An Intelligent Data Uploading Selection Mechanism for Offloading Uplink Traffic of Cellular Networks
Abstract
1. Introduction
- Our proposed IDUSM is distributed. It as a background program runs in every participant helping the participant make data uploading decision. It is feasible in large scale scenarios. Meanwhile, the proposed IDUSM realized a trade-off between the offloaded cellular networks traffic and participants’ uploading cost considering the differences among participants’ data plans and probabilities of opportunistic transmissions.
- The decision of data uploading manner in IDUSM is based on our proposed probability prediction model. The model precisely predicts a participant’s probability of successfully transferring data to a Wi-Fi AP considering direct and indirect opportunistic transmission and time variation of opportunistic contact patterns. It increases the accuracy of data uploading decision.
- The proposed IDUSM considers the waste of participants’ limited resources by the redundant data produced in the Wi-Fi uploading process. It reduces the data redundancy by only allowing participants carrying data to replicate data to participants with higher probability of contacting the Wi-Fi AP.
2. Related Work
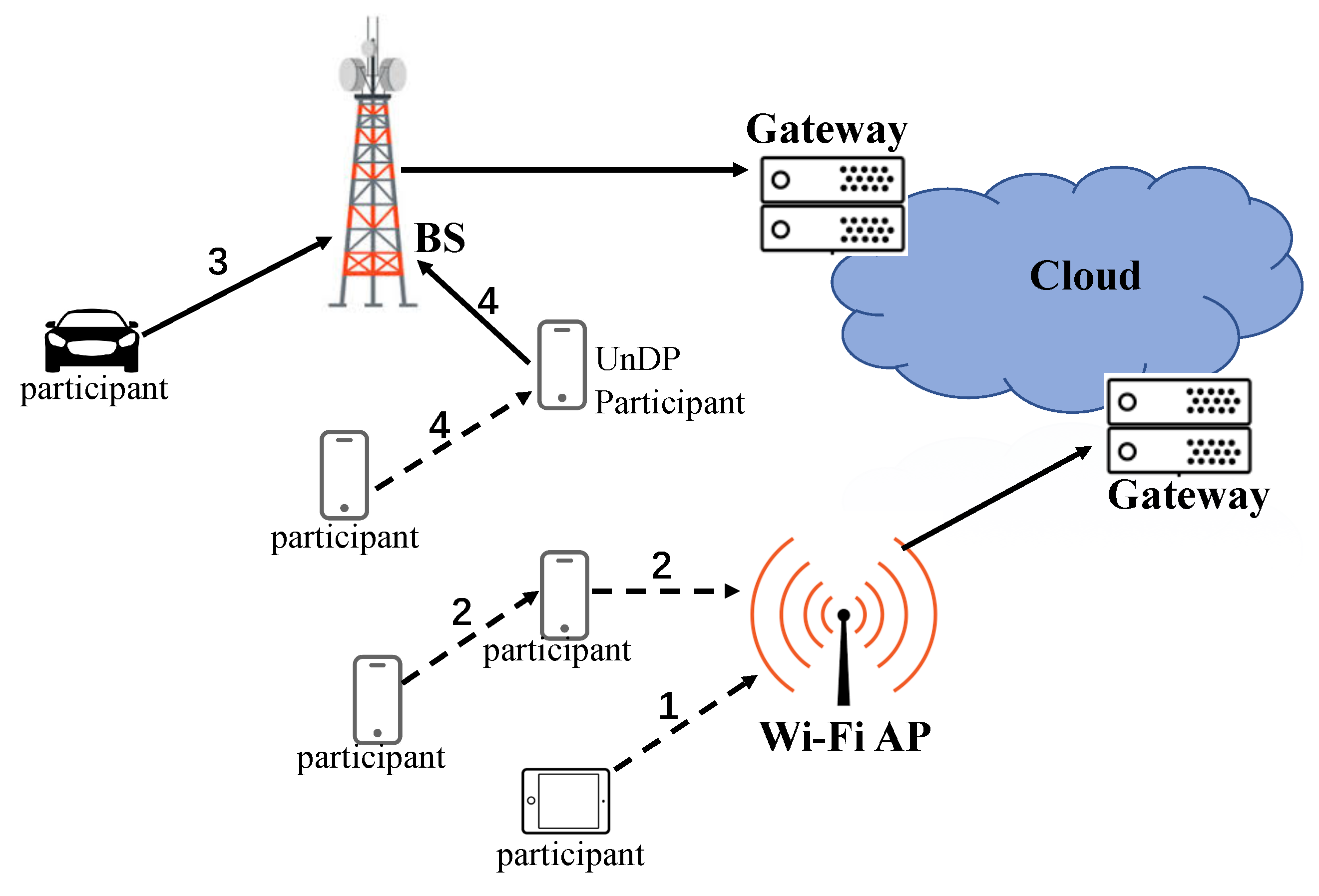
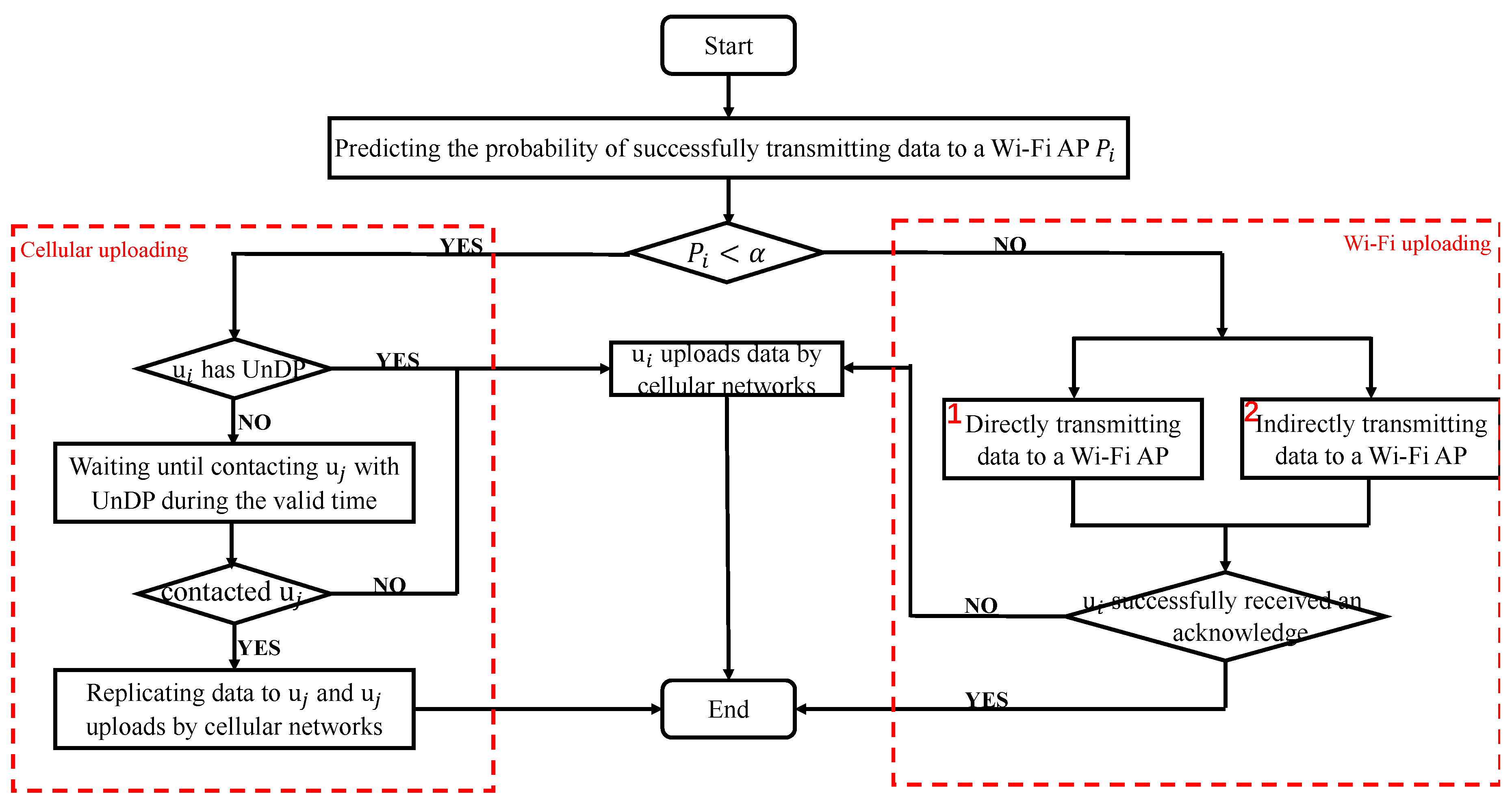
3. The Intelligent Data Uploading Selection Mechanism
4. The Probability of Transmitting Data to a Wi-Fi AP
4.1. The Probability of Directly Contacting a Wi-Fi AP
4.1.1. Spatial Prediction
4.1.2. Temporal Prediction
4.1.3. The Combination of Spatial and Temporal Prediction
| Algorithm 1 Predicting the probability of directly contacting a Wi-Fi Access Point (AP) within a time constraint |
| Input: the starting region , the starting time interval t, the stop time interval . Output: Initialize: 1: OneStepTransition() { 2: if ( contains a Wi-Fi AP) then 3: ; 4: else 5: Getting the staying time intervals d and using (2); 6: ; 7: ifthen 8: for every possible next region do 9: Calculating using (1); 10: Calculating using (3); 11: ; 12: ; 13: Calling OneStepTransition() 14: end for 15: end if 16: end if } 17: return ; |
