Security Evaluation under Different Exchange Strategies Based on Heterogeneous CPS Model in Interdependent Sensor Networks
Abstract
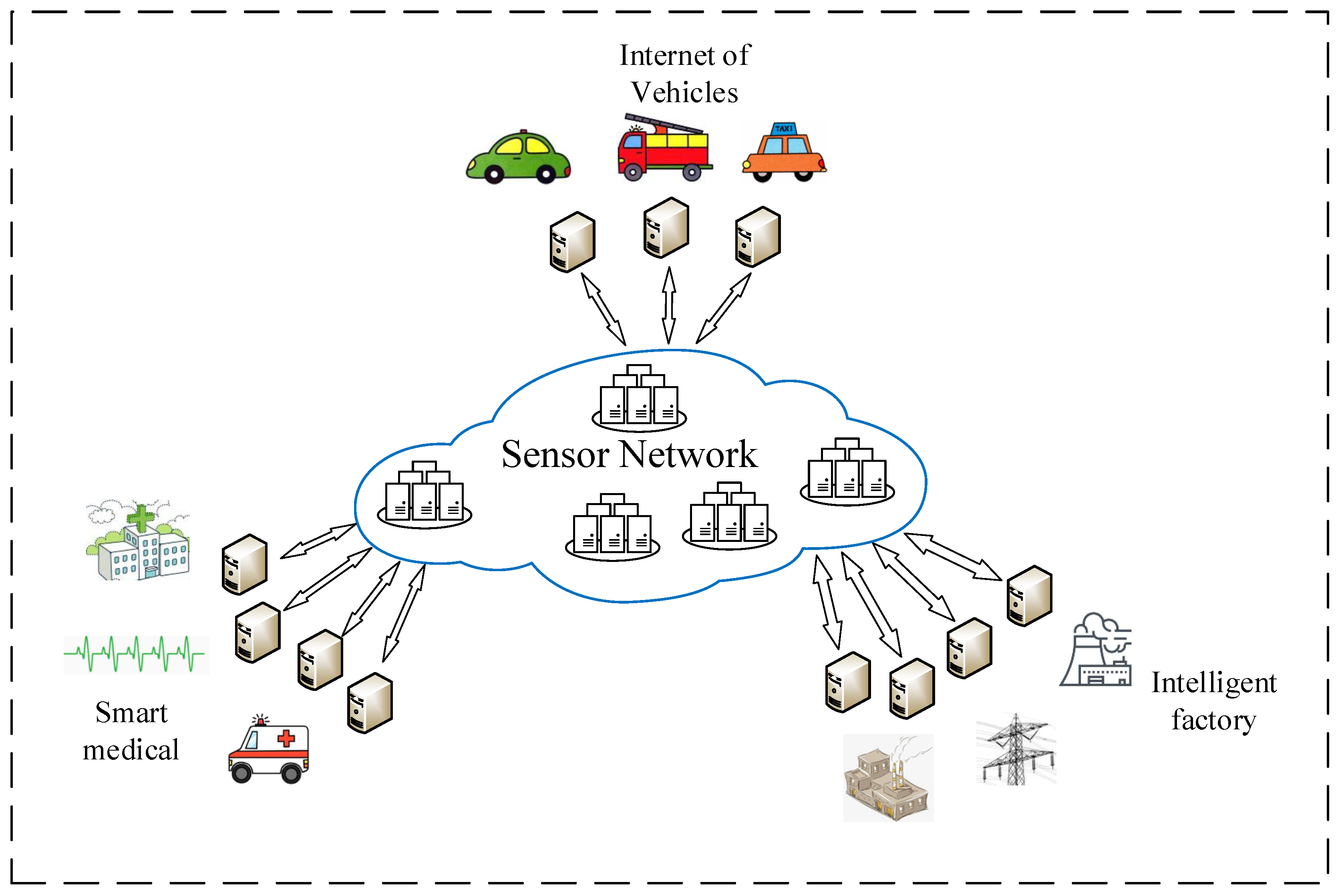
1. Introduction
- (i)
- First, we abstract the interdependent networks into various CPS models and attack at a fixed ratio to obtain the influence of different methods on enhancing the robustness of interdependent networks.
- (ii)
- Second, the high betweenness centrality and high eigenvector centrality swapping inter-links strategies have a better performance than other methods in enhancing G and in all CPS models, respectively.
