1. Introduction
The TSCH (Time-Slotted Channel Hopping) protocol [
1] is suitable for wireless network applications where high reliability and predictability is desired in conjunction with low power consumption. These include applications in industrial IoT [
2], smart homes for healthcare [
3], smart buildings [
4], agricultural monitoring [
5], and other areas.
Simulation is a critical step in the workflow of designing and deploying such networks. It is also an actively used research tool. To this end, the 6TiSCH (IPv6 over the TSCH mode of IEEE 802.15.4e) working group [
6] has developed the 6TiSCH simulator [
7]—a discrete event simulator that implements the TSCH and 6TiSCH protocols. Another frequently used tool for TSCH network research and validation is the Cooja simulator [
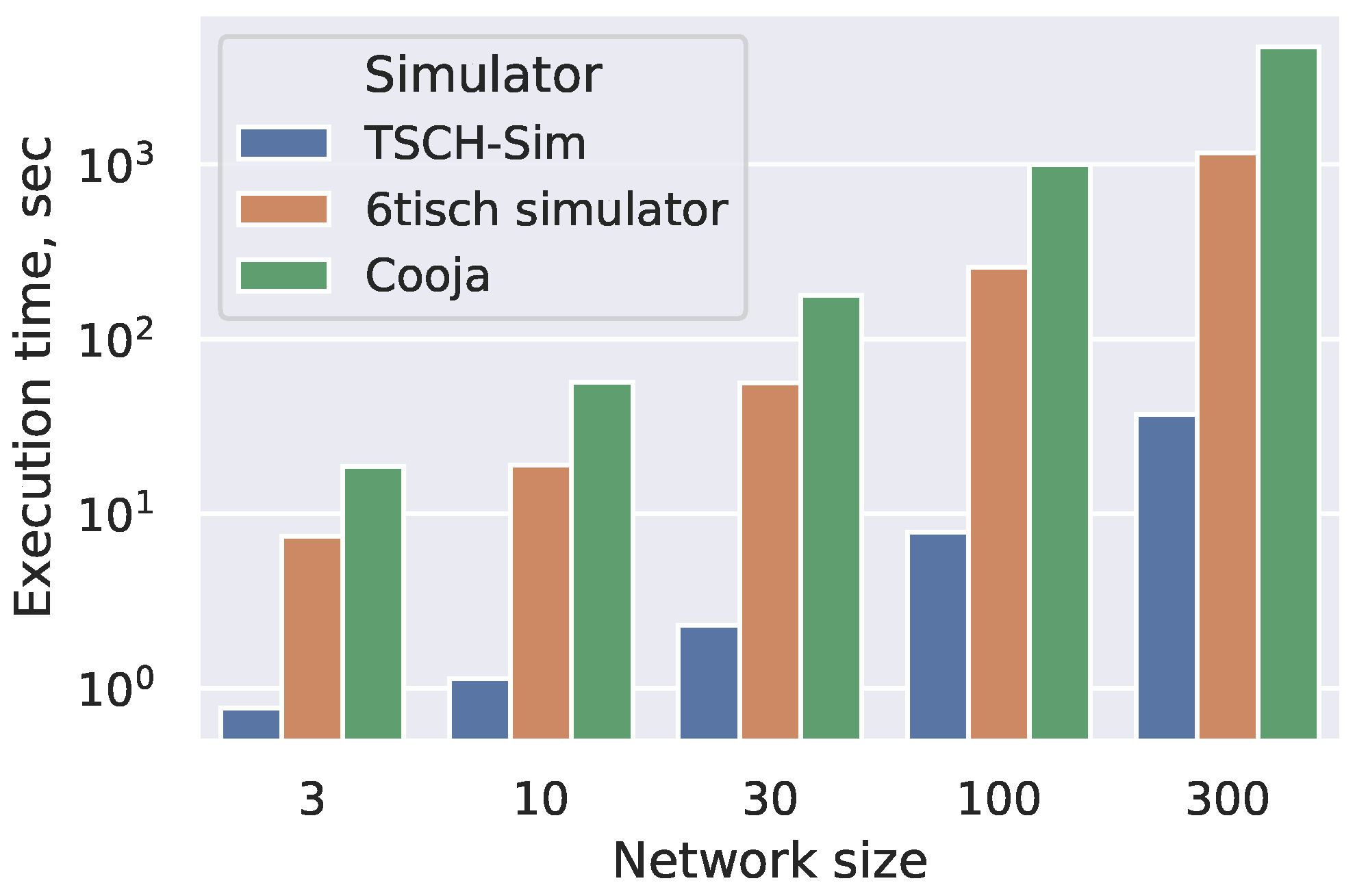
8], which allows use of the Contiki and Contiki-NG implementations of TSCH & 6TiSCH protocols in simulated environments. While highly useful, these simulators have limited scalability [
7] for simulations of large networks and when many scenarios need to be investigated (
Section 4). This problem is becoming more acute with each year, as IoT networks expand in popularity and in size, and TSCH starts to get applied to LoRa-based networks [
9] where large deployments are commonplace.
This paper presents TSCH-Sim: a new discrete event simulator for TSCH and 6TiSCH networks, available at
https://github.com/edi-riga/tsch-sim. TSCH-Sim is implemented in JavaScript with modules to facilitate extensions by users and integration with the Web. It supports the TSCH protocol as defined in the IEEE 802.15.4-2015 standard [
1], as well as aspects of the emerging 6TiSCH standards, including integration of TSCH with IPv6 and the RPL (Routing Protocol for Low-Power and Lossy Networks) protocol [
10]. It allows the selection of multiple schedulers including the 6TiSCH minimal schedule and Orchestra [
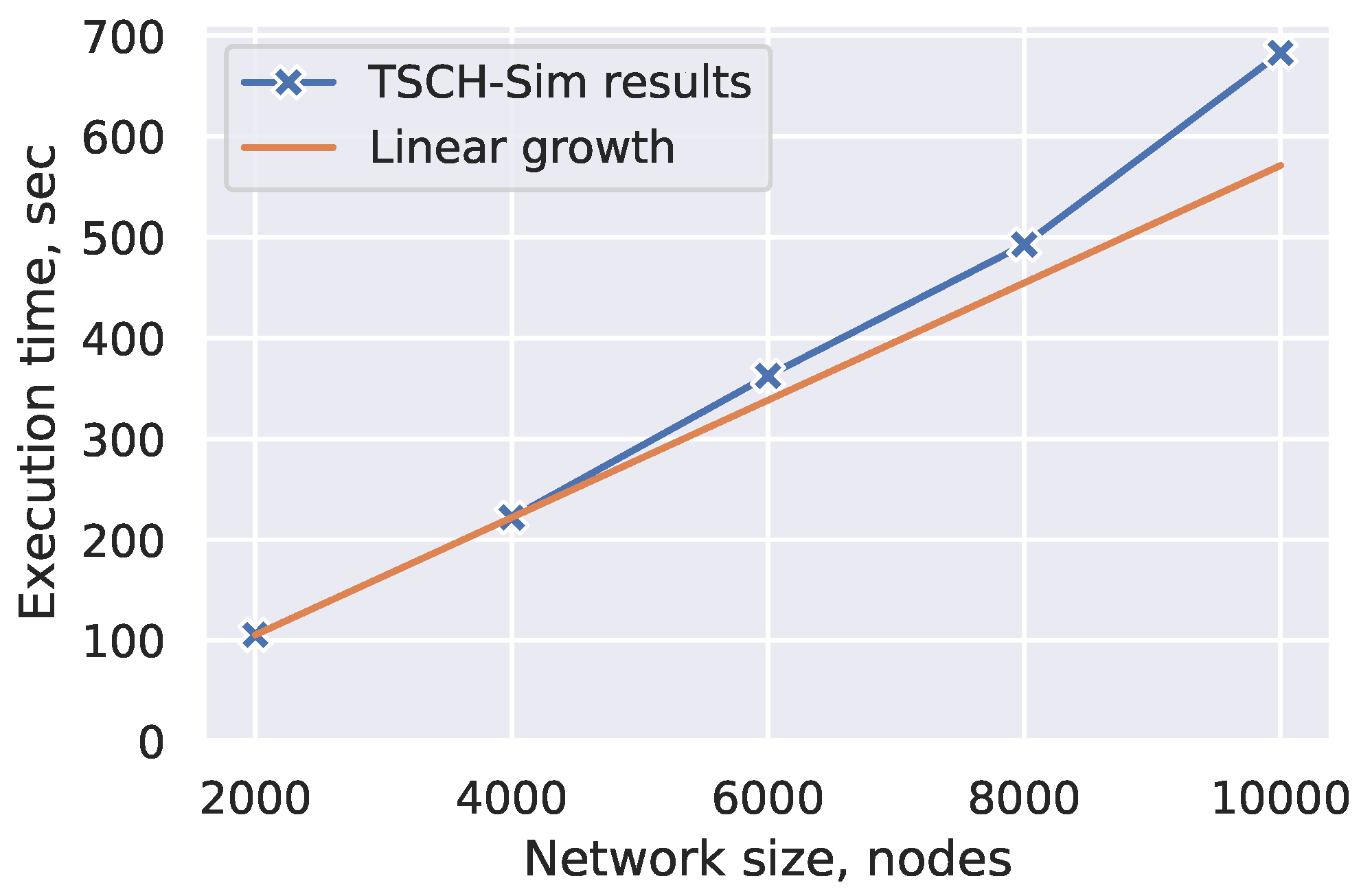
