Abstract
The sinkhole attack in an edge-based Internet of Things (IoT) environment (EIoT) can devastate and ruin the whole functioning of the communication. The sinkhole attacker nodes (s) have some properties (for example, they first attract the other normal nodes for the shortest path to the destination and when normal nodes initiate the process of sending their packets through that path (i.e., via ), the attacker nodes start disrupting the traffic flow of the network). In the presence of s, the destination (for example, sink node i.e., gateway/base station) does not receive the required information or it may receive partial or modified information. This results in reduction of the network performance and degradation in efficiency and reliability of the communication. In the presence of such an attack, the throughput decreases, end-to-end delay increases and packet delivery ratio decreases. Moreover, it may harm other network performance parameters. Hence, it becomes extremely essential to provide an effective and competent scheme to mitigate this attack in EIoT. In this paper, an intrusion detection scheme to protect EIoT environment against sinkhole attack is proposed, which is named as SAD-EIoT. In SAD-EIoT, the resource rich edge nodes (edge servers) perform the detection of different types of sinkhole attacker nodes with the help of exchanging messages. The practical demonstration of SAD-EIoT is also provided using the well known NS2 simulator to compute the various performance parameters. Additionally, the security analysis of SAD-EIoT is conducted to prove its resiliency against various types of s. SAD-EIoT achieves around detection rate and false positive rate, which are considerably better than other related existing schemes. Apart from those, SAD-EIoT is proficient with respect to computation and communication costs. Eventually, SAD-EIoT will be a suitable match for those applications which can be used in critical and sensitive operations (for example, surveillance, security and monitoring systems).
1. Introduction
Internet of Things (IoT) objects include smart sensors (devices) which are capable of gathering and transmitting the sensing information in an IoT network where the human involvement is minimally required. In a generalized IoT architecture presented in Figure 1 [1,2] consists of various scenarios like smart home, smart transportation and smart community. All these scenarios are installed with smart devices such as smart home appliances, smart traffic management appliances and smart environment monitoring devices. These devices are placed and installed in order to communicate with other heterogeneous devices over the Internet via the gateway node(s) where the traffic goes out and comes in. In this scenario, various users (i.e., smart home users) use the s to access the real-time information via smart devices deployed in the network [1,3,4]. IoT based applications become the essential requirement of the society as they provide people a dependable, responsive and ingenious network connectivity which helps in controlling the remote smart IoT devices in a real time fashion.
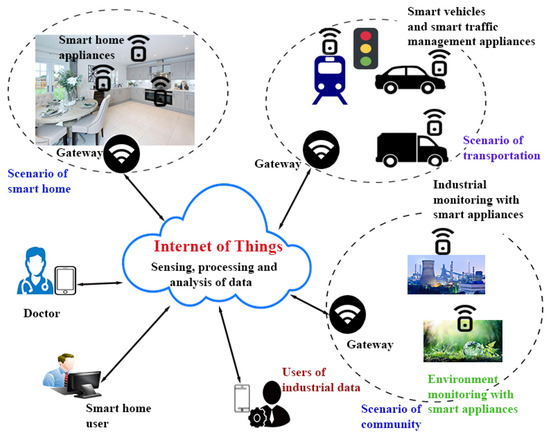
Figure 1.
Generic Internet of Things (IoT) architecture (adapted from [1]).
In an edge-based communication network, the data is processed near the edge (i.e., edge device) where the data is being generated unlike the centralized data-processing facility. This further improves response time of the network and also saves the bandwidth. In edge computing, there is a corner (i.e., edge) where the data traffic goes out and comes in, which is also named as edge router (device or node) or simply a gateway. In an edge-based IoT communication environment, edge node performs heavy computations on data on behalf of the smart IoT devices which have limited computational, communication and storage resources. The data analysis is performed near the sensing devices which speed up the process of data analysis and further reduce the decision making time [5,6]. Edge-based IoT communication environment (EIoT) is better than the cloud-based architecture because of its enhanced and improved performance with moderate cost. EIoT may have different applications such as smart cities, smart health care system and smart environment monitoring like the cloud computing communication environment. However, at the same time, EIoT suffers from several privacy and security problems. EIoT consists of different devices such as edge router (gateway node), various users and smart devices. Most of the time interested users can access real-time data possessed by the smart devices [3,5,6,7,8]. For such kind of communication environment, edge computing provides additional benefits such as “enhanced security, decreased bandwidth and reduced latency”. Henceforth, it is promising communication technology for different IoT applications.
Edge-based IoT architecture for smart home scenario is presented in Figure 2. In this scenario, certain smart devices are deployed to monitor and support the day-to-day activities inside a home. The smart devices (i.e., IoT sensors) sense, process and send the data of home appliances to the nearby node (edge device). The edge server receives and further processes the data and forwards it to the cloud server. The authenticated (genuine) smart home users can access the data of the smart home through the cloud servers. The advantage of this architecture is that the resource rich edge devices can do processing on behalf of resource constrained smart devices. Furthermore, edge devices can also be utilized for other types of tasks, such as for the detection of intrusion in the network as they are powerful devices (resource rich nodes) of the network. Hence, the same approach is followed in this paper.
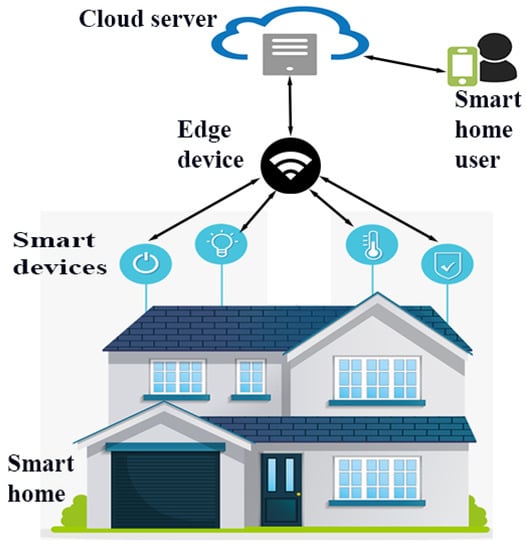
Figure 2.
Edge-based IoT architecture for smart home scenario.
Additionally, Figure 3 is also provided which consists of different kinds of devices (for example, edge router (gateway) and smart devices, i.e., IoT sensors and cloud servers). The task of an IoT sensor is to sense, process and transmit the data of environmental phenomena (i.e., humidity level, temperature, pressure, etc.) to the edge node. IoT smart devices (IoT sensors) are resource-constrained with limited memory, battery backup and processing capability, whereas the edge node is rich in resources (in terms of memory, battery power to sense and process the data and long communication ranges). Then an edge node processes and analyzes the received data and after that it transmits the processed data to the remote server(s) over the cloud. However, such type of communication environment is vulnerable to various security threats which lead to significant security problems as different attacks (for instance, routing attacks, sybil attack, data leakage, replaying of old messages, man-in-the middle, impersonation, physical capturing of smart devices, password guessing and privileged insider attacks) are possible [1,3,6,9].
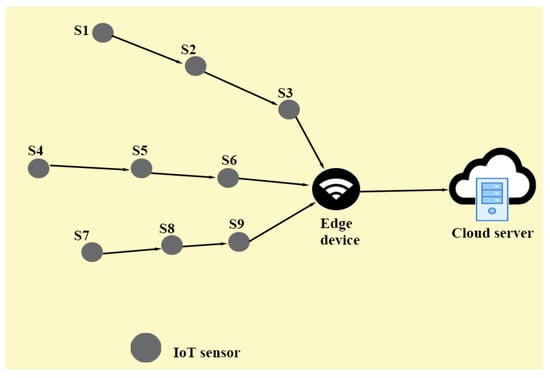
Figure 3.
Edge-based Internet of Things (IoT) environment (EIoT)-communication under the normal flow of traffic.
Zhao et al. [10] designed a mechanism to detect location injection attacks (LIAs), called ILLIA. ILLIA is based on the “k-anonymity-based privacy preservation against LIA in continuous location-based services (LBSs) queries”. They emphasized that the attackers attempt to attack some particular users who they are interested in. Such type of user is referred to as high-risk user. ILLIA has the ability to protect LIA without having advance knowledge of how fake locations are exploited. At the same time, ILLIA also maintains high quality of services.
Wang et al. [11] proposed another intrusion detection approach, known as MIASec. It provides “input data indistinguishability” and defends against membership inference attacks in “Machine Learning as a Service (MLaaS)”. In a “membership inference attack”, an attacker is provided with given black-box access to a target classifier and inclines to infer if a specific record is covered in the training set or not.
1.1. Attack Schema of Sinkhole Attack in Edge-based IoT Environment
A possible scenario of sinkhole attack in EIoT environment provided in Figure 4 represents the flow of network traffic under the presence of s. The communication scenario of EIoT under the normal flow of traffic has been presented in Figure 3. Each IoT smart device (i.e., IoT sensor) can sense and transmit the information to the destination (i.e., edge device/node) under the normal flow of traffic. After collecting the data from different IoT devices, an edge node can process and analyze the data and then transmit the information to the cloud server for further processing and storage.
