Abstract
A new kind of malware called Mirai is spreading like wildfire. Mirai is characterized by targeting Internet of Things (IoT) devices. Since IoT devices are increasing explosively, it is not realistic to manage their vulnerability by human-wave tactics. This paper proposes a new approach that uses a white-hat worm to fight malware. The white-hat worm is an extension of an IoT worm called Hajime and introduces lifespan and secondary infectivity (the ability to infect a device infected by Mirai). The proposed white-hat worm was expressed as a formal model with agent-oriented Petri nets called PN. The model enables us to simulate a battle between the white-hat worm and Mirai. The result of the simulation evaluation shows that (i) the lifespan successfully reduces the worm’s remaining if short; (ii) if the worm has low secondary infectivity, its effect depends on the lifespan; and (iii) if the worm has high secondary infectivity, it is effective without depending on the lifespan.
1. Introduction
In September 2016, unprecedented Distributed Denial-of-Service (DDoS) attacks knocked out Twitter, Amazon, and other major sites. They were launched by lots of Internet of Things (IoT) devices which were infected by a new kind of malware called Mirai. Mirai infects IoT devices one after another and makes them a botnet to perform DDoS attacks [1]. Mirai is spreading like wildfire and actually has infected over 300,000 IoT devices in 164 countries [2]. This so-called Mirai pandemic results from characteristics of IoT devices such as (i) increasing explosively, (ii) existing anywhere, and (iii) using easy-to-guess passwords. Thus, DDoS attacks brought by IoT devices tend to become massive and disruptive [3].
There are some mitigation methods against Mirai. One method proposed by US Computer Emergency Readiness Team (US-CERT) [4] is to reboot the device infected by Mirai. This is simple, but the device would be reinfected soon if it is not updated. A promising method is to use a kind of IoT worms called Hajime as a vaccine against Mirai. Hajime infects IoT devices one after another and blocks ports that Mirai uses to infect [5]. However, there are few quantitative evaluations of Hajime’s effect.
Since November 2017, the authors of Ref. [6] have evaluated Hajime’s effect quantitatively. They regarded the battle between Mirai and Hajime as a multi-agent system and expressed it with agent-oriented Petri net called Petri Nets in a Petri Net (PN for short) [7]. The evaluation result showed that Hajime protected IoT devices from Mirai’s infection. However, the devices became infected by Hajime instead. For now, unlike Mirai, Hajime does not have any DDoS capability. However, Hajime has a remote control mechanism, which is an unfavorable attribute.
IoT devices are increasing explosively. Thus, it is not realistic to manage their vulnerability against Mirai by human-wave tactics. In this paper, we propose a new approach that uses a white-hat worm to fight Mirai. We first extend Hajime to become the white-hat worm by introducing lifespan and secondary infectivity (the ability to infect a device infected by Mirai). Next, we construct a PN model representing the white-hat worm. Then, we evaluate the effect of the white-hat worm against Mirai through the simulation of the model.
The rest of this paper is organized as follows: Section 2 surveys the related work. Section 3 gives the design of the white-hat worm and its PN model. Section 4 presents the simulation for evaluating the effect of the white-hat worm against Mirai. Section 5 summarizes our key points and gives future work.
2. Related Work
2.1. Mirai and Hajime
Mirai is a kind of malware that infects IoT devices. It turns them into bots and creates a botnet. The botnet becomes a hotbed of large-scale DDoS attacks. In August 2016, Mirai was found by a malware research group MalwareMustDie. The first attack happened in September 2016. Since then, Mirai has been spreading like wildfire around the world.
Mirai takes the following two stages. The first is the infection stage. Mirai searches for an IoT device using port 23 or 2323. Once Mirai finds such a device, it tries to log-in with easy-to-guess passwords. If succeeding in log-in, Mirai downloads an architecture-dependent code from the Command and Control (C&C) server and executes it. As a result, the device becomes a bot. The second is the attack stage. Once an attacker issues a command, the C&C server delivers it to bots. All the bots begin a DDoS attack on the target specified by the attacker. In November 2016, US-CERT announced that Mirai can be removed if the infected device is rebooted. For the detail of Mirai, refer to Ref. [8].
