An Identity Authentication Method of a MIoT Device Based on Radio Frequency (RF) Fingerprint Technology
Abstract
1. Introduction
2. Related Work
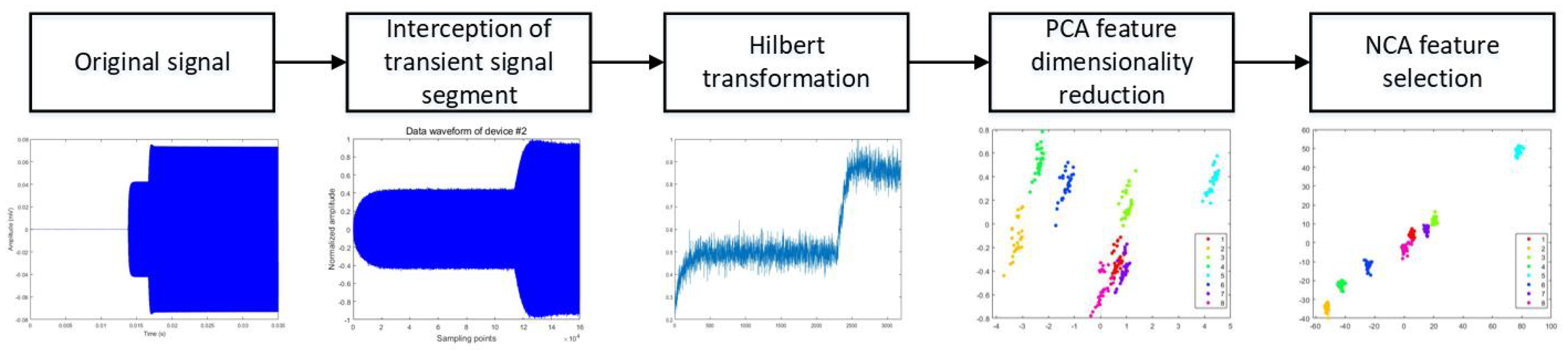
2.1. RF Fingerprint Feature Extraction
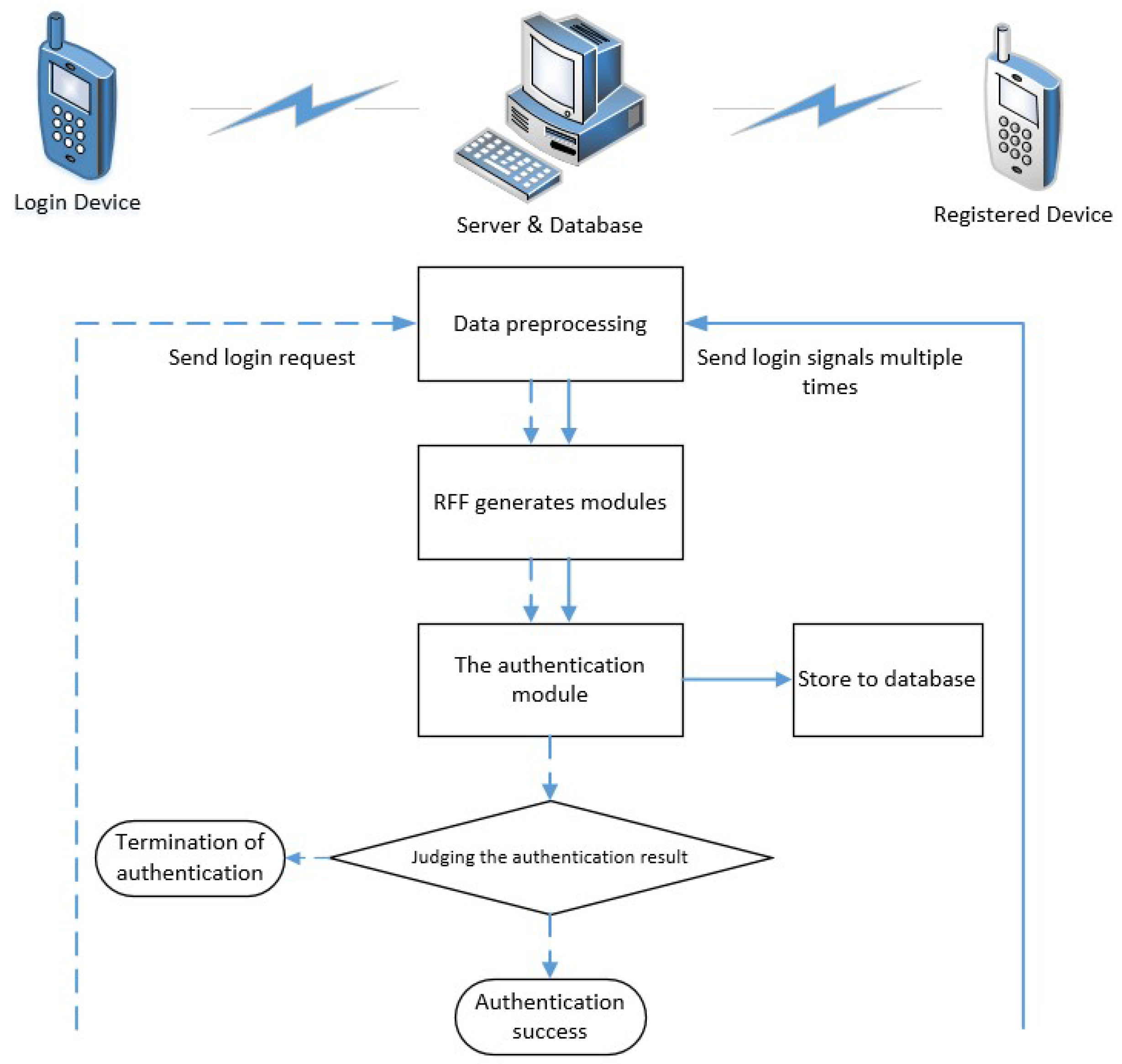
2.2. RF Fingerprint Authentication
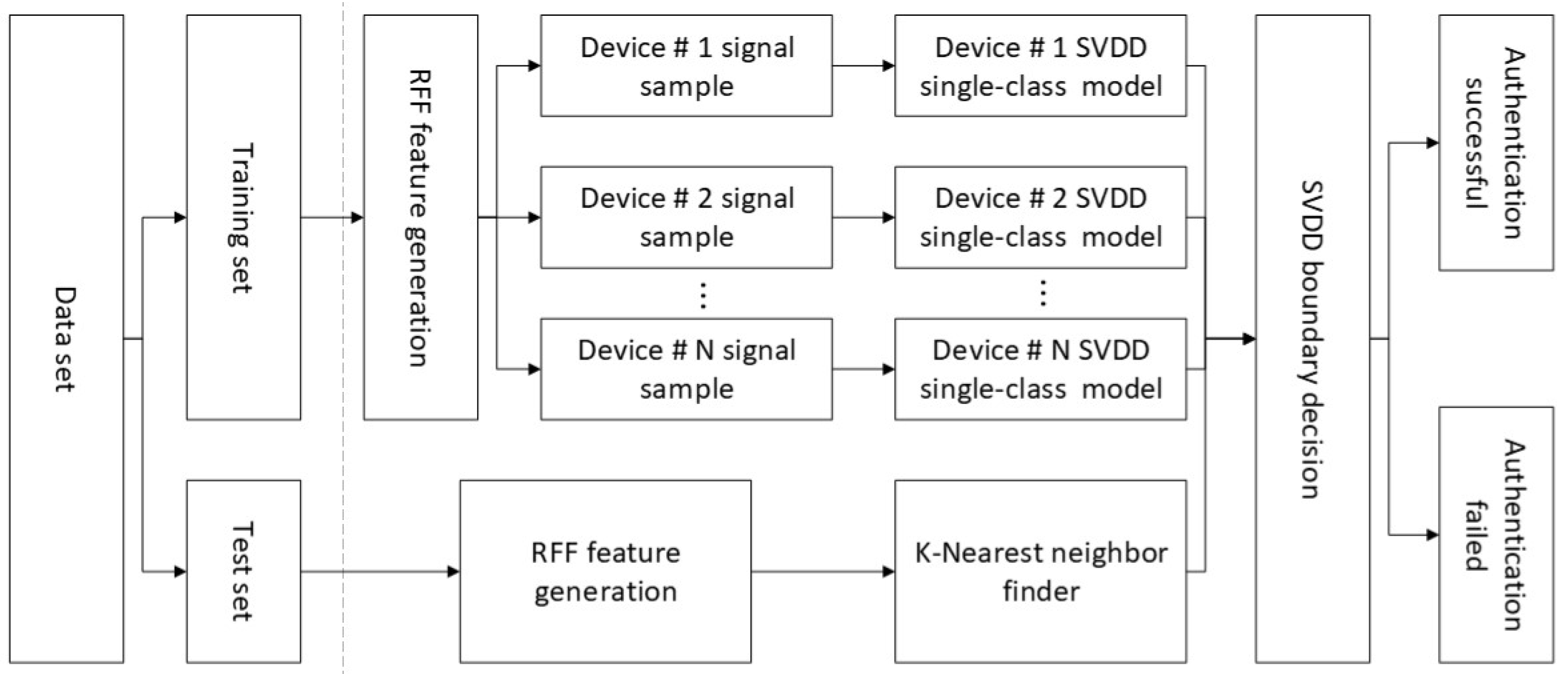
3. Method
3.1. NCA Feature Selection
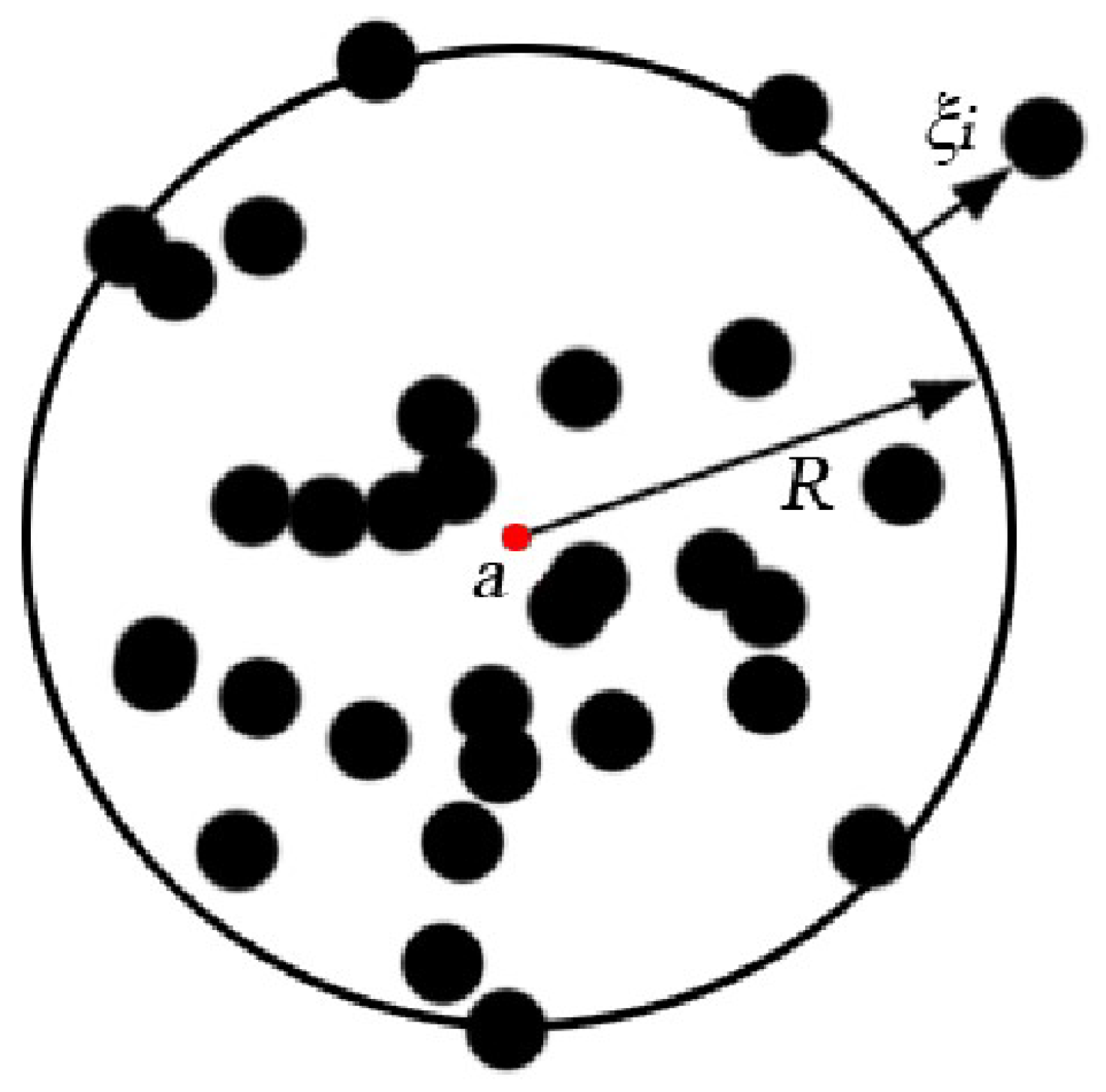
3.2. Support Vector Data Description
3.3. Whale Swarm Optimization Algorithm
4. Experiment
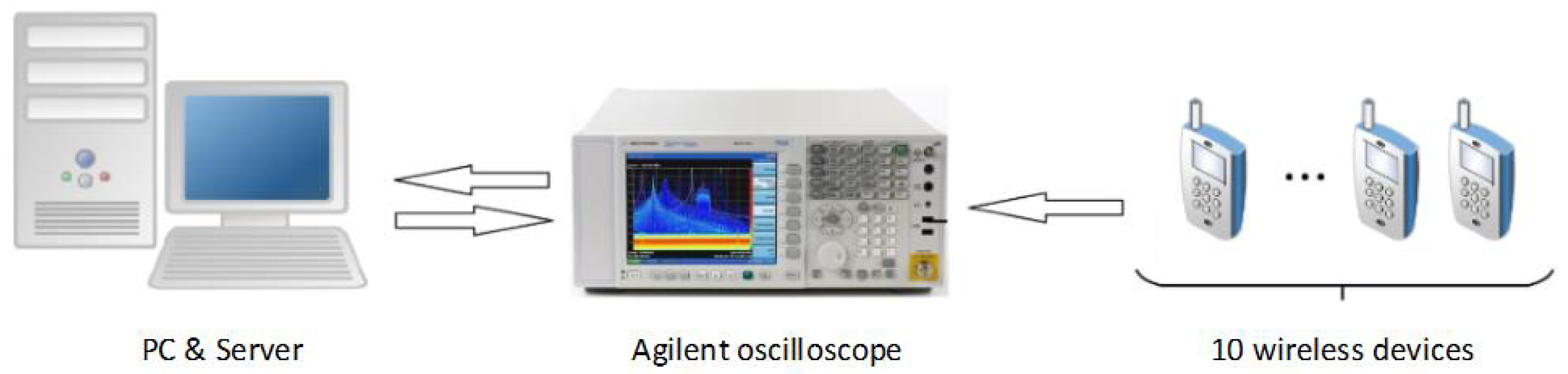
4.1. Experimental Environment and Experimental Devices
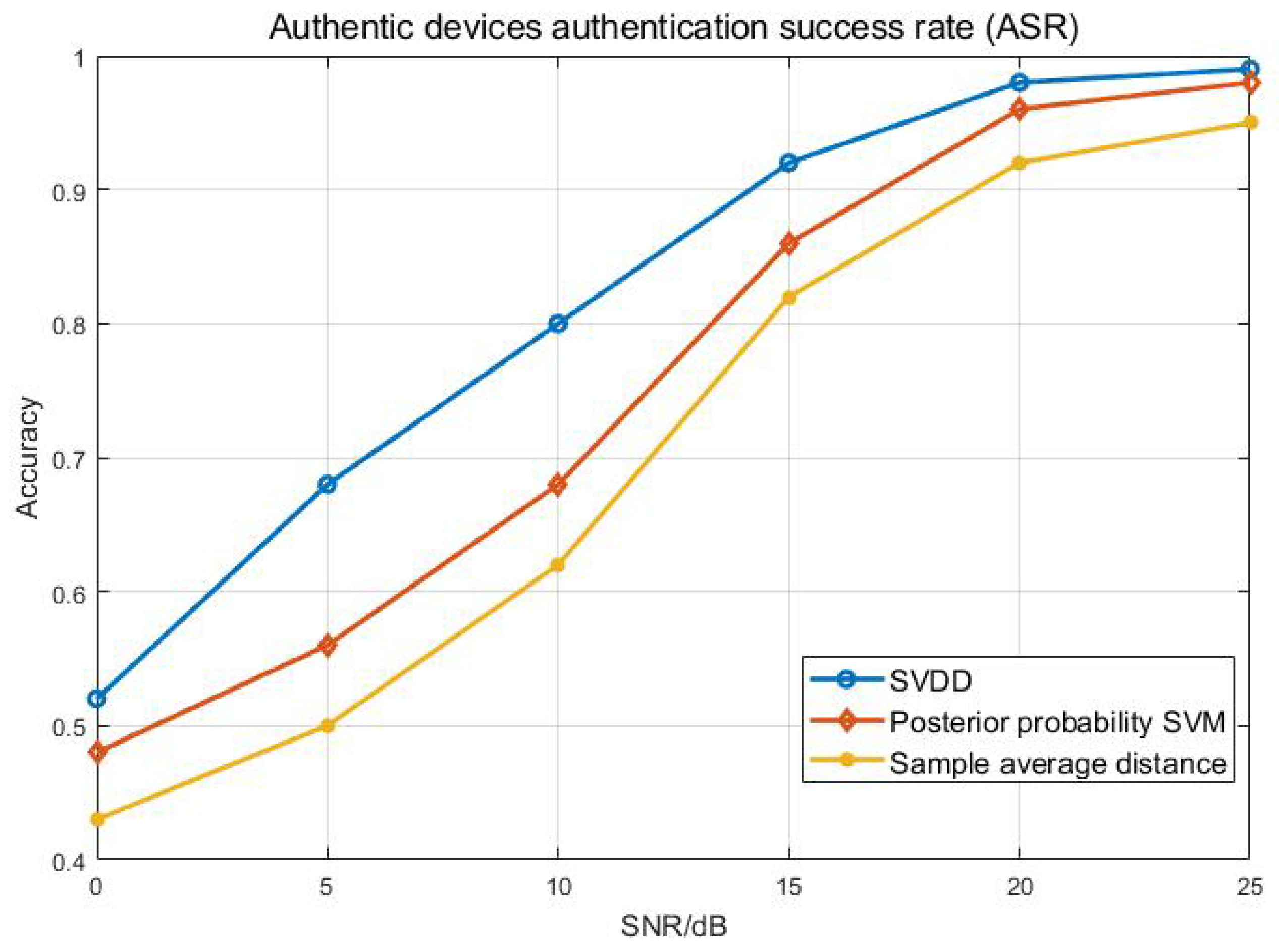
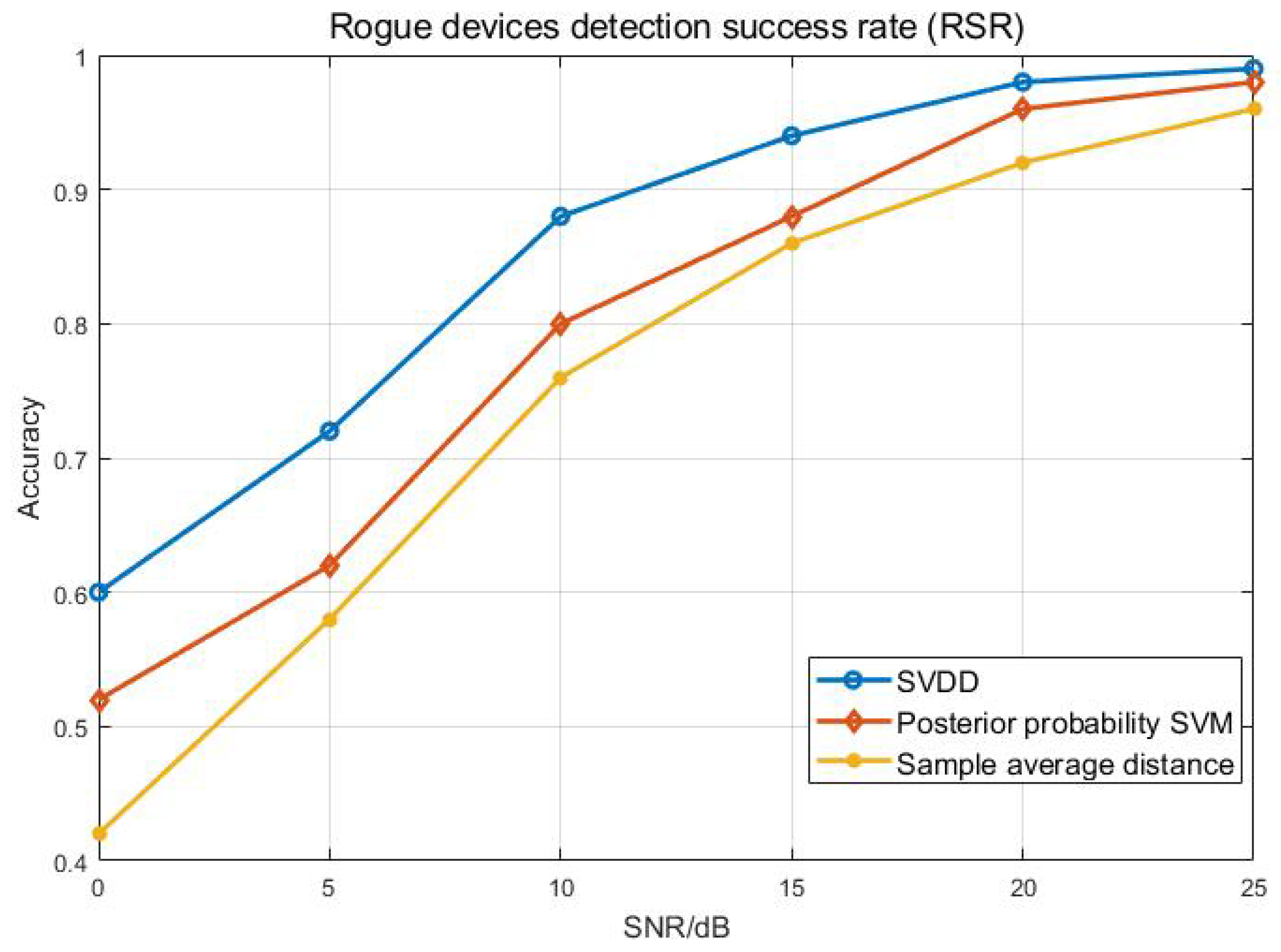
4.2. Simulation Analysis
5. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
References
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Welbourne, E.; Battle, L.; Cole, G.; Gould, K.; Rector, K.; Raymer, S. Building the Internet of Things using RFID: The RFID ecosystem experience. IEEE Internet Comput. 2009, 13, 48–55. [Google Scholar] [CrossRef]
- Wang, J.; Gu, X.; Liu, W.; Sangaiah, A.K.; Kim, H.J. An Empower Hamilton Loop based Data Collection Algorithm with Mobile Agent for WSNs. Hum. Centric Comput. Inf. Sci. 2019, 9, 1–14. [Google Scholar] [CrossRef]
- Li, W.; Chen, Z.; Gao, X.; Liu, W.; Wang, J. Multimodel Framework for Indoor Localization Under Mobile Edge Computing Environment. IEEE Internet Things J. 2019, 6, 4844–4853. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Y.; Yin, X.; Li, F.; Kim, H.J. An Enhanced PEGASIS Algorithm with Mobile Sink Support for Wireless Sensor Networks. Wirel. Commun. Mob. Comput. 2018, 2018, 9472075. [Google Scholar] [CrossRef]
