ECCM Schemes against Deception Jamming Using OFDM Radar with Low Global PAPR
Abstract
1. Introduction
- (1)
- We present the signal models based on a monostatic OFDM radar with the ability of pulse diversity in the presence of the different types of deception jamming. This work is utilized to pave the way to the ECCM scheme for improving the local signal-to-interference-and-noise ratio (SINR) via designing the proper waveform.
- (2)
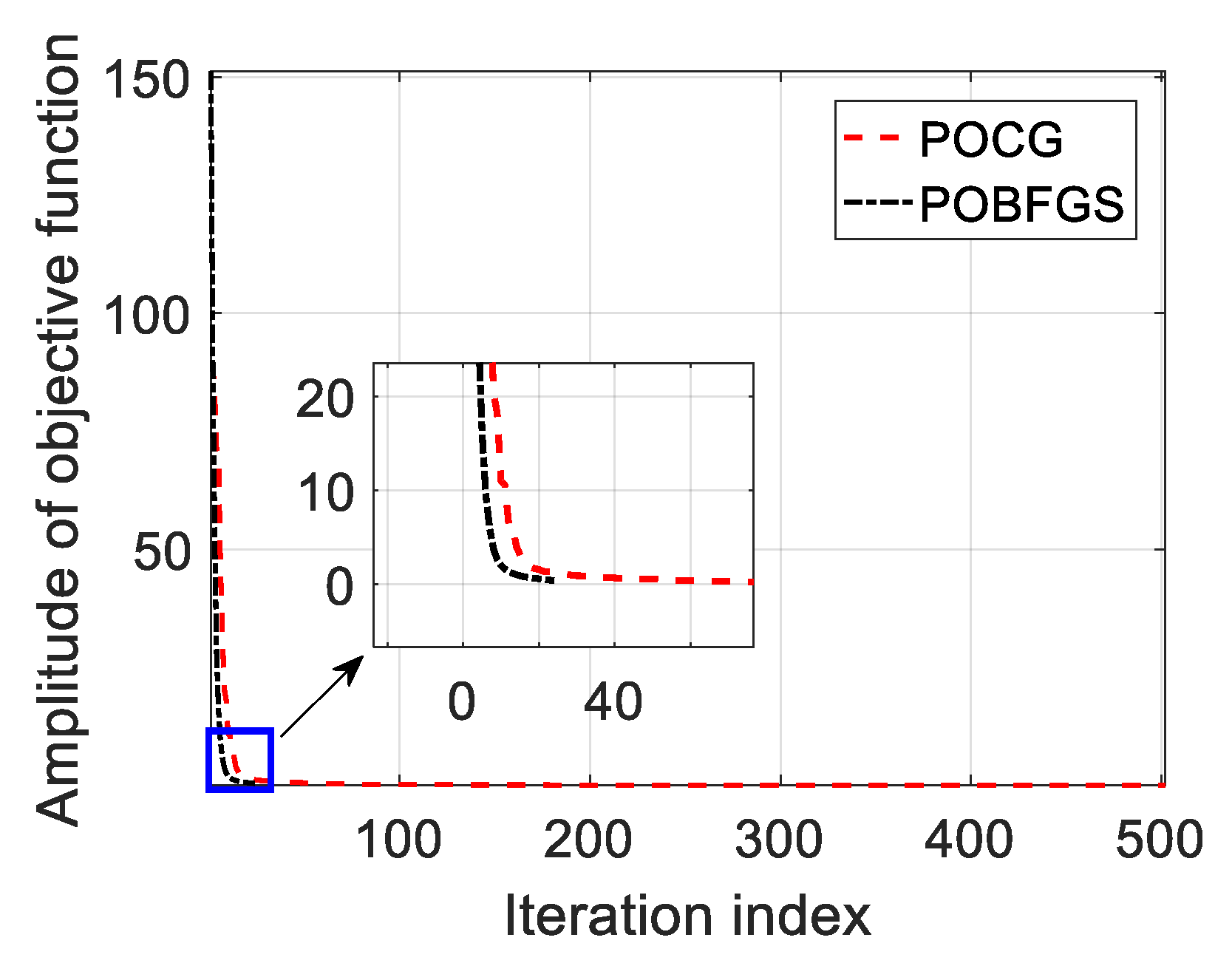
- A method of optimizing the initial phases is proposed to resist the VDJ. An optimization problem aiming at minimizing the energy near the false targets by devising the differences of the initial phases between the radar signal and the jamming signal repeated by jammer is formulated under a constant modulus constraint. Hence in order to force the components of the variable vector to be the same, we devise a method called phase-only BFGS (POBFGS) to obtain the phase vector of the optimization variable. It has some outstanding advantages over the existing methods in the performance of the algorithmic convergence.
