1. Introduction
Two-party cryptographic protocol is a significant branch of modern cryptography. It can realize communication between mutually distrustful parties [
1,
2,
3]. However, the advent of a quantum computer will pose a huge threat to cryptographic protocols that originally rely on computational complexity. Fortunately, Bennett and Brassard proposed the first quantum cryptographic protocol in 1984, known as BB84 quantum key distribution (QKD) protocol [
1]. BB84 protocol allows two mutually trusted parties to generate identical secret keys for encryption. Quantum cryptography, laying its foundation on quantum mechanics, can provide unconditional security in the communication process. Therefore, studies over quantum cryptography have aroused worldwide attention.
While QKD has gained extensive concern nowadays, researchers also consider introducing quantum technology into two-party cryptographic protocols. However, Lo and Mayers independently demonstrated that unconditionally secure two-party cryptographic protocol does not exist without restricting the attacker’s ability [
4,
5,
6,
7]. Therefore, a perfect two-party cryptographic protocol is more difficult to be realized than key distribution. Even so, several solutions were proposed to seek more secure quantum two-party cryptographic schemes, among which there are mainly three types. The first solution introduces the relativity theory to restrain attacker’s behavior [
3,
8,
9,
10]. The second solution weakens the demand for security. In other words, it gives up the pursuit of perfect security and allows the attacker’s behavior to succeed with negligible probability. The most representative example is the cheat-sensitive quantum bit commitment (CSQBC) protocol [
11,
12,
13,
14]. The third solution is limiting the attacker’s power to current technologies. For example, in 2005, Damgård demonstrated secure two-party cryptography under the assumption that the attacker’s capability of storing quantum states was limited. In this so-called bounded storage model [
15,
16], the attacker is equipped with perfect quantum storage, but the storage capacity is limited because of unaffordable cost. Later, Schaffner extended the model to the noisy storage model [
2,
17], where the attacker possesses quantum storage with unlimited capacity, but the noise increases over time.
Although Konig manifested secure two-party cryptographic protocols are feasible under noisy bounded model [
2,
17], we are still interested in designing two-party cryptographic protocols when the attacker possesses perfect quantum storage inspired by He’s work [
18]. We have discovered that two-party cryptographic protocols, like bit commitment, oblivious transfer, in Ref. [
2,
11,
17] do not have the process of error estimation, which serves as a significant indicator of eavesdropping attack in QKD. The reasons are obvious: For one thing, the communication parties do not trust each other and for another, the information is asymmetric between parties during the communication process.
Inspired by the foundations of measurement-device-independent QKD (MDI-QKD) [
19,
20,
21] and phase-matching QKD (PM-QKD) [
22,
23], we make it possible to introduce error estimation into two-party cryptographic protocols. In the QKD process, once there is an eavesdropper, the final key error rate will exceed the upper limit. Therefore, in encrypted communication between the two parties, if one party is dishonest, the information they previously negotiated will also have a higher error rate, which is difficult in avoiding detection by another party. In MDI-QKD, the measurement stage is independent of the final key. This de-emphasizes the assumptions for the attacker’s quantum memory and enables us to discover the attacker by the increased quantum bit error rate during the estimation process.
In this paper, we introduce joint measurement method in MDI-QKD and PM-QKD, and error estimation into two-party cryptographic protocols, and raise our improved weak string erasure (WSE) protocol and 1-2 random oblivious transfer (ROT) protocol. These two protocols are significant for other TPC (two-party cryptographic protocols) applications. Compared with existing WSE and 1-2 ROT protocol, our protocol does not make any assumption on the attacker’s devices. Instead, we restrict the attacking behavior by the protocol itself, which offers greater security. In our protocol, the honest party does not need quantum storage devices and the devices are compatible with mainstream QKD platforms.
The paper is organized as follows.
Section 2 introduces the foundations of our research.
Section 3, and
Section 4 discuss our proposed WSE and 1-2 ROT respectively, and demonstrate their security. In
Section 5, we probe into applications of two-party cryptographic protocols and propose two important practices, quantum bit commitment and password-based identification. Finally, the paper ends with a conclusion.