4.2. The Probability of Indirectly Contacting a Wi-Fi AP
| Algorithm 2 Predicting the probability of indirectly contacting a Wi-Fi AP within a time constraint |
| Input: the starting region , the starting time interval t, the stop time interval . Output: Initialize: 1: for every historical records of do 2: if (&) then 3: Calculating using (4); 4: Calling Algorithm 1() to get ; 5: ; 6: end if 7: end for 8: return ; |
5. Performance Evaluation
5.1. Environment Setup
5.2. Performance of the Proposed IDUSM
5.3. Performance Comparison with Other Mechanisms
5.3.1. Impact of the Density of Wi-Fi APs
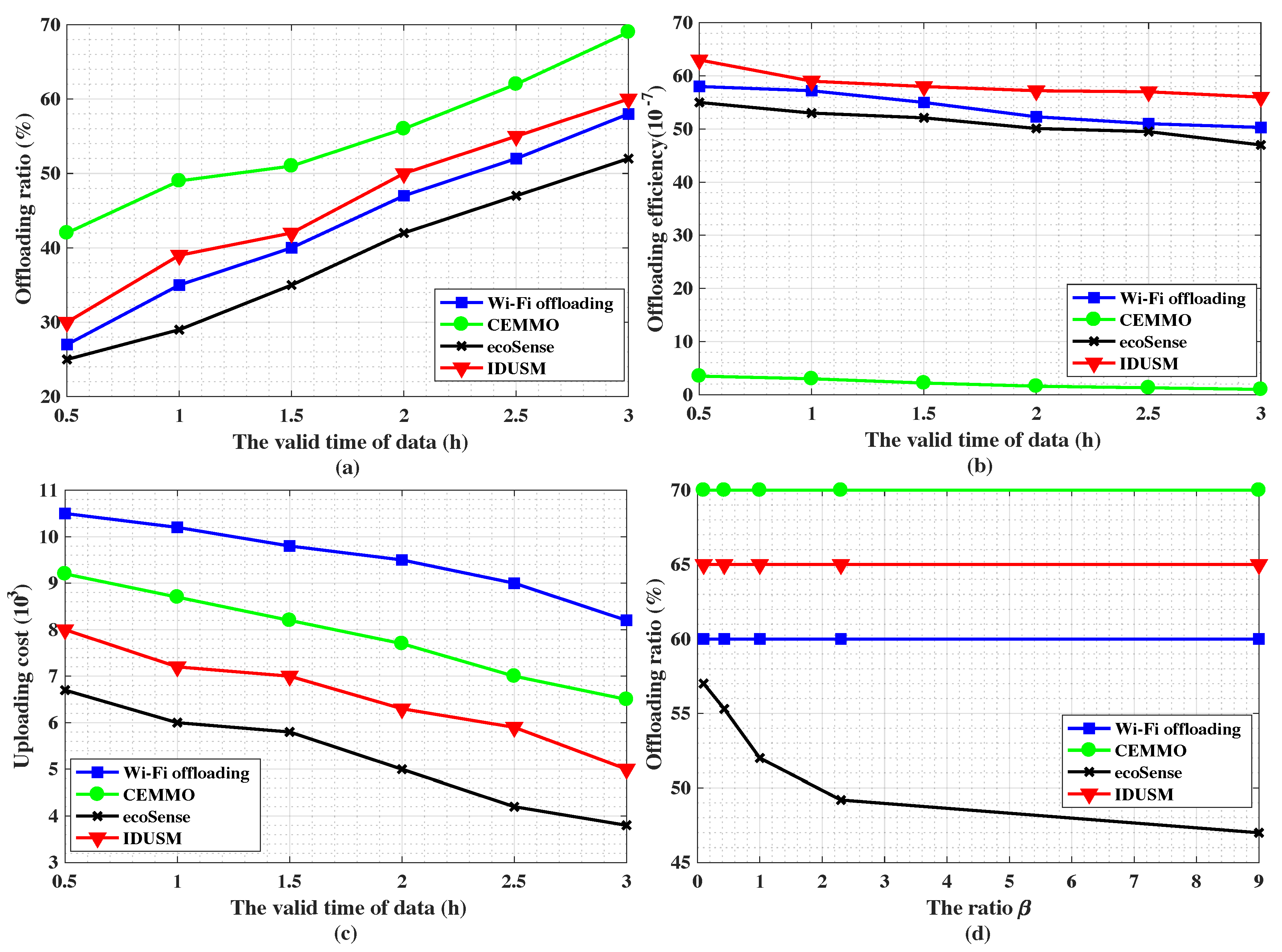
5.3.2. Impact of the Valid Time of Data
5.3.3. Impact of the Ratio
6. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Guo, B.; Yu, Z.; Zhou, X.; Zhang, D. From participatory sensing to mobile crowd sensing. In Proceedings of the 2014 IEEE International Conference on Pervasive Computing and Communication Workshops (PERCOM WORKSHOPS), Budapest, Hungary, 24–28 March 2014; pp. 593–598. [Google Scholar]
- Capponi, A.; Fiandrino, C.; Kantarci, B.; Foschini, L.; Kliazovich, D.; Bouvry, P. A survey on mobile crowdsensing systems: Challenges, solutions, and opportunities. IEEE Commun. Surv. Tutor. 2019, 21, 2419–2465. [Google Scholar] [CrossRef]
- Sun, G.; Song, L.; Yu, H.; Du, X.; Guizani, M. A Two-tier Collection and Processing Scheme for Fog-based Mobile Crowd Sensing in the Internet of Vehicles. IEEE Int. Things J. 2020. [Google Scholar] [CrossRef]
- Zhou, P.; Zheng, Y.; Li, M. How long to wait? Predicting bus arrival time with mobile phone based participatory sensing. In Proceedings of the 10th International Conference on Mobile Systems, Applications, and Services, Manchester, UK, 22–25 June 2012; pp. 379–392. [Google Scholar]
