Game Theory in Mobile CrowdSensing: A Comprehensive Survey
Abstract
1. Introduction
2. Background and Challenges in Mobile Crowdsensing
2.1. Privacy and Security
2.2. Quality of Data
2.3. Trustworthiness
2.4. Energy
2.5. Incentives
2.6. Agent-Based Strategies
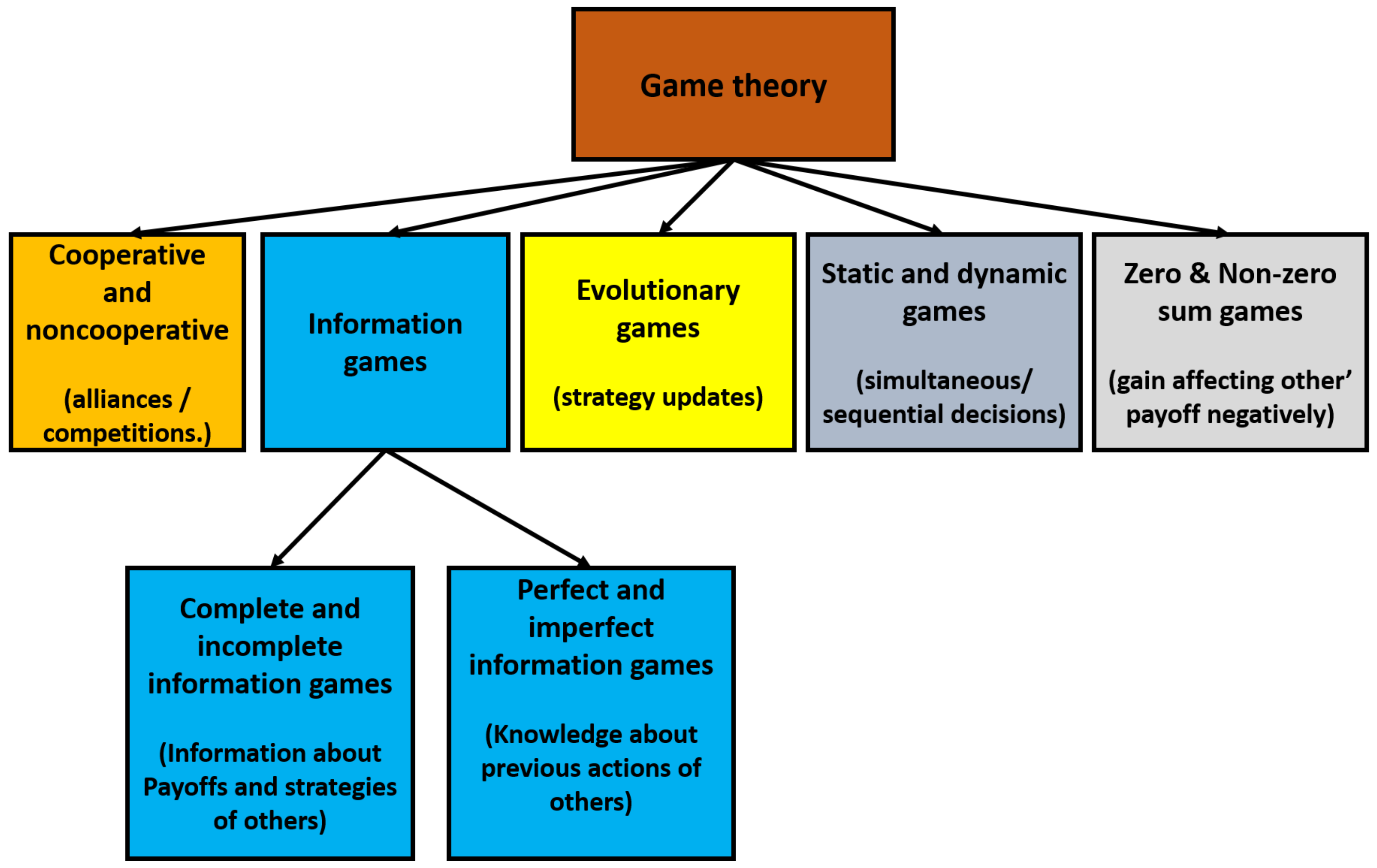
3. Presentation of Common Game Theory Models
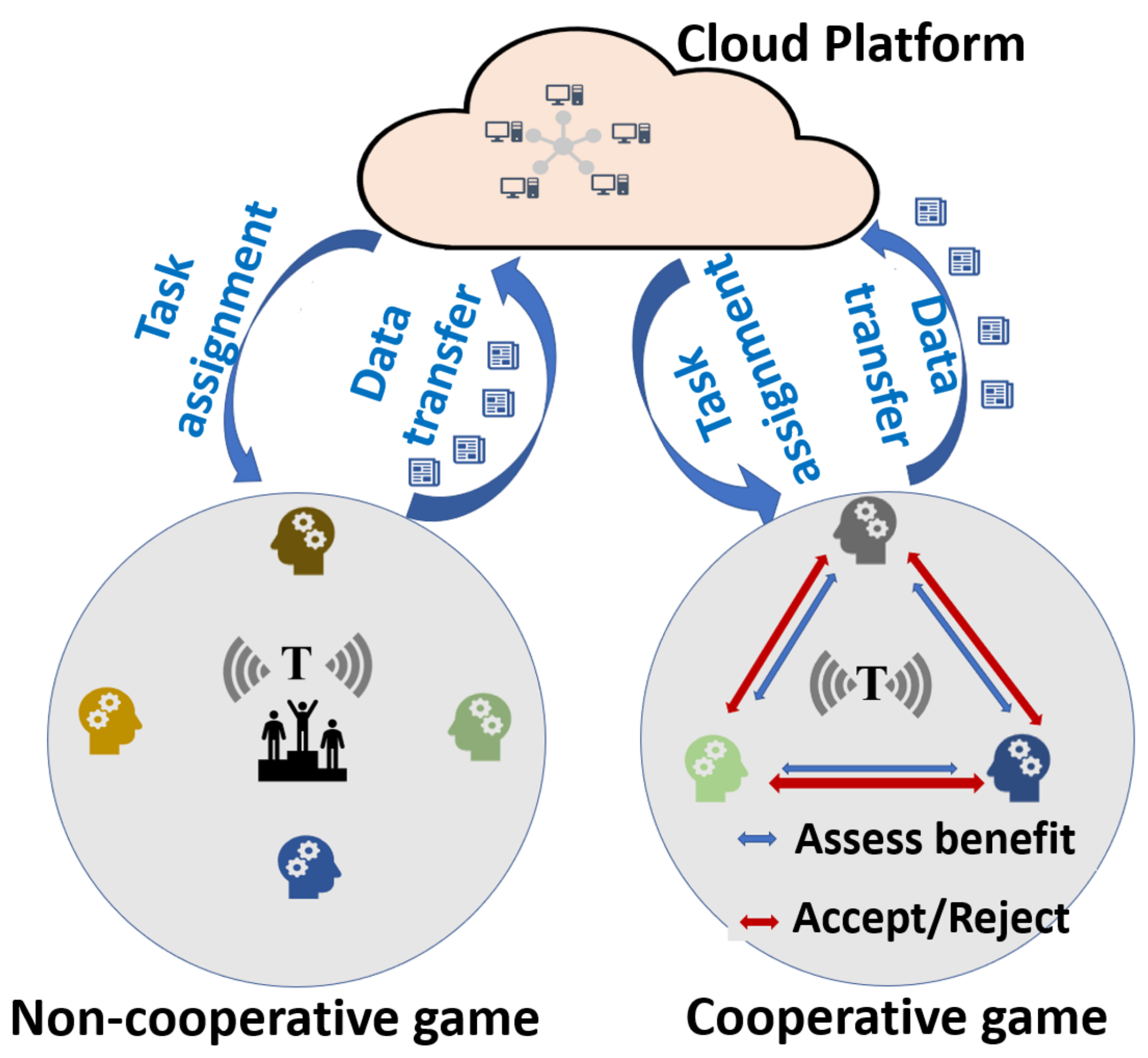
3.1. Co-Operative and Non-Co-Operative Games
3.2. Information Games
3.2.1. Perfect and Imperfect Information Games
3.2.2. Complete and Incomplete Information Games
3.3. Evolutionary Games
3.4. Static and Dynamic Games
3.5. Zero Sum and Non Zero-Sum Games
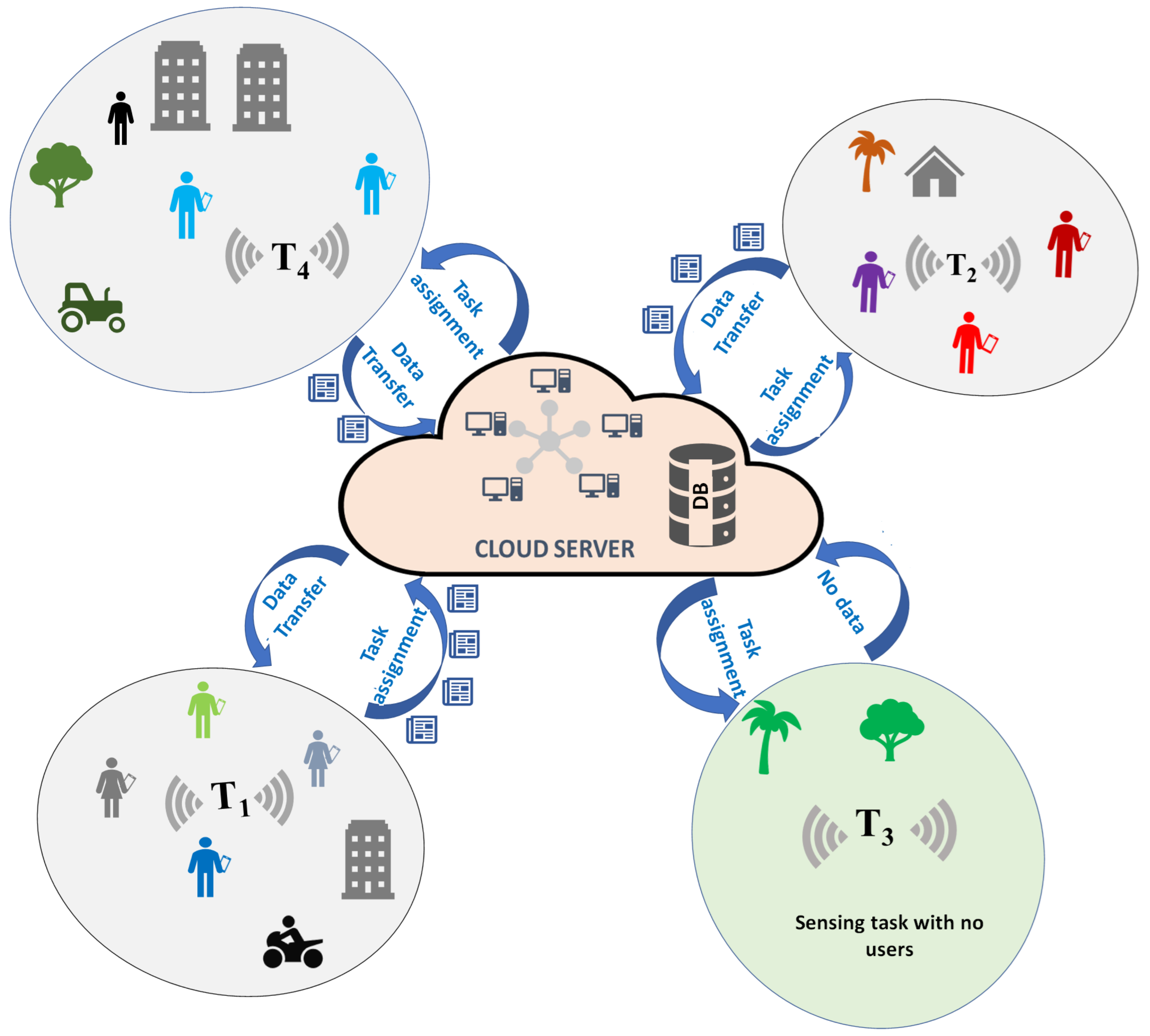
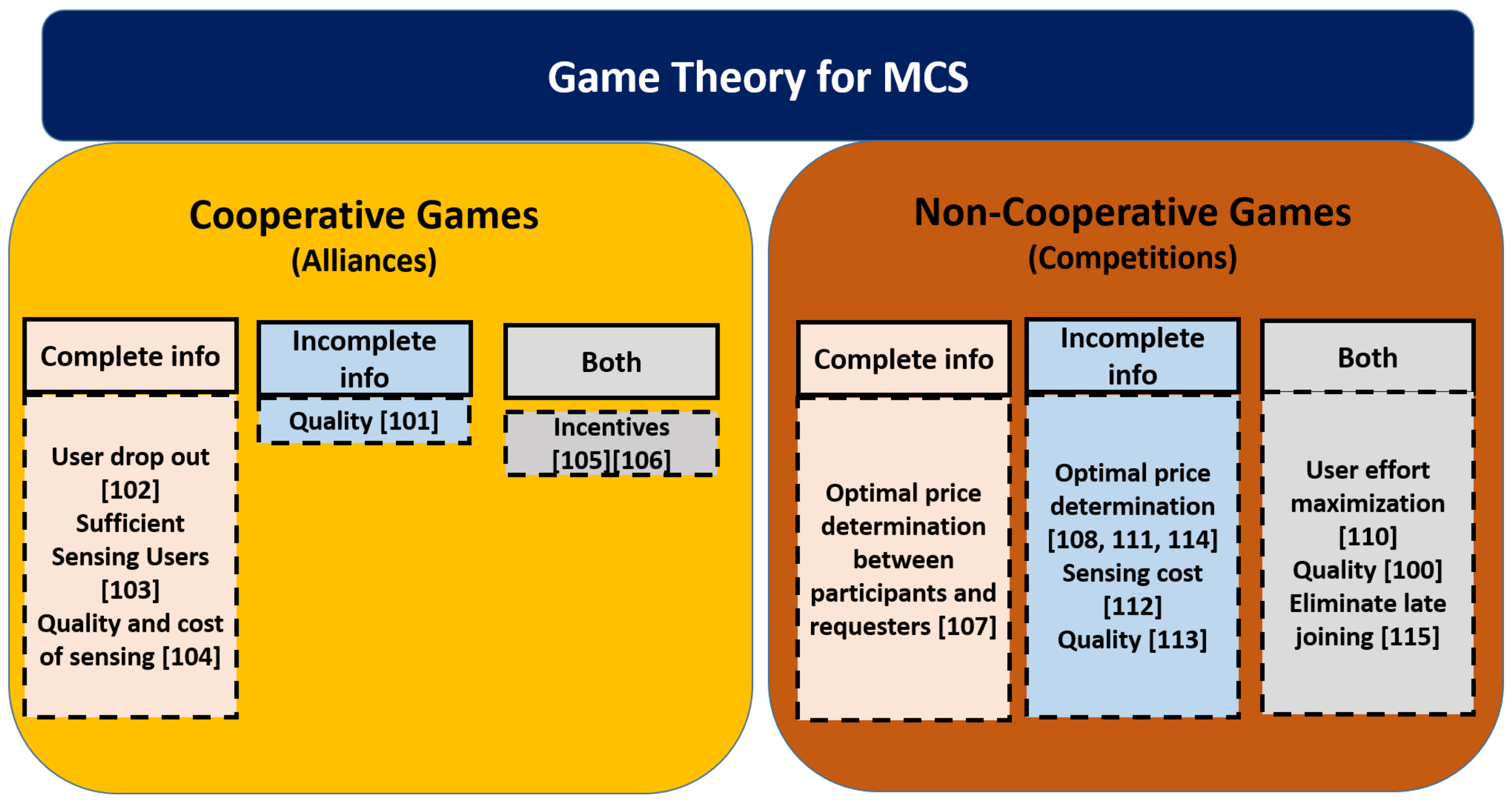
4. Game Theory in MCS
4.1. Co-Operative Games in MCS
4.1.1. Co-Operative Games in MCS with Complete Information
4.1.2. Co-Operative Games in MCS with Incomplete Information
4.1.3. Co-Operative Games in MCS Considering Both Complete and Incomplete Information
4.2. Non-Co-Operative Games in MCS
4.2.1. Non-Co-Operative Games in MCS with Complete Information
4.2.2. Non-Co-Operative Games in MCS with Incomplete Information
4.2.3. Non-Coperative Games in MCS Considering Both Complete and Incomplete Information
5. Open Research Areas
5.1. Evolutionary Games
5.2. Nash Equilibrium
5.3. Stackelberg Game
5.4. Co-Operative Games
5.5. Non-Cooperative Games
6. Conclusions and Discussion
Author Contributions
Funding
Conflicts of Interest
References
- Cisco Blogs. Internet of Things (IoT) Data Continues to Explode Exponentially. Who Is Using That Data and How? Available online: https://blogs.cisco.com/datacenter/internet-of-things-iot-data-continues-to-explode-exponentially-who-is-using-that-data-and-how (accessed on 4 April 2020).
- Capponi, A.; Fiandrino, C.; Kantarci, B.; Foschini, L.; Kliazovich, D.; Bouvry, P. A Survey on Mobile Crowdsensing Systems: Challenges, Solutions, and Opportunities. IEEE Commun. Surv. Tutor. 2019, 21, 2419–2465. [Google Scholar] [CrossRef]
- An, J.; Gui, X.; Yang, J.; Sun, Y.; He, X. Mobile crowd sensing for internet of things: A credible crowdsourcing model in mobile-sense service. In Proceedings of the 2015 IEEE International Conference on Multimedia Big Data (BigMM), Beijing, China, 20–22 April 2015; pp. 92–99. [Google Scholar]
- Liu, Y.; Kong, L.; Chen, G. Data-Oriented Mobile Crowdsensing: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2019, 21, 2849–2885. [Google Scholar] [CrossRef]
- Mohan, P.; Padmanabhan, V.N.; Ramjee, R. Nericell: Rich monitoring of road and traffic conditions using mobile smartphones. In Proceedings of the 6th ACM Conference on Embedded Network Sensor Systems, Raleigh, NC, USA, 5 November 2008; pp. 323–336. [Google Scholar]