2. Preliminaries
This section will introduce several fundamental concepts to our research, including entropy qualities, joint measurement, error estimation, and privacy amplification.
This paper follows the notations in Ref. [
2], using
for the set of nature number, and
is the set of all possible subsets of
.
2.1. Entropy Qualities
Here, we present some crucial entropy qualities for our security proof. Bulleted lists look like this:
Definition 1 (Shannon entropy)
. is the probability distribution function of a random variable X. The entropy is defined as: As same as Ref. [
2,
19], we define guessing probability:
where
is the probability of guessing
X when given register
E, and its maximization is over all positive operate-valued measurements (POVMs) {
} acting on register
E. Then we can easily get that the conditional min-entropy of
X given
E is:
and also the definition of conditional smooth min-entropy is:
where for any event
, we have:
Next, we discuss min-entropy-splitting lemma used in Ref. [
2,
17] for the security proof of 1-2 ROT and WSE protocol.
Lemma 1 (Entropy splitting [
2,
17]).
Let , and and Z are random variables subjected to (). There exists a random variable such that for any independent random variable with , Lemma 2 (Min-entropy splitting [
2,
17]).
Let , and , , and Z are random variables subjected to . Then there exists a random variable , such that: Finally, we introduce quantum uncertainty relation as the core of security proof for our redesigned protocol.
Theorem 1 (Quantum uncertainty relation [
24]).
Suppose Q is an arbitrary fixed n-qubit state, and θ is a random basis (), and is a random variable for the outcome of measuring Q in basis , then it has , and the conditional smooth min-entropy has a lower bound such that: 2.2. Joint Measurement
Joint measurement and phase-matching are widely used in QKD, and we introduce them to our two-party cryptographic protocol. Next, we explain these two methods.
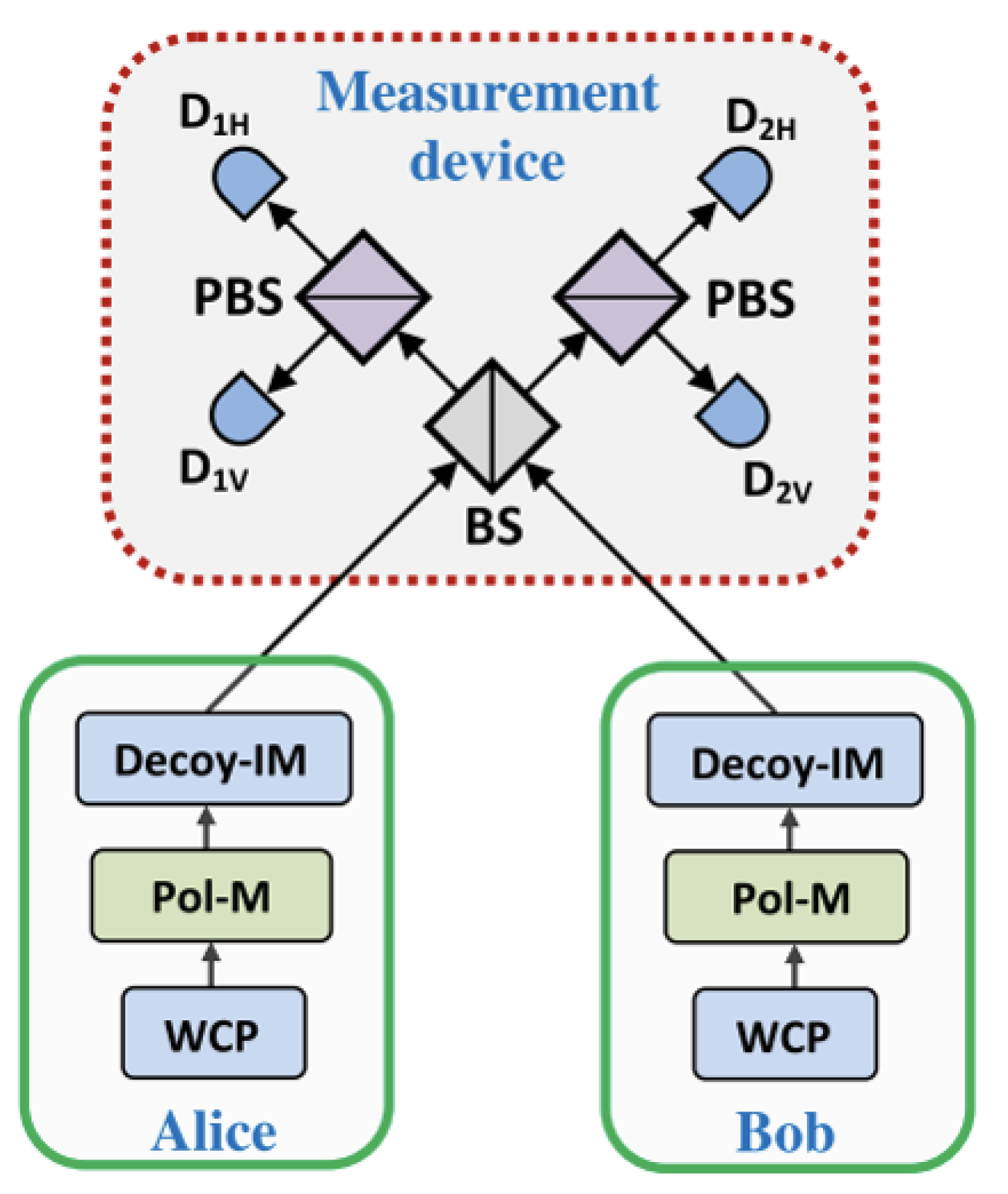
Prior to 2012, most quantum cryptographic protocols, including QKD and many two-party cryptography protocols, used single-state measurement. The earliest application of joint measurement to quantum protocols is introduced by Hoi-Kwong Lo [
19]. In Ref. [
19], he presented the idea of MDI-QKD using joint measurement. The measurement method is shown in
Figure 1.
In
Figure 1, Alice and Bob will prepare a single quantum state and send it to the third party, Charlie. Charlie will measure those quantum states in Bell basis. The state
is joint by a click in