There are some systems that detect IoT malware like Mirai. Bezerra et al. [9] proposed a host-based malware detection system, named IoTDS (Internet of Things Detection System). It analyzes the host’s CPU and memory utilization, CPU temperature, and the number of running tasks and classifies its behavior as malicious or legitimate. On one hand, with the continuous development of machine learning algorithms, some learning-based malware detection systems have been proposed. However, these learning-based detection systems are often vulnerable to adversarial samples. Liu et al. [10] proposed an automated testing framework that can generate an effective adversarial sample without affecting the features of the IoT application. This framework enables us to perform black-box testing. However, IoTDS and the learning-based malware detection systems detect malware but don’t take any action for the detected malware themselves. Ceron et al. [11] proposed a network layer that adapts itself to mitigate the network traffic generated by IoT malware. It can modify the traffic at the network layer based on the actions performed by the malware. However, the network layer is not something to remove the malware.
Hajime is a kind of worms that infects IoT devices. In October 2016, Hajime was found by the security research group at Rapidly Networks, Inc. [5]. Hajime aims at creating a botnet like Mirai. However, there is a crucial difference between Mirai and Hajime. Hajime has no capability for DDoS attacks [12]. On the contrary, Hajime blocks the ports that Mirai accesses to infect the device and displays a warning message to inform the user of the risk of malware. Hajime is an unethical way but can be regarded as one of the mitigation methods against Mirai.
When utilizing worms like Hajime as a mitigation method against Mirai, there are several challenges to be overcome about viability, capability, legality, and ethics of the worms. Molesky et al. [13] discussed some of the challenges from the viewpoints of individual, business and government. They proposed a perspective for utilizing worms through balancing them. However, they provided no more than qualitative concepts and have not evaluated them quantitatively.
2.2. PN and Modeling
Yamaguchi et al. [14] regarded the battle between Mirai and Hajime as a multi-agent system and expressed it with PN.
A PN is intuitively a Petri net (called as environment net) whose tokens are again Petri nets (called as agent nets). Each agent net represents the state-transition of an agent, and the environment net specifies the interaction between agents. The number of tokens in the environment net may increase or decrease. This means the creation or deletion of agents. The transitions of two or more agent nets may fire simultaneously. This means an interaction between the corresponding agents. The combination of agents related to the interaction is dynamically decided because PN allows dynamic bindings of transitions. Nakahori et al. [15] developed a tool, called as PN2Simulator, to edit and simulate PN. For the detail of Petri nets and PN, refer to Refs. [7,16].
There are some agent-oriented approaches in the research area in cybersecurity. For example, García-Magariño et al. [17] proposed a process called PEABS for constructing efficient multi-agent simulators. They applied it to some cybersecurity issues and successfully developed simulators like ABS-SecurityUAV [18]. Such previous research is oriented to the expressiveness of agent-based systems. In contrast, our approach based on PN is oriented to mathematical analysis. The semantics of PN enables us to formally describe the phenomenon and to analyze with Petri net’s properties and their abundant analysis methods.
PN enables us to model a battle between Mirai and Hajime. An example is shown in Figure 1. The agent net of Figure 1a represents the state-transition of Mirai. Transition t1 (drawn by □) labeled as m_infect represents an infection action. Transition t2 labeled as m_reboot represents a reboot action. Place p1 forms a self-loop together with each transition. p1 possesses a token (drawn by •). A token distribution is called as a state and is denoted by a multi-set over the set P of places, i.e., , where is the number of tokens at p. with state being denoted by . Since p1 has a token, the transitions can fire repeatedly. This means that Mirai repeatedly infects a device and is deleted by a reboot action.
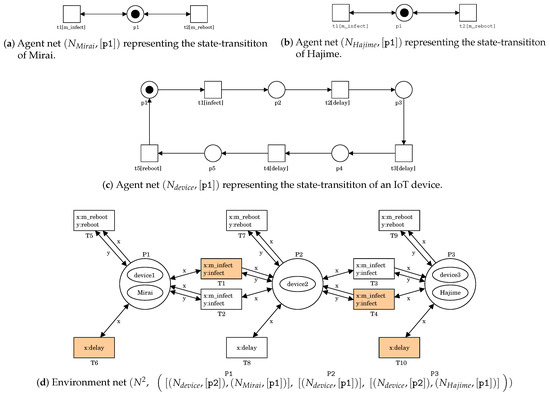
Figure 1.
A PN model representing a battle between Mirai and Hajime.
The agent net of Figure 1b represents the state-transition of Hajime. It is the same net structure as Mirai because Hajime has the same capabilities except for the DDoS one.