2. Literature Review
3. The Model
3.1. Interdependent Networks Model
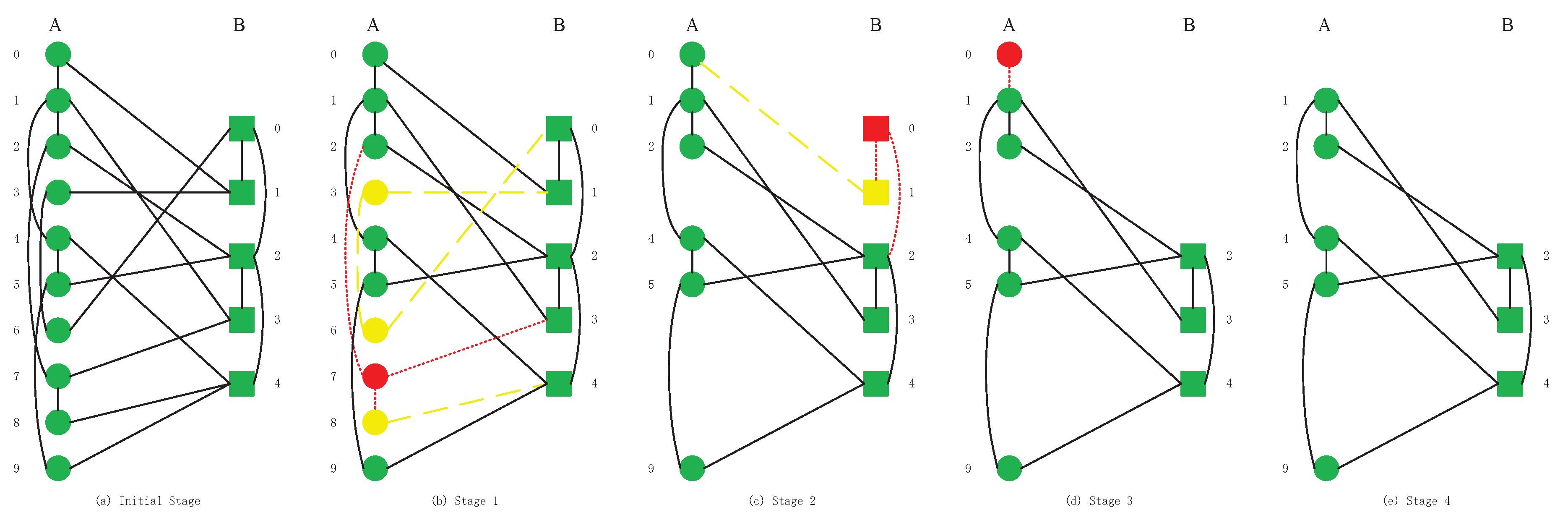
3.2. Cascading Failures Model
- This node must belong to the giant component of its network;
- The node must have at least one inter-link from other networks.
- All nodes are removed, and the interdependent networks are completely collapsing;
- The rest of the nodes both obey conditions I and II. These nodes will not continue to fail nor propagate failures. In this case, the interdependent networks achieve a steady state.
4. The Method
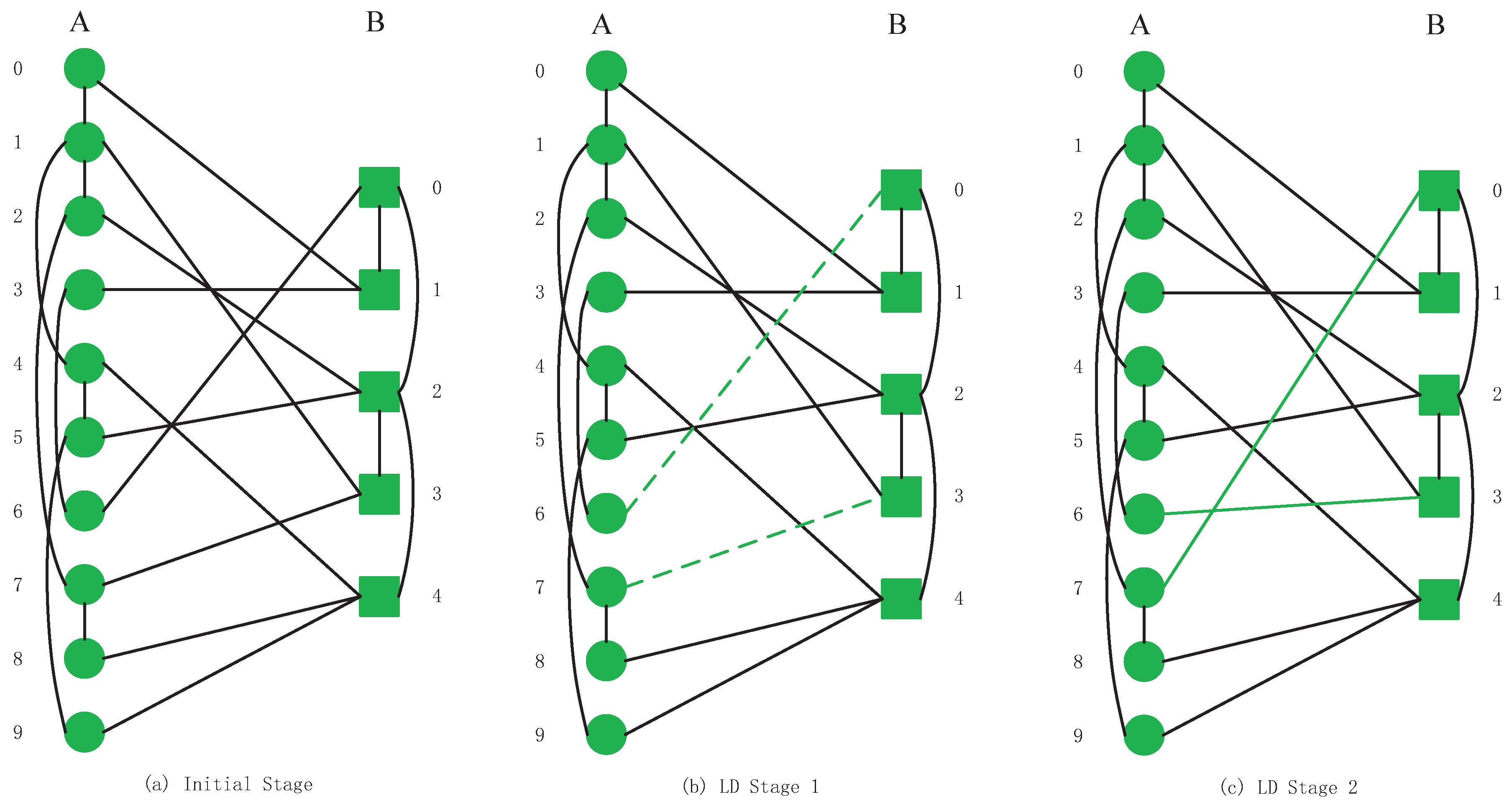
4.1. Strategy 1: Low Degree (LD)
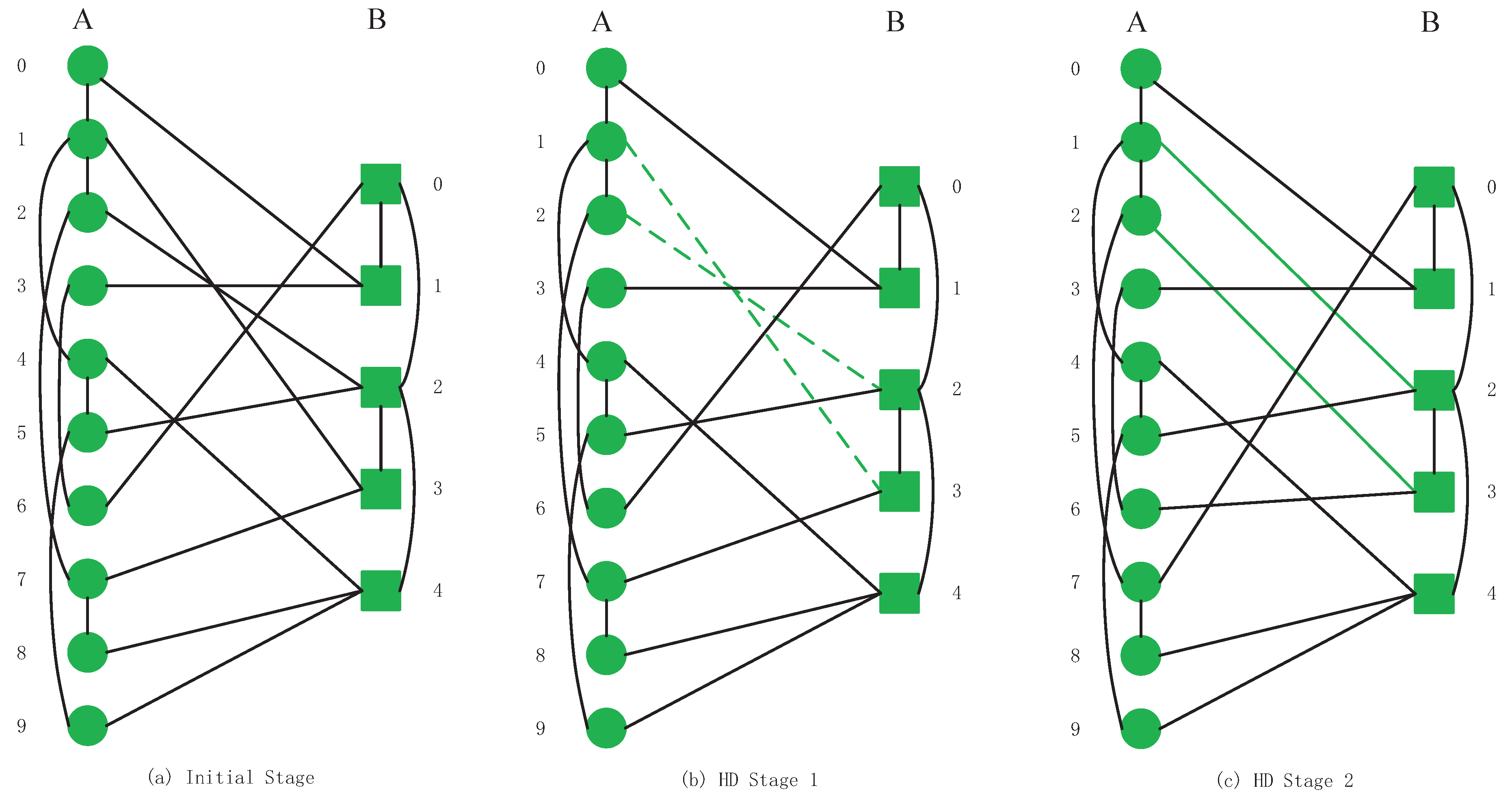
