1. Introduction
The UCCN is known as the CR which is a promising technology and innovative solution for dealing with the radio spectrum allocation and precise requirements issues [
1]. CR permits secondary users (SUs or unlicensed users) to access the dormant frequency spectrum without causing interruption to the primary users (PUs or licensed user). Due to SUs being accepted to the PUs at the same time, the SUs have to keep their transmit powers within the acceptable levels. Besides that, with rapidly extending wireless sensor networks (WSNs) in many areas of industry, the security of information transfer becomes a more serious problem. Many researchers investigated PLS to help security transmission between the source node and the destination node to improve and enhance the secrecy of WSNs.
Recently, many solutions and technologies have been investigated for the purposes of speeding up mobile data transmission, extending wireless communication range, and assisting users in connecting security together. Examples of these technologies include amplify-and-forward (AF), orthogonal multiple access (OMA), and energy harvesting [
2,
3,
4]. NOMA technology, however, is a promising method and has attracted significant attention in recent years [
5,
6,
7,
8,
9,
10].
NOMA technology has gradually become one of the most efficient solutions in developing the fifth-generation mobile network (5G). In the NOMA technique, the users can share both time and frequency resources and only adjust their power allocation ratios. The users with better channel conditions can serve as relays to enhance the system performance by using SIC [
9]. This technology improves the limitation of orthogonal multiple access (OMA). It meets the needs of end users in providing access to data quickly and securely. NOMA and PLS are therefore very important techniques in data transfer. They assist in transmitting signals from the source node to destination node with high speed, efficiency, and data confidentiality.
Several studies have examined NOMA and PLS in wireless systems [
11,
12,
13]. In [
11], the authors considered a cooperative relaying system using the NOMA technique to enhance the efficiency of the transmitted signal. The researchers in [
13] investigated the effectiveness of new schemes that combined partial relay selection and NOMA in AF relaying systems to increase data transmission rates for 5G mobile networks.
A considerable amount of literature has been published on PLS [
14,
15,
16]. In [
14], the authors analyzed the secrecy performance of cooperative protocols with relay selection methods influenced by co-channel interference. The authors in [
15] inspected the impact of correlated fading on the secrecy performance of multiple DF relaying that uses the optimal relay selection method. Some researchers have also combined the NOMA technique with PLS [
17,
18,
19]. In [
17], the authors resolved the problem of maximizing the minimum confidential information rate in users subject to the secrecy outage constraint and instantaneous transmit power constraint. Cooperative NOMA systems with PLS in both AF and DF were studied by the authors in [
18].
The application of NOMA techniques and security principles in underlay cognitive radio networks were also suggested by some authors in [
20,
21,
22,
23,
24]. In [
20], the authors discussed a cooperative transmission scheme for a downlink NOMA in CR systems. This research exploited maximum spatial diversity. The researchers in [
24] considered secure communication in cognitive DF relay networks in which a pair of cognitive relays were opportunistically selected for security protection against eavesdroppers.
Channel state information (CSI) has a vital role in wireless communication systems. It describes how a signal propagates from the source node to the relay, such as scattering, fading, and power decay over distance. During a receiver’s set-up period, the CSI is evaluated and transferred to related nodes in the system through a media access control protocol. In [
25], the authors researched the effect of imperfect channel CSI on secondary users in an underlay DF cognitive network with multiple primary receivers. In [
26], scientists studied the effect of imperfect CSI on a DF cooperative underlay cognitive radio NOMA network in order to determine the optimal power allocation factors for different user distances.
In most of the literature reported above, the combination of NOMA and PLS in a UCCN influenced by CSI was not proposed. Motivated and inspired by the above ideas, a cooperative scheme is suggested in this paper. In this scheme, a proposed UCCN using NOMA is required to both decode and forward the messages and from node S to two destination nodes (U and U) under the effect of CSI and an eavesdropper. The secrecy performance of the communications and in the proposed system were then examined and estimated in terms of secrecy outage probability over Rayleigh fading channels to improve spectral efficiency and secure communication.
