A Secure Enhanced Non-Cooperative Cognitive Division Multiple Access for Vehicle-to-Vehicle Communication
Abstract
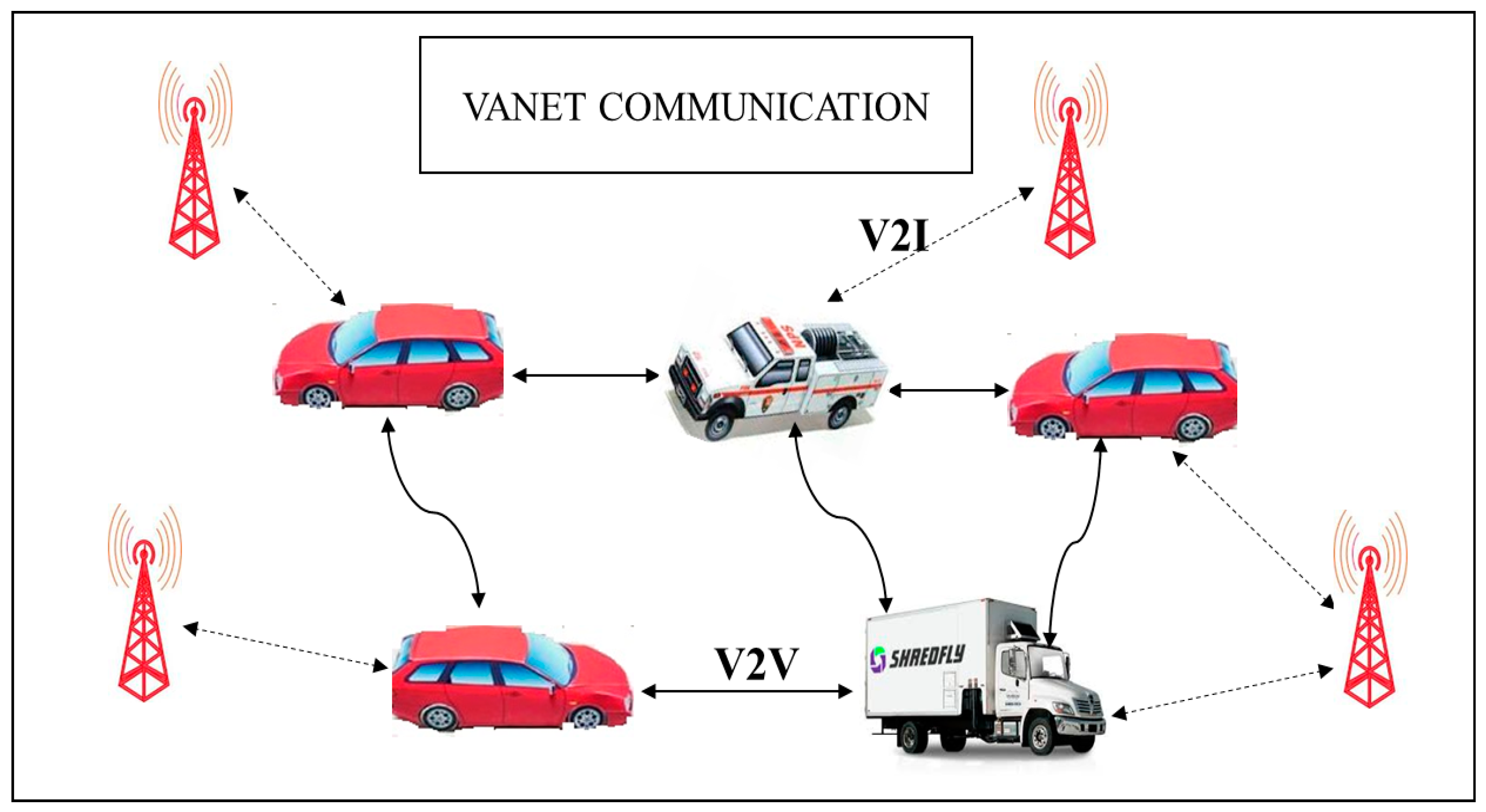
1. Introduction
- The message integrity and privacy are preserved using the commutative cryptography technique.
- The model preserves privacy in the presence of non-trusted or dishonest authorities.
