Abstract
The secure full-duplex (FD) simultaneous wireless information and power transfer (SWIPT) system and non-orthogonal multiple access (NOMA) have been deemed two promising technologies for the next generation of wireless communication. In this paper, the network is combined with device-to-device (D2D) and a practical bounded channel state information (CSI) estimation scheme. A system total transmit power minimization problem is studied and formulated as a multi-objective optimization (MOO) problem via the weighted Tchebycheff approach. A set of linear matrix inequalities (LMI) is used to transform the non-convex form of constraints into the convex form. Considering the imperfect CSI of the potential eavesdropper for robust power allocation, a bounded transmission beamforming vector design along with artificial noise (AN) is used, while satisfying the requirements from the secrecy rates as well as the energy harvesting (EH) task. Numerical simulation results validate the convergence performance and the trade-off between the uplink (UL) and downlink (DL) data transmit power. It is also shown that by FD and NOMA, the performance of the proposed algorithm is higher than that of half-duplex (HD) and orthogonal multiple access (OMA).
1. Introduction
Next-generation communication systems require self-sustainability wireless nodes to maintain a high data rates network and guarantee quality of service (QoS) [1]. Radio frequency (RF) signal-based simultaneous wireless information and power transfer (SWIPT) is a promising technique for prolonging the lifetime of continuous network operation [2,3]. SWIPT can jointly extract information and replenish energy from the same signal by performing two circuits to separate the information processing and power transfer alternatively [4,5]. Non-orthogonal multiple access (NOMA) has also become a key issue of the novel energy and spectrum efficient technologies due to a higher network capacity compared with orthogonal multiple access (OMA) in the next-generation communication networks [6]. NOMA can provide the same resource (e.g., time/frequency/code) for multiple users by using different a power level in one subcarrier [7,8]. The combination of NOMA and device-to-device (D2D) communication is essential for alleviating the traffic burden on future networks. In contrast to the traditional concept of “D2D pair”, the concept of “D2D group” involves several D2D receivers that are capable of receiving information from a single D2D transmitter. To further improve the system spectrum efficiency (SE), the full-duplex (FD) transceiver is considered as it can be adopted in simultaneous downlink (DL) and uplink (UL) transmission in the same frequency band [9]. However, FD NOMA communication is more susceptible to eavesdropping compared to conventional half-duplex (HD) OMA. Further, this situation also causes extra energy consumption in SWIPT.
In practical systems, secrecy is a critical concern for the design of wireless communication protocols due to the broadcast nature of the wireless medium [10]. Physical security techniques can improve secure wireless information transmission by generating more interference to potential eavesdroppers [11]. By adding artificial noise (AN) and projecting it onto the null space of information user channels in information transmit beamforming, the potential eavesdroppers would experience a higher noise floor and thus obtain less information about the messages transmitted to the legitimate receivers [12]. In SWIPT systems, the secure communication problem is severer because of larger power consumption in the energy harvesting (EH) task [13]. Besides, taking into account that the base station (BS) may not perfectly know the channel state information (CSI) of the roaming users (RU) also creates a potential vulnerability of ensuring secure communications [10].
Most of the studies mentioned above rely on one case that the BS can get the perfect knowledge of CSI. However, in practice, the BS always has imperfect CSI. To deal with it, we assume a channel estimation error model where the BS only knows the estimated channel gain and a prior knowledge of the variance of the estimation error [14]. In this paper, we consider D2D-aided FD NOMA-enhanced secure SWIPT communications with imperfect CSI, in which D2D receivers can reuse the same subcarrier occupied by the information transmit user to improve the spectrum utilization in the power domain NOMA. To the best of our knowledge, the existing works cannot use a power efficiency algorithm in secure NOMA- and D2D-enhanced FD SWIPT systems with channel estimation and energy constraints. To study the problem, we propose an algorithm that involves constraints from EH and secure information transmission tasks to jointly extract information and replenish energy. Hence, the proposed algorithm needs to transform the probabilistic non-convex optimization problem into a bounded convex optimization problem. Besides, the existence of a trade-off between UL and DL co-channel interference (CCI) in the FD system needs to be solved by a multi-objective optimization method. Considering all the sub-problems above, a Pareto optimal policy is able to be defined with semidefinite programming (SDP) relaxation [15]. After that, we can iteratively minimize the bounded power allocation coefficients for the objective function of the optimization problem by CVX and guarantee security and QoS, simultaneously.
The rest of the article is organized as follows. The channel model and problem formulation are introduced in Section 2. Then, the proposed algorithm is elaborated in Section 3. In Section 4, we talk about the simulation results, while Section 5 finally draws the conclusions of this work.
Notation: and denote the inverse, Hermitian transpose, trace, rank and determinant of matrix , respectively; is a diagonal matrix with the diagonal elements given by , and returns a diagonal matrix having the main diagonal elements of on its main diagonal; stands for [16]. In addition, the abbreviations in this work are summarized in Table 1.

