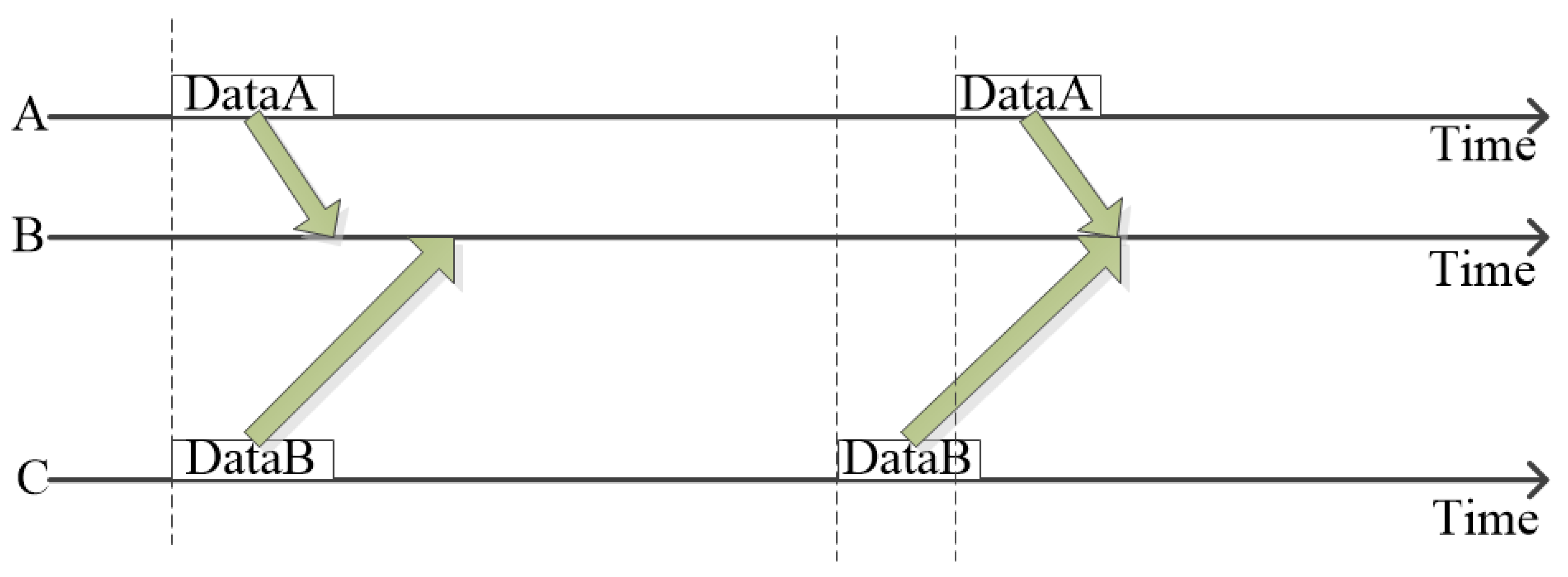
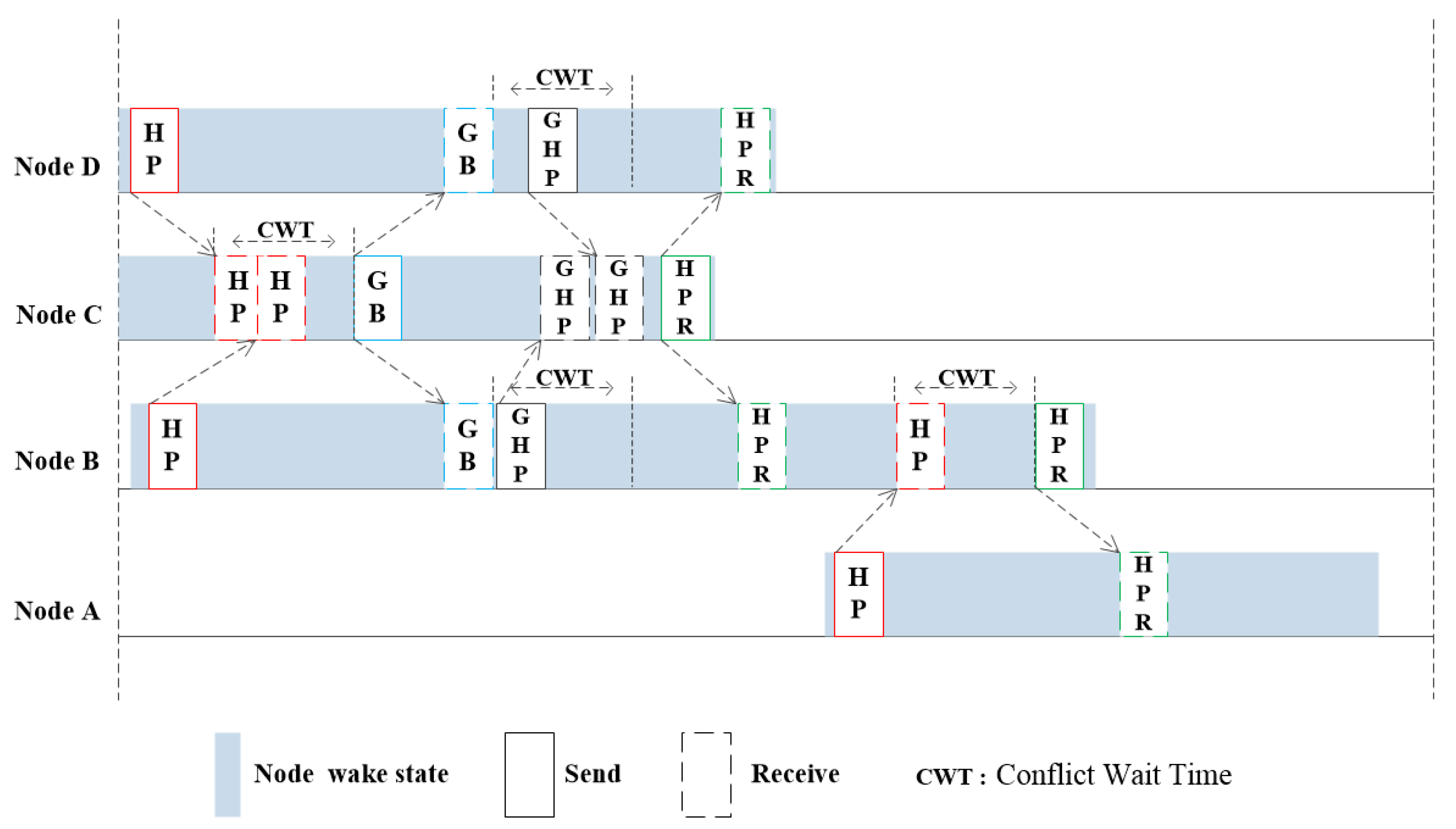
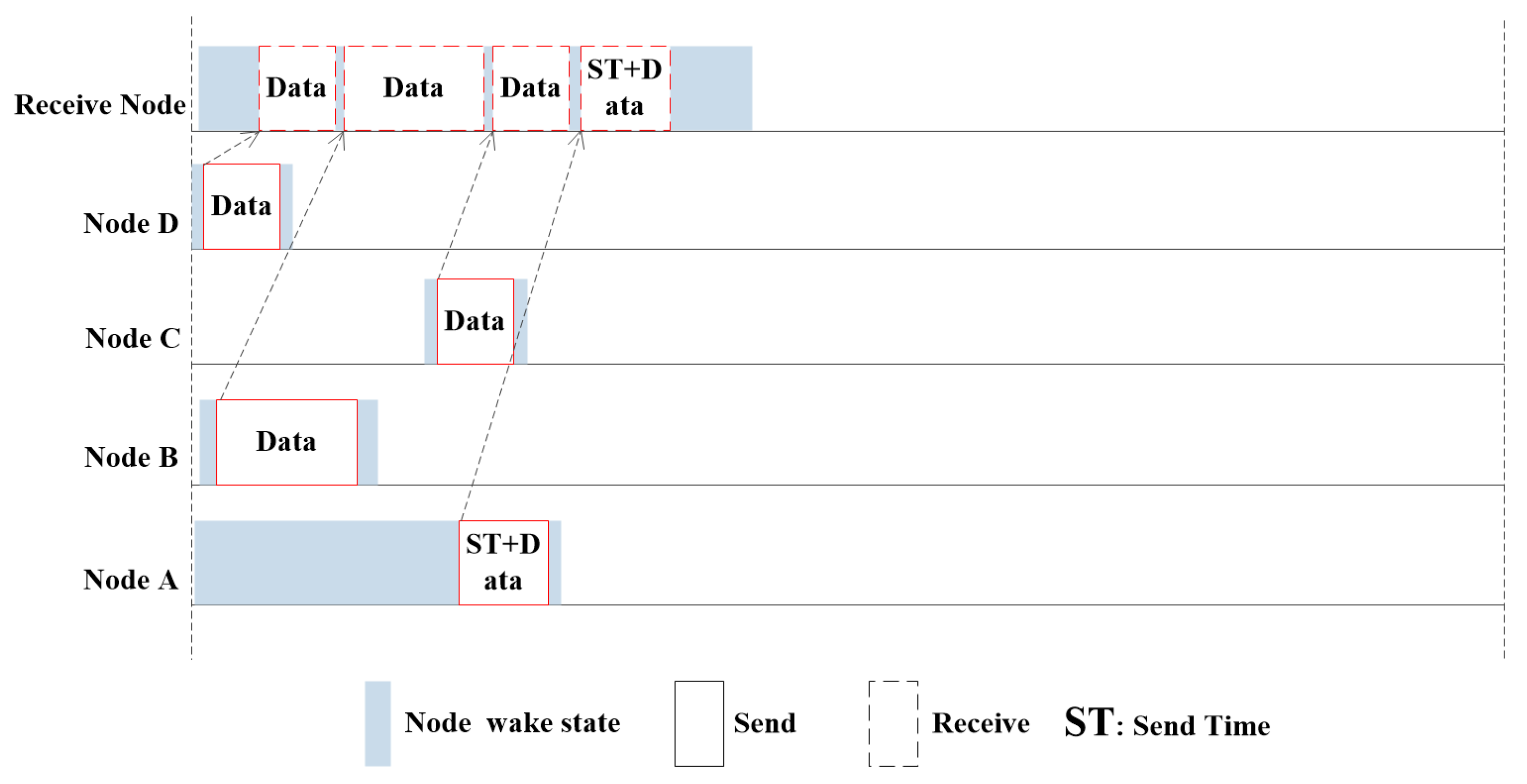
Based on NS2.3+Aqua-Sim simulation platform, we analyze the performance differences of DCN-MAC, SFAMA and ST-lohi. Both DCN-MAC and SFAMA protocols use the interaction of control packets to implement channel allocation. The difference is that the SFAMA protocol only completes a pair of nodes’ data transmission in each handshake. In DCN-MAC, the nodes exchange control packets to determine the transmission schedule, and once more handshake, the transmission of multiple data packets is achieved. The collision avoidance mechanism of DCN-MAC is similar to ST-lohi protocol. The ST-lohi protocol listens to the number of sending nodes in a period, then determines the back-off window period, and randomly sends contention channels during the back-off period. In the DCN-MAC, the scheduling node counts the number of nodes to be sent, and then obtains the information of multiple nodes in only one cycle to achieve scheduling. Compared with the larger backoff window of the ST-lohi protocol, it has higher efficiency.
4.2. Performance Evaluation
4.2.1. Throughput
In this part, we mainly consider the network throughput under different network load, MAC protocol and node density. We compared the throughput of SFAMA, St LoHi and DCN-MAC in different node number environments with data packets generation rate. In the analysis, we defined the throughput as the number of bits transmitted by the network per unit time (BPS). The calculation method is shown in (
10), and the simulation results are shown in
Figure 6.