- Our design incurs much lower overhead in providing security when compared to existing design considering throughput, collision and successful packet transmission performances.
2. Related Work
3. Proposed Secure Non-Cooperative Cognitive Division Multiple Access Model
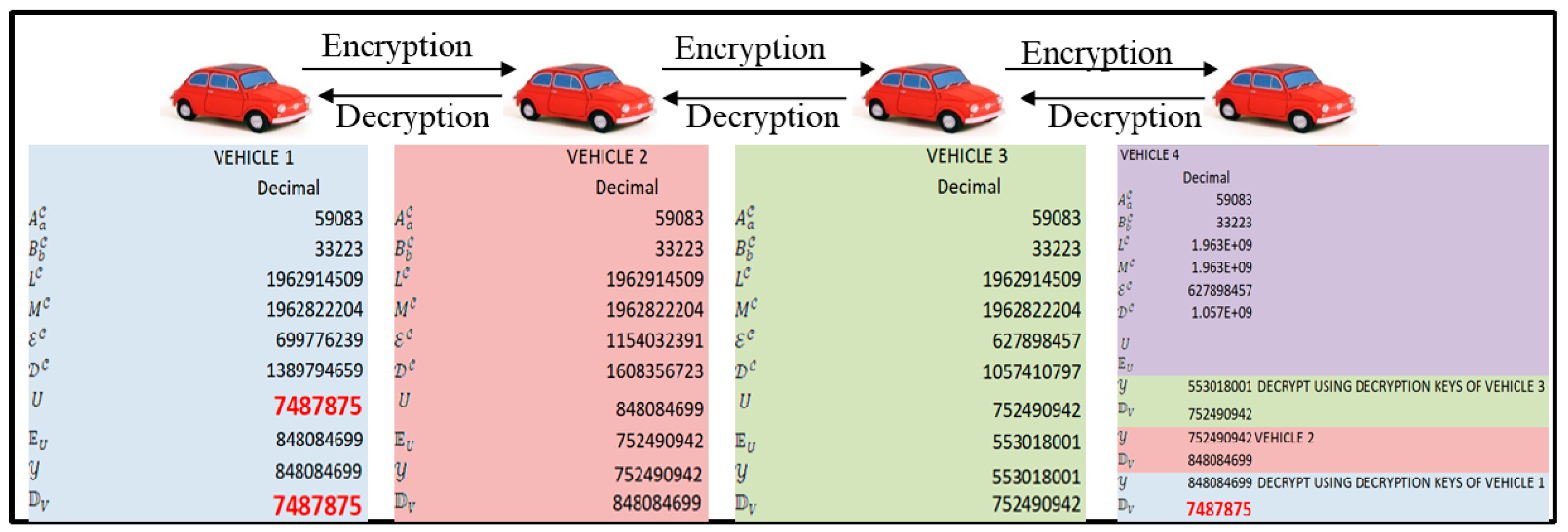
3.1. Commutative RSA (CRSA) Model
3.2. Proof of CRSA Model