- Adam, C.P.; Dennis, L.G. Wireless Device Identification Based on RF Oscillator Imperfections. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2492–2501. [Google Scholar]
- Gungor, O.; Koksal, C.E. On the basic limits of RF-fingerprint-based authentication. IEEE Trans. Inf. Theory 2016, 62, 4523–4543. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Y.; Liu, W.; Sangaiah, A.K.; Kim, H.J. An Intelligent Data Gathering Schema with Data Fusion Supported for Mobile Sink in WSNs. Int. J. Distrib. Sens. Netw. 2019, 15, 23–30. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Y.; Wang, K.; Sangaiah, A.K.; Lim, S.J. An Affinity Propagation-Based Self-Adaptive Clustering Method for Wireless Sensor Networks. Sensors 2019, 19, 2579. [Google Scholar] [CrossRef]
- Lin, Y.; Tao, H.; Tu, Y.; Liu, T. A Node Self-Localization Algorithm with A Mobile Anchor Node in Underwater Acoustic Sensor Networks. IEEE Access 2019, 7, 43773–43780. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Y.; Liu, W.; Sangaiah, A.K.; Kim, H.J. Energy Efficient Routing Algorithm with Mobile Sink Support for Wireless Sensor Networks. Sensors 2019, 19, 1494. [Google Scholar] [CrossRef] [PubMed]
- Dou, Z.; Si, G.; Lin, Y.; Wang, M. An Adaptive Resource Allocation Model with Anti-jamming in IoT Network. IEEE Access 2019, 4, 93250–93258. [Google Scholar] [CrossRef]