4.2. Strategy 2: High Degree (HD)
4.3. Strategy 3: Low Betweenness (LB)
4.4. Strategy 4: High Betweenness (HB)
4.5. Strategy 5: Low Eigenvector Centrality (LEC)
4.6. Strategy 6: High Eigenvector Centrality (HEC)
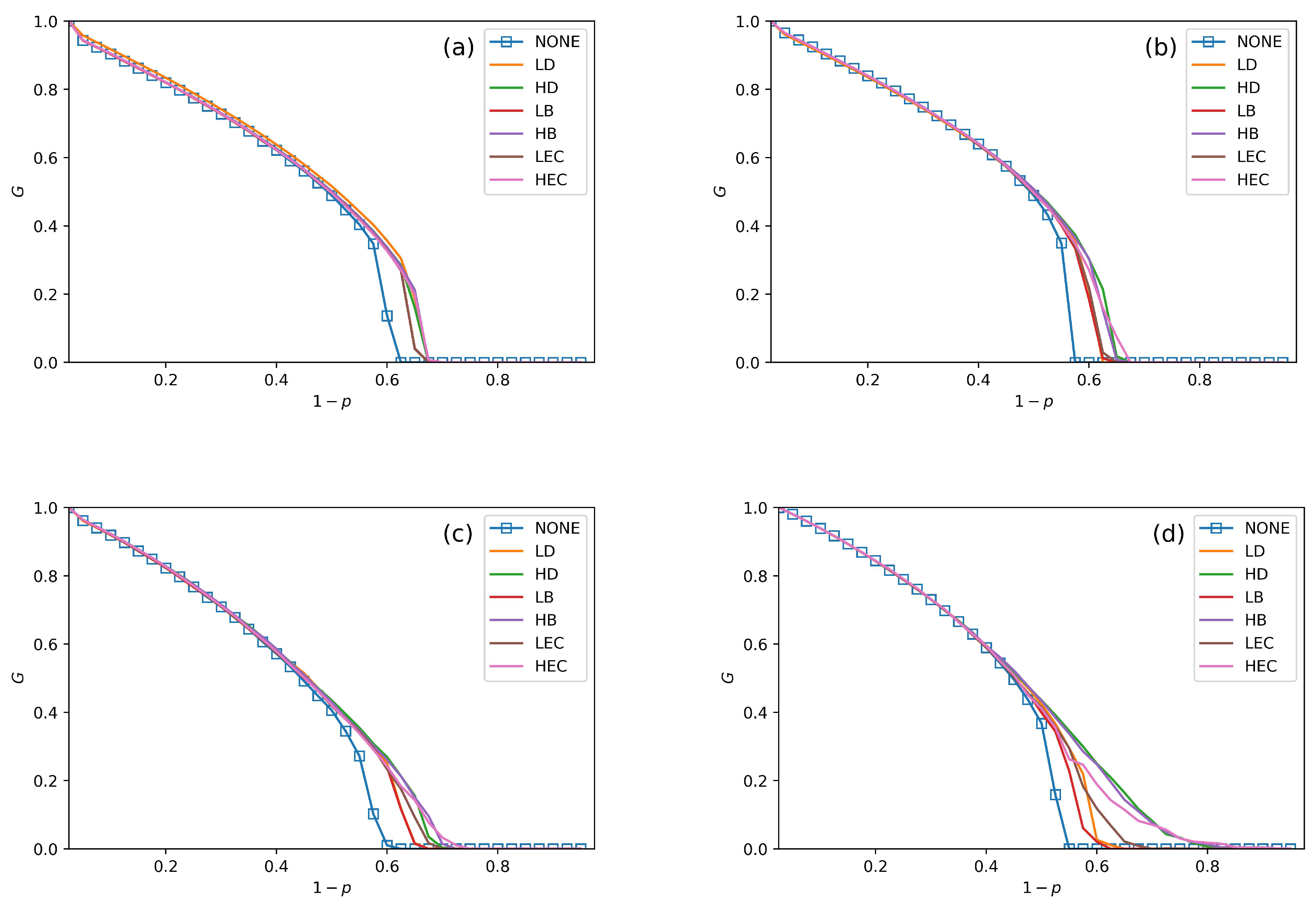
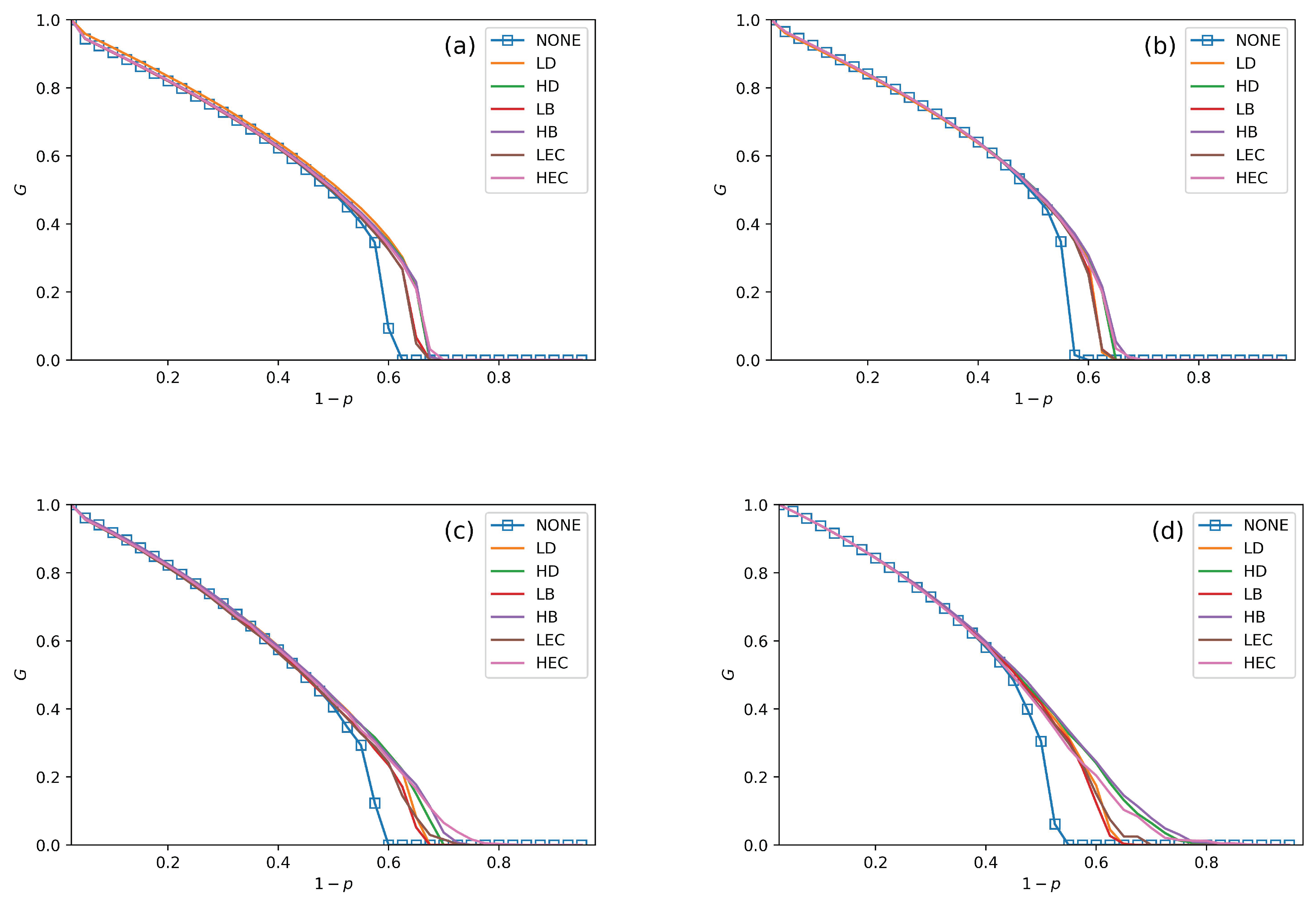
5. Simulation Results and Analysis
- All swapping strategies perform better than NONE in improving G and . The values of G are clearly bigger in swapping strategies than NONE when increases. For example, the values of G in NONE are lower than the other strategies when in Figure 5a. When , the value of G in NONE is lower than other strategies in Figure 6b. This situation can be observed in all four subfigures in Figure 5, Figure 6 and Figure 7.
- In Figure 5, Figure 6 and Figure 7, all curves can be divided into three categories. The first is NONE, which shows the worst performance in improving system reliability. The second is swapping inter-links by low centrality values, which are LD, LB, and LEC strategies. Although they show better performance than NONE in enhancing G and , they are not the best choices to achieve more robust systems. The last category is swapping inter-links with high centrality values. High centrality swapping strategies increase the values of G and . We should adopt a high centrality value swapping strategy for improving system reliability. This finding is the same conclusion as in [39,44].
- The sharp drop of G gets relief under all swapping strategies. This phenomenon is best reflected in Figure 5d, Figure 6d and Figure 7d. When gets close to , the G value of NONE is sharply decreased. The stark contrast is the G value under the HB strategy in the SF–SF system, which is smoother. This finding means that swapping inter-links in a CPS combined by SF networks is more sensitive in enhancing reliability than combining by ER networks. This conclusion is also found in the ‘one-to-one correspondence’ model [44].
