T.; Jha, S.; Miller, B.P. Automated discovery of mimicry attacks. In Proceedings of the 9th International Workshop on Recent Advances in Intrusion Detection, Hamburg, Germany, 20–22 September 2006; Springer: Berlin/Heidelberg, Germany, 2006; pp. 41–60. [Google Scholar]
- Tapiador, J.E.; Clark, J.A. Masquerade mimicry attack detection: A randomised approach. Comput. Secur. 2011, 30, 297–310. [Google Scholar] [CrossRef]
- Maestre Vidal, J.; Sotelo Monge, M. A novel Self-Organizing Network solution towards Crypto-ransomware Mitigation. In Proceedings of the 13th International Conference on Availability, Reliability and Security, Hamburg, Germany, 27–30 August 2018; ACM: New York, NY, USA, 2018; pp. 1–6. [Google Scholar]
- Camina, J.B.; Monroy, R.; Trejo, L.A.; Medina-Pérez, M.A. Temporal and spatial locality: An abstraction for masquerade detection. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2036–2051. [Google Scholar] [CrossRef]
- Camiña, J.B.; Hernández-Gracidas, C.; Monroy, R.; Trejo, L. The Windows-Users and-Intruder simulations Logs dataset (WUIL): An experimental framework for masquerade detection mechanisms. Expert Syst. Appl. 2014, 41, 919–930. [Google Scholar] [CrossRef]
- Breiman, L. Random forests. Mach. Learn. 2001, 45, 5–32. [Google Scholar] [CrossRef]
- Safavian, S.R.; Landgrebe, D. A survey of decision tree classifier methodology. IEEE Trans. Syst. Man Cybern. 1991, 21, 660–674. [Google Scholar] [CrossRef]
- Salzberg, S.L. C4. 5: Programs for machine learning by j. ross quinlan. morgan kaufmann publishers, inc., 1993. Mach. Learn. 1994, 16, 235–240. [Google Scholar] [CrossRef]
- Breiman, L. Bagging predictors. Mach. Learn. 1996, 24, 123–140. [Google Scholar] [CrossRef]
- John, G.H.; Langley, P. Estimating continuous distributions in Bayesian classifiers. In Proceedings of the Eleventh conference on Uncertainty in artificial intelligence, Montreal, QC, Canada, 18–20 August 1995; Morgan Kaufmann Publishers Inc.: Burlington, MA, USA, 1995; pp. 338–345. [Google Scholar]
- Byun, H.; Lee, S.W. Applications of support vector machines for pattern recognition: A survey. In International Workshop on Support Vector Machines; Springer: Berlin/Heidelberg, Germany, 2002; pp. 213–236. [Google Scholar]
- Wang, K.; Parekh, J.J.; Stolfo, S.J. Anagram: A content anomaly detector resistant to mimicry attack. In International Workshop on Recent Advances in Intrusion Detection; Springer: Berlin/Heidelberg, Germany, 2006; pp. 226–248. [Google Scholar]
- Goel, J.N.; Mehtre, B. Vulnerability assessment & penetration testing as a cyber defence technology. Procedia Comput. Sci. 2015, 57, 710–715. [Google Scholar]
- Wang, P.; Li, Y.; Reddy, C.K. Machine learning for survival analysis: A survey. ACM Comput. Surv. (CSUR) 2019, 51, 110. [Google Scholar] [CrossRef]
- Quinlan, J.R. Induction of decision trees. Mach. Learn. 1986, 1, 81–106. [Google Scholar] [CrossRef]
- Quinlan, J.R. Learning efficient classification procedures and their application to chess end games. In Machine Learning; Springer: Berlin/Heidelberg, Germany, 1983; pp. 463–482. [Google Scholar]
- Breiman, L.; Friedman, J.; Olshen, R.; Stone, C. Classification and regression trees. Wadsworth Int. Group 1984, 37, 237–251. [Google Scholar]
- Luštrek, M.; Gams, M.; Martinčić-Ipšić, S. What makes classification trees comprehensible? Exp. Syst. Appl. 2016, 62, 333–346. [Google Scholar]
- Buczak, A.L.; Guven, E. A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Commun. Surv. Tutor. 2015, 18, 1153–1176. [Google Scholar] [CrossRef]
- Deng, H.; Runger, G.; Tuv, E. Bias of importance measures for multi-valued attributes and solutions. In International Conference on Artificial Neural Networks; Springer: Berlin/Heidelberg, Germany, 2011; pp. 293–300. [Google Scholar]
- WEKA. Available online: http://www.cs.waikato.ac.nz/ml/weka (accessed on 11 February 2020).