and
or
and
, and
is joint by a click in
and
or
and
. Therefore, Alice and Bob can get the raw key based on measurement outcomes and prepared basis, which is shown in
Table 1.
Another joint measurement method uses phase coding, which is generally used in the continuous variable QKD. The representative protocols are PM-QKD [
22] and TF-QKD [
23]. The measurement method is shown in
Figure 2. Phase-matching QKD uses coherent state to send information. We define that
and
, where
are the basis phase chosen by Alice and Bob.
According to Mach–Zehnder interference, the detector clicks when the phase difference of and is an even multiple of , and the detector clicks when the phase difference of and is an odd multiple of . When a phase difference of and is not a multiple of , a random click occurs. Bob will flip his key when detector click because only will cause the phase difference to be an odd multiple of .
2.3. Error Estimation
Error estimation is one of the most important methods to ensure security in quantum cryptographic protocols. However, so far, in the two-party quantum encryption protocol, no method to improve the security of the protocol by error estimation has been seen. This is due to the asymmetry of the information in the two-party encryption protocols and the coupling between the measurement results and final key. We find that joint measurement reduces this coupling and try to introduce the error estimation method into the two-party encryption protocol. In this paper, because of the asymmetry of the information, we use the random sampling method for error estimation.
In QKD, the operation process of the random sampling method can be described as follows: Among the raw key and owned by Alice and Bob, randomly extract a certain percentage p of the key at the corresponding positions and publishing these bits through the classical channel with trusted authentication. The inconsistency rate of the sampling key can be regarded as the code error rate of the raw key (since the extracted key has been published, it cannot be used in subsequent processing steps and needs to be discarded). In the two-party quantum cryptographic protocol, due to the asymmetry of information (for example, in the ROT protocol, after performing base matching, Bob does not discard the key that failed to match, but performs key separation according to his chosen c), Alice will perform random sampling from all keys, and require that the preparation base and key of the sampling part be made public, and then calculate the code error rate.
