Adaptive Real-Time Routing Protocol for (m,k)-Firm in Industrial Wireless Multimedia Sensor Networks †
Abstract
1. Introduction
- To recognize the shortcomings or limitations of QoS routing protocol in WMSN, we provide a comprehensive survey that investigates state-of-the-art research work and further research directions for applying application specific requirement to the QoS routing protocol.
- To overcome the problem of general routing protocol considering deadline, we take (m,k)-firm based routing protocol while considering application requirements which is modeled by (m,k)-firm stream together.
- Unlike most of existing approaches which are based on (m,k)-firm stream, we propose a new adaptive path selection and traffic shaping algorithm.
- The proposed scheme is compared to existing (m,k)-firm based QoS routing protocols. Through various simulations, we prove that the proposed approach can reduce the dynamic failure ratio without regard to the background traffic as well as extend network lifetime.
2. Related Work
2.1. Wireless Multimedia Sensor Networks and Its Applications
2.2. Real-Time Routing Protocols
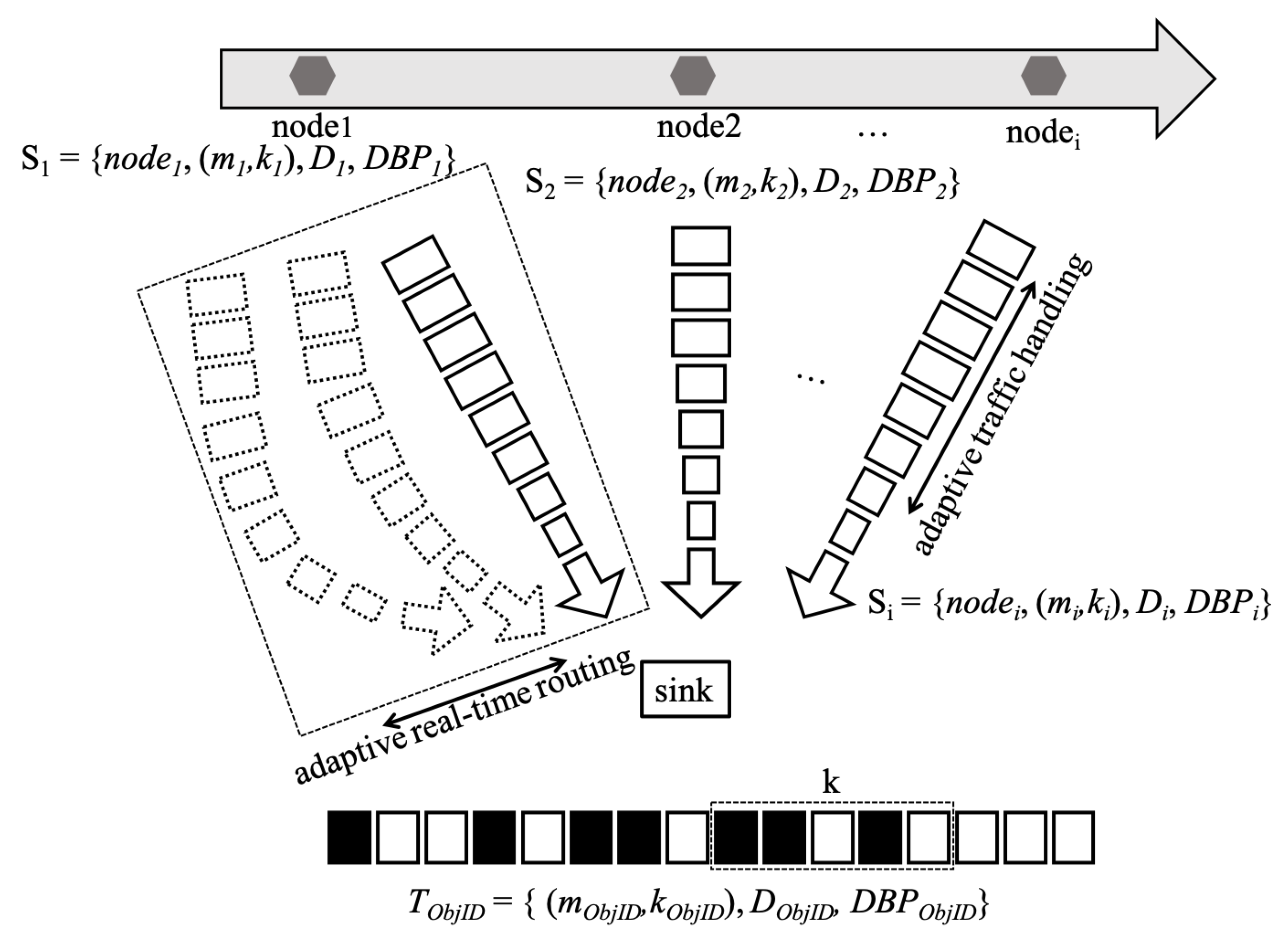
3. Adaptive Real-Time Routing Protocol
3.1. Real-Time Model
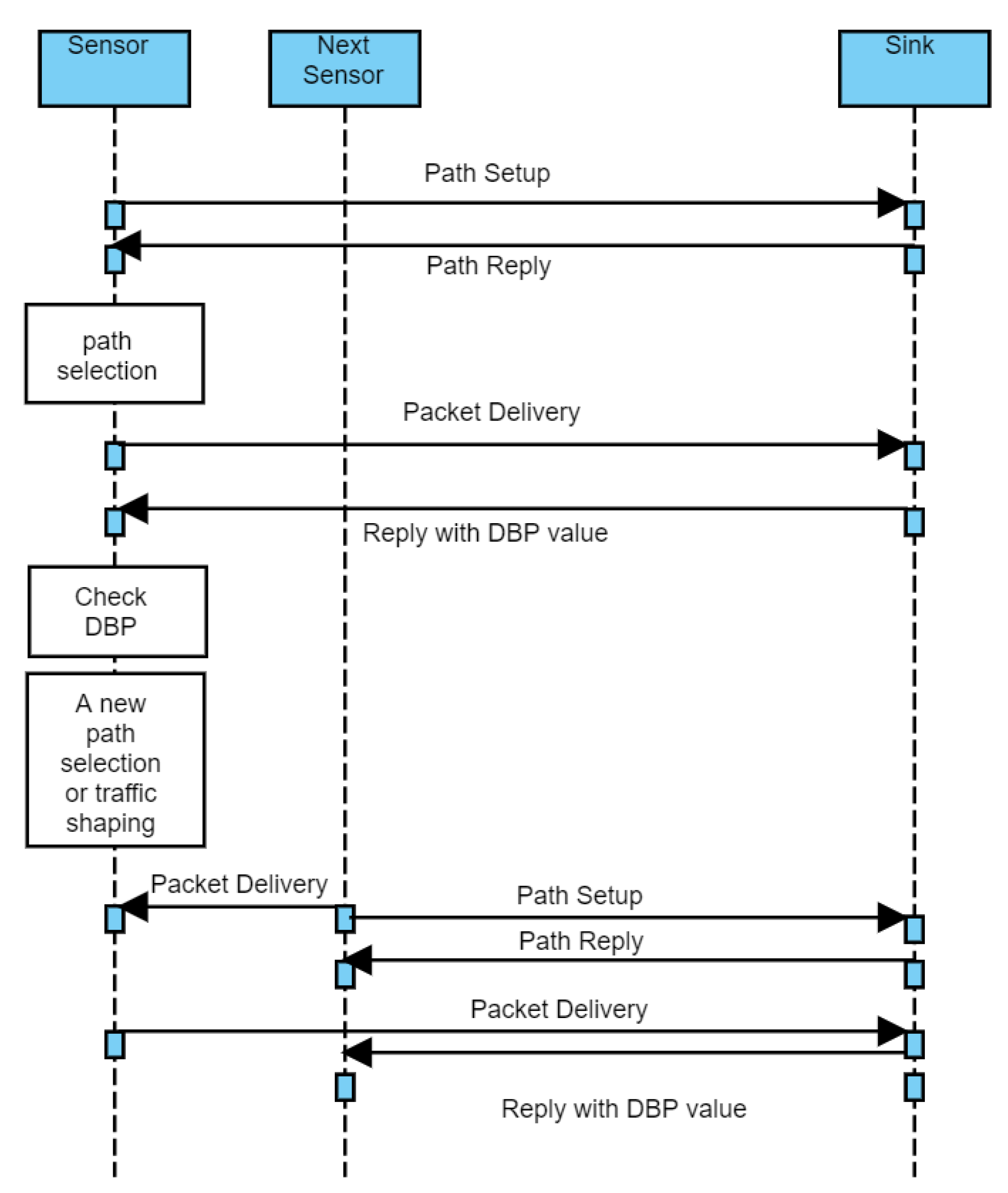
3.2. Adaptive QoS Routing Protocol
| Algorithm 1 Adaptive QoS routing protocol for packet transmission from node i to the sink. | |
| 1: n← Number of available real-time paths | |
| 2: ← Path between node i and the sink where its end-to-end delay is bounded within | ▹ |
| has the shortest delay whereas has the longest delay, ≤≤ … ≤ | |
| 3: n← Path_Search_Probing(i,sink) | ▹ Obtain number of possible multiple paths from node i and sink |
| 4: Transmit packets along | ▹ Packets are transmitted along the longest end-to-end delay in |
| 5: for every do | ▹ After obtaining value of |
| 6: if ≥ 0 then | ▹ If application stream meets the requirement |
| 7: if < 0 then | ▹ If the session stream is not meeting the requirment |
| 8: if > 0 then | |
| 9: Transmit packets along | ▹ Change the path along alternative with the next |
| longest delay if possible | |
| 10: else | |
| 11: Maintain | ▹ Current path is maintain if no alternative is available |
| 12: end if | |
| 13: end if | |
| 14: else | ▹ If application stream doesn’t meet the requirement, more complex path selection |
| algorithm is performed | |
| 15: t← | + | | ▹ Compute how many distance from positive status with two |
| DBP values | |
| 16: if ≥ 0 then | ▹ if current session meets the requirement |
| 17: if > 0 then | ▹ if an available path exists |
| 18: Transmit packets along | ▹ Change alternative path among multiple paths. |
| Adaptive approach in the aspects of session | |
| 19: else | |
| 20: Transmit packets along | ▹ Change path with the shortest end-to-end delay in case |
| of two requirements missing | |
| 21: end if | |