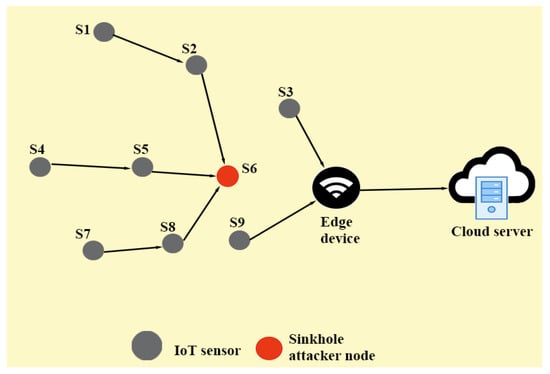
Figure 4.
EIoT-communication in the case of sinkhole attack.
An adversary, say , can physically capture some IoT smart devices as the devices are installed (deployed) in an unattended (hostile) environment where h physical monitoring may not be feasible. It further helps to physically capture some nodes (IoT sensors). Thus, can extract the stored sensitive information by applying power analysis attacks [12,13]. can also install malicious sinkhole attack by launching script in the IoT devices which can execute the attack [14,15,16,17,18]. Then, can deploy these malicious nodes in the target area to launch the required attack. When s start working in the network, the confidential information may be leaked, delayed or lost [17], which can further trouble the entire functioning of the network. Therefore, a robust mechanism to defend against s is required. Hence, intrusion detection technique for EIoT has become one of the primary research problems in recent years [14,15,16,17,19,20,21,22,23,24].
1.2. Goal of Designing Proposed Scheme
Sometimes IoT devices are installed in an “unattended (hostile) environment” (for example, smart security and surveillance), where the ceaseless physical monitoring of these devices [25,26,27,28] is not possible. may take the advantage of lack of physical monitoring and captures some legitimate IoT sensor nodes. It is worth noticing that the s have several interesting properties, such as they first attract the other normal nodes for the shortest path to the destination, and when normal nodes start sending their packets through that path (i.e., via ), the s start disrupting the flow of the traffic. As a result, the s may or may not forward the packets to the destination. Moreover, it may forward the packets selectively (for example, forwarding of packets of a particular network service (i.e., UDP packets) and restricting the others (i.e., TCP packets)). The packets are passed through the s, which may delay, drop or modify the information inside these packets. An EIoT network consists of resource rich edge nodes (servers) and resource constrained sensing devices. The resource rich edge nodes can be used to detect the presence of attacker nodes. In our proposed architecture, the edge nodes are assumed to be the destination nodes, which receive the packets from the other neighbour nodes. In the presence of s in EIoT, an edge node may not receive the information or it may receive modified or partially modified information. It then degrades the performance, efficiency and reliability of the communication happening in EIoT. In the presence of s, there are various chances: (a) decrement in throughput of the network, (b) increment in end-to-end delay and (c) decrement in packet delivery ratio. The sinkhole attack has been investigated in recent years in wireless sensor networks and several solution were proposed. However, the chance of occurrence of sinkhole attacks in IoT environment is also high. The sinkhole attack detection techniques for Wireless Sensor Networks (WSNs) are not directly applicable in IoT. Therefore, a new scheme to mitigate sinkhole attacks in IoT is required. Hence, an effective intrusion detection scheme for protecting sinkhole attacks in an EIoT communication environment has been designed.
1.3. Attack Model
The widely followed “Dolev-Yao threat model (known as the DY model)” [29] can be used in the designing of SAD-EIoT, where “any two communicating entities communicate over an insecure public channel” [30]. Thus, the communication channel is treated as insecure and also the end-point entities (i.e., IoT sensors) are not considered to be trusted. Other possibilities of the sinkhole attack can also be considered. It is possible that an attacker can physically capture some IoT smart devices (for example, IoT sensors) and take out the desired sensitive information from its memory [12,13]. can clone new malicious nodes with sinkhole attack functionality by making use of extracted information. After the manufacturing of these malicious devices (i.e., s), can directly deploy them in the network [16,17,24]. As discussed in Section 1.1, under the successful execution of a sinkhole attack in EIoT, the data packets may get lost, dropped, delayed or modified. This may cause degradation in the performance of the communication in EIoT. Furthermore, this may cause the reduction in the throughput and packet delivery ratio of the network along with the increment in end-to-end delay. Hence, a strong intrusion detection mechanism to protect against the sinkhole attack is desirable in EIoT environment.
1.4. Research Contributions
The research contributions made in the proposed scheme are provided below.
- A new intrusion detection scheme for the detection of sinkhole attack in edge-based IoT environment (SAD-EIoT) has been proposed.
- SAD-EIoT is shown to be secure against sinkhole attacks in EIoT. It is validated through security analysis and also the results obtained through the NS2 simulation.
- Furthermore, SAD-EIoT is compared with other closely related existing techniques. The conducted comparison demonstrates that SAD-EIoT performs better than other existing techniques.
1.5. Structure of the Paper
The remainder of the paper is organised as follows. In Section 2, the background study of other related existing techniques is provided. Section 3 gives in-depth details of the designed intrusion detection scheme for sinkhole detection (SAD-EIoT) in EIoT environment. The research process and research methodology of SAD-EIoT is also explained here. Section 4 contains the details of various mathematical models. Section 5 contains the security analysis of SAD-EIoT, which proves that SAD-EIoT is competent and efficient enough to defend sinkhole attacks. The simulation study of SAD-EIoT using the widely-used NS2 tool is further provided in Section 6. Next, the performance comparison of SAD-EIoT with other closely related existing schemes is provided in Section 7. Finally, the work is concluded in Section 8.
2. Background
This section contains the background study of the various types of available intrusion detection techniques for Internet of Things and and wireless sensor network. The details are as follows.
Salehi et al. [31] designed a mechanism to detect sinkhole attack in Wireless Sensor Networks (WSNs). In the proposed mechanism, the attackers’ nodes are detected by considering the flow of packets in the network. First, the intrusion region is identified and then after collected data evaluation, the malicious nodes are identified. However, the presented mechanism raises the high false positive rate. Wang et al. [32] proposed a method to mitigate anomalies in a cluster-based WSN. A real time data monitoring system is used to analyse the data packets in the network, where any type of node (edge nodes, source nodes and sensors) can be compromised by an attacker node. Three types of detection schemes such as intelligent hybrid intrusion detection system (IDS), hybrid IDS and misuse IDS were used. The attacker nodes are identified by the misuse of data identification and anomaly detection. However, their implemented mechanism provides marginally improved detection rate.
Hamedheidari et al. [20] suggested a technique to defend WSN against the sinkhole attacks which uses mobile agent to inform the neighbours to prevent the attack. However, the overheads induced by the mobile agents reduce the performance of the network. Wang et al. [33] used “Gaussian distribution technique” for detection of intrusions. They discussed two methods to defend malicious nodes, called “single-sensing” and “multiple-sensing”.
Wang et al. [34] discussed the expected probability of “Intrusion Detection”. The provided solution uses parameters, such as node density, range in heterogeneous and homogeneous WSN for sensing anomalies. The calculated probability is used to analyse the efficiency and performance of the proposed method. To protect WSN from “misleading attackers in a multihop routing”, Zhan et al. [35] also suggested a framework named as“Trust-Aware Routing (TARF)”, which is capable of resolving the intrusions in dynamic sensor networks. Without making use of “time synchronisation and geographic location of the sensor nodes”, the trusted and energy saver routes can be identified.
Shin et al. [36] discussed various structures of “Wireless Industrial Sensor Networks (WISN)”. They proposed a hierarchical design to mitigate the attacks. “One-hop clustering” was the key point, which was utilised in the presented design. To mitigate the hierarchical anomalies, the logical protocols were used. Yu et al. [37] provided information about different kinds of intrusions and also the methods used to resolve them. A comprehensive literature survey was provided to highlight the existing standard and associated techniques in two different categories, which are for securing data and its routing.
Liu et al. [38] demonstrated an intrusion detection system to prevent sinkhole attack for the “Internet of Things (IoT)” communication. Their proposed scheme not only detects the s but also bypasses the attack region by making use of routing mechanisms named as “hop-by-hop basis and multihop basis”. The location of the attacker nodes is also determined by their presented scheme. However, their scheme exhibits high computation and communication costs. Chen et al. [39] proposed a “Low-rate Denial of Service (LDoS)” attack mitigation technique which can be used for both WSN and IoT. They combined “Hilbert Huang transformation and trust evaluation” methods to find LDoS attacker nodes in WSN.
Fang et al. [40] examined the need for cyber security in “information-centric networking (ICN)”. They analysed the typical attack behaviours and defence methods. Furthermore, they presented a “Fast and Efficient Trust Management Scheme (FETMS)” for mitigating the On-Off attack with the help of communication trust, data trust and reputation values. Pongle et al. [41] investigated the possible attacks on “IPv6 over Low-Power Wireless Personal Area Networks (6LoWPAN)” and “IPv6 Routing Protocol for Low power and Lossy Networks (LLNs), called RPL”. They highlighted the possible techniques to mitigate these attacks. The emphasis was on protecting the RPL network from various attacks, such as Sybil, blackhole, wormhole and clone ID attacks.