- Tu, Y.; Lin, Y.; Wang, J.; Kim, J.U. Semi-Supervised Learning with Generative Adversarial Networks on Digital Signal Modulation Classification. CMC Comput. Mater. Continua 2018, 55, 243–254. [Google Scholar]
- Wang, H.; Guo, L.; Dou, Z.; Lin, Y. A New Method of Cognitive Signal Recognition Based on Hybrid Information Entropy and D-S Evidence Theory. Mob. Netw. Appl. 2018, 4, 677–685. [Google Scholar] [CrossRef]
- Wang, H.; Li, J.; Guo, L.; Dou, Z.; Lin, Y.; Zhou, R. Fractal Complexity-Based Feature Extraction Algorithm of Communication Signals. Fractals Complex Geom. Patterns Scaling Nat. Soc. 2017, 25, 10–18. [Google Scholar] [CrossRef]
- Lin, Y.; Zhu, X.; Zheng, Z.; Dou, Z.; Zhou, R. The individual identification method of wireless device based on dimensionality reduction and machine learning. J. Supercomput. 2019, 75, 3010–3027. [Google Scholar] [CrossRef]
- Shi, Q.; Kang, J.; Wang, R.; Yi, H.; Lin, Y.; Wang, J. A Framework of Intrusion Detection System based on Bayesian Network in IoT. Int. J. Perform. Eng. 2018, 14, 2280–2288. [Google Scholar] [CrossRef][Green Version]
- Wu, R.; Chen, X.; Han, H.; Zhao, H.; Lin, Y. Abnormal Information Identification and Elimination in Cognitive Networks. Int. J. Perform. Eng. 2018, 14, 2271–2279. [Google Scholar] [CrossRef][Green Version]
- Hall, J.; Barbeau, M.; Kranakis, E. Enhancing intrusion detection in wireless networks using radio frequency fingerprinting. Commun. Internet Inf. Technol. 2004, 2004, 201–206. [Google Scholar]