From the overall trend, the throughput of the three protocols increased first and then decreased with the growth of network load. This is because when the network load was too large, the protocols caused the throughput to drop because the number of packet conflict was increased and the nodes avoided more often.
Firstly, we analyzed the 18 nodes. When the node packet delivery rate was 0.002, the throughput performance of the three protocols was basically the same. However, when the packet generation rate rose a little, the performance of SFAMA protocol dropped sharply to only about 20 bps. It can be seen that the SFAMA protocol could not effectively handle the multi-node data conflict when the network load was high. This is because the SFAMA protocol needed to wait twice the maximum propagation delay of the network for each control packet transmission, thus causing more nodes to conflict. In addition, SFAMA protocol used the random avoidance of nodes to deal with conflict. It also introduced a large delay, which made the probability of conflicts increase again. The throughput of ST-lohi and DCN-MAC protocols was in the rising phase when the node’s packet delivery rate was in the phase of 0–0.01 packets per second, and the curves were basically consistent. However, when the packet delivery rate continued to rise, the throughput of ST-lohi protocol began to stabilize until the packet delivery rate was greater than 0.03. What is more, the throughput of DCN-MAC protocol declined until the packet delivery rate exceeds 0.04, and after the packet delivery rate exceeded 0.01, the throughput of DCN-MAC protocol was about 40% higher than that of ST-lohi protocol. The reason for this trend is that DCN-MAC protocol did not need all the nodes to avoid randomly according to the number of conflict nodes when dealing with multi-node conflict. It could schedule the data RTS of multi-node in a avoidance cycle. In contrast, when dealing with multi-node conflicts, the ST-lohi protocol required multiple nodes to perform the same avoidance algorithm according to the number of conflicting nodes N. It took at least N cycles to complete the processing of this conflict.
Then the throughput performance of the three protocols in different network scenarios was compared horizontally. In all three cases, the DCN-MAC protocol had the highest throughput, especially after network load increased, the DCN-MAC protocol performed better than the others. When the number of nodes was 10, the SFAMA protocol also showed a low throughput due to the huge network load and its own conflict avoidance mechanism. However, compared with 18 nodes, the throughput was increased to about 60 bps, because the overall network load was lower than the scenario of 18 nodes, so the throughput was improved. ST-lohi protocol and DCN-MAC protocol were similar in the scenario of 10 nodes and 18 nodes, and the trend was basically the same. Compared with 18 nodes, the maximum throughput of the two protocols was reduced by about 50 bps, and the degree of the priority in DCN-MAC protocol was reduced to about 20%. In the case of three nodes, it can be seen that the performance of the SFAMA protocol was significantly improved, and the throughput of the three protocols was basically the same when the packet delivery rate was less than 0.01. When the packet delivery rate was increased to 0.01, the throughput of SFAMA protocol tended to be stable at around 100 bps. However, the throughput of ST-lohi and DCN-MAC protocols continued to grow, and the change of DCN-MAC was more obvious than ST-lohi, and the performance of DCN-MAC was about 30% better than ST-lohi. The reason for this trend is that ST-lohi’s conflict avoidance mechanism still had a large probability of packet loss when dealing with multi-node conflicts, resulting in lower throughput.
In summary, the SFAMA protocol performed better than the other simulated protocols when the network load was low, and the protocol was relatively easy to implement. However, due to the fact that the SFAMA protocol could not effectively handle multi-node conflicts, so its performance decreased rapidly after the network load increased. Therefore, this protocol is more suitable for some network application scenarios where the number of nodes is low and the packet delivery rate is not high. The throughput performance of the ST-lohi protocol and the DCN-MAC protocol are basically the same at low network load, but the throughput of the DCN-MAC protocol is higher after the network load is further increased, which is about 35% higher than the ST-lohi protocol.