The main contributions of the paper are summarized as follows:
- -
A study of the impact of imperfect CSI and the secrecy performance of a UCCN applying the NOMA technique to improve system performance in a 5G wireless network.
- -
Secrecy outage probability (SOP) is performed over Rayleigh fading channels and verified with Monte Carlo simulations.
- -
The results achieved by the proposed scheme demonstrate the security performance of U and U.
- -
The secrecy performance of the proposed system improved when the distance between the eavesdropper node E and the source and cooperative relay increased.
The paper has five sections.
Section 1 introduces the topic.
Section 2 describes the proposed scheme’s system model.
Section 3 presents the results of an analysis of the secrecy outage probability at the source nodes.
Section 4 presents the simulation results.
Section 5 summarizes the conclusions.
2. System Model
Figure 1 illustrates the influence of imperfect CSI in a UCCN using NOMA and PLS. The system model consists of the source nodes S transferring a superimposed signal
and
to U
and U
, respectively, through relay node R. One eavesdropper node E is proposed to wiretap the signals
,
of the links S-U
, S-U
. In addition, the system model also consists of a node Pu which is known as the primary user having the license. Due to the interference constraint at the Pu node in the UCCN, the relay R and source S adjust their transmitting powers. In this model, we assume that the intermediate relay node R operates in DF relaying method and applies the NOMA principle under the influence of imperfect CSIs and PLS in UCCN. In addition, the variances of Zero-mean White Gaussian Noises (AWGNs) are equal, given as
. In this work, the corresponding distances of the links S-Pu, R-Pu, S-R, S-E, R-E, R-Pu, R-U
, and R-U
in
Figure 1 are given as
, and
.
Regarding the system channels,
represents the Rayleigh fading channel coefficient,
. We assume that the channels
do not change during block time T and are independently and identically distributed between two consecutive block times [
10].
Finally, all of nodes in the system model have a single antenna for transmitting and receiving messages.
In principle, there are two time slots involved in each system communication process, and are given as follows:
At the first time slot, the source node S transfers the information e
to the relay R and the eavesdropper node E, which is given by the math expression as
where Ps is the power at source node S,
, and
are the messages of U
, U
, respectively, with
, (
being notated for the expectation process of
e). The
and
are the power allocation coefficients. Following the principle of the NOMA, we assume that
with
.
Because of the estimation errors of channels
, the evaluated fading channel coefficients at the nodes are represented as follows [
25]:
where
are modeled as the additive white Gaussian noise (AWGN) with the random variable
. The correlation coefficient
is described as the average quality of the channel estimation.
Notation: The Cumulative Distribution Function (CDF) and probability density function (pdf) of the random variable is denoted respectively as and , where , and is a path-loss exponent.
The received signal at R from source node S for decode
under impact imperfect CSIs is given as follows:
Replace
from formula (2), the signal
is calculated as
where
denotes the AWGNs at the relay R with the same variance
.
Because of applying NOMA technology, thanks to the deployment of SIC in NOMA principle, firstly, the relay R decodes the signal
from formula (3b) and removes it, then the signal
will be decoded without the component
in formula (3b). Therefore, the signal
received at R from source S after removing the signal
is expressed as follows:
Similarly, the node E also wiretaps the packets
and
from S, respectively, and the received signals at node E are obtained as follows:
where
denotes the AWGNs at the E with the same variance
.
In the second time slot, after the received signals, the relay R sends them to the source nodes U
and U
. Hence, the received signals at the destination node U
, U
are given respectively as
where
denote the AWGNs at the destination U
, U
with the same variance
, and
is a transmit power of the relay R.
In the proposed scheme, under the interference constraint at the node
Pu, the source node S and relay node R have to adjust their transmitting powers so that the interference power at the Pu must be less than a threshold value, which is assumed as
I. The maximum powers of nodes S and R are given, respectively,
Because the node E connects to the relay R directly, so it wiretaps the packets
and
from relay R. Therefore, the received signals at E through the link R-E are expressed as
We define the received Signal-to-Interference and Noise Ratios (SINRs) as E{|overall noise|2}.