| 22: else | ▹ if current session and application don’t meet the requirement at the same time. This is |
| the worst case | |
| 23: if t < Threshold then | ▹ Distance is not bounded within the threshold |
| 24: Transmit packets along | ▹ Change the path with the shortest end-to-end delay |
| 25: else | |
| 26: Transmit packets along | ▹ Change the path according to distance to |
| meeting status | |
| 27: end if | |
| 28: end if | |
| 29: end if | |
| 30: end for | |
3.3. Adaptive Traffic Handling
| Algorithm 2 Adaptive Traffic Handling at node i. | |
| 1: ← DBP value of node i at time t | |
| 2: e← Current index in {, ), …(, } | ▹ The larger index means the looser (m,k)-firm requirement |
| 3: k← Parameter to reduce packet size | |
| 4: if < 0 then | |
| 5: if < 0 then | ▹ if two consecutive DBP values are negative |
| 6: if e != s then | ▹ If any available traffic set for (m,k) is available |
| 7: (, ) = (, ) | ▹ Change traffic set for next loose (m,k) |
| 8: else | ▹ If any available traffic set for (m,k) is not available |
| 9: (, ) = (, ) | ▹ Set the traffic as the least (m,k) requirement |
| 10: ← × | ▹ Traffic shaping by reducing packet size |
| 11: Payload_Size_Changed == TURE | ▹ Set the flag |
| 12: end if | |
| 13: else | ▹ if only one DBP values are negative |
| 14: (, ) = (, ) | ▹ Set the traffic as the next strict (m,k) requirement |
| 15: end if | |
| 16: else | ▹ If the second DBP value become postive |
| 17: if > 0 then | |
| 18: if e == s && Packet_Size_Changed == TURE then | ▹ If the current set index is the largest |
| value | |
| 19: ← × k | ▹ Restore the packet size |
| 20: end if | |
| 21: else | |
| 22: (, ) = (, ) | ▹ Set the traffic as the next strict (m,k) requirement |
| 23: end if | |
| 24: end if | |
- If the two values are negative as shown in lines 3 and 4, the current requirements of (, ) are relaxed to (, ), where the current index does not reach the maximum value. This is to allow more missed packets in by loosing (m,k)-firm requirement. This kind of adjustment is available when any subset is available. Otherwise, if the current index is the maximum, another approach to reduce the payload size is applied.
- If the second DBP value becomes positive, the index for (, ) increases to make current (m,k)-firm requirement strict because packet delay is not passed beyond deadline. This is, recovery procedure is invoked according to current positive DBP value.
- If the two consecutive DBP values are positive, two different tasks are performed according to the current index according to current index value. If the current index reaches the maximum value and the packet size is changed, the previous payload size is restored. Otherwise, (, ) is set to close to (, ) by decreasing the index number.
- If the DBP value becomes positive every time, the algorithm for adaptive traffic handling is not executed because the (, )-firm requirement is met by adaptive QoS routing.