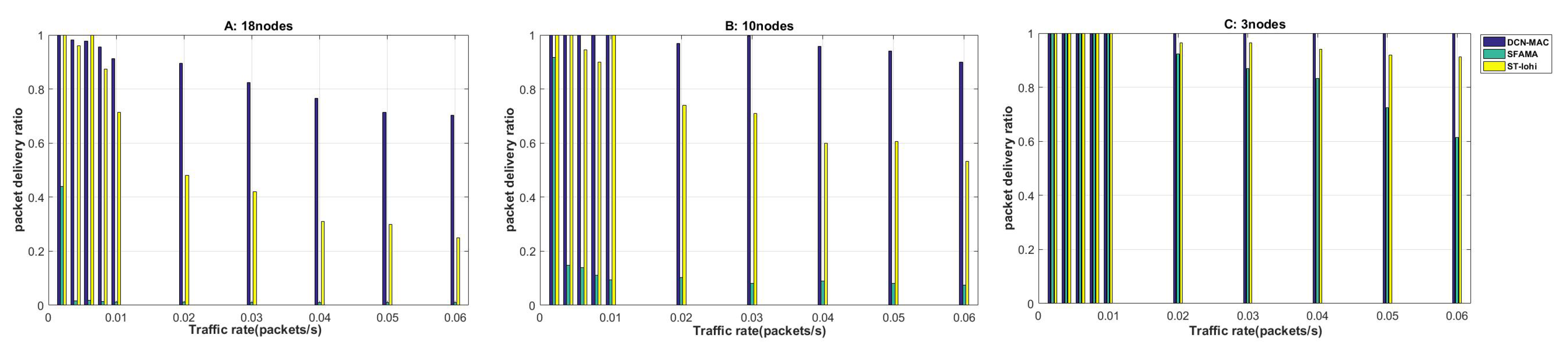
4.2.2. Delivery Ratio
The delivery ratio reflects the ability of the underwater acoustic network to process multi-node data packets. Generally, in the case of higher network load, the delivery ratio will be increased due to conflicts between data packets, which may result in the protocol failing to process these conflicting data packets in time, thereby reducing the delivery ratio. Therefore, the performance of delivery ratio directly reflects the conflict avoidance ability of underwater protocols. Here we define the delivery ratio as the number of packets successfully received by the receiving node compared to the total number of packets generated in the network. The calculation method is shown in (
11), and the simulation results are shown in
Figure 7. First, observe
Figure 7 from a macro perspective. We can see that the trend of delivery ratio of the three protocols was consistent with the trend of throughput change in
Figure 7. A high delivery ratio at the same packet delivery rate indicated a higher throughput of the corresponding protocol. This is because we calculate the throughput of the protocol based on the number of packets successfully received by the receiving node and the number of bits in the packet in a period of time. The delivery ratio of the MAC protocol was stable for a period of time as the network load increased, and then began to show a downward trend.
First, we analyzed the situation of 18 nodes. When the node’s packet delivery rate was 0.002, the delivery ratio of ST-lohi and DCN-MAC could reach 1, and the delivery ratio of SFAMA protocol was only about 0.4. When the data packet generation rate rose slightly, the performance of the SFAMA protocol dropped sharply to zero; that is, the data packets were basically lost at this time. This is because the SFAMA protocol needed to wait twice the maximum propagation delay of the network for each control packet transmission, and the nodes avoided randomly after the conflict occurred, thus causing more nodes to conflict. When the packet delivery rate was in the 0–0.01 phase, the delivery ratio of both ST-lohi and DCN-MAC protocols were basically stable below 1. When the packet delivery rate exceeded 0.01, the delivery ratio of the ST-lohi protocol began to decline first, and the rate of decline was always higher than the DCN-MAC protocol. In the process of decline, the delivery ratio of the DCN-MAC protocol maintained a 50% lead compared to ST-lohi. This trend indicates that the conflict avoidance mechanism of the ST-lohi protocol was not as robust as the mechanism of the DCN-MAC protocol. The DCN-MAC protocol performed better under the same network load. The reason for this trend is that the DCN-MAC protocol did not require all nodes to avoid randomly according to the number of conflicting nodes when dealing with multi-node conflicts. It could schedule data RTS for multiple nodes in an avoidance cycle. In contrast, the ST-lohi protocol required multiple nodes to perform the same avoidance algorithm according to the number of conflicting nodes N when dealing with multi-node conflicts. It took at least N cycles to complete the processing of this conflict.