Yang et al. [42] did a survey on IoT communication environment. They identified some constraints for IoT devices, for example, computing resources and battery lifetime, and some solutions were also suggested. Lyu et al. [43] proposed a “selective authentication based geographic opportunistic routing (SelGOR)” to mitigate the DoS attacks, which can fulfil the requirements of authenticity, integrity and reliability in WSNs. By “statistic state information (SSI)” of links between nodes, SelGOR took the advantage of an SSI-based trust model to increase the network efficiency in terms of data delivery. SelGOR used an entropy-based algorithm to maintain integrity which was also able to detect DoS attacker nodes to improve the performance.
He et al. [44] proposed a scheme called “sector-based random routing (SRR)” to resolve the source location privacy problem. Under the implementation of the proposed method, the energy consumption is also reduced. As per SRR mechanism, the routing paths are disappeared by dividing the network into several sectors, which further improves the security.
Airehrour et al. [45] proposed a SecTrust-RPL protocol that used “SecTrust” system. It identifies some nodes to make decisions for routing using trust. The trust computation was done through exchanged packets between the nodes to determine the trustworthiness. It can identify the attacker nodes and also improve the throughput of the RPL. Sicari et al. [46] proposed a technique to mitigate DoS attack against the IoT middleware, called “networked Smart object (NOS)”. They designed a variable number of dynamic virtual ports on each NOS, and the second thing is that it binds the identifier virtual port of each NOS’s port to UID, which was more tedious to predict by attacker nodes.
Bhosale et al. [47] implemented an intrusion detection technique in which they compared “Received Signal Strength Indicator (RSSI)” value of neighbour nodes and the victim nodes with the threshold values. They kept the record of the broadcasting node’s RSSI value, from where the victim packet was disseminated. It helped to locate the presence of attacker node in their technique. Liu et al. [48] developed a detection mechanism for low rate DOS attack. They used the expired state entries and proposed an “enhanced distributed low-rate attack mitigating (eDLAM)” method to mitigate the attacks. Their presented eDLAM can detect an attack based on expired state-entry numbers.
Raoof et al. [49] presented a comparative analysis of “Routing Protocol for Low-Power and Lossy Networks (RPL)”. Some of the routing attacks along with the mitigation methods were also discussed. Mayzaud et al. [50] presented a method to mitigate version number attacks in RPL networks. This was based on “distributed monitoring architecture” which conserves the energy of resource constrained nodes for the “Advanced Measurement Infrastructures (AMI)”. Their detection procedure is performed by the source node after collecting the detection information from all deployed nodes. In addition, Wazid et al. [16,17,24] also discussed intrusion detection schemes for detection of various attacks, including sinkhole, blackhole, hybrid anomaly as well as routing attacks in hierarchical WSNs and edge-based IoT (EIoT) networks.
In Table 1, the comparison to existing intrusion detection techniques is provided. It contains different parameters such as “name of the technique/protocol”, “its goal”, “method used” and “its outcomes and limitations”.

Table 1.
Comparison of existing techniques.
3. The Proposed Sinkhole Attack Detection Scheme
In this section, the different phases of the proposed “sinkhole attack detection scheme for edge-based IoT environment”, called SAD-EIoT, are explained. The different message formats required to describe SAD-EIoT are also presented. Furthermore, the notations and their significance shown in Table 2 are used in the proposed SAD-EIoT.

Table 2.
Notations utilised in SAD-EIoT.
3.1. Network Scenario
For an edge-based IoT environment, Figure 3 suggests that there is a resource-rich edge device (node/router) which works like a gateway node. For instance,“Personal Digital Assistant (PDA)” can be configured as an edge node [51,52,53]. In an edge-based IoT environment, there are resource-constrained IoT smart devices (i.e., IoT sensors) with limited resources (for instance, MICAz motes [53]). The IoT sensors can be deployed randomly or manually in a required area (i.e., in a forest for environment monitoring) based on application scenarios. After deployment, the first task of sensing devices is to find the neighbours in its communication range. To perform such a task, IoT sensors can broadcast “HELLO messages” (containing their identity) to other nodes in their communication ranges. After receiving “HELLO messages” from the neighbouring sensing nodes, each IoT sensor constructs a neighbour list [54]. Every edge node also finds its “physical neighbors” (for example, the IoT sensors). is responsible for anomaly detection in the network. For ensuring secret communications among an edge node and IoT sensing devices, and also among different IoT sensors and itself, a key management protocol, namely the “unconditionally secure deterministic key management” suggested by Das [52] can be utilised. Assume that and are two different symmetric (secret) keys among two neighbouring IoT sensing nodes, say and and among an edge node and its neighbour IoT sensing node . The method for key establishment can be defined on the basis of deterministic key management scheme available in [52]. With the help of the established secret keys, neighbour nodes can securely communicate with each other in the edge-based IoT environment. The delay between and can be computed by using the technique given in [17,55].
Assume each transmitted packet of a sensing node contains a distinct sequence number and the sequence numbers are kept in an ascending order. Next, denoted as a packet j’s receiving time on a node k corresponding to the “perfect clock ” and the packet j’s transmitting time on the node k. The transmission or reception time of a message is considered as the “time just before the first byte of a packet (message) is sent or received”. Let a and b represent the source and destination nodes along with a chosen path. If is another parameter denoting the packet j’s generation time on a, the packet j’s “end-to-end delay for a path” is calculated as [16,17,24]:
Now, if the packet j’s waiting time at node k on the path is represented by , then . It is important to notice that waiting time incorporates node’s backoff time for competing for the channel. Therefore, end-to-end delay is calculated as
where the number of total nodes in that path is denoted by n. Since the IoT sensors do not have tamper-resistant hardware in general due to the cost factor, an adversary gets a chance to extract all the required information from the memory of a physically captured IoT sensor node [12,13]. can then store the extracted information in the memory of the newly manufactured (cloned) IoT sensor node and can also load the sinkhole attack functionality program required to launch that attack in the network.
3.2. Process Involved in SAD-EIoT
The process involved in SAD-EIoT is explained using a sequence diagram of sinkhole attack detection through SAD-EIoT (see Figure 5). Its details are given below.
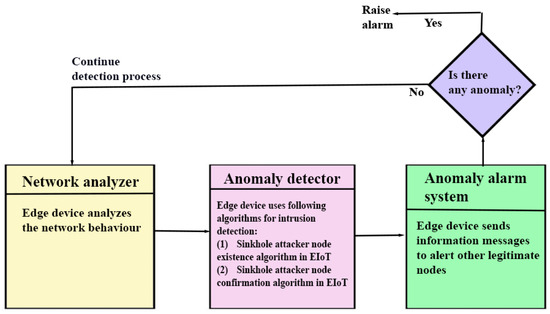
Figure 5.
Sequence diagram of sinkhole attack detection through SAD-EIoT.
Edge node keeps all the important information, such as identity of every IoT sensing node , ranks information and its battery level. As per the nature of sinkhole attack, the malicious node (sinkhole attacker node, say ) advertises a shortest path to the destination (i.e., edge node) and the neighbouring IoT sensor nodes get attracted towards that path and send their packets to as they assume that the shortest path to the destination is through . After receiving the data from neighbour IoT sensors, can play with the communication. can perform the following malicious tasks:
- Dropping of the packets
- Modification of information in the packets
- Forwarding the packets selectively (i.e., forwarding of UDP packets and dropping of TCP packets)
- Forwarding the packets with some delay
The sinkhole attack can disturb the overall configuration of the network as it affects most of the important network parameters. For instance, it may reduce the throughput (sometimes, it tends to zero when drops all packets) and increase the end-to-end delay along with extremely low packet delivery ratio [16,17,22,24]. Since an edge node is resource rich in the network, it can be easily used for detection of sinkhole attacks. The detection of sinkhole attack is executed in the following two phases:
Phase 1 (Identifying the presence of sinkhole attacker nodes): In this phase, we identify the existence of s in the network by applying the steps in Algorithm 1. The parameters, such as node identity , hop count from (), remaining energy at the nodes and rank information are used. An IoT node is recognised as a suspected , if following conditions hold [9,17,18]:
Here, and are threshold values of the network hop count and remaining energy, respectively. and are lower and upper limits of ranks for a particular node (i.e., ), respectively. A node loses some energy whenever it transmits or receives packets and the edge node knows about the initial battery status of all the nodes. If an attacker node provides modified battery status to the edge node, in turn that edge node can calculate the battery (energy) value using the available technique in the literature. A similar approach can be applicable for hop counts and rank information. By the end of this phase, a list of suspected attacker nodes is prepared, if they exist in the network.
Phase 2 (Confirming the existence of sinkhole attacker nodes): In this phase, the confirmation of identified nodes as the sinkhole attacker or some battery drained nodes is done. The steps stated in Algorithm 2 are required to perform this task. In this phase of attack detection, the possible cases are outlined below.
- Case 1: If does not get messages from a doubtful node , it attempts to figure out that node as or normal (genuine) node which has depleted its entire battery (might be a node failure). In such a situation, transmits to and waits some time for its response. If the condition holds, where is the waiting time’s threshold, it will indicate the expiry of waiting time. If both response message as well as data message from are not received by , it makes a decision as the ’s failure. Note that additional factors like network congestion have been included in .