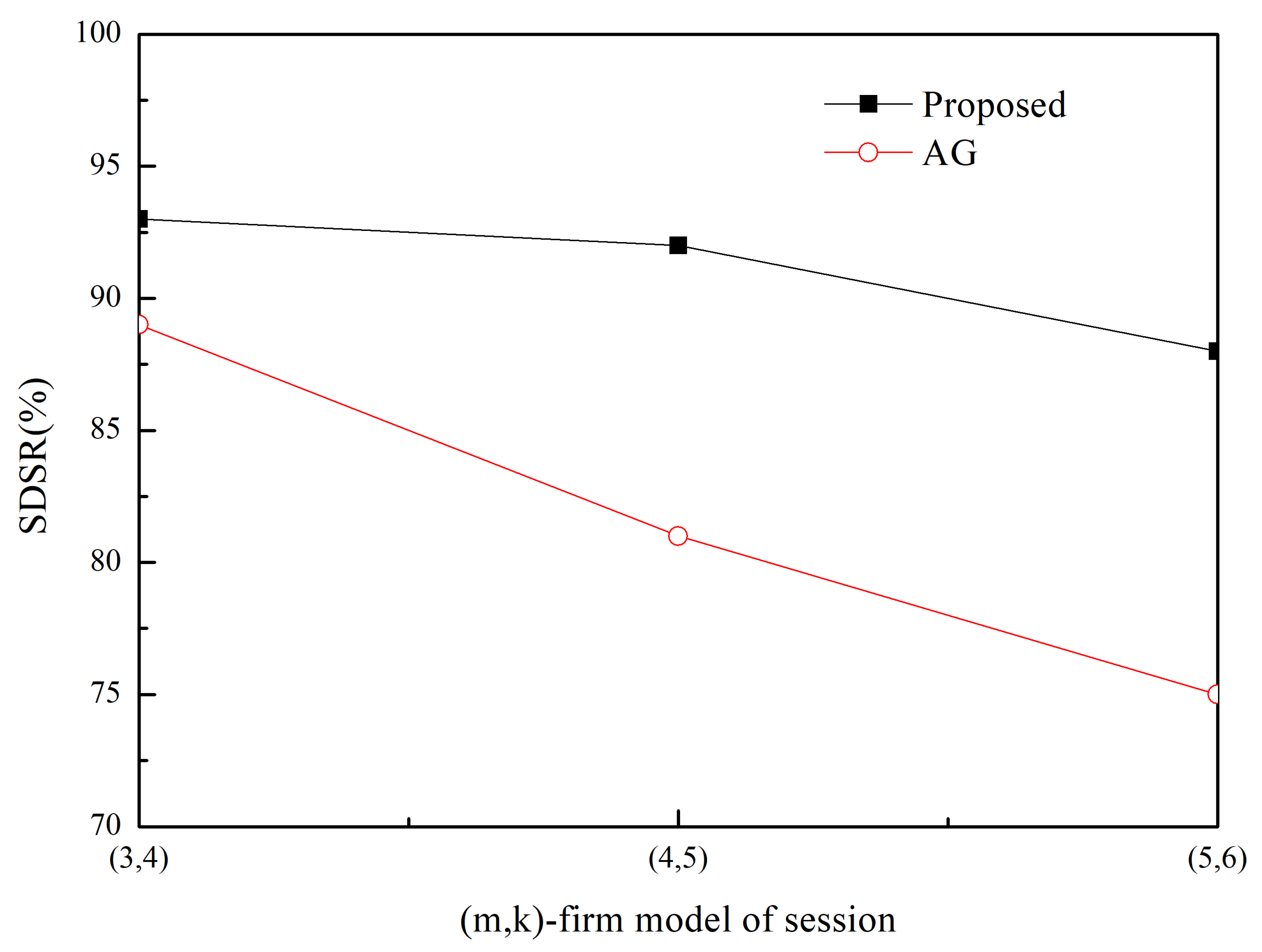
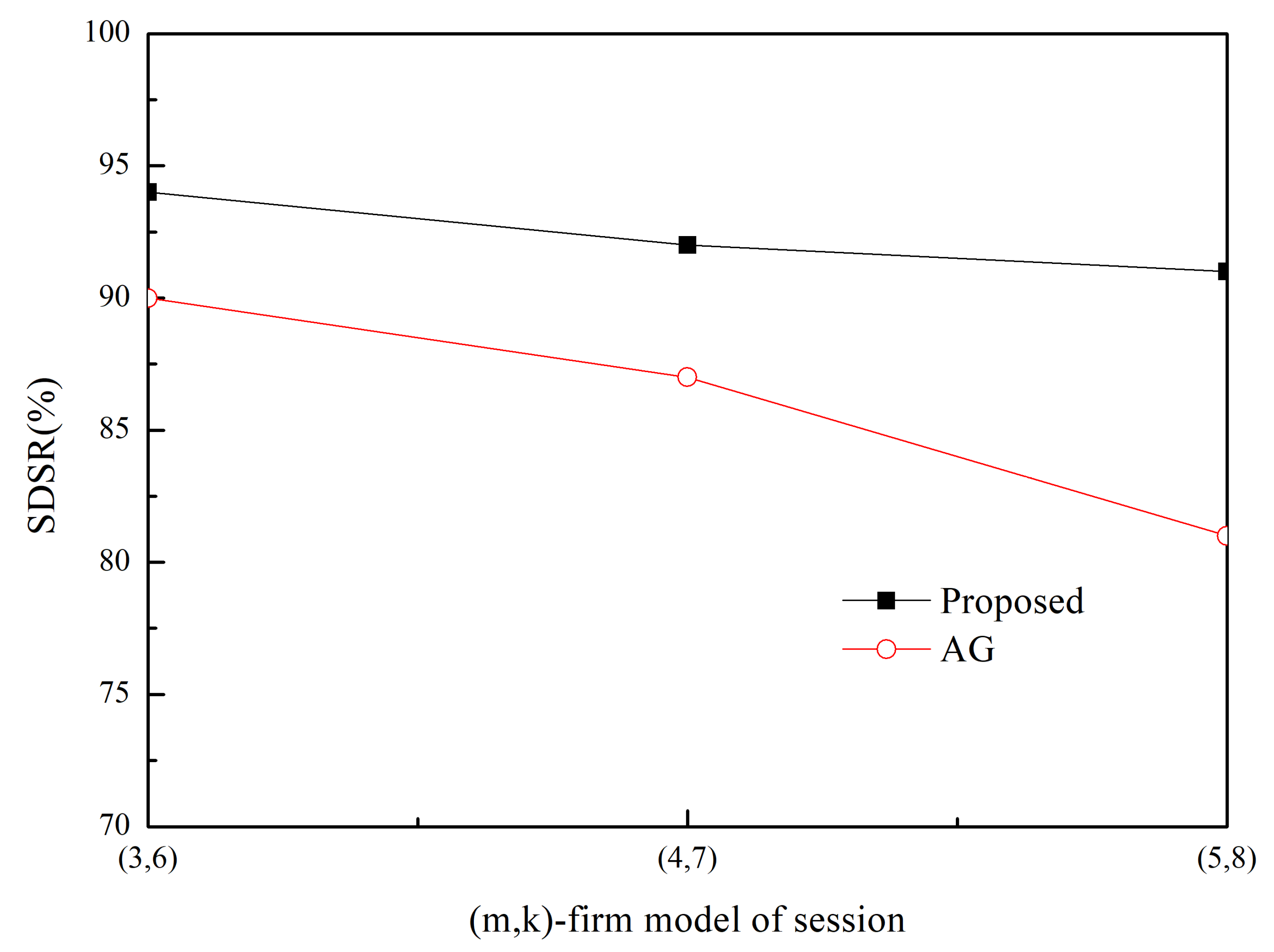
4. Performance Evaluation
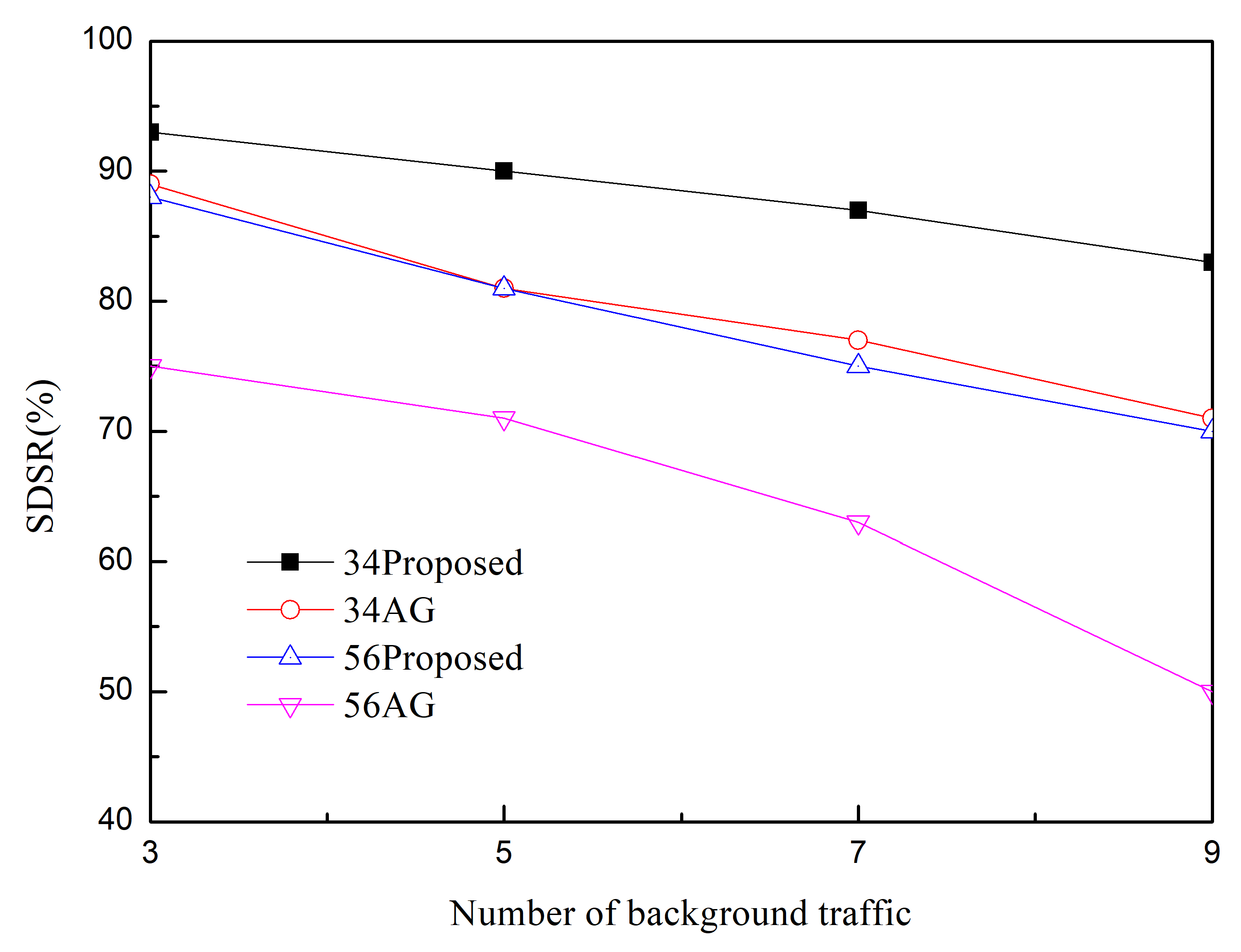
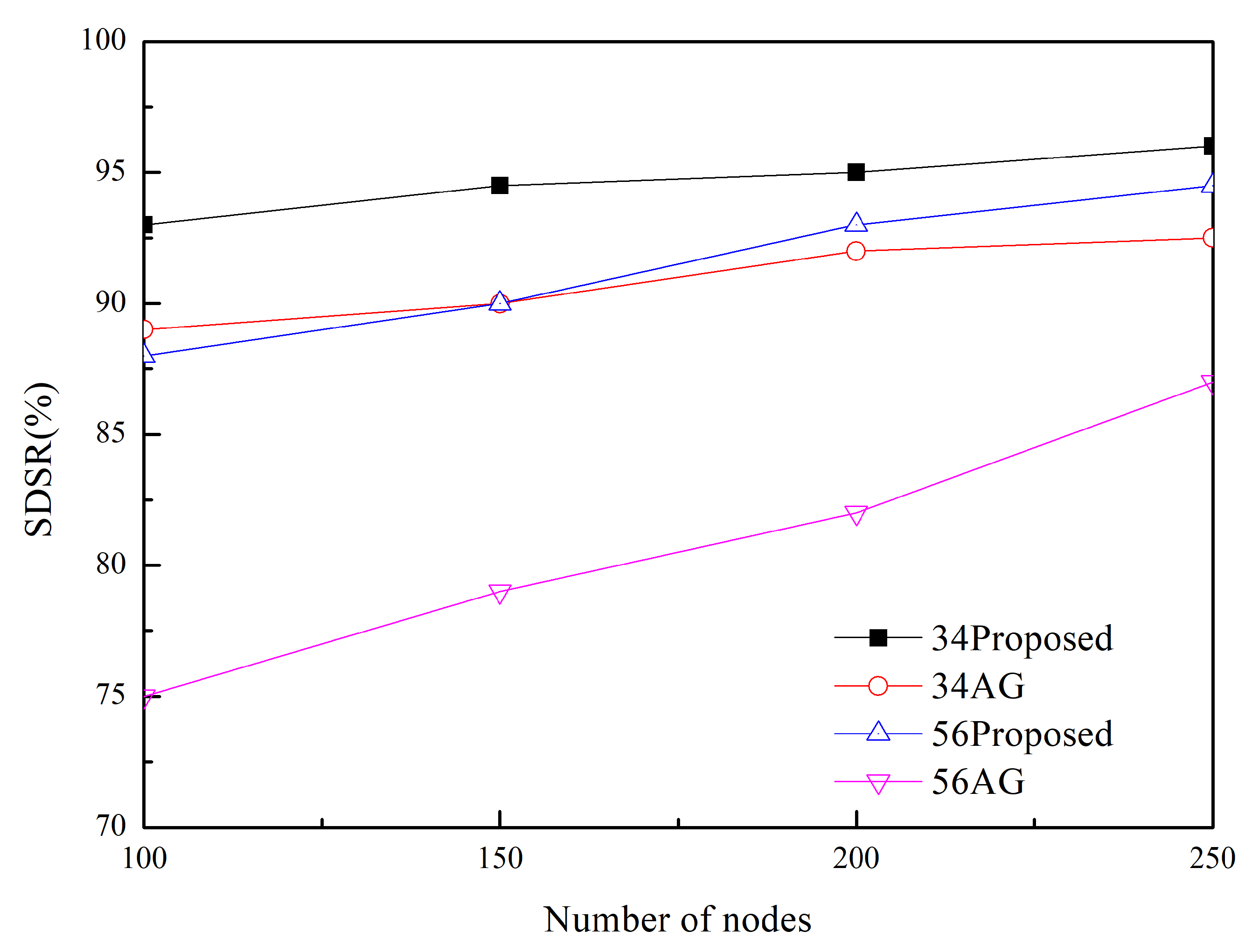
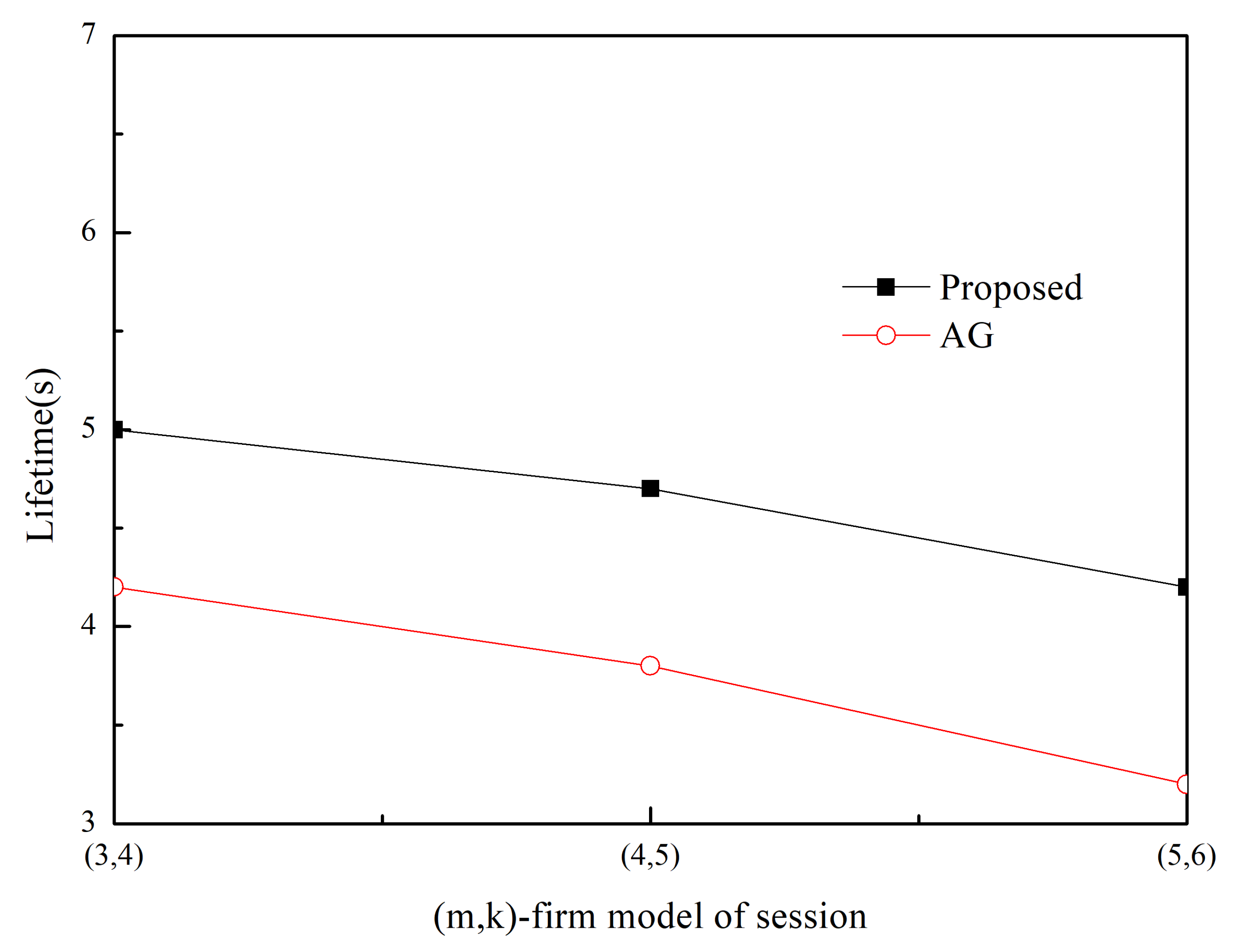
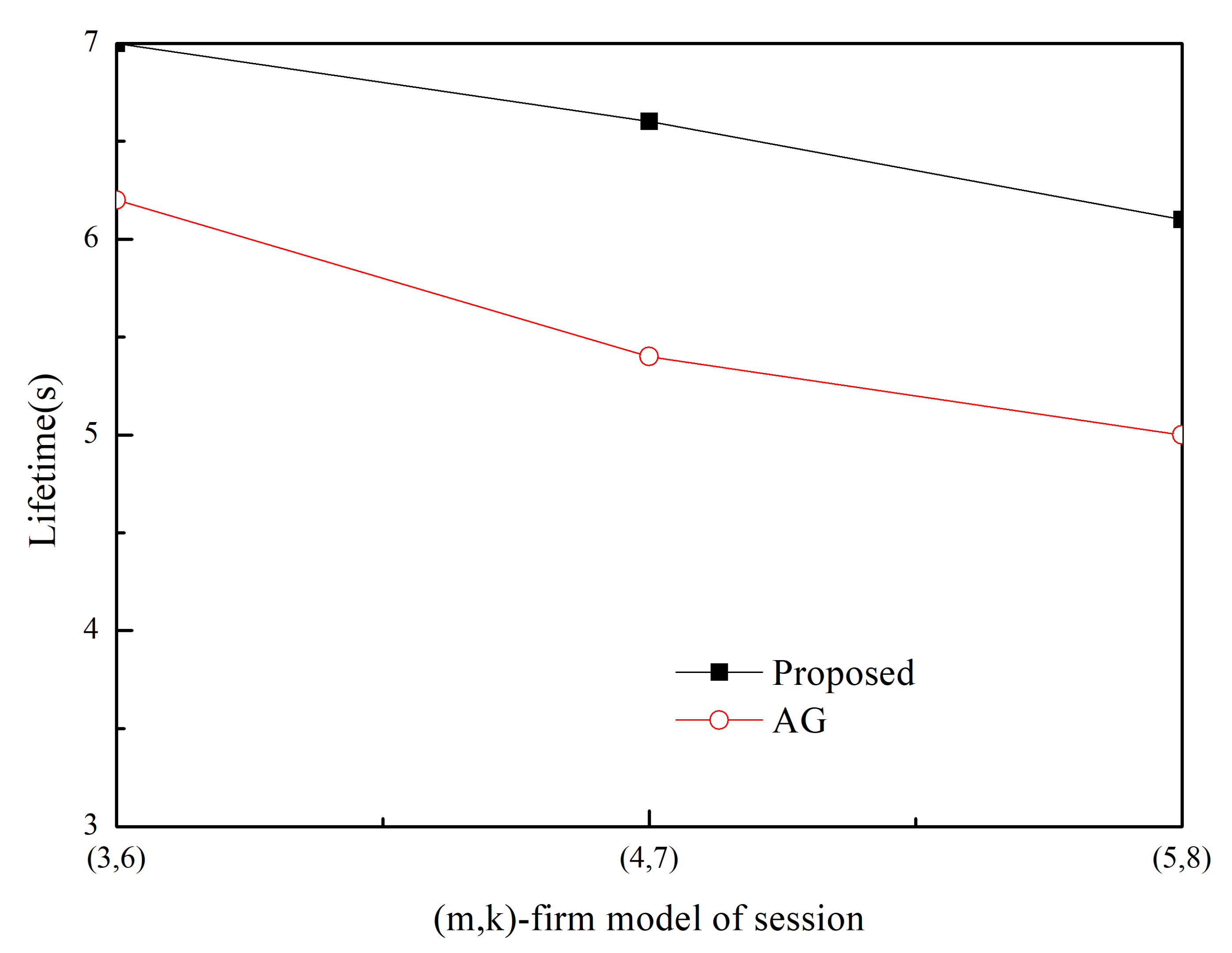
Simulation Results
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Hayat, M.; Khan, H.; Iqbal, Z.; Rahman, Z.; Tahir, M. Multimedia sensor networks: Recent trends, research challenges and future directions. In Proceedings of the International Conference on Communication, Computing and Digital Systems, Islamabad, Pakistan, 8–9 March 2017. [Google Scholar]
- Gungor, V.; Hancke, G. Industrial Wireless Sensor Networks: Challenges, Design Principles, and Technical Approaches. IEEE Trans. Ind. Electron. 2009, 56, 4258–4265. [Google Scholar] [CrossRef]
- Alanazi, A.; Elleithy, K. Real-Time QoS Routing Protocols in Wireless Multimedia Sensor Networks: Study and Analysis. Sensors 2015, 15, 22209–22233. [Google Scholar] [CrossRef] [PubMed]
- Shen, H.; Bai, G. Routing in wireless multimedia sensor networks: A survey and challenges ahead. J. Netw. Comput. Appl. 2016, 71, 30–49. [Google Scholar] [CrossRef]
- Bhandary, V.; Malik, A.; Kumar, S. Routing in Wireless Multimedia Sensor Networks: A Survey of Existing Protocols and Open Research Issues. J. Eng. 2016, 2016, 27. [Google Scholar] [CrossRef]
- Hamdaoui, M.; Ramanathan, P. A dynamic priority assignment technique for streams with (m,k)-firm deadlines. IEEE Trans. Comput. 1995, 44, 1443–1451. [Google Scholar] [CrossRef]