Later, the delivery ratio of the three protocols in different network scenarios was compared horizontally. In all three cases, the delivery ratio of the DCN-MAC protocol remained the highest, especially after the network load increaseed, the DCN-MAC protocol performed better than the others. When the number of nodes was 10, the network load was still relatively high. Therefore, at this time, the SFAMA protocol also presented a lower delivery ratio because of its own conflict avoidance mechanism. However, compared with the results of 18 nodes, the delivery ratio obviously increased, and the stability was around 0.1. The ST-lohi and DCN-MAC protocols showed the same trend in 10 nodes and 18 nodes. The delivery ratio of the two protocols was 30% higher than that of the 18 nodes, and the performance lead of the DCN-MAC protocol was reduced to 30%. This performance is consistent with the simulation results of throughput performance. In the case of three nodes, we can see that the performance of the SFAMA protocol was significantly improved. When the packet delivery rate is less than 0.01, the delivery ratio of the three protocols is 1. At this time, the data packets in the network could be 100% processed. When the node’s packet delivery rate was increased to 0.01, and the delivery rate was reduced from the 100% delivery ratio at the packet delivery rate of 0.01 to the delivery ratio of 0.6 at the packet delivery rate of 0.06. The delivery ratio of the ST-lohi protocol also decreased, but the minimum has a delivery ratio of 0.9. The DCN-MAC protocol performed better, and the delivery ratio remained at 1 during the change in the packet delivery rate from 0 to 0.06.
In summary, the SFAMA protocol had a high delivery ratio when the network load was low, but the protocol could not be effectively processed the multi-node conflict. Therefore, the delivery ratio of the SFAMA protocol dropped rapidly after the network load increased. If the network load was too high, there may have been a case where the delivery ratio was zero. The delivery ratio of the ST-lohi protocol and the DCN-MAC protocol was basically the same at low network load, but the DCN-MAC protocol delivered a higher delivery ratio when the network load was further improved, with an average lead of around 35% of the ST-lohi protocol.
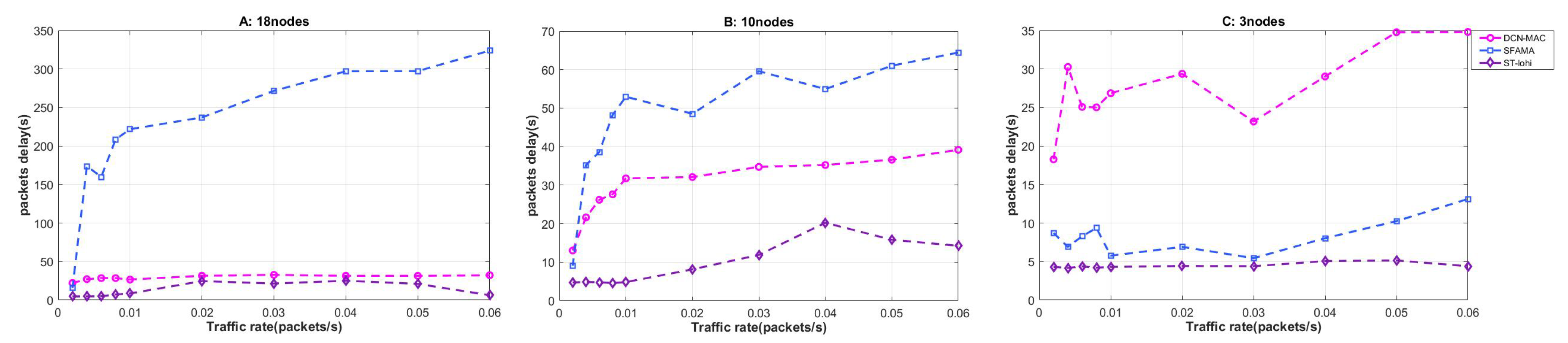
4.2.3. Packet Delay
Packet delay reflects the timeliness of network processing the node bursting data packet. The low packet delay means that the protocol handles the data faster, and the data processing is not delayed due to the mechanism of the protocol itself. In the underwater acoustic network, since the propagation delay of underwater acoustic communication is long, packet delay is an important performance to examine the underwater MAC protocol. In the simulation experiment, we defined the packet delay as: the time it took for a node to randomly generate a data packet to the node was served. The calculation method is shown in (
12), and the simulation results are shown in
Figure 8.