- Amin, S.; Andrews, S.; Apte, S.; Arnold, J.; Ban, J.; Benko, M.; Bayen, R.M.; Chiou, B.; Claudel, C.; Claudel, C.; et al. Mobile Century Using GPS Mobile Phones as Traffic Sensors: A Field Experiment. CiteSeer 2008. [Google Scholar]
- Rutten, M.; Minkman, E.; van der Sanden, M. How to get and keep citizens involved in mobile crowd sensing for water management? A review of key success factors and motivational aspects. Wiley Interdiscip. Rev. Water 2017, 4, e1218. [Google Scholar] [CrossRef]
- Restuccia, F.; Thandu, S.C.; Chellappan, S.; Das, S.K. RescuePal: A smartphone-based system to discover people in emergency scenarios. In Proceedings of the 2016 IEEE 17th International Symposium on A World of Wireless, Mobile and Multimedia Networks (WoWMoM), Coimbra, Portugal, 21–24 June 2016; pp. 1–6. [Google Scholar]
- Fiandrino, C.; Capponi, A.; Cacciatore, G.; Kliazovich, D.; Sorger, U.; Bouvry, P.; Kantarci, B.; Granelli, F.; Giordano, S. CrowdSenSim: A Simulation Platform for Mobile Crowdsensing in Realistic Urban Environments. IEEE Access 2017, 5, 3490–3503. [Google Scholar] [CrossRef]
- Mendez, D.; Colorado, J.; Rodriguez, L.; Chancon, A.; Hernandez, M. Monitoring Air Pollution By Combining A Static Infrastructure With A Participatory Sensing Approach: Design And Performance Evaluation. Int. J. Sustain. Dev. Plan. 2018, 13, 638–652. [Google Scholar] [CrossRef][Green Version]
- Gao, R.; Zhao, M.; Ye, T.; Ye, F.; Wang, Y.; Bian, K.; Wang, T.; Li, X. Jigsaw: Indoor Floor Plan Reconstruction via Mobile Crowdsensing. In Proceedings of the MobiCom ’14: The 20th Annual International Conference on Mobile Computing and Networking, Maui, HI, USA, 7–11 September 2014; pp. 249–260. [Google Scholar]
- Dasari, V.S.; Pouryazdan, M.; Kantarci, B. Selective versus Non-Selective Acquisition of Crowd-Solicited IoT Data and Its Dependability. In Proceedings of the 2018 IEEE International Conference on Communications Workshops (ICC Workshops), Kansas City, MO, USA, 20–24 May 2018. [Google Scholar]
- Kantarci, B.; Mouftah, H.T. Reputation-based sensing-as-a-service for crowd management over the cloud. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, Australia, 10–14 June 2014; pp. 3614–3619. [Google Scholar]
- Pouryazdan, M.; Kantarci, B.; Soyata, T.; Song, H. Anchor-assisted and vote-based trustworthiness assurance in smart city crowdsensing. IEEE Access 2016, 4, 529–541. [Google Scholar] [CrossRef]
- Ren, J.; Zhang, Y.; Zhang, K.; Shen, X.S. SACRM: Social aware crowdsourcing with reputation management in mobile sensing. Comput. Commun. 2015, 65, 55–65. [Google Scholar] [CrossRef]