- Case 2: If gets , but the is not received by , is identified as the “sinkhole attacker node” . It is also determined that is a kind of which consumes all packets and does not forward them towards the destination (i.e., ).
- Case 3: If receives the and also from , it checks the integrity of by using hashing algorithm (i.e., SHA-1 or SHA-256 [56]). If the integrity does not hold, is treated as the which has modified .
- Case 4: receives and also from , but the quality of service of the network is not up to the mark [57]. Since is a powerful node, it can run some technique to maintain the quality of the service of the network [57]. For example, may forward the UDP packets but not the TCP packets. If all these features are included then it becomes a sign of selective forwarding of packets (a kind of packet forwarding attack) [57,58,59]. For the detection purpose, can execute the following steps if the count of packets for a particular service (i.e., TCP) does not exceed the threshold value of count of packets in a particular duration of time. considers node as the . Further, note that the threshold value of count of packets in a particular duration of time is an empirical value which can be set at the at the time of the deployment of the nodes in the network.
- Case 5: When the is transmitted by to , it waits some time for the response message. If the condition holds, it will indicate the expiry of waiting time. If receives , it waits for receipt of from . If receives after the expiry of the waiting time (i.e., ), the node is detected as the because it delays the packets before forwarding them towards the destination (i.e., ).
As the detection work proceeds with the time, tries to detect malicious sinkhole (attacker) nodes and also adds them to the list of sinkhole attacker nodes . In the “anomaly alarm system phase”, ignores the detected , where n and raises an alert to warn the other legitimate nodes about the existence of s. After that, the legitimate IoT devices remove the entry of node from its neighbour list and start sending their packets to the other possible route(s).
The sequence diagram of sinkhole attack detection through SAD-EIoT provided in Figure 5 is helpful to explain the overall communication process of SAD-EIoT. It has the following important stages:
- Network analyser: An edge node performs the analysis of the network behaviour. then identifies normal and abnormal activities of the network.
- Anomaly detector: For the detection of s, two different phases are used, namely Phase 1 for identifying the existence of s and Phase 2 for confirming the existence of s. does the work of sinkhole node detection by using the steps of existence algorithm in EIoT (Algorithm 1). After the completion of all steps mentioned in Phase 1, a list of doubted nodes is constructed that may or may not have the attacker nodes. To confirm the existence of s in the network, executes the steps of confirmation algorithm in EIoT (see Algorithm 2). After the successful completion of Phase 2, a list of confirmed s and is obtained which contains the entries for all types of s which exist in the network.
- Alarm system: After the successful completion of both phases of s detection, the list is generated. The blacklists these malicious nodes and also sends alarm messages to other legitimate IoT devices (i.e., IoT sensor nodes). Then, these legitimate nodes remove the entries of s from their neighbour list and start sending their packets to the other possible available route(s).
3.3. Formats of Messages Used in Sinkhole Attack Detection
SAD-EIoI uses four messages which are also utilised in some existing techniques: [16,17,18,24], namely, (i) “status and data query message ”, (ii) “status response message ”, (iii) “data message ” and (iv) “information message ”. The structures of these different messages are provided below.
- Status and data query message: The message is shown in Figure 6. transmits to all IoT devices (sensors). This message is constructed using the different fields, such as an ’s identity , an IoT device ’s identity , the information field and also the hashed message authentication code , where .
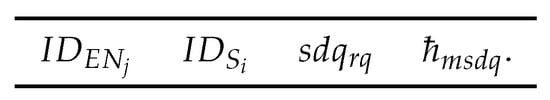 Figure 6. Assembly of status and data query message .
Figure 6. Assembly of status and data query message . - Status response message: The structure of provided in Figure 7 is composed of different fields, such as , “remaining energy (battery power)” of , “rank information” of , the information field and . sends the message to . For saving energy, an IoT sensing device can utilize any one of the modes (“sleep”, “idle” and “working”) [60,61]. For the detection of sinkhole attack, the information about the two modes is needed (i.e., “idle” and “working”), because sensing devices cannot respond when they are in the sleeping state. The may contain two response types: 0 (idle state) and 1 (working state).
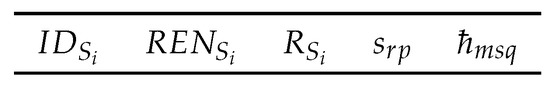 Figure 7. Structure of status response message .
Figure 7. Structure of status response message . - Data message: The structure of provided in Figure 8 is composed of different fields, for example, , and of , as the sensing data needs to be transmitted to , and . Note that session key can be used to encrypt the data, if it is required.
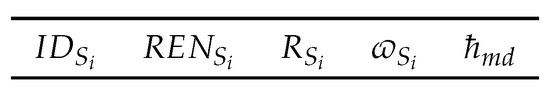 Figure 8. Assembly of data message .
Figure 8. Assembly of data message . - Information message After performing the detection of s, sends the information message to alert the other legitimate IoT sensors. The structure of provided in Figure 9 is also composed of different fields, like and detection information field contains the information of the detected s.
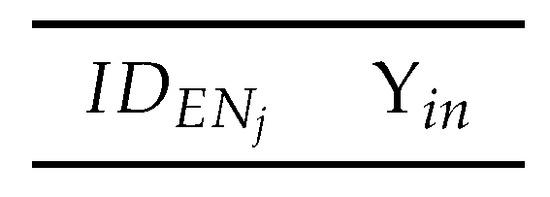 Figure 9. Structure of information message .
Figure 9. Structure of information message .
3.4. Research Methodology of SAD-EIoT
In this section, the research methodology of SAD-EIoT is discussed. SAD-EIoT can detect the sinkhole attacker nodes in an EIoT environment efficiently. The detection procedure happens in two phases. Phase 1 identifies the s by the “sinkhole attacker node existence algorithm”, whereas Phase 2 allows to see the existence of the doubted nodes (either normal or s) are identified by using the “sinkhole attacker node confirmation algorithm”. These phases are discussed in the subsequent sections.
3.4.1. Sinkhole Attacker Node Existence Algorithm in EIoT
The “sinkhole attacker node existence algorithm in EIoT” is discussed in Algorithm 1 which is used to recognise the existence of the suspected s. It utilises various parameters, such as node ’s identity , hop count from , remaining energy at nodes and rank information . This algorithm finds the s, in the case of a sensor node , if the conditions , and are satisfied, where and are threshold values of hop count and remaining energy, respectively. Moreover, , is a pair of lower and upper limits of rank for a particular node . Algorithm 1 also provides a list of suspicious attacker nodes, say , if these suspicious s exist in the network.
Remark 1.
If the “hop count” of an IoT sensing node from is less than the network hop count threshold , that is, if , may be considered as .
Example 1.
To validate the statement of Remark 1, the scenario provided in Figure 4 should be considered. If a node is far away from a destination , that is, its hop count value from is high, chances are that this will not be an exact . In order to be an exact , this particular node should be as close as possible to the destination . If a sinkhole attacker node is closer to , it can get a greater number of packets from the neighbour nodes and it may further damage the network operations quickly. Otherwise, if the is far away from the destination , in that case it will not get a greater number of packets. In this situation, the damage to the network will be minimum. Thus, an attacker’s advantage to launch the sinkhole attack will be very low. The empirical threshold value of hop count of the network, , can be set at the time of the deployment of the IoT sensors and it can be compared to the hop count value for that particular node to identify a sign of intrusion in the network. Therefore, if holds, can be treated as a suspected .
Remark 2.
If the “remaining energy under the normal behaviour and abnormal behaviour of an IoT sensing node ” are and , respectively, the criteria needs to hold for a sinkhole attack.
Example 2.
To justify Remark 2, the scenario available in Figure 4 should be considered. A node receives a lower number of messages if it is a normal node. However, if it is a , it will definitely receive a greater number of messages as per the mechanism of a sinkhole attack. When a node receives a greater number of packets, its battery depletion will be greater as compared to the normal node. Suppose sets a threshold value of remaining energy for a particular node as and in actual scenario it is . So, if a node is a , the condition turns out to be valid. Otherwise, is a normal sensor node of EIoT. Therefore, in the case of sinkhole attack, the condition becomes true.
| Algorithm 1 Sinkhole attacker node existence algorithm in EIoT. |
|
3.4.2. Sinkhole Attacker Node Confirmation Algorithm in EIoT
The “sinkhole attacker node existence algorithm in EIoT” provides a list of suspected attacker nodes. However, to prove a suspected node is an attacker node, the sinkhole attacker node confirmation algorithm in EIoT, which comes under Algorithm 2, is required.