4. Simulation Analysis and Result
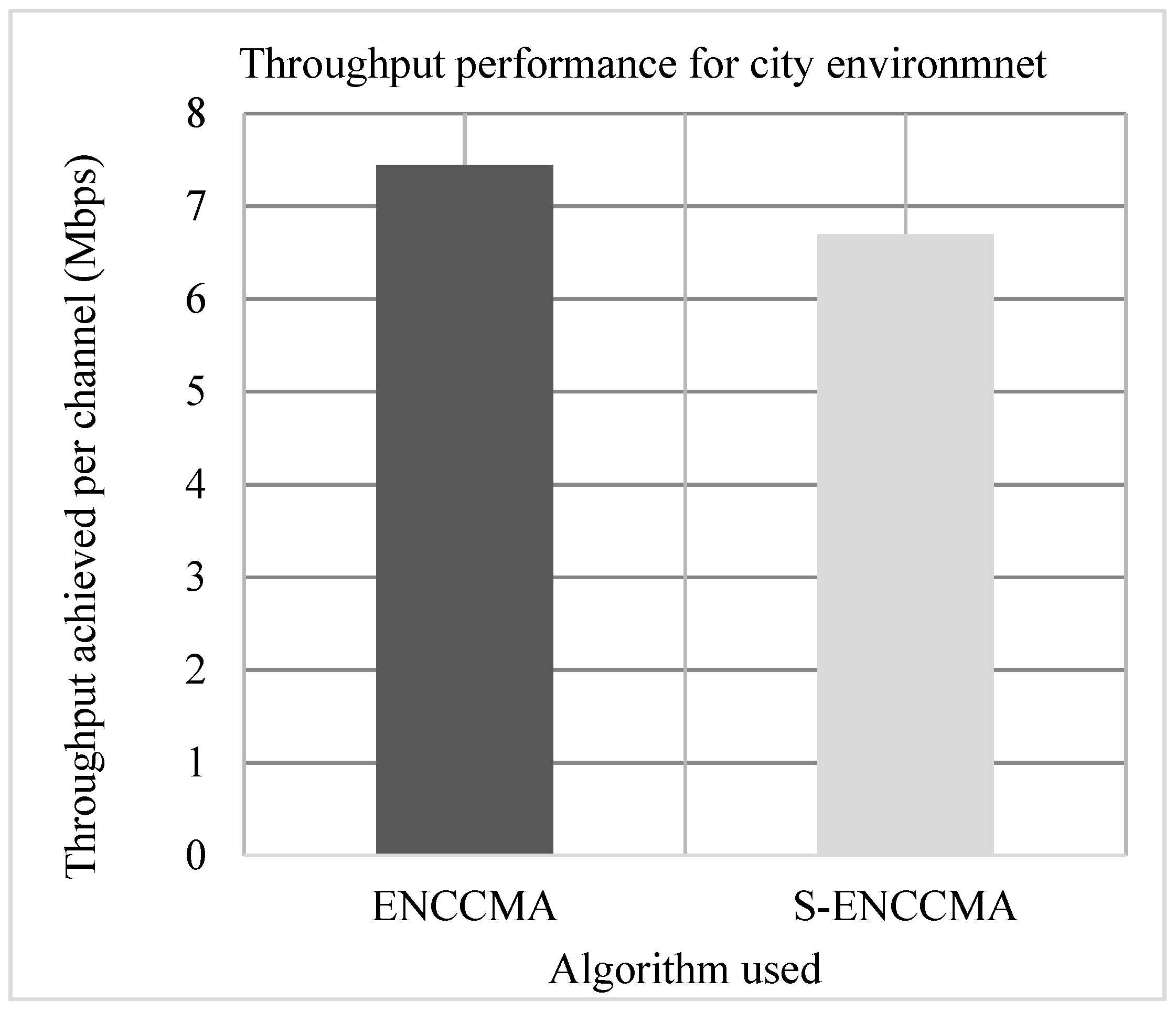
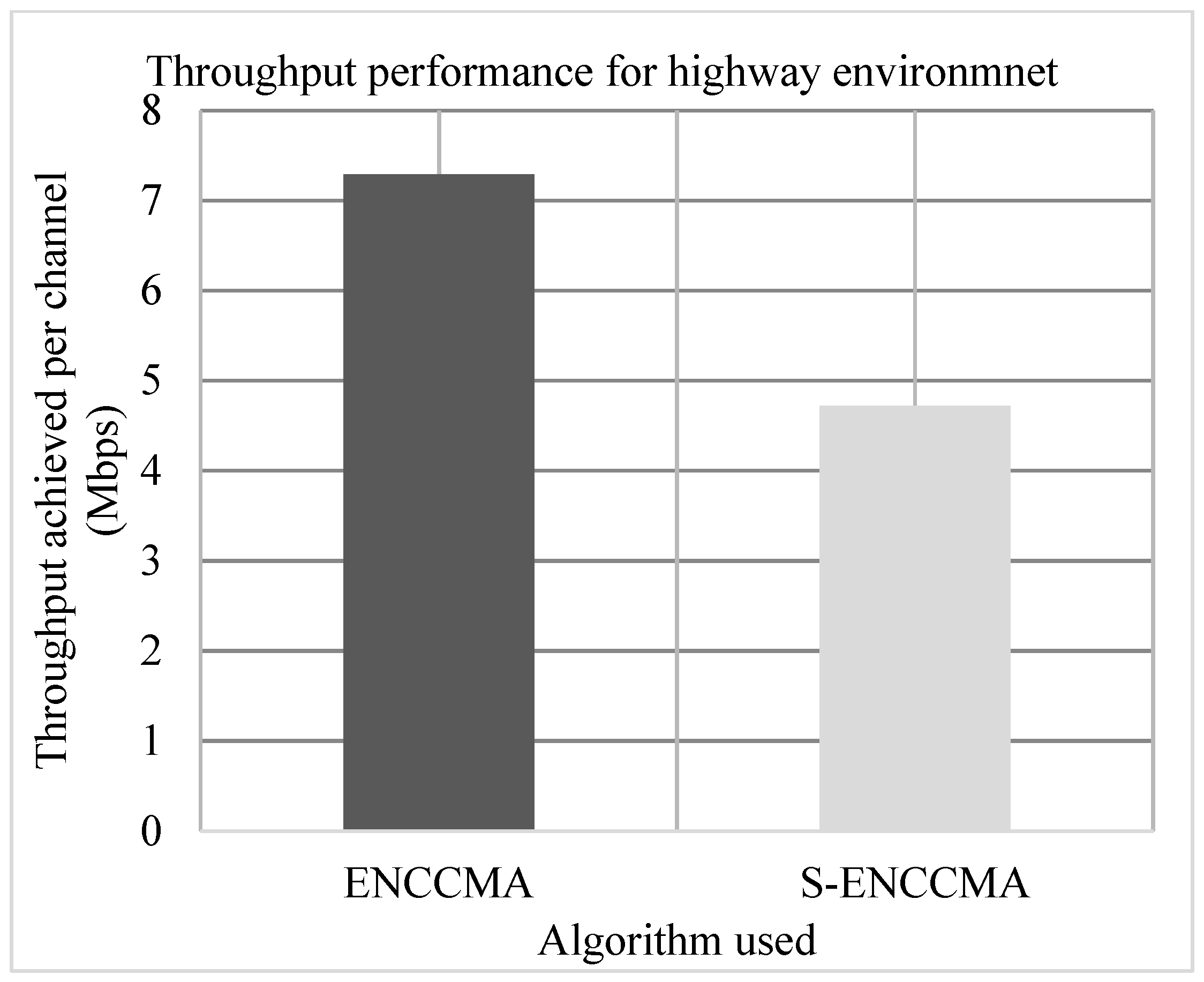
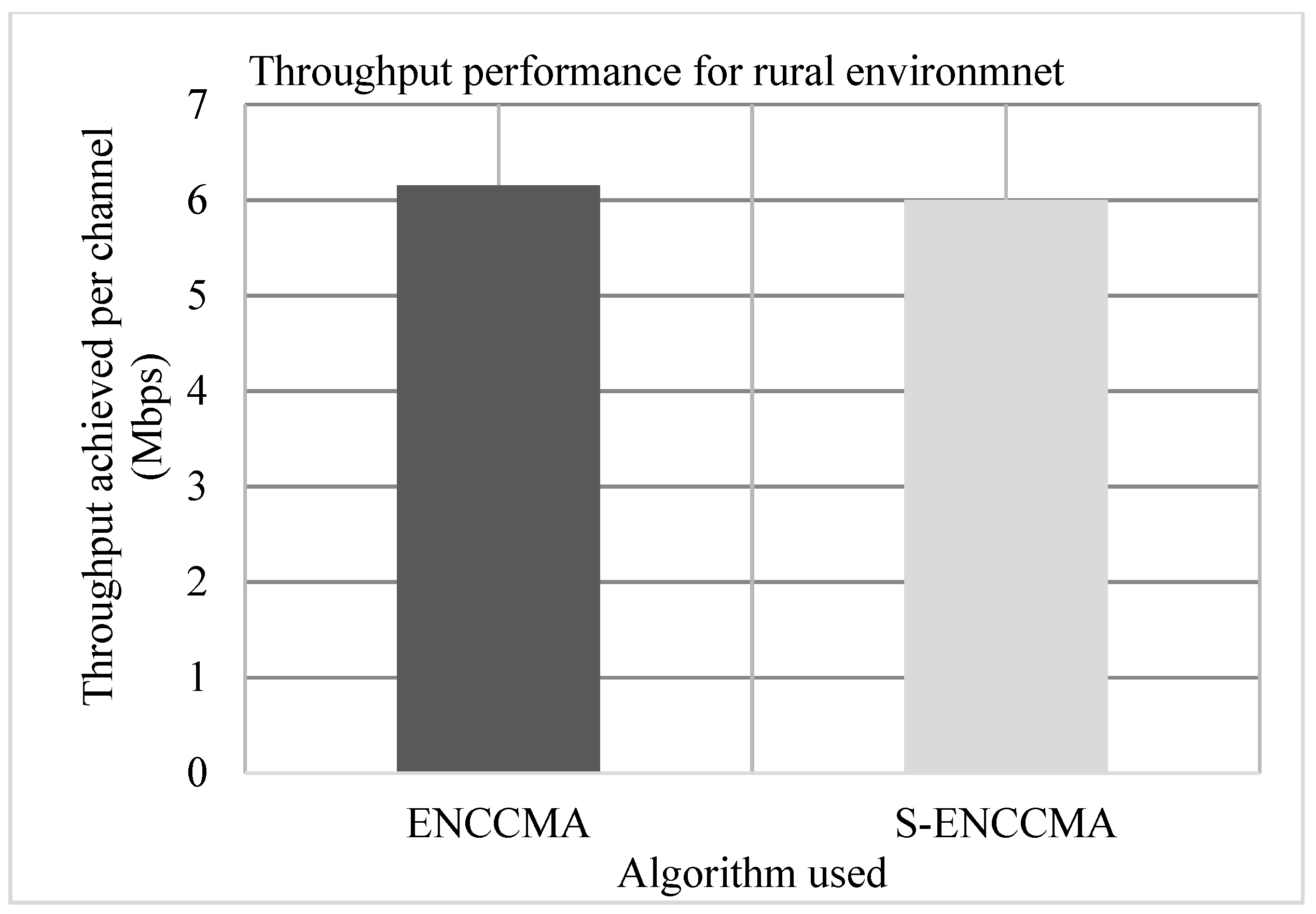
4.1. Throughput Performance
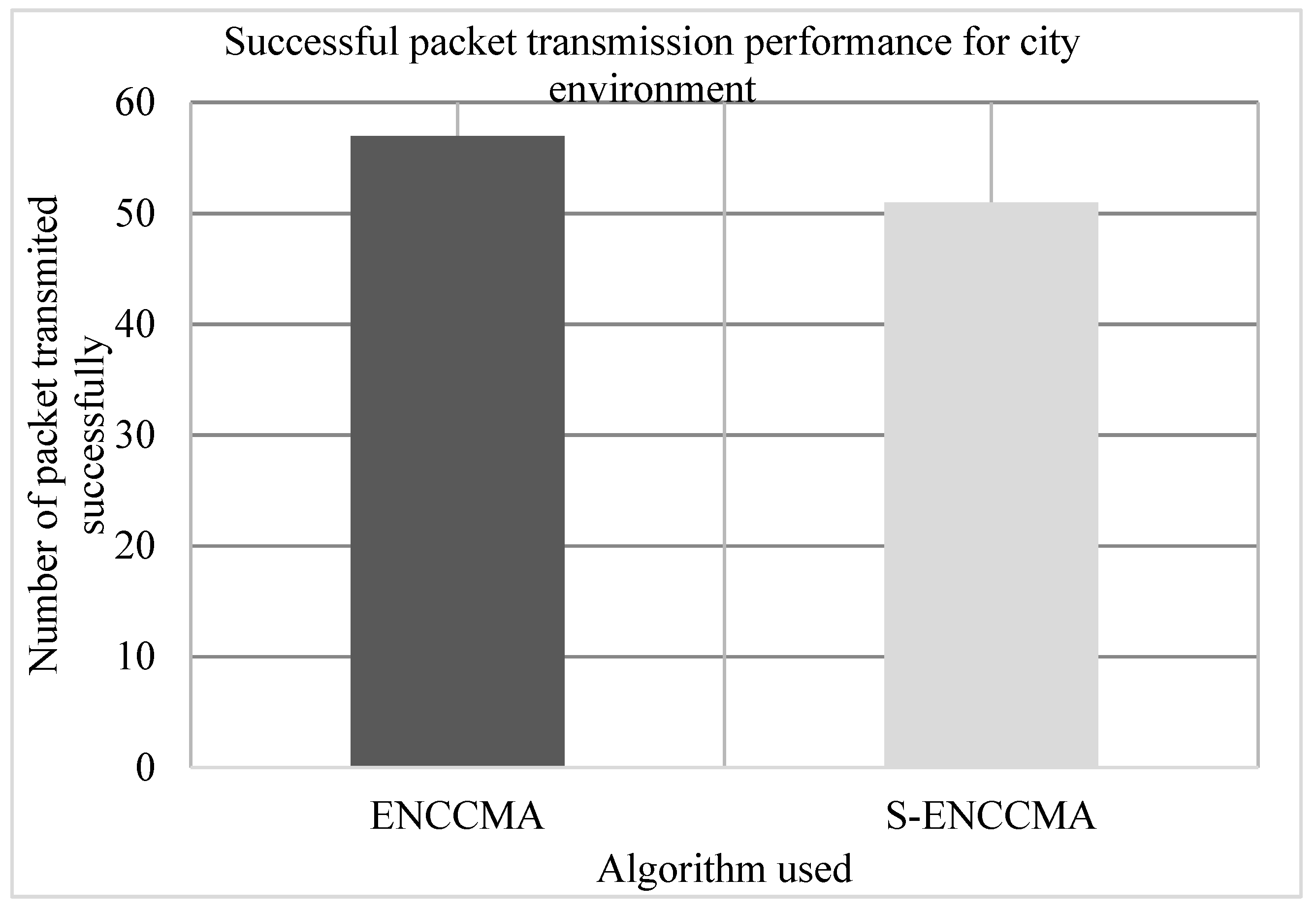
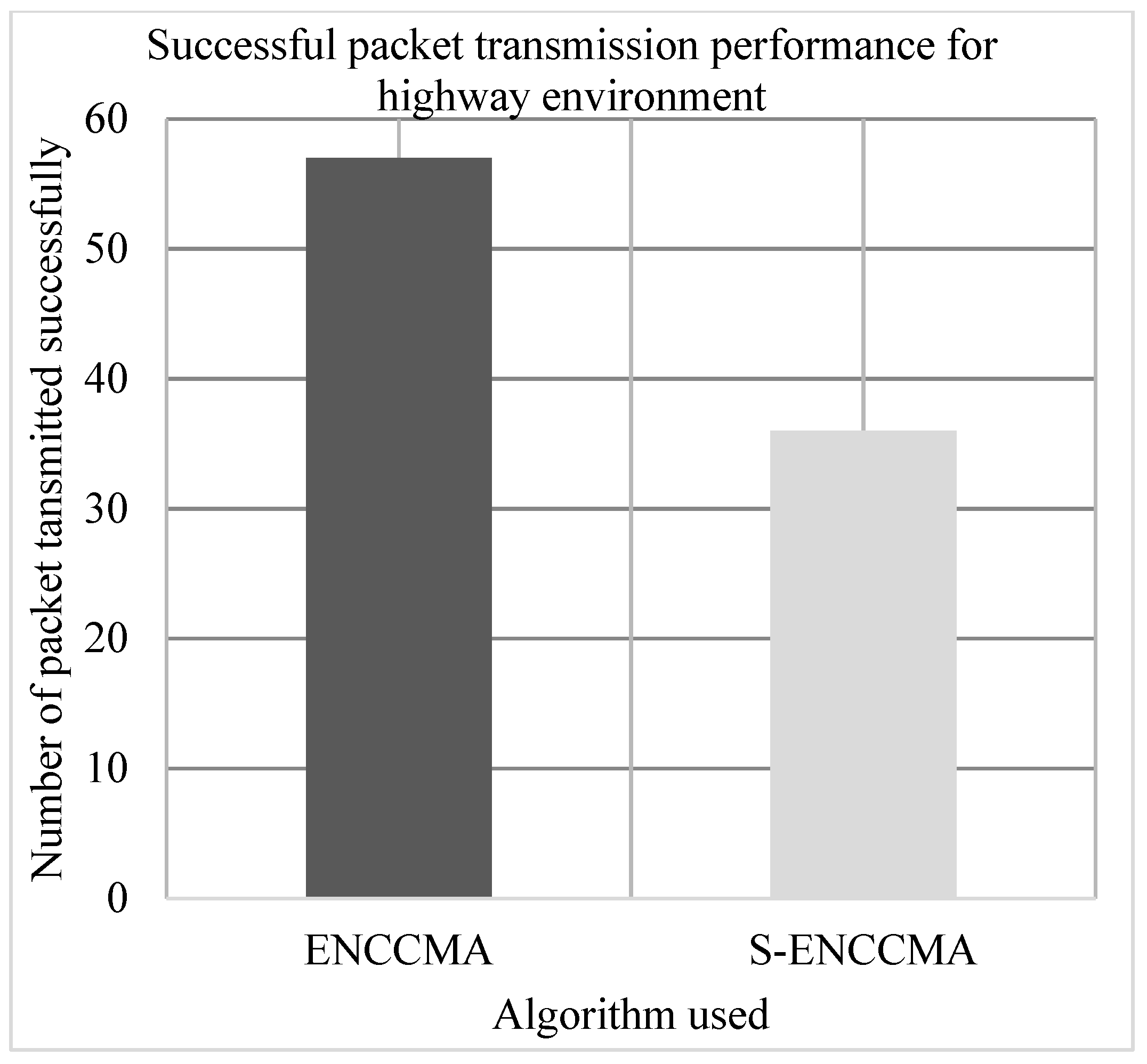
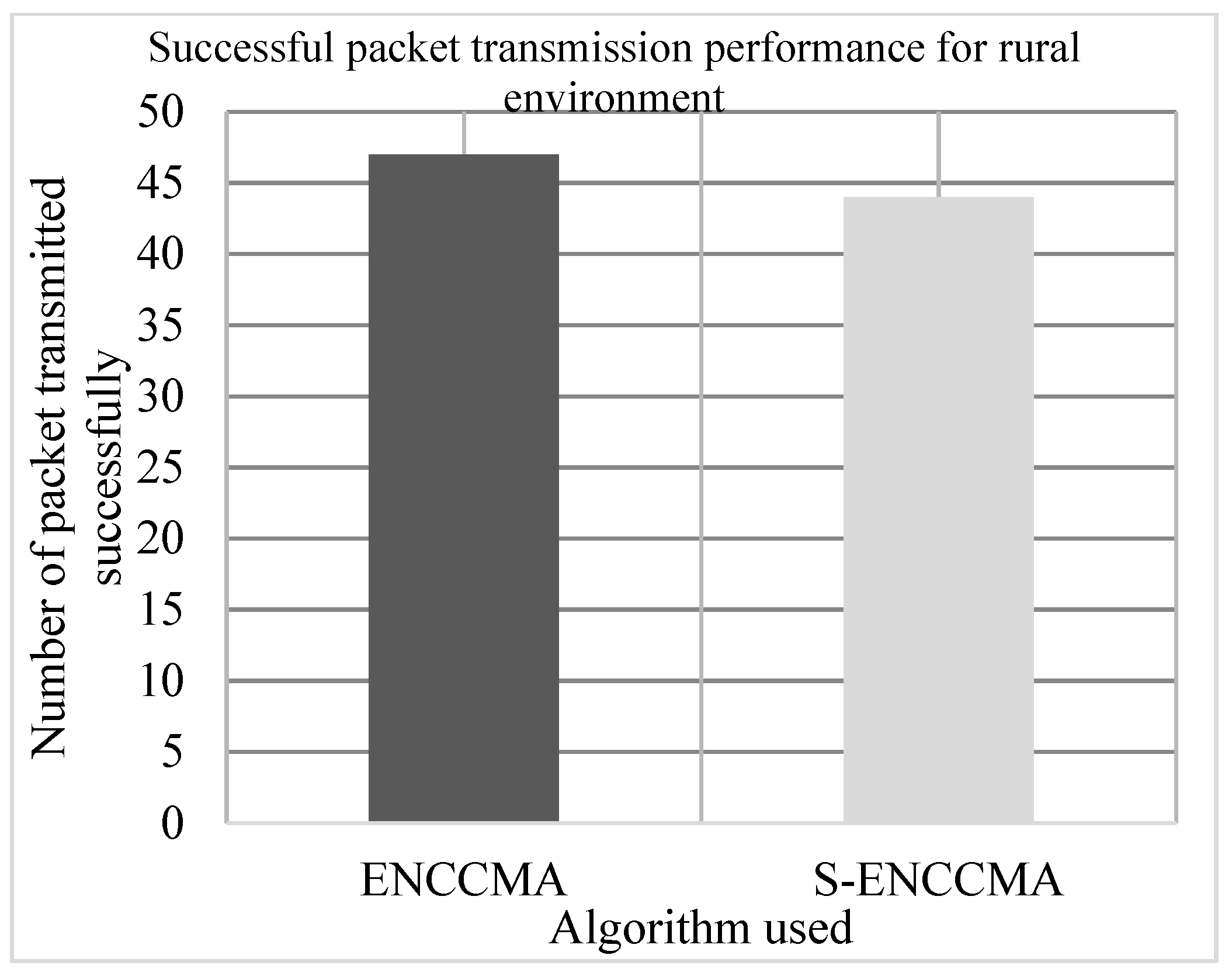
4.2. Successful Packet Transmission Performance
