A Lightweight Authentication and Key Agreement Schemes for IoT Environments
Abstract
1. Introduction
- We analyze existing lightweight authentication and key agreement schemes for IoT environments.
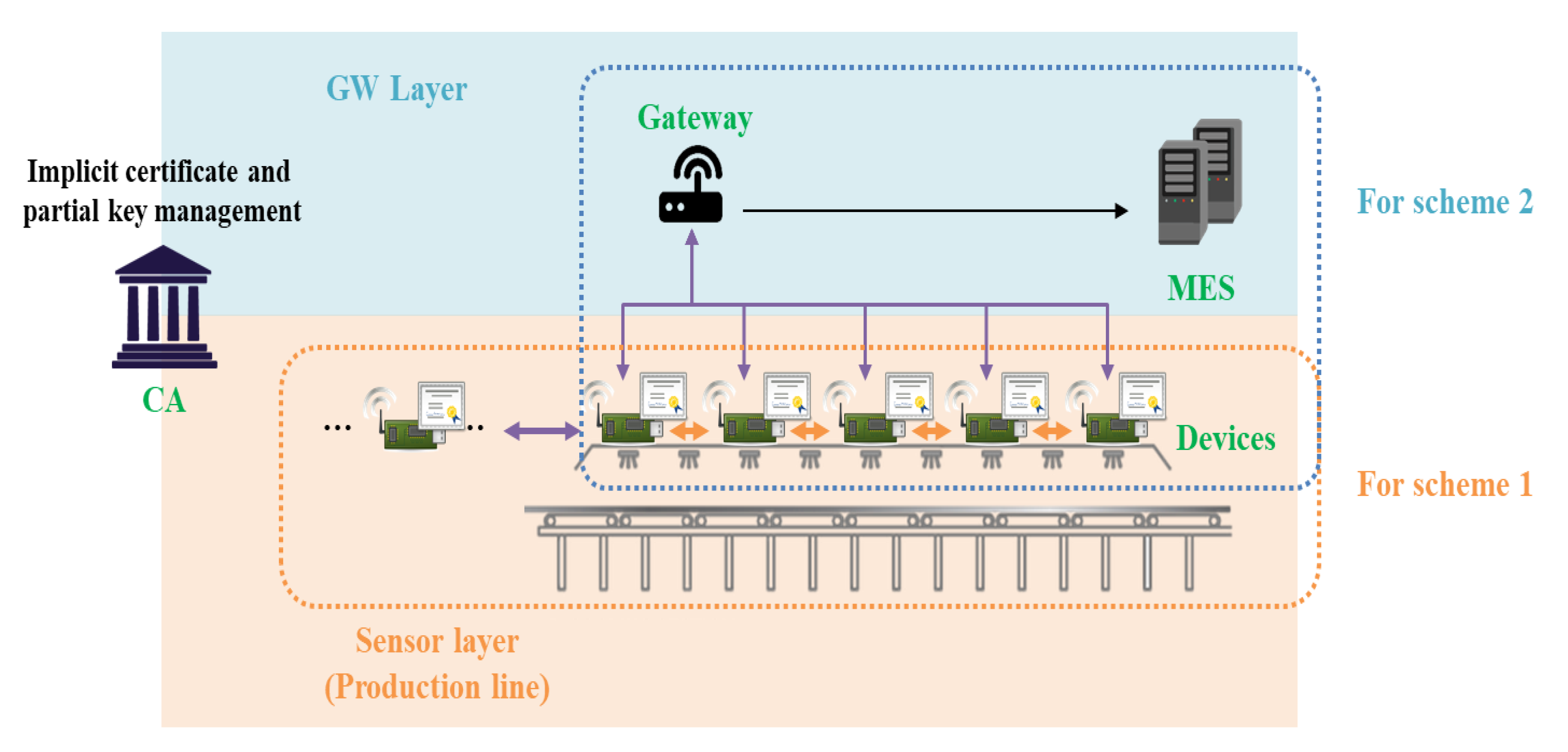
- In an environment where fast communication is required, we propose a scheme that enables rapid mutual authentication and key agreement through ECQV implicit certificates. This scheme provides implicit authentication for public keys (Scheme 1).