To perform this task, executes the following steps. If an edge node does not receive data packets from a suspicious node , it will try to segregate that node as or normal (genuine) node which completely drained its battery (due to node malfunctioning). In such case, sends to and waits for some time for its response. If holds, it indicates the expiry of waiting time. If does not get and also from , it is the case of failure of . Note that in the threshold value of waiting time other factors, such as network congestion, are also included. If receives , but not , is confirmed as . It is also determined that is a kind of which consumes all packets and does not forward them towards the destination (). If receives the and also from , checks the integrity of by using hash algorithm (i.e., SHA1 or SAH256) [56]. If the integrity does not hold, is treated as the which can modify . Another case is that receives and also from but the quality of service of the network is not up to the mark [57]. is a powerful node which can keep the quality of the communication up to the mark [57]. For example, may forward the UDP packets but not the TCP packets. If all these features are included then it becomes a sign of selective forwarding of packets (a kind of packet forwarding attack) [57,58,59]. For the detection purpose, can execute the following steps if the count of packets for a particular service (i.e., TCP) is less than the threshold value of count of packets in a particular duration of time, that is, . Then considers node as . Further note that the threshold value of count of packets in a particular duration of time is an empirical value which can be set at at the time of the deployment of the different nodes. When transmits the to , it waits for some time for its response. If holds, where is the “threshold value of the waiting time”, it indicates the expiry of waiting time. If receives , it waits for the receiving of from . If receives after the expiry of the waiting time (), the node is identified as which can delay the packets before forwarding them towards the destination (). After the detection, blacklists and adds s to the list .
| Algorithm 2 Sinkhole attacker node confirmation algorithm in EIoT |
|
4. Mathematical Models for SAD-EIoT
In this part of the paper, the various mathematical models utilised in SAD-EIoT such as packet delivery ratio, “throughput” and end-to-end delay for edge-based IoT environment are explained [16,17,24].
4.1. Packet Delivery Ratio
Suppose the symbols , and are respectively the “packet delivery ratios” associated with the normal flow, sinkhole attack and SAD-EIoT. Further, assume that , , , and represent the count of “data packets” sent by IoT sensing devices, “authentic packets” received by an edge node, , “data packets that are not transmitted by sinkhole nodes”, “data packets that are not transmitted by the sinkhole nodes ” and “data packets that are not transmitted by sinkhole nodes ”, respectively. Thus it is clear that = . The estimation of “packet delivery ratio ” with respect to “normal traffic flow” is given as [16,17,24]:
Under sinkhole attack, can be computed as
under the proposed method “SAD-EIoT” can also be formulated as
The packet loss rate is an additional important network parameter that is explained as the number of lost packets per unit time and it can be computed as where the “total time (in seconds)” is and the total lost packets is denoted by . It is also very important for a dependable network communication to keep packet loss rate as low as possible. The mathematical model for packet loss rate can be defined in a similar way as the packet delivery ratio.
4.2. Throughput
Let , and represent the “throughput of the network” under the various scenarios, for example, “normal flow”, sinkhole attack and SAD-EIoT, respectively. Let us assume , and are the “packets delivery time” under “normal flow”, sinkhole attack and SAD-EIoT, respectively. Then, the throughput under normal flow of traffic as follows [16,17,24]:
Similarly, the throughput under sinkhole attack can be computed as
and the throughput under the deployment of SAD-EIoT is represented by
where a data packet size is represented by .
4.3. End-to-End Delay
Let , and be the “end-to-end delays” under different scenarios such as “normal flow”, sinkhole attack and SAD-EIoT, respectively. Then, the end-to-end delay under normal flow of traffic can be approximated as [16,17,24]:
where can be represented as
is the “receiving time”, is the “sending time” of a “packet i” and p is the “total number of packets”.
The end-to-end delay under sinkhole attack is approximated as
where n denotes total IoT sensing nodes in the network, is the count of sinkhole nodes, counts towards “number of normal nodes for sinkhole attack scenario” and is the “delay corresponding to sinkhole attacker nodes”. Finally, the “end-to-end delay under the proposed SAD-EIoT” can be computed as
where is the “number of nodes identified as normal nodes” by SAD-EIoT, but these are actually sinkhole nodes, is the normal node count in SAD-EIoT and represents the delay associated with nodes. Hence, if the count of false negative nodes is zero, the end-to-end delay will be .
5. Analysis of SAD-EIoT
In this part of the paper, the analysis of the security of SAD-EIoT, along with its communication and computational costs is conducted.
5.1. Security Analysis
For an IoT sensing node, say , the corresponding edge node has the responsibility to keep information like its identity , its “remaining energy ”, hop count value and “rank information ”. If a is placed successfully in EIoT then it can start to damage normal network operations (i.e., transmitted packets can be dropped, delayed, updated or selectively forwarded). Designed SAD-EIoT has the capability to detect s. This work is divided into two phases. In “phase 1”, it first identifies the existence of suspected s in EIoT by using the steps of “Sinkhole attacker node existence algorithm in EIoT (Algorithm 1)”. This algorithm uses parameters, such as node ’s identity , its “remaining energy ”, hop count value and “rank information ”. A node is identified as a suspected if , and where and are threshold values of network hop count, remaining energy and , are lower and upper limits of ranks for a particular node (i.e., ). After successful execution of phase 1, the “sinkhole attacker node confirmation algorithm in EIoT (Algorithm 2)” is accomplished in phase 2. If an edge node does not receive messages from a particular node , then first it confirms the node is or “a case of node failure”. To confirm this sends the messages to node , and starts the “waiting time counter”. If waiting time is over and does not receive and from IoT sensor , then it is determined that this is a case of node failure (i.e., is a failure node). Otherwise, if receives the , but it does not receive , is detected as which has the capability to drop the packets. All these analyses are preformed by using the above two cases discussed in Section 3.4.2. Similarly, the security of SAD-EIoT for other types of s can be confirmed. Therefore, designed SAD-EIoT is capable enough to defend edge-based IoT communication environment from different types of s.
5.2. Communication Cost
For the communication cost analysis, n nodes in edge-based IoT environment are considered. In a scenario of a normal flow of traffic, each edge node sends n number of messages ” to IoT sensors. Then IoT sensors have to reply with n number of “status response messages” to . Moreover, also receives at most n number of “data messages ”. Therefore, total number of messages exchanged in the case of normal flow of traffic can be estimated as . Whereas in the case of sinkhole attack, only gets “data messages ” where are the messages dropped by sinkhole attacker nodes (s) which drop the packets and are the messages dropped by s which selectively drop (in selective forwarding case) the packets. The total number of different messages exchanged under sinkhole attack can be estimated as .
Under the scenario of SAD-EIoT, when does not receive the data messages from some of the s, it resends number of messages only to sinkhole message dropping attacker nodes and sinkhole selective forwarding attacker nodes. The sinkhole message dropping attacker and sinkhole selective forwarding attacker nodes send only messages but not messages. Note that receives and data messages from s which delay the packets and s which modify the packets. Whereas only receives number of messages. After the successful completion of both phases of proposed mechanism, identifies the different types of sinkhole nodes and sends information messages to alert the other legitimate nodes of the network. Where are messages corresponding to s which delay the packets and are s which modify the packets. It is understood that does not transmit any information messages to s. Hence, as a result, the total number of messages exchanged under the implementation of SAD-EIoT can be estimated as .
It is assumed that identity, “hash digest (output) (if we apply SHA-1 hash algorithm)”, “remaining energy field”, “rank information field” and data fields in various types of messages are of 32 bits, 160 bits, 32 bits, 32 bits and 160 bits, respectively. Therefore, different messages’ sizes can be estimated as , , and require 384 bits, 416 bits, 416 bits and 192 bits, respectively.
5.3. Computation Cost
As discussed earlier, SAD-EIoT is divided into two phases. In the first phase of SAD-EIoT, the presence of suspected attacker nodes are detected using the steps of the “sinkhole attacker node existence algorithm in EIoT”. Further note that these nodes may or may not be the attacker nodes. If s exist in EIoT, this will be confirmed by Algorithm 2. First Algorithm 1 is executed and then Algorithm 2 will be executed. The different steps of Algorithm 1 and Algorithm 2 are executed in linear time, which can be executed with time complexity , where n is number of IoT sensing nodes installed in EIoT. Thus, the cumulative time complexity of SAD-EIoT is estimated as which is needed for an .
Remark 3.
It is important to notice that in designed SAD-EIoT, an IoT sensor node needs to send one “status response message ” and one to an edge node . Furthermore, needs to compute “two HMAC operations” in the transmission of and messages. Apart from that needs another HMAC operation in the validation of message. Hash function computations are very lightweight which again surges in very low computational cost for node. The provided estimation infers that SAD-EIoT is very helpful and handy for the “extremely resource-constrained IoT sensors in EIoT” due to low computational cost and lower number of messages exchanged.
6. Practical Implementation of SAD-EIoT
In this part of the paper, the designed SAD-EIoT is practically implemented using the widely-used NS2 2.35 simulation software tool [62].
6.1. Simulation Environment
SAD-EIoT is implemented on Ubuntu Linux 14.04 LTS platform using the NS2 simulation software tool [16,17,18]. The considered deployment area is 650 × 250 m. In the considered deployment field, 121 nodes which consist of different devices such as cloud server, IoT sensor nodes and edge router are placed. This deployment field consists of one cloud server along with six edge nodes. Table 3 consists of values of different simulation parameters used in the practical demonstrations. The “Constant bitrate (CBR)/UDP (User Datagram Protocol)” is treated as the traffic type. The considered routing protocol is “Ad Hoc On-Demand Distance Vector (AODV)” which is applicable for routing methods in wireless communications. That supports both “unicast as well as multicast routing” mechanism [63]. The communication range of an IoT device (sensor) is taken to be 100 m.