First, observe
Figure 8 from a macro perspective. It can be seen that the packet delay of ST-lohi and DCN-MAC protocols was not directly related to the network load, and both of them did not show an intuitive tendency with the increase of network load. The packet delay of the SFAMA protocol increased as the network load increased. It had the same packet delay as the ST-lohi protocol in a low network load environment.
Studying at the three protocols separately, we can find that the packet delay of the DCN-MAC protocol in three different network scenarios was distributed around 30 s, which is closely related to the mechanism of this protocol, because the DCN-MAC protocol is a kind of periodic wake-up and sleep of the receiving node according to the duty ratio cycle mechanism. The receiving node slept for 50 s and then woke up for 10 s to start data receiving periodically. That is to say, the DCN-MAC protocol did not process the data packet quickly after the packet was generated, but waited until the receiving node woke up and uniformly received the data packet. Therefore, the packet delay of the DCN-MAC protocol was limited by the protocol mechanism and remained at around 30 s.
The packet delay of the ST-lohi protocol basically maintainsedat about 5 s when the network load was low, and it increased with the increase of the network load. This is because the protocol firstly divided the time slots when implementing the channel allocation, and the length of each time slot was T = max + Td, where Td is the time spent for processing the tone signal. In the ST-lohi protocol, the node to be sent firstly sent a tone signal to contend the channel. If the tone signal of other nodes was not received in the same time slot, it was considered that it occupied the channel and could start the transmission of data.
Therefore, in the case of low network load and no multi-node conflict, the packet delay of the ST-lohi protocol was the length of two time slots (about 5 s). When the network load was increased, the node was backed off, so the packet delay was improved.
The packet delay of the SFAMA protocol had a large relationship with the network load. This is because the SFAMA protocol had a high probability of node conflict when the network load was high. From having a node with a data RTS to successfully send and receive a data packet, it had to go through many conflicts and avoidance. Therefore, it took a long time, resulting in a delay up to 300 s under a high network load. In the case of low network load, the packet delay of the SFAMA protocol was stable at around 10 s. This is because SFAMA was based on the handshake to complete the channel assignment. Whenever a node had a data request to send, it sent an RTS control packet, requesting to occupy the channel to send the data packet. If the node received the reply CTS control packet from the receiving node, it meant that no other node contended for the channel at this time. The node started to send data, and in the end the receiving node replied with an acknowledge character (ACK) control packet to mark the completion of the current data transmission. Therefore, four times of packet transmission was required in this process, resulting in a packet delay of approximately 10 s.