- Although slower than Scheme 1, we propose an efficient authentication and key agreement scheme based on CL-PKC that allows explicit verification of public keys (Scheme 2).
2. Background and Related Work
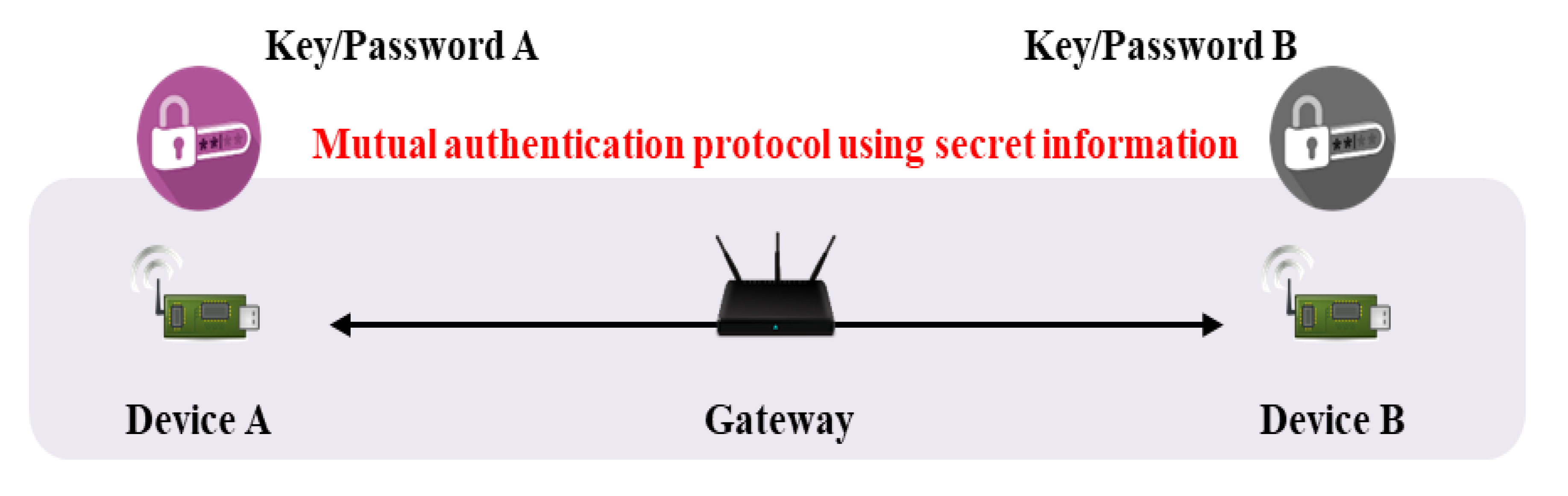
2.1. Authentication and Key Agreement (AKA)
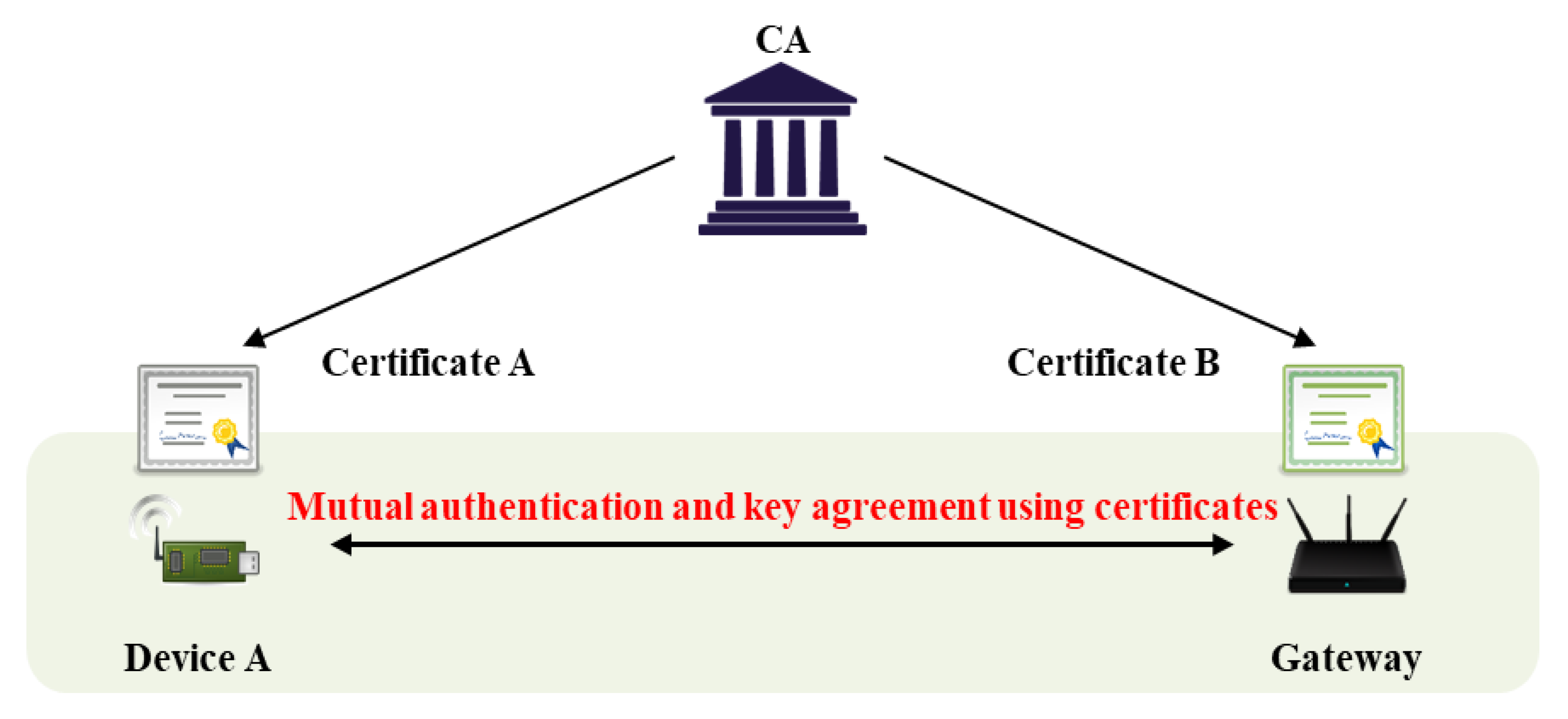
2.2. AKA with ECQV Implicit Certificate
2.3. AKA with Pairing-Free Certificateless PKC
2.4. Analysis of Existing Schemes
2.4.1. Fast AKA Schemes Including ECQV-Based AKA
2.4.2. CL-AKA Schemes
- Setup: the KGC generates a public parameter and a master secret key (security parameter inputs).
- Partial-Key-Extract: the KGC generates a user’s partial private and public keys using the public parameter, master secret key, and user’s ID, and delivers it to the user.
- Set-Secret-Value: the user creates secret information by inputting the public parameter and his/her ID.
- Set-Private-Key: the user sets a private key by inputting the public parameter, partial private key, and secret information.
- Set-Public-Key: the user sets a public key by inputting the public parameter, his/her partial public key, and secret information.
- Key Agreement: users A and B generate messages using their IDs, public keys, and temporary keys. After exchanging messages, a common session key is generated using secret information. If the protocol is successful, the session keys generated by the two communicators will be identical.
