Identification of Data Injection Attacks in Networked Control Systems Using Noise Impulse Integration †
Abstract
:1. Introduction
- provide information for an autonomous process intended to redesign the NCS control function, to mitigate the attack effects in the plant behavior;
- reveal the attacker intentions, for forensic purposes, helping to estimate the possible impacts of the attack on the plant and its services.
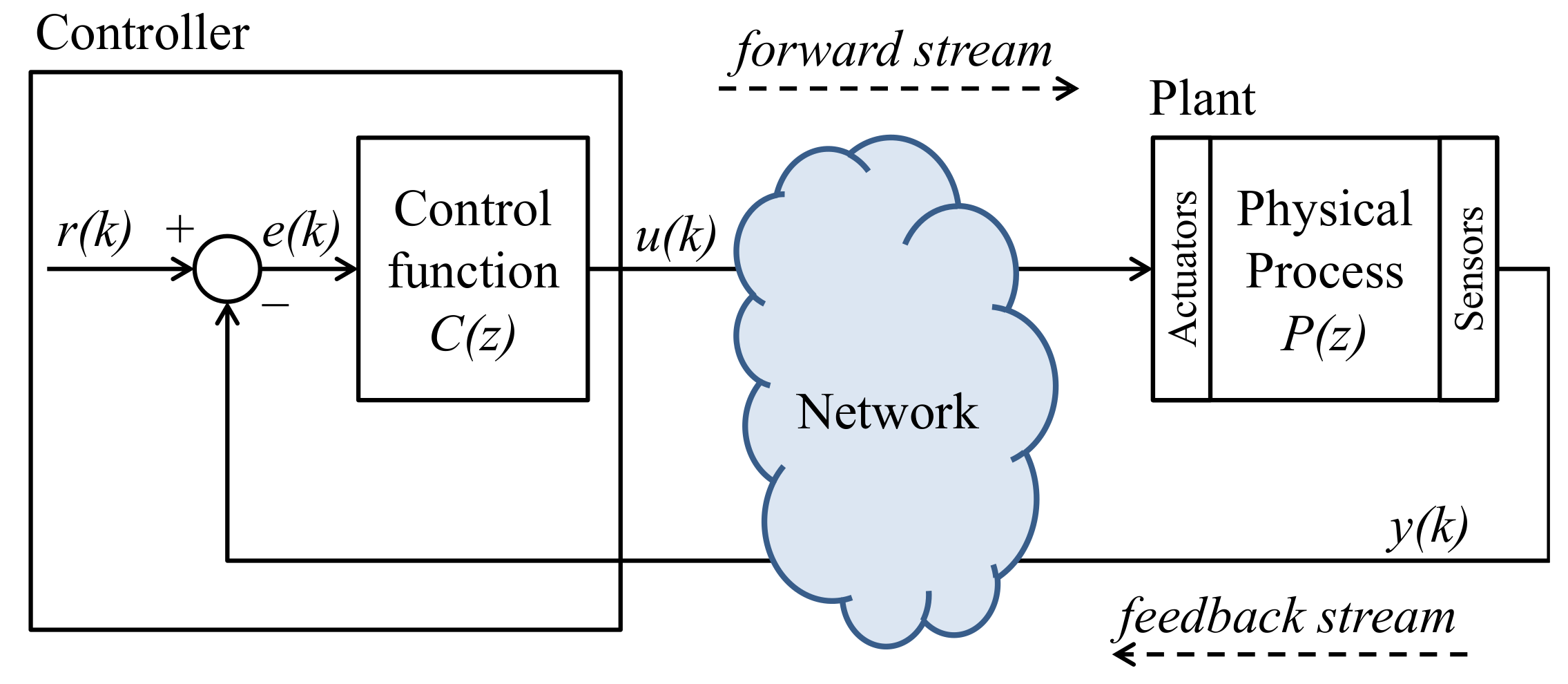
2. SD-Controlled Data Injection Attack
- STAGE-I:
- The system identification stage [8,13] is executed to provide the attacker an accurate knowledge about the models of the targeted system, i.e., the plant’s transfer function and the controller’s control function . This knowledge is obtained either through a Passive System Identification process [8] or through an Active System Identification process [13].
- STAGE-II:
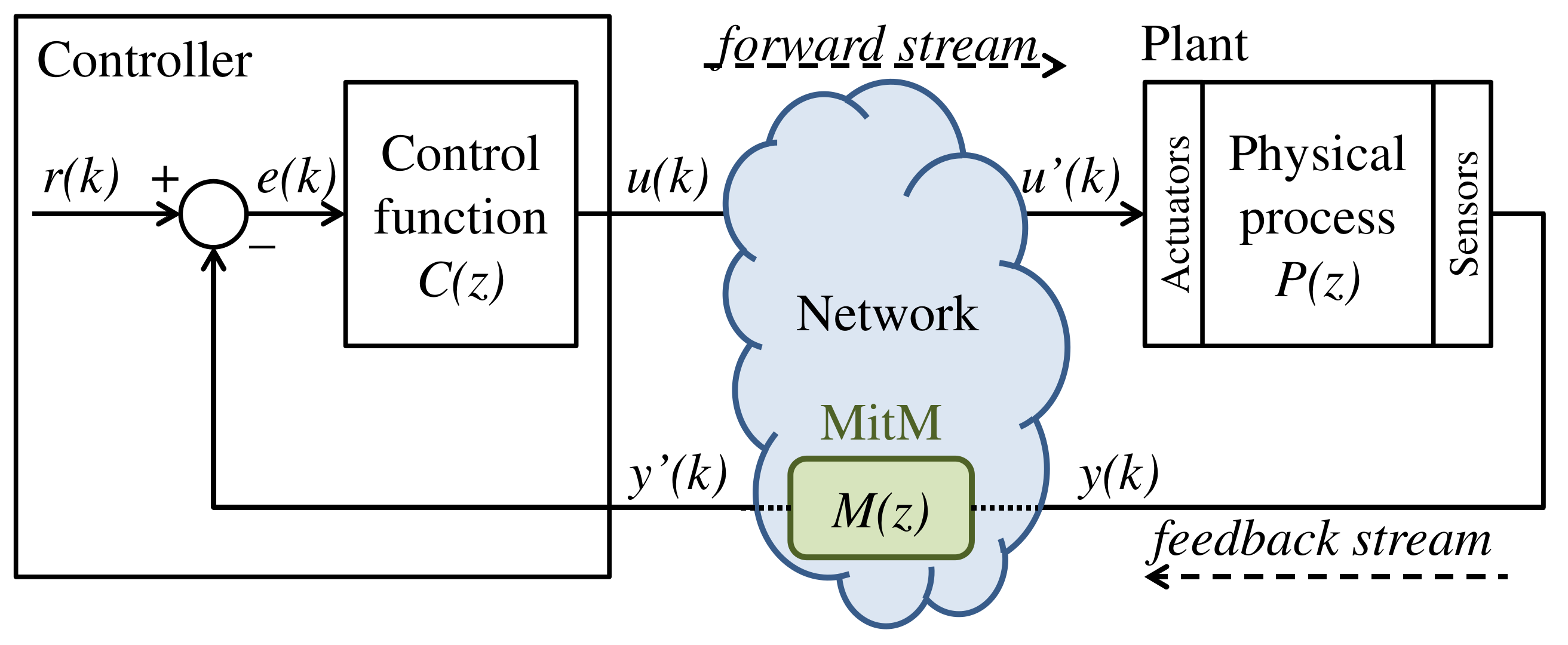
- The Data Injection stage is performed. The attacker, as an MitM, injects false data in the NCS control loop. To accurately change the plant physical behavior, the injected false data is computed according to which, in turn, is designed based on the knowledge obtained by the attacker during STAGE-I.