- From all subfigures, we plot in Figure 5, Figure 6 and Figure 7. We conclude that the HB swapping strategy can be the first choice in improving G and HEC is the first choice in improving values. HB strategy shows the best performance in improving the value of G, and the HEC strategy is better in enhancing values. The values of in Figure 5a–d figures under the HEC strategy are 0.66, 0.69, 0.73 and 0.84, in Figure 6a–d are 0.68, 0.69, 0.75 and 0.85, and in Figure 7a–d are 0.68, 0.7, 0.78 and 0.82. This conclusion is more significant in the SF–SF CPS model. In Figure 5d, the value of under HEC is close to 0.8. The value of with HEC is more than 0.8 in Figure 6d. This finding is different from [39,44]. We reveal that network construction plays a vital role in system reliability.
6. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Zhu, Y.H.; Li, E.; Chi, K.; Tian, X. Designing prefix code to save energy for wirelessly powered wireless sensor networks. IET Commun. 2018, 12, 2137–2144. [Google Scholar] [CrossRef]
- Casado-Vara, R.; Novais, P.; Gil, A.B.; Prieto, J.; Corchado, J.M. Distributed continuous-time fault estimation control for multiple devices in IoT networks. IEEE Access 2019, 7, 11972–11984. [Google Scholar] [CrossRef]
- Cheng, C.F.; Wang, C.W. The target-barrier coverage problem in wireless sensor networks. IEEE Trans. Mob. Comput. 2017, 17, 1216–1232. [Google Scholar] [CrossRef]
- Gao, H.; Duan, Y.; Shao, L.; Sun, X. Transformation-based processing of typed resources for multimedia sources in the IoT environment. Wirel. Netw. 2019, 1–17. [Google Scholar] [CrossRef]
- Liu, X.; Lin, P.; Liu, T.; Wang, T.; Liu, A.; Xu, W. Objective-variable tour planning for mobile data collection in partitioned sensor networks. IEEE Ann. Hist. Comput. 2020, 1. [Google Scholar] [CrossRef]
- Wang, W.; Liu, Q.H.; Liang, J.; Hu, Y.; Zhou, T. Coevolution spreading in complex networks. Phys. Rep. 2019, 820, 1–51. [Google Scholar] [CrossRef]
- Koc, H.; Shaik, S.S.; Madupu, P.P. Reliability Modeling and Analysis for Cyber Physical Systems. In Proceedings of the 2019 IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 7–9 January 2019; pp. 7–9. [Google Scholar]
- Jazdi, N. Cyber physical systems in the context of Industry 4.0. In Proceedings of the 2014 IEEE International Conference on Automation, Quality and Testing, Robotics, Cluj-Napoca, Romania, 22–24 May 2014; pp. 1–4. [Google Scholar]
- Wang, T.; Luo, H.; Zeng, X.; Yu, Z.; Liu, A.; Sangaiah, A.K. Mobility based trust evaluation for heterogeneous electric vehicles network in smart cities. IEEE Trans. Intell. Transp. Syst. 2020, 1–10. [Google Scholar] [CrossRef]
- Zhang, J.; Yeh, E.; Modiano, E. Robustness of interdependent random geometric networks. IEEE Trans. Netw. Sci. Eng. 2018, 6, 474–487. [Google Scholar] [CrossRef]
- Pennekamp, J.; Henze, M.; Schmidt, S.; Niemietz, P.; Fey, M.; Trauth, D.; Bergs, T.; Brecher, C.; Wehrle, K. Dataflow Challenges in an Internet of Production: A Security & Privacy Perspective. In Proceedings of the ACM Workshop on Cyber-Physical Systems Security & Privacy, London, UK, 11 November 2019; pp. 27–38. [Google Scholar]
- Mihalache, S.F.; Pricop, E.; Fattahi, J. Resilience Enhancement of Cyber-Physical Systems: A Review. In Power Systems Resilience; Mahdavi Tabatabaei, N., Najafi Ravadanegh, S., Bizon, N., Eds.; Springer: Berlin/Heidelberg, Germany, 2019; pp. 269–287. [Google Scholar]
- Zikria, Y.B.; Afzal, M.K.; Kim, S.W. Internet of Multimedia Things (IoMT): Opportunities, Challenges and Solutions. Sensors 2020, 20, 2234. [Google Scholar] [CrossRef]
- Buldyrev, S.V.; Parshani, R.; Paul, G.; Stanley, H.E.; Havlin, S. Catastrophic cascade of failures in interdependent networks. Nature 2010, 464, 1025–1028. [Google Scholar] [CrossRef]
- Gao, J.; Buldyrev, S.V.; Stanley, H.E.; Havlin, S. Networks formed from interdependent networks. Nat. Phys. 2012, 8, 40. [Google Scholar] [CrossRef]
- Wu, Y.; Huang, H.; Wu, Q.; Liu, A.; Wang, T. A risk defense method based on microscopic state prediction with partial information observations in social networks. J. Parallel Distr. Com. 2019, 131, 189–199. [Google Scholar] [CrossRef]
- Huang, Z.; Wang, C.; Stojmenovic, M.; Nayak, A. Characterization of cascading failures in interdependent cyber-physical systems. IEEE Trans. Comput. 2014, 64, 2158–2168. [Google Scholar] [CrossRef]