Table 3.
Parameters used in simulations.
6.2. Simulation Scenarios
The simulations of EIoT environment are performed for different cases such as normal traffic flow, under sinkhole attack and under the deployment of SAD-EIoT. The information about the different scenarios is provided below.
- Scenario of normal flow of traffic: The scenario of EIoT in the case of normal flow of traffic is simulated, containing all 121 normal nodes. Therefore, traffic of the network flows normally without any problem.
- Scenario of sinkhole attack: The scenario of EIoT under sinkhole attack is further simulated which consists of attacker nodes i.e., 24 IoT sensor nodes becomes s. Remaining nodes are normal nodes out of 121. The 24 attacker nodes contain various types of nodes like the “sinkhole attacker nodes which drop the packets”, “sinkhole nodes which delay the messages”, “sinkhole nodes which modify the messages” and “sinkhole nodes which selectively forward the messages”.
- Scenario of SAD-EIoT: The EIoT scenario under sinkhole attack along with the implementation of SAD-EIoT is further simulated. For the detection of s, each edge node transmits and receives various types of messages in EIoT. After performing the detection process blacklists all detected s and also informs other legitimate IoT sensor nodes through alert (information) messages.
6.3. Discussion on Simulation Results
In this part of the paper, the following statistics for SAD-EIoT are accomplished: (i) packet delivery ratio, (ii) end-to-end delay (in seconds), (iii) “throughput” (in bps), (iv) packet loss rate, (v) “detection rate ”, (vi) “false positive rate ”.
6.3.1. Effect on Packet Delivery Ratio
The packet delivery ratio is formulated as “the ratio of packets received at the base station to packets transmitted by source nodes” (for example, from to ). Table 4 provides packet delivery ratio in different instances, such as normal flow of traffic, under sinkhole attack and “under deployed SAD-EIoT”. From Table 4 and Figure 10, it is confirmed that the packet delivery ratio for the instances under normal flow of traffic, under sinkhole attack and “under SAD-EIoT” are , and , respectively. Thus, it is observed that the packet delivery ratio is indubitably improved under the deployment of “SAD-EIoT” as compared to the case of sinkhole attack.

Table 4.
Obtained statistics of EIoT for different cases.
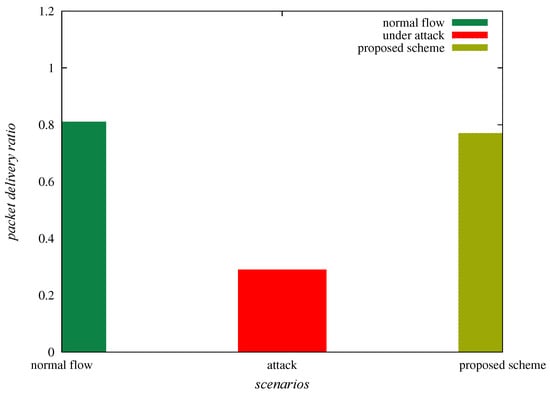
Figure 10.
Comparison of packet delivery ratios.
6.3.2. Effect on Packet Loss Rate
The packet loss rate is also one of the important network parameters. It is estimated as the “number of packets lost per unit time”. It is required that for a reliable communication of the network, the packet loss rate should be as least as possible. Table 4 and Figure 11 show that the packet loss rate (packets per second ), under normal flow of traffic, under sinkhole attack and “under SAD-EIoT” are , and , respectively. Thus, it is observed that the packet loss rate is indubitably reduced under the deployment of “SAD-EIoT” as compared to the case of sinkhole attack.
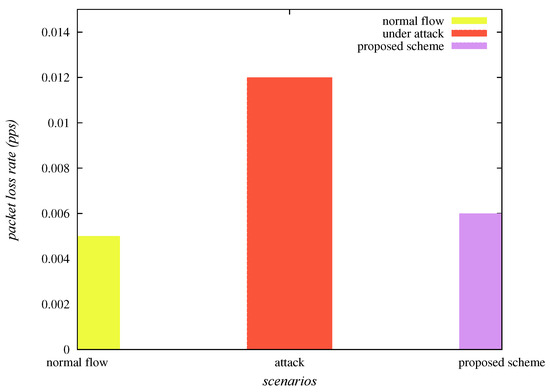
Figure 11.
Comparison of packet loss rates.
6.3.3. Effect on End-to-End Delay
The end-to-end delay is estimated as “the average time taken by the data packets to arrive at the base station, for example, from ”. Table 4 represents the “end-to-end delay (in seconds)”, under normal flow of traffic, under sinkhole attack and “under the deployment of SAD-EIoT”. Table 4 and Figure 12 confirm that the end-to-end delay, under normal flow of traffic, under sinkhole attack and “under SAD-EIoT” are , and , respectively. Thus, it is cleared that the end-to-end delay is indubitably reduced under the deployment of “SAD-EIoT” as compared to the case of sinkhole attack.
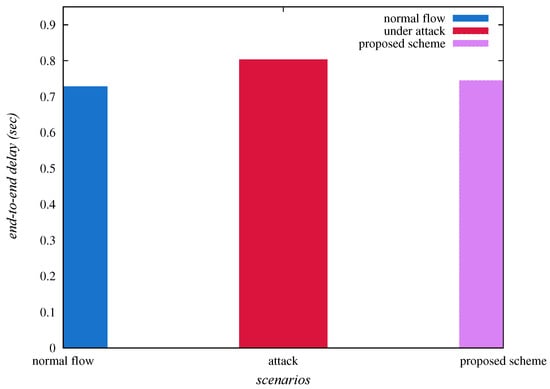
Figure 12.
Comparison of end-to-end delays.
6.3.4. Effect on Throughput
Throughput is “the number of bits transferred per unit time”. Table 4 represents the throughput (in bps), under normal flow of traffic, under sinkhole attack and “under the deployment of SAD-EIoT”. From Table 4 and Figure 13, it is confirmed that the “throughput”, under normal flow of traffic, under sinkhole attack and “under SAD-EIoT” are , and , respectively. Thus it is observed that the end-to-end delay is indubitably improved under the deployment of “SAD-EIoT” as compared to the case of sinkhole attack.
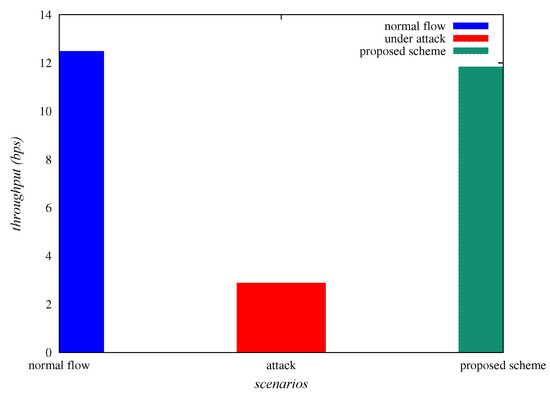
Figure 13.
Comparison of throughput.
The diverse statistics of SAD-EIoT as per the various scenarios are provided in Table 4.
6.3.5. Effect on Detection Rate and False Positive Rate
The other essential performance parameter of an IDS is the (which is also known as “true positive rate or sensitivity or hit rate” or “false positive rate or fall out ”). It is very essential to consider this parameter in the evaluation of performance of a proposed intrusion detection scheme. can be estimated as “the number of attackers detected by an IDS divided by the total number of attackers present in the test sample” which is formulated as
whereas is estimated as “the number of nodes falsely detected as attacker nodes” which is formulated as
The obtained results are briefed as follows:
- A confusion matrix of the obtained results is constructed and its details are provided in Table 5. The provided matrix clears that SAD-EIoT detects 23 s.
 Table 5. Confusion matrix for SAD-EIoT.Thus, there is a total of 23 nodes (actual attackers), one node (normal nodes), 96 nodes (normal nodes) and one node (actually an attacker but identified as a normal node).
Table 5. Confusion matrix for SAD-EIoT.Thus, there is a total of 23 nodes (actual attackers), one node (normal nodes), 96 nodes (normal nodes) and one node (actually an attacker but identified as a normal node). - There are in total 24 s and 81 normal nodes. Accordingly, and are and respectively.
7. Comparative Analysis of SAD-EIoT with Other Related Existing Schemes
In this part of the paper, the results of SAD-EIoT are compared with other closely related schemes proposed by Salehi et al. [31], Wang et al. [32], Wang et al. [33], Wang et al. [34], Wazid et al. [17] and Wazid et al. [18]. The comparative analysis of outcomes is presented in Table 6. The following observations have been made:

Table 6.
Accuracy comparison among existing schemes and SAD-EIoT.
- The for Salehi et al.’s scheme [31], Wang et al.’s scheme [32], Wang et al.’s scheme [33], Wang et al.’s scheme [34], Wazid et al.’s scheme [17], Wazid et al.’s scheme [18] and SAD-EIoT are 93.00, 90.96, 86.00, 83.00, 95.00, 95.00 and 95.83, respectively.