- Li, B.; Kim, K. An-firm real-time aware fault-tolerant mechanism in wireless sensor networks. Int. J. Distrib. Sens. Netw. 2012, 20, 719–731. [Google Scholar] [CrossRef]
- Kafi, M.; Challal, Y.; Djenouri, D.; Doudou, M.; Bouabdallah, A.; Badache, N. A Study of Wireless Sensor Networks for Urban Traffic Monitoring: Applications and Architectures. Procedia Comput. Sci. 2013, 19, 617–626. [Google Scholar] [CrossRef]
- Nellore, K.; Gerhard, P. A Survey on Urban Traffic Management System Using Wireless Sensor Networks. Sensors 2016, 16, 157. [Google Scholar] [CrossRef]
- Moreno-Garcia, I.; Palacios-Garcia, E.; Pallares-Lopez, V.; Santiago, I.; Gonzalez-Redondo, M.; Varo-Martinez, M.; Real-Calvo, R. Real-Time Monitoring System for a Utility-Scale Photovoltaic Power Plant. Sensors 2016, 16, 770. [Google Scholar] [CrossRef]
- Campos, A.; Garcia-Valdecasas, J.; Molina, R.; Castillo, C.; Alvarez-Fanjul, E.; Staneva, J. Addressing Long-Term Operational Risk Management in Port Docks under Climate Change Scenarios—A Spanish Case Study. Water 2019, 11, 2153. [Google Scholar] [CrossRef]
- Huo, H.; Xu, Y.; Yan, H.; Mubeen, S.; Zhang, H. An Elderly Health Care System Using Wireless Sensor Networks at Home. In Proceedings of the Third International Conference on Sensor Technologies and Applications, Athens, Greece, 18–23 June 2009. [Google Scholar]
- Velrani, K.S.; Geetha, G. Sensor based healthcare information system. In Proceedings of the IEEE Technological Innovations in ICT for Agriculture and Rural Development (TIAR), Chennai, India, 15–16 July 2016. [Google Scholar]
- Dobslaw, F.; Zhang, T.; Gidlund, M. QoS-Aware Cross-Layer Configuration for Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2009, 12, 1679–1691. [Google Scholar] [CrossRef]