- Cheung, M.H.; Southwell, R.; Hou, F.; Huang, J. Distributed time-sensitive task selection in mobile crowdsensing. In Proceedings of the 16th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Hangzhou, China, 22–25 June 2015; pp. 157–166. [Google Scholar]
- Xiong, J.; Ma, R.; Chen, L.; Tian, Y.; Lin, L.; Jin, B. Achieving Incentive, Security, and Scalable Privacy Protection in Mobile Crowdsensing Services. Wirel. Commun. Mob. Comput. 2018, 2018. [Google Scholar] [CrossRef]
- Zhang, Y.; van der Schaar, M. Reputation-based incentive protocols in crowdsourcing applications. In Proceedings of the 2012 Proceedings IEEE INFOCOM, Orlando, FL, USA, 25–30 March 2012; pp. 2140–2148. [Google Scholar]
- Wang, X.O.; Cheng, W.; Mohapatra, P.; Abdelzaher, T. Enabling reputation and trust in privacy-preserving mobile sensing. IEEE Trans. Mob. Comput. 2014, 13, 2777–2790. [Google Scholar] [CrossRef]
- Zhang, X.; Yang, Z.; Sun, W.; Liu, Y.; Tang, S.; Xing, K.; Mao, X. Incentives for mobile crowd sensing: A survey. IEEE Commun. Surv. Tutor. 2016, 18, 54–67. [Google Scholar] [CrossRef]
- Chou, C.M.; Lan, K.c.; Yang, C.F. Using virtual credits to provide incentives for vehicle communication. In Proceedings of the 2012 12th International Conference on ITS Telecommunications, Taipei, Taiwan, 5–8 November 2012; pp. 579–583. [Google Scholar]
- Reddy, S.; Estrin, D.; Hansen, M.; Srivastava, M. Examining micro-payments for participatory sensing data collections. In Proceedings of the 12th ACM International Conference on Ubiquitous Computing, Copenhagen, Denmark, 26–29 September 2010; pp. 33–36. [Google Scholar]
- Chen, X. Task trading for crowdsourcing in opportunistic mobile social networks. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018; pp. 1–6. [Google Scholar]
- Talla, V.; Kellogg, B.; Ransford, B.; Naderiparizi, S.; Gollakota, S.; Smith, J.R. Powering the next billion devices with Wi-Fi. In Proceedings of the 11th ACM Conference on Emerging Networking Experiments and Technologies, Heidelberg, Germany, 1–4 December 2015. [Google Scholar]
- Miessler, D. HP study reveals 70 percent of internet of things devices vulnerable to attack. Retrieved June 2014, 30, 2015. [Google Scholar]
- Yang, K.; Zhang, K.; Ren, J.; Shen, X. Security and privacy in mobile crowdsourcing networks: Challenges and opportunities. IEEE Commun. Mag. 2015, 53, 75–81. [Google Scholar] [CrossRef]
- Krontiris, I.; Freiling, F.C.; Dimitriou, T. Location privacy in urban sensing networks: Research challenges and directions [security and privacy in emerging wireless networks]. IEEE Wirel. Commun. 2010, 17, 30–35. [Google Scholar] [CrossRef]