- Kong, X.; Xia, F.; Li, J.; Hou, M.; Li, M.; Xiang, Y. A shared bus profiling scheme for smart cities based on heterogeneous mobile crowdsourced data. IEEE Trans. Ind. Inform. 2019, 16, 1436–1444. [Google Scholar] [CrossRef]
- Cisco, C. Global mobile data traffic forecast update, 2017–2022. White Paper, 28 February 2020. [Google Scholar]
- Romanous, B.; Bitar, N.; Imran, A.; Refai, H. Network densification: Challenges and opportunities in enabling 5G. In Proceedings of the 2015 IEEE 20th International Workshop on Computer Aided Modelling and Design of Communication Links and Networks (CAMAD), Guildford, UK, 7–9 September 2015; pp. 129–134. [Google Scholar]
- Bader, A.; ElSawy, H.; Gharbieh, M.; Alouini, M.S.; Adinoyi, A.; Alshaalan, F. First mile challenges for large-scale IoT. IEEE Commun. Mag. 2017, 55, 138–144. [Google Scholar] [CrossRef]
- Gharbieh, M.; Bader, A.; ElSawy, H.; Yang, H.C.; Alouini, M.S.; Adinoyi, A. Self-organized scheduling request for uplink 5G networks: A D2D clustering approach. IEEE Trans. Commun. 2018, 67, 1197–1209. [Google Scholar] [CrossRef]
- Akpakwu, G.A.; Silva, B.J.; Hancke, G.P.; Abu-Mahfouz, A.M. A survey on 5G networks for the Internet of Things: Communication technologies and challenges. IEEE Access 2017, 6, 3619–3647. [Google Scholar] [CrossRef]
- Al-Falahy, N.; Alani, O.Y. Technologies for 5G networks: Challenges and opportunities. IT Prof. 2017, 19, 12–20. [Google Scholar] [CrossRef]
- Feng, B.; Zhang, C.; Liu, J.; Fang, Y. D2D communications-assisted traffic offloading in integrated cellular-WiFi networks. IEEE Int. Things J. 2019, 6, 8670–8680. [Google Scholar] [CrossRef]
- Wang, L.; Zhang, D.; Yan, Z.; Xiong, H.; Xie, B. effSense: A novel mobile crowd-sensing framework for energy-efficient and data uploading. IEEE Trans. Syst. Man Cybern. Syst. 2015, 45, 1549–1563. [Google Scholar] [CrossRef]
- Yu, H.; Cheung, M.H.; Huang, L.; Huang, J. Predictive delay-aware network selection in data offloading. In Proceedings of the 2014 IEEE Global Communications Conference, Austin, TX, USA, 8–12 December 2014; pp. 1376–1381. [Google Scholar]