11], routing protocols (currently RPL), network connectivity models, including the models available in 6TiSCH and Cooja, node mobility models, as well as full control over the low-level details of the simulations such as the channel hopping sequence, queue size, and duration of individual timeslots. TSCH-Sim automatically collects simulation statistics for each run, including end-to-end Packet Delivery Ratio (PDR), hop-by-hop Packet ACK Ratio (PAR), radio duty cycle (RDC) and charge consumption for each node. The model of charge consumption is validated with hardware measurements on a Texas Instruments CC2650 device. TSCH-Sim has an easy-to-use web interface and uses the JSON format for configuration files. The simulator features a built-in random number generator that allows conduct replicable experiments, and a configuration option for running the same experiment multiple times with different random seeds, executed concurrently in case of a multicore CPU. Most importantly, TSCH-Sim demonstrates an order of magnitude faster execution time for medium-sized and large networks compared with other simulators evaluated in this paper, mostly because of a high abstraction level, improved link processing, and reduced log file sizes. In particular, in sparse networks it demonstrates approximately linear dependence between simulation speed and the number of nodes.
The paper is structured as follows:
Section 2 presents the background on the network protocols and overviews the existing simulation options.
Section 3 briefly describes the main aspects of TSCH-Sim.
Section 4 evaluates TSCH-Sim and quantitatively compares it with existing options, and
Section 5 provides an application example for the simulator. Finally,
Section 6 concludes the paper.
3. TSCH-Sim Overview
3.1. Core Functionality
TSCH-Sim is implemented in JavaScript using classes and code separation in modules. This language is selected to make the simulator easy-to-extend by users, as well as to facilitate the integration with a web frontend.
Table 1 shows a summary of TSCH-Sim core features and their comparison with other simulators.