The agent net of Figure 1c represents the state-transition of an IoT device. Transition t1 labeled as infect represents an infection action. Even if it becomes a bot, it can be returned to normal by rebooting. However, it is not always rebooted immediately after the infection. Thus, we should introduce some delay until the reboot. Transitions t2, t3, and t4 labeled as delay respectively represent a delay action. Transition t5 labeled as reboot represents a reboot action.
The environment net of Figure 1d represents an IoT network of linear topology which consists of three nodes. The first node connects with the second node and the second node connects with the third node. Each node is expressed as a place. A token (drawn by ⬭) represents an IoT device, Mirai, or Hajime. We assume in this paper that each node has one device. Place P1 possesses two tokens representing Mirai and a device device1. This means that Mirai infects device1. Place P2 possesses only one token representing a device device2. This means that device2 is normal. Place P3 possesses two tokens representing Hajime and a device device3. This means that Hajime infects device3. A transition represents an interaction among them, e.g., an infection of Mirai to a device. PN2Simulator can highlight which transition is firable in red. For each place p in , let denote a multi-set of agent nets corresponding to tokens at p. Any state of is denoted by a vector of all ’s. The state of Figure 1d is written as follows:
2.3. Simulation Evaluation
We can simulate the battle between Mirai and Hajime by using the PN model given in Section 2.2. Figure 2 shows an execution of . Note that is shown in Figure 1d. In , there are four firable transitions T1, T4, T6, and T10 because
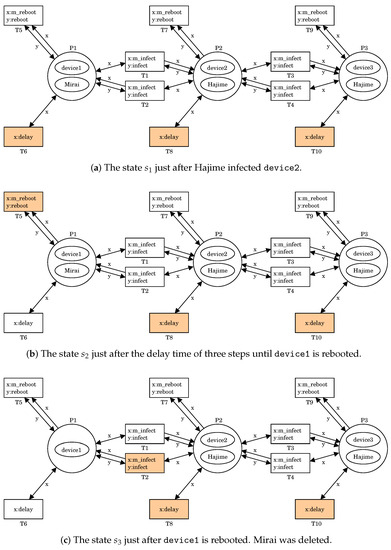
Figure 2.
An execution of .
- For T1, x:m_infect and y:infect can be respectively bounded with t1 in at P1 and t1 in at P2.
- For T4, x:m_infect and y:infect can be respectively bounded with t1 in at P3 and t1 in at P2.
- For T6, x:delay can be bounded with t2 in at P1.
- For T10, x:delay can be bounded with t2 in at P3.
Let us fire T4. It means that Hajime infects device2, i.e., Hajime at P3 produces a copy of itself into P2, and the copy infects device2. This results in a new state
shown in Figure 2a.
In , there are three firable transitions T6, T8, and T10 because, for each transition, x:delay can be bounded with t2 in . T1 is no longer firable in . This means that Hajime at P2 protects device2 from Mirai. Let us fire T6 three times. It means that the delay time of three steps passed. This results in a new state
shown in Figure 2b.
In , T5 becomes firable because x:m_reboot and y:reboot can be respectively bounded with t2 in at P1 and t5 in at P1. Let us fire T5. It means a reboot of device1, i.e., Mirai at P1 is deleted and device1 gets back to normal. This results in a new state
shown in Figure 2c.
Using the PN model, Yamaguchi et al. [14,19] have evaluated the effect of Hajime against Mirai. They used the PN model representing a lattice-structured network. The network consists of 25 (=) nodes and each node has one device. They measured Mirai’s infection rate after 1000 steps. is given by
where is the number of devices and is the number of devices infected by Mirai. The parameters are as follows:
- The delay time until rebooting = 0, 1, 2, 3, or 4 steps.
- The initial number of devices infected by Mirai = 1.
- The initial number of devices infected by Hajime = 0, 1, 2, or 3.
Mirai and/or Hajime were initially put at random nodes.
Table 1 shows the simulation result. Each value is the mean of for 10000 trials. The result is illustrated in Figure 3. The horizontal axis shows the delay time until rebooting. The vertical axis shows Mirai’s infection rate . First, let us see the effect of only reboot, i.e., when . Rebooting infected devices drastically reduces the value of when , but the effect is rapidly lost with the increase in . This is consistent with the fact [20] that, if the devices are not updated on security, they can be reinfected within minutes of the reboot. Next, let us see on the effect of Hajime, i.e., when . Hajime reduces the value of to less than half without depending on . decreased with the increase in , but the reduction rate gradually decreased. The reason is that the network became saturated with Hajime.