- Xu, D.; Li, Y.; Chen, X.; Li, J.; Hui, P.; Chen, S.; Crowcroft, J. A survey of opportunistic offloading. IEEE Commun. Surv. Tutor. 2018, 20, 2198–2236. [Google Scholar] [CrossRef]
- Zhou, H.; Wang, H.; Zhu, C.; Leung, V.C. Freshness-Aware Initial Seed Selection for Traffic Offloading Through Opportunistic Mobile Networks (WCNC). In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018; pp. 1–6. [Google Scholar]
- Barua, B.; Khan, Z.; Han, Z.; Abouzeid, A.A.; Latva-aho, M. Incentivizing selected devices to perform cooperative content delivery: A carrier aggregation-based approach. IEEE TWC 2016, 15, 5030–5045. [Google Scholar] [CrossRef]
- Rebecchi, F.; de Amorim, M.D.; Conan, V. Should I Seed or Should I Not: On the Remuneration of Seeders in D2D Offloading. In Proceedings of the 2016 IEEE 17th International Symposium on A World of Wireless, Mobile and Multimedia Networks (WoWMoM), Coimbra, Portugal, 21–24 June 2016; pp. 1–9. [Google Scholar]
- Chang, Z.; Gong, J.; Zhou, Z.; Ristaniemi, T.; Niu, Z. Resource Allocation and Data Offloading for Energy Efficiency in Wireless Power Transfer Enabled Collaborative Mobile Clouds. In Proceedings of the 2015 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Hong Kong, China, 26 April–1 May 2015; pp. 336–341. [Google Scholar]
- Wang, W.; Wu, X.; Xie, L.; Lu, S. Joint storage assignment for D2D offloading systems. Comput. Commun. 2016, 83, 45–55. [Google Scholar] [CrossRef]
- Zhou, H.; Chen, X.; He, S.; Zhu, C.; Leung, V.C. Freshness-aware seed selection for offloading cellular traffic through opportunistic mobile networks. IEEE Trans. Wirel. Commun. 2020, 19, 2658–2669. [Google Scholar] [CrossRef]
- Balaji, C.G.; Anu Monisha, A.; Murugan, K. A Novel Hybrid UE Selection Scheme for Efficient Data Offloading Using D2D Communication. Comput. J. 2020, 63, 1513–1523. [Google Scholar]
- Dash, S.K.; Dash, S.; Mishra, J.; Mishra, S. Opportunistic mobile data offloading using machine learning approach. Wirel. Pers. Commun. 2020, 110, 125–139. [Google Scholar] [CrossRef]