- Dibaji, S.M.; Pirani, M.; Flamholz, D.B.; Annaswamy, A.M.; Johansson, K.H.; Chakrabortty, A. A systems and control perspective of CPS security. Annu. Rev. Control 2019, 47, 394–411. [Google Scholar] [CrossRef]
- Prathiba, A.; Bhaaskaran, V.K. Hardware footprints of S-box in lightweight symmetric block ciphers for IoT and CPS information security systems. Integration 2019, 69, 266–278. [Google Scholar] [CrossRef]
- Tippenhauer, N.O.; Wool, A. CPS-SPC 2019: Fifth Workshop on Cyber-Physical Systems Security and PrivaCy. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, New York, NY, USA, 11–15 November 2019; pp. 2695–2696. [Google Scholar]
- Gardiner, J.; Craggs, B.; Green, B.; Rashid, A. Oops I did it again: Further adventures in the land of ICS security testbeds. In Proceedings of the ACM Workshop on Cyber-Physical Systems Security & Privacy, London, UK, 11 November 2019; pp. 75–86. [Google Scholar]
- Zhang, J.; Yang, A.; Hu, Q.; Hancke, G.P. Security Implications of Implementing Multistate Distance-Bounding Protocols. In Proceedings of the ACM Workshop on Cyber-Physical Systems Security & Privacy, London, UK, 11 November 2019; pp. 99–108. [Google Scholar]
- Romagnoli, R.; Krogh, B.H.; Sinopoli, B. Design of software rejuvenation for cps security using invariant sets. In Proceedings of the 2019 American Control Conference (ACC), Philadelphia, PA, USA, 10–12 July 2019; pp. 3740–3745. [Google Scholar]
- Castellanos, J.H.; Zhou, J. A modular hybrid learning approach for black-box security testing of cps. In Applied Cryptography and Network Security; Deng, R., Gauthier-Umaña, V., Ochoa, M., Yung, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2019; pp. 196–216. [Google Scholar]
- Wang, T.; Cao, Z.; Wang, S.; Wang, J.; Qi, L.; Liu, A.; Xie, M.; Li, X. Privacy-enhanced data collection based on deep learning for Internet of vehicles. IEEE Trans. Industr. Inform. 2020, 16, 6663–6672. [Google Scholar] [CrossRef]
- Zikria, Y.B.; Afzal, M.K.; Kim, S.W.; Marin, A.; Guizani, M. Deep learning for intelligent IoT: Opportunities, challenges and solutions. Elsevier 2020, 164, 50–53. [Google Scholar] [CrossRef]
- Zhang, F.; Shi, Z.; Mukhopadhyay, S. Robustness analysis for battery-supported cyber-physical systems. ACM Trans. Reconfigurable Technol. Syst. 2013, 12, 69. [Google Scholar] [CrossRef]
- Wang, Z.; Scaglione, A.; Thomas, R.J. Generating statistically correct random topologies for testing smart grid communication and control networks. IEEE Trans. Smart Grid 2010, 1, 28–39. [Google Scholar] [CrossRef]
- Derler, P.; Lee, E.A.; Vincentelli, A.S. Modeling cyber–physical systems. Proc. IEEE Inst. Electr. Electron. Eng. 2011, 100, 13–28. [Google Scholar] [CrossRef]
- Tu, H.; Xia, Y.; Iu, H.H.C.; Chen, X. Optimal robustness in power grids from a network science perspective. IEEE Trans. Circuits Syst. II Express Briefs 2018, 66, 126–130. [Google Scholar] [CrossRef]
- Ruj, S.; Pal, A. Analyzing cascading failures in smart grids under random and targeted attacks. In Proceedings of the 2014 IEEE 28th International Conference on Advanced Information Networking and Applications, Victoria, BC, Canada, 13–16 May 2014; pp. 226–233. [Google Scholar]
- Nguyen, D.T.; Shen, Y.; Thai, M.T. Detecting Critical Nodes in Interdependent Power Networks for Vulnerability Assessment. IEEE Trans. Smart Grid 2013, 4, 151–159. [Google Scholar] [CrossRef]
- Shao, J.; Buldyrev, S.V.; Havlin, S.; Stanley, H.E. Cascade of failures in coupled network systems with multiple support-dependence relations. Phys. Rev. E 2011, 83, 036116. [Google Scholar] [CrossRef] [PubMed]
- Cui, P.; Zhu, P.; Wang, K.; Xun, P.; Xia, Z. Enhancing robustness of interdependent network by adding connectivity and dependence links. Physica A 2018, 497, 185–197. [Google Scholar]
- Kamran, K.; Zhang, J.; Yeh, E.; Modiano, E. Robustness of interdependent geometric networks under inhomogeneous failures. In Proceedings of the 2018 16th International Symposium on Modeling and Optimization in Mobile, Ad Hoc, and Wireless Networks (WiOpt), Shanghai, China, 7–11 May 2018; pp. 1–6. [Google Scholar]
- Ji, X.; Wang, B.; Liu, D.; Chen, G.; Tang, F.; Wei, D.; Tu, L. Improving interdependent networks robustness by adding connectivity links. Physica A 2016, 444, 9–19. [Google Scholar] [CrossRef]
- Beygelzimer, A.; Grinstein, G.; Linsker, R.; Rish, I. Improving network robustness by edge modification. Physica A 2005, 357, 593–612. [Google Scholar] [CrossRef]