Table 1.
Effect of Hajime against Mirai.
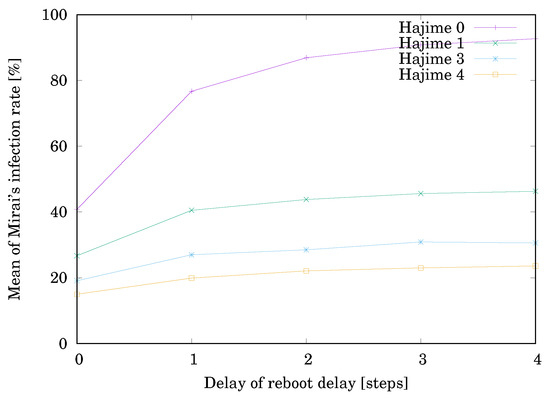
Figure 3.
Effect of Hajime against Mirai.
3. White-Hat Worm
3.1. Analysis and Design
The number of IoT devices is exponentially increasing. This fact makes Mirai’s threat more serious. We need to manage their vulnerability against Mirai, but human-wave tactics are unrealistic because of the huge amount. In this paper, we propose a new approach that uses a white-hat worm to fight Mirai.
Hajime actually protects IoT devices from Mirai’s infection. However, a new problem appears here. Those devices became infected by Hajime instead. Is Hajime a white-hat worm? Once Hajime infects an IoT device, it displays a message for warning the user. At present, there is not any DDoS capability in Hajime. However, Hajime can add new capabilities on the fly, which is an unfavorable attribute. In addition, Hajime continues to stay at the infected device even though completing the defense against Mirai. From these reasons, Hajime is said to be gray-hat.
We extend Hajime to become a white-hat worm. The white-hat worm should not stay at the device once the protection completed. To achieve this, we introduce a concept of lifespan. The white-hat worm destructs itself when exhausting the lifespan. We also introduce a concept of secondary infectivity, which is the ability to infect a device infected by Mirai. This enables the white-hat worm to drive out Mirai.
3.2. Modeling
To express a battle between Mirai and the white-hat worm, we extend the PN model described in Section 2.2. The extended PN model is denoted by and is shown in Figure 4. The agent net of Figure 4b represents the state-transition of the white-hat worm. It is an extension of of Figure 1b. Transition t3 labeled as m_die represents a self-destruction action. Transition t4 labeled as h_2infect represents a secondary infection action.
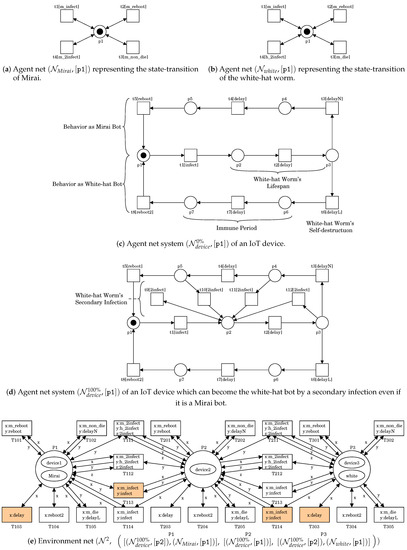
Figure 4.
A PN system representing a battle between Mirai and the white-hat worm.
The agent net of Figure 4a represents the state-transition of Mirai. It is the same structure as . However, transition t3 is labeled as m_non_die and represents an action of doing nothing unlike the white worm’s self-destruction action. Transition t4 is labeled as m_2infect and represents a secondary infection action by the white-hat worm.
The agent net of Figure 4c represents the state-transition of an IoT device. It is an extension of of Figure 1c. For symbol , its superscript “” indicates the possibility of the white-hat worm’s secondary infection. That is, this white-hat worm does not have any secondary infectivity against Mirai. has a branch structure at place p3. Which transition t3 or t6 to fire is decided by dynamic binding. If this device is infected by Mirai, t3 would fire. The upper cycle p1t1p2t2p3t3p4t4p5t5p1 represents the behavior as a Mirai bot. If this device is infected by the white-hat worm, t6 would fire. The lower cycle p1t1p2t2p3t6p6t7p7t8p1 represents the behavior as a white-hat bot. Note that each cycle corresponds to of Figure 1c. In this example, the white-hat worm’s lifespan is assumed to be one step, of which the delay is represented by transition t2. t6 labeled as delayL represents the white-hat worm’s self-destruction action. Note that the remaining time until reboot means the period of immunity provided by the white-hat worm.