Table 1.
Abbreviation index.
2. Network Model and Problem Formulation
In this section, the considered FD NOMA and D2D network in SWIPT along with the channel models is presented. Further, in the formulation of this problem, we first define the secure transmission problem in SWIPT employing a resource allocation scheme and give the imperfect CSI channel model. Then, a non-convex optimization problem is presented with the resource allocation design.
2.1. Network Model
We focus on a secure NOMA-based SWIPT UL and DL scenario in a heterogeneous network, as shown in Figure 1, which requires a D2D group communication including one D2D transmitter (DT) and two D2D receivers (DR). In Figure 1, the FD BS is assumed to be equipped with antennas to facilitate secure transmission. UL cellular users (CU) and three D2D users (DU) are trusted users. Among them, DT in the D2D group is assumed to work in full-duplex mode and is equipped with three antennas. The other trusted users are assumed to have a single antenna for low hardware complexity. All antennas in the user devices are assumed to work in half-duplex (HD) mode. The D2D communication has two missions to accomplish. On each subcarrier, the FD BS transmits a signal to DT and receives a signal from CU. In the same scheduling time slot, two DRs in the D2D group receive two independent signal streams simultaneously from DT in the NOMA way. Each DR uses a successive interference canceller to detect its own signal. Since the network model has an untrusted user with the energy harvesting task, it is treated as a potential eavesdropper with antennas . Thus, in the power allocation scheme, we take the untrusted user into account to guarantee secure information transmission of the wireless network.
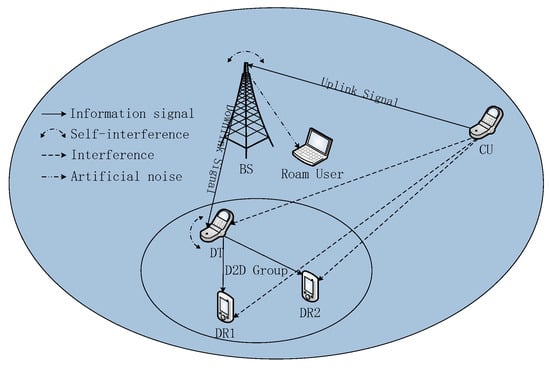
Figure 1.
Full-duplex (FD) non-orthogonal multiple access (NOMA)-based simultaneous wireless information and power transfer (SWIPT) with the device-to-device (D2D) communications network model with one multiple-antennas base station (BS), four half-duplex (HD) single-antenna trusted users and one HD untrusted user.
According to the system model in Figure 1, the signals received by the network devices can be written as follows. The received signal at the FD BS can be written as
where is the data transmission power from the uplink CU to the FD BS; is the uplink channel vector of the CU; represents the complex matrix; is the information bearing signal for CU. It is assumed that ; is the self-interference (SI) channel matrix of the FD BS; is the corresponding beamforming vector; is the data from the FD BS to DT; is distributed as a complex Gaussian random vector with mean , and represents the AN sent by the FD BS to degrade the signal to noise ratio (SNR) of the eavesdropper or the RU; ⪰ 0 is the covariance matrix of and M, where M is an Hermitian matrix; and is the additive white Gaussian Noise (AWGN) from the uplink channel to the FD BS, where denotes the identity matrix [14].
The received signal at the DT can be written as
where is the downlink channel between DT and the FD BS; is the SI channel matrix of DT; denote the corresponding beamforming vectors of D2D receivers; and are the data from DT to DR; is the channel between DT and the UL CU; and is the AWGN from the FD BS to DT, where denotes the identity matrix.
To study the signals of D2D receivers, we assume that the channel state of DR1 is better than DR2 as DR1 is located far away from the CU and the eavesdropper in Figure 1, and In NOMA, DR1 first decodes the signal of DR2 by successive interference cancellation (SIC). The received information signal at DR1 is derived as
where is the downlink channel between DT and DR1; is the downlink channel between FD BS and DR1; is the channel between DR1 and the UL CU; and is the AWGN of DR1.
Similarly, the received signal at DR2 can be written as
where is the downlink channel between DT and DR2; is the downlink channel between FD BS and DR2; is the channel between DR2 and the UL CU; and is the AWGN of DR2.
As for the potential eavesdropper, here we use RU for convenience, with multiple antennas, and the received signal can be written as
where is the channel between the RU and the FD BS; is the channel between RU and DT; is the channel between RU and the uplink CU; and is the AWGN of RU, where denotes the identity matrix.
2.2. Problem Formulation
In this part, we first analyze the achievable rate and secrecy rate for the considered heterogeneous network. Then, we talk about the CSI knowledge in the communication system for the FD BS to control the power resource. In the end, a joint multi-objective UL and DL power minimization problem is formulated for resource allocation.