- Kazawa, Y.; Tsugawa, S. Robustness of networks with skewed degree distributions under strategic node protection. In Proceedings of the 2016 IEEE 40th Annual Computer Software and Applications Conference (COMPSAC) 2016, Atlanta, GA, USA, 10–14 June 2016; pp. 14–19. [Google Scholar]
- Chattopadhyay, S.; Dai, H.; Hosseinalipour, S. Designing optimal interlink patterns to maximize robustness of interdependent networks against cascading failures. IEEE Trans. Commun. 2017, 65, 3847–3862. [Google Scholar] [CrossRef]
- Chen, L.; Yue, D.; Dou, C.; Cheng, Z.; Chen, J. Robustness of cyber-physical power systems in cascading failure: Survival of interdependent clusters. Int. J. Electr. Power Energy Syst. 2020, 114, 105374. [Google Scholar] [CrossRef]
- Huang, Z.; Wang, C.; Ruj, S.; Stojmenovic, M.; Nayak, A. Modeling cascading failures in smart power grid using interdependent complex networks and percolation theory. In Proceedings of the 2013 IEEE 8th Conference on Industrial Electronics and Applications (ICIEA), Melbourne, VIC, Australia, 19–21 June 2013; pp. 1023–1028. [Google Scholar]
- Dong, G.; Chen, Y.; Wang, F.; Du, R.; Tian, L.; Stanley, H.E. Robustness on interdependent networks with a multiple-to-multiple dependent relationship. J. Nonlinear Sci. 2019, 29, 073107. [Google Scholar] [CrossRef]
- Chen, L.; Yue, D.; Dou, C. Optimization on vulnerability analysis and redundancy protection in interdependent networks. Physica A 2019, 523, 1216–1226. [Google Scholar] [CrossRef]
- Peng, H.; Liu, C.; Zhao, D.; Ye, H.; Fang, Z.; Wang, W. Security Analysis of CPS Systems under Different Swapping Strategies in IoT Environments. IEEE Access 2020, 8, 63567–63576. [Google Scholar] [CrossRef]
- Kumari, P.; Singh, A. Approximation and Updation of Betweenness Centrality in Dynamic Complex Networks. In Computational Intelligence: Theories, Applications and Future Directions-Volume I; Verma, N., Ghosh, A., Eds.; Springer: Singapore, 2019; pp. 25–37. [Google Scholar]
- Newman, M. Networks; Oxford University Press: Oxford, UK, 2018. [Google Scholar]

| Approaches | Pros | Cons |
|---|---|---|
| Protecting critical network nodes | This method has strong pertinence | Finding the critical nodes is an NP-hard problem |
| Making nodes autonomous | It can make the failure node recover its function and reduce manpower | Expensive; Hard to choosing important nodes |
| Refiguring the topology of network | It can achieve the purpose of enhancing network reliability | It is not suitable for the existing network |
| Adding intra-links in systems | Simple; More choices | Increase cost |
| Adjusting dependency link allocation | The amount that needs to be exchanged is relatively small | The inter-link’s distance between nodes is longer than intra-link |
| Symbol | Meaning |
|---|---|
| The fraction of attacked nodes at the first stage | |
| , | The fraction of nodes in the giant component of network A, B in stage i |
| , | The number of nodes remaining in network A, B in stage i |
| The fraction of remaining in network nodes | |
| The fraction of normal operation nodes in network | |
| , | The generating functions of network A, B |
| x, y | The final stage nodes’ number of network A, B |
| Symbol | Values |
|---|---|
| 15,000 | |
| 5000 | |
| 4 | |
| 3 | |
| simulation times of each | 20 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Peng, H.; Liu, C.; Zhao, D.; Hu, Z.; Han, J. Security Evaluation under Different Exchange Strategies Based on Heterogeneous CPS Model in Interdependent Sensor Networks. Sensors 2020, 20, 6123. https://doi.org/10.3390/s20216123
Peng H, Liu C, Zhao D, Hu Z, Han J. Security Evaluation under Different Exchange Strategies Based on Heterogeneous CPS Model in Interdependent Sensor Networks. Sensors. 2020; 20(21):6123. https://doi.org/10.3390/s20216123
Chicago/Turabian StylePeng, Hao, Can Liu, Dandan Zhao, Zhaolong Hu, and Jianmin Han. 2020. "Security Evaluation under Different Exchange Strategies Based on Heterogeneous CPS Model in Interdependent Sensor Networks" Sensors 20, no. 21: 6123. https://doi.org/10.3390/s20216123
APA StylePeng, H., Liu, C., Zhao, D., Hu, Z., & Han, J. (2020). Security Evaluation under Different Exchange Strategies Based on Heterogeneous CPS Model in Interdependent Sensor Networks. Sensors, 20(21), 6123. https://doi.org/10.3390/s20216123