- (3)
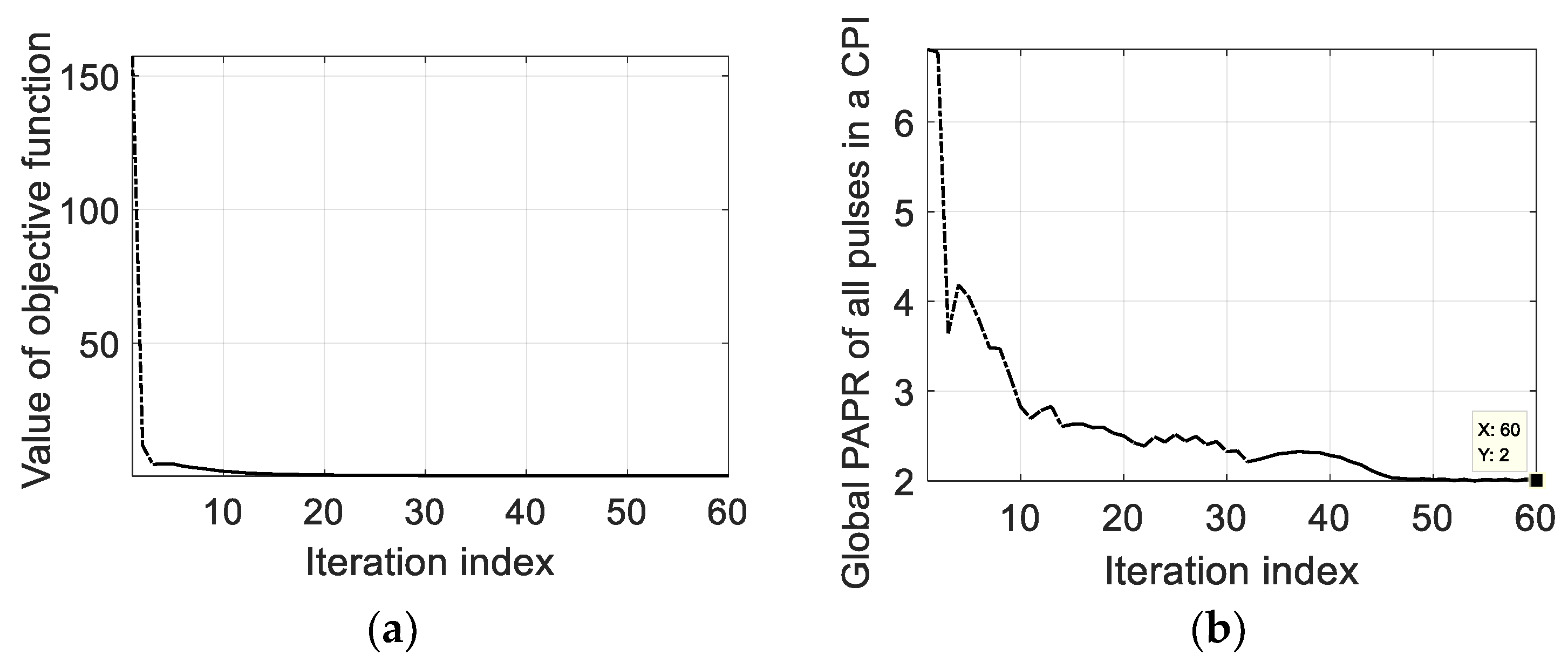
- An ECCM scheme of optimizing the OFDM waveform is proposed to suppress the RDJ and the JRVDJ. In these two cases, two optimization problems are, respectively, formulated for the first time, and both of them comply with the criterion of minimizing the jamming energy near the false targets by designing the phase codes of the subcarriers (PCSs) of the OFDM pulses. Fortunately, they boil down to the same kind of non-convex optimization model. If the PCSs are changed, the PAPR may vary. The proper PAPR could help the transmitted signal to avoid suffering from severe nonlinear distortion. Therefore, a new concept of global PAPR is defined as the PAPR with regard to all OFDM pulses to be optimized, and controlling the global PAPR works as an indispensable constraint in the constructed mathematical model. Aiming at managing to get the optimal waveform, an algorithm called the phase-only alternating direction method of multipliers (POADMM) is devised to solve the formulated optimization problem in the phase domain.