Assume that the error rate of the raw key owned by Alice and Bob is
e and the key length is
l, compared with the Alice’s key, Bob’s raw key has
errors. The amount of randomly extracted key bits is
and satisfies
, that is,
. Assume that there are
m bit errors in the extracted
keys, then consider that the error rate of the raw key is:
In this paper, in order to ensure the security of the two-party encryption protocol, we put the error estimation process before the base matching. Thus, we can get:
2.4. Privacy Amplification
Generally speaking, we will use two-universal hash function for privacy amplification. The definition of two-universal hash function is as follows:
Definition 2 (Two-universal hash function).
Let be a cluster of functions (). If for all , we have:Then we say that is two-universal. Using two-universal hash function for privacy amplification, we also have privacy amplification theorem [
2].
Firstly, we know the security of a key is defined with respect to its L1-distance from a perfect key which is uniformly distributed and independent of the adversary’s state. Then the L1-distance from uniform of
given Q is:
where
is the fully mixed state.
Theorem 2 (Privacy amplification [
25]).
Given a set of two-universal hash functions , and a hash function , let be a classical-quantum state, then for any . we have: 3. Weak String Erasure
In order to better demonstrate the application of joint measurement and error estimation technology in two-party cryptographic protocols, we first discuss its enhancement to the security performance of weak string erasure (WSE), which was originally proposed by Konig [
2], and studied as the basic protocol of other two-party cryptographic protocols.
3.1. Definition
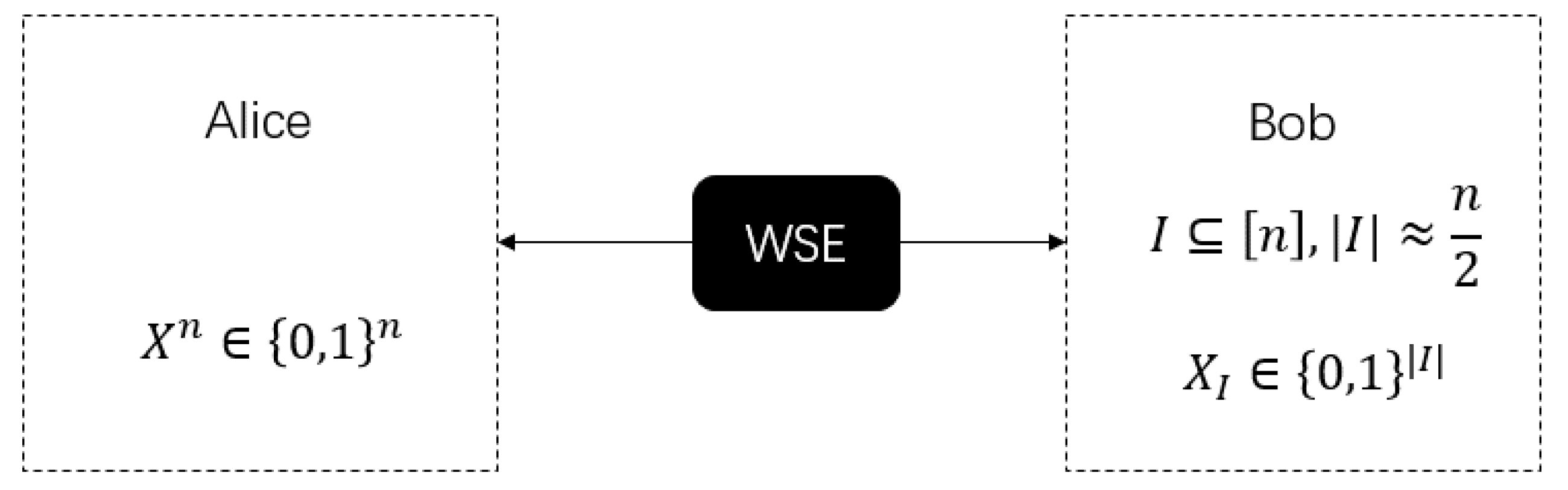
Before introducing our redesigned WSE protocol, we first introduce its definition. WSE is a basic two-party cryptographic protocol between Alice and Bob that can be used to construct other two-party cryptographic protocols, such as bit commitment, oblivious transfer, etc. The ideal functionality of WSE is shown in
Figure 3 [
2].