- Hall, J.; Barbeau, M.; Kranakis, E. Radio frequency fingerprinting for intrusion detection in wireless networks. IEEE Trans. Def. Secur. Comput. 2005, 12, 1–35. [Google Scholar]
- Hao, P.; Wang, X.; Behnad, A. Relay authentication by exploiting I/Q imbalance in amplify-and-forward system. IEEE GLOBECOM 2014, 12, 613–618. [Google Scholar]
- Knox, D.; Kunz, T. Wireless fingerprints inside a wireless sensor network. ACM Trans. Sens. Netw. (TOSN) 2015, 11, 37–52. [Google Scholar] [CrossRef]
- Deng, S.; Huang, Z.; Wang, X. Radio frequency fingerprint extraction based on multidimension permutation entropy. Int. J. Antennas Propag. 2017, 2017, 1538728. [Google Scholar] [CrossRef]
- Huang, N.E.; Shen, Z.; Long, S.R. The empirical mode decomposition and the Hilbert spectrum for nonlinear and non-stationary time series analysis. Proc. Math. Phys. Eng. Sci. 1998, 454, 90–95. [Google Scholar] [CrossRef]
- Frei, M.; Osorio, I. Intrinsic time-scale decomposition: Time-frequency-energy analysis and real-time filtering of non-stationary signals. Proc. Math. Phys. Eng. Sci. 2007, 463, 321–342. [Google Scholar] [CrossRef]
- Klein, R.W.; Temple, M.A.; Mendenhall, M.J. Application of wavelet-based RF fingerprinting to enhance wireless network security. J. Commun. Netw. 2012, 11, 544–555. [Google Scholar] [CrossRef]
- Polak, A.C.; Dolatshahi, S.; Goeckel, D.L. Identifying wireless users via transmitter imperfections. IEEE J. Sel. Areas Commun. 2011, 29, 1469–1479. [Google Scholar] [CrossRef]