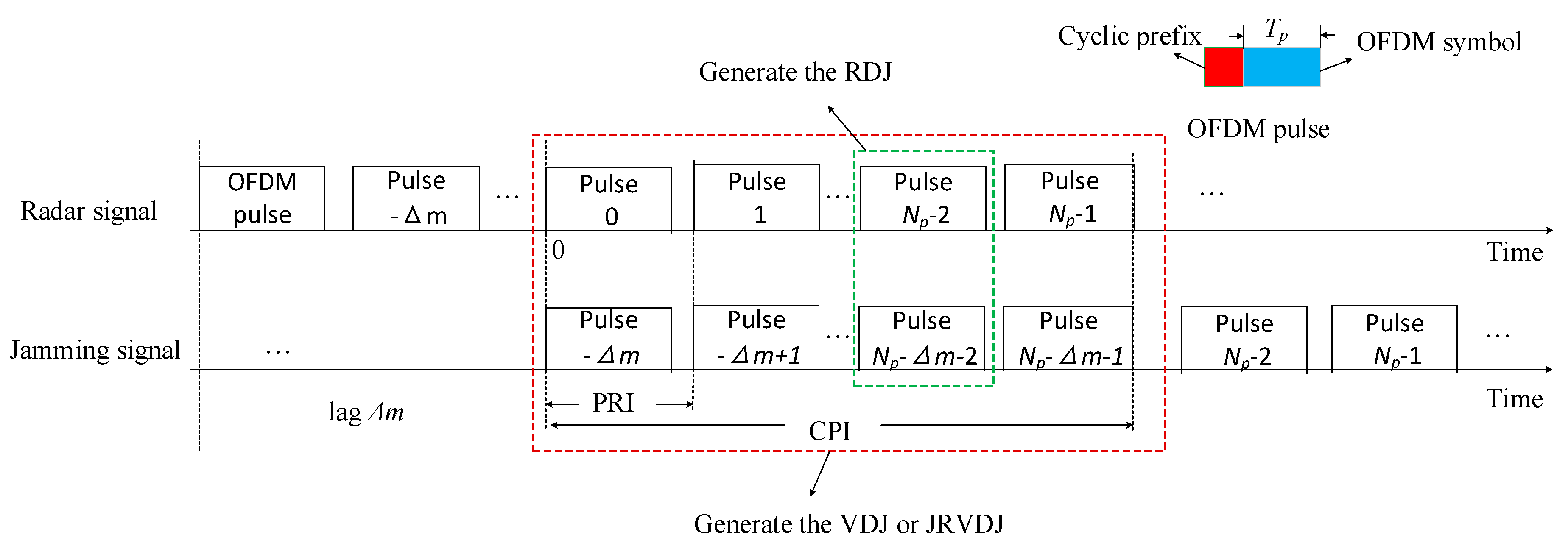
2. Signal Model Under Deception Jamming
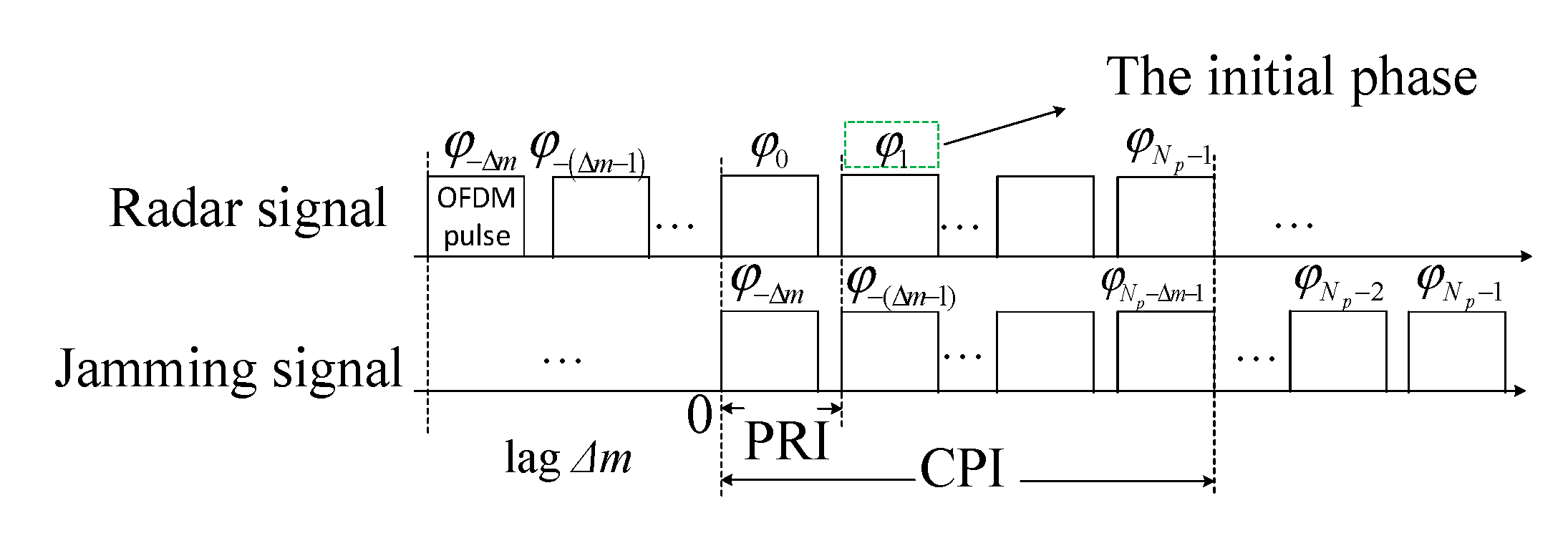
2.1. Echo Signal Model in the Presence of VDJ
2.2. Echo Signal Model in the Presence of RDJ
2.3. Echo Signal Model in the Presence of the Joint Range-Velocity Deception Jamming
3. Proposed ECCM Schemes
3.1. Scheme of Suppressing VDJ
3.2. Scheme of Suppressing RDJ
3.3. Scheme of Suppressing JRVDJ
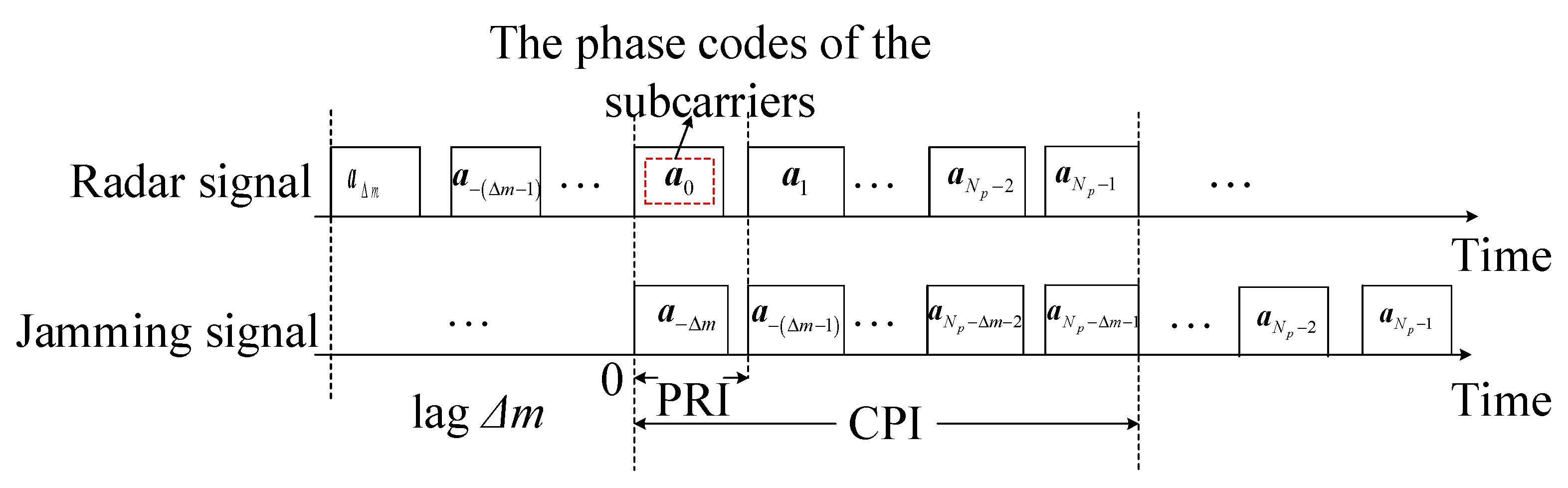
4. Designing OFDM Waveform for ECCM
4.1. Waveform Design for Suppressing the VDJ
| Algorithm 1: Solving the problem (40) with POBFGS |
| Initialization: Initialize the iteration number l = 0. And generate randomly and the stopping threshold value is set to be ε. Let H0 = INp. (The letter l in the subscript denotes the number of the iteration and is the value of at l-th iteration.) For l = 0,1,2,3,…
|
4.2. Waveform Design for Suppressing the RDJ and JRVDJ
| Algorithm 2: Solving the optimization problem (53) using POADMM |
| Initialization: Initialize () as () and The iteration index is set to be k = 0. Let K is the maximum number of iterations. Initialize the thresholds , and . For k = 1,2,3,…K
Then let the optimal waveform be . |
5. Numerical Simulation
5.1. The ECCM Performance of Resisting the VDJ
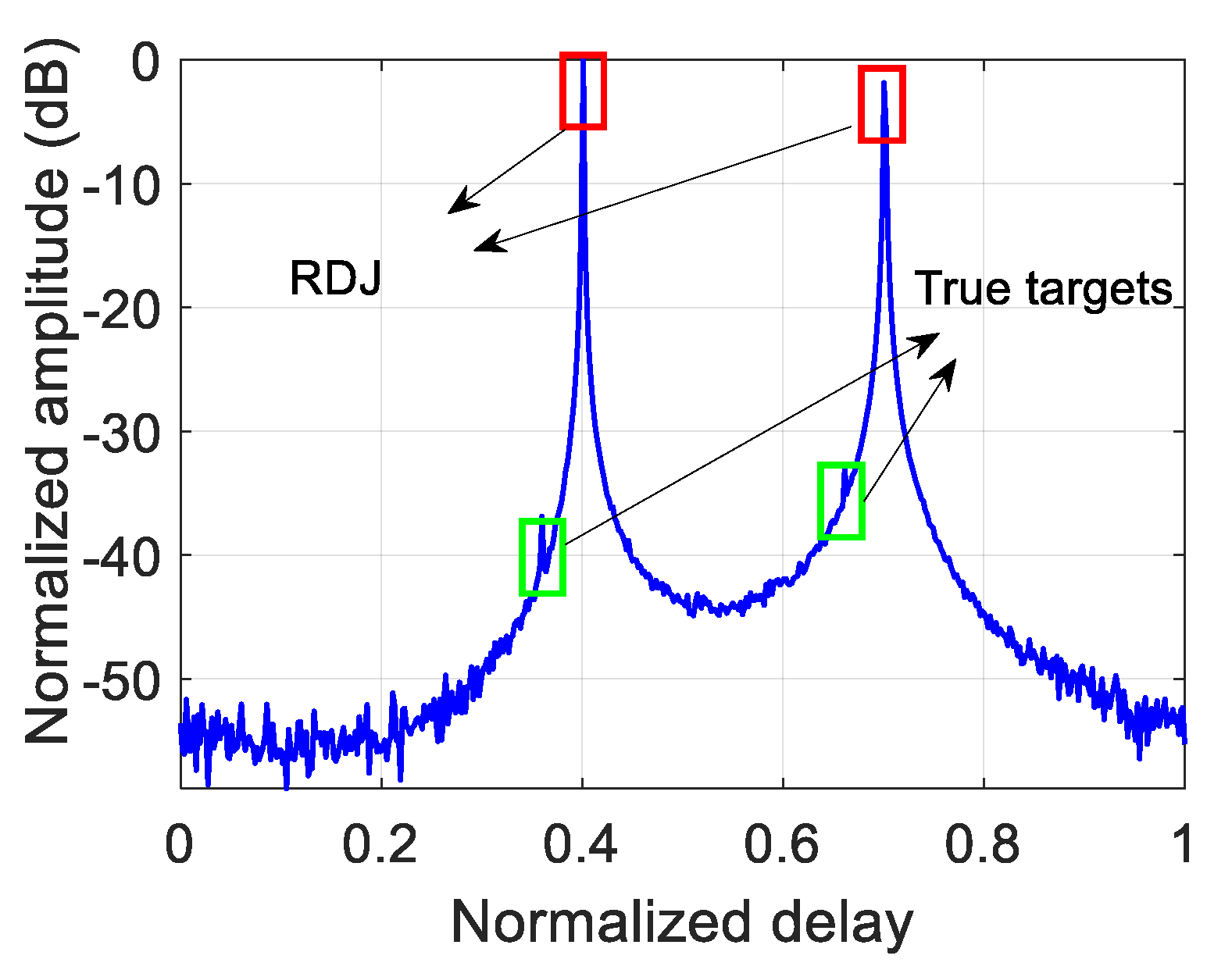
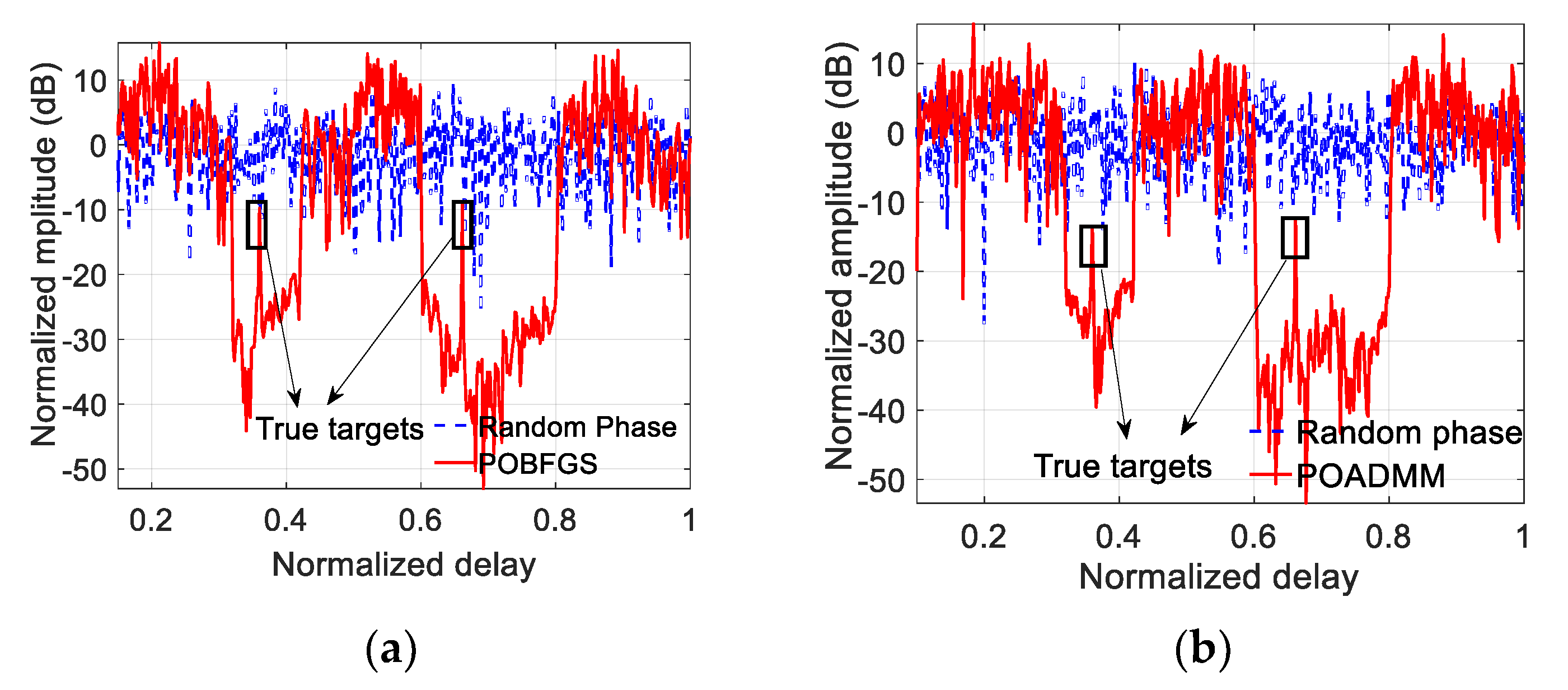
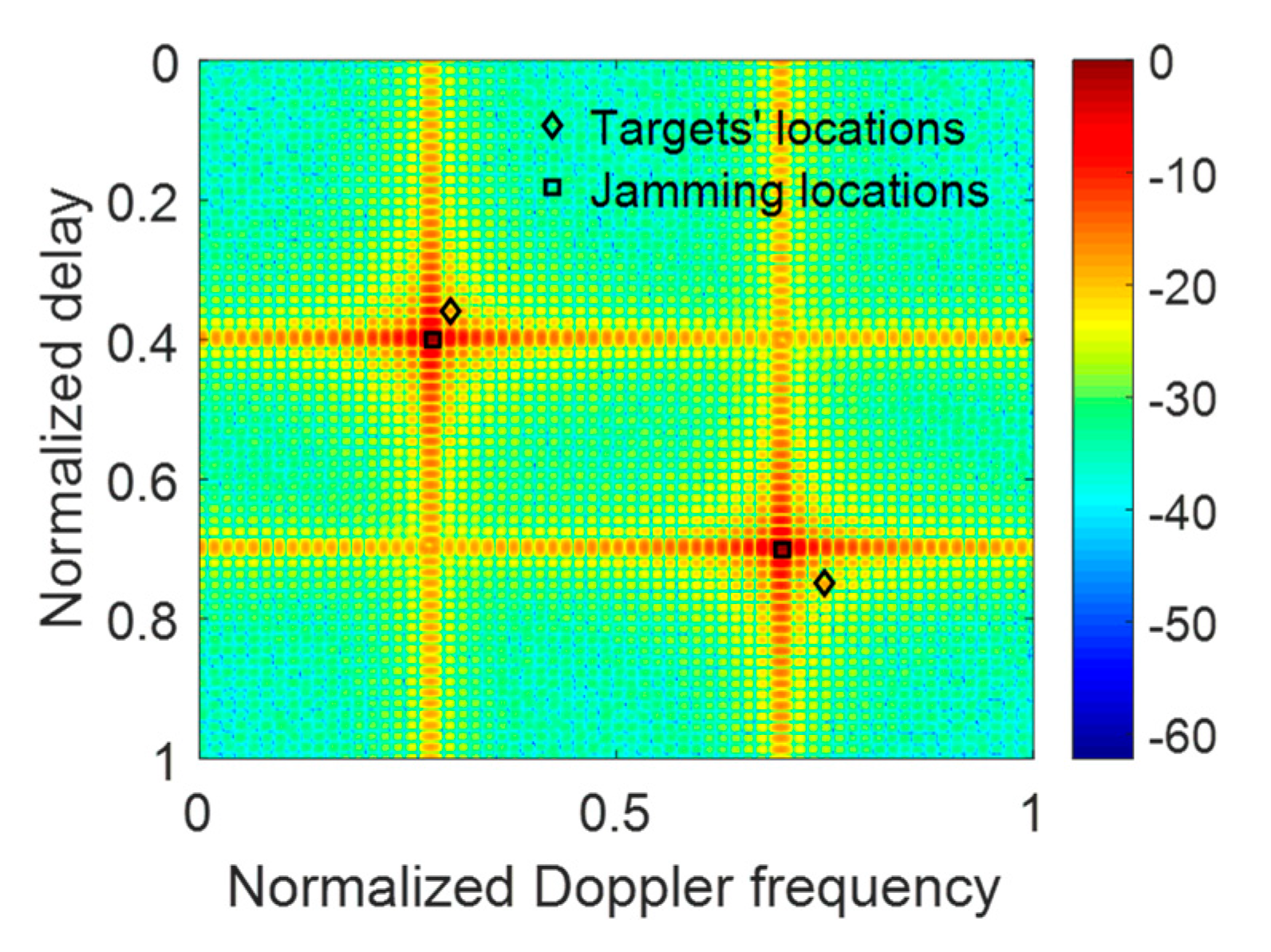
5.2. The ECCM Performance of Resisting RDJ and JRVDJ
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Appendix A
Appendix B
References
- Li, N.-J.; Zhang, Y.-T. A survey of radar ECM and ECCM. IEEE Trans. Aerosp. Electron. Syst. 1995, 31, 1110–1120. [Google Scholar]