The achievable rate of CU can be written as
With
where denotes the receiving signal-to-interference-plus-noise ratio (SINR) for CU at the FD BS; denotes the receiving beamforming vector of FD BS to decode the information from the CU; and . The CSI on the uplink channel of CU is estimated by zero-force beamforming (ZF-BF). It is adopted because of the computationally efficient performance for resource allocation. Further, its performance is close to the minimum mean square error beamforming (MMSE-BF) when the receiving SINR at the BS is high. Hence, in ZF-BF, and represents the Euclidean vector norm of . The residual SI coefficient represents the ratio of the power received at an antenna that reflects the performance of the SI cancellation, here [15].
The achievable rate of DT can be written as
With
where denotes the receiving SINR from the FD BS to DT.
After SIC, the achievable data rate of DR1 is
with
where is the receiving SINR from the DT to DR1.
The achievable rate of DR2 can be written as
with
where is the receive SINR from the DT to DR2.
As outlined before, the RU who has the EH task can be treated as a potential eavesdropper to eavesdrop the information signals of UL and DL trusted CU. Hence, to guarantee communication security, the system is designed to have the ability to deal with the circumstance that RU is able to cancel all multiuser interference. Further, to study the system security, we define the channel capacity for the RU. The channel capacity for RU to eavesdrop information of the UL CU can be written as
where is the interference-plus-noise covariance matrix of RU.
The channel capacity for RU to eavesdrop information of the DL DT can be written as
The channel capacity for RU to eavesdrop information of the DL DRs can be written as
The achievable secrecy rates of the trusted links in the network are given by
respectively.
Considering the EH task, the total amount of energy harvested by RU can be written as
where is the energy conversion coefficient of RU.
Assuming all channels vary slowly in each scheduled time slot, the BS can perfectly get the CSI from the trusted users via handshaking. However, the RU only exchanges the pilot information with the BS in the beginning of the working phase for the EH task. When the location of the wireless network users is changing, the FD BS needs to estimate the CSI of RU to guarantee communication security because the RU can become a potential eavesdropper with channel uncertainty [16]. The channel between FD BS and RU and the channel between DT and RU , along with the channel between RU and CU , can be modeled as
where , and are defined to represent the estimated CSI; , and represent the respective channel uncertainties. The continuous sets , and are defined to contain all the possible channel uncertainties with bounded magnitudes , and . , here, represents the Frobenius matrix norm of and .
Having the CSI, we focus on the transmit power minimization for the system which is an essential issue for green communication.
Problem 1 (Transmit Power Minimization for the FD BS):
Formula (27) depicts the power allocation optimization problem of minimizing the transmit energy for DT and AN. – are the minimum SINR thresholds of the trusted users of the system with . Constraints – are proposed to guarantee network security. is the maximum tolerable or the minimum achievable data rate for RU to decode information from the signals of the trusted users in the wireless network. ensures RU gets the minimum required amount of energy. Constraint denotes that is the non-negative power. is a rank-one constraint of , and to obtain rank-one beamforming. is the constraint of the Hermitian positive semidefinite matrix , , and .
Note that the objective function in Problem 1 minimizes the transmit energy from the BS without considering the transmit power from DT and UL CU. Thus, the second network objective function is proposed to minimize the transmit power from DT to DR and total transmit power of UL CU.
Problem 2 (Transmit Power Minimization for DT and CU):
Problem 2 targets the transmit power minimization of DT and CU under – without considering the power consumed by the FD BS.
From the two sub-problems, we find a trade-off between the two target functions and the existence of the multiple-antennas RU in the constraints also increases the complexity of solving the optimization problem. The objectives in Problem 1 affect the DL transmit power of the FD BS and the receiving signals of DT, while the objectives in Problem 2 affect the UL transmit power of the UL CU and the receiving signals of the DR. Further discussion is proposed in the next section.
3. Solution of the Optimization Problem
In this part, we first solve the two sub-problems with the Pareto optimality. Then, we analyze the network computational complexity.
Assume that for minimizing total energy consumption, the transmit power of the UL CU first decreases which impairs the objects in Problem 1. The transmit power objects of Problem 1, and , which result in significant SI should decrease to satisfy the SINR requirement . Besides, as for the links between DUs, the low power of AN causes a higher risk on the information leakage to the RU. Thus, the DT lowers the transmit power to DRs to meet the security requirement . It seems to converge to a reasonable circumstance that each of the allocated user powers approximately achieves the minimum SINR requirements. However, in practice, the user QoS is dynamically changing all the time. For example, increases when DT needs a higher bandwidth for a live high-quality video. A higher directs to a higher , which puts higher SI on the UL channel. This means also needs to increase to compensate this interference for satisfying the minimum required QoS . As for security, the increment in the BS emission power also causes a higher risk on the information leakage which leads to another power increment of AN. This further impacts the RUs as they need more power to ensure QoS. Therefore, the objectives in the two sub-problems conflict with each other. When we pursue an object to minimize the system consumed power, the result tends to become higher.