The process of WSE can be seen as a black box, with no inputs from Alice and Bob. As outputs, Alice gets a randomly chosen bits string and Bob obtains a randomly chosen subset of indices and the bits . Next, we denote A and B as honest Alice and Bob, and and as dishonest Alice and Bob. represents the joint state generated in the actual protocol operation, and represents the state generated in the ideal protocol operation.
The specific definition of WSE is as follows [
2]:
Definition 3 (Weak string erasure [
2]).
A -weak string erasure (WSE) scheme is a protocol between Alice and Bob satisfying the following properties:- 1.
Correctness: If both parties are honest, then for any attack strategy of the third-party attacker, Alice always gets a uniformly distributed string and Bob will get an index and ;
- 2.
Security for Alice: If Alice is honest, then for any attack strategy of dishonest Bob, we have: - 3.
Security for Bob: If Bob is honest, then for any attack strategy of dishonest Alice, there exists :
3.2. Protocol
In the previous protocol, there is a no error estimation process because the measurement results of the BB84 protocol are directly related to the final key. We redesign the WSE protocol by using the independence of key and measurement results of the MDI-QKD and PM-QKD protocols, adding a error estimation process to improve the security of the protocol.
The specific agreement is as follows:
Alice chooses a string and bases the specifying string randomly. She encodes each bit in the basis given by (as ) and sends it to the third party Charlie;
Similarly to Alice, Bob chooses a string and bases specifying string randomly. He encodes each bit in the basis given by (as ), and sends it to the third party Charlie;
Charlie performs a Bell measurement, and announces the outcome;
Alice selects a subset of the measurement outcome as the error estimator (about
m qubits) and sends a subset of the measurement outcome
to Bob. Bob sends
and a subset of the measurement outcome
(
) to Alice. Then, they initiate error estimation process and compute:
If , the communication is terminated, otherwise, the process continues;
Alice sends the remaining bases to Bob and outputs the remaining string ;
Bob computes and outputs .
3.3. Security Proof of WSE
Before analyzing the security of WSE protocol, we need to explain the constraint of Bob’s storage capacity under joint state measurement and error estimation. When we remove any assumption about storage devices, we need other approaches to limit Bob’s ability to store quantum states sent by Alice. Due to the constraints of the protocol process, we naturally think that Bob would cause the error rate increasement of the final key when he stores the quantum state and the error estimation is used to detect this attack. Next, we need to explain an important conception of the error correction upper bound of any channel error correction code. From [
26] we know that:
where
f is the reconciliation efficiency which is given by the redundancy of disclosed information to the theoretical limit necessary for successful error correction,
R is the code rate of a given channel error correction code,
e is the error rate, and function
h is the Shannon binary entropy. Then we can get the error correction upper bound when
f approaches 1, i.e., its Shannon limit:
where
is the inverse function of
h.
We consider when Bob stores the quantum state because the joint measurement cannot be performed and the published detection results are random. The increasement of error rate is explained the Lemma 3.
Lemma 3. Assume that Bob has a perfect and unlimited capacity of quantum memory. Our protocol has a storage rate v, where .
Proof. In our protocol, the measurement outcomes are jointly measured by a third party in the bell state and published before Alice sends the bases
. Alice will ask Bob to publish partial information for error estimation before sending bases
. Now, we assume that Bob’s storage rate is
v, which means Bob will store
quantum state in his memory. If Bob stores the quantum states, it means that he can not measure these quantum states, because quantum mechanics tells us that the measurement will cause the collapse of the quantum states and the loss of information. Therefore, Bob can publish a random fake outcome, and we have error rate introduced by this:
and we have:
where
is error rate that caused by channel noise. ☐
In fact, with Lemma 3, we can easily convert our protocol into a WSE protocol under the bounded-storage model. Therefore, we can use the proof methods and results in Ref. [
2,
17] to prove the security of our protocol.
Lemma 4 (Security for Alice).