- Anil, K.M. Electronic Warfare; Wiley: New York, NY, USA, 2018; pp. 475–554. [Google Scholar]
- Liu, Y.; Zhao, Y.; Zhu, J.; Wang, J.; Tang, B. A Switched-Element System Based Direction of Arrival (DOA) Estimation Method for Un-Cooperative Wideband Orthogonal Frequency Division Multi Linear Frequency Modulation (OFDM-LFM) Radar Signals. Sensors 2019, 19, 132. [Google Scholar] [CrossRef]
- Guerreiro, J.; Dinis, R.; Campos, L. On the Achievable Capacity of MIMO-OFDM Systems in the CathLab Environment. Sensors 2020, 20, 938. [Google Scholar] [CrossRef]
- Shi, Z.; Zhou, C.; Gu, Y.; Goodman, N.A.; Qu, F. Source estimation using coprime array: A sparse reconstruction perspective. IEEE Sens. 2016, 17, 755–765. [Google Scholar] [CrossRef]
- Shi, C.; Wang, F.; Salous, S.; Zhou, J. Optimal Power Allocation Strategy in a Joint Bistatic Radar and Communication System Based on Low Probability of Intercept. Sensors 2017, 17, 2731. [Google Scholar] [CrossRef]
- Schuerger, J.; Garmatyuk, D. Performance of random OFDM radar signals in deception jamming scenarios. In Proceedings of the 2009 IEEE Radar Conference, Pasadena, CA, USA, 4–8 May 2009; pp. 1–6. [Google Scholar]
- Greco, M.; Gini, F.; Farina, A. Radar Detection and Classification of Jamming Signals Belonging to a Cone Class. IEEE Trans. Signal Process. 2008, 56, 1984–1993. [Google Scholar] [CrossRef]
- Bandiera, F.; Farina, A.; Orlando, D.; Ricci, G. Detection Algorithms to Discriminate Between Radar Targets and ECM Signals. IEEE Trans. Signal Process. 2010, 58, 5984–5993. [Google Scholar] [CrossRef]