3. Identification of Controlled Data Injection Attacks
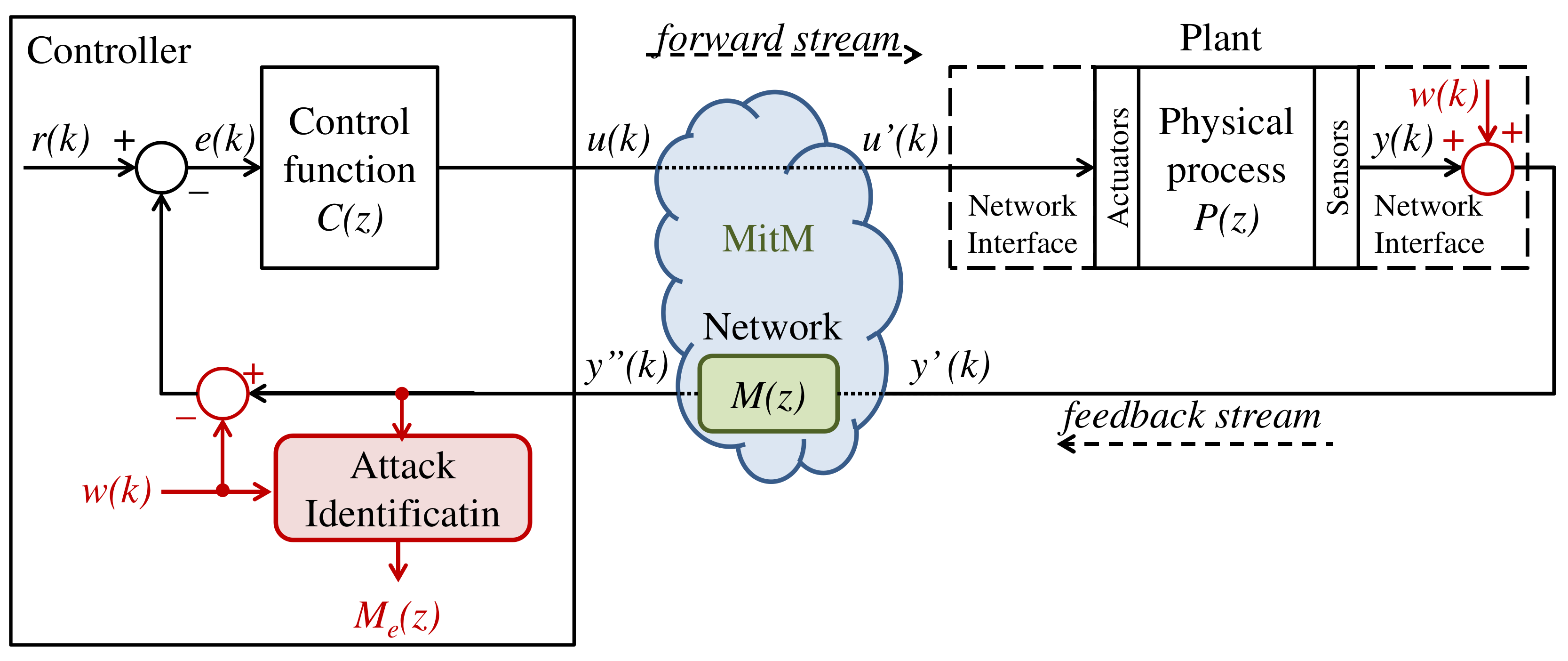
3.1. Strategy to Identify the Attack
| Algorithm 1: Attack Identification without the NII technique. |
 |
3.2. Integrating Impulses of Noise
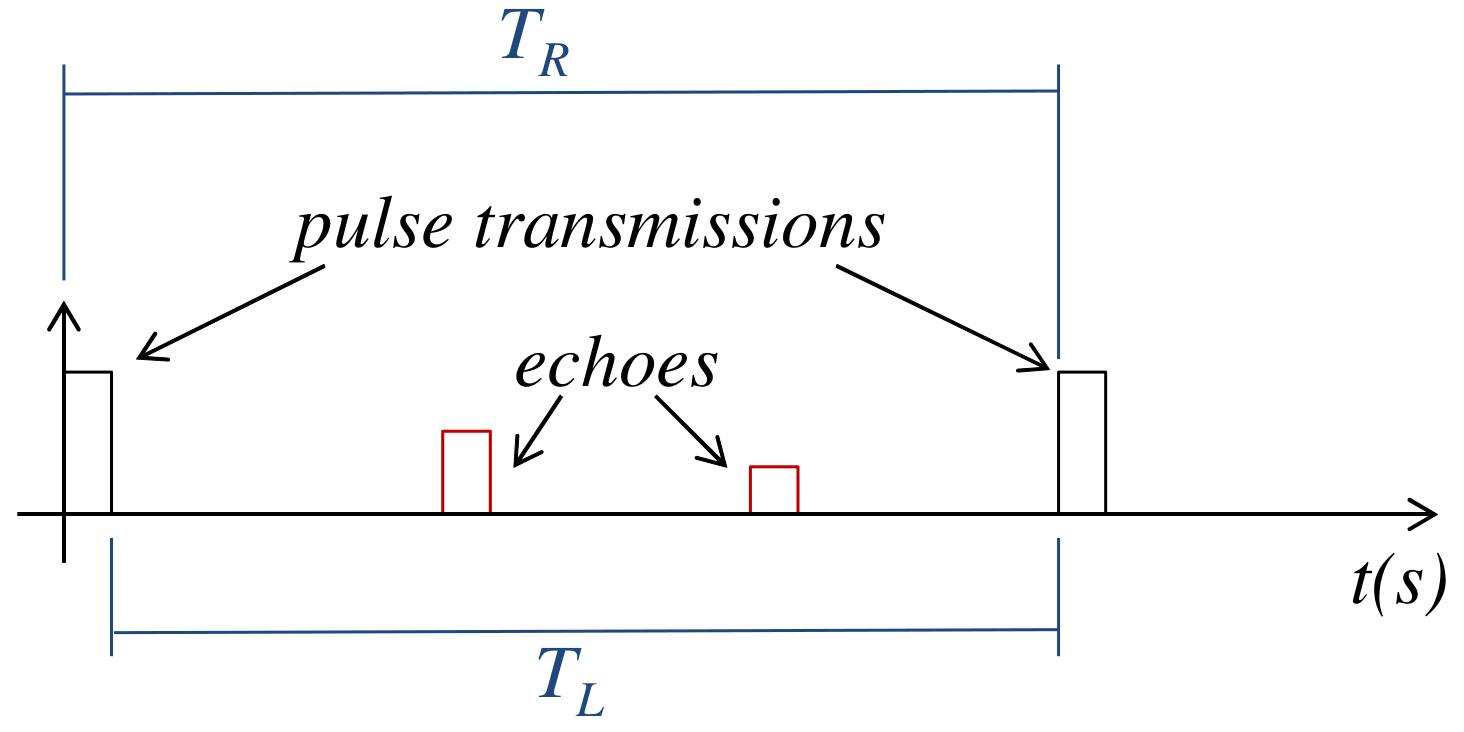
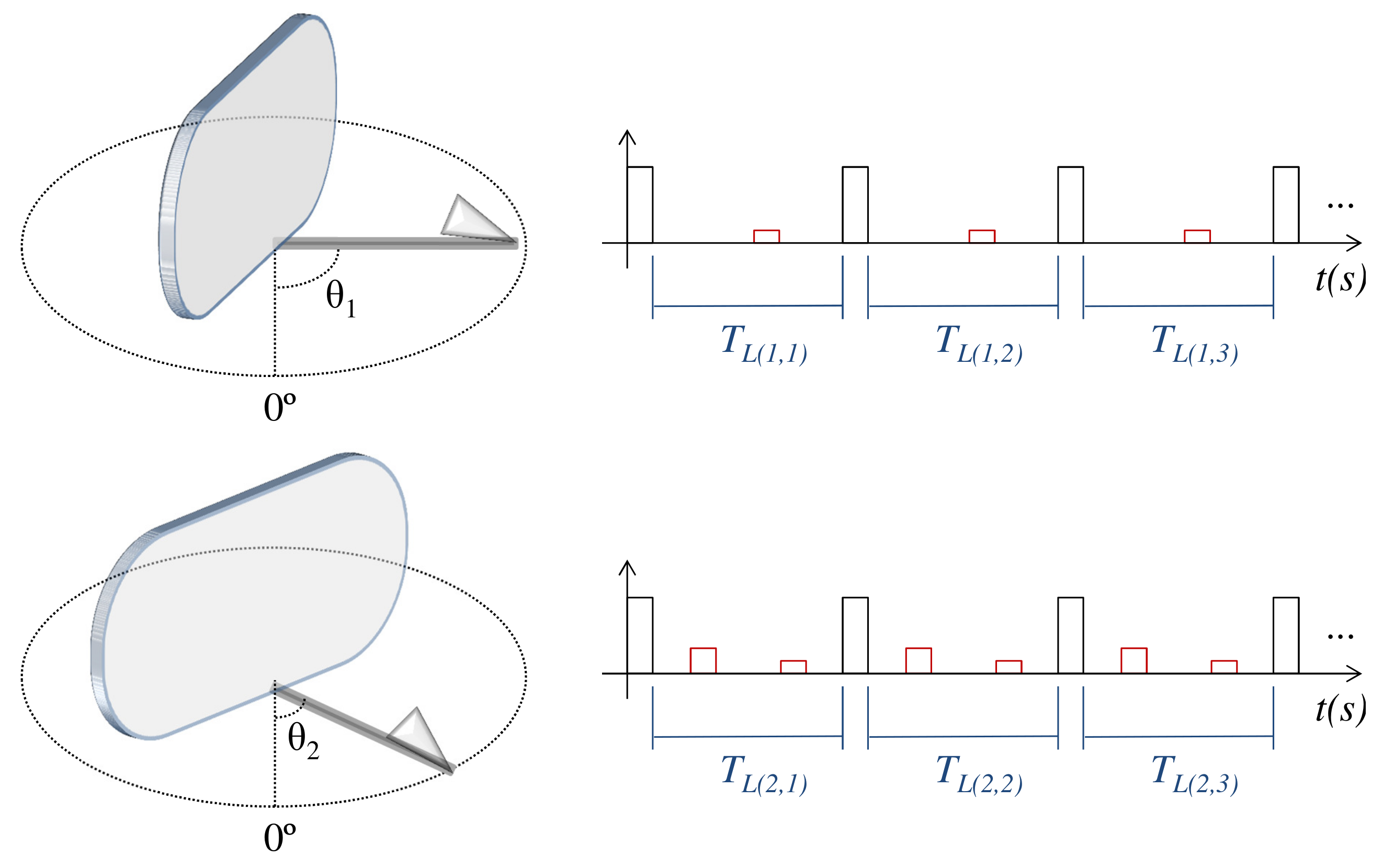
3.2.1. Radar Pulse Integration
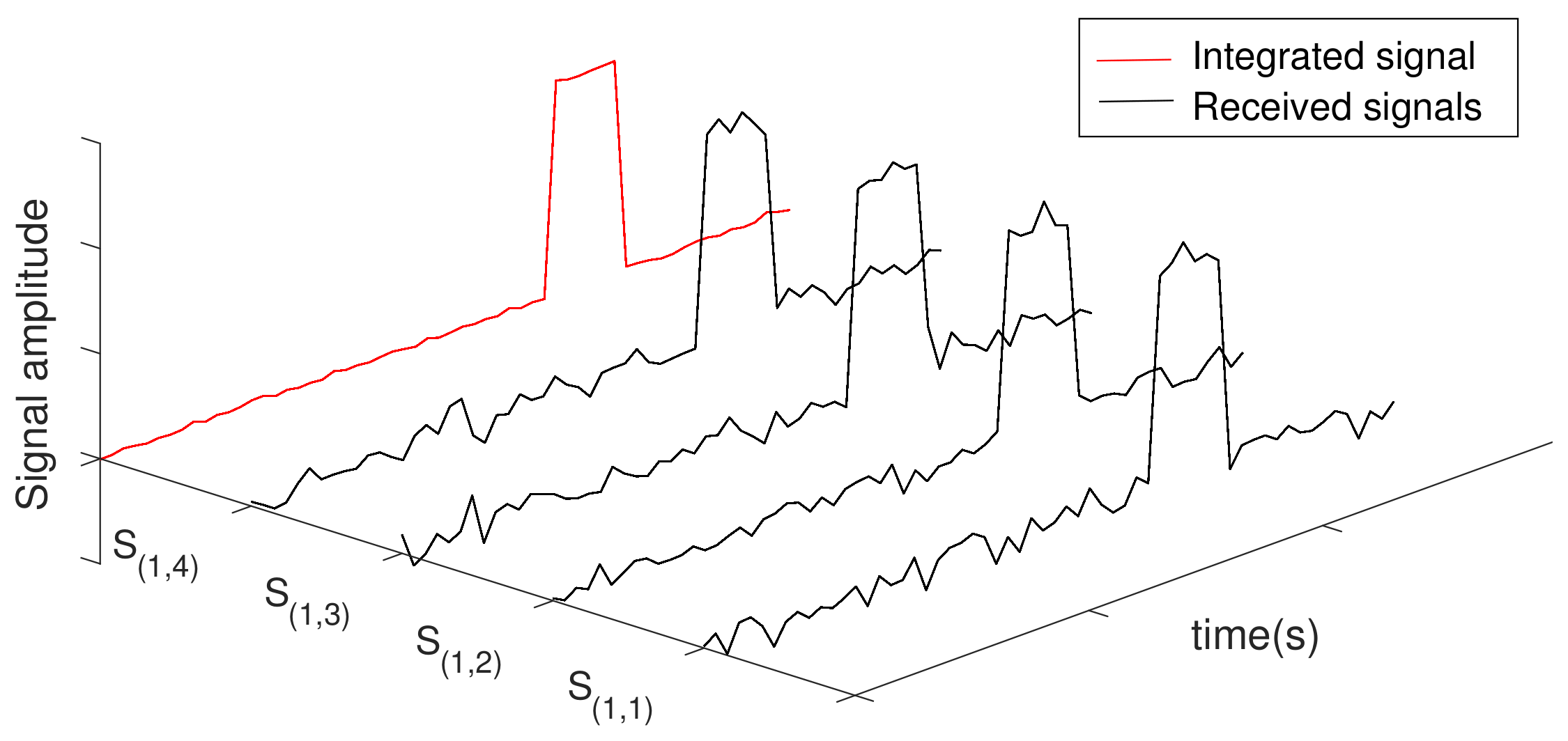
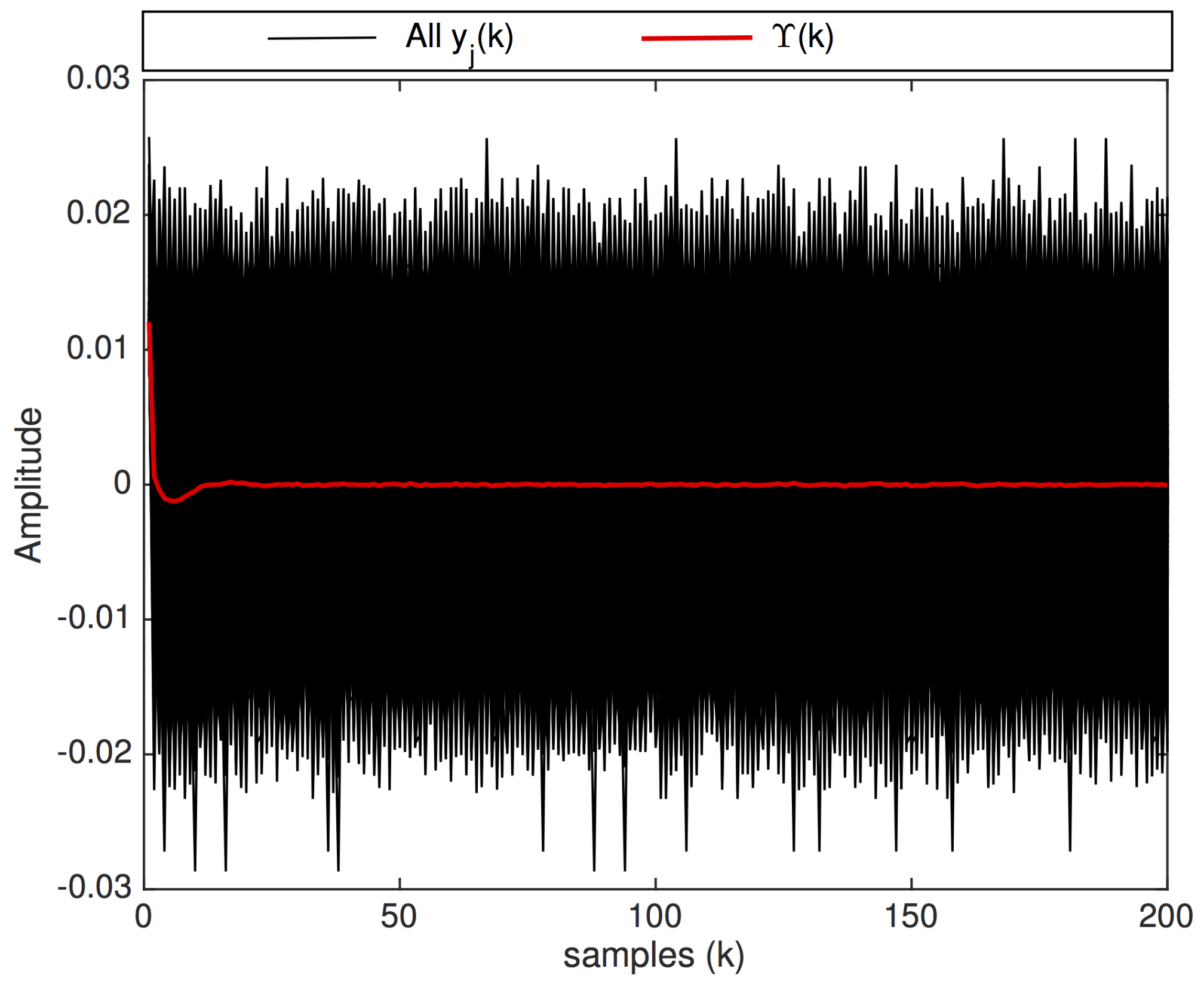
3.2.2. Noise Impulse Integration Technique
- Goal: The goal of the RPI technique is to minimize the uncorrelated noise contained in signals received by the radar, and reinforce the echoes reflected by bodies within the radar antenna’s line of sight—i.e., produce a signal with grater SNR. The goal of the NII technique is to obtain a clear impulse response function of an LTI system, when it is excited by a white gaussian noise;
- Integrated signals: The RPI technique integrates signals received between consecutive pulse transmissions, containing, in general, reflected pulses and noise. The NII technique integrates portions of the signal produced by an LTI system when white gaussian noise is injected into it.