- Sun, W.; Yuan, X.; Wang, J.; Li, Q.; Chen, L.; Mu, D. End-to-End Data Delivery Reliability Model for Estimating and Optimizing the Link Quality of Industrial WSNs. IEEE Trans. Autom. Sci. Eng. 2018, 15, 1127–1137. [Google Scholar] [CrossRef]
- Zhang, W.; Liu, Y.; Han, G.; Feng, Y.; Zhao, Y. An Energy Efficient and QoS Aware Routing Algorithm Based on Data Classification for Industrial Wireless Sensor Networks. IEEE Access 2018, 6, 46495–46504. [Google Scholar] [CrossRef]
- Sarisaray-Bolukand, P.; Akkaya, K. Performance Comparison of Data Reduction Techniques for Wireless Multimedia Sensor Network Applications. Int. J. Distrib. Sens. Netw. 2015, 11, 873495. [Google Scholar] [CrossRef]
- Bavarva, A.; Jani, P.; Ghetiya, K. Performance Improvement of Wireless Multimedia Sensor Networks Using MIMO and Compressive Sensing. J. Commun. Inf. Netw. 2018, 3, 84–90. [Google Scholar] [CrossRef]
- He, T.; Stankovic, J.; Abdelzaher, T.; Lu, C. A spatiotemporal communication protocol for wireless sensor networks. IEEE Trans. Parallel Distrib. Syst. 2005, 16, 995–1006. [Google Scholar] [CrossRef]
- Yu, Z.; Lu, B. A multipath routing protocol using congestion control in wireless multimedia sensor networks. Peer Netw. Appl. 2019, 12, 1585–1593. [Google Scholar] [CrossRef]
- Oh, S.; Yim, Y.; Lee, J.; Park, H.; Kim, S. An opportunistic routing for real-time data in Wireless Sensor Networks. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Shanghai, China, 7–10 April 2013. [Google Scholar]