- Sastry, N.; Shankar, U.; Wagner, D. Secure verification of location claims. In Proceedings of the 2nd ACM Workshop on Wireless Security, San Diego, CA, USA, 19 September 2003; pp. 1–10. [Google Scholar]
- Capkun, S.; Hubaux, J.P. Secure positioning of wireless devices with application to sensor networks. In Proceedings of the 24th Annual Joint Conference of the IEEE Computer and Communications Societies, Miami, FL, USA, 13–17 March 2005; pp. 1917–1928. [Google Scholar]
- Patterson, D.J.; Liao, L.; Fox, D.; Kautz, H. Inferring high-level behavior from low-level sensors. In Proceedings of the International Conference on Ubiquitous Computing, Seattle, WA, USA, 12–15 October 2003; pp. 73–89. [Google Scholar]
- Hoh, B.; Gruteser, M.; Xiong, H.; Alrabady, A. Enhancing security and privacy in traffic-monitoring systems. IEEE Pervasive Comput. 2006, 5, 38–46. [Google Scholar]
- Cheng, R.; Zhang, Y.; Bertino, E.; Prabhakar, S. Preserving user location privacy in mobile data management infrastructures. In Proceedings of the International Workshop on Privacy Enhancing Technologies, Cambridge, UK, 28–30 June 2006; pp. 393–412. [Google Scholar]
- Talasila, M.; Curtmola, R.; Borcea, C. ILR: Improving location reliability in mobile crowd sensing. Int. J. Bus. Data Commun. Netw. 2013, 9, 65–85. [Google Scholar] [CrossRef]
- Acquisti, A.; Grossklags, J. Privacy and rationality in individual decision making. IEEE Secur. Priv. 2005, 3, 26–33. [Google Scholar] [CrossRef]
- Chen, P.Y.; Cheng, S.M.; Ting, P.S.; Lien, C.W.; Chu, F.J. When crowdsourcing meets mobile sensing: A social network perspective. arXiv 2015, arXiv:1508.00299. [Google Scholar] [CrossRef]
- Wang, X.O.; Cheng, W.; Mohapatra, P.; Abdelzaher, T. Artsense: Anonymous reputation and trust in participatory sensing. In Proceedings of the 2013 Proceedings INFOCOM, Turin, Italy, 14–19 April 2013; pp. 2517–2525. [Google Scholar]
- Barkhuus, L.; Dey, A.K. Location-Based Services for Mobile Telephony: A Study of Users’ Privacy Concerns. In Proceedings of the 9th IFIP TC13 International Conference on Human-Computer Interaction, Zurich, Switzerland, 1–5 September 2003; Volume 3, pp. 702–712. [Google Scholar]
- Barkhuus, L. Privacy in location-based services, concern vs. coolness. In Proceedings of the Workshop on Location Systems Privacy and Control at MobileHCI, Glasgow, UK, 13–16 September 2004. [Google Scholar]
- Wayne, W. Data quality and the bottom line: Achieving business success through a commitment to high quality data. The Data Warehouse Institute (TDWI) Report; TDWI: Seattle, WA, USA, 2004; Available online: www.dw-institute.com (accessed on 4 April 2020).