| Dataset | Random Forest | SVM | REPTree | Bagging | C4.5 | Naïve Bayes |
|---|---|---|---|---|---|---|
| Original | 98.22 | 97.76 | 97.95 | 98.11 | 97.91 | 94.24 |
| NO Obs. | Random Forest | SVM | REPTree | Bagging | C4.5 | Naïve Bayes |
|---|---|---|---|---|---|---|
| 10 | 99.17 | 98.76 | 98.82 | 99.02 | 98.83 | 97.92 |
| 100 | 99.12 | 98.75 | 98.80 | 98.91 | 98.81 | 97.22 |
| 500 | 98.13 | 96.85 | 97.06 | 97.64 | 97.42 | 77.95 |
| 750 | 97.27 | 94.59 | 95.70 | 96.5 | 96.32 | 76.57 |
| 1000 | 96.23 | 92.17 | 93.67 | 95.29 | 94.13 | 77.37 |
| 1500 | 92.99 | 88.13 | 89.23 | 91.06 | 89.58 | 74.78 |
| 2000 | 91.40 | 87.20 | 88.43 | 90.29 | 88.73 | 82.34 |
| 2500 | 90.87 | 85.26 | 86.71 | 88.61 | 87.98 | 79.23 |
| 3000 | 89.05 | 82.45 | 84.63 | 86.64 | 86.09 | 75.82 |
| 3500 | 85.68 | 78.44 | 81.11 | 82.90 | 81.65 | 71.42 |
| 4000 | 84.81 | 78.41 | 80.17 | 81.81 | 80.51 | 75.80 |
| 6000 | 85.26 | 78.81 | 80.45 | 83.34 | 82.09 | 75.35 |
| NO Obs. | Random Forest | SVM | REPTree | Bagging | C4.5 | Naïve Bayes |
|---|---|---|---|---|---|---|
| 10 | 98.23 | 97.69 | 97.91 | 98.12 | 97.88 | 94.16 |
| 100 | 98.68 | 97.95 | 98.25 | 98.45 | 98.22 | 97.84 |
| 500 | 97.56 | 94.28 | 96.69 | 96.89 | 96.86 | 64.30 |
| 750 | 96.34 | 90.11 | 94.57 | 95.50 | 94.78 | 58.57 |
| 1000 | 94.73 | 84.12 | 92.18 | 93.25 | 92.24 | 58.44 |
| 1500 | 89.14 | 66.42 | 83.65 | 86.23 | 84.52 | 60.42 |
| 2000 | 83.91 | 68.71 | 76.47 | 80.22 | 77.61 | 67.18 |
| 2500 | 80.82 | 63.41 | 72.19 | 76.34 | 74.76 | 62.85 |
| 3000 | 77.15 | 59.13 | 67.52 | 71.97 | 69.06 | 56.35 |
| 3500 | 70.28 | 50.57 | 58.02 | 64.83 | 60.91 | 47.35 |
| 4000 | 70.31 | 51.95 | 58.58 | 64.64 | 58.75 | 47.48 |
| 6000 | 70.08 | 51.78 | 57.84 | 63.28 | 60.51 | 47.53 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Maestre Vidal, J.; Sotelo Monge, M.A. Obfuscation of Malicious Behaviors for Thwarting Masquerade Detection Systems Based on Locality Features. Sensors 2020, 20, 2084. https://doi.org/10.3390/s20072084
Maestre Vidal J, Sotelo Monge MA. Obfuscation of Malicious Behaviors for Thwarting Masquerade Detection Systems Based on Locality Features. Sensors. 2020; 20(7):2084. https://doi.org/10.3390/s20072084
Chicago/Turabian StyleMaestre Vidal, Jorge, and Marco Antonio Sotelo Monge. 2020. "Obfuscation of Malicious Behaviors for Thwarting Masquerade Detection Systems Based on Locality Features" Sensors 20, no. 7: 2084. https://doi.org/10.3390/s20072084
APA StyleMaestre Vidal, J., & Sotelo Monge, M. A. (2020). Obfuscation of Malicious Behaviors for Thwarting Masquerade Detection Systems Based on Locality Features. Sensors, 20(7), 2084. https://doi.org/10.3390/s20072084






