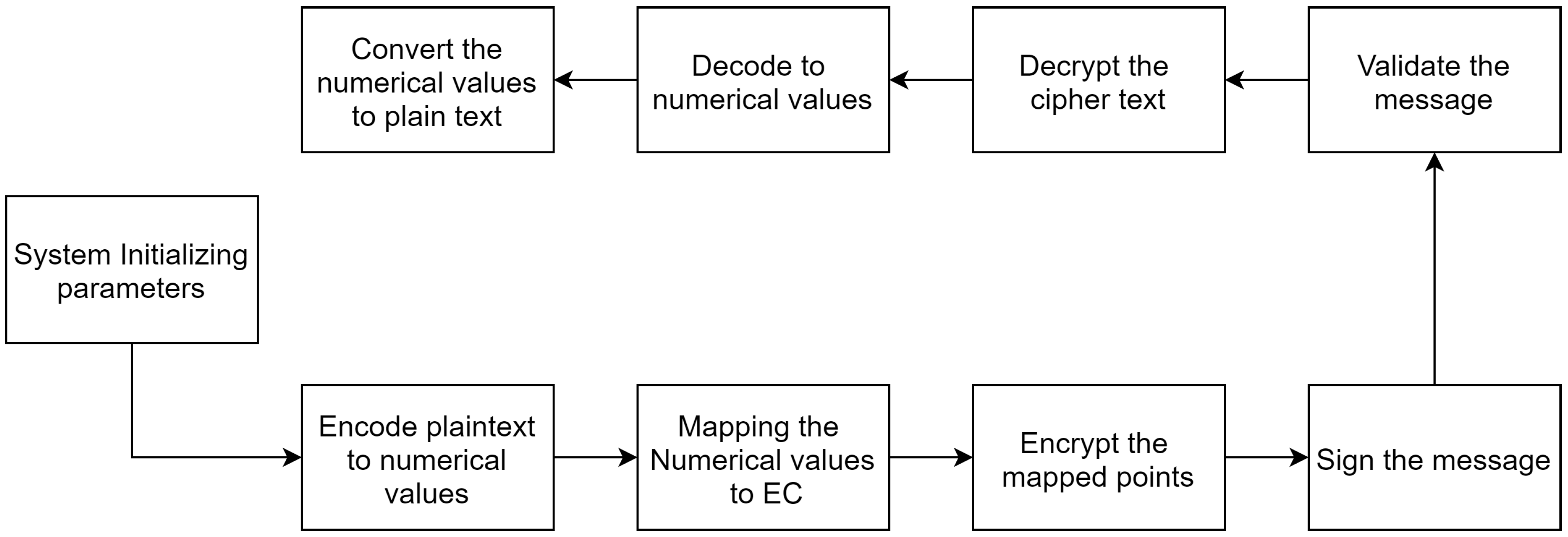
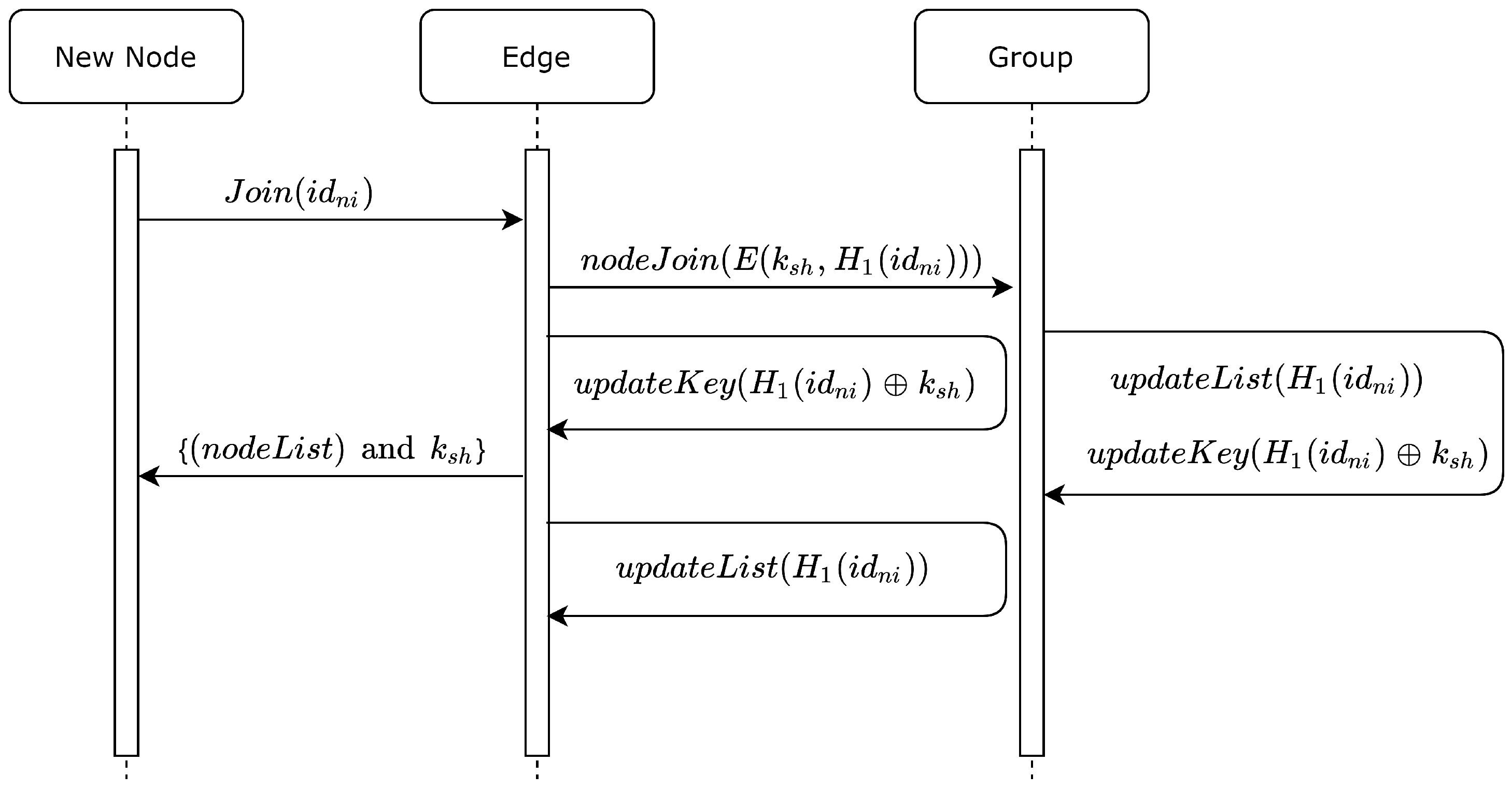
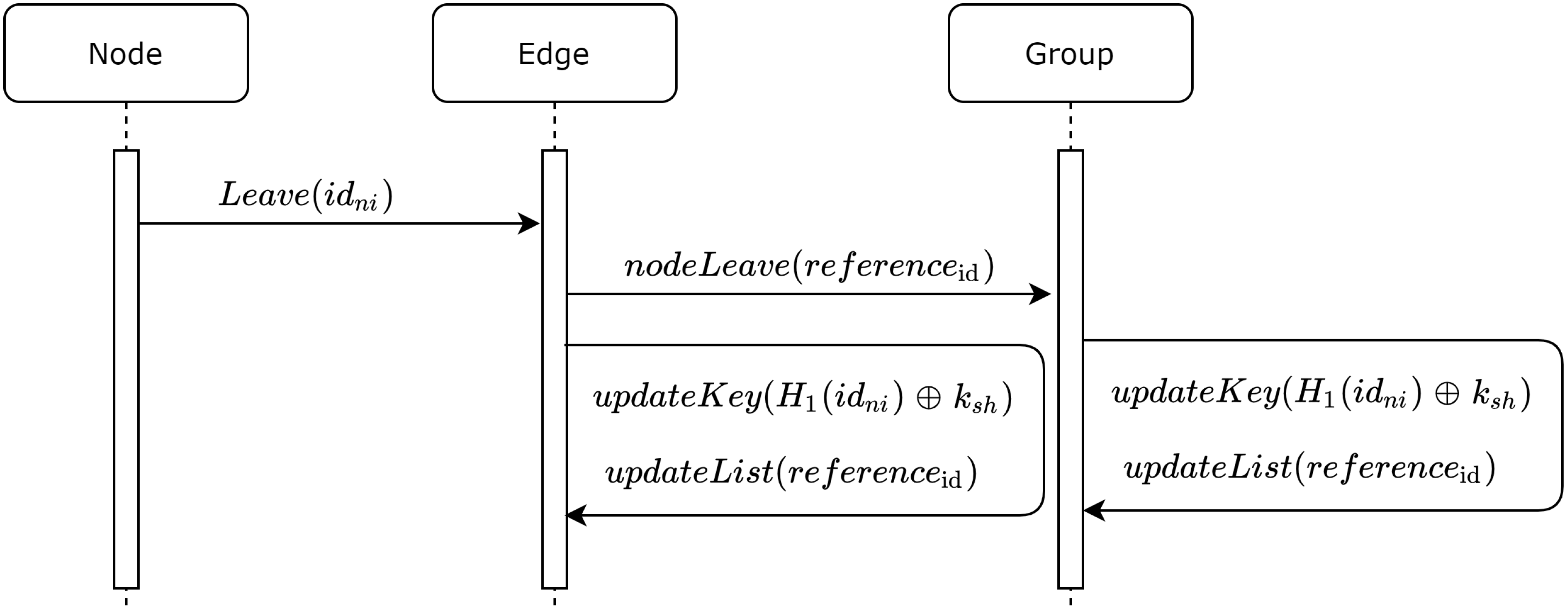
2. Related Works
Elliptic curve cryptography (ECC) is frequently used to reduce the computational overhead caused by the limited capabilities of devices in constrained environments. Many schemes use ECC to secure communications between two parties by safeguarding the shared key exchange process. In particular, the elliptic curve integrated encryption scheme (ECIES) first employed the asymmetric approach by generating the shared key between two parties using ECC, after which the plain text was encrypted using the symmetric approach under the AES scheme [
44,
45,
46,
47]. On the other hand, many of these schemes failed to provide detail on how ECC was used to secure the plain text and/or how they were encoded into numerical values for use in ECC’s mapping phase.
Various proposed systems have enhanced key elements of the encryption process in ECC, but gaps have been identified in the literature. For instance, schemes proposed in [
48,
49,
50] employ ECC without providing sufficient detail about how the plain text was encoded and mapped onto an elliptic curve. Therefore, enhancing these schemes tended to focus on performance rather than security. Similarly, [
51,
52,
53] provided efficient algorithms for scalar multiplication in ECC that speed up the multiplication process. However, many schemes focus on securing ECC, and they offer more insights into the approach used to encode plain text and map it onto an elliptic curve. The rest of this literature review focuses on these schemes and, in particular, on the question of how the plain texts are encoded into numerical values, in addition, how these values are mapped onto the elliptic curve.