Figure 4d shows the agent net , where the possibility of this white-hat worm’s secondary infection is 100%. That is, the white-hat worm can always infect the device infected by Mirai. In , the four states and mean that the device is a Mirai bot. Transitions t9, t10, t11, and t12 respectively represent the white-hat worm’s secondary infection actions. The firing of one transition results in the state in which the white-hat worm infected the device instead of Mirai. Since those four transitions one-to-one correspond to all of the four states, the white-hat worm’s secondary infection becomes 100%. We can specify any possibility of the white-hat worm’s secondary infection by the presence of those transitions.
3.3. Simulation
We can simulate the battle between Mirai and the white-hat worm by using the PN model proposed in Section 3.2. Figure 5 shows an execution of . Note that is shown in Figure 4e. In , there are four firable transitions T103, T113, T214, and T303. Let us fire T113. It means that Mirai infects device2. This results in a new state
shown in Figure 5a.
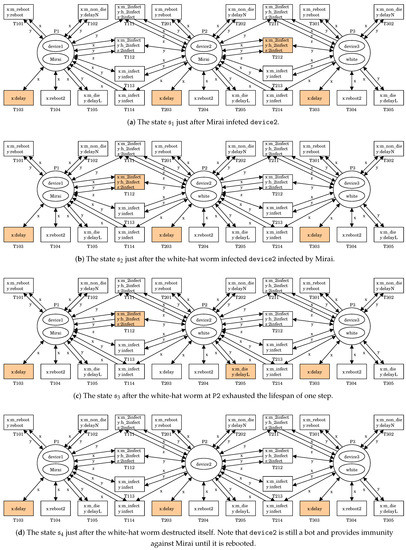
Figure 5.
An execution of .
In , there are four firable transitions T103, T203, T212, and T303 because
- For T103, T203, or T303, x:delay can be bounded with t2 in .
- For T212, x:m_2infect, y:h_2infect and z:2infect can be respectively bounded with t4 in at P2, t4 in at P3 and t9 in at P2.
Let us fire T212. It means the white-hat worm’s secondary infection for device2 infected by Mirai, i.e., the white-hat worm at P3 removes Mirai from P2 and produces a copy of itself into P2, and the copy infects device2. This results in a new state
shown in Figure 5b.
In , there are four firable transitions T103, T112, T203, and T303 because
- For T103, T203, or T303, x:delay can be bounded with t2 in .
- For T112, x:m_2infect, y:h_2infect and z:2infect can be respectively bounded with t4 in at P1, t4 in at P2 and t9 in at P1.
Let us fire T203. It means that the white-hat worm exhausts the lifespan of one step. This results in a new state
shown in Figure 5c.
In , there are four firable transitions T103, T112, T205, and T303. For T205, x:m_die and y:delayL can be respectively bounded with t3 in at P2 and t6 in at P2. Let us fire T205. It means that the white-hat worm destructs itself. This results in a new state
shown in Figure 5d. Note that device2 is still a bot and provides immunity against Mirai until it is rebooted.
4. Simulation Evaluation
We performed an experiment to evaluate the effect of the white-hat worm. In this experiment, we used the PN model representing a lattice-structured network composed of 25 (=) nodes, i.e., = 25. Each node has one device. Figure 6 illustrates the model.
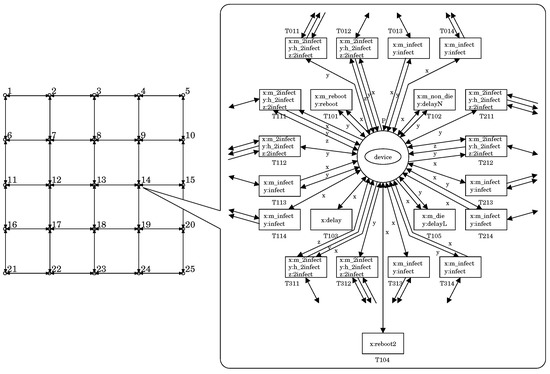
Figure 6.
Illustration of the PN model used in the experiment.