- The “false positive rate (FPR)” for Salehi et al.’s scheme [31], Wang et al.’s scheme [32], Wazid et al.’s scheme [17], Wazid et al.’s scheme [18] and SAD-EIoT is 10.00, 2.06, 1.25, 1.23 and 1.03, respectively.
Therefore, the designed SAD-EIoT performs better than other related existing schemes.
The comparison of computational complexities of existing schemes and SAD-EIoT is provided in Table 7. The computational complexities for the schemes of Salehi et al. [31], Wang et al. [32], Wang et al. [33], Wang et al. [34], Wazid et al. [17], Wazid et al. [18] and SAD-EIoT are , , , , , and respectively. Here, n denotes the total number of deployed IoT sensing nodes or sensor nodes in the specified area. The complexities for other existing schemes are quadratic whereas for SAD-EIoT they are linear. Hence, SAD-EIoT performed better in terms of computational costs.

Table 7.
Comparison of computational complexity among existing schemes and SAD-EIoT.
8. Concluding Remarks
As discussed in this work, the performance of edge-based IoT communication degrades very rapidly under the presence of various sinkhole attacker nodes (s). Most of the existing schemes for sinkhole node detection are not effective as they cannot identify all possible types of s in EIoT. Moreover, the existing intrusion detection schemes have other limitations, such as inefficiency in terms of communication and computation costs. To overcome this problem, an efficient intrusion detection scheme for the detection of various kinds of s in EIoT (SAD-EIoT) is proposed. SAD-EIoT requires a lower number of exchanged messages that further causes reduction in overall communication cost. Furthermore, SAD-EIoT achieves around detection rate and false positive rate, which is considerably better than other related existing schemes. The performed security analysis also confirms the resilience of SAD-EIoT against sinkhole attack. Apart from these characteristics, in SAD-EIoT, the resource-constrained IoT devices (sensors) need less computation and communication costs because the resource-rich edge node only executes the steps of s detection algorithm. Eventually, SAD-EIoT will be a suitable match for those applications which can be used in critical and sensitive operations (for example, surveillance, security and monitoring systems).
In the future, a testbed for the proposed SAD-EIoT scheme along with detection of a greater number of attacks, such as blackhole, greyhole, wormhole and other routing attacks in IoT environment can be implemented and analysed.
Author Contributions
All the authors contributed equally to this work. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Science, ICT and Future Planning (2017R1A2B1002147), in part by FCT/MCTES through national funds and when applicable cofunded EU funds under the project UIDB/EEA/50008/2020 and in part by Brazilian National Council for Scientific and Technological Development (CNPq) via Grant No. 309335/2017-5.
Acknowledgments
We thank the anonymous reviewers and the editor for their valuable comments, which helped us to improve the quality and presentation of the paper.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Challa, S.; Wazid, M.; Das, A.K.; Kumar, N.; Reddy, A.G.; Yoon, E.; Yoo, K. Secure Signature-Based Authenticated Key Establishment Scheme for Future IoT Applications. IEEE Access 2017, 5, 3028–3043. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Esposito, C.; Castiglione, A.; Pop, F.; Choo, K.K.R. Challenges of Connecting Edge and Cloud Computing: A Security and Forensic Perspective. IEEE Cloud Comput. 2017, 4, 13–17. [Google Scholar] [CrossRef]
- Sheth, A. Internet of Things to Smart IoT Through Semantic, Cognitive, and Perceptual Computing. IEEE Intell. Syst. 2016, 31, 108–112. [Google Scholar] [CrossRef]
- Raut, S. What Is Edge Computing? Available online: http://bigdata-madesimple.com/edge-computing/ (accessed on 18 January 2020).
- Marjanović, M.; Antonić, A.; Žarko, I.P. Edge Computing Architecture for Mobile Crowdsensing. IEEE Access 2018, 6, 10662–10674. [Google Scholar] [CrossRef]
- Stojmenovic, I.; Wen, S. The Fog computing paradigm: Scenarios and security issues. In Proceedings of the Federated Conference on Computer Science and Information Systems, Warsaw, Poland, 7–10 September 2014; pp. 1–8. [Google Scholar]
- Choo, K.K.R.; Rana, O.F.; Rajarajan, M. Cloud Security Engineering: Theory, Practice and Future Research. IEEE Trans. Cloud Comput. 2017, 5, 372–374. [Google Scholar] [CrossRef]
- Sukhov, A.; Sagatov, E.; Baskakov, A. Rank distribution for determining the threshold values of network variables and the analysis of DDoS attacks. Procedia Eng. 2017, 201, 417–427. [Google Scholar] [CrossRef]
- Zhao, P.; Li, J.; Zeng, F.; Xiao, F.; Wang, C.; Jiang, H. ILLIA: Enabling k-Anonymity-Based Privacy Preserving against Location Injection Attacks in Continuous LBS Queries. IEEE Internet Things J. 2018, 5, 1033–1042. [Google Scholar] [CrossRef]
- Wang, C.; Liu, G.; Huang, H.; Feng, W.; Peng, K.; Wang, L. MIASec: Enabling Data Indistinguishability against Membership Inference Attacks in MLaaS. IEEE Trans. Sustain. Comput. 2019. [Google Scholar] [CrossRef]
- Messerges, T.S.; Dabbish, E.A.; Sloan, R.H. Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 2002, 51, 541–552. [Google Scholar] [CrossRef]
- Ryoo, J.; Han, D.; Kim, S.; Lee, S. Performance Enhancement of Differential Power Analysis Attacks with Signal Companding Methods. IEEE Signal Process. Lett. 2008, 15, 625–628. [Google Scholar] [CrossRef]
- Rajan, A.; Jithish, J.; Sankaran, S. Sybil attack in IOT: Modelling and defenses. In Proceedings of the International Conference on Advances in Computing, Communications and Informatics (ICACCI’17), Udupi, India, 13–16 September 2017; pp. 2323–2327. [Google Scholar]
- Zhang, K.; Liang, X.; Lu, R.; Shen, X. Sybil Attacks and Their Defenses in the Internet of Things. IEEE Internet Things J. 2014, 1, 372–383. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K. A Secure Group-Based Blackhole Node Detection Scheme for Hierarchical Wireless Sensor Networks. Wirel. Pers. Commun. 2017, 94, 1165–1191. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumari, S.; Khan, M.K. Design of sinkhole node detection mechanism for hierarchical wireless sensor networks. Secur. Commun. Networks 2016, 9, 4596–4614. [Google Scholar] [CrossRef]
- Wazid, M.; Reshma Dsouza, P.; Das, A.K.; Bhat K, V.; Kumar, N.; Rodrigues, J.J.P.C. RAD-EI: A routing attack detection scheme for edge-based Internet of Things environment. Int. J. Commun. Syst. 2019, 32, e4024. [Google Scholar] [CrossRef]
- Dong, D.; Li, M.; Liu, Y.; Li, X.; Liao, X. Topological Detection on Wormholes in Wireless Ad Hoc and Sensor Networks. IEEE/ACM Trans. Netw. 2011, 19, 1787–1796. [Google Scholar] [CrossRef]
- Hamedheidari, S.; Rafeh, R. A novel agent-based approach to detect sinkhole attacks in wireless sensor networks. Comput. Secur. 2013, 37, 1–14. [Google Scholar] [CrossRef]
- Ngai, E.C.H.; Liu, J.; Lyu, M.R. An efficient intruder detection algorithm against sinkhole attacks in wireless sensor networks. Comput. Commun. 2007, 30, 2353–2364. [Google Scholar] [CrossRef]
- Shafiei, H.; Khonsari, A.; Derakhshi, H.; Mousavi, P. Detection and mitigation of sinkhole attacks in wireless sensor networks. J. Comput. Syst. Sci. 2014, 80, 644–653. [Google Scholar] [CrossRef]
- Wazid, M.; Katal, A.; Sachan, R.S.; Goudar, R.H.; Singh, D.P. Detection and prevention mechanism for Blackhole attack in Wireless Sensor Network. In Proceedings of the IEEE International Conference on Communications and Signal Processing (ICCSP’13), Melmaruvathur, India, 3–5 April 2013; pp. 576–581. [Google Scholar]
- Wazid, M.; Das, A.K. An Efficient Hybrid Anomaly Detection Scheme Using K-Means Clustering for Wireless Sensor Networks. Wirel. Pers. Commun. 2016, 90, 1971–2000. [Google Scholar] [CrossRef]