- Liu, W.; Liu, J.; Wang, L.; Duan, K.; Chen, Z.; Wang, Y. Adaptive array detection in noise and completely unknown jamming. Digit. Signal Process. 2015, 46, 41–48. [Google Scholar] [CrossRef]
- Soumekh, M. SAR-ECCM using phase-Perturbed LFM chirp signals and DRFM repeat jammer penalization. IEEE Trans. Aerosp. Electron. Syst. 2006, 42, 191–205. [Google Scholar] [CrossRef]
- Cui, G.; Yu, X.; Yuan, Y.; Kong, L. Range jamming suppression with a coupled sequential estimation algorithm. IET Radar Sonar Navig. 2018, 12, 341–347. [Google Scholar] [CrossRef]
- Zhang, J.; Zhu, D.; Zhang, G. New Antivelocity Deception Jamming Technique using Pulses with Adaptive Initial Phases. IEEE Trans. Aerosp. Electron. Syst. 2013, 49, 1290–1300. [Google Scholar] [CrossRef]
- Yang, Y.; Wu, J.; Cui, G.; Li, L.; Kong, L.; Huang, Y. Optimized phase-Coded waveform design against velocity deception. In Proceedings of the 2015 IEEE Radar Conference, Arlington, VA, USA, 10–15 May 2015; pp. 0400–0404. [Google Scholar]
- Huang, D.; Cui, G.; Yu, X.; Ge, M.; Kong, L. Joint range–Velocity deception jamming suppression for SIMO radar. IET Radar Sonar Navig. 2019, 13, 113–122. [Google Scholar] [CrossRef]
- Yan, L.; Addabbo, P.; Hao, C.; Orlando, D.; Farina, A. New ECCM Techniques Against Noise-Like and/or Coherent Interferers. IEEE Trans. Aerosp. Electron. Syst. 2019. [Google Scholar] [CrossRef]
- Bingham, J.A.C. Multicarrier modulation for data transmission: An idea whose time has come. IEEE Commun. Mag. 1990, 28, 5–14. [Google Scholar] [CrossRef]
- RichéV Méric, S.; Baudais, J.; Pottier, É. Investigations on OFDM Signal for Range Ambiguity Suppression in SAR Configuration. IEEE Trans. Geosci. Remote Sens. 2014, 52, 4194–4197. [Google Scholar]