- Song, Z.; Liu, C.H.; Wu, J.; Ma, J.; Wang, W. Qoi-aware multitask-oriented dynamic participant selection with budget constraints. IEEE Trans. Veh. Technol. 2014, 63, 4618–4632. [Google Scholar] [CrossRef]
- Wang, L.; Zhang, D.; Pathak, A.; Chen, C.; Xiong, H.; Yang, D.; Wang, Y. CCS-TA: Quality-guaranteed online task allocation in compressive crowdsensing. In Proceedings of the 2015 ACM International Joint Conference on Pervasive and Ubiquitous Computing, Osaka, Japan, 7–8 September 2015; pp. 683–694. [Google Scholar]
- Liono, J.; Jayaraman, P.P.; Qin, A.; Nguyen, T.; Salim, F.D. QDaS: Quality driven data summarisation for effective storage management in Internet of Things. J. Parallel Distrib. Comput. 2018. [Google Scholar] [CrossRef]
- Liu, C.H.; Hui, P.; Branch, J.W.; Bisdikian, C.; Yang, B. Efficient network management for context-aware participatory sensing. In Proceedings of the 2011 8th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks, Salt Lake City, UT, USA, 27–30 June 2011; pp. 116–124. [Google Scholar]
- Gong, W.; Zhang, B.; Li, C. Task Assignment in Mobile Crowdsensing: Present and Future Directions. IEEE Netw. 2018, 32, 100–107. [Google Scholar] [CrossRef]
- Wang, L.; Zhang, D.; Wang, Y.; Chen, C.; Han, X.; M’hamed, A. Sparse mobile crowdsensing: Challenges and opportunities. IEEE Commun. Mag. 2016, 54, 161–167. [Google Scholar] [CrossRef]
- Kong, L.; Xia, M.; Liu, X.Y.; Wu, M.Y.; Liu, X. Data loss and reconstruction in sensor networks. In Proceedings of the 2013 Proceedings IEEE INFOCOM, Turin, Italy, 14–19 April 2013; pp. 1654–1662. [Google Scholar]
- Restuccia, F.; Ghosh, N.; Bhattacharjee, S.; Das, S.K.; Melodia, T. Quality of Information in Mobile Crowdsensing: Survey and Research Challenges. ACM Trans. Sens. Netw. 2017, 13, 1–43. [Google Scholar] [CrossRef]
- Ipeirotis, P.G.; Provost, F.; Wang, J. Quality management on amazon mechanical turk. In Proceedings of the ACM SIGKDD Workshop on Human Computation, Washington, DC, USA, 25–28 July 2010; pp. 64–67. [Google Scholar]
- Jøsang, A.; Pope, S. Semantic constraints for trust transitivity. In APCCM ’05: Proceedings of the 2nd Asia-Pacific Conference on Conceptual Modelling; Australian Computer Society, Inc.: Darlinghurst, Australia, 2005; Volume 43, pp. 59–68. [Google Scholar]
- Sawand, A.; Djahel, S.; Zhang, Z.; Nait-Abdesselam, F. Toward energy-efficient and trustworthy eHealth monitoring system. China Commun. 2015, 12. [Google Scholar] [CrossRef]
- Xiang, C.; Yang, P.; Tian, C.; Yan, Y.; Wu, X.; Liu, Y. Passfit: Participatory sensing and filtering for identifying truthful urban pollution sources. IEEE Sens. J. 2013, 13, 3721–3732. [Google Scholar] [CrossRef]
- Chang, S.H.; Chen, Z.R. Protecting mobile crowd sensing against sybil attacks using cloud based trust management system. Mob. Inf. Syst. 2016, 2016. [Google Scholar] [CrossRef]
- Huang, K.L.; Kanhere, S.S.; Hu, W. Are you contributing trustworthy data? The case for a reputation system in participatory sensing. In Proceedings of the 13th ACM international conference on Modeling, analysis, and simulation of wireless and mobile systems, Bodrum, Turkey, 20–21 October 2010; pp. 14–22. [Google Scholar]
- Pouryazdan, M.; Kantarci, B. The smart citizen factor in trustworthy smart city crowdsensing. IT Prof. 2016, 18, 26–33. [Google Scholar] [CrossRef]
- Kantarci, B.; Mouftah, H.T. Trustworthy sensing for public safety in cloud-centric internet of things. IEEE Internet Things J. 2014, 1, 360–368. [Google Scholar] [CrossRef]
- Pouryazdan, M.; Kantarci, B.; Soyata, T.; Foschini, L.; Song, H. Quantifying User Reputation Scores, Data Trustworthiness, and User Incentives in Mobile Crowd-Sensing. IEEE Access 2017, 5, 1382–1397. [Google Scholar] [CrossRef]
- Wang, W.; Gao, H.; Liu, C.H.; Leung, K.K. Credible and energy-aware participant selection with limited task budget for mobile crowd sensing. Ad Hoc Netw. 2016, 43, 56–70. [Google Scholar] [CrossRef]
- Amintoosi, H.; Kanhere, S.S. A reputation framework for social participatory sensing systems. Mob. Netw. Appl. 2014, 19, 88–100. [Google Scholar] [CrossRef]
- Javed, A.; Shahid, M.A.; Sharif, M.; Yasmin, M. Energy Consumption in Mobile Phones. Int. J. Comput. Netw. Inf. Secur. 2017, 9, 18. [Google Scholar] [CrossRef][Green Version]
- Balasubramanian, N.; Balasubramanian, A.; Venkataramani, A. Energy consumption in mobile phones: A measurement study and implications for network applications. In Proceedings of the 9th ACM SIGCOMM Conference on Internet Measurement, Chicago, IL, USA, 4–6 November 2009; pp. 280–293. [Google Scholar]
- Yan, Z.; Subbaraju, V.; Chakraborty, D.; Misra, A.; Aberer, K. Energy-efficient continuous activity recognition on mobile phones: An activity-adaptive approach. In Proceedings of the 2012 16th International Symposium on Wearable Computers (ISWC), Newcastle, UK, 18–22 June 2012; pp. 17–24. [Google Scholar]
- Anjomshoa, F.; Kantarci, B. SOBER-MCS: Sociability-Oriented and Battery Efficient Recruitment for Mobile Crowd-Sensing. Sensors 2018, 18, 1593. [Google Scholar] [CrossRef] [PubMed]