To overcome the shortcomings, the multi-objective optimization (MOO) problem is adopted with the concept of Pareto optimality. We first denote sub-problem i as . A resource allocation policy that can be set as can achieve the Pareto optimal if and only if all the set members satisfy where represents the optimal objective value of Problem i. To capture the complete Pareto optimal set, we resort to the weighted Tchebycheff scheme that can jointly solve the trade-off between the two sub-problems in MOO as shown in Problem 3 [10].
Problem 3:
where
and
denotes an auxiliary optimization variable that targets the total transmit power minimization of the trusted UL and DL users. Variable specifies the priority of the i-th objective compared to the other objectives and reflects the preference of the system operator [15].
As – are non-convex constraints and – have uncertain CSI, we consider using a linear relaxation approach to transform – into a set of linear matrix inequalities (LMI) and the generalized S-procedure approach to solve the infinite number of inequality constraints – produced by CSI uncertainty.
First, to handle the non-convex constraints –, we note the implications in the following equivalent transformation:
and
where: , , and .
Next, note that – and still involve an infinite number of inequality constraints [17], and we consider introducing the generalized S-procedure to solve it.
Let , and D⪰0. For , ⪰0, is equivalent to
Since involves two coupled estimation error variables, a slack matrix variable M first needs to be introduced to handle it. In particular, is equivalently represented by
Then, we apply (35) to and to get and .
for , and
for .
By substituting into (33), we have
where and . Then, constraint is equivalently written as
where .
Similar to is equivalently represented by
where N and .
Then, we apply (35) to and to get and .
for , and
for . Similarly, constraint is equivalently written as
for .
Now, the MOO problem (29) becomes a convex semidefinite programming (SDP) and can be written as
The convex problem (47) is efficiently optimized by the standard convex programming software named CVX [18]. Note that once we find a rank-one matrix to be the solution of the relaxed SDP problem, the matrix can also be used as a solution of the original problem of (47). Next, we proof the existence of an optimal solution of (47).
Proof.
The proof of the existence of an optimal solution of (47) is given in the Appendix A. □
In the proposed secure FD-SWIPT network, the CSI received by a device is assumed to be bounded. This circumstance directs the infinite number of CSI values for a user to compute the accurate CSI of another one. Besides, considering the constraints, we treat the optimization problem as a non-convex problem. To directly apply the S-procedure method to the power minimization problem, we introduce several leverage parameters into the non-convex constraints with bounded CSI values. Then, the constraints can be written as equivalent matrices with linear form elements. At last, the non-convex problem is transformed into a convex form, which can be classified as the relaxed SDP problem.
4. Simulation Results
The performance of the proposed MOO resource allocation algorithm is investigated in this section. Table 2 specifies the most important simulation parameters. The RU is equipped with N = 2 antennas. The cell BS is on the center of the cellular with M = 3 antennas with a radius of 1000 m. The small-scale fading is modeled by Rayleith distribution and the large-scale fading can be calculated by (d/d0)−η, where d is the distance between two network devices and d0 is the reference distance, which is set to be 100 m. Besides, the path loss exponent η is set to be 3. We set the communication radius of the D2D group as 300 m.

Table 2.
System parameters.
4.1. Convergence of the Proposed Algorithm
The minimum transmit power of the users versus the number of iterations is shown in Figure 2. We set the initial transmit power of the network as 20 dBm. The results in Figure 2 are averaged over 1000 independent adaptation processes which have different locations of the users in the cellular. It can be observed that, with an iteration interval of the proposed algorithm has a fast convergence rate within 10 iterations. It is shown in Figure 2 that the proposed power minimization approach is capable of saving more power when the number of antennas on the FD BS become larger. This is because the inherent spatial diversity comes up with more antennas which creates a benefit for power efficiency. With that, the system can indeed combat the path loss with a smaller portion of radiated power.
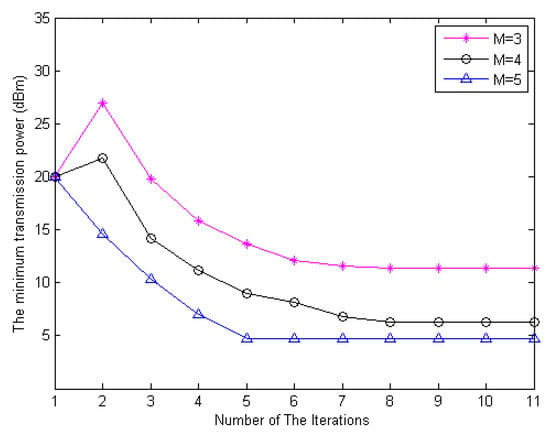
Figure 2.