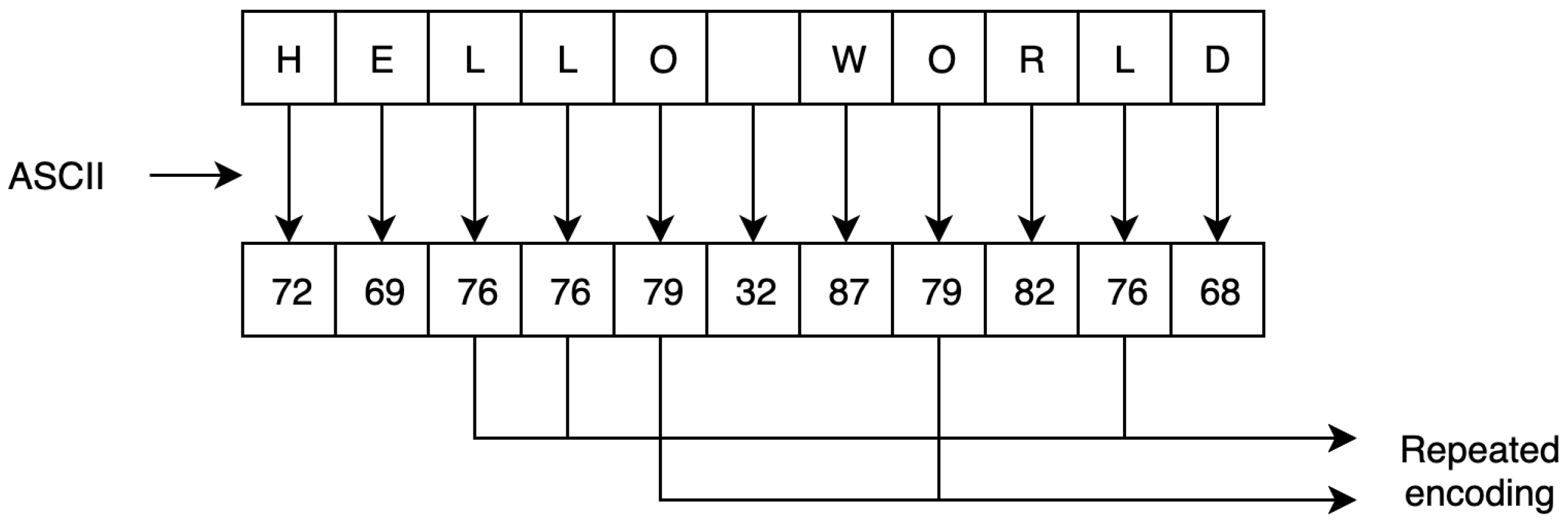
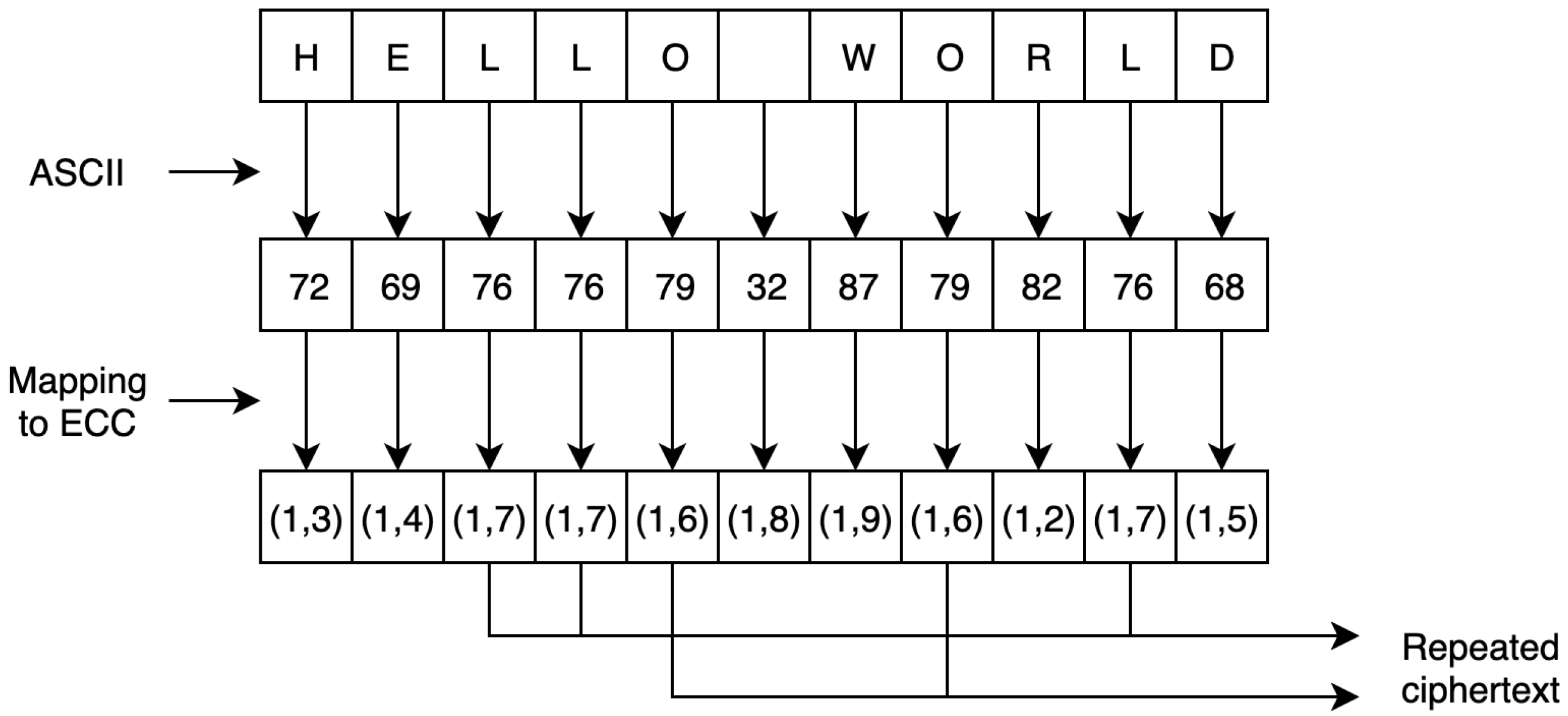
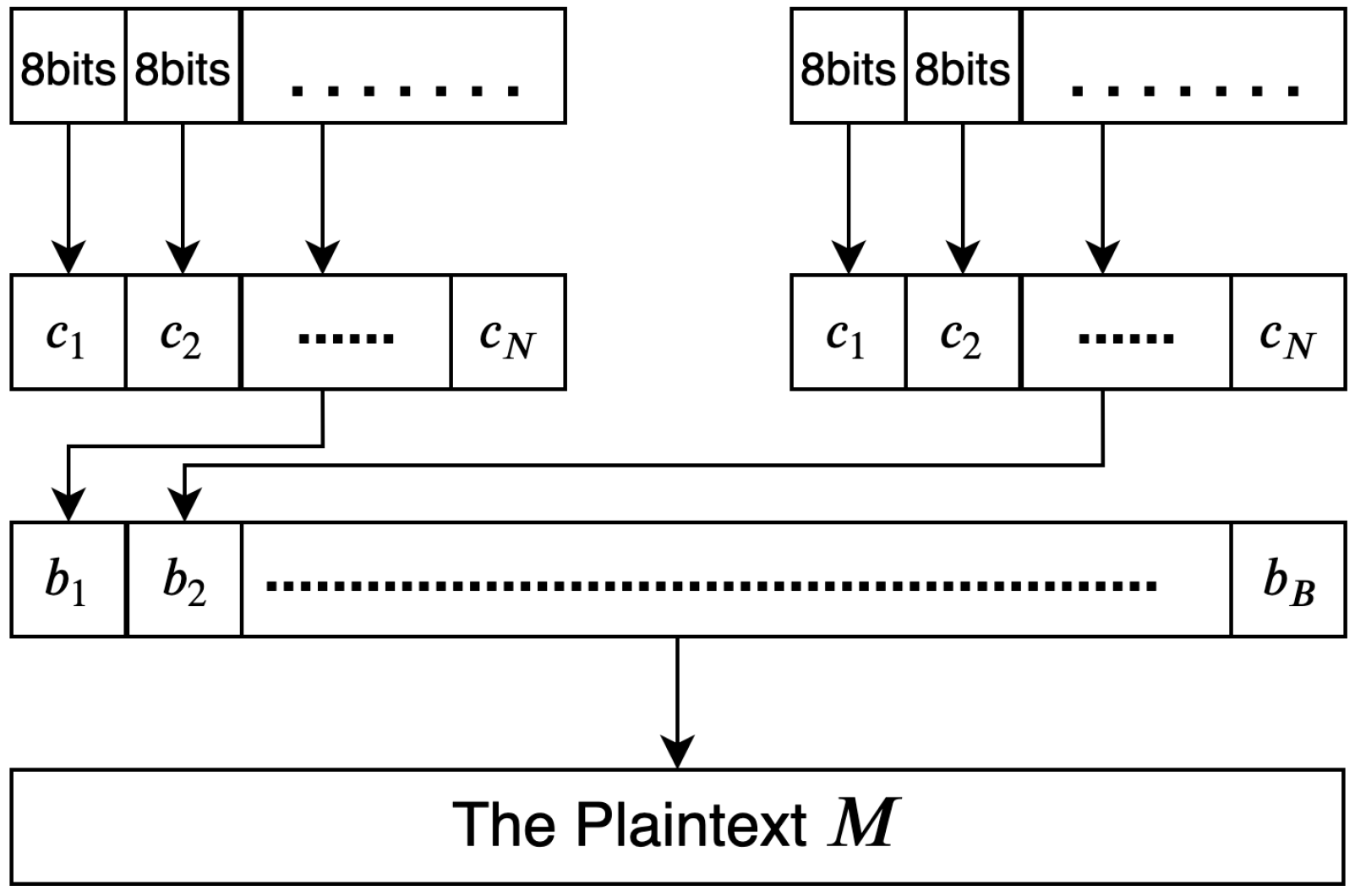
Several schemes proposed ways to secure plain text by encoding the characters to numerical values, thus giving them the ability to be mapped onto the elliptic curve. Many approaches use these schemes to encode the plain text. For instance, using the ASCII table, each character is converted into its decimal number [
26,
54,
55,
56]. In this case, the plain text “Hello” would be encoded to become “72” “101” “108” “108” “111”. These values are then mapped directly onto the elliptic curve as cipher text. However, this approach falls under the chosen plain text attack (CPA). This is because the attacker has the power to decrypt the chosen cipher text (in this case, a commonly used scheme). For this reason, other schemes manipulate the ASCII table by multiplying it by a secure number that is agreed on by both parties [
57].
Critically, the issue of sharing the secure number is similar to the challenge of agreeing on the sharing of a secure key between the two parties. Such a scheme could also fall under the CPA and CCA. Similarly, other schemes are based on different encoding approaches that rely on matrix-based methods to conceal the matching table [
58]. Specifically, these schemes use secret mapping tables that are unknown to anyone except the recipient, and which are used to encode and decode the plain text in a secure manner. While this may be true, there are two weakness associated with this approach: first, the dilemma of how to secure the delivery of the matrix table to the recipient in a secure way, thereby preventing CPA; and second, it is known that if the matrix-table is assumed to be securely delivered, then the cipher text falls under the CCA. This is because the same encrypted characters are repeated for the same plain characters in each encryption process.
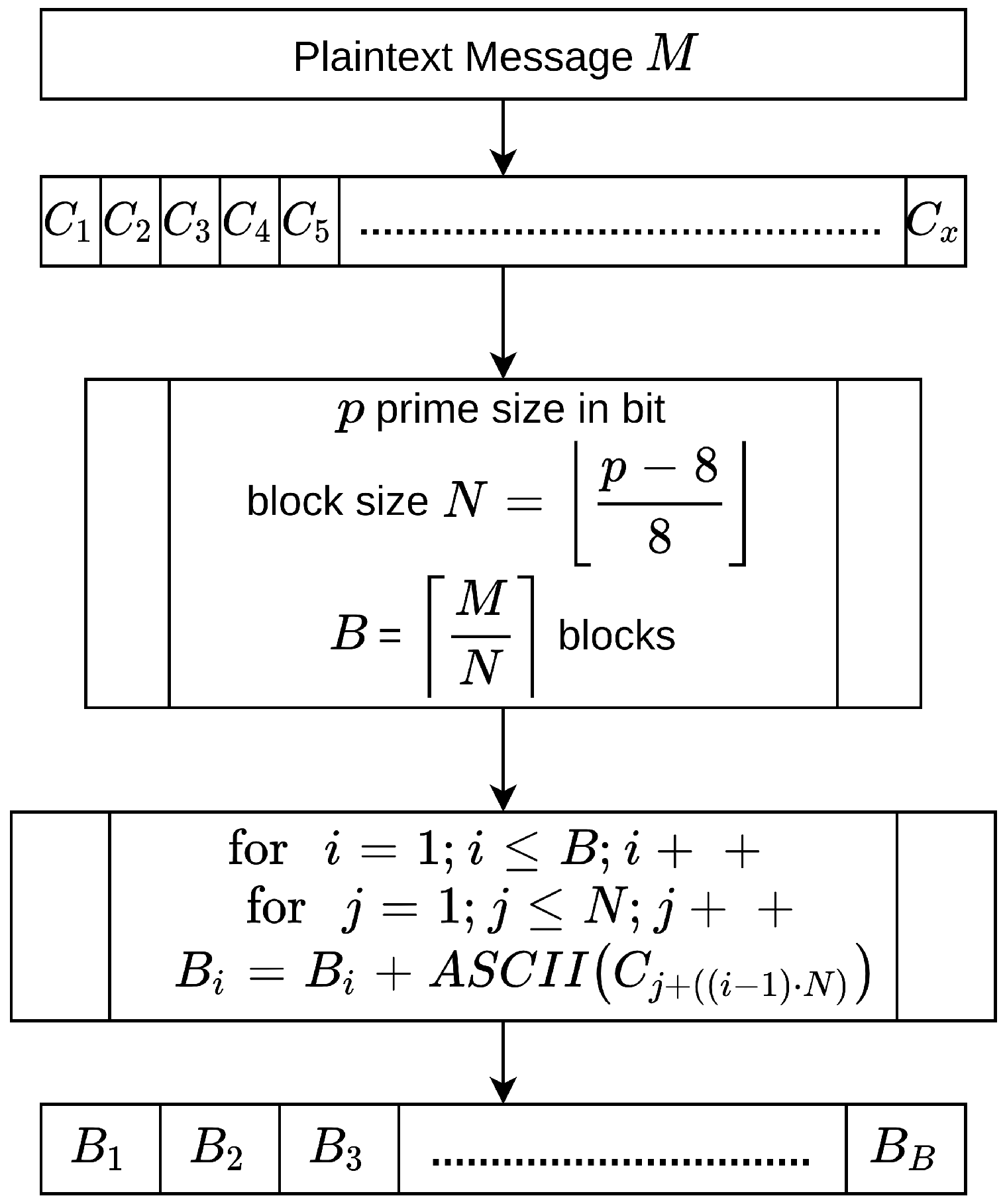
The third approach to overcome flaws in ECC involves Block Chaining operations. The first step is to divide the plain text into a set of fixed-size blocks. In turn, the first block of the plain text is XORed with an initial vector
[
59]. Following this, the result of the first XORed value is used for the second XOR operation with a second block, and the process is repeated for all plain text blocks. This is a good approach, but it is vulnerable to CPA and CCA when the plain text is divided into a set of blocks and all blocks are same (e.g., the plain text is a repeated character). As a result, the second XORing process results in the value of the
as following
. This is because
. Therefore, the result of the XORing operation becomes
, where
. Additionally, this scheme lacks AE property, which increases vulnerability to cipher text tampering attacks and nonrepudiation issues.
Barman et al. [
60] proposed an encryption method to secure IoT communications informed by DNA-based ECC. For each set of characters in the plain text, a DNA genome sequence is mapped to it. There are many genome sequences publicly available, and so randomizing the selection of genome sequences is part of the encryption process for the plain text. Furthermore, the decryption process should use the same DNA genome sequences. Therefore, both parties, the sender and the recipient, must use the same sequences before encrypting and decrypting the plain text. For this reason, the DNA genome sequences should be securely used only by the sender and recipient. If an attacker discovers the sequence, the scheme will be vulnerable to encryption attacks such as CPA. Additionally, even if the sequence is delivered securely, the cipher text will be the same for each repeated plain text encryption process. Resultantly, the scheme is also vulnerable to other encryption attacks, including CCA.
Duarah et al. [
61] introduced Securing IoT Using Machine Learning and ECC. In their scheme, the authors first classified the data set to enhance the transmitted data, where the accurate data were transmitted only to reduce computation efforts. If the data were clean, then they were moved into a second stage, namely encryption via ECC. However, if the data is malicious then it is discarded to save the encryption computation efforts. In the encryption phase, the authors wrote the key generation algorithms that use the ECC scalar multiplication operation
s.t.
P is a point in the elliptic curve, and
d is the private random integer. In their encryption algorithm, the authors defined how the shared key is constructed in order to encrypt the plain text by the addition operation between the plain text and the shared key. Although the scheme produced a new strategy for performance enhancement in the IoT environment by limiting data transmission only to clean data, the security analysis indicates that it is vulnerable to CPA when the same data are encrypted and sent using the same scheme.
Joglekar et al. [
62] proposed Lightweight ECC for Data Integrity and User Authentication in Smart Transportation IoT System. In their scheme, the authors use One Time Password (OTP) to exchange the shared key securely to prevent the man in the middle attack (MITM). The 4-digit OTP is encrypted using ECC and transmitted to the recipient to complete the registration process. The shared key between the two parties is constructed as follows:
, where
are private keys for Sender
A and Recipient
B, respectively. Similarly,
and
are the public keys for Sender
A and Recipient
B. Using OTP to prevent the MITM is a good approach, but the authors neglected to state whether there is an assumption about the 4-digit OTP. It is relevant that the brute force attack needs
possible choices to break the OTP, which can be completed in several minutes. Furthermore, the authors did not state how to encrypt the OTP or how to map it onto an elliptic curve.
Finally, Das & Giri [
55] proposed two encoding algorithms, which generate sets of numerical values via the sum of weight
n with base
b . The first encoding algorithm is used when the value of the base
b is a dynamic integer. In this case, the highest accepted value is
(i.e., the highest value of ASCII table). In addition,
n is the size of the prime field, where the authors suggest the use of a 192-bit key. Resultantly, the set of groups that can be combined based on their method is
. The base
b can be reduced below
, which increases the set of groups more than 11 based on
b. However, the reduction of
b should also contribute to a reduction in ASCII table mapping, and the authors did not provide a safe reduction mechanism. When
b is not dynamic in the second algorithm, the suggested set of the combing group is equal to
. Based on the scheme described by the authors, it is
, and the number of groups based on both algorithms is small. Thus, the computation overhead will increase compared to other schemes. Notably, the encoding and mapping phases did not manipulate the plain text characters after using the ASCII table values, which heightened the scheme’s vulnerability to CPA.