- Zhang, Y.; Li, J.; Li, Y.; Xu, D.; Ahmed, M.; Li, Y. Cellular Traffic Offloading via Link Prediction in Opportunistic Networks. IEEE Access 2019, 7, 39244–39252. [Google Scholar] [CrossRef]
- Du, X.; Lin, F. Improving sensor network performance by deploying mobile sensors. In Proceedings of the PCCC 2005 24th IEEE International Performance, Computing, and Communications Conference, Phoenix, Arizona, 7–9 April 2005; pp. 67–71. [Google Scholar]
- Wang, N.; Wu, J. Opportunistic WiFi Offloading in a Vehicular Environment: Waiting Or Downloading Now? In Proceedings of the IEEE INFOCOM 2016—The 35th Annual IEEE International Conference on Computer Communications (INFOCOM), San Francisco, CA, USA, 10–14 April 2016; pp. 1–9. [Google Scholar]
- Wang, N. Optimal Cellular Traffic Offloading Through Opportunistic Mobile Networks by Data Partitioning. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Wang, N.; Wu, J. Optimal Data Partitioning and Forwarding in Opportunistic Mobile Networks. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018; pp. 1–6. [Google Scholar]
- Du, X.; Wu, D. Adaptive cell relay routing protocol for mobile ad hoc networks. IEEE Trans. Veh. Technol. 2006, 55, 278–285. [Google Scholar] [CrossRef]
- Miliotis, V.; Alonso, L.; Verikoukis, C. Weighted proportional fairness and pricing based resource allocation for uplink offloading using IP flow mobility. Ad Hoc Netw. 2016, 49, 17–28. [Google Scholar] [CrossRef]
- He, X.; Liu, M.; Yang, G. Spatiotemporal opportunistic transmission for mobile crowd sensing networks. Pers Ubiquit Comput. 2020, 4, 1–11. [Google Scholar] [CrossRef]
- Jung, Y.; Baek, Y. Multi-hop data forwarding method for crowd sensing networks. Peer-to-Peer Netw. Appl. 2016, 9, 628–639. [Google Scholar] [CrossRef]
- Komnios, I.; Tsapeli, F.; Gorinsky, S. Cost-effective multi-mode offloading with peer-assisted communications. Ad Hoc Netw. 2015, 25, 370–382. [Google Scholar] [CrossRef]