The minimum transmit power versus the number of iterations for the proposed algorithm with an iteration interval of .
In Figure 3, the cumulative distribution function (CDF) of the proposed algorithm is displayed using the bounded CSI error model to deal with the imperfect CSI. It can be observed that, with more antennas at the FD BS, the proposed algorithm has a faster convergence rate within 10 iterations because of the full accomplishment of the available degrees of freedom (DoF) in globally optimal resource allocation. Summarizing the results obtained from Figure 2 and Figure 3, we can observe the convergence of the power minimization algorithm with the same parameters.
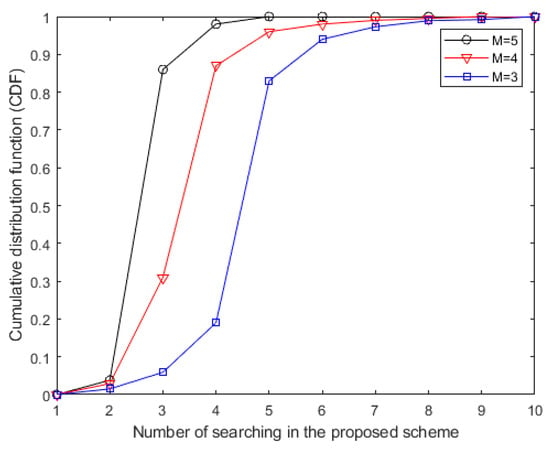
Figure 3.
The cumulative distribution function (CDF) of the proposed minimum transmission power allocation scheme with imperfect channel state information (CSI) under the parameters of the FD BS antenna numbers with M = 5, M = 4 and M = 3.
4.2. Transmit PowerTrade-off Region
The trade-off between the average transmit power of each device in sub-problem 1 and sub-problem 2 with imperfect CSI and different antenna numbers on the FD BS is shown in Figure 4. It can be observed that the average transmit power consumption of each user in sub-problem 1 is monotonically decreased with respect to the higher average transmit power of the users in sub-problem 2, which means that maximizing the power consumption of one sub-problem leads to lower power consumption of the other and vice versa. In other words, the results in Figure 4 confirm that minimizing the transmit power of UL and DL in FD devices creates conflicting design objectives. For instance, when M = 4, 3 dBm transmit power of sub-problem 2 can be saved by a 3.5 dBm increment in the total transmit power of sub-problem 1. In addition, it can be indicated in the figure that a significant amount of total transmit power is saved with the increment in the number of FD BS antennas. This is because additional antennas offer extra (DoF) to facilitate more power efficiency. Under this circumstance, the FD BS does not need to transmit extra power for neutralizing the increasing potential of information leakage anymore. With advanced interference management technologies in the next-generation wireless network, the increment in the FD BS antennas number has a good prospect in providing higher power efficiency for the wireless communication system.
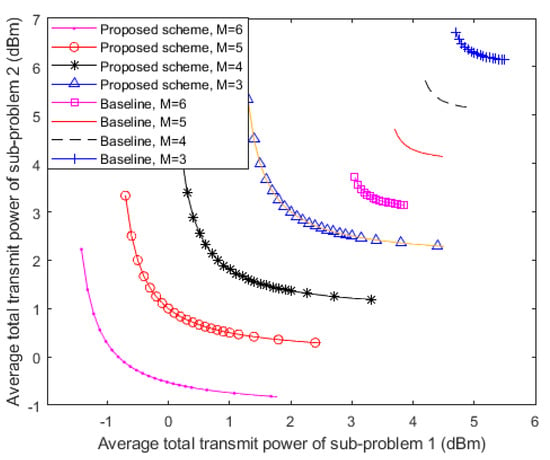
Figure 4.
Average transmit power trade-off region between the two sub-problems of each device achieved by the proposed power minimization resource allocation policy. The baseline is simulated under the parameters of the FD BS antenna numbers with M = 6, M = 5, M = 4 and M = 3.
Considering the baseline scheme, ZF-BF is adopted as the power emission approach for comparison. It is shown in Figure 4 that the resource allocation approach in this paper is capable of saving more power because the curves are below the trade-off regions from the baseline scheme. It can also be indicated from the depiction that when M = 4, only 0.6 dBm power from sub-problem 2 can be saved by around a 1.5 dBm increment in the power from sub-problem 1. In fact, because the baseline scheme cannot exploit the full benefits of having available DoF from more antennas, the proposed approach is more energy-efficient.