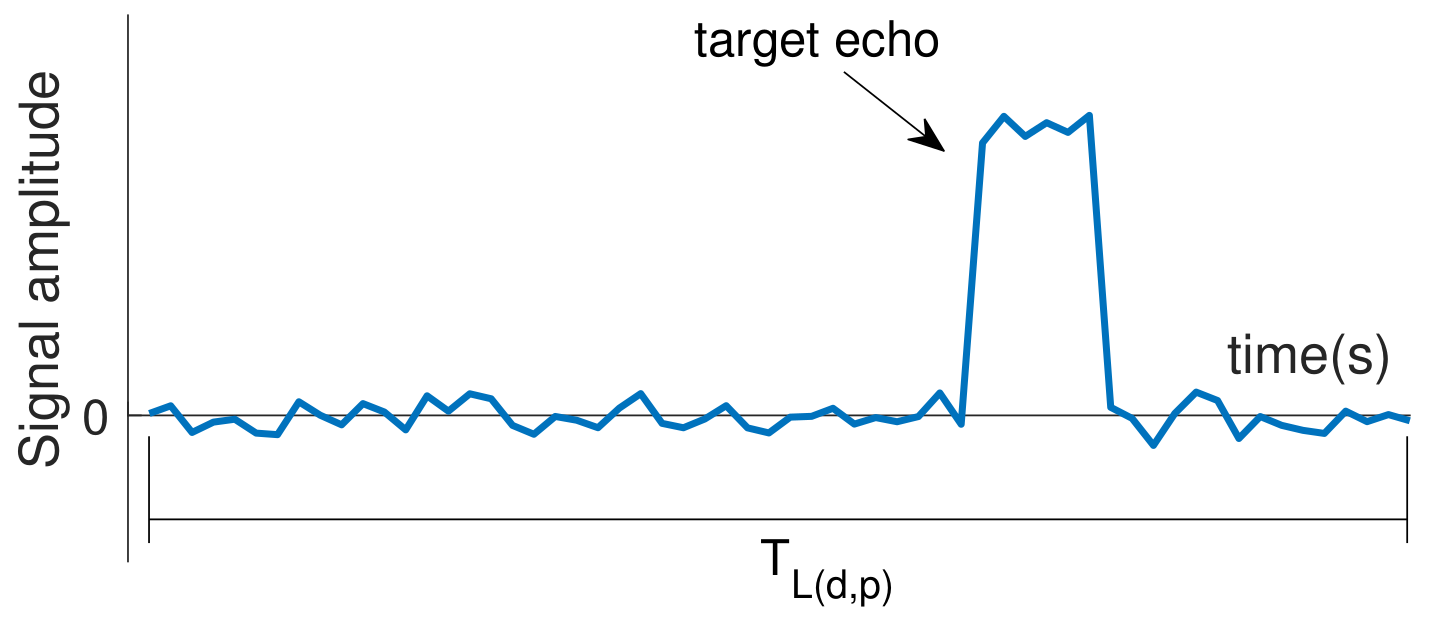
- Selection of signals to be integrated: In the RPI technique, the selection of signals to be integrated is straightforward. As explained in Section 3.2.1, it integrates signals received between the transmission of consecutive radar pulses. This selection provides a synchronism between the signals to be integrated, which, as shown in Figure 7, aligns the information that must be reinforced by the RPI—i.e., reinforce echoes that are constantly present in the received signal. The RPI’s signal selection cannot be used in the NII technique, given that the latter is not triggered by pulses. Therefore, it is necessary to use other criteria to select the portions of signal to be integrated, which is explained in the remainder of this section.
| Algorithm 2: Generation of signals . |
 |
- and are obtained through the NII technique, by processing signals and —specified in Section 3.1 and indicated in Figure 3;
| Algorithm 3: Attack Identification with the NII technique. |
 |
4. Results
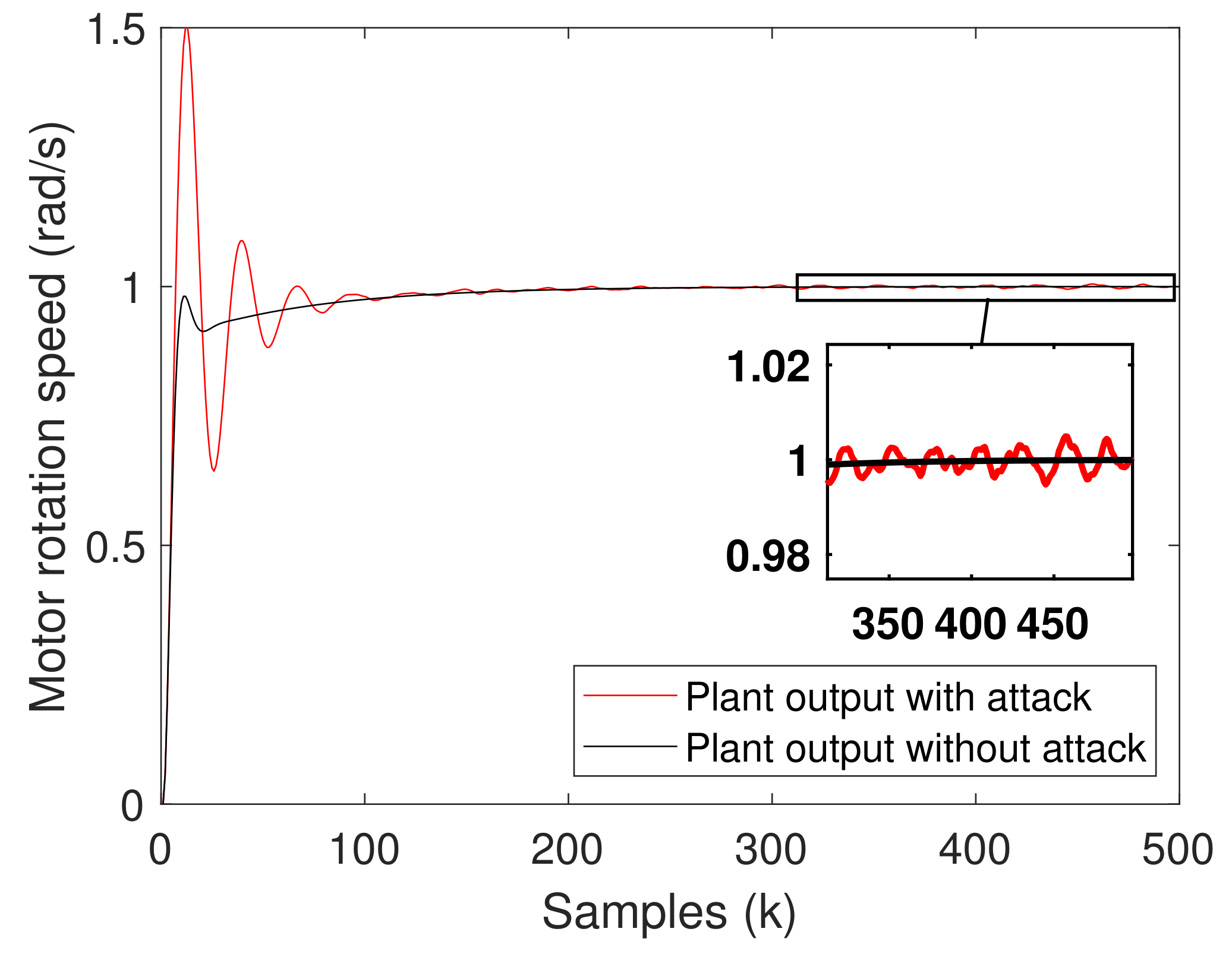
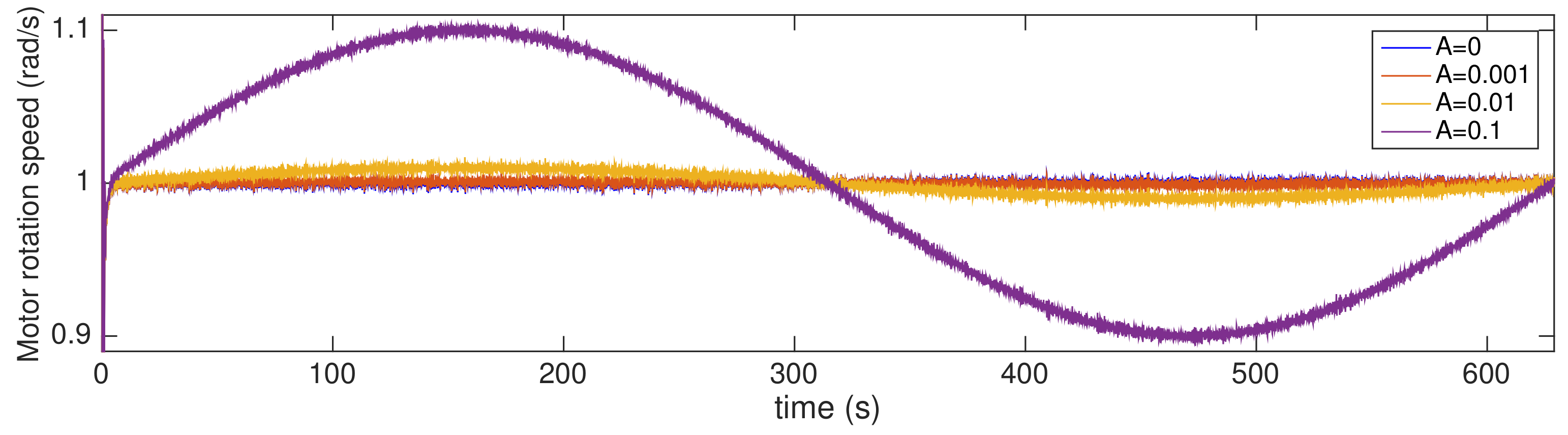
4.1. Attacked NCSs and Parameters of the Attack
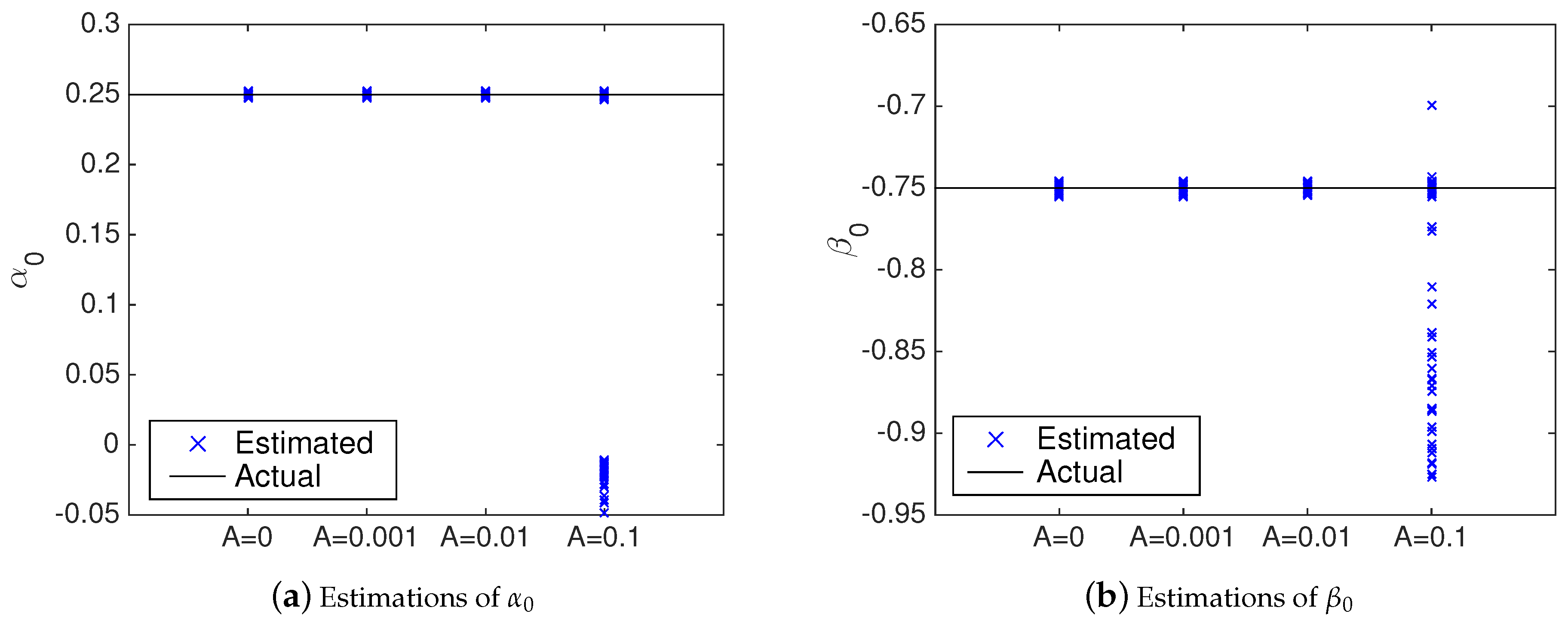
4.2. Performance of the Attack Identification
- 100 simulations using the identification process shown in Algorithm 1—i.e., without the NII technique; and
- 100 simulations using the identification process shown in Algorithm 3—i.e., with the NII technique.
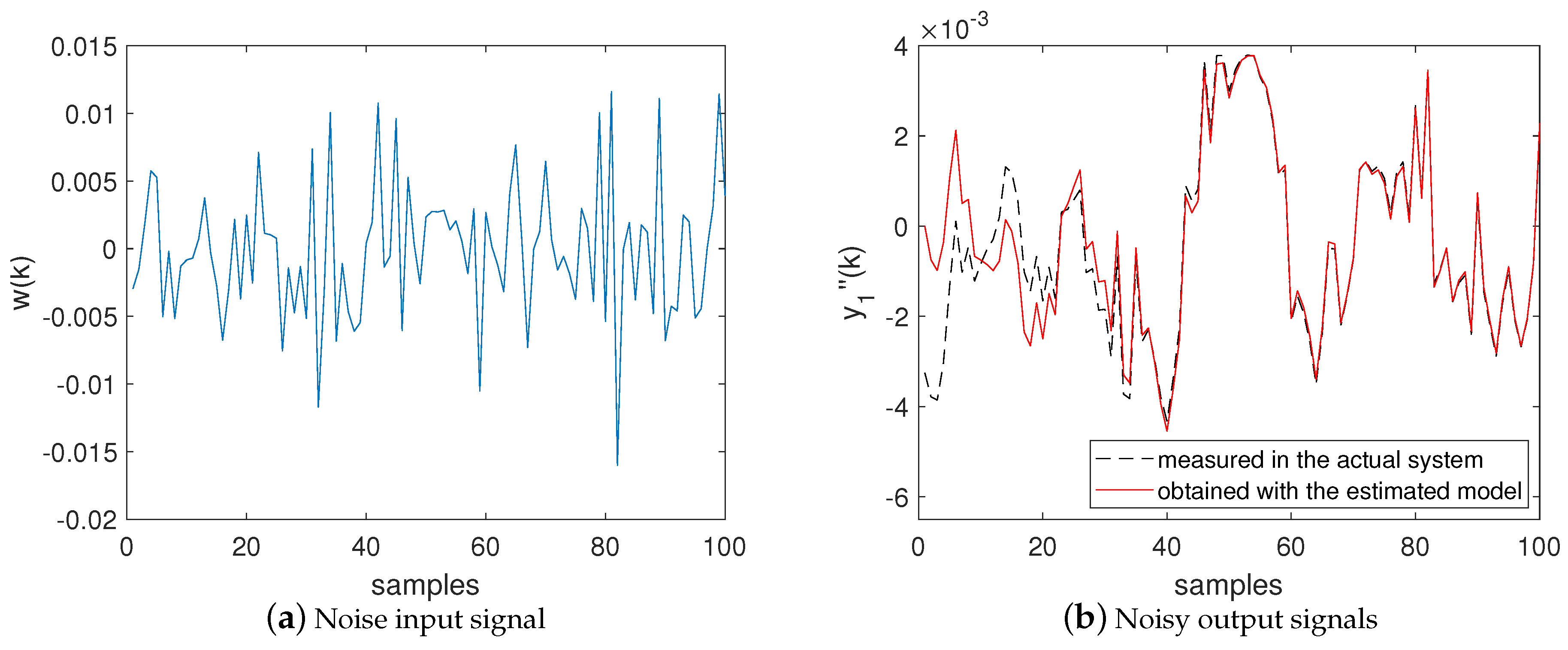
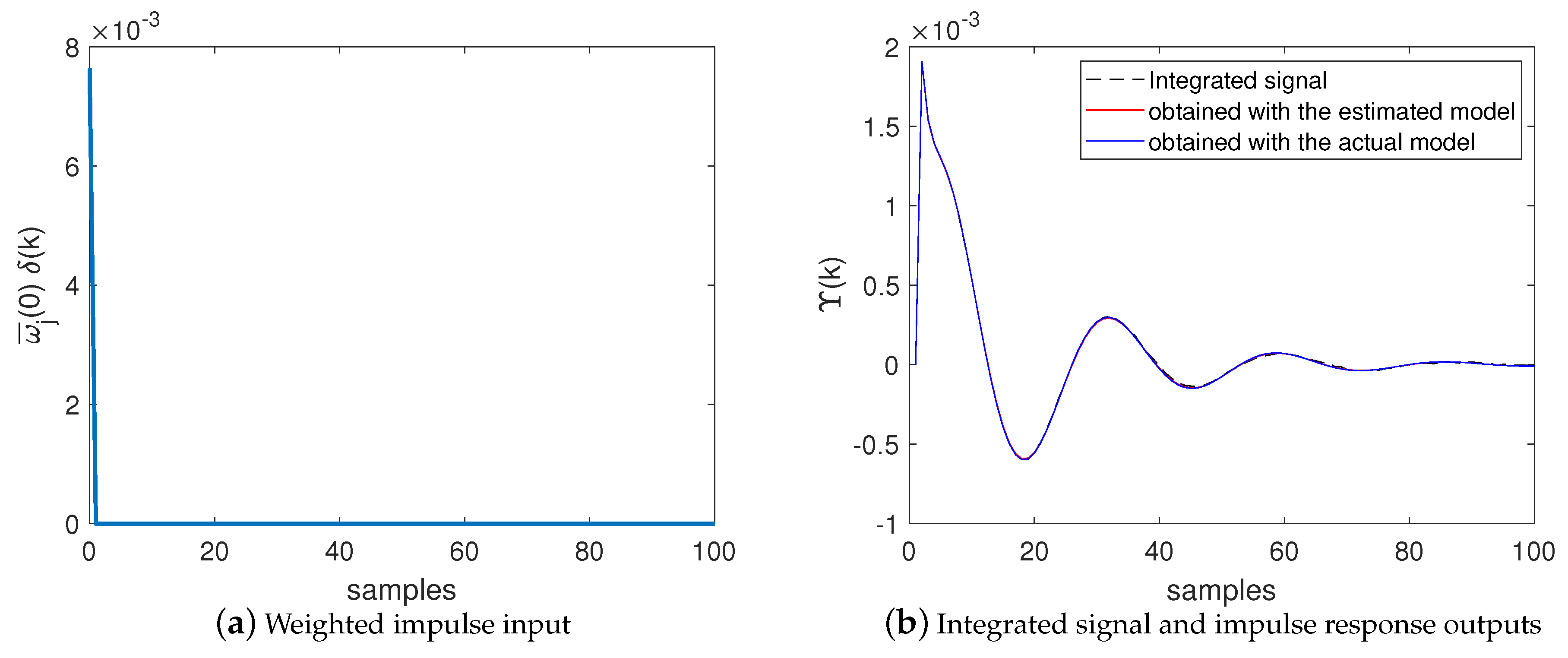
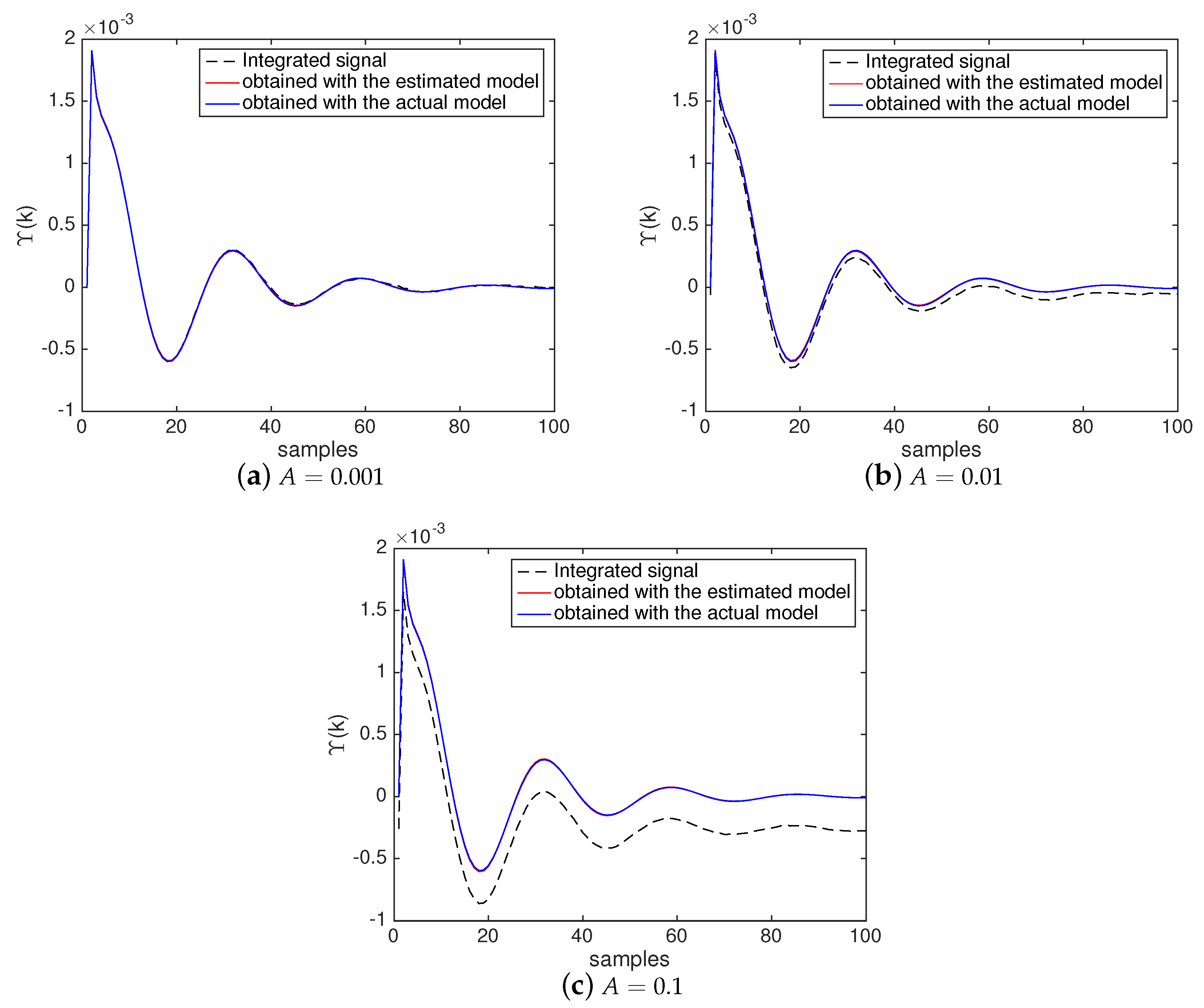
- In black dashed line: the integrated signal produced by the NII stage (based on measurements in the actual system) and used by the BSA as the reference output for the model defined in (28);
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Lasi, H.; Fettke, P.; Kemper, H.G.; Feld, T.; Hoffmann, M. Industry 4.0. Bus. Inf. Syst. Eng. 2014, 6, 239–242. [Google Scholar] [CrossRef]
- Jazdi, N. Cyber physical systems in the context of Industry 4.0. In Proceedings of the 2014 IEEE International Conference on Automation, Quality and Testing, Robotics, Cluj-Napoca, Romania, 22–24 May 2014; pp. 1–4. [Google Scholar]
- Latrech, C.; Chaibet, A.; Boukhnifer, M.; Glaser, S. Integrated longitudinal and lateral networked control system design for vehicle platooning. Sensors 2018, 18, 3085. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Ju, H.H.; Long, Y.; Wang, H. Reliable Finite Frequency Filter Design for Networked Control Systems with Sensor Faults. Sensors 2012, 12, 7975–7993. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Santos, C.; Martínez-Rey, M.; Espinosa, F.; Gardel, A.; Santiso, E. Event-based sensing and control for remote robot guidance: An experimental case. Sensors 2017, 17, 2034. [Google Scholar] [CrossRef] [Green Version]