Fix , and let,then for any attack strategy of dishonest Bob with any storage model , we have: Proof. According to the conclusion in Ref. [
2], we have:
where we have:
and in our protocol, we have parameters
,
,
,
, and
. So, we have:
then,
☐
Next, we will discuss the security for Bob. Proving the security for Bob is relatively simple because Bob has no other leaked information besides his quantum state information during the protocol.
Lemma 5 (Security for Bob).
According to [2,27], for any attack of dishonest Alice with any storage model , then we have: 4. 1-2 Random Oblivious Transfer
In this section, we further investigate 1-2 random oblivious transfer (ROT), which is also a basic two-party cryptographic protocol as WSE. Similarly, we give its definition first and then propose our protocol based on joint measurement and error estimation followed by its security proof.
4.1. Definition
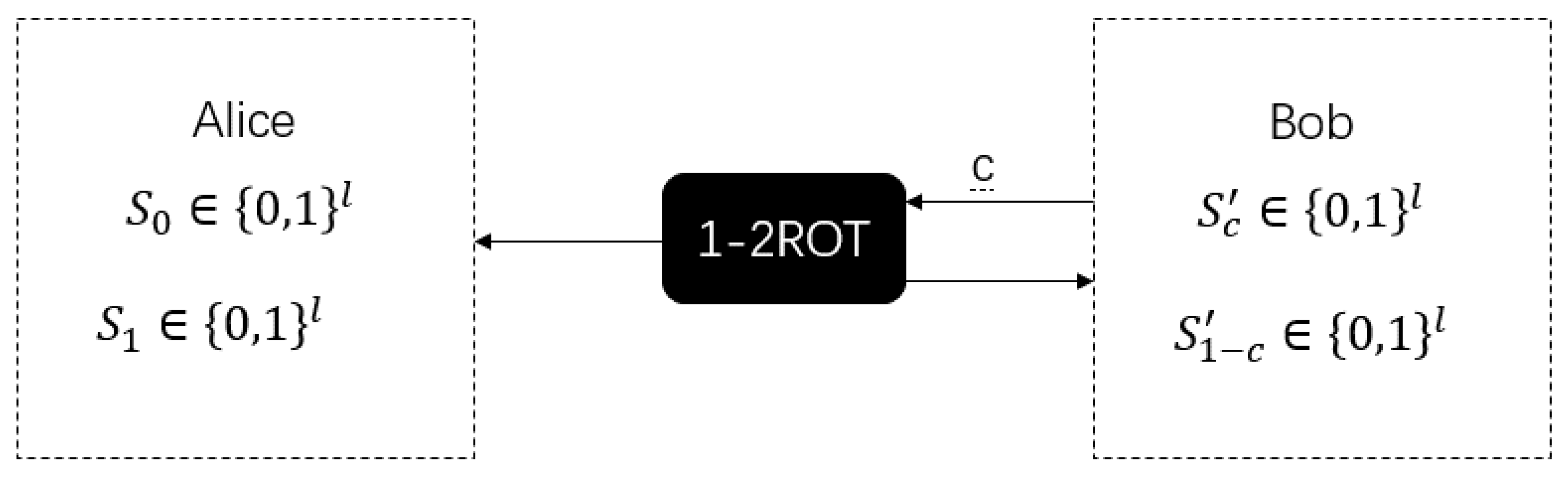
As in
Figure 4, like the WSE protocol, the 1-2 random oblivious transfer (ROT) protocol is also a basic two-party cryptographic protocol and is a random version of the 1-2 oblivious transfer (OT). Based on the 1-2 ROT protocol, we can easily implement the 1-2 OT protocol and the bit commitment (BC) protocol. In the 1-2 ROT protocol, instead of inputting two information strings
, Alice obtains two random key strings
. At the same time, Bob obtains the random key string
according to its input
c. If we want to implement the 1-2 OT protocol, just after running the 1-2 ROT protocol, Alice encrypts the information strings
and
with the two strings of keys
and
obtained by ROT protocol. Bob can use
for decryption to obtain
.
In the security definition of the 1-2 ROT protocol, Alice cannot obtain Bob’s input c, and Bob cannot obtain another string of keys except . The specific definition of security is as follows:
Definition 4. An ε - secure 1-2 ROT is a protocol between Alice and Bob, where Bob has input , and Alice has no input, satisfying:
- 1.