- Toonstra, J.; Kinsner, W. Transient analysis and genetic algorithms for classification. Wescanex 95 Commun. Power Comput. Conf. IEEE 1995, 29, 501–510. [Google Scholar]
- Wang, J.; Zhuang, L.; Cheng, W.; Chao, X.; Wu, X.; Zhang, Z. Analysis of Classification Methods Based on Radio Frequency Fingerprint for Zigbee Devices. In Advances in Computer Communication and Computational Sciences; Springer: Singapore, 2019; pp. 121–132. [Google Scholar]
- Peng, L.; Hu, A.; Zhang, J.; Jiang, Y. Design of a Hybrid RF Fingerprint Extraction and Device Classification Scheme. IEEE Internet Things J. 2019, 6, 349–360. [Google Scholar] [CrossRef]
- Dubendorfer, C.K.; Ramsey, B.W.; Temple, M.A. An RF-DNA verification process for ZigBee networks. Mil. Commun. Conf. IEEE 2013, 29, 1–6. [Google Scholar]
- Cobb, W.E.; Laspe, E.D.; Baldwin, R.; Temple, M.A. Intrinsic Physical-Layer Authentication of Integrated Circuits. IEEE Trans. Inf. Forensics Secur. 2012, 7, 14–24. [Google Scholar] [CrossRef]
- Patel, H.J.; Temple, M.A.; Baldwin, R.O. Improving ZigBee Device Network Authentication Using Ensemble Decision Tree Classifiers With Radio Frequency Distinct Native Attribute Fingerprinting. IEEE Trans. Reliab. 2015, 64, 221–233. [Google Scholar] [CrossRef]
- Reising, D.R.; Temple, M.A.; Jackson, J.A. Authorized and Rogue Device Discrimination Using Dimensionally Reduced RF-DNA Fingerprints. IEEE Trans. Inf. Forensics Sec. 2015, 10, 1180–1192. [Google Scholar] [CrossRef]