- Wang, L.; Zhang, D.; Xiong, H.; Gibson, J.P.; Chen, C.; Xie, B. ecoSense: Minimize participants’ total 3G data cost in mobile crowdsensing using opportunistic relays. IEEE Trans. Syst. Man Cybern. Syst. 2016, 47, 965–978. [Google Scholar] [CrossRef]
- Gong, W.; Huang, X.; Huang, G.; Zhang, B.; Li, C. Data Offloading for Mobile Crowdsensing in Opportunistic Social Networks. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar]
- Wang, E.; Yang, Y.; Wu, J.; Liu, W.; Wang, X. An efficient prediction-based user recruitment for mobile crowdsensing. IEEE Trans. Mob. Comput. 2017, 17, 16–28. [Google Scholar] [CrossRef]
- Yang, C.; Stoleru, R. CEO: Cost-Aware Energy Efficient Mobile Data Offloading via Opportunistic Communication. In Proceedings of the 2020 International Conference on Computing, Networking and Communications (ICNC), Big Island, HI, USA, 17–20 February 2020; pp. 548–554. [Google Scholar]
- Cheung, M.H.; Huang, J. DAWN: Delay-aware Wi-Fi offloading and network selection. IEEE J. Sel. Areas Commun. 2015, 33, 1214–1223. [Google Scholar] [CrossRef]
- Kim, S.; Chon, Y.; Lee, S.; Cha, H. Prediction-based personalized offloading of cellular traffic through WiFi networks. In Proceedings of the 2016 IEEE international conference on pervasive computing and communications (PerCom), Sydney, Australia, 14–16 March 2016; pp. 1–9. [Google Scholar]
- Zhou, X.; Ye, T.; Lee, T.T. Designing and Analysis of A Wi-Fi Data Offloading Strategy Catering for the Preference of Mobile Users. arXiv 2020, arXiv:2005.13195. [Google Scholar]
- Phe-Neau, T.; De Amorim, M.D.; Conan, V. The Strength of Vicinity Annexation in Opportunistic Networking. In Proceedings of the 2013 Proceedings IEEE INFOCOM, Turin, Italy, 14–19 April 2013; pp. 3369–3374. [Google Scholar]
- Cheng, N.; Lu, N.; Zhang, N.; Yang, T.; Shen, X.; Mark, J.W. Vehicle-assisted device-to-device data delivery for smart grid. IEEE Trans. Veh. Technol. 2015, 65, 2325–2340. [Google Scholar] [CrossRef]