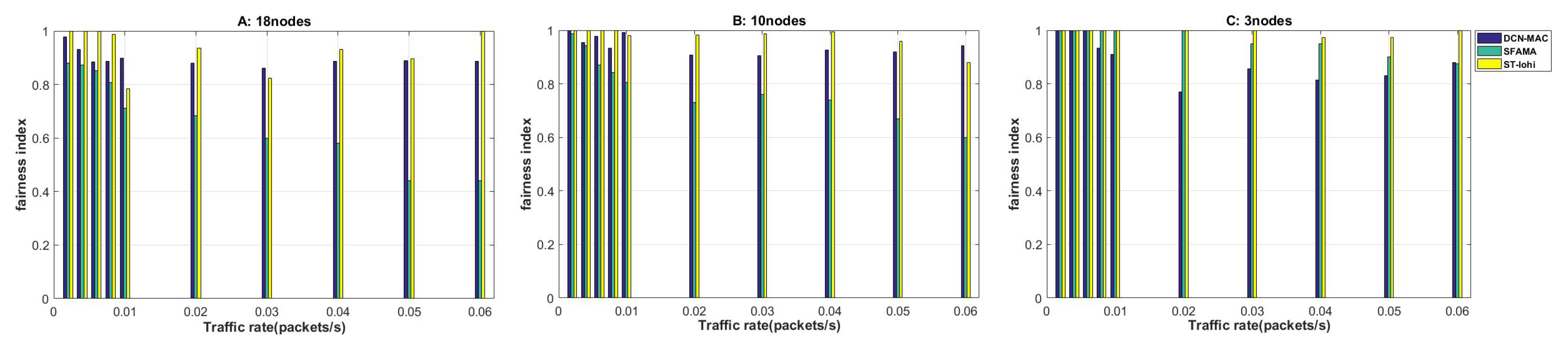
4.2.4. Fairness
The reason for examining the fairness performance is that the underwater acoustic channel has a long delay, and the node with a long distance will send the request first, but the node that is closer to the receiving node is processed first unfairly, due to the distance. The request acquisition of a distant node will not be processed, and the role of some sensor nodes is difficult to play. In the actual calculation, we calculate the fairness of the network by counting the data request order of the sending node and the service order of the receiving node. The calculation method is shown in (
13), and the simulation results are shown in
Figure 9.
Firstly, macroscopically observing the fairness results in the three network scenarios, we can find that the two protocols, SFAMA and ST-lohi, had strong links with the network load level, showing a trend of becoming fairer as the network load decreased. In addition, the fairness of the ST-lohi agreement always maintained a leading edge over SFAMA. The DCN-MAC protocol had consistent performance in different network loads, and the fairness of the network was stable at around 0.9.
The horizontal observation of the fairness of the SFAMA protocol in three scenarios showed that the fairness of the protocol varied widely among different network loads. SFAMA’s fairness could reach a maximum of 1, when the network load was small. When the network load increased, the fairness of the protocol was reduced to less than 0.5, and continued to decline. The fairness of the SFAMA protocol was so dependent on the degree of network load, which was caused by the mechanism of the protocol itself. The probability of conflict between nodes increased rapidly during high network load. The result of random avoidance caused the node data sent first to be post-processed or even lost, which seriously affected fairness.
The ST-lohi protocol was similar to the fairness trend of the SFAMA protocol, but the result was more than 20% ahead of the SFAMA protocol. It is because the ST-lohi protocol could make the sending node itself count the number of nodes that sent tone signals in the same time slot through the avoidance algorithm. It determined its own backoff behavior and did not need to wait to receive additional control packets from other nodes, which reduced the waiting time. Therefore, the multi-node conflict problem could be solved more efficiently, and the resulting unfairness between nodes was less.
The fairness of the DCN-MAC protocol was consistent in the three scenarios. When the network load was extremely low, the fairness was close to 1, but when the load was slightly increased, it stabilized at around 0.9. The reason why the fairness of the DCN-MAC protocol was low was not the conflict between multiple nodes, but the mechanism of the protocol itself. In order to further compress the total time used for receiving when calculating the sending table, there may have been a phenomenon that some nodes have data requests early but are serviced later. Therefore, the fair performance of the protocol was not optimal. In general, the fairness of the DCN-MAC protocol was limited by the mechanism of the protocol itself. It was difficult to achieve 100% fairness even in low network load, but it could reach 0.9 even at very high network loads. The SFAMA protocol had better network fairness only at low network load, and the fairness index was much lower than the DCN-MAC protocol and the ST-lohi protocol after the network load was increased. The fairness of performance of the ST-lohi protocol at high network load was similar to that of the DCN-MAC protocol, which led the DCN-MAC protocol by about 5% at low network load.
According to the simulation results: the advantage of the DCN-MAC protocol was that it could handle the conflicts generated during multi-node contention channels more efficiently. Moreover, the packet delay and fairness were basically stable, they did not drop sharply due to the increase of network load. Therefore, it had a greater advantage in the scenario of multi-node and high network load.