Let us first focus on the white-hat worm’s lifespan. We measured Mirai’s infection rate given by Equation (1) and the white-hat worm’s infection rate after 1000 steps. is given by
where is the number of devices infected by the white-hat worm. The parameters are as follows:
- The delay time until rebooting = 7 or 11 steps,
- The initial number of devices infected by Mirai = 12,
- The initial number of devices infected by the white-hat worm = 5,
- The white-hat worm’s lifespan ℓ = 1, 3, or 5 steps,
- The white-hat worm’s secondary infection possibility = 100%.
The simulation results are shown in Table 2. Table 2a shows Mirai’s infection rate and the white-hat worm’s infection rate when the delay time until rebooting . Table 2b shows and when . Each value is the mean of or for 10,000 trials. The grayed cell means that the value is getting worse than the initial one. Figure 7a,b respectively illustrate the tables. The horizontal axis shows the white-hat worm’s lifespan ℓ. The vertical axis shows and . In both cases, was rapidly decreasing with increasing ℓ. In contrast, started at zero when and increased with increasing ℓ. This means that, if the lifespan is short, it successfully reduces the white-hat worm’s remaining.

Table 2.
Effect of the white-hat worm’s lifespan ℓ on Mirai’s and the white-hat worm’s infection rates. (a) Delay time until rebooting = 7; (b) Delay time until rebooting = 11.
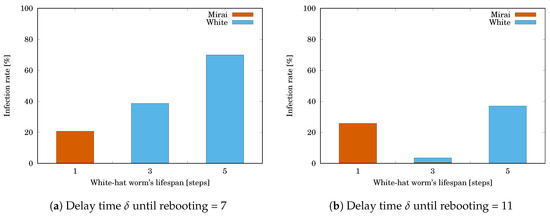
Figure 7.
Effect of the white-hat worm’s lifespan ℓ on Mirai’s and the white-hat worm’s infection rates.
Next, let us focus on the white-hat worm’s secondary infectivity. We measured and after 1000 steps by varying the following parameters.
- The white-hat worm’s secondary infection possibility = 0, 25, 50, 75, or 100%
The other parameters are the same as the previous simulation.
The simulation results are shown in Table 3 and Table 4. Table 3a,b respectively show when and 11. Table 4a,b respectively show when and 11. Each value is the mean of or for 10,000 trials. The grayed cell means that the value is getting worse than the initial one. Figure 8a,b respectively illustrate when and 11. The horizontal axis shows the white-hat worm’s secondary infection possibility . The vertical axis shows . was decreasing with increasing . Note that the decreasing rate depends on the lifespan ℓ. Figure 9a,b respectively illustrate when and 11. The horizontal axis shows . The vertical axis shows . was increasing with increasing and reached a ceiling. Note that the increasing rate depends on ℓ. The result means that, if is low, the white-hat worm’s effect depends on ℓ. If is high, the worm is effective without depending on ℓ.

Table 3.
Effect of the white-hat worm’s secondary infectivity on Mirai’s infection rate when . (a) Delay time until rebooting = 7; (b) Delay time until rebooting = 11.

Table 4.
Effect of the white-hat worm’s secondary infectivity on the worm’s infection rate when . (a) Delay time until rebooting = 7; (b) Delay time until rebooting = 11.
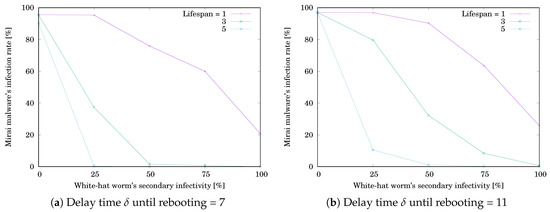
Figure 8.
Effect of the white-hat worm’s secondary infectivity on Mirai’s infection rate when .
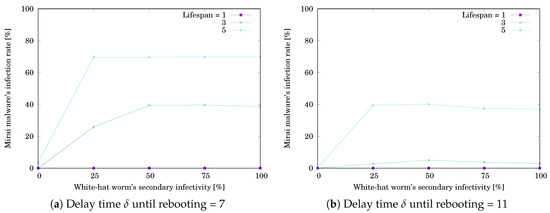
Figure 9.
Effect of the white-hat worm’s secondary infectivity on the worm’s infection rate when .
The effect of the white-hat worm would be influenced by the other factors, e.g., the number of nodes, the connectivity of the nodes, and so on. To investigate how much the number of nodes affects the effect, we performed another experiment. In this experiment, we used the PN model representing a larger lattice-structured network. The network consists of 36 () nodes, i.e., = 36. We measured and after 1000 steps. The parameters are as follows:
- The initial number of devices infected by Mirai = 18,
- The initial number of devices infected by the white-hat worm = 7.