- Zhang, T.; Xia, X.; Kong, L. IRCI Free Range Reconstruction for SAR Imaging with Arbitrary Length OFDM Pulse. IEEE Trans. Signal Process. 2014, 62, 4748–4759. [Google Scholar] [CrossRef]
- Garmatyuk, D.; Brenneman, M. Adaptive Multicarrier OFDM SAR Signal Processing. IEEE Trans. Geosci. Remote Sens. 2011, 49, 3780–3790. [Google Scholar] [CrossRef]
- Wen, F.; Shi, J.; Zhang, Z. Joint 2D-DOD, 2D-DOA and polarization angles estimation for bistatic EMVS-MIMO radar via PARAFAC analysis. IEEE Trans. Veh. Technol. 2019, 69, 1626–1638. [Google Scholar] [CrossRef]
- Wen, F.; Wang, J.; Shi, J.; Gui, G. Auxiliary Vehicle Positioning Based on Robust DOA Estimation with Unknown Mutual Coupling. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Zhou, C.; Gu, Y.; Fan, X.; Shi, Z.; Mao, G.; Zhang, Y.D. Direction-Of-Arrival estimation for coprime array via virtual array interpolation. IEEE Trans. Signal Process. 2018, 66, 5956–5971. [Google Scholar] [CrossRef]
- Wen, F.; Shi, J.; Zhang, Z. Direction Finding for Bistatic MIMO Radar with Unknown Spatially Colored Noise. Circuits Syst. Signal Process. 2020. [Google Scholar] [CrossRef]
- Wang, W. Space–Time Coding MIMO-OFDM SAR for High-Resolution Imaging. IEEE Trans. Geosci. Remote Sens. 2011, 49, 3094–3104. [Google Scholar] [CrossRef]
- Zhou, C.; Gu, Y.; Shi, Z.; Zhang, Y.D. Off-Grid direction-Of-Arrival estimation using coprime array interpolation. IEEE Signal Process. Lett. 2018, 25, 1710–1714. [Google Scholar] [CrossRef]
- Zhou, C.; Gu, Y.; Zhang, Y.D.; Shi, Z.; Jin, T.; Wu, X. Compressive sensing-Based coprime array direction-Of-Arrival estimation. IET Commun. 2017, 11, 1719–1724. [Google Scholar] [CrossRef]