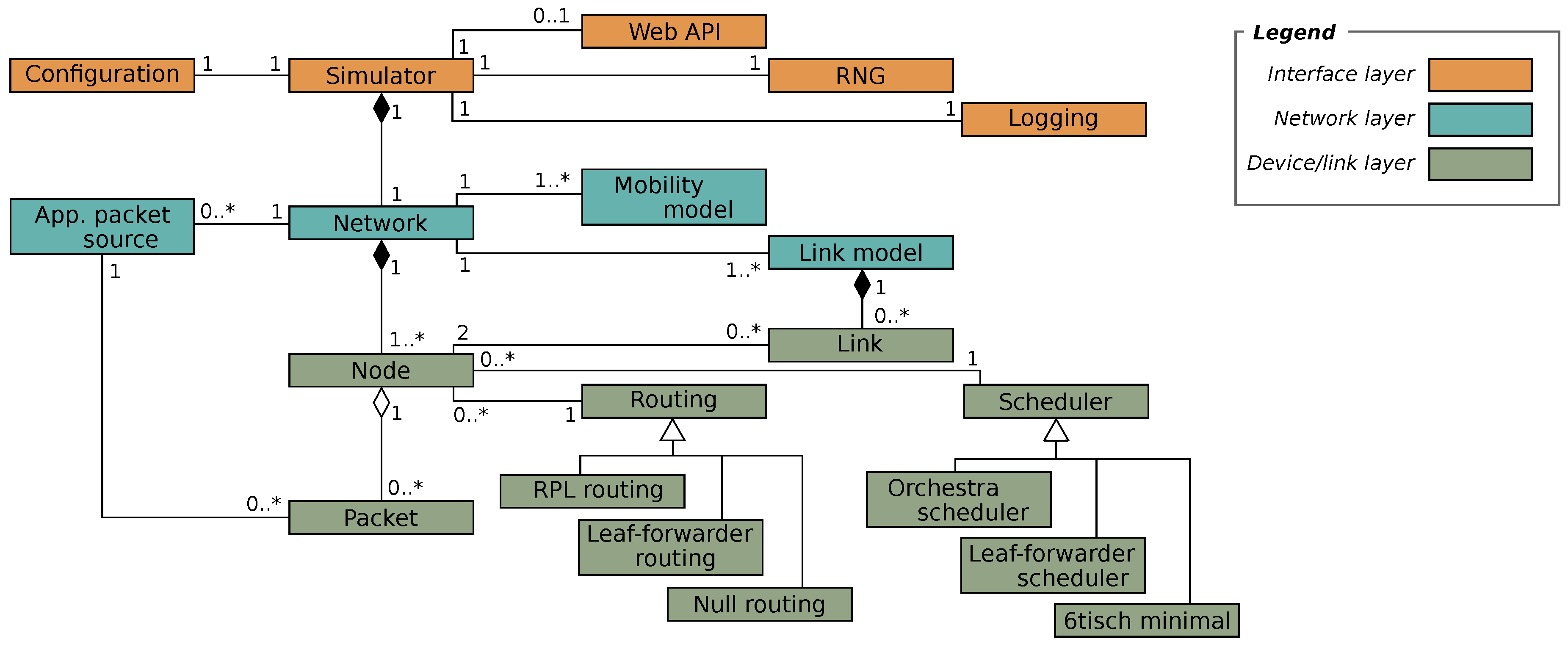
The TSCH-Sim code is loosely structured in three layers (
Figure 2). The highest of these is the
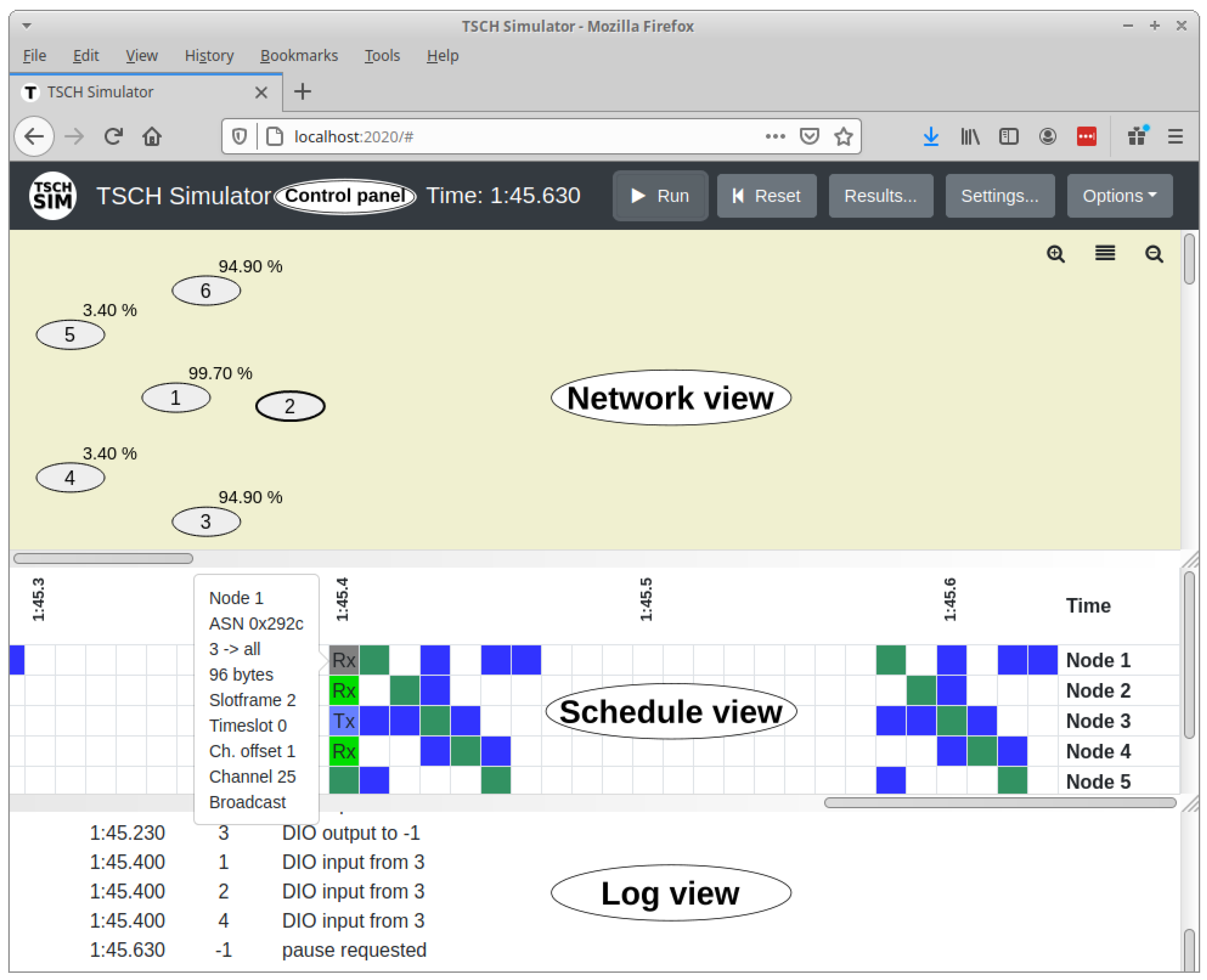
interface layer with modules that keeps the global configuration, route web API calls, and perform logging. A web GUI frontend is available (
Figure 3). The intermediate is the
network layer, which implements the upper half of the core simulator functionality. Multiple link connectivity options are available, including models that estimate packet reception probability and RSSI (Received signal strength indication) based on the distance between nodes, models that emulate options available on Cooja and the 6TiSCH simulator, and a trace-based model. Similarly, line mobility and random-waypoint mobility models are available. Finally, the
device layer implements the state of a network node, including the IEEE TSCH protocol state machine. This layer also features multiple routing and scheduling options, which can be selected via configuration. Besides RPL, a simple leaf-and-forwarder routing is available. In terms of schedulers, Orchestra, leaf-and-forwarder scheduler, and the 6TiSCH minimal scheduler are currently implemented.
The JavaScript language includes a random number generator (RNG). However, this RNG is not suitable for simulation purposes, as JavaScript does not allow seeding of its RNG from user code, making it impossible to conduct repeatable simulations. TSCH-Sim features a custom random number module that uses the multiply-with-carry algorithm. This RNG algorithm characterized by fast execution speed and ability to pass statistical tests of randomness very well [
15]. However, the multiply-with-carry algorithm generates uniform random numbers, and for some aspects of simulation the Gaussian distribution is required: for example, RSSI on communication links is characterized by additive white Gaussian noise. The random number module computes the Box-Muller transform [
16] to convert uniform random numbers to the Gaussian distribution.