- Yang, T.; Kim, C.; Kim, S.; Lee, E.; Kim, S. Poster Abstract: Enhanced Real-Time Transmission Using Time Gain in Wireless Sensor Networks. In Proceedings of the 15th ACM/IEEE International Conference on Information Processing in Sensor Networks (IPSN), Vienna, Austria, 11–14 April 2016. [Google Scholar]
- Hasan, M.; Al-Rizzo, H.; Al-Turjman, F. A Survey on Multipath Routing Protocols for QoS Assurances in Real-Time Wireless Multimedia Sensor Networks. IEEE Commun. Surv. Tutor. 2017, 19, 1424–1456. [Google Scholar] [CrossRef]
- Park, J.; Jo, M.; Seong, D.; Yoo, J. Disjointed Multipath Routing for Real-Time Data in Wireless Multimedia Sensor Networks. Int. J. Distrib. Sens. Netw. 2014, 10, 783697. [Google Scholar] [CrossRef]
- Deepaa, O.; Sugnuab, J. An optimized QoS-based clustering with multipath routing protocol for Wireless Sensor Networks. J. King Saud. Univ. Comp. Inf. Sci. 2017, 9. [Google Scholar] [CrossRef]
- Kim, S.; Kim, B.; Kim, K.H.; Kim, K.I. Opportunistic Multipath Routing in Long-Hop Wireless Sensor Networks. Sensors 2019, 19, 4072. [Google Scholar] [CrossRef] [PubMed]
- Kim, K.; Sung, T. Cross-Layered Approach for (m,k)-Firm Stream in Wireless Sensor Networks. Wirel. Pers. Commun. 2013, 68, 1883–1902. [Google Scholar] [CrossRef]
- Li, B.; Kim, K. A novel real-time scheme for (m,k)-firm streams in wireless sensor networks. Wirel. Netw. 2014, 20, 719–731. [Google Scholar] [CrossRef]
- Kim, B.; Park, H.; Kim, K.; Godfrey, D.; Kim, K. A Survey on Real-Time Communications in Wireless Sensor Networks. Wirel. Commun. Mob. Comput. 2017, 2017, 14. [Google Scholar] [CrossRef]