- Zhou, C.; Gu, Y.; He, S.; Shi, Z. A robust and efficient algorithm for coprime array adaptive beamforming. IEEE Trans. Veh. Technol. 2017, 67, 1099–1112. [Google Scholar] [CrossRef]
- Stralka, J.P. Applications of Orthogonal Frequency-Division Multiplexing (OFDM) to Radar. Ph.D. Dissertation, Johns Hopkins University, Baltimore, MD, USA, 2008. [Google Scholar]
- Guo, L.; Deng, H.; Himed, B.; Ma, T.; Geng, Z. Waveform Optimization for Transmit Beamforming with MIMO Radar Antenna Arrays. IEEE Trans. Antennas Propag. 2015, 63, 543–552. [Google Scholar] [CrossRef]
- Smith, S.T. Optimum phase-Only adaptive nulling. IEEE Trans. Signal Process. 1999, 47, 1835–1843. [Google Scholar] [CrossRef]
- Boyd, S.; Parikh, N.; Chu, E.; Peleato, B.; Eckstein, J. Distributed Optimization and Statistical Learning via the Alternating Direction Method of Multipliers. Found. Trends Mach. Learn. 2010, 3, 1–122. [Google Scholar] [CrossRef]
- Wang, Y.; Wang, Y.; Shi, Q. Optimized Signal Distortion for PAPR Reduction of OFDM Signals With IFFT/FFT Complexity Via ADMM Approaches. IEEE Trans. Signal Process. 2019, 67, 399–414. [Google Scholar] [CrossRef]





| Physical Meanings | Quantity |
|---|---|
| The number of the subcarriers | 512 |
| The number of the pulses in a CPI | 512 |
| Signal-to-noise ratio | 0 dB |
| Jamming-to-signal ratio | 40 dB |
| The normalized Doppler frequency of the targets | 0.4, 0.75 |
| The normalized Doppler frequency of the VJs | 0.38, 0.72 |
| The suppressed intervals of the normalized Doppler frequency | [0.35, 0.45], [0.7, 0.8] |
| Physical Meanings | Quantity |
|---|---|
| The number of the subcarriers | 512 |