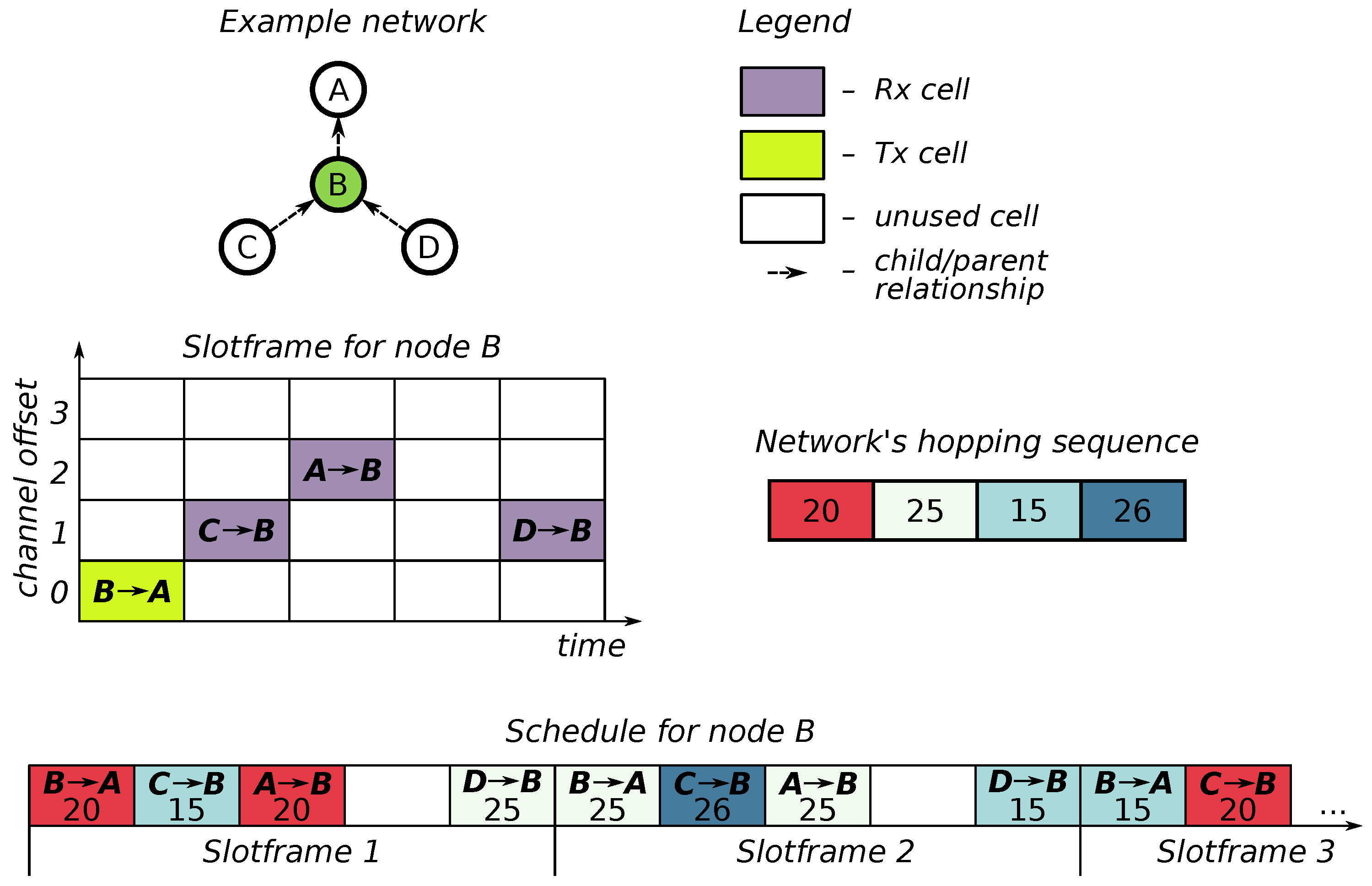
The TSCH-Sim simulator does not impose any specific slotframe structure: this depends in the scheduler. By default, TSCH-Sim has the Orchestra scheduler enabled. This scheduler adds three slotframes: one for node-specific unicast cells, one for sending and receiving Enhanced Beacon messages, and one called “common default”, shared by all nodes in the network and used for broadcast messages, such as RPL DIO messages. See Duquennoy et al. [
11] and Elsts et al. [
17] for the details.
3.2. Modeling Packet Transmissions and Collisions
The discrete nature of TSCH slotframe simplifies packet transmission modeling as packets may only be sent at a specific point in each timeslot. In each TSCH timeslot, all nodes in the network are processed and a scheduling decision made for each node. These decisions are possible: (1) transit a packet; (2) listen for a packet; (3) sleep. Nodes that transmit their packets do that by going through their links, checking whether the potential receiver is listening for packets and is on the right channel. If these preconditions are true, the link model is queried for transmission success probability between the transmitter and receiver nodes, a random number between 0 and 1 generated to determine the success for the packet, and the packet added on the receiver node: either to potentially received packets if the transmission is successful, or to interfering packets if it is not.
If the receiver node only has a single potentially received packet and no interfering packets in a given timeslot, the one packet is simply received. If there is more than one packet, Algorithm 1 implements reception with the capture effect [
18]. In the algorithm’s pseudo-code, functions
dBm_to_mW() and
mW_to_dBm() refer to conversion between RSSI, as commonly given in decibel-milliwatts, and transmission power in milliwatts. The goal is to determine whether any of the packets can still be received, which is the case if the strongest RSSI is more than the sum of the other RSSI minus the hardware-specific co-channel rejection threshold (by default −3 dBm in TSCH-Sim).
| Algorithm 1. Packet reception with collisions. |
- 1:
function ReceivePacket(, ) - 2:
SelectByStrongestRSSI() - 3:
dBm_to_mW() - 4:
- 5:
for do - 6:
if then - 7:
dBm_to_mW() - 8:
end if - 9:
end for - 10:
for do - 11:
dBm_to_mW() - 12:
end for - 13:
if mW_to_dBm() > - 14:
mW_to_dBm() then - 15:
return - 16:
else - 17:
return - 18:
end if - 19:
end function
|
3.3. Achieving High Performance
The TSCH-Sim connectivity model only considers packet reception possible if there is an existing link between the transmitter node and receiver node. The existence of these links is precalculated at the start of the simulation by the link model (
Section 3.5) and these links are kept in a cache for fast access. Due to this optimization, the execution time of TSCH-Sim simulations does not grow quadratically with the number of nodes (
N), but linearly with the number of links (
L). This is important in particular for sparse networks where
, as this property enables scaling up the network size as long as the number of potential connections per node remains small.
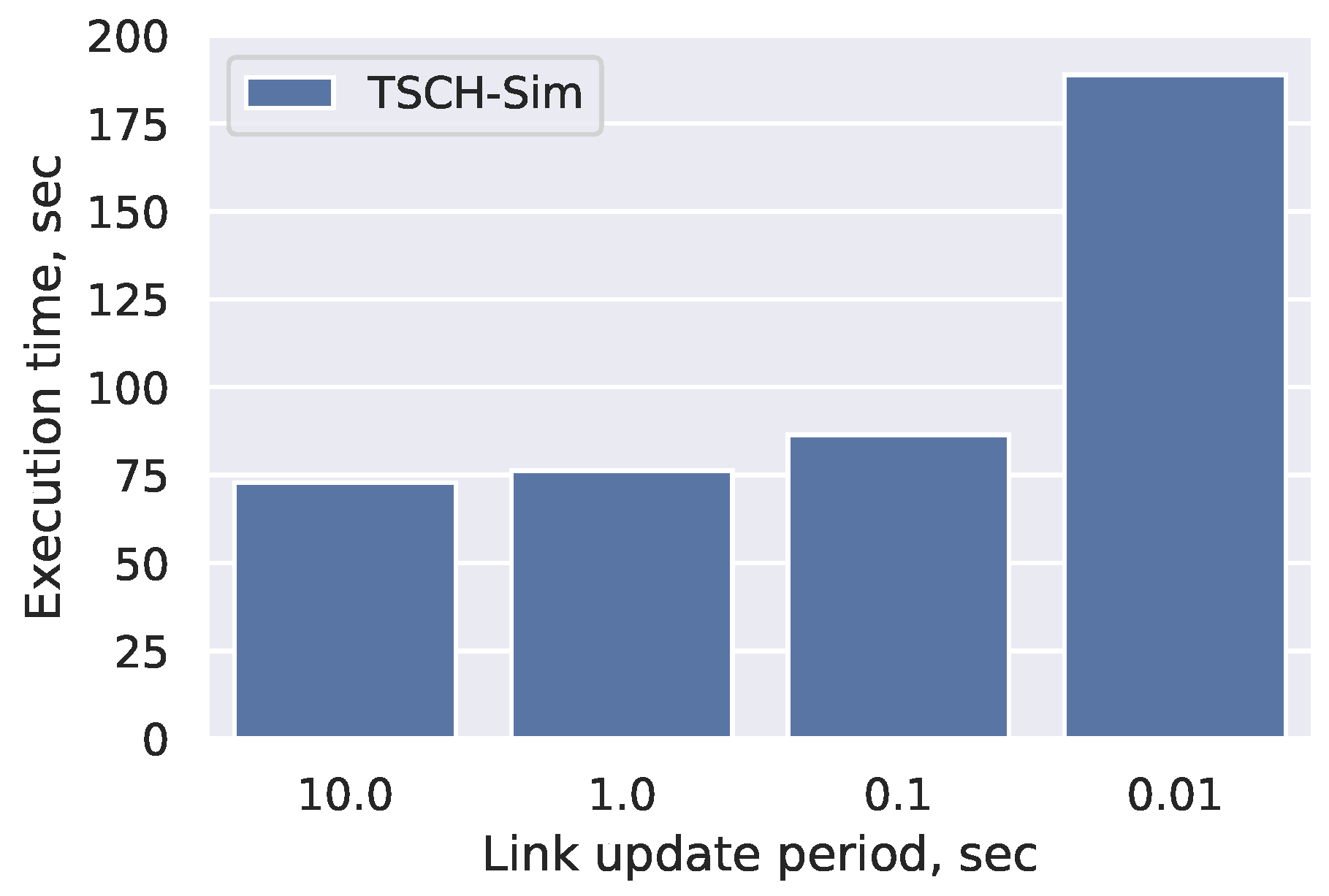
Cooja and the 6TiSCH simulator use similar strategies; however, the details are different. Cooja also caches the links in a hash table, but updates the links from a particular device whenever its radio is turned on or off. In a heavily duty-cycled protocol such a TSCH this creates a large overhead. The 6TiSCH simulator uses a connectivity matrix to provide fast access for all connections. The drawback of this approach is that whenever a transmission is done, all listening nodes need to be processed to the ones able to hear the packet, instead of iterating through the list of links from the transmitter with expected size.