4.3. Average Power Consumption versus Transmit SNR
Figure 5 depicts the relationships between average power consumption of the users in the FD system and the transmit signal to noise ratio (SNR) for different antenna numbers at the FD BS, here
. From Figure 5, it is observed that the average power consumption of the users is getting smaller while at the FD BS keeps getting bigger when M increases. In terms of M, more antennas create the condition that the direction of the beamforming vector can be more accurately steered towards the users. This situation reduces the power consumption and the leakage of the AN power in the system. As we can also see from Figure 5, the average power consumption decreases gradually with the transmit SNR at the FD BS. However, the transmission power cannot be infinitely small because of the existence of constraints for guaranteeing the EH task of the RU. Furthermore, we compare the performance between two methods: the exhausted search method (ESA) with perfect CSI and our proposed method with the same parameters. The ESA can give optimal search results after infinite times of iterations but costs a lot of time. Within a lower computing resource cost, the results of our proposed method indicate that multiple antennas (M > 3) in this network can effectively improve the performance of the proposed algorithm to find the optimal solution. In fact, more antennas provide a more stringent QoS in this situation, and this reduces the average power consumption of SWIPT and interference management.
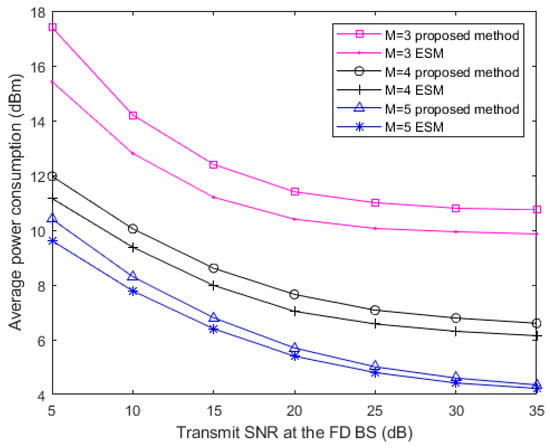
Figure 5.
Average transmit power of the users versus the transmit SNR of the FD BS for different total antenna numbers at the FD BS with M = 5, M = 4 and M = 3, in two methods.
4.4. The Minimum Transmit Power in Different Situations
In Figure 6, the impact of the residual SI of each FD antenna on the achievable average DL and UL security rate of the users is presented with bounded CSI. It can be observed from the figure that the security rate performance in FD communication degrades as increases, while that in the HD situation remains the same. Moreover, the UL security rate is always lower than the DL security rate under the same . This is because, as compared with the UL, RU exerts a negligible impact on the DL due to the strong interference cancellation ability of the FD BS along with the DT. Nevertheless, with more SI, the FD BS needs to transmit higher power to satisfy the network data rate which brings information leakage to the RU. Thus, the proposed scheme has to be devoted to allocate more power to the AN injection for wireless transmission secrecy. When the total energy of the system is limited, the UL network security data rate of FD becomes lower than HD.
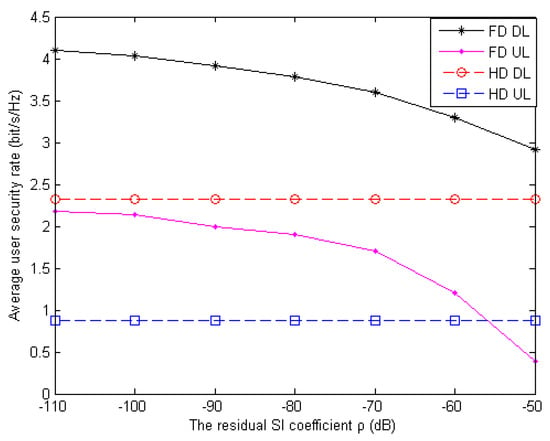
Figure 6.
Average user security rate versus the self-interference (SI) coefficient of the antennas for the downlink (DL) and uplink (UL) in different FD and HD schemes.
In the above simulations, we make efforts on minimizing the network transmit power while jointly guaranteeing the QoS and the secrecy limits. However, the transmission power cannot become infinitely small because of another existence of constraints for guaranteeing the EH task of the RU. In this paragraph, we pay attention to satisfying the EH constraint with perfect and imperfect CSI under NOMA and OMA, respectively.
Figure 7 depicts the minimum transmit power versus the minimum EH value of the RU in the system with perfect and imperfect CSI. It can be seen from the result by the proposed algorithm that the transmit power consumption by adopting NOMA is lower than that of adopting OMA in the scenarios of perfect and imperfect CSI. As a matter of fact, NOMA outperforms OMA in the network secrecy rate. This situation leads to a relatively low power requirement for guaranteeing the network secrecy rate and the energy consumption of AN. It is also seen that the scenario with imperfect CSI causes a significant impact on the minimum transmit power because of the estimation errors. Moreover, as the EH requirement of RU increases, a higher level of the minimum transmit power is needed to fulfill the secrecy of the information transfer and the QoS requirement for the EH task.