All schemes in the literature are vulnerable to CPA and/or CCA, such that the encryption of the same plain texts always produce same cipher texts. Besides, these schemes use the appending method in the mapping phase which results in increasing the computation overhead. Although, some schemes that use the probability method to map points to EC failed to justify the chosen value of k. Moreover, many of the existing schemes fail to offer secure AE scheme, which means they are vulnerable to tampering attacks. An attacker can modify the transmitted cipher text without detection by the receiver. The cipher text offers confidentiality only; it does not offer integrity by itself. Therefore, to prevent tampering, to maintain the integrity of the cipher text, to ensure that the transmitted message is secured against encryption attacks, and to enhance the mapping phase performance, the proposed scheme ensures the AE property, resists CPA and CCA, and enhances the mapping phase performance.
4. Security Analysis and Performance Evaluation
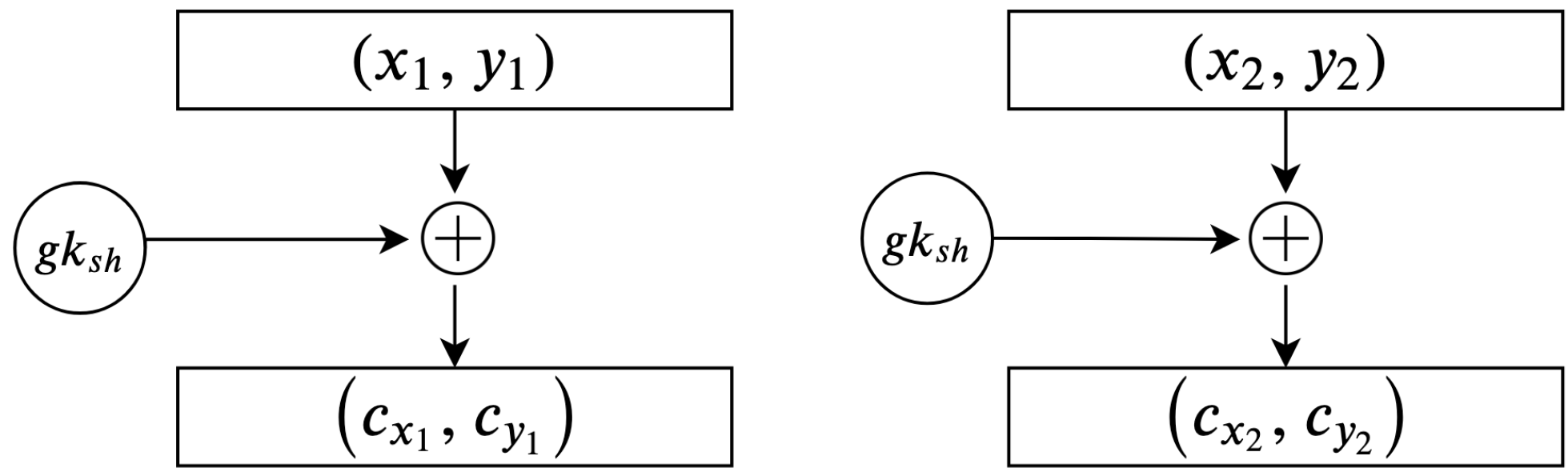
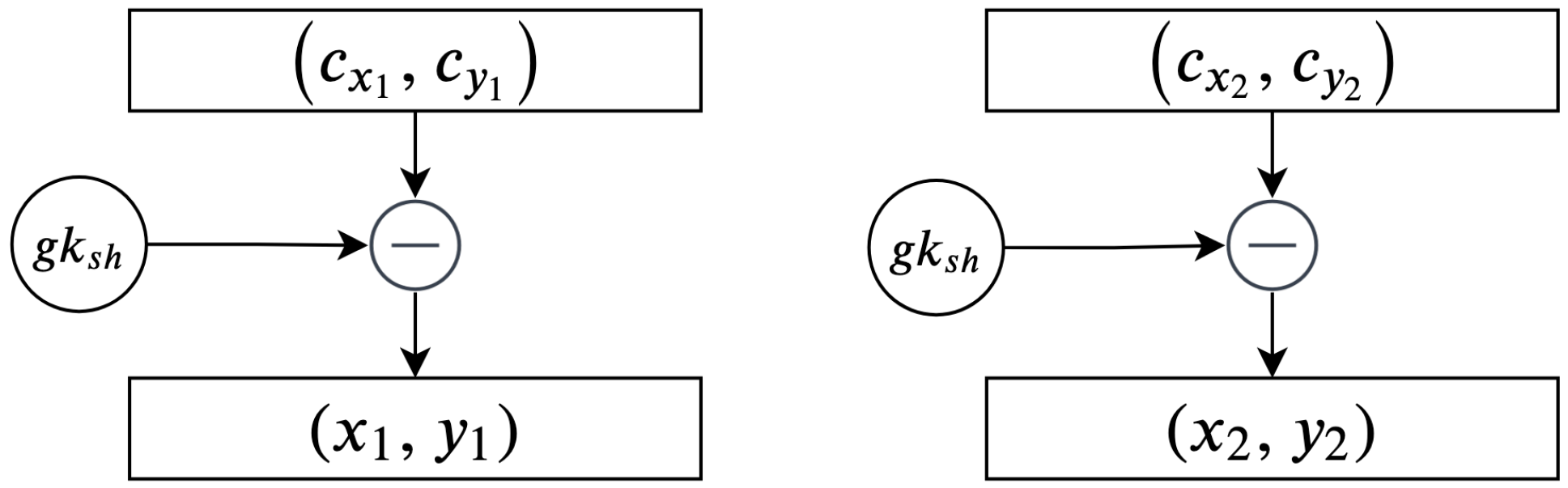
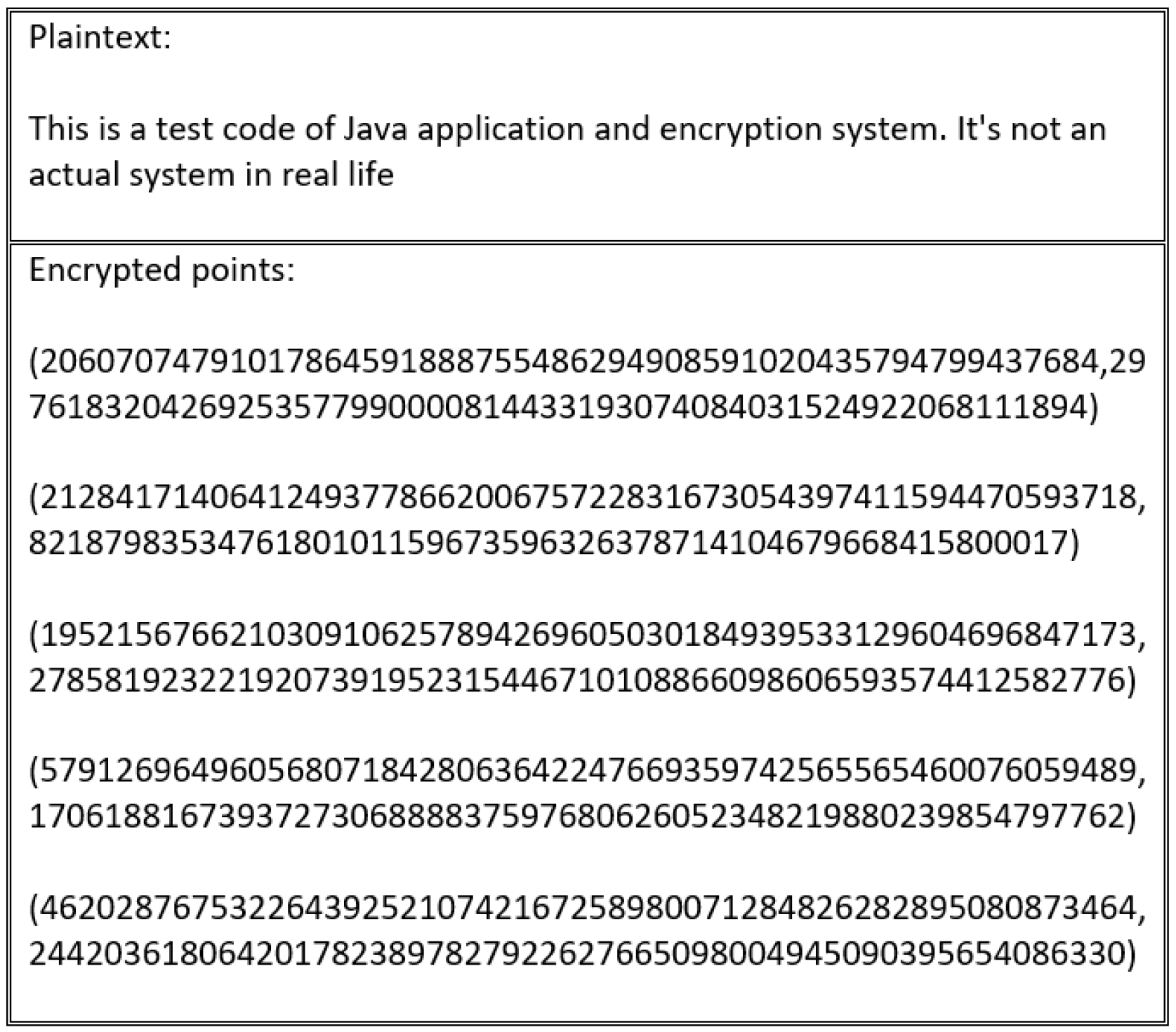
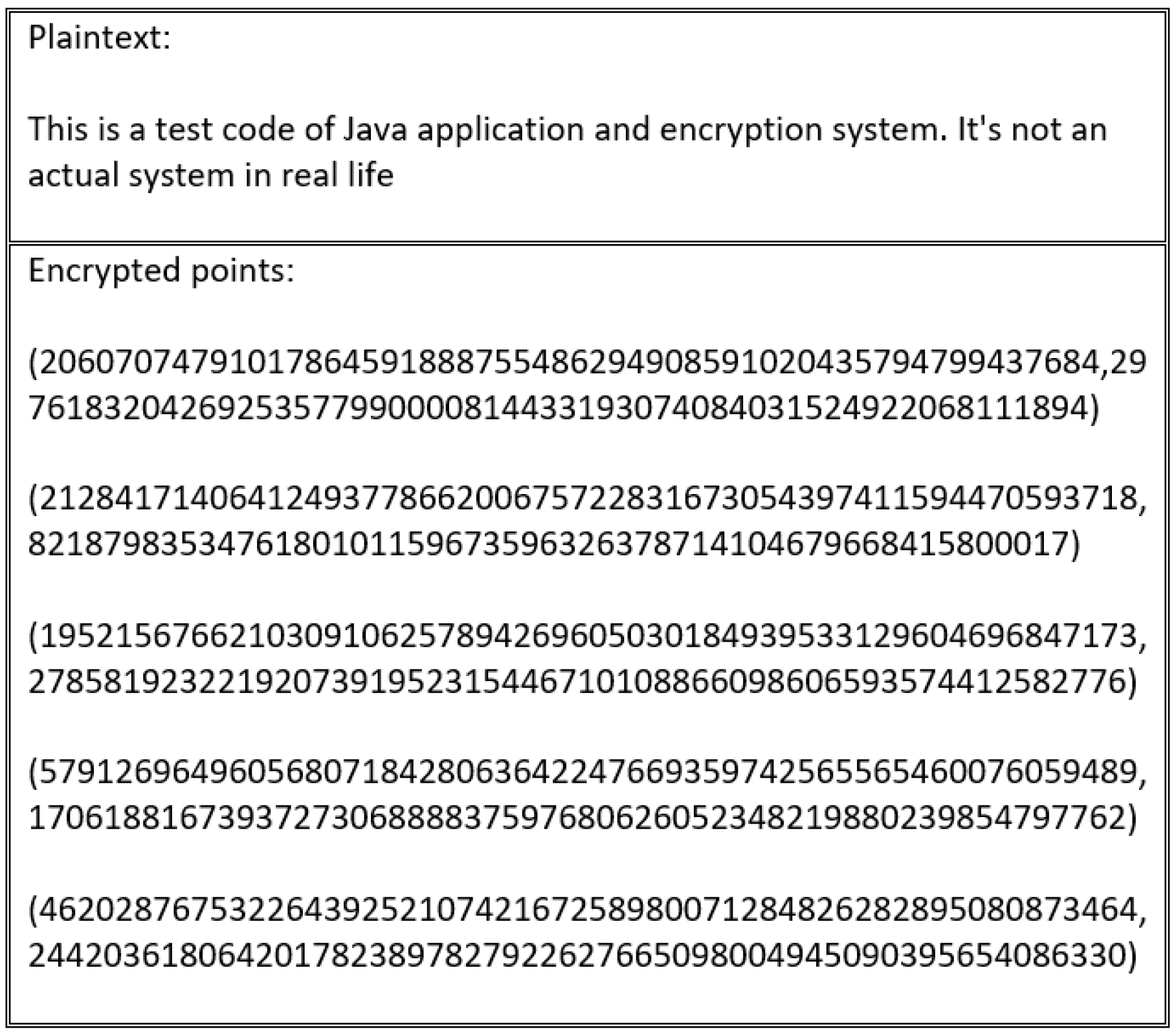
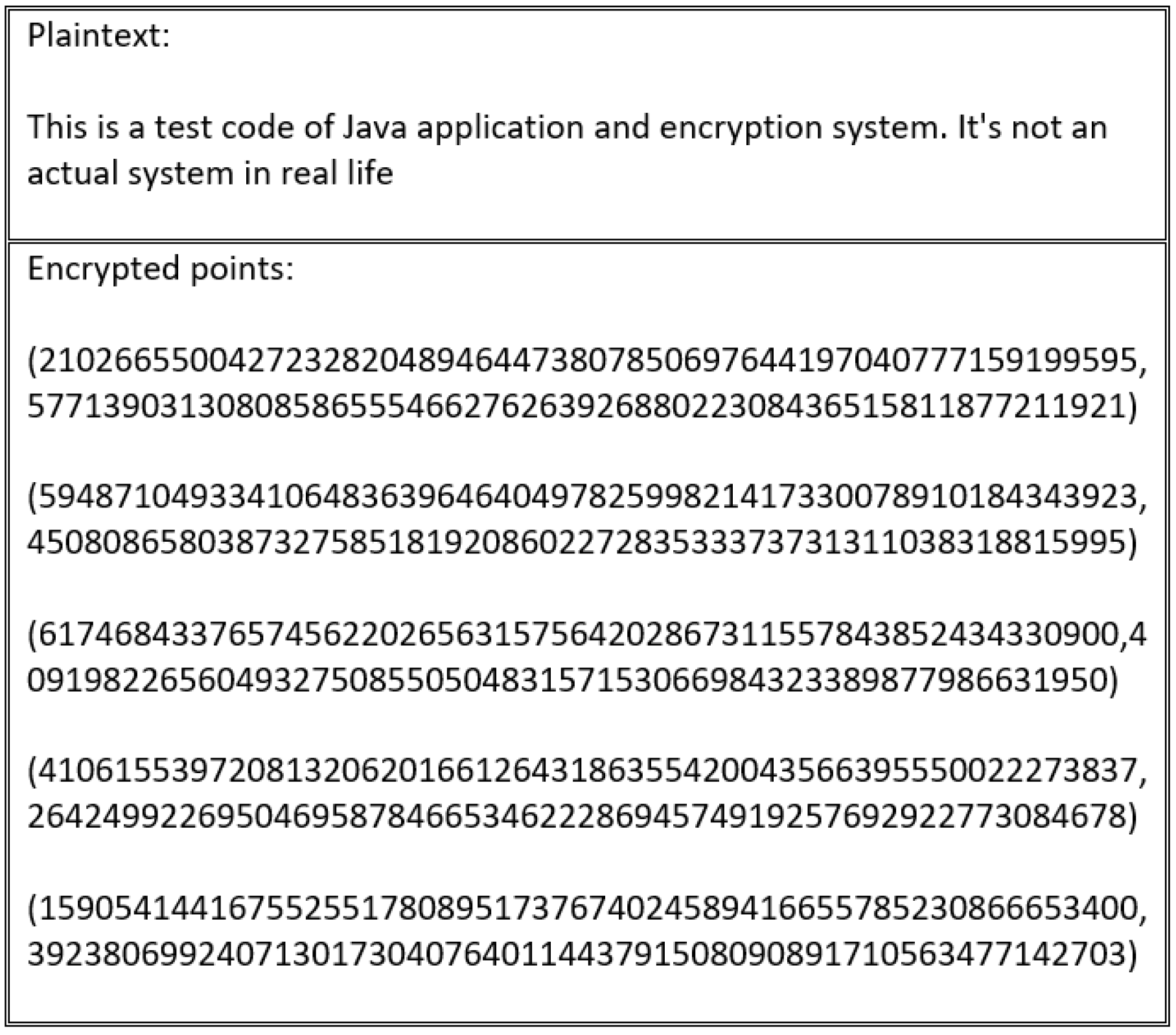
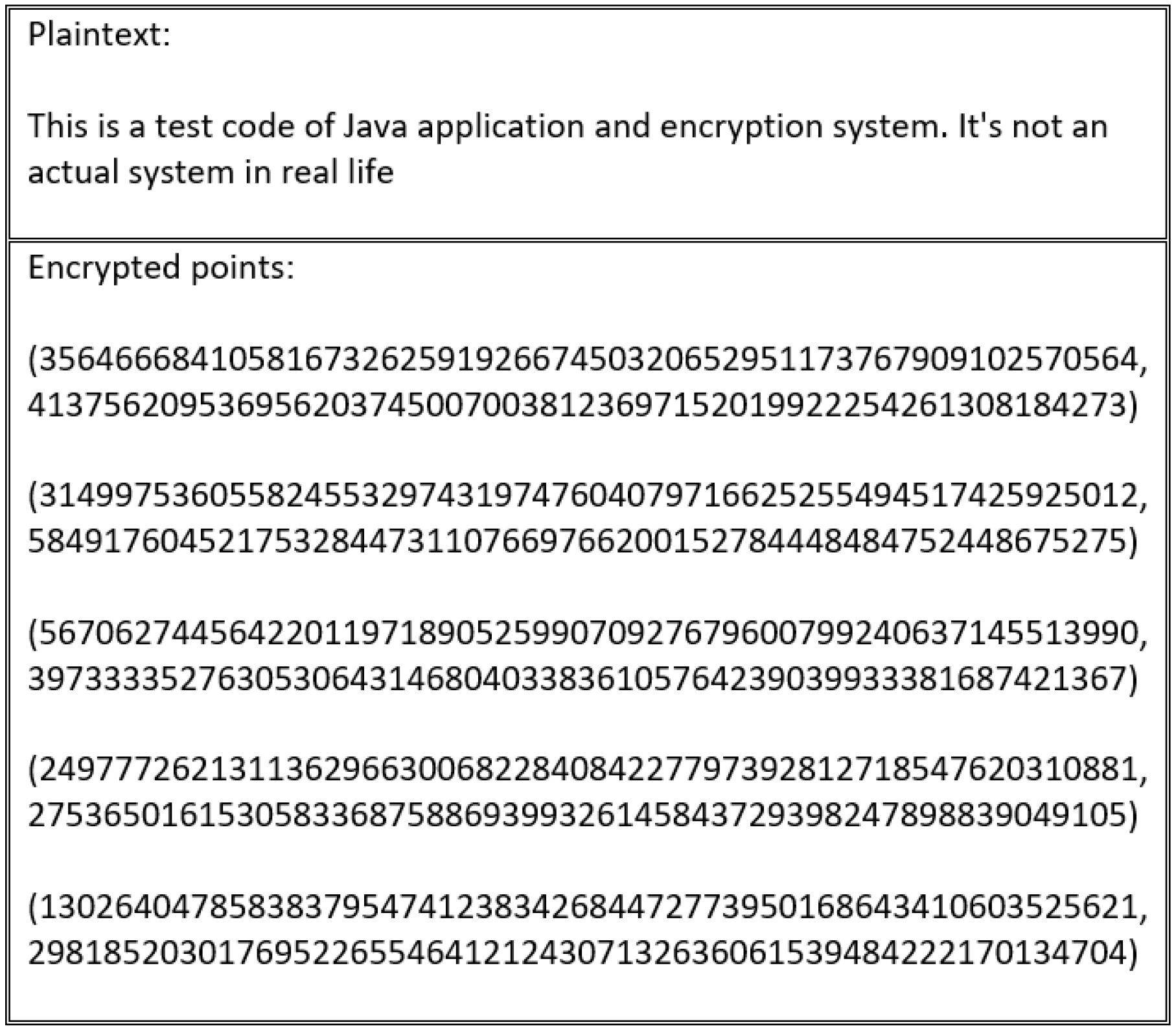
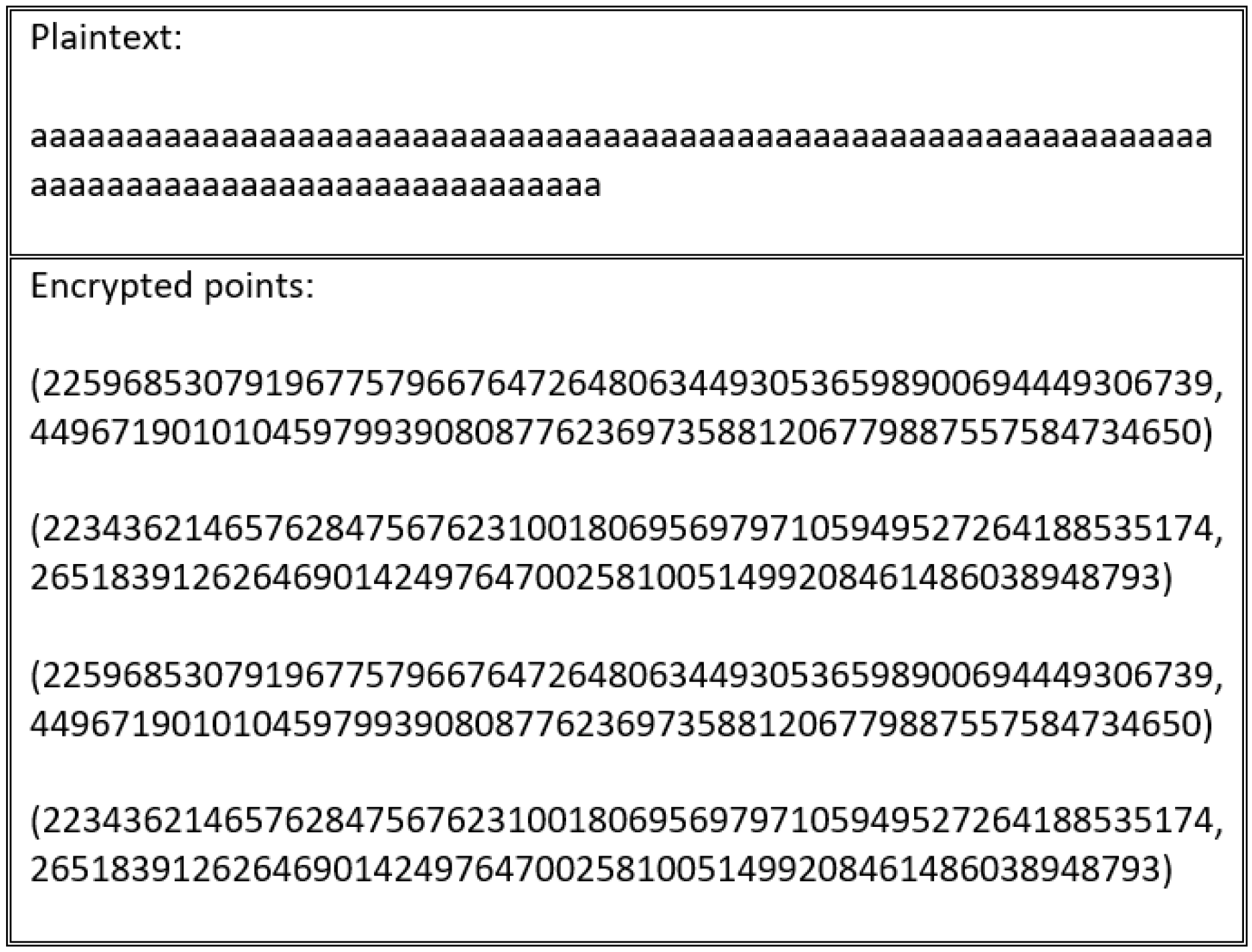
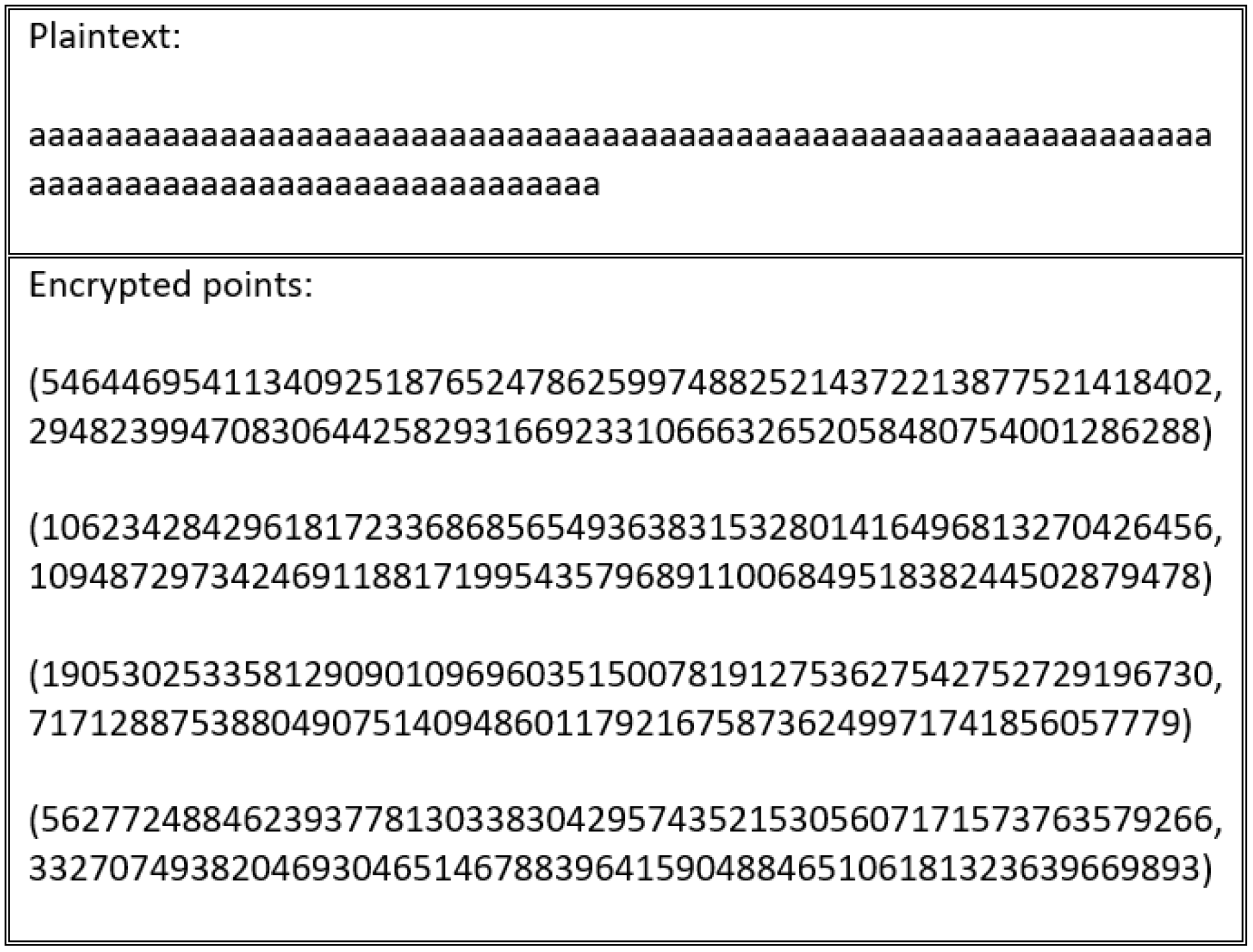
Every scheme discussed in this study’s literature review is vulnerable to an encryption flaw. For instance, the encryption schemes presented in [
55,
60,
61,
62] produce the same cipher text when repeated several times, as outlined in
Figure 16 and
Figure 17.
These schemes suffer from an encryption weakness because they offer the same cipher text if the sender encrypts the plain text using the same encryption key. The main factor that underlies this flaw is that the encryption process in these schemes neglects to consider the importance of manipulating plain text before encrypting and decrypting it. This ensures that a distinct cipher text is produced for every encryption process. Therefore, in the absence of a manipulation step, the adversary can learn from the cipher text, determining whether certain cipher texts are the same or different.
In the scheme proposed by [
59], this flaw is resolved by using XOR with
.
Figure 18 shows that the cipher text outputted from the encryption process is different to the cipher text generated by the process depicted in
Figure 19, which uses the same plain text. However, these schemes are vulnerable to the same flaw, particularly in the special cases outlined in
Figure 20. This flaw occurs when the blocks divided for XOR with
are equal to
. In this case,
,
,
, and so on. Therefore, in the event that all blocks are the same, an attacker can exploit the encryption flaw because XOR with
operations become:
This encryption flaw is illustrated in
Figure 20.