- Liu, C.H.; Zhang, B.; Su, X.; Ma, J.; Wang, W.; Leung, K.K. Energy-aware participant selection for smartphone-enabled mobile crowd sensing. IEEE Syst. J. 2017, 11, 1435–1446. [Google Scholar] [CrossRef]
- Xiao, F.; Jiang, Z.; Xie, X.; Sun, L.; Wang, R. An energy-efficient data transmission protocol for mobile crowd sensing. Peer- Netw. Appl. 2017, 10, 510–518. [Google Scholar] [CrossRef]
- Tomasoni, M.; Capponi, A.; Fiandrino, C.; Kliazovich, D.; Granelli, F.; Bouvry, P. Profiling Energy Efficiency of Mobile Crowdsensing Data Collection Frameworks for Smart City Applications. In Proceedings of the 2018 6th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud), Bamberg, Germany, 26–29 March 2018; pp. 1–8. [Google Scholar]
- Lane, N.D.; Chon, Y.; Zhou, L.; Zhang, Y.; Li, F.; Kim, D.; Ding, G.; Zhao, F.; Cha, H. Piggyback CrowdSensing (PCS): Energy efficient crowdsourcing of mobile sensor data by exploiting smartphone app opportunities. In Proceedings of the 11th ACM Conference on Embedded Networked Sensor Systems, Roma, Italy, 11–15 November 2013. [Google Scholar]
- Peng, D.; Wu, F.; Chen, G. Pay as how well you do: A quality based incentive mechanism for crowdsensing. In Proceedings of the 16th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Hangzhou, China, 22–25 June 2015; pp. 177–186. [Google Scholar]
- Jaimes, L.G.; Vergara-Laurens, I.J.; Raij, A. A survey of incentive techniques for mobile crowd sensing. IEEE Internet Things J. 2015, 2, 370–380. [Google Scholar] [CrossRef]
- Reddy, S.; Estrin, D.; Srivastava, M. Recruitment framework for participatory sensing data collections. In Pervasive Computing; Springer: Berlin/Heidelberg, Germany, 2010; pp. 138–155. [Google Scholar]
- Lee, J.S.; Hoh, B. Sell your experiences: A market mechanism based incentive for participatory sensing. In Proceedings of the 2010 IEEE International Conference on Pervasive Computing and Communications (PerCom), Mannheim, Germany, 29 March–2 April 2010; pp. 60–68. [Google Scholar]
- Zhang, X.; Yang, Z.; Zhou, Z.; Cai, H.; Chen, L.; Li, X. Free market of crowdsourcing: Incentive mechanism design for mobile sensing. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 3190–3200. [Google Scholar] [CrossRef]
- Zhao, D.; Li, X.Y.; Ma, H. Budget-feasible online incentive mechanisms for crowdsourcing tasks truthfully. IEEE/ACM Trans. Netw. (TON) 2016, 24, 647–661. [Google Scholar] [CrossRef]
- Wang, Z.; Tan, R.; Hu, J.; Zhao, J.; Wang, Q.; Xia, F.; Niu, X. Heterogeneous incentive mechanism for time-sensitive and location-dependent crowdsensing networks with random arrivals. Comput. Netw. 2018, 131, 96–109. [Google Scholar] [CrossRef]
- Leppänen, T.; Alvarez Lacasia, J.; Tobe, Y.; Sezaki, K.; Riekki, J. Mobile Crowdsensing with Mobile Agents: JAAMAS Extended Abstract. In Proceedings of the 2016 International Conference on Autonomous Agents & Multiagent Systems AAMAS ’16, Singapore, 9–13 May 2016; pp. 738–739. [Google Scholar]
- Urra, O.; Ilarri, S. Spatial crowdsourcing with mobile agents in vehicular networks. Veh. Commun. 2019, 17, 10–34. [Google Scholar] [CrossRef]
- Bosse, S.; Engel, U. Real-Time Human-In-The-Loop Simulation with Mobile Agents, Chat Bots, and Crowd Sensing for Smart Cities. Sensors 2019, 19, 4356. [Google Scholar] [CrossRef]
- Wang, Z.; Pang, X.; Chen, Y.; Shao, H.; Wang, Q.; Wu, L.; Chen, H.; Qi, H. Privacy-Preserving Crowd-Sourced Statistical Data Publishing with An Untrusted Server. IEEE Trans. Mob. Comput. 2019, 18, 1356–1367. [Google Scholar] [CrossRef]
- Xiao, L.; Chen, T.; Xie, C.; Liu, J. Mobile crowdsensing game in vehicular networks. In Proceedings of the TENCON 2015—2015 IEEE Region 10 Conference, Macao, China, 1–4 November 2015; pp. 1–6. [Google Scholar]
- Cao, B.; Xia, S.; Han, J.; Li, Y. A Distributed Game Methodology for Crowdsensing in Uncertain Wireless Scenario. IEEE Trans. Mob. Comput. 2020, 19, 15–28. [Google Scholar] [CrossRef]
- Nie, J.; Luo, J.; Xiong, Z.; Niyato, D.; Wang, P. A Stackelberg Game Approach Toward Socially-Aware Incentive Mechanisms for Mobile Crowdsensing. IEEE Trans. Wirel. Commun. 2019, 18, 724–738. [Google Scholar] [CrossRef]
- Xiao, L.; Liu, J.; Li, Q.; Poor, H.V. Secure mobile crowdsensing game. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 7157–7162. [Google Scholar]
- Yang, Y.; Liu, W.; Wang, E.; Wang, H. Beaconing Control strategy based on Game Theory in mobile crowdsensing. Future Gener. Comput. Syst. 2018, 86, 222–233. [Google Scholar] [CrossRef]
- Gao, H.; Xu, H.; Zhang, L.; Zhou, X. A Differential Game Model for Data Utility and Privacy-Preserving in Mobile Crowdsensing. IEEE Access 2019, 7, 128526–128533. [Google Scholar] [CrossRef]
- Chen, Z.G.; Wang, T.; Xiao, D.G.; Xu, Y. Can remembering history from predecessor promote cooperation in the next generation? Chaos Solitons Fractals 2013, 56, 59–68. [Google Scholar] [CrossRef]
- Kreps, D.M.; Milgrom, P.; Roberts, J.; Wilson, R. Rational cooperation in the finitely repeated prisoners’ dilemma. J. Econ. Theory 1982, 27, 245–252. [Google Scholar] [CrossRef]
- Yıldız, N. Identification of parameters in an asymmetric perfect information game. Econ. Lett. 2011, 112, 243–246. [Google Scholar] [CrossRef]