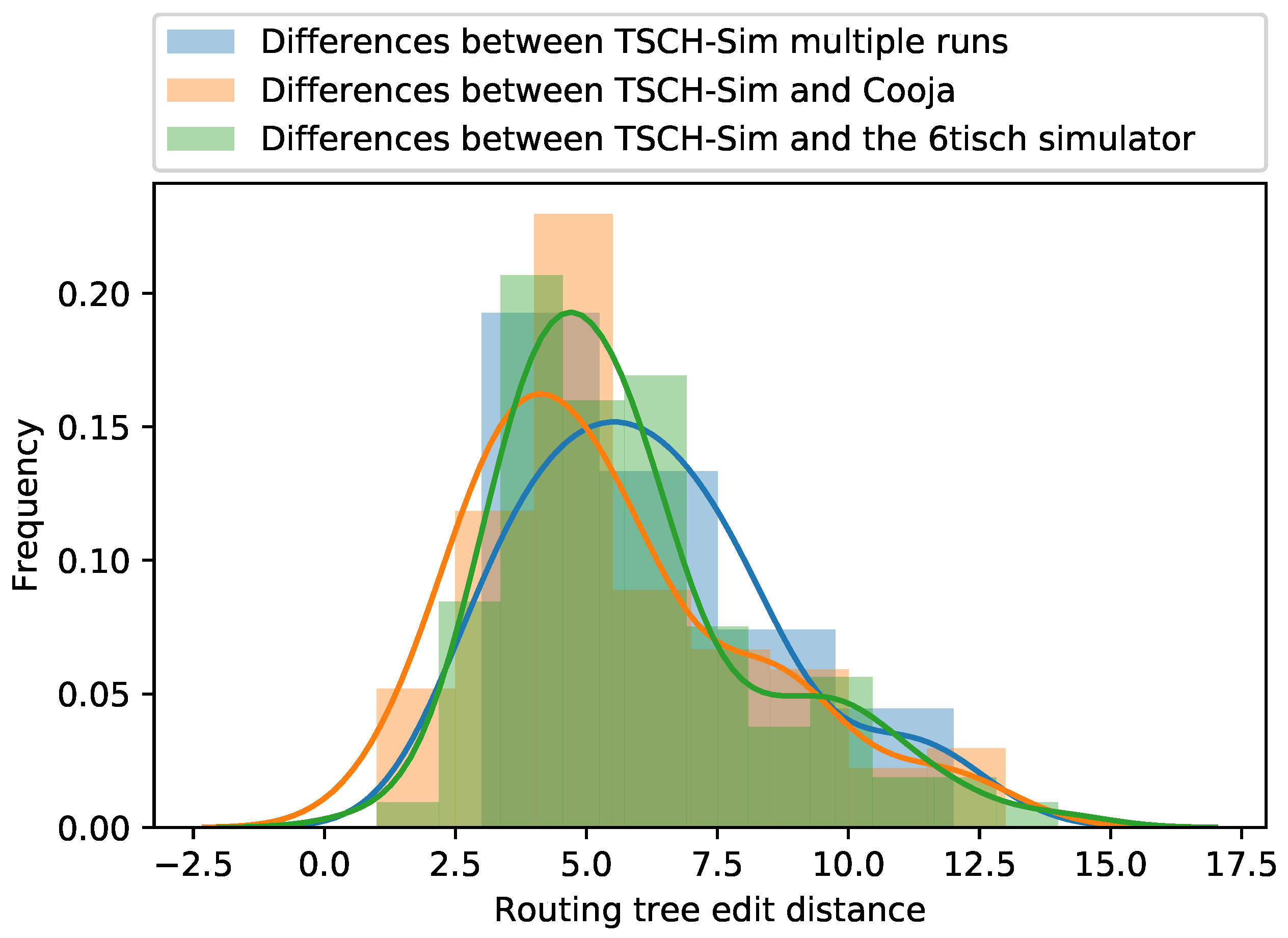
The second main performance optimization included in the TSCH-Sim is related to the collection of simulation results. The 6TiSCH simulator and Cooja use a two-step approach for result collection: during the simulation run, unstructured or loosely structured results are logged in an output file. After the simulation is completed, the file needs to be analyzed with a script to produce summary metrics. To reconstruct the main performance metrics (
Section 4.2), heavy log output is required; this takes a lot of disk space, and a lot of the runtime is spent waiting for I/O. The 6TiSCH simulator in particular creates files larger than a gigabyte for the 300 node simulations (
Section 4.3). TSCH-Sim is able to generate detailed log files as well; in fact, the main performance metrics (
Section 4.2) were reconstructed from these log files for a fair comparison with the other simulators. However, the TSCH-Sim code itself can collect all the required statistics during a simulation run, and report it immediately after the simulation is completed. This allows fully disabling of the log output and achievement of faster execution time without losing essential information about the results.
3.4. User Workflow
The main task of the user is to prepare a configuration for simulation runs. The configuration can be prepared either using the web interface or by directly writing the values in a JSON file; see the Listing 1 for an example. Example files are available along the source code of the simulator (
Section 3.7).