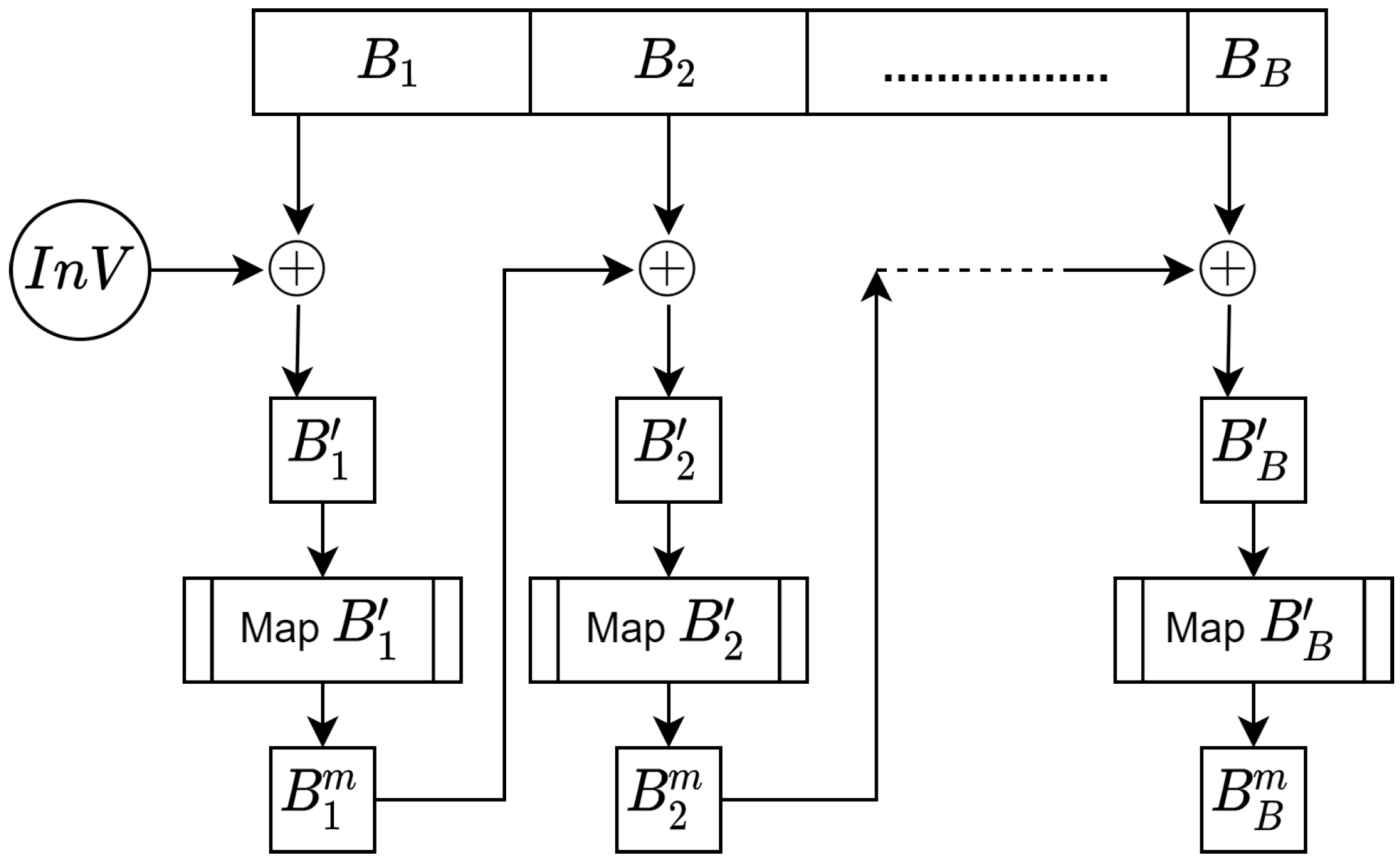
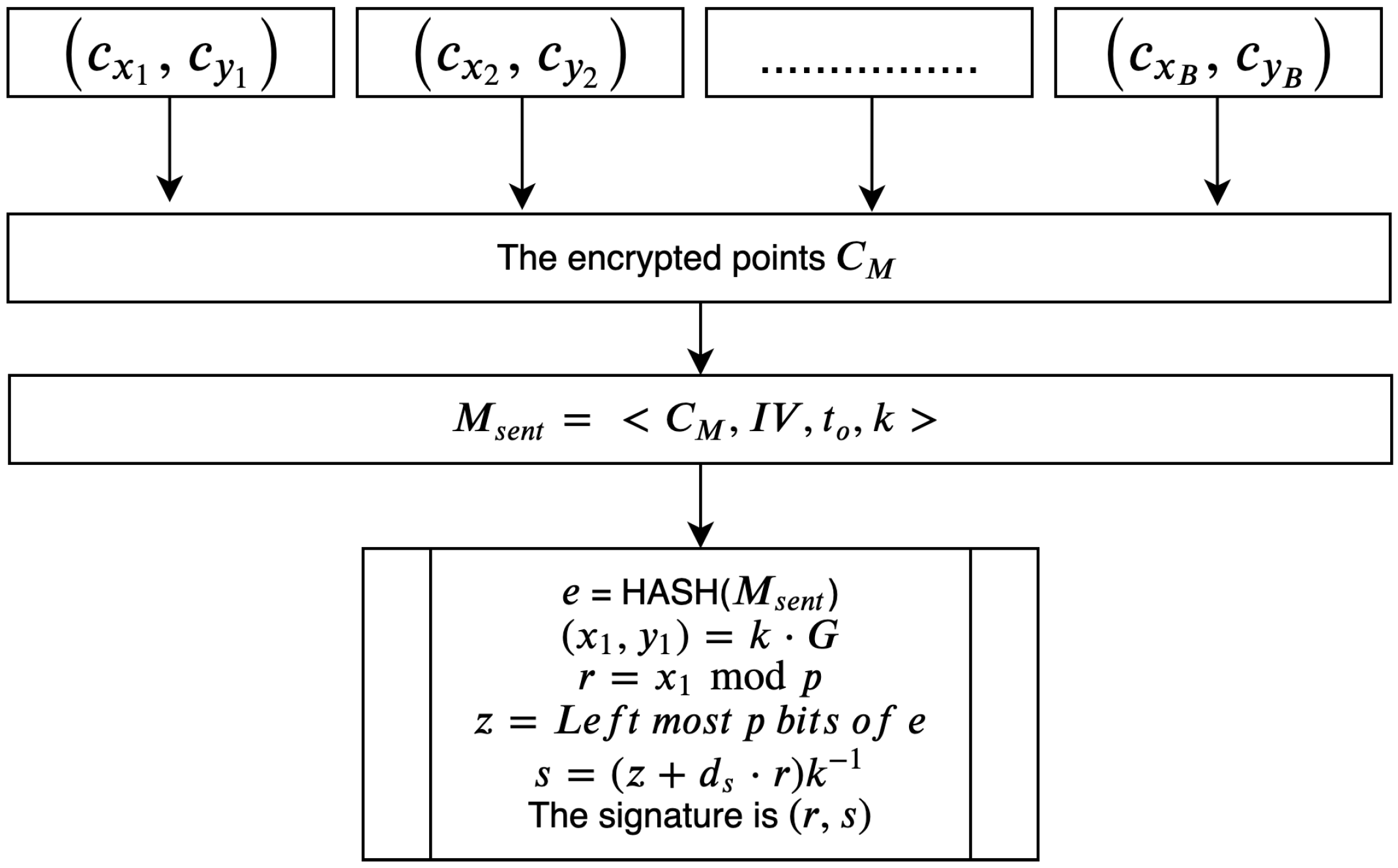
Based on the flaws identified in existing schemes, it is a valuable contribution to the literature to improve the encryption process with CBC. In the proposed scheme, all previous flaws are resolved by using CBC with
derived from mapping points to secure the cipher text in all forms, as described in Algorithm 5. The encryption operation generated by the optimized encryption process is illustrated in
Figure 21.
To evaluate the proposed schemes, security analysis was used with IND-CPA and IND-CCA. In the next subsections, results are given to show that the schemes examined in the literature review are not IND-CPA and IND-CCA. Therefore, it is necessary to prove that the novel scheme proposed in the presented study is both IND-CPA and IND-CCA.
4.1. Indistinguishability under Chosen Plain Text Attack IND-CPA
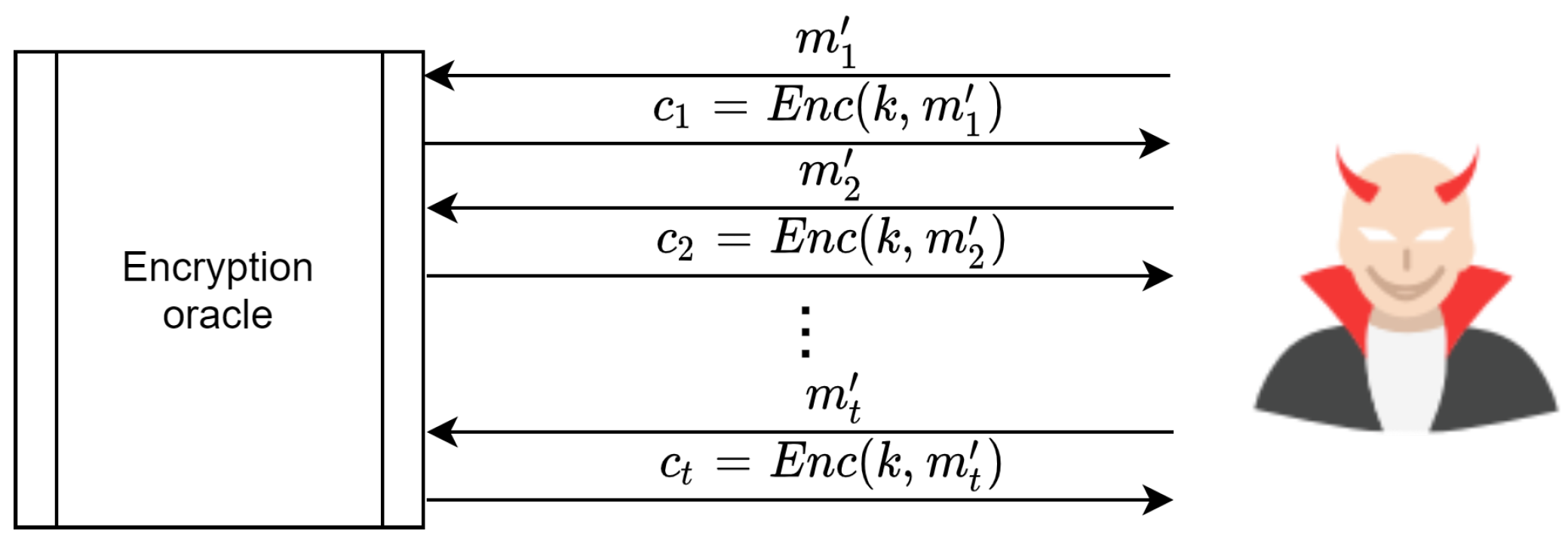
A scheme known as IND-CPA if the adversary has the power to submit as many
,
as desired and also when he or she receives the cipher texts for each message. Then, the adversary must submit two distinct messages,
, to the encryption oracle, receiving
. This is illustrated in
Figure 22. The challenge is that the adversary is required to guess the value of
b with a probability of the following:
Thus, schemes proposed in [
55,
60,
61,
62] are insecure under CPA. An adversary can win a challenging game by submitting two identical messages,
, to the encryption oracle. In turn, the encryption oracle sends the cipher text
, which is the cipher text for
. In an experiment, the adversary sends two messages,
where
, and the encryption oracle responds by encrypting one message and sending one cipher text
. The adversary is then challenged to guess the value of
, and to determine which cipher text belongs to
or
. However, the adversary can win the challenge with
. This is because the encryption oracle in such schemes always encrypts the same messages with the same cipher texts and the same key. Therefore, since the adversary already has
, he or she can determine whether the value of
b is 0 or 1. This is achieved by matching
with
. If
, then
; otherwise,
. This process is illustrated in
Figure 23.
Theorem 1. The proposed scheme is (IND-CPA) such that the probability of the adversary to decrypt the message in the two experiments is negligible, as written in Equation (7). Proof. This theorem is proven by the fact that the proposed scheme uses a different value of for each experiment. Hence, the adversary can submit as many messages as he or she wants to the encryption oracle. The cipher texts generated by the experiment will not be the same, even for the same message. For example, in the second experiment, in was different compared to in . Therefore, when the adversary submits the same message in , he or she will receive the corresponding cipher text in that experiment, which is . However, when the adversary moves to where the encryption oracle challenges the adversary, the two messages submitted by the adversary are not distinguishable. This is because the cipher text from in is different from the cipher text from the same message in . For this reason, the probability that the adversary wins the challenge is
Let be an ECC encryption scheme, and let us define the experiment between the challenger and the attacker A as follows:
Consider the following games:
Game (0)
The attacker A makes a request for encrypting a message , and receives .
Game (1)
The attacker A sends two messages , where is the same as in game 0. The challenger outputs to challenge A to guess the value of b.