- Nowak, M.A.; Page, K.M.; Sigmund, K. Fairness versus reason in the ultimatum game. Science 2000, 289, 1773–1775. [Google Scholar] [CrossRef]
- MacKenzie, A.B.; Wicker, S.B. Stability of multipacket slotted aloha with selfish users and perfect information. In Proceedings of the IEEE INFOCOM 2003. Twenty-second Annual Joint Conference of the IEEE Computer and Communications Societies (IEEE Cat. No.03CH37428), San Francisco, CA, USA, 30 March–3 April 2003; Volume 3, pp. 1583–1590. [Google Scholar]
- Liu, X.; Pan, Q.; He, M.; Liu, A. Promotion of cooperation in evolutionary game dynamics under asymmetric information. Phys. A: Stat. Mech. Its Appl. 2019, 521, 258–266. [Google Scholar] [CrossRef]
- Hassan, A.S.; Rafie, M.M. A survey of game theory using evolutionary algorithms. In Proceedings of the 2010 International Symposium on Information Technology, Kuala Lumpur, Malaysia, 15–17 June 2010; pp. 1319–1325. [Google Scholar]
- Kreps, D.M.; Wilson, R. Reputation and imperfect information. J. Econ. Theory 1982, 27, 253–279. [Google Scholar] [CrossRef]
- Hart, S. Games in extensive and strategic forms. In Handbook of Game Theory with Economic Applications; Elsevier: Amsterdam, The Netherlands, 1992; Chapter 2; Volume 2, pp. 19–40. [Google Scholar]
- Lasaulce, S.; Tembine, H. Moving from Static to Dynamic Games. In Game Theory and Learning for Wireless Networks; Lasaulce, S., Tembine, H., Eds.; Academic Press: Oxford, UK, 2011; Chapter 3; pp. 69–113. [Google Scholar]
- Müller, M. Global and local game tree search. Inf. Sci. 2001, 135, 187–206. [Google Scholar] [CrossRef]
- Rosenberg, D.; Vieille, N. Zero-sum games with ambiguity. Games Econ. Behav. 2019, 117, 238–249. [Google Scholar] [CrossRef]
- Berg, K. Set-valued games and mixed-strategy equilibria in discounted supergames. Discret. Appl. Math. 2019, 255, 1–14. [Google Scholar] [CrossRef]
- Luo, T.; Kanhere, S.S.; Das, S.K.; Tan, H.P. Incentive mechanism design for heterogeneous crowdsourcing using all-pay contests. IEEE Trans. Mob. Comput. 2016, 15, 2234–2246. [Google Scholar] [CrossRef]
- Xie, H.; Lui, J.; Jiang, J.W.; Chen, W. Incentive mechanism and protocol design for crowdsourcing systems. In Proceedings of the 2014 52nd Annual Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, IL, USA, 30 September–3 October 2014; pp. 140–147. [Google Scholar]
- Li, X.; Zhu, Q. Social Incentive Mechanism Based Multi-User Sensing Time Optimization in Co-Operative Spectrum Sensing with Mobile Crowd Sensing. Sensors 2018, 18, 250. [Google Scholar] [CrossRef]
- Yang, S.; Wu, F.; Tang, S.; Gao, X.; Yang, B.; Chen, G. On designing data quality-aware truth estimation and surplus sharing method for mobile crowdsensing. IEEE J. Sel. Areas Commun. 2017, 35, 832–847. [Google Scholar] [CrossRef]
- Jin, H.; Su, L.; Nahrstedt, K. Theseus: Incentivizing truth discovery in mobile crowd sensing systems. In Proceedings of the 18th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Chennai, India, 10–14 July 2017. [Google Scholar]
- Jiang, C.; Gao, L.; Duan, L.; Huang, J. Scalable mobile crowdsensing via peer-to-peer data sharing. IEEE Trans. Mob. Comput. 2018, 17, 898–912. [Google Scholar] [CrossRef]
- Li, M.; Lin, J.; Yang, D.; Xue, G.; Tang, J. QUAC: Quality-Aware Contract-Based Incentive Mechanisms for Crowdsensing. In Proceedings of the 2017 IEEE 14th International Conference on Mobile Ad Hoc and Sensor Systems (MASS), Orlando, FL, USA, 22–25 October 2017; pp. 72–80. [Google Scholar]
- Cheung, M.H.; Hou, F.; Huang, J. Delay-Sensitive Mobile Crowdsensing: Algorithm Design and Economics. IEEE Trans. Mob. Comput. 2018, 17, 2761–2774. [Google Scholar] [CrossRef]
- Peng, J.; Zhu, Y.; Shu, W.; Wu, M.Y. When data contributors meet multiple crowdsourcers: Bilateral competition in mobile crowdsourcing. Comput. Netw. 2016, 95, 1–14. [Google Scholar] [CrossRef]
- Luo, S.; Sun, Y.; Ji, Y.; Zhao, D. Stackelberg Game Based Incentive Mechanisms for Multiple Collaborative Tasks in Mobile Crowdsourcing. Mob. Netw. Appl. 2016, 1–17. [Google Scholar] [CrossRef]
- Duan, L.; Kubo, T.; Sugiyama, K.; Huang, J.; Hasegawa, T.; Walrand, J. Incentive mechanisms for smartphone collaboration in data acquisition and distributed computing. In Proceedings of the 2012 Proceedings IEEE INFOCOM, Orlando, FL, USA, 25–30 March 2012; pp. 1701–1709. [Google Scholar]
- Jaimes, L.G.; Chakeri, A.; Lopez, J.; Raij, A. A cooperative incentive mechanism for recurrent crowd sensing. In Proceedings of the SoutheastCon 2015, Fort Lauderdale, FL, USA, 9–12 April 2015; pp. 1–5. [Google Scholar]
- Dong, X.; Zhang, X.; Yi, Z.; Peng, Y. Incentive Mechanism for Crowdsensing Platforms Based on Multi-leader Stackelberg Game. In Proceedings of the International Conference on Communicatins and Networking in China, Chongqing, China, 24–26 September 2016; pp. 138–147. [Google Scholar]
- Xu, Y.; Zhou, Y.; Mao, Y.; Chen, X.; Li, X. Can Early Joining Participants Contribute More?-Timeliness Sensitive Incentivization for Crowdsensing. arXiv 2017, arXiv:1710.01918. [Google Scholar]