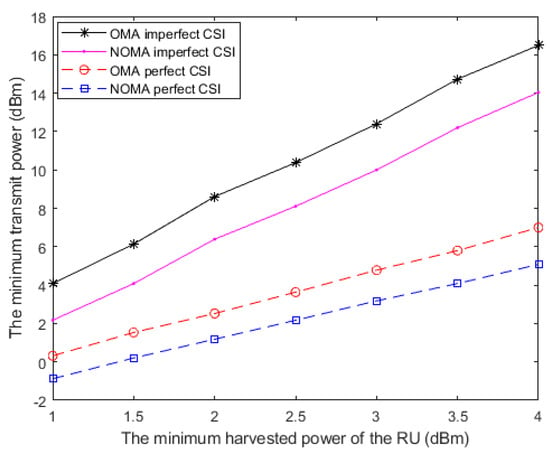
Figure 7.
The minimum transmit power versus the minimum harvested power of the roaming users (RU) in the system with perfect and imperfect CSI.
5. Conclusions
In this paper, a novel secure FD SWIPT scheme was proposed using NOMA and D2D, where a practical bounded CSI estimation method was applied. The secrecy rate was defined to guarantee the secure transmission and a linear EH model was built to evaluate the energy saving of the system. The proposed network transmit power minimization problem was divided into two sub-problems and formulated as an MOO problem via the weighted Tchebycheff approach. A method with LMI was used to transform the non-convex constraints into convex form. Taking into account the potential eavesdropper RU with imperfect CSI for the robust power-efficient resource allocation, a bounded transmission beamforming vector design along with an AN vector was used. Through this method, the system could satisfy the requirements of the secrecy rates as well as the EH task. Numerical simulation results not only validated the convergence performance but also showed a trade-off between the UL and DL transmit power of the MOO algorithm. Furthermore, we noted that by FD and NOMA, the utility of the proposed iterative algorithm is higher than that with HD and OMA with the same parameter. Moreover, our proposed SWIPT optimization scheme is efficient to satisfy the EH requirement.
Author Contributions
Conceptualization, J.W. and Z.X.; methodology, J.W.; software, J.W.; validation, X.S., Y.M. and Z.X.; formal analysis, J.W.; investigation, Y.M.; resources, X.S. data curation, Y.M.; writing—original draft preparation, J.W.; writing—review and editing, Z.X.; visualization, J.W.; supervision, Y.M.; project administration, X.S.; funding acquisition, X.S. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Nature Science Foundation of China grant number 61601109. And the APC was funded by the Fundamental Research Funds for the Central Universities grant number N152305001.
Acknowledgments
The authors thank the anonymous reviewers for their insightful comments that helped improve the quality of this study.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
The Lagrange function of problem (47) is as follows (take as an example):
where and are dual variables, and is the adjoint variable of .
where and . With Karush–Kuhn–Tucker (KKT) conditions, we have
where . Further, we define that and Thus,
Next, we proof . Substituting part of (A5) with (A2), we have
By post-multiplying , we get
Note that and define , we can get
After both sides of (A6) are multiplied by , we can get
Lemma A1.
If the Hermitian matrix ⪰0, then it immediately follows that and must be the positive semi-definite (PSD) matrix [20].
Here, we can claim that ⪰0 and the left side of this formula is nonsingular. We post-multiply a nonsingular matrix without changing the matrix rank and get
Lemma A2.
Let and be two matrixes of the same size. Then, it holds true that rank ( − ) rank () - rank () [21].
Through Lemma A2, we can derive . If is a positive definite, and . However, if rank () = M, i.e., becomes a full-rank matrix. Following 54, we note that cannot be the optimal solution to (47). Therefore, we have rank () = M−1, and with 54, we can conclude rank () = 1. Hence, can be substituted by , and here, spans the null space of with .
The next step is to proof ⪰ 0, which means to show that is a positive definite matrix. Since we have the conditions that ⪰ 0 and ⪰ 0 for ⪰ 0 and ⪰ 0, by contradiction, we can explain that ⪰ 0 must always hold. Assume 0 is the minimum eigenvalue of . Then, there exists at least a vector such that According to (A4), it follows that <0. This means that is not PSD and violates the KKT conditions in (A7). Hence, we conclude that ⪰ 0 must hold.