Firstly, we calculate the received Signal-to-Interference and Noise Ratios (SINRs) for decoding the information signal e.
Thus, from formula (3b), the SINR at the relay R with the link S-R is obtained as follows:
Replacing
in (9a), and setting
,
is rewritten as
Similarly, with the formula in (7), we also calculate
, and this is achieved by mathematical expression as
where
.
Applying formulas (5) and (10), the received SINRs at the eavesdropper node E with the link S-E and R-E are given, respectively, as follows:
In the second, similar to decoding the information signal , we find the received SINRs for decoding the information signal as follows.
We apply formulas (4) and (6), the received SINRs at the nodes R with the link S-R, and at the eavesdropper node E with the link S-E are expressed, respectively, as follows:
Similarly, with formulas (8) and (12), the received SINRs at the nodes U
and E from relay R are inferred, respectively, as follows:
Applying the Shannon capacity formula, the achievable rates of the links
X–Y are formulated as
where the ratio 1/2 represents the fact that data transmission is split into two time slots,
, and
. The secrecy capacity of the UCCN systems with DF-based NOMA for the S-U
communication can be expressed as
where
;
and
are the secrecy capacities from the source node S to the relay R and from the relay R to the destination U
are given, respectively, as
4. Simulation Results
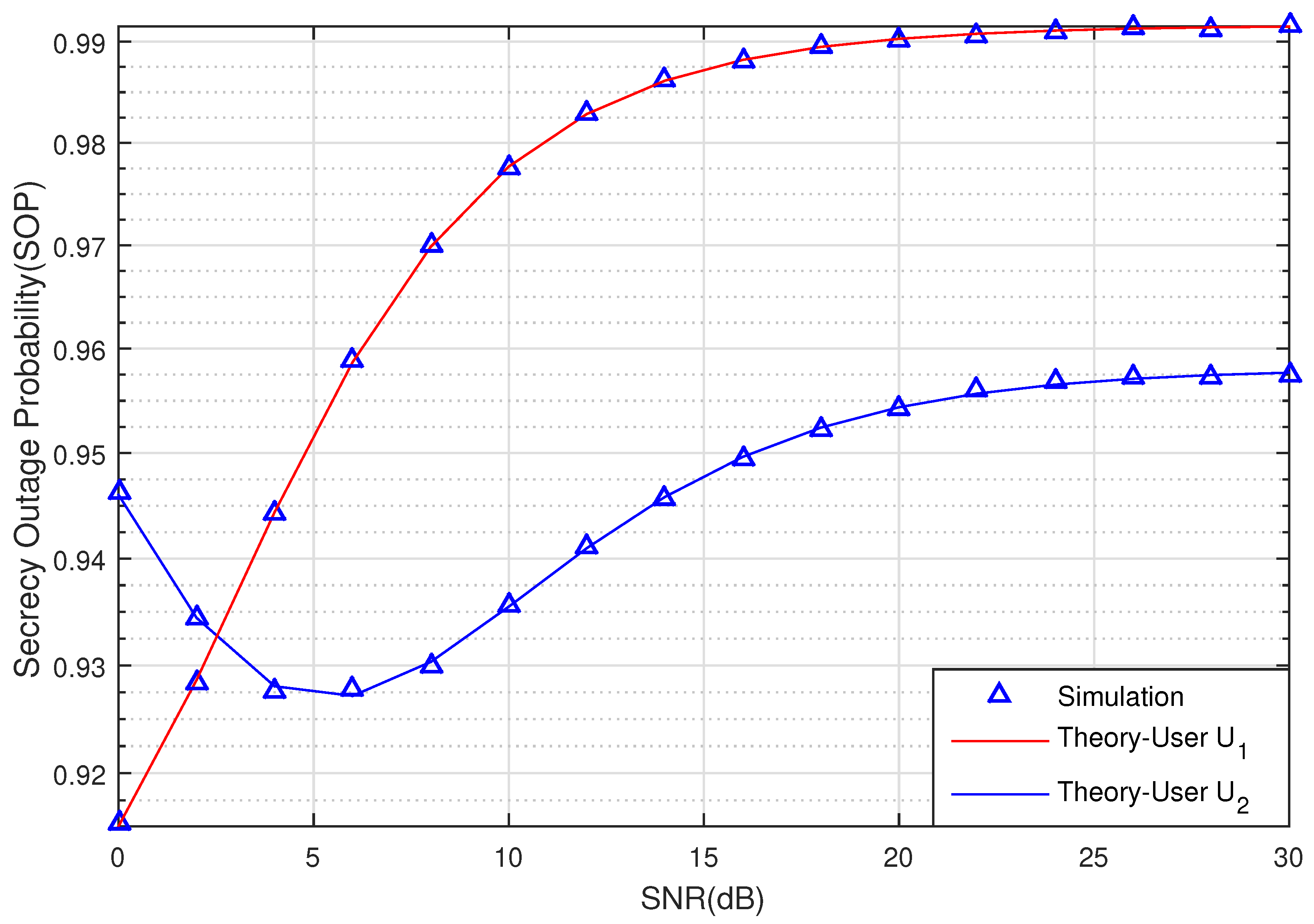
In this section, the secrecy performance of a NOMA scheme and the impact of imperfect CSI in a UCCN were examined, analyzed, and evaluated. The theoretical results of the analyses were verified with Monte Carlo simulations. The coordinates of S, R, U, U, Pu, and E were set to ), , , , , respectively, in the two-dimensional plane and satisfying . Hence, , , , , , , and . We assume that the target secrecy capacity (bit/s/Hz) and the exponent is set to a constant .