- Lee, J.; Shah, B.; Pau, G.; Prieto, J.; Kim, K. Editorial: Real-Time Communication in Wireless Sensor Networks. Wirel. Commun. Mob. Comput. 2018, 2018, 2. [Google Scholar] [CrossRef]
- Kim, K.; Sung, T. Modeling and Routing Scheme for (m,k)-firm Streams in Wireless Multimedia Sensor Networks. Wirel. Commun. Mob. Comput. 2015, 15, 475–483. [Google Scholar] [CrossRef]
- Lee, C.; Shar, B.; Kim, K. An Architecture for (m,k)-firm Real-Time Streams in Wireless Sensor Networks. Wirel. Netw. 2016, 22, 69–81. [Google Scholar] [CrossRef]
- Azim, M.; Kim, B.; Shah, B.; Kim, K. Real-time routing protocols for (m,k)-firm streams based on multi-criteria in wireless sensor networks. Wirel. Netw. 2017, 23, 1233–1248. [Google Scholar] [CrossRef]
- Park, H.; Kim, B.; Kim, K.; Shah, B.; Kim, K. A Tree Based Broadcast Scheme for (m,k)-firm Real-Time Stream in Wireless Sensor Networks. Sensors 2017, 17, 2578. [Google Scholar] [CrossRef]
- Kim, B.; Aldwairi, M.; Kim, K. An Efficient Real-Time Data Dissemination Multicast Protocol for Big Data in Wireless Sensor Networks. J. Grid Comput. 2019, 17, 341–355. [Google Scholar] [CrossRef]
- Marina, M.; Das, S. Ad hoc on-demand multipath distance vector routing. Wirel. Commun. Mob. Comput. 2006, 6, 969–988. [Google Scholar] [CrossRef]


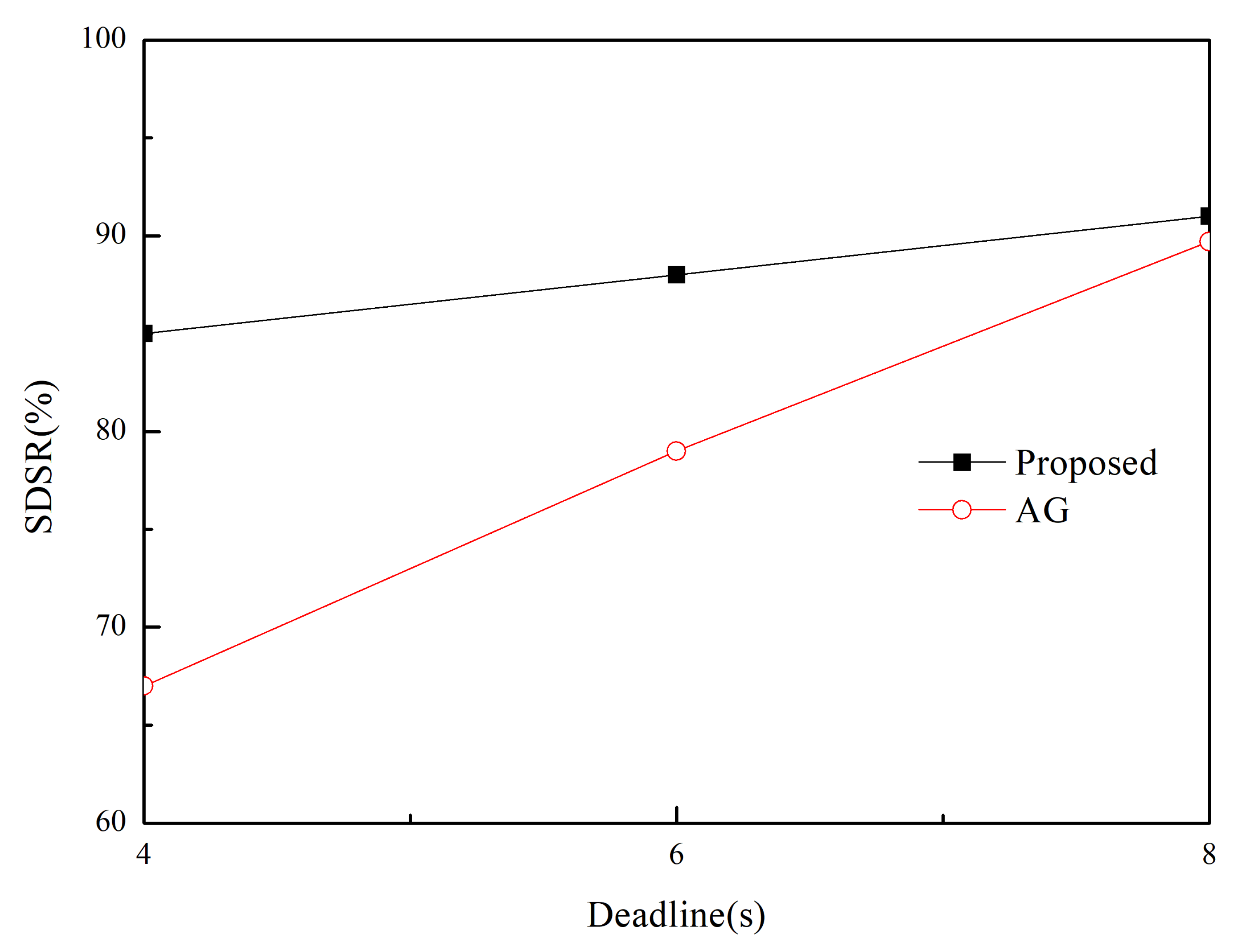
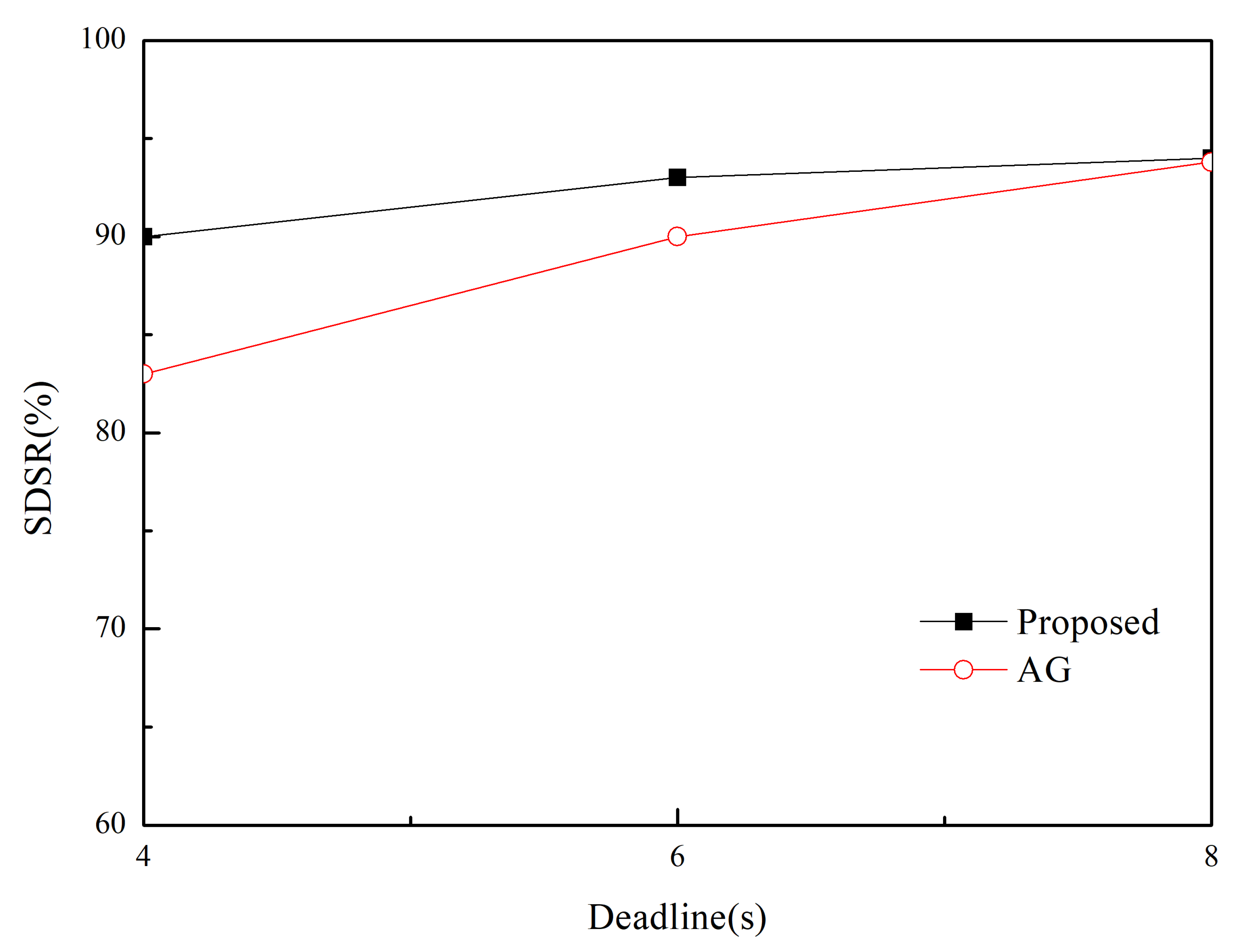
| Parameter | Value(s) |
|---|---|
| Terrain | (1000 m, 1000 m) |
| Number of nodes | 100 Nodes |
| Node placement | Uniform & Random placement |
| Transmission range (m) | 40 m |
| PHY and MAC protocol | 802.15.4 PHY & MAC |
| Bandwidth | 250 Kb/s |
| Payload size | 64 bytes |
| Reduced payload size | 32 bytes |