- Wang, H.; Zeng, S.; Li, Y.; Jin, D. Predictability and prediction of human mobility based on application-collected location data. IEEE Trans. Mob. Comput. 2020. [Google Scholar] [CrossRef]
- Shi, H.; Li, Y.; Cao, H.; Zhou, X.; Zhang, C.; Kostakos, V. Semantics-aware hidden Markov model for human mobility. IEEE Trans. Knowl. Data Eng. 2019. [Google Scholar] [CrossRef]
- Tu, L.; Wang, S.; Zhang, D.; Zhang, F.; He, T. ViFi-MobiScanner: Observe Human Mobility via Vehicular Internet Service. IEEE Trans. Intell. Transp. Syst. 2019. [Google Scholar] [CrossRef]
- Masdari, M. Markov chain-based evaluation of the certificate status validations in hybrid MANETs. J. Netw. Comput. Appl. 2017, 80, 79–89. [Google Scholar] [CrossRef]
- Keränen, A.; Ott, J.; Kärkkäinen, T. The ONE simulator for DTN protocol evaluation. In Proceedings of the 2nd International Conference on Simulation Tools and Techniques, Rome, Italy, 2–6 March 2009; pp. 1–10. [Google Scholar]
- Gao, G.; Xiao, M.; Wu, J.; Han, K.; Huang, L. Deadline-sensitive mobile data offloading via opportunistic communications. In Proceedings of the 13th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), London, UK, 27–30 June 2016; pp. 1–9. [Google Scholar]
- Dimatteo, S.; Hui, P.; Han, B.; Li, V.O. Cellular traffic offloading through WiFi networks. In Proceedings of the 2011 IEEE Eighth International Conference on Mobile Ad-Hoc and Sensor Systems, Valencia, Spain, 17–22 October 2011; pp. 192–201. [Google Scholar]
- Zhang, B.; Wang, L.; Han, Z. Contracts for joint downlink and uplink traffic offloading with asymmetric information. IEEE J. Sel. Areas Commun. 2020, 38, 723–735. [Google Scholar] [CrossRef]
- Xu, D.; Li, Y.; Xia, T.; Li, J.; Tarkoma, S.; Hui, P. Portfolio Optimization in Traffic Offloading: Concept, Model, and Algorithms. IEEE Trans. Mob. Comput. 2019. [Google Scholar] [CrossRef]
- Ning, Z.; Huang, J.; Wang, X.; Rodrigues, J.J.; Guo, L. Mobile edge computing-enabled Internet of vehicles: Toward energy-efficient scheduling. IEEE Netw. 2019, 33, 198–205. [Google Scholar] [CrossRef]