Game (3)
The attacker A returns the value of b based on the comparison he or she can perform to distinguish between , which relies on game 0 and 1. However, the probability that A achieves this is 0 because the in game 0 is not the same as in game 1. It is also relevant to note that the XOR operation in both games is undertaken with different . □
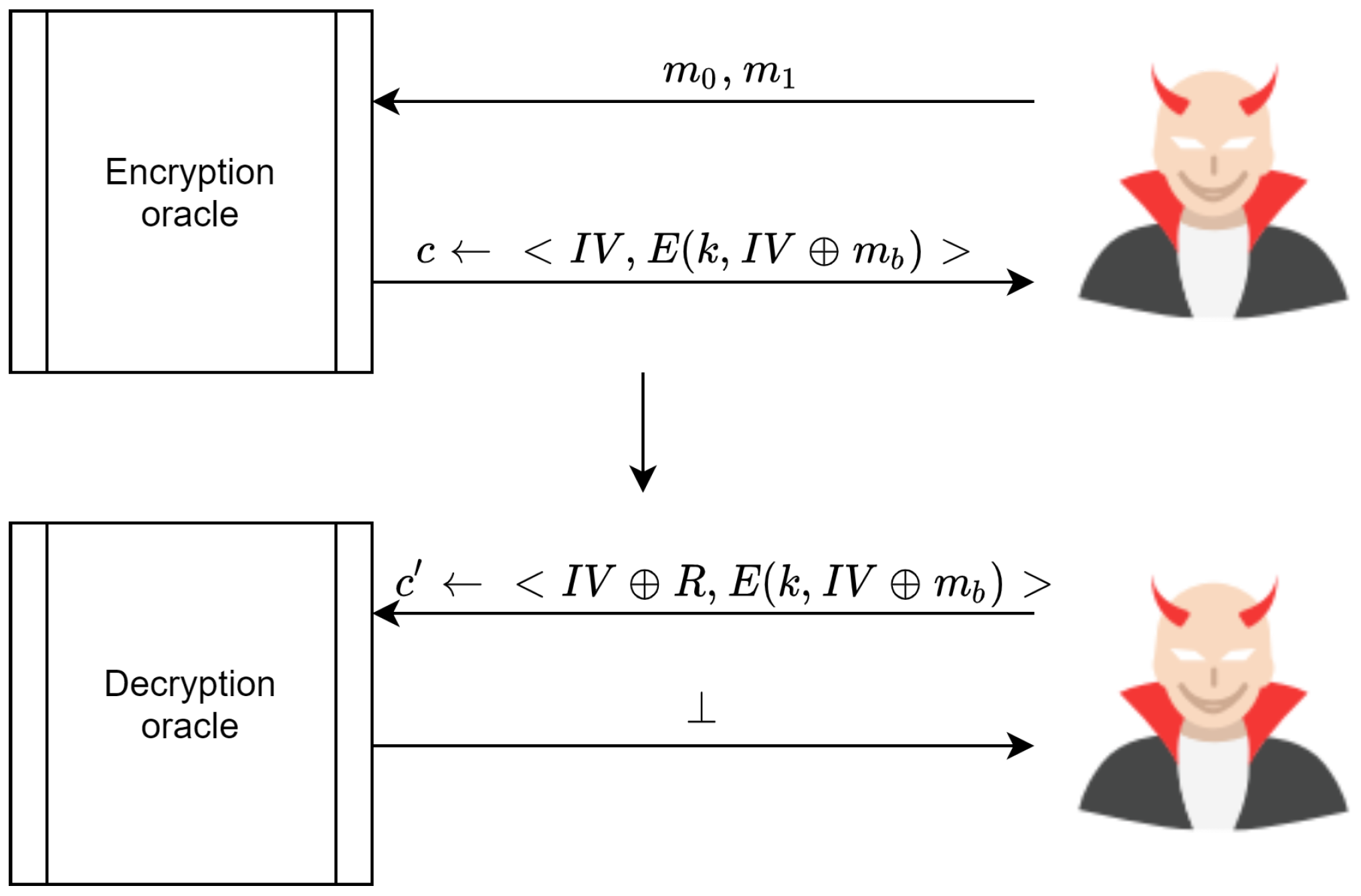
4.2. Indistinguishability under Chosen Ciphertext Attack IND-CCA
An encryption scheme is IND-CCA if the adversary has the ability to submit as cipher texts as he wants
,
and to receive the plain text for that cipher text. In addition, the adversary submits any two distinct messages
and
, where
to the encryption oracle and receives
. This process is depicted in
Figure 24. The challenge is that the adversary is required to guess the value of
b to differentiate between the two experiment’s games, with probability as follows:
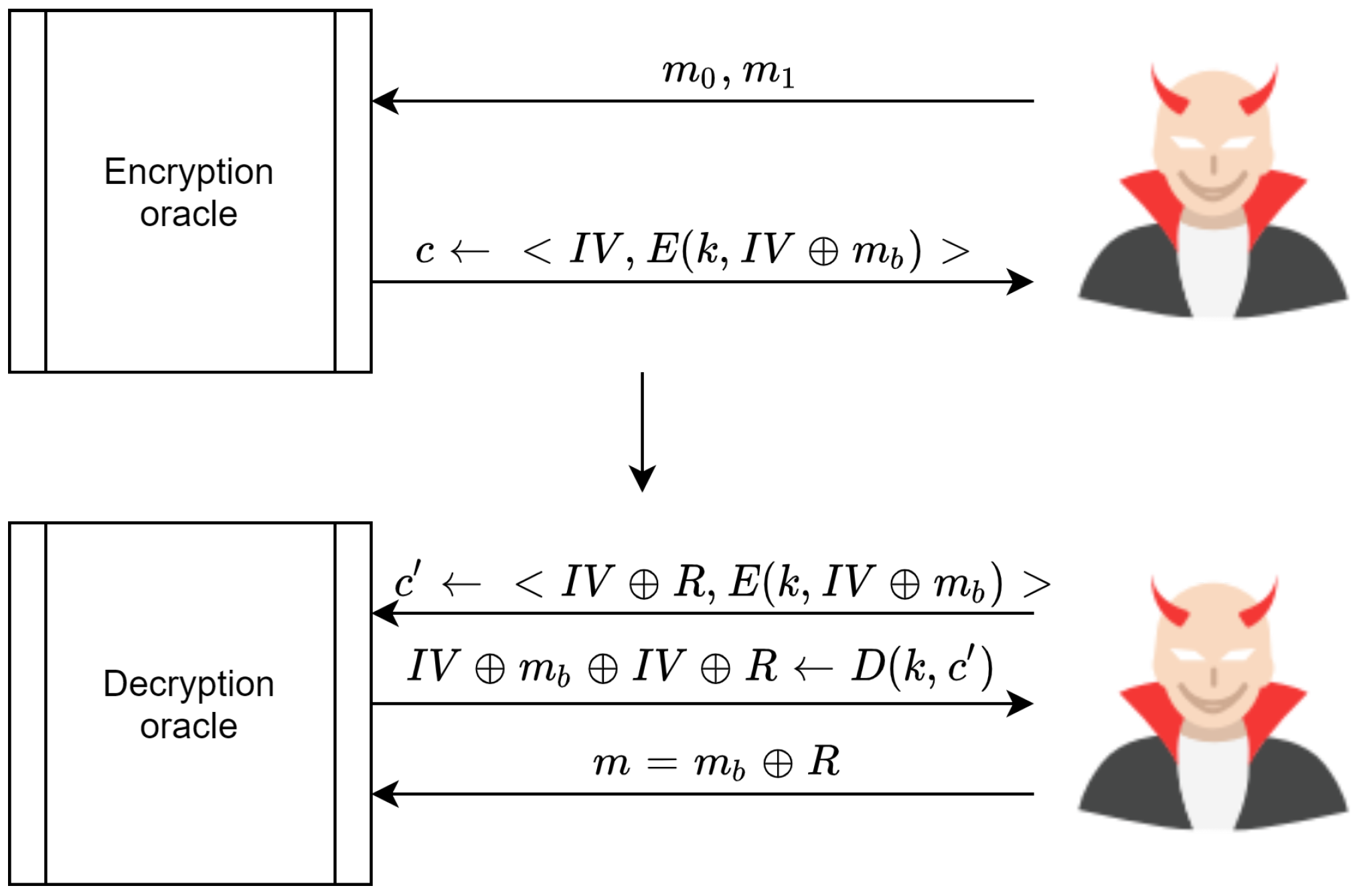
With the above in mind, the scheme proposed in [
59] is not secure under CCA. The adversary can win the challenging game by submitting two messages,
, to the encryption oracle. In turn, the encryption oracle sends the cipher text
, which is the cipher text for either
or
. Subsequently, the adversary modifies
c by XORing
with
R, where
. This produces
where
, which is sent to the decryption oracle for decryption.
The decryption oracle responds by decrypting the cipher text
. This process relies on the modified
. The result is that the decryption process is
. Consequently, an adversary can guess the value of
or
by XORing
, after which it can be compared directly with the received message
. Therefore, the adversary can win the challenge with
. This process is illustrated in
Figure 25.
Theorem 2. The proposed scheme is indistinguishable under IND-CCA such that the probability of the adversary decrypting the message in the two experiments is negligible, as written in Equation (8). Proof. The proof for
starts by noting the adversary’s ability to access both the encryption and decryption oracle. At the same time, the adversary cannot submit
received from the encryption oracle and then submit it for decryption to distinguish the experiment game. However, the adversary can modify the received
and submit it for decryption as the modified
. Thus, the adversary can win the challenging game by XORing
with a random R, thereby guessing
(see
Figure 25). The proposed scheme offers integrity to cipher texts. It also protects transmitted cipher texts from tampering. Therefore, the decryption oracle drops any modified
, meaning that the oracle responds to the adversary with
for every modified message, as illustrated in
Figure 26. Resultantly, the proposed scheme is negligible under Equation (
8), meaning that it is indistinguishable under IND-CCA.
Let be an ECC encryption scheme, and let us define an experiment between the challenger and attacker A as follows:
Consider the following games:
Game (0)
The attacker A makes a request for encrypting a message , and receives .
Game (1)
The attacker A modifies the cipher text from game 0 to XOR the with a random value . A request is made for the challenger to decrypt the cipher text .
Game (3)
The attacker A can compute the plain text from , which results in . In this case, A can compare with and . However, A will fail to win because the challenger will discard the modified . This stems from the fact that is invalid, meaning that probability of the success of A is 0. □
4.3. Malleability Attack
Changing encrypted data can lead to the modification of the plain text after decryption, which is known as a malleability attack. For instance, the attacker modifies the
with the value of 1, which means that the first block of the plain text message will be XORed with 1. As a result, the reset of blocks in the CBC will also be modified. The steps involved in the malleability attack are depicted in
Figure 27.
Theorem 3. The proposed scheme is resistant to the malleability attack.
Proof. It is known that an adversary can eavesdrop on the messages sent between the two parties. Adversaries can also change messages and return them to either party. However, the recipient checks the received message’s integrity before decrypting the cipher text. Therefore, the recipient ignores the received message because it has an invalid signature. An illustration of this proof is given in
Figure 28□
A security analysis comparison was undertaken between the scheme proposed in this study and others mentioned in the literature (see
Table 2).
4.4. Performance Evaluation
The main goal of the proposed scheme was to provide a secure scheme that resolved encryption flaws that yield to CPA and CCA attacks. The study also sought to offer a scheme with a suitable level of performance in constrained environments. The security aspect of the proposed scheme was proven in the previous section, and this section evaluated the performance of the scheme based on two criteria: enhancing the process of mapping points to an elliptic curve; and time, space overhead, and power consumption in a simulation environment.
4.4.1. Mapping Points to an Elliptic Curve
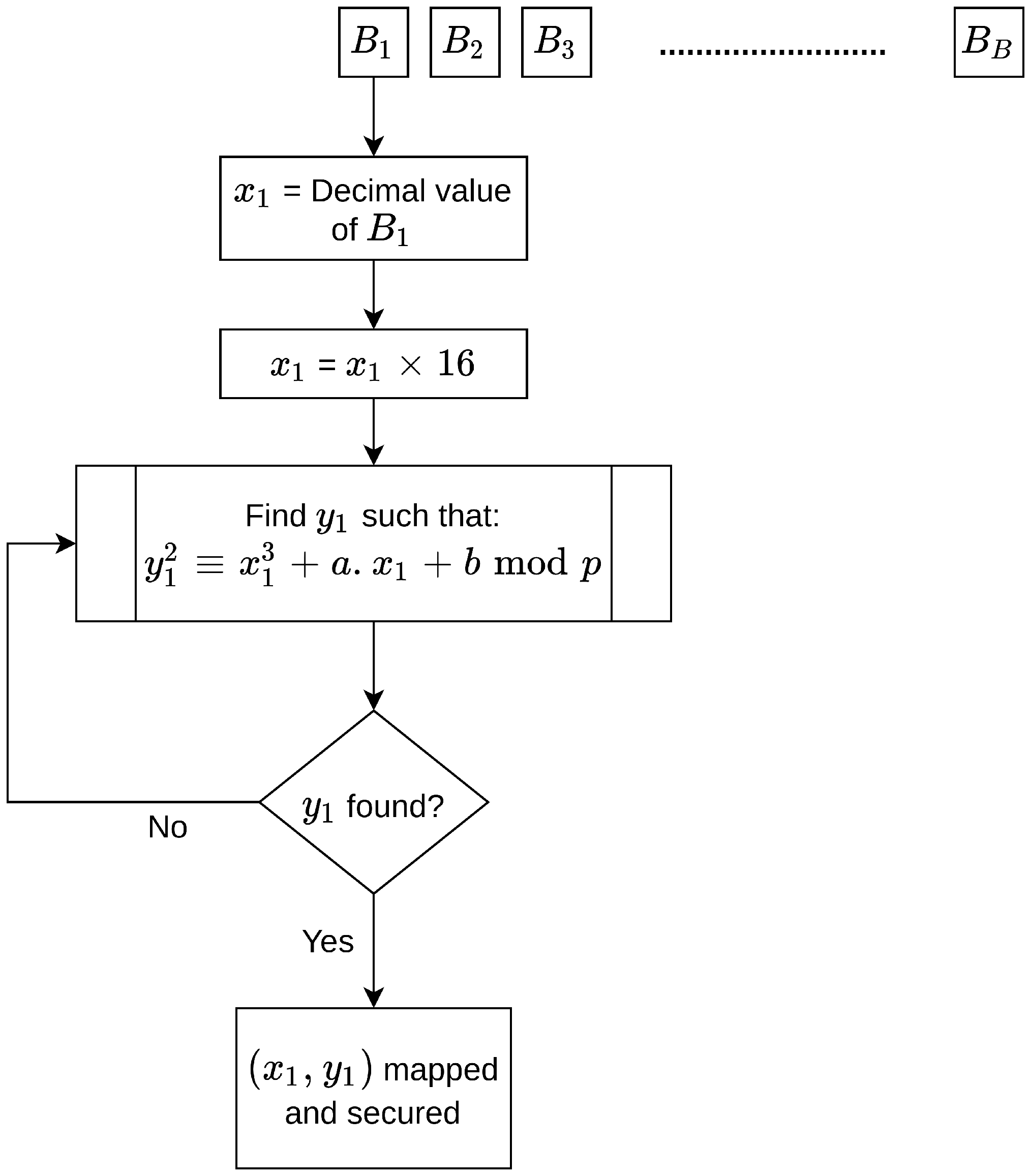
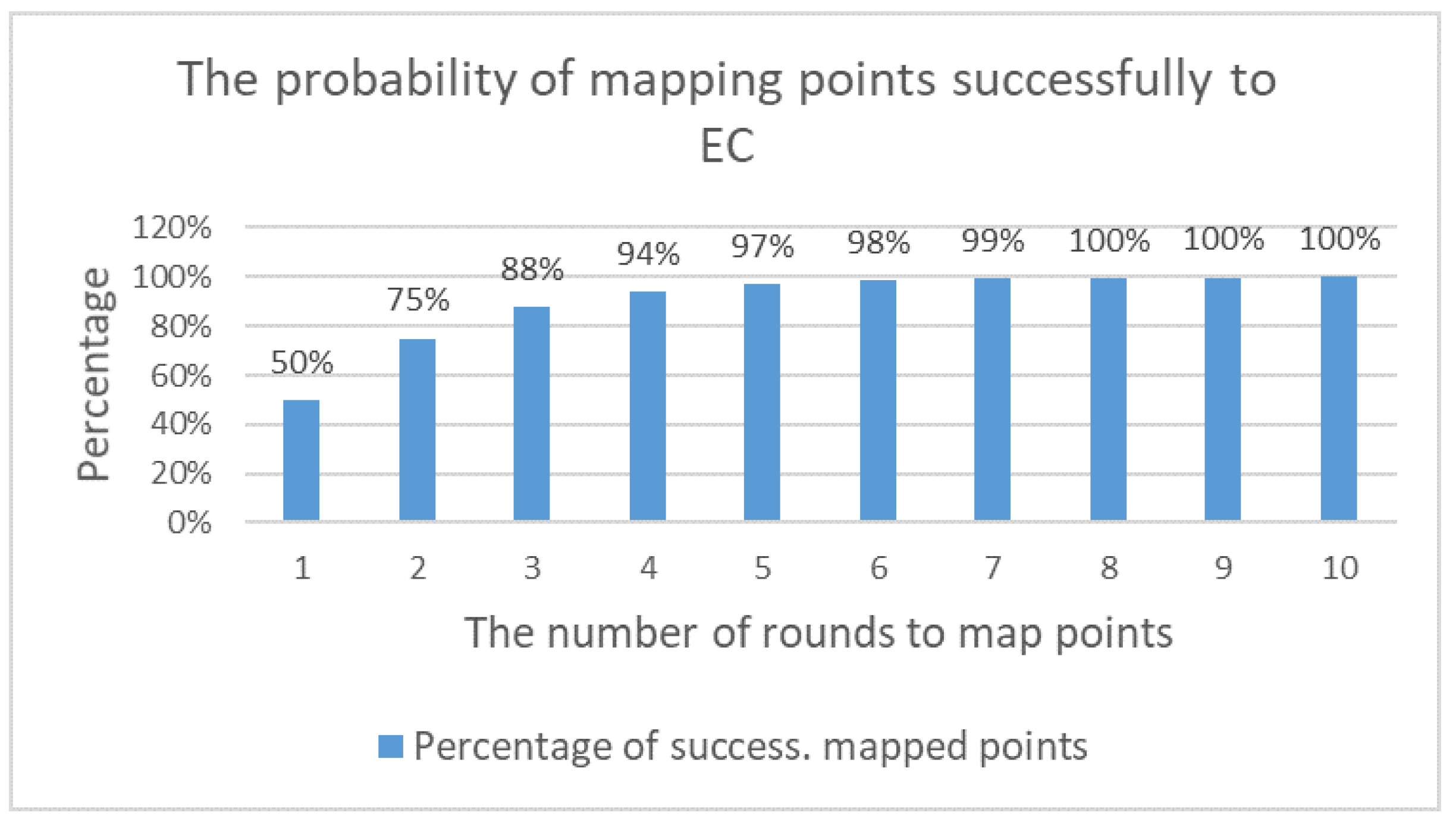
Mapping points to an elliptic curve should be undertaken correctly and efficiently. As illustrated in
Figure 29, 50% of
points cannot be mapped to the EC as there is no
axis that meets the EC’s equation. Therefore, it is necessary to increase the value of
by 1, and then to recompute
until a value is found that matches. As a result, the
point is eventually mapped. In many schemes, the characters in plain text are converted into numerical values based on the ASCII table, which facilitates their mapping onto the elliptic curve. Therefore, when these values are not mapped from the beginning, the value to be mapped increases. However, this step changes the original value, and the plain text is lost. For this reason, to overcome this problem, two methods are widely used to map points: the probability method and the appending method.