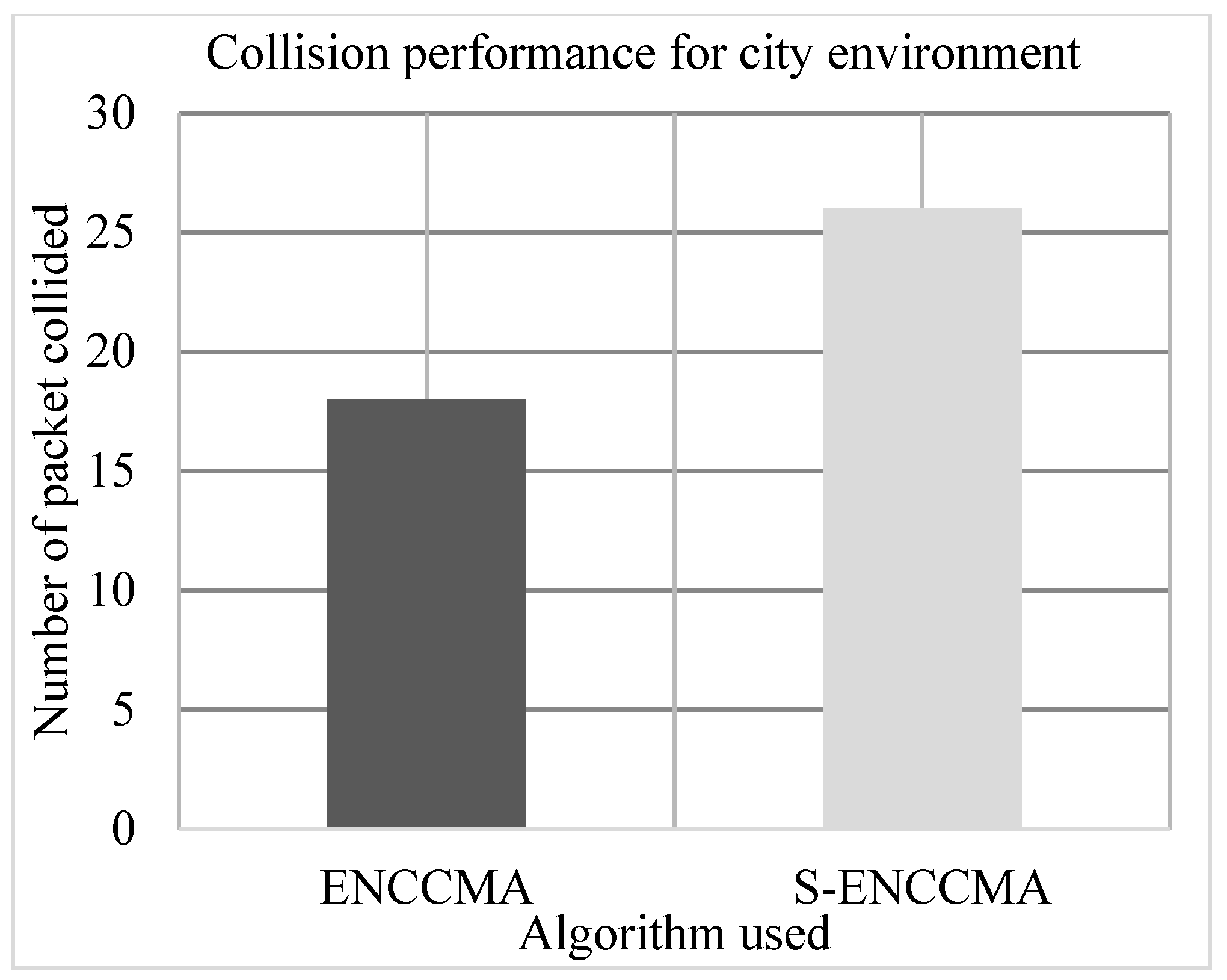
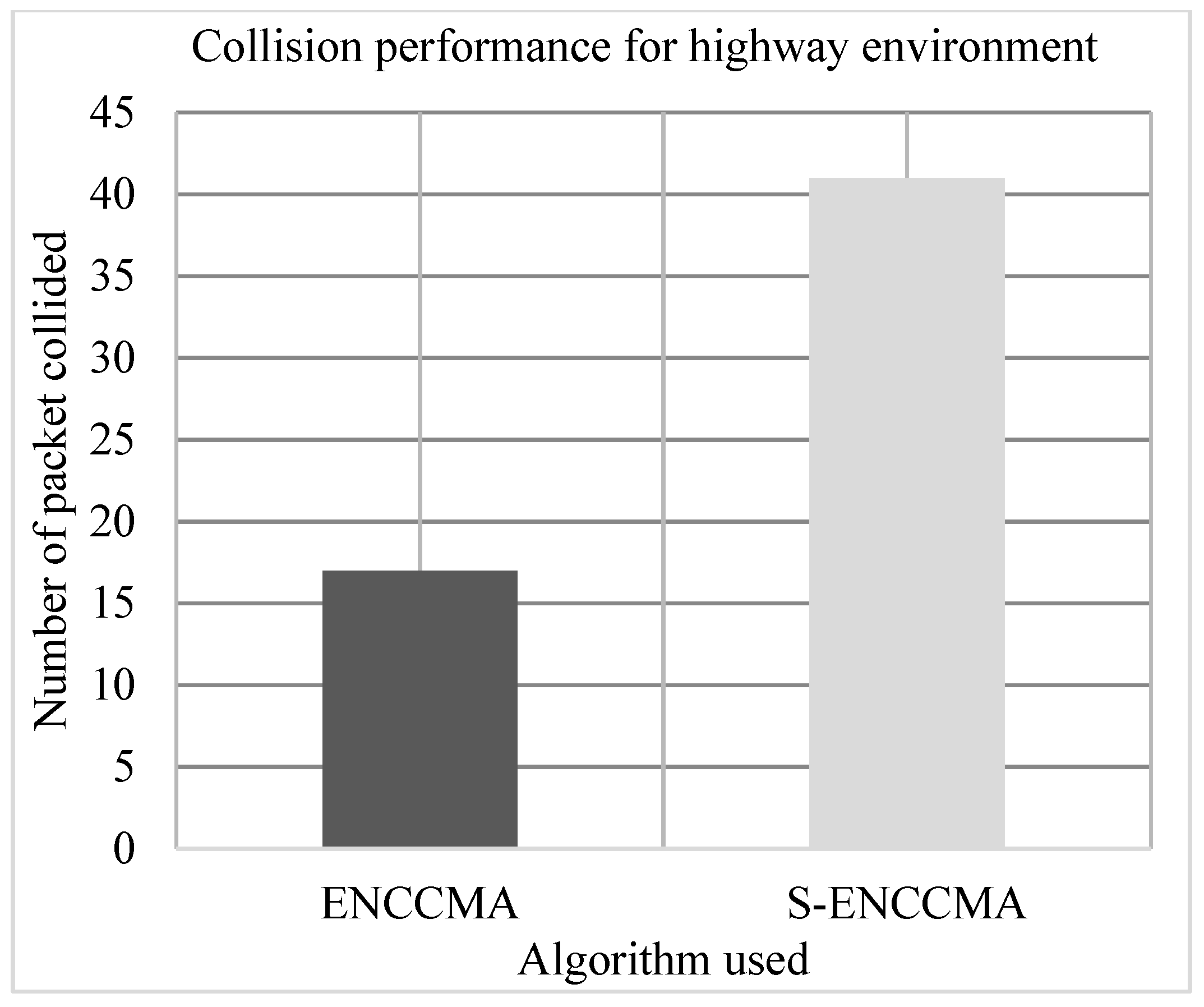
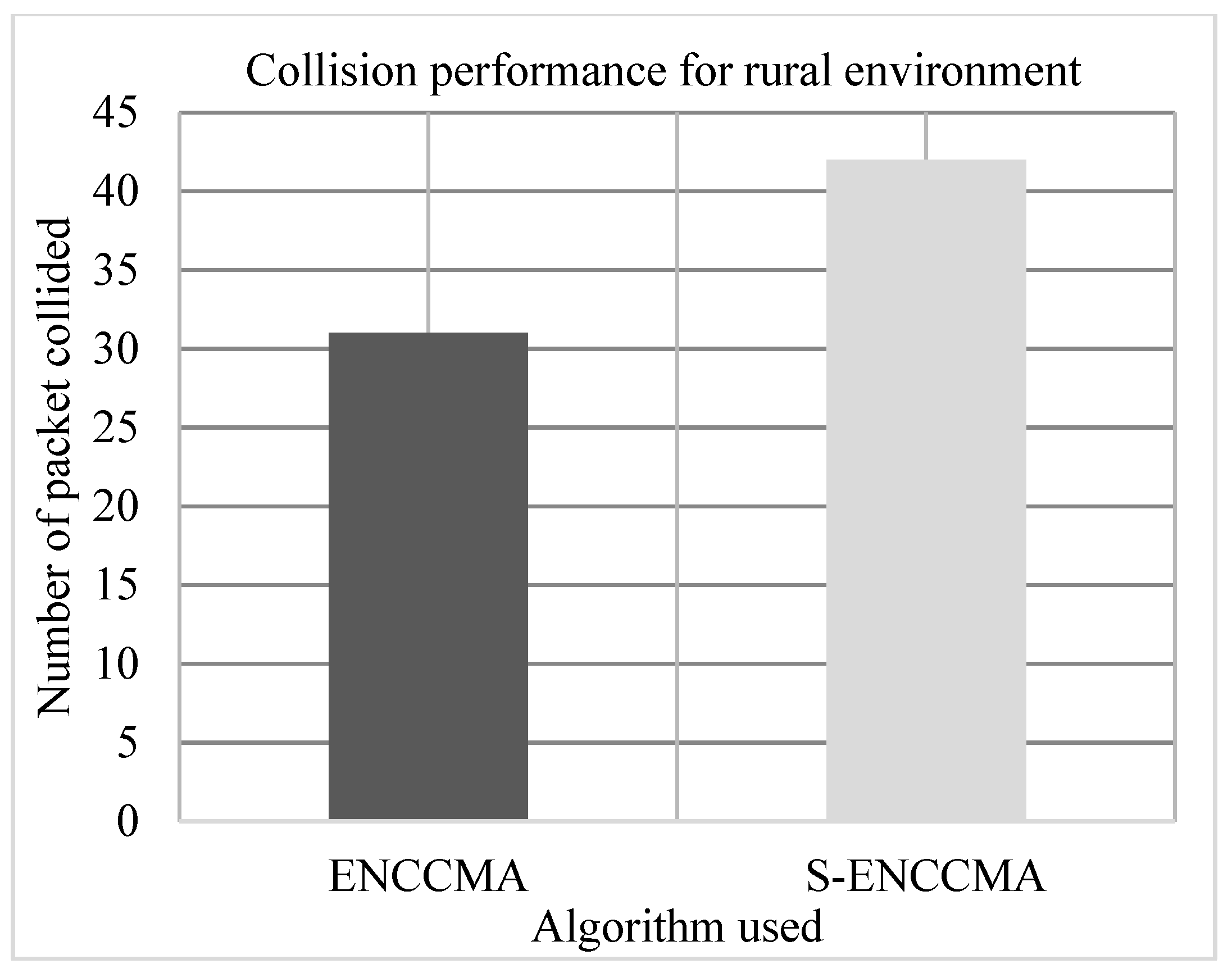
4.3. Collision Performance
| S-ENCCMA (Ours) | ENCCMA [15] | Mobile Slotted Aloha (MS-ALOHA) [22] | Slotted Period (SLOP) [23] | Earliest Deadline First based Carrier Sense Multiple Access (EDF-CSMA) [24] | |
|---|---|---|---|---|---|