The other parameters are the same as the previous simulation.
The simulation results are shown in Table 5 and Table 6. Table 5a,b respectively show when and 11. Table 6a,b respectively show when and 11. Each value is the mean of or for 1000 trials. The grayed cell means that the value is getting worse than the initial one. Figure 10 and Figure 11 respectively illustrate Table 5 and Table 6. The horizontal axis shows the white-hat worm’s secondary infection possibility . The vertical axis shows or . was decreasing with increasing , while was increasing with increasing and reached a ceiling. However, the changing rates depend on ℓ. Comparing the results for and 36, we see that the trend is similar. We can say that secondary infectivity and lifespan are more important factors than the number of nodes.

Table 5.
Effect of the white-hat worm’s secondary infectivity on Mirai’s infection rate when . (a) Delay time until rebooting = 7; (b) Delay time until rebooting = 11.

Table 6.
Effect of the white-hat worm’s secondary infectivity on the worm’s infection rate when . (a) Delay time until rebooting = 7; (b) Delay time until rebooting = 11.
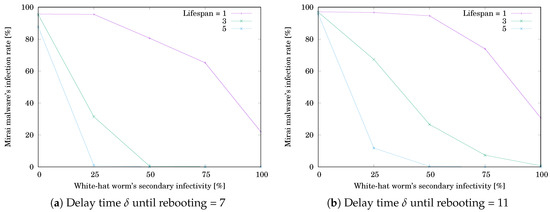
Figure 10.
Effect of the white-hat worm’s secondary infectivity on Mirai’s infection rate when .
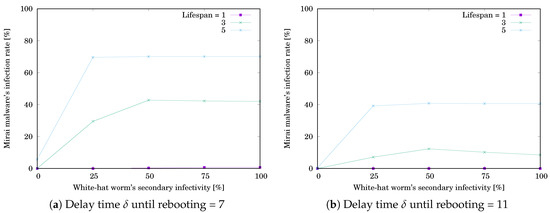
Figure 11.
Effect of the white-hat worm’s secondary infectivity on the worm’s infection rate when .
5. Conclusions
In this paper, we proposed a new approach that uses a white-hat worm to fight malware. We designed the white-hat worm by introducing the concept of lifespan and secondary infectivity to Hajime. The white-hat worm destructs itself when exhausting the lifespan. In addition, it can drive out Mirai from the infected device. We expressed the white-hat worm with PN and performed the simulation for evaluating the effect of the white-hat worm against Mirai. The result of the simulation evaluation shows that (i) the lifespan successfully reduces the white-hat worm’s remaining if short; (ii) if the worm has low secondary infectivity, its effect depends on the lifespan; and (iii) if the worm has high secondary infectivity, it is effective without depending on the lifespan.
In future work, we are going to work up the proposed white-hat worm into a new kind of cybersecurity systems, named Botnet Defense System (BDS) [21], which defends a network system against malicious botnets.
Funding
This work was supported by JSPS KAKENHI Grant No. JP19K11965.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Sinaović, H.; Mrdovic, S. Analysis of Mirai malicious software. In Proceedings of the 25th International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Split, Croatia, 21–23 September 2017; pp. 1–5. [Google Scholar]
- Nakao, K. Proactive cyber security response by utilizing passive monitoring technologies. In Proceedings of the 36th IEEE International Conference on Consumer Electronics (ICCE 2018), Las Vegas, NV, USA, 12–14 January 2018. [Google Scholar]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and other botnets. IEEE Comput. 2017, 50, 80–84. [Google Scholar] [CrossRef]
- US Computer Emergency Readiness Team. Heightened DDoS Threat Posed by Mirai and Other Botnets. alert TA16-288A. Available online: Https://www.us-cert.gov/ncas/alerts/TA16-288A (accessed on 29 October 2019).
- Edwards, S.; Profetis, I. Hajime: Analysis of a Decentralized Internet Worm for IoT Devices. Available online: Http://security.rapiditynetworks.com/publications/2016-10-16/Hajime.pdf (accessed on 29 October 2019).