In the probability method, which was introduced by King (2009) [
64], the value of
k is defined, which represents the number of rounds needed to map the points. This value is multiplied by
, and the product is used in the mapping phase with ability to increment it in
k rounds. In turn, the value of
can be restored by calculating the value of the mapped point:
. In the second method, the appending method,
is appended by number of bits representing the number of rounds required. For instance, if the scheme defines the appended bits as 000, then the number of rounds that can be safely used in the mapping phase is
rounds.
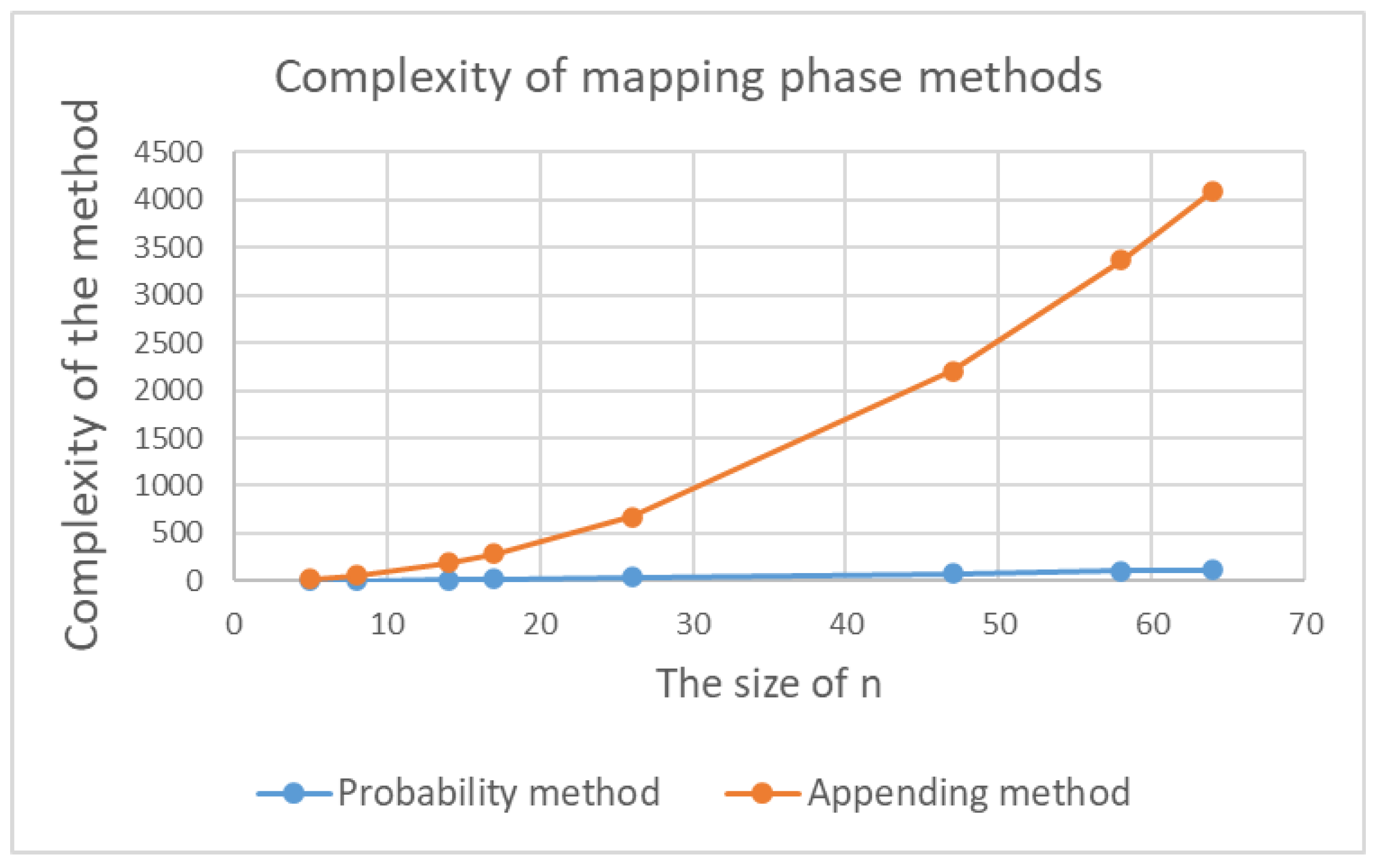
Each method has advantages and disadvantages relating to computational efficiency and the maximum number of rounds. The probability method is more efficient and less complex than the appending method. Using the Harvey-Hoeven algorithm [
65], the multiplication operation complexity is
, where
n is the numerical value size in bits. However, the complexity of appending two texts (i.e., concatenations) is denoted as
[
66], which highlights the fact that the appending method is more complex than the probability method. This is illustrated in
Figure 30.
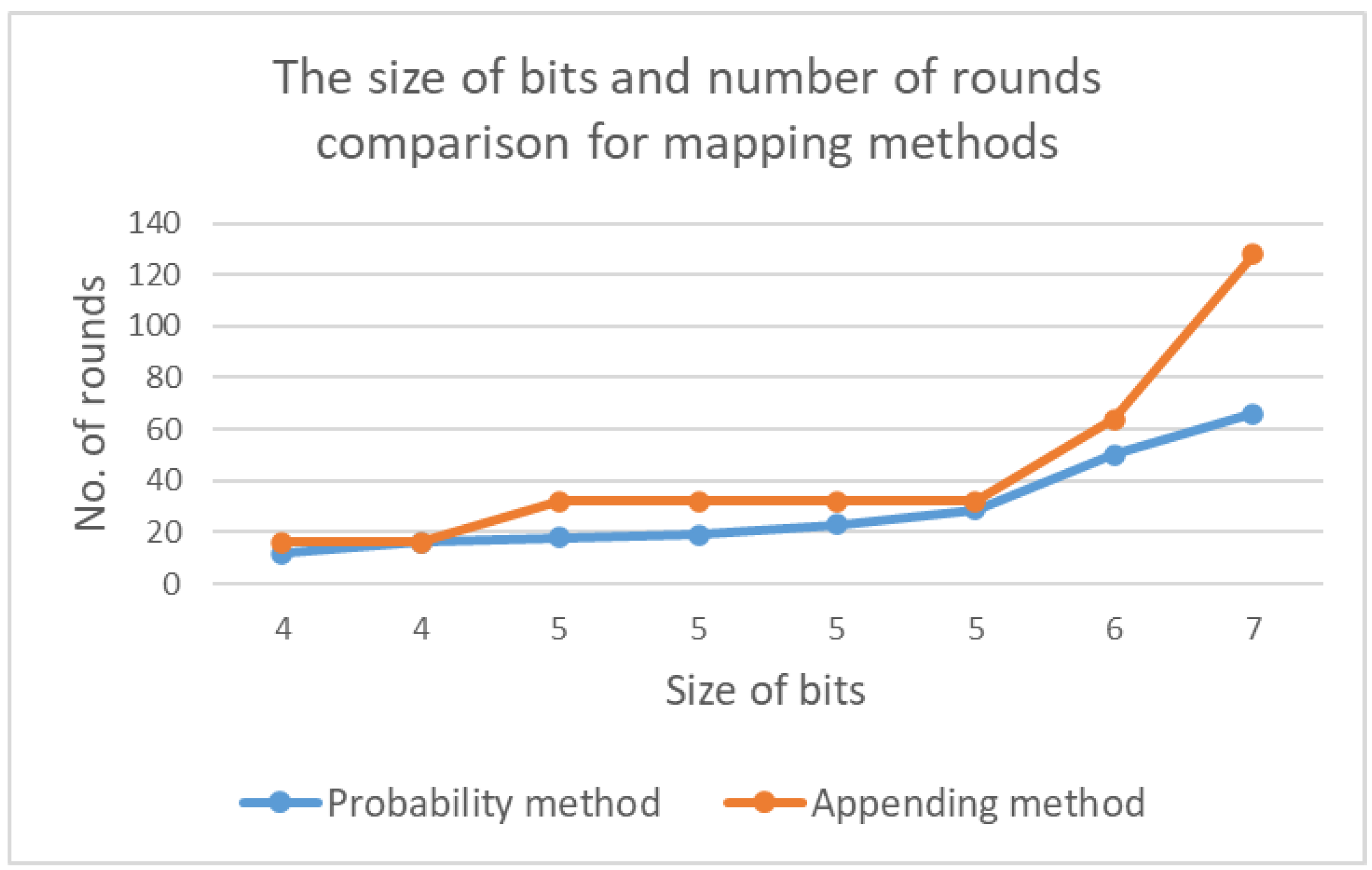
The appending method guarantees to provide a maximum number of rounds base on the appended bits. As the appending methods concatenate fixed bits
b to the corresponding binary
value,
can be incremented
times. In contrast, the probability method increases the same size of bits, but in many cases, it would allow fewer round increments compared to the appending method. This is outlined in
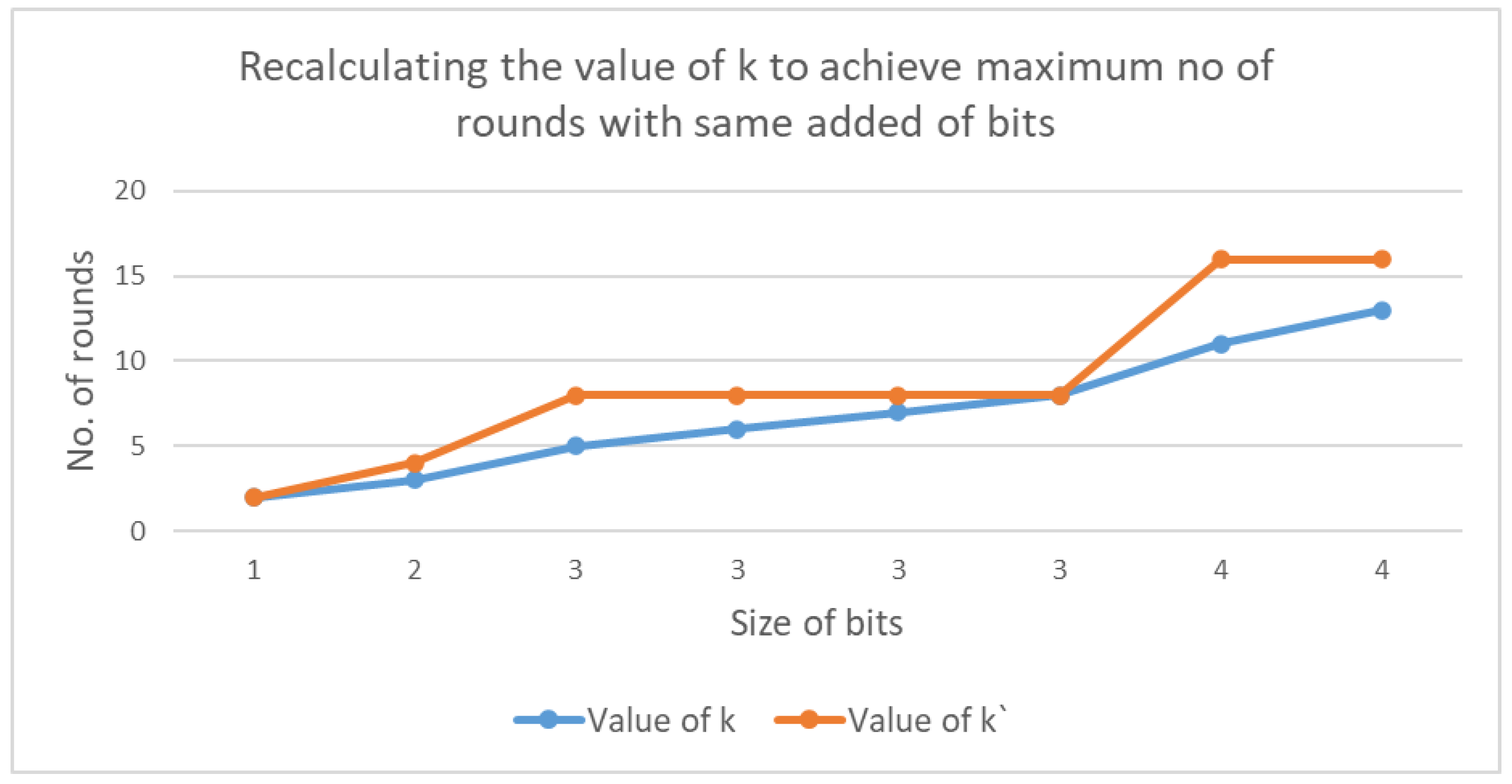
Figure 31.