Figure 2 and
Figure 3 graph the SOP of the two Users U
and U
via SNR (dB) with
(bit/s/Hz). The relay R, Pu, U
, U
, and eavesdropper E are located in positions
,
,
,
,
, respectively. From the results in
Figure 2, we can see the effect of the eavesdropping node E to the SOP when SNR is changed from 0 dB to 20 dB. With
, the SOP values of User U
are greater than User U
when SNR < 2.5 dB. Nevertheless, when the SNR increases from
dB to 30 dB, the SOP of User U
is better than User U
, and both also increase when the SNR increases as a result of large transmitting power. Besides that, it is noted that imperfect CSI degrades the SOP of the signal.
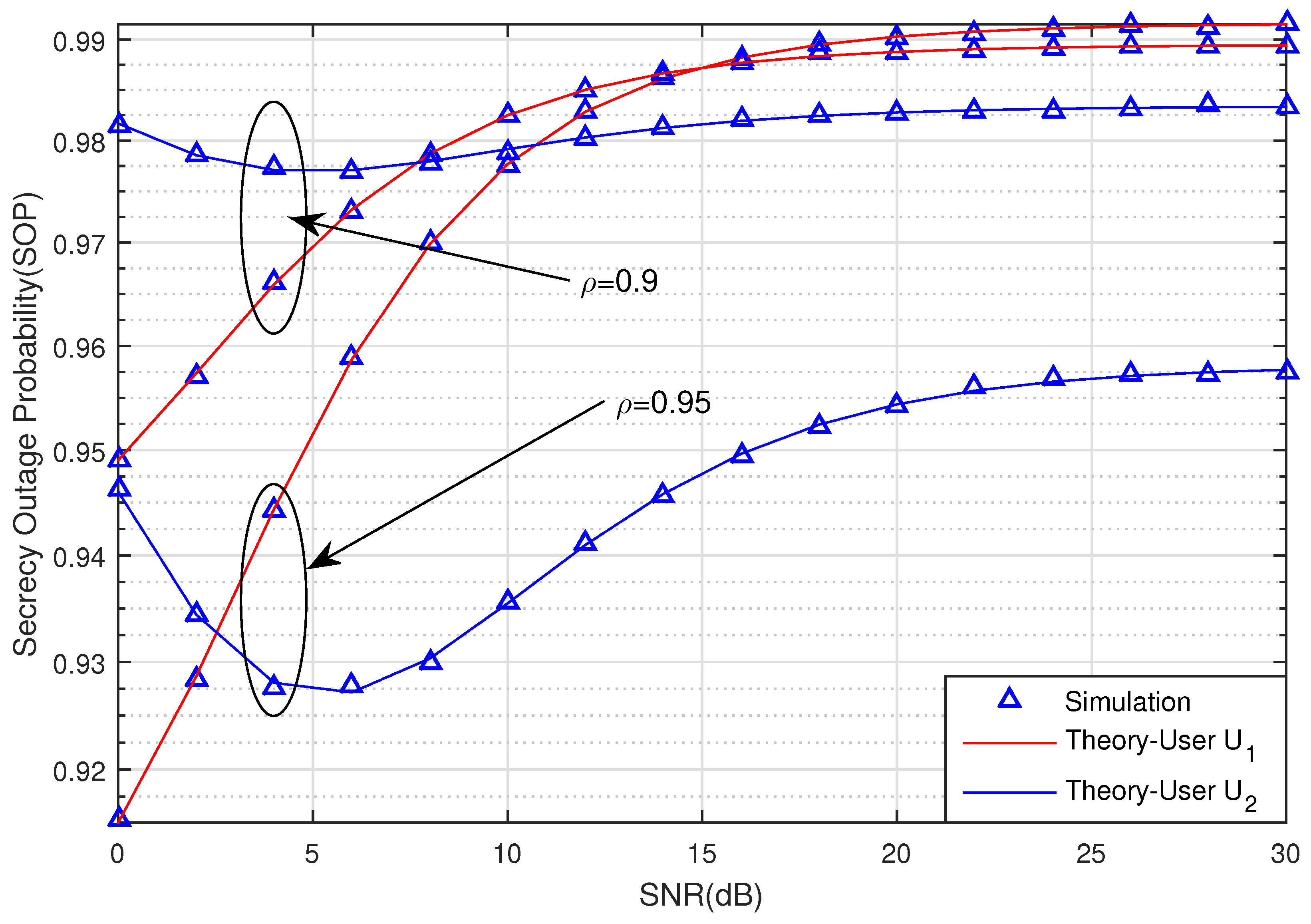
In
Figure 3, we observe the obvious affection of the channel estimation coefficient
to the SOP. The SOP of the two users in case
outperforms the SOP in case