- Dasgupta, S.; Halder, K.; Banerjee, S.; Gupta, A. Stability of Networked Control System (NCS) with discrete time-driven PID controllers. Control Eng. Pract. 2015, 42, 41–49. [Google Scholar] [CrossRef]
- McLaughlin, S.; Konstantinou, C.; Wang, X.; Davi, L.; Sadeghi, A.R.; Maniatakos, M.; Karri, R. The cybersecurity landscape in industrial control systems. Proc. IEEE 2016, 104, 1039–1057. [Google Scholar] [CrossRef]
- de Sa, A.O.; da Costa Carmo, L.F.R.; Machado, R.C.S. Covert Attacks in Cyber-Physical Control Systems. IEEE Trans. Ind. Inf. 2017, 13, 1641–1651. [Google Scholar] [CrossRef] [Green Version]
- Ferrari, P.; Flammini, A.; Rizzi, M.; Sisinni, E. Improving simulation of wireless networked control systems based on WirelessHART. Comput. Stand. Interfac. 2013, 35, 605–615. [Google Scholar] [CrossRef]
- Das, M.; Ghosh, R.; Goswami, B.; Gupta, A.; Tiwari, A.; Balasubrmanian, R.; Chandra, A. Network control system applied to a large pressurized heavy water reactor. IEEE Trans. Nucl. Sci. 2006, 53, 2948–2956. [Google Scholar] [CrossRef]
- Dasgupta, S.; Routh, A.; Banerjee, S.; Agilageswari, K.; Balasubramanian, R.; Bhandarkar, S.; Chattopadhyay, S.; Kumar, M.; Gupta, A. Networked control of a large pressurized heavy water reactor (PHWR) with discrete proportional-integral-derivative (PID) controllers. IEEE Trans. Nucl. Sci. 2013, 60, 3879–3888. [Google Scholar] [CrossRef]
- Smith, R.S. Covert Misappropriation of Networked Control Systems: Presenting a Feedback Structure. Control Syst. IEEE 2015, 35, 82–92. [Google Scholar]
- De Sa, A.O.; da Costa Carmo, L.F.R.; Machado, R.C.S. Bio-inspired Active System Identification: A Cyber-Physical Intelligence Attack in Networked Control Systems. Mob. Netw. Appl. 2017, 1–14. [Google Scholar] [CrossRef]
- Langner, R. Stuxnet: Dissecting a cyberwarfare weapon. Secur. Priv. IEEE 2011, 9, 49–51. [Google Scholar] [CrossRef]
- Smith, R. A decoupled feedback structure for covertly appropriating networked control systems. In Proceedings of the 18th IFAC World Congress 2011, IFAC-PapersOnLine, Milano, Italy, 28 August–2 September 2011. [Google Scholar]
- Teixeira, A.; Shames, I.; Sandberg, H.; Johansson, K.H. A secure control framework for resource-limited adversaries. Automatica 2015, 51, 135–148. [Google Scholar] [CrossRef] [Green Version]
- Zetter, K. Countdown to Zero Day: Stuxnet and the Launch of the World’s First Digital Weapon; Crown: New York, NY, USA, 2014. [Google Scholar]
- Falliere, N.; Murchu, L.O.; Chien, E. W32. stuxnet dossier. White Pap. Symantec Corp. Secur. Response 2011, 5, 29. [Google Scholar]
- Muller, I.; Netto, J.C.; Pereira, C.E. WirelessHART field devices. IEEE Instrum. Meas. Mag. 2011, 14, 20–25. [Google Scholar] [CrossRef]
- Petersen, S.; Carlsen, S. WirelessHART Versus ISA100. 11a: The Format War Hits the Factory Floor. IEEE Ind. Electron. Mag. 2011, 4, 23–34. [Google Scholar] [CrossRef] [Green Version]