In the proposed scheme, the probability method was used to improve performance. Hoevewr, to increase the efficiency of the choice of
k, the proposed scheme took advantage of the appending method to select this value. This was achieved by recalculating
, which was used to set the number of rounds to the maximum value of the extra bits added to the value of
, as shown in
Figure 32.
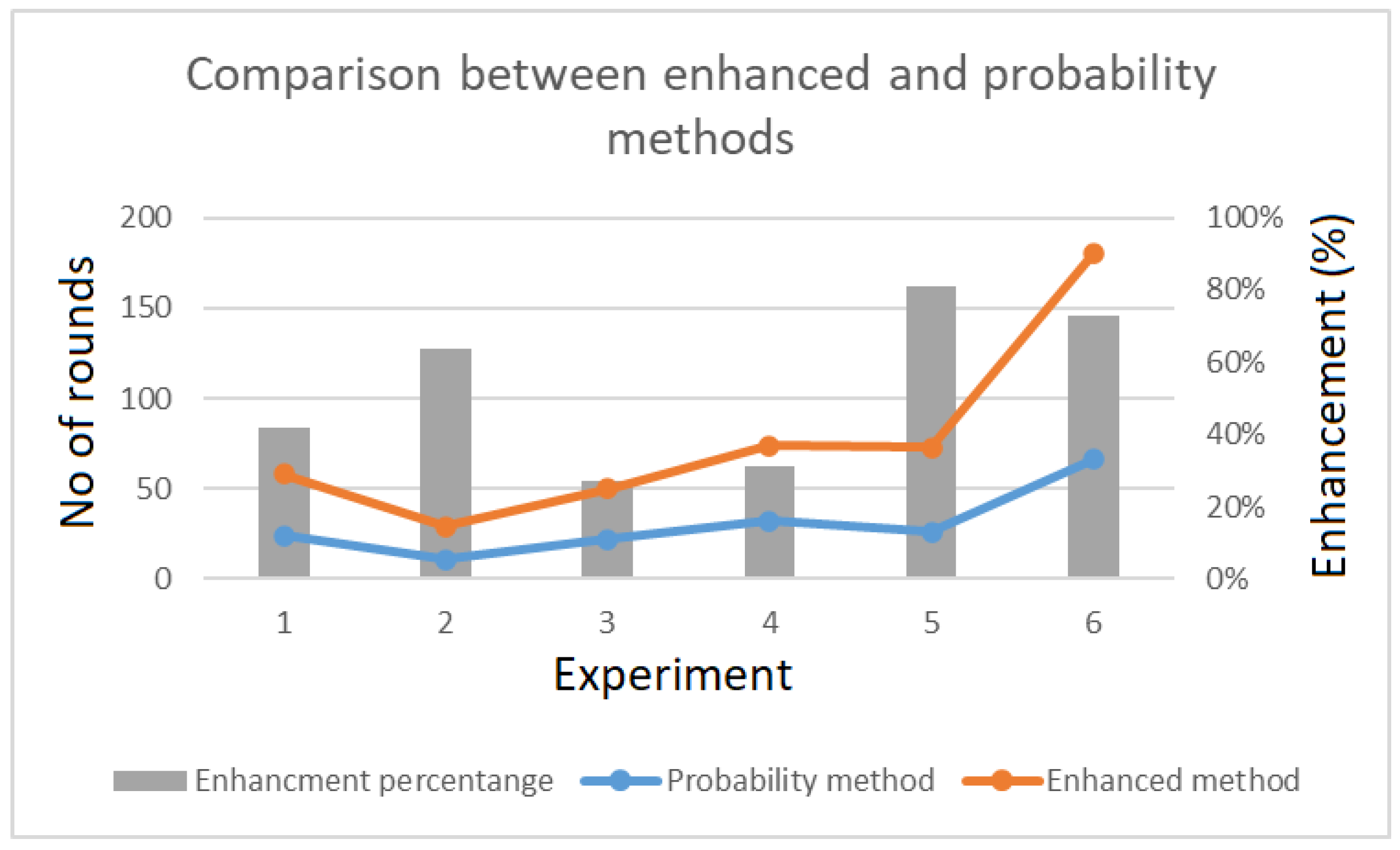
The enhancement made to the probability method increases the number of mapping rounds with same size of the padding bit. As a result, the efficiency was more than 80% in some cases.
Figure 33 shows the percentage of improvement that the proposed enhanced selection of
k method offers compared to the probability method.
4.4.2. Simulation Performance Evaluation
The performance evaluation of the proposed scheme focused on whether the enhancement of the encoding and mapping phases, which was intended to improve resistance to encryption attacks, negatively affected performance. Therefore, the performance of the proposed scheme against other schemes took place to evaluate time overhead, space usage, and power consumption. The schemes are divided to three groups: schemes that did not use
or any other methods to manipulate the mapped points as [
55,
60,
61,
62]; schemes that used fixed
to overcome CPA, including [
59]; and finally, schemes that used CBC to overcome the CCA (in this case, only the proposed scheme).
The performance evaluation involved running an experimental simulation 5 times for 20 s each using a low computation device.
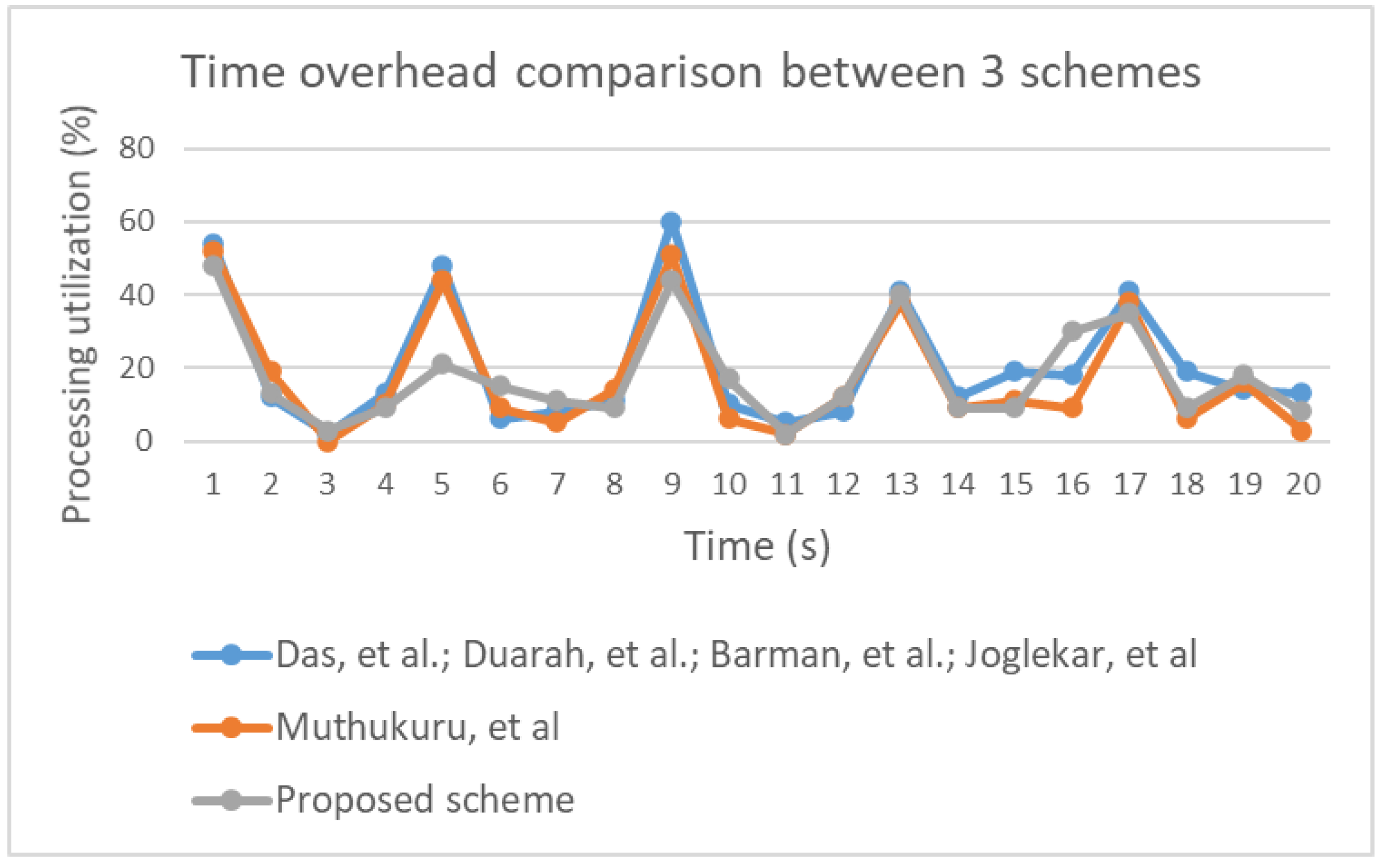
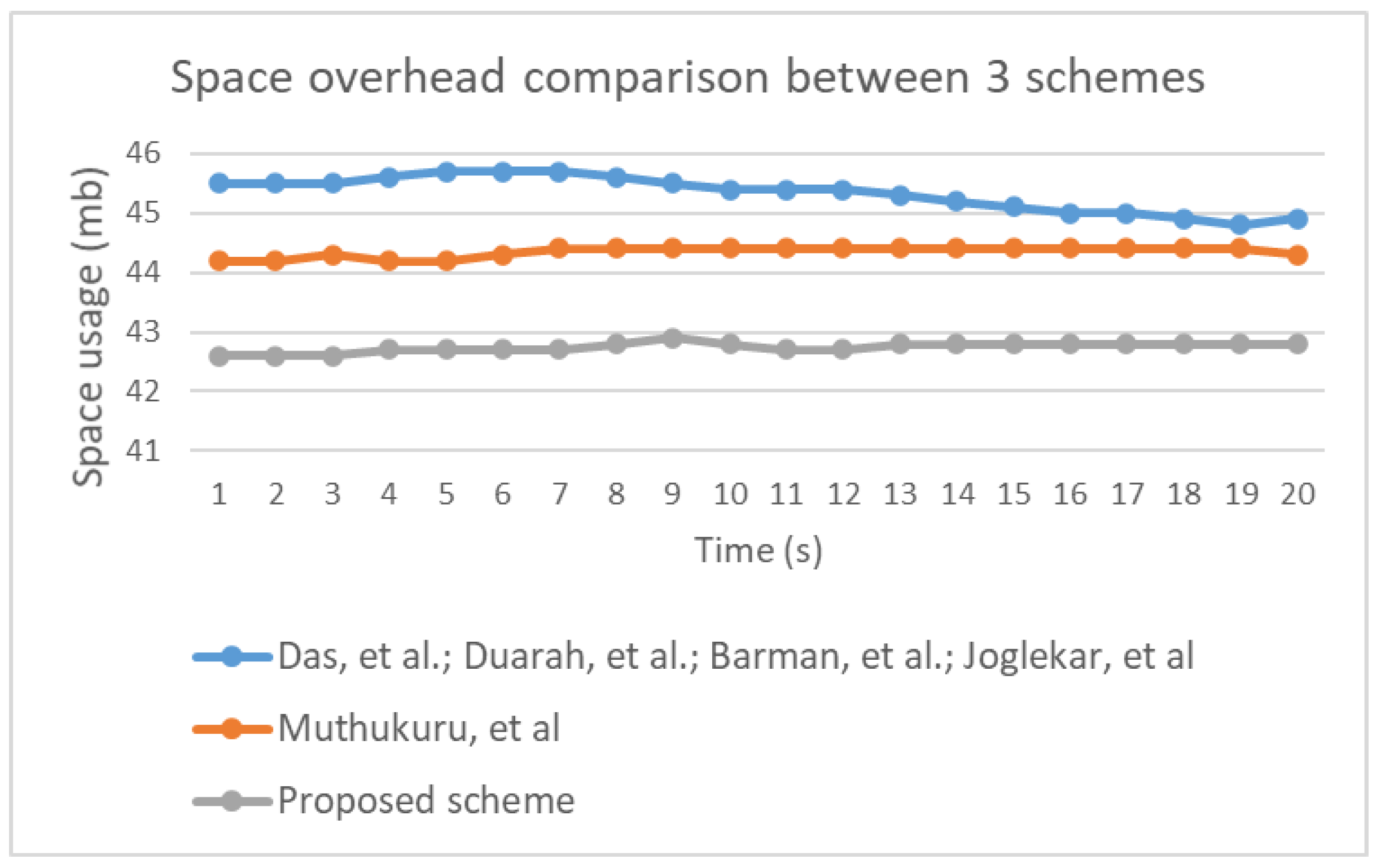
Figure 34 illustrates time overhead in the three groups included in the performance evaluation. Notably, all three groups were associated with similar levels of utilization. Therefore, it is reasonable to conclude that improving the security of the proposed scheme did not affect the time overhead. Space usage variation was identified during the experiment, as illustrated in
Figure 35. Additionally, power consumption for each group was determined based on values (high, medium, low, or none), which are shown in
Figure 36. The results indicate that power consumption was similar across the three groups.
It is worth mentioning that, the proposed scheme was simulated, tested and compared to the state of the art schemes in a simulated environment using an Android Virtual Device (AVD). AVD has variety of low computation devices images built by Android OS, and it provides processing space and power consumption monitoring and logging. In addition, we used the Bluej Java Development Environment to code the proposed scheme. The platform used to host the AVD is based on Windows 10, and, in terms of hardware, an Intel Core i7-4510U was used with a 128 GB SSD and 8 GB RAM.
5. Conclusions and Future Research
This study proposes a novel approach to elliptic curve cryptography (ECC) that offers AE properties to secure cipher text and to enhance the encoding of text effectively and map the encoded text to an elliptic curve. Previous schemes neglect to consider the importance of the encoding phase, which makes them vulnerable to attack. Therefore, this study focused on the encoding phase, seeking to secure it against several encryption attacks, including CPA, CCA, and malleability attacks. This study also undertook a security analysis to present a proof for the resistance of the proposed scheme against specific encryption attacks. Additionally, the study conducted a performance evaluation to compare the impact of the security enhancement of the proposed scheme on time overhead, space usage, and power consumption to other schemes. The simulation experiment shows that the proposed scheme performed just as well as the other schemes, with no noticeable increase in computation overhead. As a result, the proposed scheme outperforms the security of other schemes and maintains the same computational overhead.
In future research, the authors intend to implement the proposed scheme in different environments such as enhance the protection using TPM-based for mobile agents. Moreover, adapt the scheme in Monitoring the cloud computing architecture to enhance Dynamic Security Properties. In addition, apply the proposed scheme with Policy Based Management to increase the Security of Cloud Computing. These application of proposed scheme lead to study the security analysis and performance evaluation in comparison with other similar schemes. Additionally, more security properties may be added to the study to increase the security requirements, which might be required in new environments.