- Chatterjee, S.; Das, A.K. An effective ECC-based user access control scheme with attribute-based encryption for wireless sensor networks. Secur. Commun. Netw. 2015, 8, 1752–1771. [Google Scholar] [CrossRef]
- Das, A.K. A secure and robust temporal credential-based three-factor user authentication scheme for wireless sensor networks. Peer-To-Peer Netw. Appl. 2016, 9, 223–244. [Google Scholar] [CrossRef]
- Das, A.K. A secure and effective biometric-based user authentication scheme for wireless sensor networks using smart card and fuzzy extractor. Int. J. Commun. Syst. 2017, 30, 1–25. [Google Scholar] [CrossRef]
- Das, A.K. A Secure and Efficient User Anonymity-Preserving Three-Factor Authentication Protocol for Large-Scale Distributed Wireless Sensor Networks. Wirel. Pers. Commun. 2015, 82, 1377–1404. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A.C. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar] [CrossRef]
- Salehi, S.A.; Razzaque, M.A.; Naraei, P.; Farrokhtala, A. Detection of sinkhole attack in wireless sensor networks. In Proceedings of the IEEE International Conference on Space Science and Communication (IconSpace’13), Melaka, Malaysia, 1–3 July 2013; pp. 361–365. [Google Scholar]
- Wang, S.S.; Yan, K.Q.; Wang, S.C.; Liu, C.W. An Integrated Intrusion Detection System for Cluster-based Wireless Sensor Networks. Expert Syst. Appl. 2011, 38, 15234–15243. [Google Scholar] [CrossRef]
- Wang, Y.; Fu, W.; Agrawal, D.P. Gaussian versus Uniform Distribution for Intrusion Detection in Wireless Sensor Networks. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 342–355. [Google Scholar] [CrossRef]
- Wang, Y.; Wang, X.; Xie, B.; Wang, D.; Agrawal, D.P. Intrusion Detection in Homogeneous and Heterogeneous Wireless Sensor Networks. IEEE Trans. Mob. Comput. 2008, 7, 698–711. [Google Scholar] [CrossRef]
- Zhan, G.; Shi, W.; Deng, J. Design and Implementation of TARF: A Trust-Aware Routing Framework for WSNs. IEEE Trans. Dependable Secur. Comput. 2012, 9, 184–197. [Google Scholar] [CrossRef]
- Shin, S.; Kwon, T.; Jo, G.; Park, Y.; Rhy, H. An Experimental Study of Hierarchical Intrusion Detection for Wireless Industrial Sensor Networks. IEEE Trans. Ind. Inform. 2010, 6, 744–757. [Google Scholar] [CrossRef]
- Yu, Y.; Li, K.; Zhou, W.; Li, P. Trust Mechanisms in Wireless Sensor Networks: Attack Analysis and Countermeasures. J. Netw. Comput. Appl. 2012, 35, 867–880. [Google Scholar] [CrossRef]
- Liu, Y.; Ma, M.; Liu, X.; Xiong, N.; Liu, A.; Zhu, Y. Design and Analysis of Probing Route to Defense Sink-hole Attacks for Internet of Things Security. IEEE Trans. Netw. Sci. Eng. 2018. [Google Scholar] [CrossRef]
- Chen, H.; Meng, C.; Shan, Z.; Fu, Z.; Bhargava, B.K. A Novel Low-Rate Denial of Service Attack Detection Approach in ZigBee Wireless Sensor Network by Combining Hilbert-Huang Transformation and Trust Evaluation. IEEE Access 2019, 7, 32853–32866. [Google Scholar] [CrossRef]
- Fang, W.; Xu, M.; Zhu, C.; Han, W.; Zhang, W.; Rodrigues, J.J.P.C. FETMS: Fast and Efficient Trust Management Scheme for Information-Centric Networking in Internet of Things. IEEE Access 2019, 7, 13476–13485. [Google Scholar] [CrossRef]
- Pongle, P.; Chavan, G. A survey: Attacks on RPL and 6LoWPAN in IoT. In Proceedings of the International Conference on Pervasive Computing (ICPC’15), Pune, India, 8–10 January 2015; pp. 1–6. [Google Scholar]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A Survey on Security and Privacy Issues in Internet-of-Things. IEEE Internet Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Lyu, C.; Zhang, X.; Liu, Z.; Chi, C. Selective Authentication Based Geographic Opportunistic Routing in Wireless Sensor Networks for Internet of Things Against DoS Attacks. IEEE Access 2019, 7, 31068–31082. [Google Scholar] [CrossRef]
- He, Y.; Han, G.; Wang, H.; Ansere, J.A.; Zhang, W. A sector-based random routing scheme for protecting the source location privacy in WSNs for the Internet of Things. Future Gener. Comput. Syst. 2019, 96, 438–448. [Google Scholar] [CrossRef]
- Airehrour, D.; Gutierrez, J.A.; Ray, S.K. SecTrust-RPL: A secure trust-aware RPL routing protocol for Internet of Things. Future Gener. Comput. Syst. 2019, 93, 860–876. [Google Scholar] [CrossRef]
- Sicari, S.; Rizzardi, A.; Miorandi, D.; Coen-Porisini, A. REATO: REActing TO Denial of Service attacks in the Internet of Things. Comput. Netw. 2018, 137, 37–48. [Google Scholar] [CrossRef]
- Deshmukh-Bhosale, S.; Sonavane, S.S. A Real-Time Intrusion Detection System for Wormhole Attack in the RPL based Internet of Things. Procedia Manuf. 2019, 32, 840–847. [Google Scholar] [CrossRef]
- Liu, G.; Quan, W.; Cheng, N.; Zhang, H.; Yu, S. Efficient DDoS attacks mitigation for stateful forwarding in Internet of Things. J. Netw. Comput. Appl. 2019, 130, 1–13. [Google Scholar] [CrossRef]
- Raoof, A.; Matrawy, A.; Lung, C. Routing Attacks and Mitigation Methods for RPL-Based Internet of Things. IEEE Commun. Surv. Tutor. 2019, 21, 1582–1606. [Google Scholar] [CrossRef]
- Mayzaud, A.; Badonnel, R.; Chrisment, I. A Distributed Monitoring Strategy for Detecting Version Number Attacks in RPL-Based Networks. IEEE Trans. Netw. Serv. Manag. 2017, 14, 472–486. [Google Scholar] [CrossRef]
- Cheng, Y.; Agrawal, D.P. An improved key distribution mechanism for large-scale hierarchical wireless sensor networks. Ad Hoc Netw. 2007, 5, 35–48. [Google Scholar] [CrossRef]
- Das, A.K. An unconditionally secure key management scheme for large-scale heterogeneous wireless sensor networks. In Proceedings of the First International on Communication Systems and Networks and Workshops (COMSNETS 2009), Bangalore, India, 5–10 January 2009; pp. 1–10. [Google Scholar]
- Das, A.K.; Sharma, P.; Chatterjee, S.; Sing, J.K. A dynamic password-based user authentication scheme for hierarchical wireless sensor networks. J. Netw. Comput. Appl. 2012, 35, 1646–1656. [Google Scholar] [CrossRef]
- Das, A.K. An efficient random key distribution scheme for large-scale distributed sensor networks. Secur. Commun. Netw. 2011, 4, 162–180. [Google Scholar] [CrossRef]
- Wang, J.; Dong, W.; Cao, Z.; Liu, Y. On the Delay Performance in a Large-Scale Wireless Sensor Network: Measurement, Analysis, and Implications. IEEE/ACM Trans. Netw. 2015, 23, 186–197. [Google Scholar] [CrossRef]
- Secure Hash Standard. FIPS PUB 180-1, National Institute of Standards and Technology (NIST), U.S. Department of Commerce, April 1995. 1995. Available online: http://csrc.nist.gov/publications/fips/fips180-4/fips-180-4.pdf (accessed on 18 January 2020).
- Farsi, M.; Badawy, M.; Moustafa, M.; Arafat Ali, H.; Abdulazeem, Y. A Congestion-Aware Clustering and Routing (CCR) Protocol for Mitigating Congestion in WSN. IEEE Access 2019, 7, 105402–105419. [Google Scholar] [CrossRef]
- Ren, J.; Zhang, Y.; Zhang, K.; Shen, X. Adaptive and Channel-Aware Detection of Selective Forwarding Attacks in Wireless Sensor Networks. IEEE Trans. Wirel. Commun. 2016, 15, 3718–3731. [Google Scholar] [CrossRef]
- Ren, K.; Lou, W.; Zhang, Y. LEDS: Providing Location-Aware End-to-End Data Security in Wireless Sensor Networks. IEEE Trans. Mob. Comput. 2008, 7, 585–598. [Google Scholar] [CrossRef]
- Ghazvini, M.; Vahabi, M.; Rasid, M.; Abdullah, R.; Musa, W. Low Energy Consumption MAC Protocol for Wireless Sensor Networks. In Proceedings of the IEEE 2nd International Conference on Sensor Technologies and Applications, Cap Esterel, France, 25–31 August 2008; pp. 49–54. [Google Scholar]
- Park, S.; Hong, S.W.; Lee, E.; Kim, S.H.; Crespi, N. Large-scale mobile phenomena monitoring with energy-efficiency in wireless sensor networks. Comput. Networks 2015, 81, 116–135. [Google Scholar] [CrossRef]
- The Network Simulator-ns-2. Available online: http://www.isi.edu/nsnam/ns/ (accessed on 18 January 2020).
- Perkins, C.E.; Royer, E.M. Ad-hoc on-demand distance vector routing. In Proceedings of the Second IEEE Workshop on Mobile Computing Systems and Applications (WMCSA’99), New Orleans, LA, USA, 25–26 February 1999; pp. 90–100. [Google Scholar]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).