- Collantes, M.H.; Padilla, A.L. Protocols and Network Security in ICS Infrastructures; Technical Report; Spanish National Institute for Cyber-Security ( INCIBE): León, Spain, 2015. [Google Scholar]
- Peschke, J.; Reinelt, D.; Yumin, W.; Treytl, A. Security in industrial ethernet. In Proceedings of the 11th IEEE International Conference on Emerging Technologies and Factory Automation, Prague, Czech Republic, 20–22 September 2006; pp. 1214–1221. [Google Scholar]
- Granat, A.; HÖFKEN, H.; Schuba, M. Intrusion Detection of the ICS Protocol EtherCAT. In Proceedings of the 2nd International Conference on Computer, Network Security and Communication Engineering (CNSCE 2017), Bangkok, Thailand, 26–27 March 2017; pp. 113–117. [Google Scholar]
- Ovaz Akpinar, K.; Ozcelik, I. Development of the ECAT Preprocessor with the Trust Communication Approach. Secur. Commun. Netw. 2018, 2018, 2639750. [Google Scholar] [CrossRef]
- Yung, J.; Debar, H.; Granboulan, L. Security Issues and Mitigation in Ethernet POWERLINK. In Proceedings of the Conference on Security of Industrial-Control-and Cyber-Physical Systems, Crete, Greece, 26–30 September 2016; pp. 87–102. [Google Scholar]
- Mathur, A.P.; Tippenhauer, N.O. SWaT: a water treatment testbed for research and training on ICS security. In Proceedings of the 2016 International Workshop on Cyber-physical Systems for Smart Water Networks (CySWater), Vienna, Austria, 11 April 2016; pp. 31–36. [Google Scholar]
- Pfrang, S.; Meier, D. On the Detection of Replay Attacks in Industrial Automation Networks Operated with Profinet IO. In Proceedings of the ICISSP, Porto, Portugal, 9–21 February 2017; pp. 683–693. [Google Scholar]
- Akerberg, J.; Bjorkman, M. Exploring security in PROFINET IO. In Proceedings of the 2009 33rd Annual IEEE International Computer Software and Applications Conference, Seattle, WA, USA, 20–24 July 2009; Volume 1, pp. 406–412. [Google Scholar]
- de Sa, A.O.; da Costa Carmo, L.F.R.; Machado, R.C.S. A controller design for mitigation of passive system identification attacks in networked control systems. J. Int. Serv. Appl. 2018, 9, 1–19. [Google Scholar] [CrossRef] [Green Version]
- Rubio-Hernan, J.; Rodolfo-Mejias, J.; Garcia-Alfaro, J. Security of cyber-physical systems. In Proceedings of the International Workshop on the Security of Industrial Control Systems and Cyber-Physical Systems, Crete, Greece, 26–30 September 2016; pp. 3–18. [Google Scholar]
- Stouffer, K.; Pillitteri, V.; Lightman, S.; Abrams, M.; Hahn, A. NIST Special Publication 800-82, Revision 2: Guide to Industrial Control Systems (ICS) Security; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2015. [Google Scholar]
- Pang, Z.H.; Liu, G.P. Design and implementation of secure networked predictive control systems under deception attacks. IEEE Trans. Control Syst. Technol. 2012, 20, 1334–1342. [Google Scholar] [CrossRef]