| Environmental model used | City, Highway, and Rural (CHR) | Freely flowing vehicles | Urban and highway | Intelligent driver | NA |
| Scheduling Algorithm Used | CRSA | ENCCMA (NCC-TDMA-FDMA) | MS-ALOHA | Wave-Slotted aloha | EDF-CSMA |
| Simulator used | SIMITS | SIMITS | VISSIM | YES (NA) | NS-3 |
| MAC USED | 802.11p MAC | 802.11p MAC | 802.11p MAC | 802.11p MAC | 802.11p MAC |
| Channel sharing available | Yes | Yes | No | No | No |
4.4. Comparison with State of Technique
5. Discussion
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Ros, F.J.; Ruiz, P.M.; Stojmenovic, I. Acknowledgment-based broadcast protocol for reliable and efficient data dissemination in vehicular ad hoc networks. IEEE Trans. Mob. Comput. 2012, 11, 33–46. [Google Scholar] [CrossRef]
- Azees, M.; Vijayakumar, P.; Deborah, L.J. Comprehensive survey on security services in vehicular ad-hoc networks. IET Intell. Transp. Syst. 2016, 10, 379–388. [Google Scholar] [CrossRef]
- DSRC Technology, Intelligent Transportation Systems. Available online: http://www.its.dot.gov/dsrc/ (accessed on 28 January 2011).