| Energy consumption (Tx) | 24.92 mJ per 1 byte |
| Energy consumption (Rx) | 19.72 mJ per 1 byte |
| Traffic model | Video traffic |
| Frame Interval Time | 10 frame/s |
| Parameters | (m,k)-Firm Type | Proposed | MK-AG |
|---|---|---|---|
| High Node Density | Strict | High | High |
| Loose | High | Medium | |
| Low Node Density | Strict | High | High |
| Loose | High | Low | |
| Network Lifetime | Strict | Medium | Low |
| Loose | High | Medium | |
| Short Deadline | Strict | Medium | Low |
| Loose | High | Medium | |
| Long Deadline | Strict | High | High |
| Loose | High | High |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, B.-S.; Kim, S.; Kim, K.H.; Sung, T.-E.; Shah, B.; Kim, K.-I. Adaptive Real-Time Routing Protocol for (m,k)-Firm in Industrial Wireless Multimedia Sensor Networks. Sensors 2020, 20, 1633. https://doi.org/10.3390/s20061633
Kim B-S, Kim S, Kim KH, Sung T-E, Shah B, Kim K-I. Adaptive Real-Time Routing Protocol for (m,k)-Firm in Industrial Wireless Multimedia Sensor Networks. Sensors. 2020; 20(6):1633. https://doi.org/10.3390/s20061633
Chicago/Turabian StyleKim, Beom-Su, Sangdae Kim, Kyong Hoon Kim, Tae-Eung Sung, Babar Shah, and Ki-Il Kim. 2020. "Adaptive Real-Time Routing Protocol for (m,k)-Firm in Industrial Wireless Multimedia Sensor Networks" Sensors 20, no. 6: 1633. https://doi.org/10.3390/s20061633
APA StyleKim, B.-S., Kim, S., Kim, K. H., Sung, T.-E., Shah, B., & Kim, K.-I. (2020). Adaptive Real-Time Routing Protocol for (m,k)-Firm in Industrial Wireless Multimedia Sensor Networks. Sensors, 20(6), 1633. https://doi.org/10.3390/s20061633