- Gerard, B.; Rebaï, S.B.; Voos, H.; Darouach, M. Cyber security and vulnerability analysis of networked control system subject to false-data injection. In Proceedings of the 2018 Annual American Control Conference (ACC), Milwaukee, WI, USA, 27–29 June 2018; pp. 992–997. [Google Scholar]
- Miao, F.; Zhu, Q.; Pajic, M.; Pappas, G.J. Coding sensor outputs for injection attacks detection. In Proceedings of the 53rd IEEE Conference on Decision and Control, Los Angeles, CA, USA, 15–17 December 2014; pp. 5776–5781. [Google Scholar]
- Dhunna, G.S.; Al-Anbagi, I. A Low Power WSNs Attack Detection and Isolation Mechanism for Critical Smart Grid Applications. IEEE Sens. J. 2019, 19, 5315–5324. [Google Scholar] [CrossRef]
- Rigatos, G.; Serpanos, D.; Zervos, N. Detection of attacks against power grid sensors using Kalman filter and statistical decision making. IEEE Sens. J. 2017, 17, 7641–7648. [Google Scholar] [CrossRef]
- Mo, Y.; Weerakkody, S.; Sinopoli, B. Physical authentication of control systems: Designing watermarked control inputs to detect counterfeit sensor outputs. IEEE Control Syst. Mag. 2015, 35, 93–109. [Google Scholar]
- Mo, Y.; Sinopoli, B. Secure control against replay attacks. In Proceedings of the 2009 47th Annual Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, VA, USA, 30 September 2009; pp. 911–918. [Google Scholar]
- Mo, Y.; Chabukswar, R.; Sinopoli, B. Detecting integrity attacks on SCADA systems. IEEE Trans. Control Syst. Technol. 2014, 22, 1396–1407. [Google Scholar]
- Ferrari, R.M.; Teixeira, A.M. Detection and isolation of replay attacks through sensor watermarking. IFAC-PapersOnLine 2017, 50, 7363–7368. [Google Scholar] [CrossRef]
- Krombholz, K.; Hobel, H.; Huber, M.; Weippl, E. Advanced social engineering attacks. J. Inf. Secur. Appl. 2015, 22, 113–122. [Google Scholar] [CrossRef]
- Skolnik, M.I. Radar Handbook; Electronic Engineering Series; McGraw-Hill: New York, NY, USA, 1990. [Google Scholar]
- Civicioglu, P. Backtracking search optimization algorithm for numerical optimization problems. Appl. Math. Comput. 2013, 219, 8121–8144. [Google Scholar] [CrossRef]
- Tulleken, H.J. Generalized binary noise test-signal concept for improved identification-experiment design. Automatica 1990, 26, 37–49. [Google Scholar] [CrossRef]
- de Sá, A.O.; Carmo, L.F.R.d.C.; Machado, R.C.S. Countermeasure for Identification of Controlled Data Injection Attacks in Networked Control Systems. In Proceedings of the 2019 II Workshop on Metrology for Industry 4.0 and IoT (MetroInd4. 0&IoT), Naples, Italy, 4–6 June 2019; pp. 455–459. [Google Scholar]
- Stallings, W. Cryptography and Network Security: Principles and Practices; Pearson Education India: Upper Saddle River, NJ, USA, 2006. [Google Scholar]