- Zhang, Z.; Guo, X.; Lin, Y. Trust Management Method of D2D Communication Based on RF Fingerprint Identification. IEEE Access 2015, 10, 1180–1192. [Google Scholar] [CrossRef]
- Mishra, D.; De, S.; Alexandropoulos, G.C.; Krishnaswamy, D. Energy-aware Mode Selection for Throughput Maximization in RF-Powered D2D Communications. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017. [Google Scholar]
- Chen, Y.; Wen, H.; Song, H.; Chen, S.; Xie, F.; Yang, Q.; Hu, L. Lightweight one-time password authentication scheme based on radio-frequency fingerprinting. IET Commun. 2018, 12, 1477–1484. [Google Scholar] [CrossRef]
- Chen, S.L.; Wen, H.; Wu, J.S.; Xu, A.D.; Jiang, Y.X.; Song, H.H.; Chen, Y. Radio Frequency Fingerprint-Based Intelligent Mobile Edge Computing for Internet of Things Authentication. Sensors 2019, 19, 3610. [Google Scholar] [CrossRef]
- Patel, H.; Temple, M.; Baldwin, R.; Ramsey, B. Application of ensemble decision tree classifiers to zig bee device network authentication using RF-DNA fingerprinting. In Proceedings of the 9th International Conference on Cyber Warfare and Security, West Lafayette, IN, USA, 24–25 March 2014; pp. 176–184. [Google Scholar]
- Tax, D.; Duin, R. Support Vector Data Description. Mach. Learn. 2004, 54, 45–66. [Google Scholar] [CrossRef]
- Wei, X.K.; Huang, G.B.; Li, Y.H. Mahalanobis Ellipsoidal Learning Machine for One Class Classification. In Proceedings of the IEEE 2007 International Conference on Machine Learning and Cybernetics, Hong Kong, China, 19–22 August 2007; pp. 3528–3533. [Google Scholar]