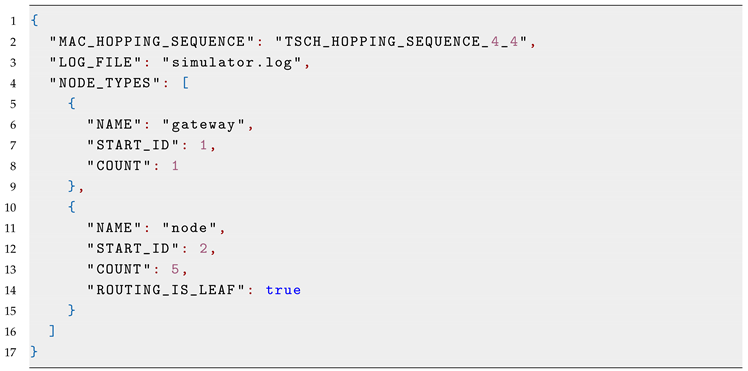
| Listing 1: TSCH-Sim configuration file example. |
![Sensors 20 05663 i001 Sensors 20 05663 i001]() |
Sensible default values for all settings are provided, with the exception of the number of nodes and their types. The configuration file is only required to contain values that differ from these defaults. The following information can be specified in the configuration file:
Simulation duration, simulation seed, the size of the simulated area;
Log file name and logging levels, including module-specific levels;
Link connectivity and node mobility models to use;
Routing protocol and scheduler to use;
Application-layer settings, such as the data packet size and generation period;
Link model settings, such as the transmission range;
Explicit link quality to use between specific nodes, if not covered by a distance-based link model;
Mobility model settings, such as the speed of nodes;
Routing protocol settings, such as the RPL packet periods, the lifetime of routes, whether to use the leaf mode, and whether to use RPL probing;
Scheduler settings, such as the TSCH slotframe size and timeslot duration;
MAC-layer settings, such as the number of retransmissions, queue size, TSCH Enhanced Beacon period, TSCH keep-alive packet period, and so on;
Node types (see below).
The configuration key “NODE_TYPES” is expected to contain an array defining node types to be included in the simulation. Each node type must have the following parameters: its name and the number of nodes of this type. It can also contain the starting ID of the first node of this type, the data packet generation frequency and the destination ID for data packets, as well as all other configuration parameters whose values are different from the top-level configuration values or the default settings. Consider an example: a network with two types of devices: full-functionality devices capable of routing and forwarding, and reduced functionality devices capable of connecting as leaf nodes. The latter are going to have “ROUTING_IS_LEAF” set to true in the configuration of their node. In contrast, the former may leave this key unspecified, as its default value is false.
There is a constant packet rate model, configurable from the JSON and implemented the “PacketSource” class. The user can attach a packet source to a node or a group of nodes and configure parameters such as the application warm-up time, packet frequency, packet size, and packet destination. It allows simulation of data collection, data dissemination, and data query applications.
Once the configuration is ready, the user may start the simulation, either by pressing the “Start” button in the web interface, or by running the simulator from command line with the configuration file name as a command-line parameter. As the simulation is executed, the output from the logging module is printed both to the standard output and to a log file. At the end of the simulation, summary metrics are calculated and saved in a JSON file, both for each node and for the simulation as a whole. Unless otherwise specified, the results are stored in the results directory under the simulator’s installation path.
3.5. Link and Mobility Models
All links in TSCH-Sim are unidirectional. This allows the creation of simulations with asymmetric communication: for example, there may be a good link from node A to node B, perhaps because A has high transmission power, but a lossy or no link from B to A. Unless a link is explicitly configured, its quality and signal strength depends on the distance between the source and destination nodes.
3.5.1. Explicitly Configured Links
For some radio links, their quality and other parameters may be fixed by the configuration. These are called “fixed” links in TSCH-Sim. The main options are link quality and the average RSSI. The link quality denotes the probability of a successful reception. There are two options for the format of this setting. First, it can be a number between 0 and 1.0, with the default value of 1.0. Second, it can be a dictionary with numerical keys corresponding to channel numbers in the TSCH channel hopping sequence, and a single value for each key, between 0 and 1. The latter allows the configuring of per-channel link qualities.
3.5.2. Unit Disk Graph Model
The unit disk graph model is the default propagation model used in Cooja and in other simulators. The unit disk graph radio signal propagation model uses circle centered at the transmitting mode to simulate radio coverage. The reception success probability normally depends on the distance d between the transmitting and the receiving node, and is calculated using the formula , where UDGM_RX_SUCCESS is a configuration value. However, if UDGM_CONSTANT_LOSS configuration setting is enabled, the reception success probability is constant everywhere in the unit disk.
3.5.3. Logistic Loss Model
The Logistic Loss radio signal propagation model uses circle centered at the transmitting mode to simulate radio coverage. The main role of Logistic Loss model is to serve as a more realistic replacement for the unit disk graph model.
The signal strength at the receiving node is determined using exponential free-space loss formula, on which Additive White Gaussian Noise (AWGN) is overlaid. The packet reception probability is modeled using the logistic function from the signal strength:
where
is the transmit power minus the path loss. To model the path loss
we use the log-distance path loss model [
19]:
where by default the transmission range
m,
dBm [
20],
dBm,
, and
[
19].
3.5.4. Pister-Hack Model
The Pister-hack model is the default propagation model used both in the 6TiSCH simulator and in OpenWSN OpenSim. The “hack” in the name refers to the property of the model is used to tune the RSSI levels to better match empirical results: namely the RSSI is randomly selected to be between the value predicted by the Friis model and to a value 40 dB below the Friis model.
3.5.5. Trace-Based Simulation
Packet reception traces allow the input of real-world radio link dynamics in simulated network. This can significantly improve the fidelity of simulations to real-world testbed. However, trace-based simulation is still no replacement for real-world experiments, as short-term dynamics are typically missed by the trace preparation process. The TSCH-Sim simulator uses a trace file format from the 6TiSCH simulator called “K7”. Both plaintext files and compressed files (with gzip) are support. The latter are expected to have .gz extension.
3.5.6. Mobility Support
Two mobility models are supported in TSCH-Sim:
Random-waypoint mobility model: a node generates a random point in the mobility range and moves towards that point. Once the point is reached, the mode repeats the process.
Line-based mobility model: a node moves along a single line segment. Once one end of the segment is reached, the node starts moving backwards, towards the other end, and so on.
Different mobility parameters can be enabled for different node types. For example, single simulation may combine static nodes, slow randomly moving nodes, fast randomly moving nodes, and nodes moving along multiple predefined lines.
3.6. Charge Consumption Model
When a simulation is executed in TSCH-Sim, the simulator keeps track of a number of statistics, including the number of slots used on each node. For the benefit of the user, at the end of the simulation, these slot-usage statistics are translated into charge consumption, which in turn can be used to estimate the battery lifetime on each node.