- Ahmed, S. Novel noncoherent radar pulse integration to combat noise jamming. IEEE Trans. Aerosp. Electron. Syst. 2015, 51, 2350–2359. [Google Scholar] [CrossRef]
- Schwartz, M. Effects of signal fluctuation on the detection of pulse signals in noise. IRE Trans. Inf. Theory 1956, 2, 66–71. [Google Scholar] [CrossRef]
- Chen, X.; Song, Y.; Yu, J. Network-in-the-Loop Simulation Platform for Control System. In AsiaSim 2012; Springer: Shanghai, China, 27 October 2012; pp. 54–62. [Google Scholar]
- Long, M.; Wu, C.H.; Hung, J.Y. Denial of service attacks on network-based control systems: impact and mitigation. Ind. Inf. IEEE Trans. 2005, 1, 85–96. [Google Scholar] [CrossRef]
- Shi, Y.; Huang, J.; Yu, B. Robust tracking control of networked control systems: application to a networked DC motor. IEEE Trans. Ind. Electron. 2013, 60, 5864–5874. [Google Scholar] [CrossRef]
- Si, M.L.; Li, H.X.; Chen, X.F.; Wang, G.H. Study on Sample Rate and Performance of a Networked Control System by Simulation. Adv. Mater. Res. Trans. Tech. Publ. 2010, 139, 2225–2228. [Google Scholar]
- Tran, T.; Ha, Q.P.; Nguyen, H.T. Robust non-overshoot time responses using cascade sliding mode-pid control. J. Adv. Comput. Intell. Intell. Inf. 2007, 11, 1224–1231. [Google Scholar] [CrossRef] [Green Version]
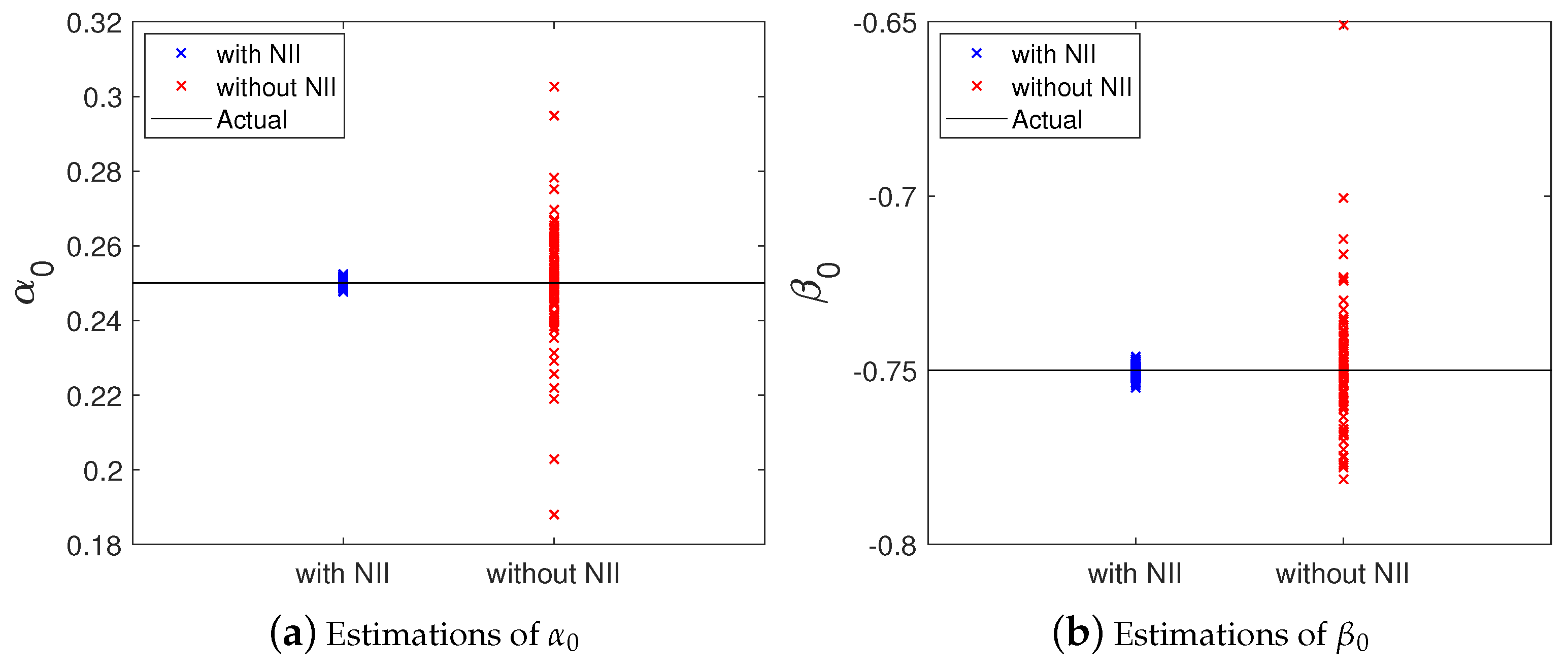
| Coefficient | Algorithm | Mean | Standard Deviation |
|---|---|---|---|
| with NII | 0.2500 | 0.0011 | |
| without NII | 0.2506 | 0.0147 | |
| with NII | −0.7502 | 0.0017 | |
| without NII | −0.7485 | 0.0172 |
| Coefficient | A | Mean | Standard Deviation |
|---|---|---|---|
| 0 * | 0.2500 | 0.0011 | |
| 0.001 | 0.2500 | 0.0011 | |
| 0.01 | 0.2500 | 0.0011 | |
| 0.1 | 0.1712 | 0.1241 | |
| 0.1 ** | 0.2500 | 0.0012 | |
| 0 * | −0.7502 | 0.0017 | |
| 0.001 | −0.7502 | 0.0017 | |
| 0.01 | −0.7501 | 0.0017 | |
| 0.1 | −0.7812 | 0.0586 | |
| 0.1 ** | −0.7500 | 0.0020 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Oliveira de Sá, A.; Casimiro, A.; Machado, R.C.S.; da C. Carmo, L.F.R. Identification of Data Injection Attacks in Networked Control Systems Using Noise Impulse Integration. Sensors 2020, 20, 792. https://doi.org/10.3390/s20030792
Oliveira de Sá A, Casimiro A, Machado RCS, da C. Carmo LFR. Identification of Data Injection Attacks in Networked Control Systems Using Noise Impulse Integration. Sensors. 2020; 20(3):792. https://doi.org/10.3390/s20030792
Chicago/Turabian StyleOliveira de Sá, Alan, António Casimiro, Raphael C. S. Machado, and Luiz F. R. da C. Carmo. 2020. "Identification of Data Injection Attacks in Networked Control Systems Using Noise Impulse Integration" Sensors 20, no. 3: 792. https://doi.org/10.3390/s20030792
APA StyleOliveira de Sá, A., Casimiro, A., Machado, R. C. S., & da C. Carmo, L. F. R. (2020). Identification of Data Injection Attacks in Networked Control Systems Using Noise Impulse Integration. Sensors, 20(3), 792. https://doi.org/10.3390/s20030792