- Zhang, Y.; Wei, X.; Jiang, H. One-class classifier based on SBT for analog circuit fault diagnosis. Measurement 2008, 41, 371–380. [Google Scholar]
- Shi, Z.; Huang, M.; Zhao, C. Detection of LSSUAV using hash fingerprint based SVDD. In Proceedings of the 2017 IEEE International Conference on Communications, Paris, France, 21–25 May 2017; pp. 1–5. [Google Scholar]
- Uslu, F.S.; Binol, H.; Ilarslan, M. Improving SVDD Classification Performance on Hyperspectral Images via Correlation Based Ensemble Technique. Opt. Lasers Eng. 2017, 89, 169–177. [Google Scholar] [CrossRef]
- Mirjalili, S.; Lewis, A. The whale optimization algorithm. Adv. Eng. Softw. 2016, 95, 51–67. [Google Scholar] [CrossRef]


| Energy Proportion | 85% | 90% | 95% |
|---|---|---|---|
| Feature dimension | 6 | 8 | 12 |
| Experiment | and | SNR | |||||
|---|---|---|---|---|---|---|---|
| 0 dB | 5 dB | 10 dB | 15 dB | 20 dB | 25 dB | ||
| 1 | 0.48 | 0.63 | 0.77 | 0.88 | 0.95 | 0.99 | |
| 0.55 | 0.69 | 0.85 | 0.95 | 1.00 | 1.00 | ||
| 2 | 0.41 | 0.61 | 0.78 | 0.86 | 0.94 | 0.98 | |
| 0.49 | 0.7 | 0.84 | 0.92 | 0.99 | 1.00 | ||
| 3 | 0.5 | 0.66 | 0.78 | 0.9 | 0.95 | 0.99 | |
| 0.6 | 0.71 | 0.82 | 0.94 | 0.98 | 1.00 | ||
| 4 | 0.48 | 0.67 | 0.79 | 0.92 | 0.97 | 1 | |
| 0.51 | 0.71 | 0.83 | 0.96 | 1.00 | 1.00 | ||
| 5 | 0.48 | 0.65 | 0.74 | 0.88 | 0.96 | 0.99 | |
| 0.56 | 0.72 | 0.82 | 0.94 | 1.00 | 1.00 | ||
| Experiment | Rogue Devices | SNR | |||||
|---|---|---|---|---|---|---|---|
| 0 dB | 5 dB | 10 dB | 15 dB | 20 dB | 25 dB | ||