. It means that the system has been impacted by imperfect CSI. We also can see that the secrecy performance of the two Users also decreases when the SNR increases. The security system will be better and it is difficult for the eavesdropper to wiretap the signal. These theoretical results match the simulation results of the proposed system well. Hence, the derived equations are sufficiently accurate for use in analysis.
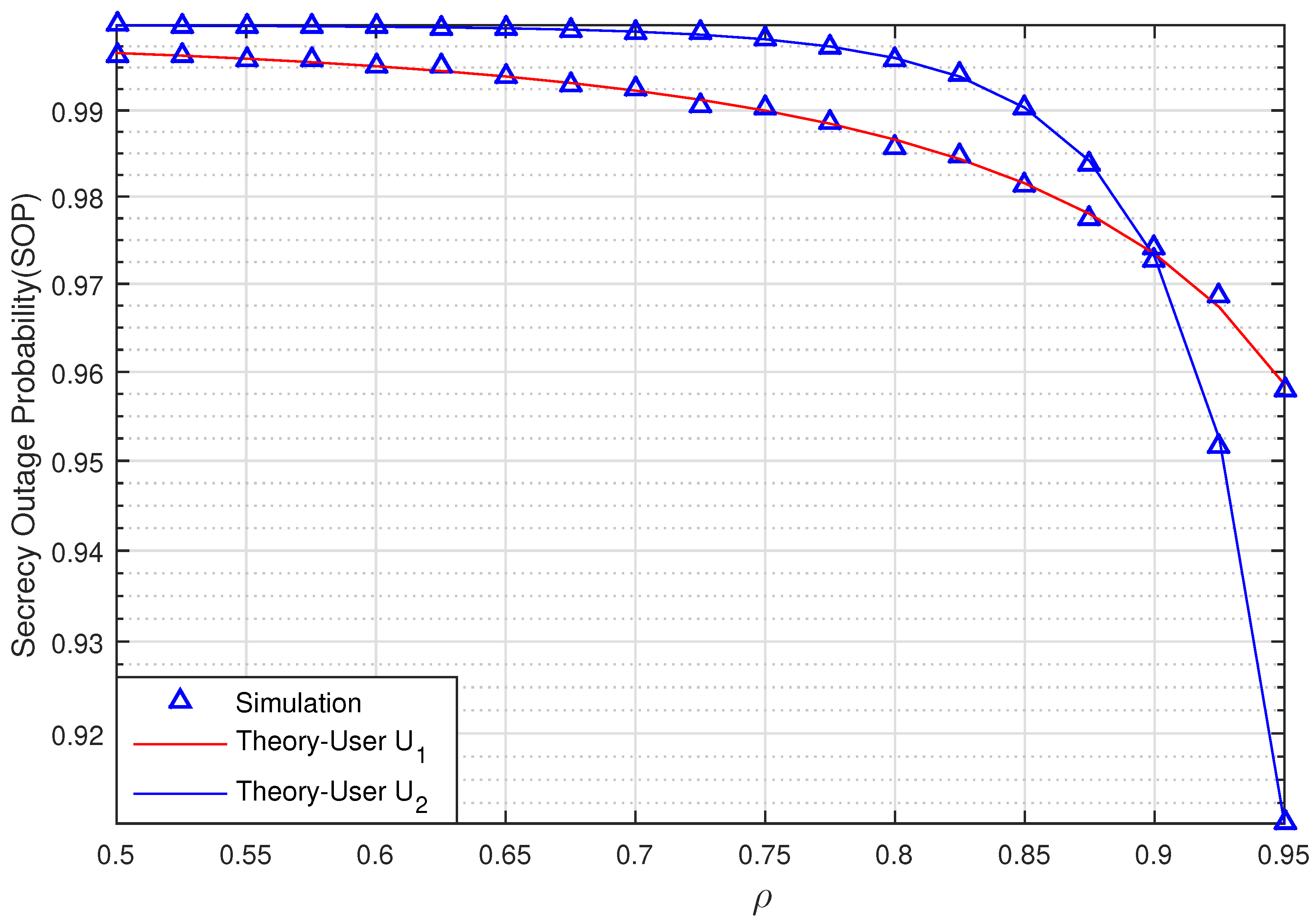
Figure 4 graphs the SOP of the two Users U
and U
via
when SNR = 10 (dB) with
(bit/s/Hz). The relay R, Pu, U
, U
, and eavesdropper E are located in positions
,
,
,
,
, respectively. As observed in
Figure 4, the secrecy performance of U
is better than U
when
. However, when the correlation coefficient
, the SOP of U
is less than U
. This means that the effects of the evaluation errors decrease when the correlation coefficients
increase. In addition, the secrecy performance of two Users is more efficient when the channel estimation coefficient
is higher.