| The number of the pulses in a CPI | 512 |
| Signal-to-noise ratio | 0 dB |
| Jamming-to-signal ratio | 40 dB |
| The normalized delay of the targets | 0.36, 0.66 |
| The normalized delay of the RJs | 0.4, 0.7 |
| The suppressed intervals of the normalized delay | [0.32, 0.42], [0.6, 0.8] |
| Physical Meanings | Quantity |
|---|---|
| The number of the targets | 2 |
| The number of the subcarriers | 512 |
| The number of the pulses in a CPI | 512 |
| Signal-to-noise ratio | 0 dB |
| Jamming-to-signal ratio | 40 dB |
| The information of the targets | (0.3,0.36), (0.75,0.65) |
| The information of the JRVDJ | (0.28,0.4), (0.7,0.6) |
| The suppressed intervals of the normalized Doppler frequency | [0.2, 0.4], [0.6, 0.8] |
| The suppressed intervals of the normalized delay | [0.3, 0.5], [0.5, 0.7] |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, X.; Zhang, G.; Wang, X.; Song, Q.; Wen, F. ECCM Schemes against Deception Jamming Using OFDM Radar with Low Global PAPR. Sensors 2020, 20, 2071. https://doi.org/10.3390/s20072071
Wang X, Zhang G, Wang X, Song Q, Wen F. ECCM Schemes against Deception Jamming Using OFDM Radar with Low Global PAPR. Sensors. 2020; 20(7):2071. https://doi.org/10.3390/s20072071
Chicago/Turabian StyleWang, Xinhai, Gong Zhang, Xiangmin Wang, Qingqing Song, and Fangqing Wen. 2020. "ECCM Schemes against Deception Jamming Using OFDM Radar with Low Global PAPR" Sensors 20, no. 7: 2071. https://doi.org/10.3390/s20072071
APA StyleWang, X., Zhang, G., Wang, X., Song, Q., & Wen, F. (2020). ECCM Schemes against Deception Jamming Using OFDM Radar with Low Global PAPR. Sensors, 20(7), 2071. https://doi.org/10.3390/s20072071