The charge consumption values used in the TSCH-Sim code are based on hardware measurements obtained using a RocketLogger device [
21] on a Texas Instruments CC2650 [
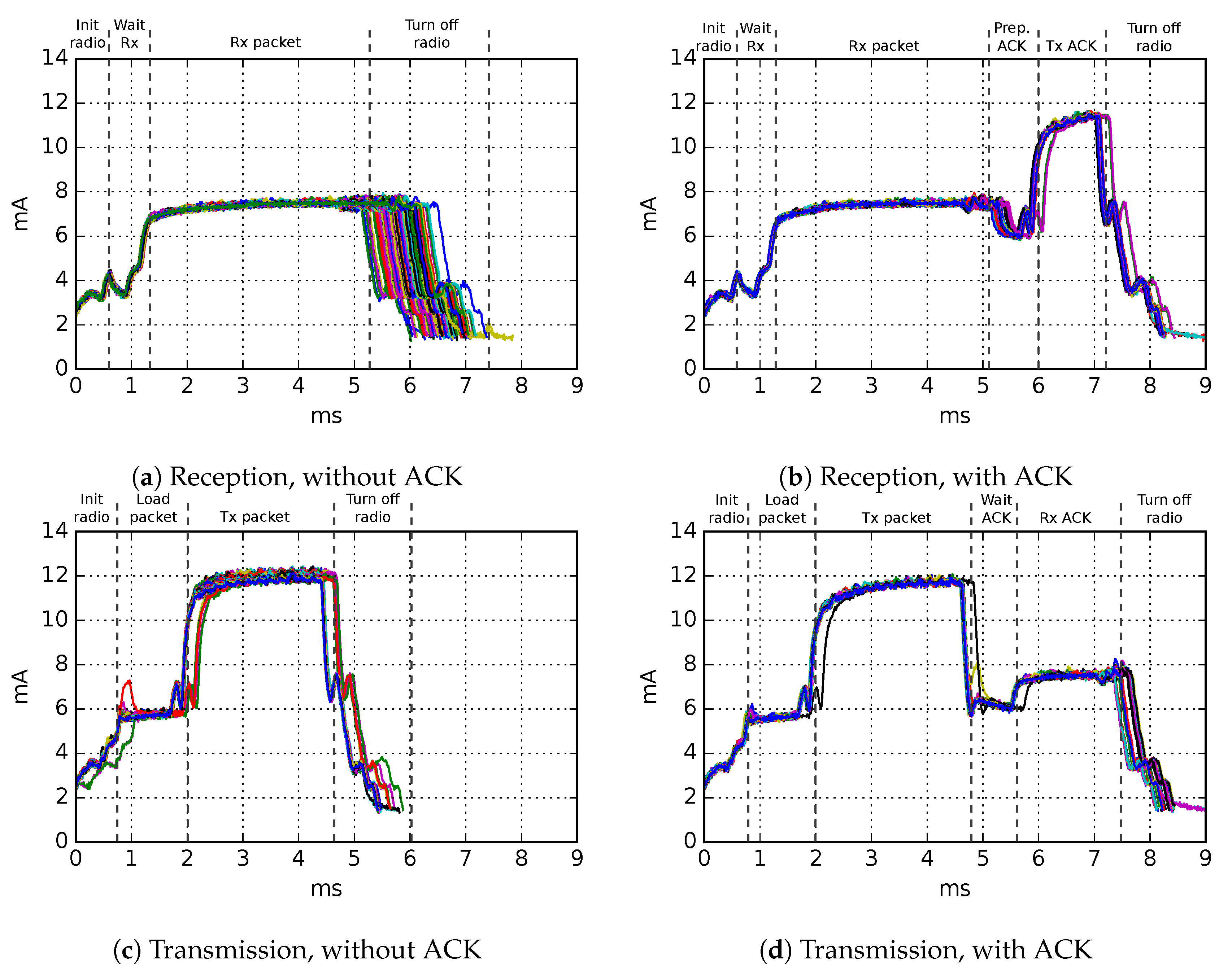
20] board. We measure the current consumption profiles of individual TSCH timeslots 100 times for each of the following: transmission of 50, 75, 100, and 123 byte sized packets (123 being the maximal MAC-layer payload) and reception of 50, 75, 100, and 123 byte sized packets, as well as idle listening slots. IEEE 802.15.4 standard encryption is enabled for all packets, and the CC2650 hardware acceleration for AES-128 is turned on.
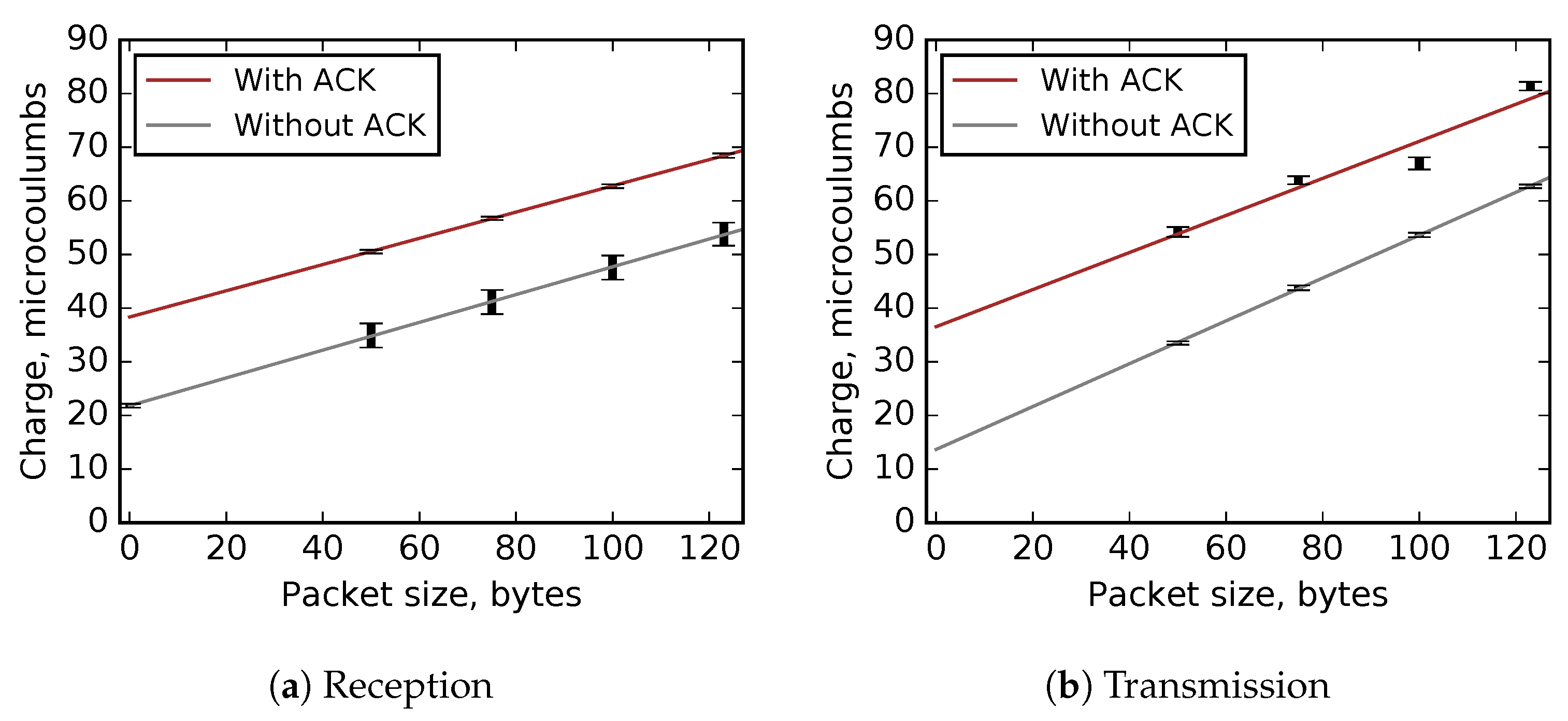
Based on the results (
Figure 4), we run linear regressions to estimate the charge consumption for packet sizes not directly measured. The regressions show very good fit, with
for transmissions with ACK and
for each of the three other experiments (
Figure 5). The results allow a conclusion that this is a reasonably accurate method for estimating charge consumption in TSCH networks.