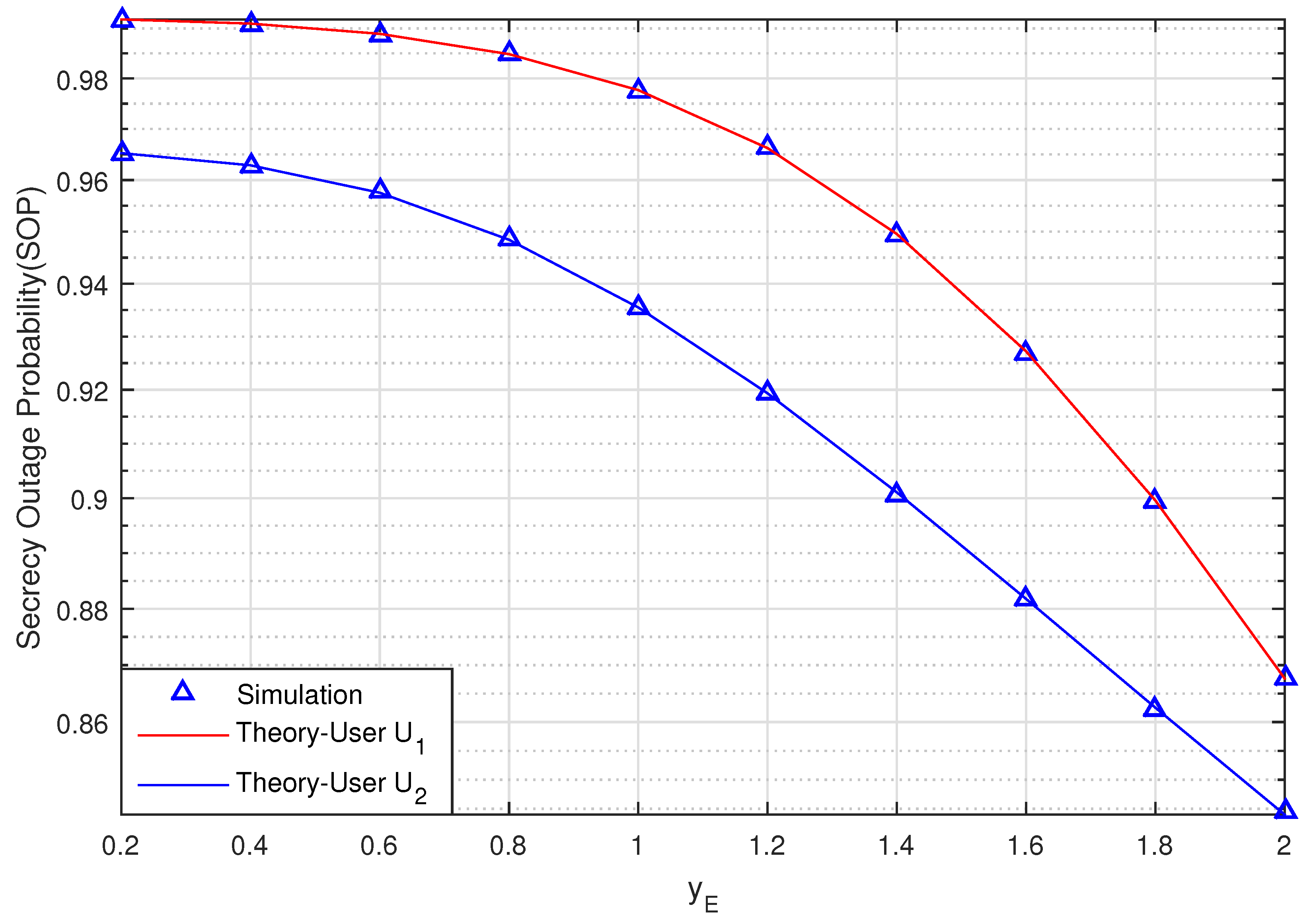
Figure 5 graphs the SOP of the proposed scheme versus the position of the of eavesdropper E on the
y-axis when the coordinate value
changes from 0.2 to 2 when SNR = 10 (dB), (bit/s/Hz),
,
,
,
.
Figure 5 shows that the SOP of U
and U
decrease when
increases. This means that the secrecy transmission of the two Users will be intact when eavesdropper E moves farther away from source S and relay R.
We can also see that the secrecy performance of U is better than U as a result of the proposed scheme applying NOMA and using SIC to detect the signal under the effect of imperfect CSI on the system.