- Yang, G.; He, S.; Shi, Z.; Chen, J. Promoting cooperation by the social incentive mechanism in mobile crowdsensing. IEEE Commun. Mag. 2017, 55, 86–92. [Google Scholar] [CrossRef]
- Goh, D.H.L.; Pe-Than, E.P.P.; Lee, C.S. Perceptions of virtual reward systems in crowdsourcing games. Comput. Hum. Behav. 2017, 70, 365–374. [Google Scholar] [CrossRef]
- Su, Z.; Qi, Q.; Xu, Q.; Guo, S.; Wang, X. Incentive scheme for cyber physical social systems based on user behaviors. IEEE Trans. Emerging Top. Comput. 2020, 8, 92–103. [Google Scholar] [CrossRef]
- Pilloni, V. How Data Will Transform Industrial Processes: Crowdsensing, Crowdsourcing and Big Data as Pillars of Industry 4.0. Future Internet 2018, 10, 24. [Google Scholar] [CrossRef]
- Hu, Q.; Wang, S.; Bie, R.; Cheng, X. Social Welfare Control in Mobile Crowdsensing Using Zero-Determinant Strategy. Sensors 2017, 17, 1012. [Google Scholar] [CrossRef]
- Adami, C.; Hintze, A. Evolutionary instability of zero-determinant strategies demonstrates that winning is not everything. Nat. Commun. 2013, 4, 2193. [Google Scholar] [CrossRef]
- Pita, J.; Jain, M.; Ordóñez, F.; Tambe, M.; Kraus, S.; Magori-Cohen, R. Effective solutions for real-world stackelberg games: When agents must deal with human uncertainties. In Proceedings of the 8th International Conference on Autonomous Agents and Multiagent Systems, Budapest, Hungary, 10–15 May 2009. [Google Scholar]
- Paruchuri, P.; Pearce, J.P.; Marecki, J.; Tambe, M.; Ordonez, F.; Kraus, S. Playing games for security: An efficient exact algorithm for solving Bayesian Stackelberg games. In Proceedings of the 7th International Joint Conference on Autonomous Agents and Multiagent Systems, Estoril, Portugal, 12–18 May 2008. [Google Scholar]
- Gal-Or, E. First mover disadvantages with private information. Rev. Econ. Stud. 1987, 54, 279–292. [Google Scholar] [CrossRef]
| Reference | Type of Game | Co-Operation | Information | Pros | Cons |
|---|---|---|---|---|---|
| [97] | Bayesian game | Non-co-operative | Incomplete | Considered asymmetric users | Arbitrary selection with allpay auction |
| [98] | Repeated game | Non-co-operative | Incomplete | Recruitment of specific task expertees | Requestors forced to pay for poor service |
| [99] | Coalition game | Yes | Complete | Energy, cost effective sensing | Truthfulness in reputation is left as future work |
| [100] | Co-operative game between-user and platform | Yes | Incomplete | Budget depend on quality of data obtained | Assumes every device have equal sensing capabilities |
| [101] | Thesus (based on Bayesian-Nash equilibrium) | Non-co-operative | Complete and Incomplete | Incentives are based on effort, truthfulness | Believed that efforts exerted by user is same for every task |
| [102] | CSRS (Non-co-operative game) | Non co-operative | Complete | Adaptable for crowded tasks | Believed transmission cost is same for all |
| [103] | Stackelberg Game | Non-co-operative | Complete and Incomplete | Maximum User Utility on par with Platform | Assumes all users target for longterm gains |
| [104] | Stackelberg Game | Non-co-operative | Incomplete | Uses WiFi to reduce cost | Not considered user trustworthiness |
| [105] | Evolutionary game | Non-co-operative | Incomplete | Examined dynamic nature of users | Data reporting delay may occur due late convergence |
| [106] | Stackelberg game | Yes | Complete and Incomplete | Effective online incentive mechanisms | Considered sensing cost for any task is equal |
| [107] | Stackelberg game | Yes | Complete, Symmetrically, Asymmetrically Incomplete | Various Incentive mechanisms for CrowdSensing, computing | Not considered negligence of users while sensing the information |
| [108] | One-shot repeated game | Yes | Complete | Low sensing cost with adequate users | All users in sensing campaign receive part of payments |
| [109] | Multi-leader Stackelberg game | Non-co-operative | Incomplete | Analyzes pricing competition between crowd sourcers | Not considered resource variation among crowd sourcers |
| [110] | Stackelberg Bayesian game | Non-co-operative | Complete and Incomplete | Promotes early contributions | Agressive payments |
| [111] | Three stage stackelberg game | Yes | Complete | Promotes co-operation with low cost | Relies largely on social relationships of users |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dasari, V.S.; Kantarci, B.; Pouryazdan, M.; Foschini, L.; Girolami, M. Game Theory in Mobile CrowdSensing: A Comprehensive Survey. Sensors 2020, 20, 2055. https://doi.org/10.3390/s20072055
Dasari VS, Kantarci B, Pouryazdan M, Foschini L, Girolami M. Game Theory in Mobile CrowdSensing: A Comprehensive Survey. Sensors. 2020; 20(7):2055. https://doi.org/10.3390/s20072055
Chicago/Turabian StyleDasari, Venkat Surya, Burak Kantarci, Maryam Pouryazdan, Luca Foschini, and Michele Girolami. 2020. "Game Theory in Mobile CrowdSensing: A Comprehensive Survey" Sensors 20, no. 7: 2055. https://doi.org/10.3390/s20072055
APA StyleDasari, V. S., Kantarci, B., Pouryazdan, M., Foschini, L., & Girolami, M. (2020). Game Theory in Mobile CrowdSensing: A Comprehensive Survey. Sensors, 20(7), 2055. https://doi.org/10.3390/s20072055