- Zheng, J.; Gao, L.; Wang, H.; Li, X.; Xu, P.; Wang, L.; Jiang, B.; Yang, X. Joint downlink and uplink edge computing offloading in ultra-dense HetNets. Mob. Netw. Appl. 2019, 24, 1452–1460. [Google Scholar] [CrossRef]
- Aloqaily, M.; Al Ridhawi, I.; Salameh, H.B.; Jararweh, Y. Data and service management in densely crowded environments: Challenges, opportunities, and recent developments. IEEE Commun. Mag. 2019, 57, 81–87. [Google Scholar] [CrossRef]
- Berdik, D.; Otoum, S.; Schmidt, N.; Porter, D.; Jararweh, Y. A Survey on Blockchain for Information Systems Management and Security. Inform. Proc. Manag. 2021, 58, 102397. [Google Scholar] [CrossRef]
- Wang, X.; Han, Y.; Wang, C.; Zhao, Q.; Chen, X.; Chen, M. In-edge ai: Intelligentizing mobile edge computing, caching and communication by federated learning. IEEE Netw. 2019, 33, 156–165. [Google Scholar] [CrossRef]
- Sun, W.; Liu, J.; Yue, Y. AI-enhanced offloading in edge computing: When machine learning meets industrial IoT. IEEE Netw. 2019, 33, 68–74. [Google Scholar] [CrossRef]






Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Q.; Fang, J.; Gong, B.; Du, X.; Guizani, M. An Intelligent Data Uploading Selection Mechanism for Offloading Uplink Traffic of Cellular Networks. Sensors 2020, 20, 6287. https://doi.org/10.3390/s20216287
Wang Q, Fang J, Gong B, Du X, Guizani M. An Intelligent Data Uploading Selection Mechanism for Offloading Uplink Traffic of Cellular Networks. Sensors. 2020; 20(21):6287. https://doi.org/10.3390/s20216287
Chicago/Turabian StyleWang, Qian, Juan Fang, Bei Gong, Xiaojiang Du, and Mohsen Guizani. 2020. "An Intelligent Data Uploading Selection Mechanism for Offloading Uplink Traffic of Cellular Networks" Sensors 20, no. 21: 6287. https://doi.org/10.3390/s20216287
APA StyleWang, Q., Fang, J., Gong, B., Du, X., & Guizani, M. (2020). An Intelligent Data Uploading Selection Mechanism for Offloading Uplink Traffic of Cellular Networks. Sensors, 20(21), 6287. https://doi.org/10.3390/s20216287