- Parno, B.; Perrig, A. Challenges in securing vehicular networks. In Workshop on Hot Topics in Networks (HotNets-IV); University of Maryland: College Park, MD, USA, 2005; pp. 1–6. [Google Scholar]
- Raya, M.; Hubaux, J.P. Securing vehicular ad hoc networks. J. Comput. Secur. 2007, 15, 39–68. [Google Scholar] [CrossRef]
- Lin, X.; Sun, X.; Ho, P.H.; Shen, X. GSIS: A secure and privacy preserving protocol for vehicular communications. IEEE Trans. Veh. Technol. 2007, 56, 3442–3456. [Google Scholar]
- Lu, R.; Lin, X.; Zhu, H.; Ho, P.H.; Shen, X. ECPP: Efficient Conditional Privacy Preservation Protocol for Secure Vehicular Communications. In Proceedings of the IEEE INFOCOM 2008—The 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008; pp. 1229–1237. [Google Scholar]
- Bellur, B. Certificate Assignment Strategies for a PKI-Based Security Architecture in a Vehicular Network. In Proceedings of the IEEE GLOBECOM 2008—2008 IEEE Global Telecommunications Conference, New Orleans, LA, USA, 30 November–4 December 2008; pp. 1–6. [Google Scholar]
- Yu, R.; Kang, J.; Huang, X.; Xie, S.; Zhang, Y.; Gjessing, S. MixGroup: Accumulative Pseudonym Exchanging for Location Privacy Enhancement in Vehicular Social Networks. IEEE Trans. Dependable Secur. Comput. 2016, 13, 93–105. [Google Scholar] [CrossRef]
- Hsiao, H.; Studer, A.; Chen, C.; Perrig, A.; Bai, F.; Bellur, B. Floodingresilient Broadcast Authentication for VANET. In Proceedings of the 17th Annual International Conference on Mobile Computing and Networking (MobiCom), Las Vegas, NV, USA, 19–23 September 2011; pp. 193–204. [Google Scholar]
- Wang, M.; Liu, D.; Zhu, L.; Xu, Y.; Wang, F. LESPP: Lightweight and efficient strong privacy preserving authentication scheme for secure VANET communication. J. Comput. 2016, 98, 685–708. [Google Scholar] [CrossRef]
- Rajput, U.; Abbas, F.; Oh, H. A Hierarchical Privacy Preserving Pseudonymous Authentication Protocol for VANET. IEEE Access 2016, 4, 7770–7784. [Google Scholar] [CrossRef]
- Cui, J.; Zhang, J.; Zhong, H.; Xu, Y. SPACF: A Secure Privacy-preserving Authentication Scheme for VANET with Cuckoo Filter. IEEE Trans. Veh. Technol. 2017, 66, 10283–10295. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, Y.; Chang, G. Efficient Privacy-Preserving Dual Authentication and Key Agreement Scheme for Secure V2V Communications in an IoV Paradigm. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2740–2749. [Google Scholar] [CrossRef]
- Manzano, M.; Espinosa, F.; Bravo-Santos, Á.M.; Gardel-Vicente, A. Cognitive Self-Scheduled Mechanism for Access Control in Noisy Vehicular Ad Hoc Networks. Math. Probl. Eng. 2015, 2015, 354292. [Google Scholar] [CrossRef]
- Mohammed, A.A.; Ahmed, A.A.; Kang, Y.J.; Lee, H.J. Obstacles Effects on Signal Attenuation in Line of Sight for Different Environments in V2V. In Proceedings of the 20th International Conference on Advanced Communication Technology (ICACT), Chuncheon-si Gangwon-do, Korea, 11–14 February 2018; pp. 17–20. [Google Scholar]
- Mohammed, A.A.; Ahmed, A.A.; Lee, H.J. V2V communication modeling for environmental channel throughput and radio propagation. In Proceedings of the 8th IEEE International Conference on ICTC Convergence, Jeju Island, Korea, 18–20 October 2017; pp. 507–512. [Google Scholar]
- Mohammed, A.A.; Ahmed, A.A.; Kim, T.; Lee, H.J. An Environmental Channel Throughput and Radio Propagation Modeling for Vehicle-to-Vehicle Communication. Int. J. Distrib. Sens. Netw. 2018, 14, 1–10. [Google Scholar]
- Mohammed, A.A.; Ahmed, A.A.; Lee, H.J. Performance Enriching Channel Allocation Algorithm for Vehicle-to-Vehicle City, Highway and Rural Network. Sensors 2019, 19, 3283. [Google Scholar]
- Mohammed, A.A.; Ahmed, A.A.; Hind, R.; Lee, H.J. A Novel Throughput and Collision for City Environment in V2V Communication. In Proceedings of the 10th IEEE International Conference on ICTC Convergence, Jeju Island, Korea, 16–18 October 2019; pp. 1413–1415. [Google Scholar]
- Bilgin, B.E.; Gungor, V.C. Performance Comparison of IEEE 802.11p and IEEE 802.11b for Vehicle-to-Vehicle Communications in Highway, Rural, and Urban Areas. Int. J. Veh. Technol. 2013, 2013, 971684. [Google Scholar] [CrossRef]
- Bazzi, A.; Zanella, A.; Masini, B.M. An OFDMA-Based MAC Protocol for Next-Generation VANETs. IEEE Trans. Veh. Technol. 2015, 64, 4088–4100. [Google Scholar] [CrossRef]
- Ferreira, N.F.G.C.; Fonseca, J.A.G. Improving Safety Message Delivery through RSU’s Coordination in Vehicular Networks. In Proceedings of the 2015 IEEE World Conference on Factory Communication Systems (WFCS), Palma de Mallorca, Spain, 27–29 May 2015; pp. 1–8. [Google Scholar]
- Chang, C.Y.; Yen, H.C.; Deng, D.J. V2V QoS Guaranteed Channel Access in IEEE 802.11p VANETs. IEEE Trans. Veh. Technol. 2015, 13, 5–17. [Google Scholar] [CrossRef]
| Notation | Meaning |
|---|---|
| p: Prime Number | |
| q: Prime Number | |
| n = p × q | |
| Phi = (p − 1) × (q − 1): Enter totient number of (n) and φ(n). | |
| e: Public Key | |
| d: Secret Key | |
| Data | |
| Enc = Data^e mod(n) | |
| EncData | |
| Dec = EncData^d mod(n) |
| Environment | City | Highway | Rural |
|---|---|---|---|
| Path loss | 1.61 | 1.85 | 1.79 |
| Shadowing deviation | 3.4 | 3.2 | 3.3 |
| Parameters | Value |
|---|---|
| Network | 30 km × 30 km |
| MAC | and |
| Modulation scheme | 64-QAM |
| Mobility of vehicles | 20 cycle per frame |
| Bandwidth | 27 Mbps |
| Frequency channels | 7 |
| Vehicles | 20 |
| Coding rate | 0.75 |
| Message size | 75 bytes |
| Time slots | 8 μs |
| Environment | Rural, City & Highway |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Al-Absi, M.A.; Al-Absi, A.A.; Lee, H.J. A Secure Enhanced Non-Cooperative Cognitive Division Multiple Access for Vehicle-to-Vehicle Communication. Sensors 2020, 20, 1000. https://doi.org/10.3390/s20041000
Al-Absi MA, Al-Absi AA, Lee HJ. A Secure Enhanced Non-Cooperative Cognitive Division Multiple Access for Vehicle-to-Vehicle Communication. Sensors. 2020; 20(4):1000. https://doi.org/10.3390/s20041000
Chicago/Turabian StyleAl-Absi, Mohammed Abdulhakim, Ahmed Abdulhakim Al-Absi, and Hoon Jae Lee. 2020. "A Secure Enhanced Non-Cooperative Cognitive Division Multiple Access for Vehicle-to-Vehicle Communication" Sensors 20, no. 4: 1000. https://doi.org/10.3390/s20041000
APA StyleAl-Absi, M. A., Al-Absi, A. A., & Lee, H. J. (2020). A Secure Enhanced Non-Cooperative Cognitive Division Multiple Access for Vehicle-to-Vehicle Communication. Sensors, 20(4), 1000. https://doi.org/10.3390/s20041000