References
- Leng, S.; Ng, D.W.K.; Zlatanov, N.; Schober, R. Multi-objective resource allocation in full-duplex SWIPT systems. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 23–27 May 2016; pp. 1–7. [Google Scholar]
- Hu, J.; Zhao, Y.; Yang, K. Modulation and Coding Design for Simultaneous Wireless Information and Power Transfer. IEEE Commun. Mag. 2019, 57, 124–130. [Google Scholar] [CrossRef]
- Zhang, J.; Tao, X.; Wu, H.; Zhang, X. Secure Transmission in SWIPT-Powered Two-Way Untrusted Relay Networks. IEEE Access 2018, 6, 10508–10519. [Google Scholar] [CrossRef]
- Xia, M.; Aissa, S. On the efficiency of far-field wireless power transfer. IEEE Trans. Signal Process. 2015, 63, 2835–2847. [Google Scholar] [CrossRef]
- Tran, H.; Kaddoum, G.; Abou-Rjeily, C. Collaborative RF and Lightwave Power Transfer for Next-Generation Wireless Networks. IEEE Commun. Mag. 2020, 58, 27–33. [Google Scholar] [CrossRef]
- Haci, H.; Zhu, H.; Wang, J. Performance of Non-orthogonal Multiple Access With a Novel Asynchronous Interference Cancellation Technique. IEEE Trans. Commun. 2017, 65, 1319–1335. [Google Scholar] [CrossRef]
- Dai, Y.; Sheng, M.; Zhao, K.; Liu, L.; Liu, J.; Li, J. Interference-aware resource allocation for D2D underlaid cellular network using SCMA: A hypergraph approach. In Proceedings of the 2016 IEEE Wireless Communications and Networking Conference, Doha, Qatar, 3–6 April 2016; pp. 1–6. [Google Scholar]
- Elshaer, H.; Vlachos, C.; Friderikos, V.; Dohler, M. Interference-Aware Decoupled Cell Association in Device-to-Device Based 5G Networks. In Proceedings of the 2016 IEEE 83rd Vehicular Technology Conference (VTC Spring), Nanjing, China, 15–18 May 2016; pp. 1–5. [Google Scholar]
- Chang, T.; Liu, Y.; Lin, S. Max-min-fairness linear transceiver design for full-duplex multiuser systems. In Proceedings of the 2017 IEEE 18th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Sapporo, Japan, 3–6 July 2017; pp. 1–5. [Google Scholar]
- Sun, Y.; Ng, D.W.K.; Zhu, J.; Schober, R. Robust and Secure Resource Allocation for Full-Duplex MISO Multicarrier NOMA Systems. IEEE Trans. Commun. 2018, 66, 4119–4137. [Google Scholar] [CrossRef]
- Tiong, T. Robust Secure SWIPT MISO. In Proceedings of the 2019 7th International Conference on Smart Computing & Communications (ICSCC), Sarawak, Malaysia, 28–30 June 2019; pp. 1–5. [Google Scholar]
- Li, Q.; Ma, W.-K. Spatially selective artificial-noise aided transmit optimization for MISO multi-eves secrecy rate maximization. IEEE Trans. Signal Process. 2013, 61, 2704–2717. [Google Scholar] [CrossRef]
- Zhao, X.; Xiao, J.; Li, Q.; Zhang, Q.; Qin, J. Joint Optimization of AN-Aided Transmission and Power Splitting for MISO Secure Communications With SWIPT. IEEE Commun. Lett. 2015, 19, 1969–1972. [Google Scholar] [CrossRef]
- Roh, W.; Seol, J.Y.; Park, J.; Lee, B.; Lee, J.; Kim, Y.; Cho, J.; Cheun, K.; Aryanfar, F. Millimeter-wave beamforming as an enabling technology for 5G cellular communications: Theoretical feasibility and prototype results. IEEE Commun. Mag. 2014, 52, 106–113. [Google Scholar] [CrossRef]
- Sun, Y.; Ng, D.W.K.; Zhu, J.; Schober, R. Multi-Objective Optimization for Robust Power Efficient and Secure Full-Duplex Wireless Communication Systems. IEEE Trans. Wirel. Commun. 2016, 15, 5511–5526. [Google Scholar] [CrossRef]
- Pi, Z.; Khan, F. An introduction to millimeter-wave mobile broadband systems. IEEE Commun. Mag. 2011, 49, 101–107. [Google Scholar] [CrossRef]
- Zhou, F.; Chu, Z.; Sun, H.; Hu, R.Q.; Hanzo, L. Artificial Noise Aided Secure Cognitive Beamforming for Cooperative MISO-NOMA Using SWIPT. IEEE J. Sel. Areas Commun. 2018, 36, 918–931. [Google Scholar] [CrossRef]
- Ng, D.W.K.; Schober, R. Secure and Green SWIPT in Distributed Antenna Networks With Limited Backhaul Capacity. IEEE Trans. Wirel. Commun. 2015, 14, 5082–5097. [Google Scholar] [CrossRef]
- Bharadia, D.; McMilin, E.; Katti, S. Full duplex radios. In Proceedings of the ACM SIGCOMM, Hongkong, China, 12–16 August 2013; pp. 375–386. [Google Scholar]
- Bertsekas, D.P. Nonlinear Programming; Athena scientific Belmont: Belmont, MA, USA, 1999. [Google Scholar]
- Lee, B.G.; Park, D.; Seo, H. Mathematical Tools for Resource Management. In Wireless Communications Resource Management; IEEE: Piscataway, NJ, USA, 2009; pp. 73–106. [Google Scholar]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).