Correctness: If Alice and Bob are honest, then for any distribution of Bob’s input c which is unknown to Alice, Alice gets outputs which are ε-close to randomness and independent of c, and Bob obtains with probability ε;
- 2.
Security for Alice: If Alice is honest, then for any cheating strategy of Bob resulting in his state , there exists a random variable , and such that:and - 3.
Security for Bob: If Bob is honest and obtains output Y, then for any cheating strategy of Alice resulting in her state , there exists a random variable , such that:and
4.2. Protocol
We now give the specific 1-2 ROT protocol using error estimation as follows:
Preparation: Alice chooses and , and Bob chooses and . Both parties send the encoding quantum state or to third party Charlie;
Measurement: Charlie measures and with Bell measurement, and announces the outcome;
Error estimation: Alice chooses
and
, and sends
to Bob. Bob sends
, and
to Alice. Then Alice calculates the error rate:
If , they stop communication, otherwise they continue where is the error correction upper bound;
Key division: Both parties discard the data that used in error estimation. Alice sends to Bob, Bob divides the key according to , where and Bob sends to Alice;
Post processing: Alice chooses two hash function , and calculates . Alice passes , , , and to Bob. Bob corrects the errors and outputs . Alice outputs and .
4.3. Security Proof of 1-2 ROT
According to the definition, we will prove the security of our proposed ROT protocol from the perspective of correctness, security for Alice, and security for Bob successively.
For correctness, if both parties are honest, Bob can calculate according to c, and , and Alice can also get . The focus is mainly on security for Alice and Bob.
Lemma 6 (Security for Alice). In 1-2 ROT protocol, n represents the number of bits transmitted during the protocol. represents the state generated in the ideal protocol operation which consists of dishonest Bob and the variable of n transmitted bits. represents the joint state generated in the actual protocol operation which consists of dishonest Bob and the variable of n transmitted bits. If Alice is honest, and the trace distance between these two states with . Then we fix , we can get:
1) ,
2) .
Proof. With uncertainty relation theorem, we have:
where
M is the outcome that announced by Charlie. According to entropy sampling theorem:
and in our protocol, according to Lemma 3, we have the storage rate
, then:
By using privacy amplification theorem:
and let the above formula be less than
, we can get:
☐
Lemma 7 (Security for Bob). In 1-2 ROT protocol, n represents the number of bits transmitted during the protocol. represents the state generated in the ideal protocol operation which consists of dishonest Alice and commit bit c. represents the joint state generated in the actual protocol operation which consists of dishonest Alice and commit bit c that is uniformly distributed on . If Bob is honest, and the trace distance between these two states , and there exits , then the conditional entropy with respect to c and , we have:
(1)
Proof. According to the definition of ROT protocol, if Alice is dishonest, then her purpose is to get
c chosen by Bob. In our protocol, Bob’s information leakage to Alice are
and
. We have:
As
, we can argue that:
and with the uncertainty relation theorem:
we can get:
when
,
, so we can get
. Namely, exists
,
. ☐
6. Conclusions
In this paper, we proposed several two-party cryptographic protocols based on joint measurement and error estimation, including WSE, 1-2 ROT, and other protocols, and demonstrated their security. Compared with the protocol mentioned in [
2,
17,
28,
29], our protocols discarded the assumption that the attacker’s storage device was defective, but instead employed a combination of joint measurement and error estimation to limit the quantum storage of the attacker. Our protocols had no assumptions, were more secure, and had wider applicability. The two basic two-party cryptographic protocols mentioned in this paper could easily be extended to other two-party encryption protocols, such as 1-2 OT and quantum identification protocols.
We eliminated the assumption that the attack was bounded by the attacker’s technology, and employed the technique of joint measurement and error estimation to improve two basic quantum two-party cryptographic protocols. We demonstrated that our improved protocols offered stronger security and is applicable to many specific quantum two-party cryptographic protocols such as BC and PID.
Inspired by [
30,
31], we learned that quantum coherence plays an important role in quantum key distribution and quantum random number generation, and this might also be used to improve our work. Future work will also begin with this aspect.