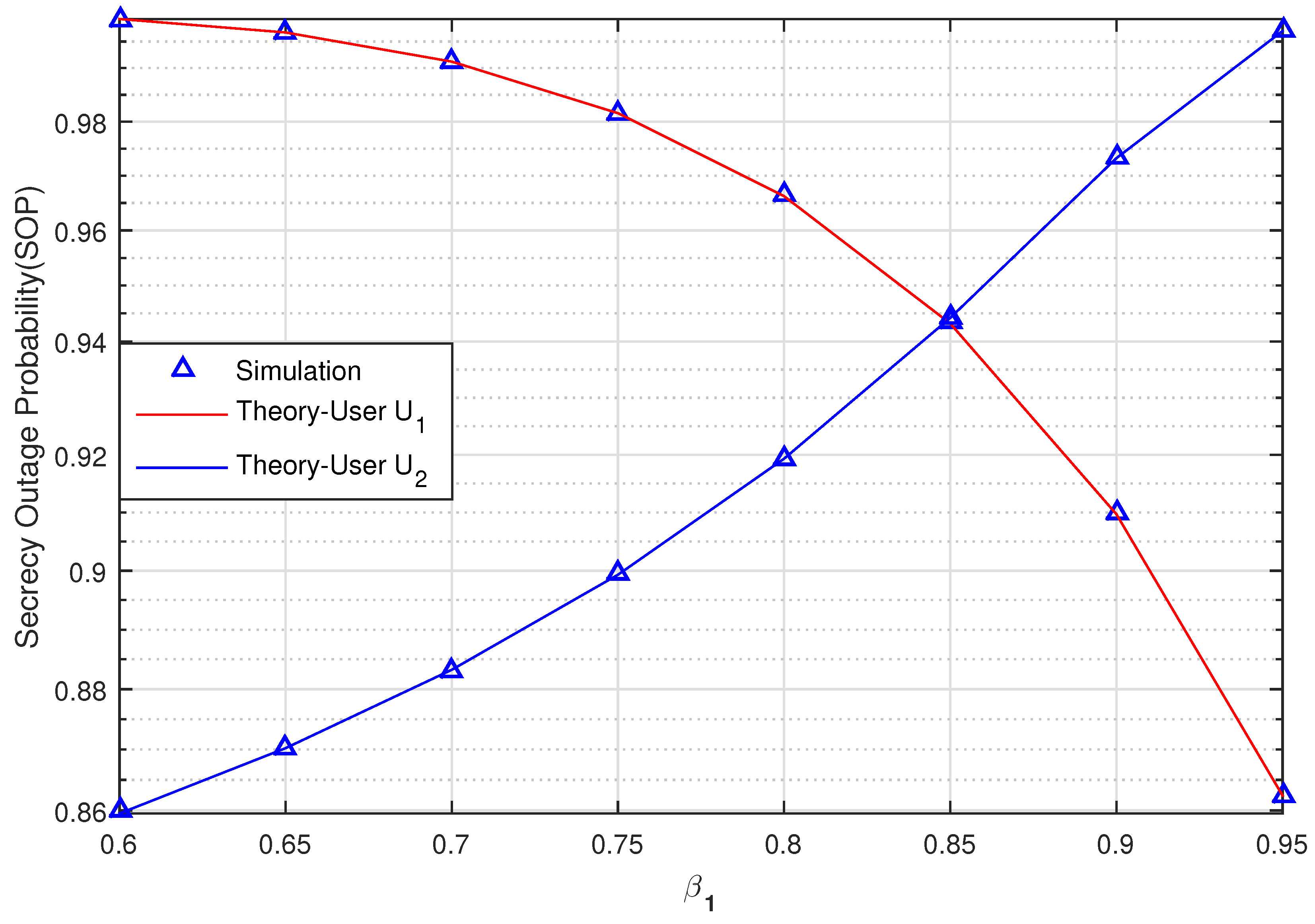
Figure 6 graphs the SOP of User U
and U
versus the power allocation coefficients
(changing from 0.6 to 0.95) when SNR = 10 (dB),
(bit/s/Hz),
,
,
,
,
. This figure shows the impact of a varying
on the system. When
increases from 0.6 to 0.85, the SOP of U
outperforms the SOP of U
. The secrecy transmission of U
is then better than U
when
. We can thus observe the impact of
on the security performance of a UCCN system with a NOMA solution under the effect of imperfect CSI.