| 1 | #9 | 0.58 | 0.72 | 0.89 | 0.93 | 0.97 | 0.99 |
| #10 | 0.59 | 0.75 | 0.90 | 0.96 | 0.99 | 1.00 | |
| 2 | #2 | 0.64 | 0.76 | 0.92 | 0.95 | 0.98 | 0.99 |
| #6 | 0.61 | 0.70 | 0.86 | 0.91 | 0.96 | 0.99 | |
| 3 | #7 | 0.58 | 0.70 | 0.87 | 0.92 | 0.97 | 0.99 |
| #8 | 0.56 | 0.67 | 0.89 | 0.94 | 0.96 | 1.00 | |
| 4 | #1 | 0.65 | 0.76 | 0.92 | 0.96 | 0.98 | 0.99 |
| #4 | 0.58 | 0.67 | 0.87 | 0.91 | 0.97 | 1.00 | |
| 5 | #3 | 0.61 | 0.73 | 0.90 | 0.95 | 0.98 | 1.00 |
| #5 | 0.60 | 0.69 | 0.86 | 0.92 | 0.97 | 0.99 | |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tian, Q.; Lin, Y.; Guo, X.; Wang, J.; AlFarraj, O.; Tolba, A. An Identity Authentication Method of a MIoT Device Based on Radio Frequency (RF) Fingerprint Technology. Sensors 2020, 20, 1213. https://doi.org/10.3390/s20041213
Tian Q, Lin Y, Guo X, Wang J, AlFarraj O, Tolba A. An Identity Authentication Method of a MIoT Device Based on Radio Frequency (RF) Fingerprint Technology. Sensors. 2020; 20(4):1213. https://doi.org/10.3390/s20041213
Chicago/Turabian StyleTian, Qiao, Yun Lin, Xinghao Guo, Jin Wang, Osama AlFarraj, and Amr Tolba. 2020. "An Identity Authentication Method of a MIoT Device Based on Radio Frequency (RF) Fingerprint Technology" Sensors 20, no. 4: 1213. https://doi.org/10.3390/s20041213
APA StyleTian, Q., Lin, Y., Guo, X., Wang, J., AlFarraj, O., & Tolba, A. (2020). An Identity Authentication Method of a MIoT Device Based on Radio Frequency (RF) Fingerprint Technology. Sensors, 20(4), 1213. https://doi.org/10.3390/s20041213