TSCH-Sim calculates the charge consumed by a given node by accounting all packets that it has sent and received, as well as all slots it has spent in idle listening and scanning the channel. Depending on whether a packet is received or transmitted, and whether it has an ACK or not, the simulator selects one of the previously determined regression equations. Then, the charge for the packet is calculated by applying the selected regression equation on the size of the packet. To calculate the total charge of idle listening, a hardware-validated constant value is used as the charge of each idle listening slot, multiplied by the number of such slots. All these charges are summed up and reported as the total charge consumed by the node, both in microcoulumbs and converted to milliampere-hours (mAh).
3.7. Examples
The simulator comes with a number of examples demonstrating specific network topologies and features of the simulator. It also includes a number of regression tests for all main simulation features. The following examples are included:
Demos with star, mesh, line and grid networks, all under examples
Demo with a two-hop hierarchical network: examples/hierarchical
Demo with a large network with 1000 nodes: examples/large-network
Demo that demonstrates parallelization of multiple simulation runs: examples/multirun
Demo that demonstrates control of a simulation with a user-defined script: examples/scripting
Demo that launches the web interface backend: examples/web
Demo with comparative simulation runs and result visualization using matplotlib with Python: examples/result-visualization
5. Application Example
The network stack of TSCH & 6TiSCH protocols has a large number of configurable parameters. The selection of these MAC-layer parameters has a significant impact on the network performance. Different parameters may be optimal for different deployments, depending on the application, the network topology, and the radio environment. Applications also impose constraints: the minimum and maximum acceptable parameter values. While some of these parameters can be found analytically, this is not always the case. As a result, experimental approach is often required [
22]. A commonly used experimental strategy is called parameter sweep. It is a technique where a large number of simulations or pilot deployments are performed with different values of parameters in order exhaustively go through all potential parameter settings.
To put it more formally, let us consider a vector of parameters
and define an optimization problem with constraints:
where
are the performance metrics to optimize, and
the set of constraints to satisfy.
For the sake of an example, we show how to use TSCH-Sim for such a parameter selection via the parameter sweep technique. We assume that the data collection application (with packet period, packet size and other parameters specified in
Table 2) needs to be deployed in a 300-node mesh network. For simplicity, we vary just a single parameter—the slotframe size
:
, and look at the following metrics: PDR (
) and battery lifetime (
). More parameters and metrics can be easily added. We generate a random network topology with 300 nodes, and run the simulation ten times on this network, changing the slotframe size from 3 to 19 with a step of 2. To estimate the battery lifetime
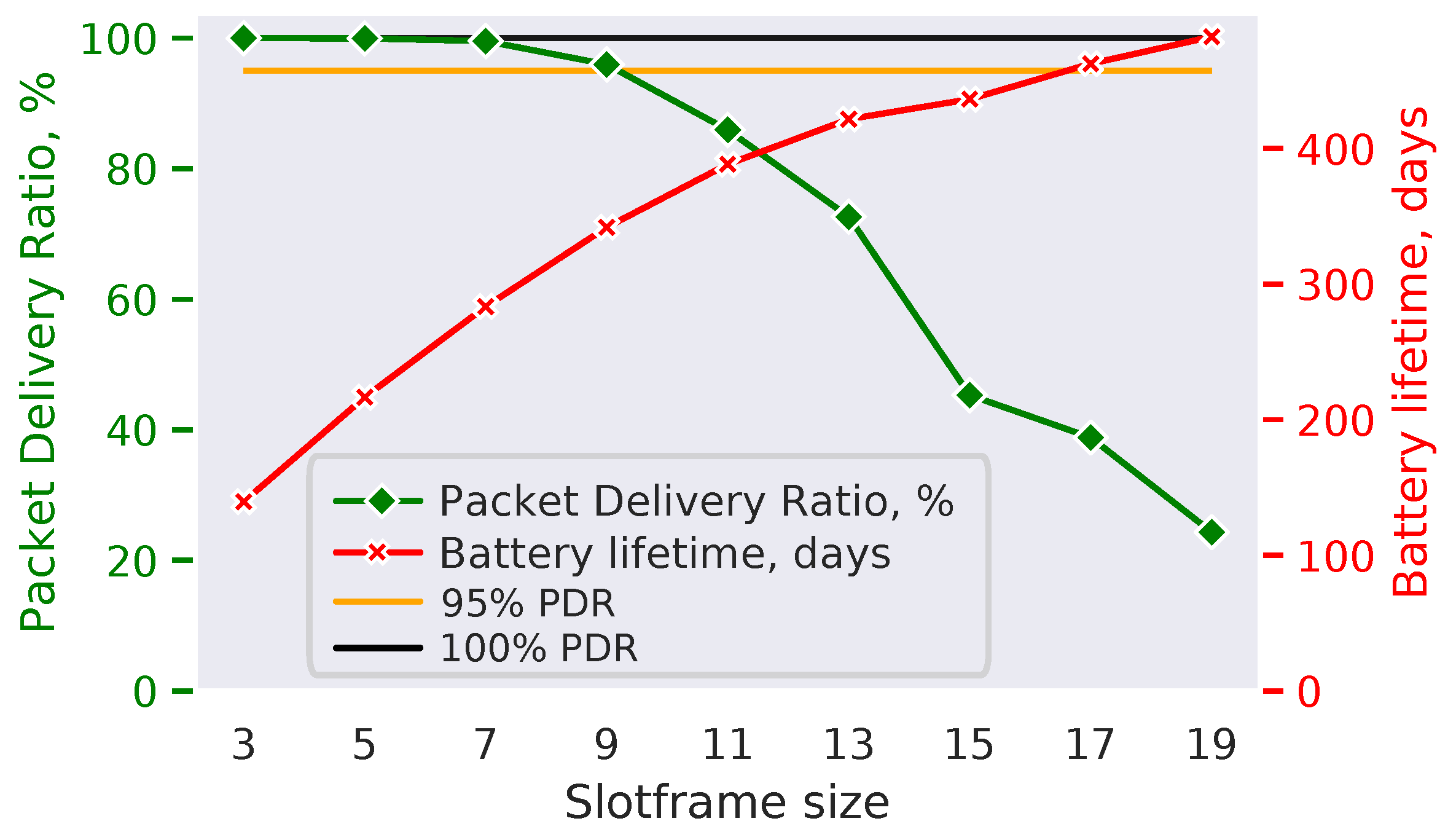
, we assume a 2600 mAh battery budget, common for off-the-shelf AA batteries. The results (
Figure 12) show that longer slotframes are associated with monotonically increasing network lifetime, while also leading to monotonically decreasing PDR. Given a specific network optimization goal, the network designer can now use the results to select an appropriate combination of parameters. For example, if the goal is to optimize the battery lifetime while maintaining at least 95% PDR (
), then slotframe size of 9 is the best option (
Figure 12).
6. Conclusions
This paper describes and evaluates TSCH-Sim, a new discrete event simulator for TSCH and 6TiSCH networks. Besides the core protocol, the simulator has support for multiple link connectivity models, mobility models, multiple TSCH schedulers including Orchestra, and the RPL routing protocol. The simulator comes with a module for summary metrics and a web interface for control and visualization. The evaluation shows that the simulator is an order of magnitude faster than existing alternatives without losing simulation accuracy, and that it can scale up to large networks, mostly due to a high abstraction level, improved link processing, and reduced log file sizes. In particular, we demonstrate faster-than-real-time simulations of a 10,000 node network on a regular PC.