- Tanaka, H.; Yamaguchi, S. On modeling and simulation of the behavior of IoT devices malwares Mirai and Hajime. In Proceedings of the IEEE International Symposium on Consumer Electronics (ISCE), Kuala Lumpur, Malaysia, 14–15 November 2017; pp. 56–60. [Google Scholar]
- Hiraishi, K. A Petri-net-based model for the mathematical analysis of multi-agent systems. IEICE Trans. Fundam. 2001, 84, 2829–2837. [Google Scholar]
- Yamaguchi, S.; Gupta, B.B. Malware Threat in Internet of Things and Its Mitigation Analysis. In Security, Privacy, and Forensics Issues in Big Data; Joshi, R.C., Gupta, B.B., Eds.; Business Science Reference: Hershey, PA, USA, 2019; pp. 363–379. [Google Scholar]
- Bezerra, V.H.; da Costa, V.G.T.; Barbon, J.; Miani, R.S.; Zarpelão, B.B. IoTDS: A One-Class Classification Approach to Detect Botnets in Internet of Things Devices. Sensors 2019, 19, 3188. [Google Scholar] [CrossRef] [PubMed]
- Liu, X.; Du, X.; Zhang, X.; Zhu, Q.; Wang, H.; Guizani, M. Adversarial Samples on Android Malware Detection Systems for IoT Systems. Sensors 2019, 19, 974. [Google Scholar] [CrossRef] [PubMed]
- Ceron, J.M.; Steding-Jessen, K.; Hoepers, C.; Granville, L.Z.; Margi, C.B. Improving IoT Botnet Investigation Using an Adaptive Network Layer. Sensors 2019, 19, 727. [Google Scholar] [CrossRef] [PubMed]
- Grange, W. Hajime Battles Mirai for Control of the Internet of Things. Available online: Https://www.symantec.com/connect/blogs/Hajime-worm-battles-Mirai-control-internet-things (accessed on 29 October 2019).
- Molesky, M.J.; Cameron, E.A. Internet of Things: An Analysis and Proposal of White Worm Technology. In Proceedings of the 37th IEEE International Conference on Consumer Electronics (ICCE 2019), Las Vegas, NV, USA, 11–13 January 2019. [Google Scholar]
- Yamaguchi, S.; Tanaka, H.; Bin Ahmadon, M.A. Modeling and Evaluation of Mitigation Methods against IoT Malware Mirai with Agent-Oriented Petri Net PN2. Int. J. Internet Things Cyber Assur. 2019. [Google Scholar] [CrossRef]
- Nakahori, K.; Yamaguchi, S. A support tool to design IoT services with NuSMV. In Proceedings of the 35th IEEE International Conference on Consumer Electronics (ICCE 2017), Las Vegas, NV, USA, 8–10 January 2017; pp. 84–87. [Google Scholar]
- Yamaguchi, S.; Bin Ahmadon, M.A.; Ge, Q.W. Introduction of Petri Nets: Its Applications and Security Challenges. In Handbook of Research on Modern Cryptographic Solutions for Computer and Cyber Security; Gupta, B.B., Agrawal, D.P., Yamaguchi, S., Eds.; IGI Publishing: Hershey, PA, USA, 2016; pp. 145–179. [Google Scholar]
- García-Magariño, I.; Gómez-Rodríguez, A.; González-Moreno, J.C.; Palacios-Navarro, G. PEABS: A Process for developing Efficient Agent-Based Simulators. Eng. Appl. Artif. Intell. 2015, 46 Pt A, 104–112. [Google Scholar] [CrossRef]
- García-Magariño, I.; Lacuesta, R. ABS-TrustSDN: An Agent-Based Simulator of Trust Strategies in Software-Defined Networks. Secur. Commun. Netw. 2017, 3, 1–9. [Google Scholar] [CrossRef]
- Tanaka, H.; Yamaguchi, S.; Mikami, M. Quantitative Evaluation of Hajime with Secondary Infectivity in Response to Mirai’s Infection Situation. In Proceedings of the 8th IEEE Global Conference on Consumer Electronics (GCCE 2019), Osaka, Japan, 15–18 October 2019; pp. 985–988. [Google Scholar]
- Moffitt, T. Source Code for Mirai IoT Malware Released. Available online: Https://www.webroot.com/blog/2016/10/10/source-code-Mirai-iot-malware-released/ (accessed on 4 November 2019).
- Yamaguchi, S. Botnet Defense System: Concept and Basic Strategy. In Proceedings of the 38th IEEE International Conference on Consumer Electronics (ICCE 2020), Las Vegas, NV, USA, 4–6 January 2020. [Google Scholar]
© 2020 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).