3. Security Requirements
3.1. Mutual Authentication
3.2. Prevent Key Leakage
3.3. Prevent Replay and Masquerade Attacks
4. Proposed Schemes
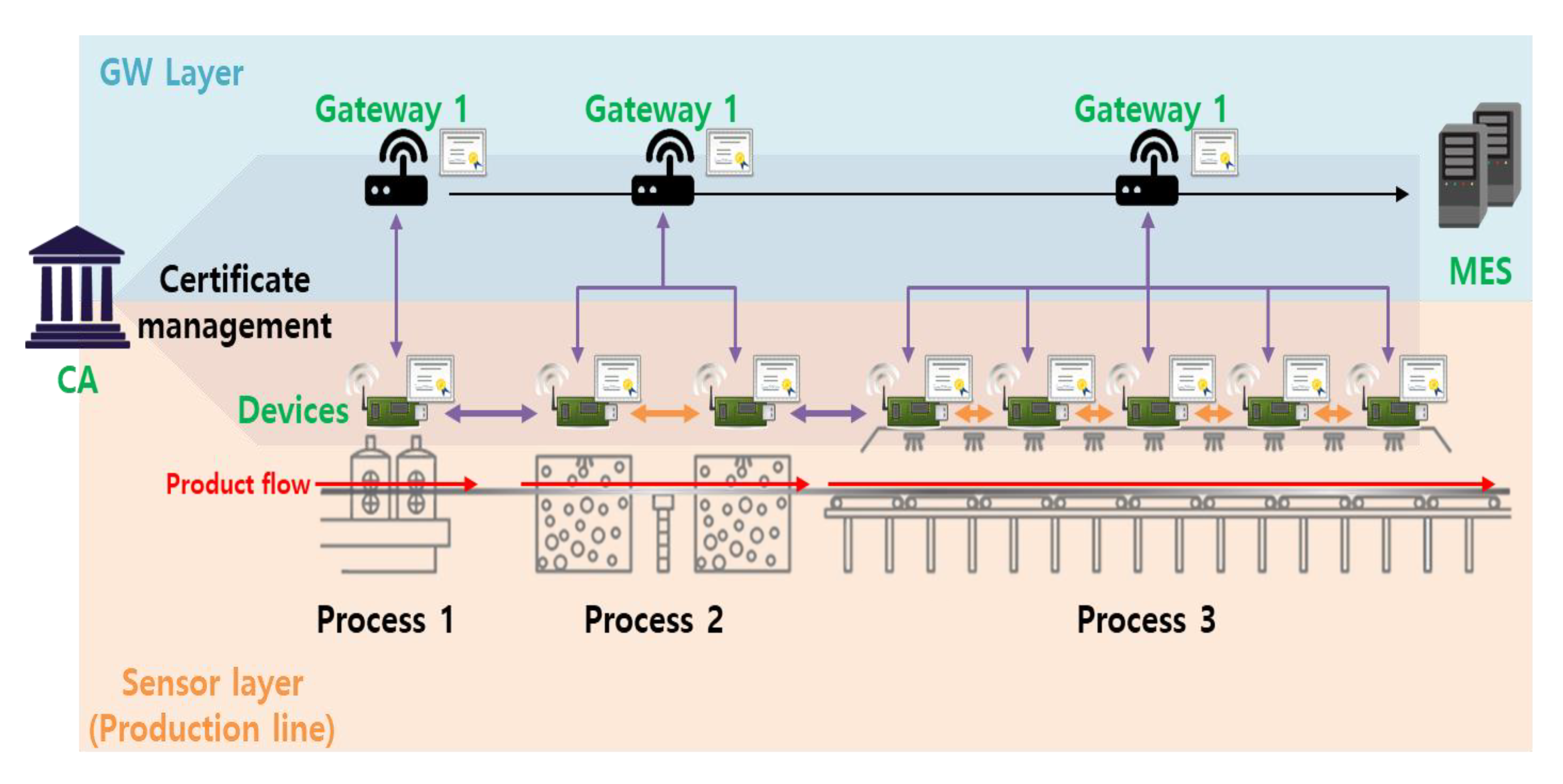
4.1. Proposed Model
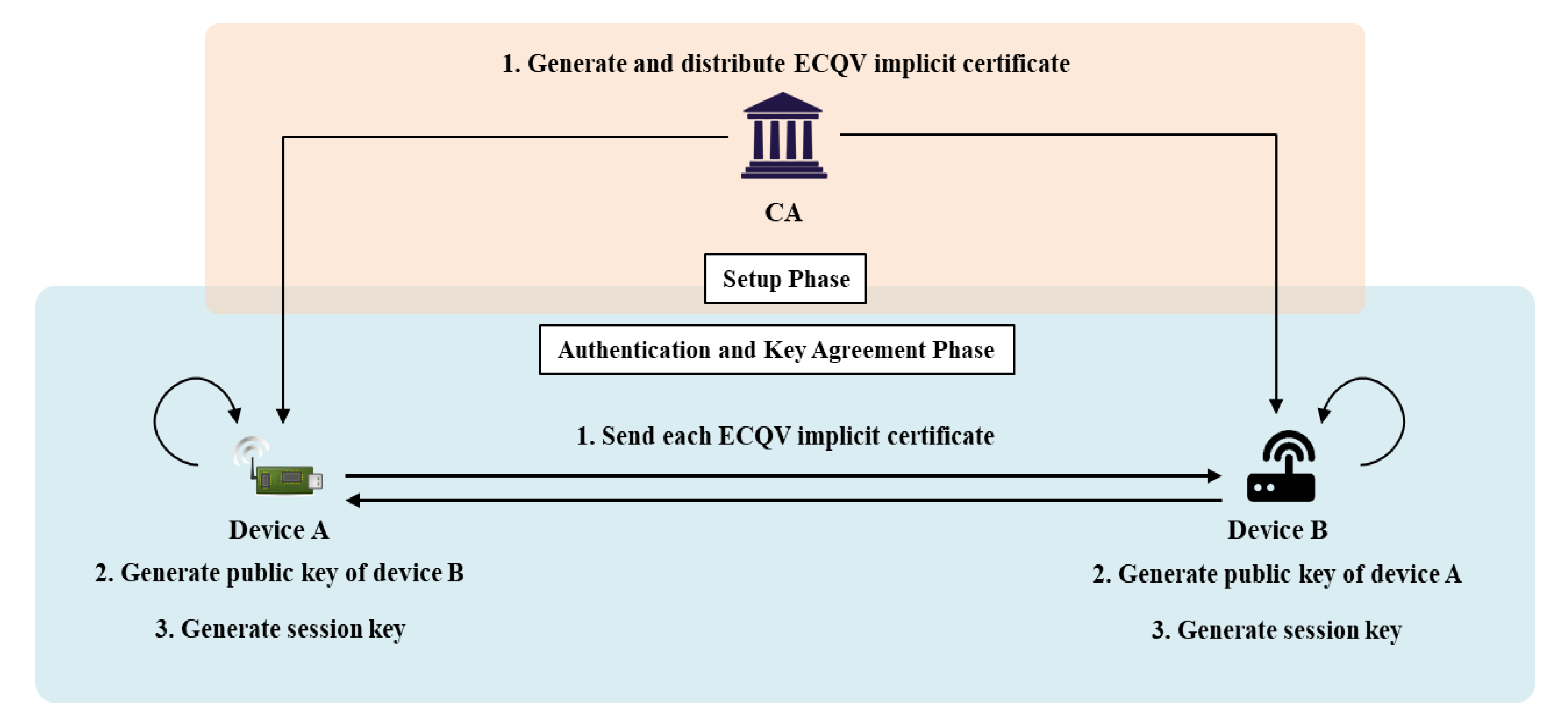
4.2. AKA via an ECQV Implicit Certificate (Scheme 1)
- : A communication participant (CA: certificate authority, A: device A, B: device B).
- : Identifier of the entity;
- : The public and private key pair of the entity;
- : An elliptic curve on group G of prime order q;
- : The generator on cyclic group G used to calculate the certificate;
- : The ECQV implicit certificate of the entity;
- : The cryptographic hash function;
- : The shared secret value used by the two objects to agree on the session key;
- : The key derivation function;
- : The agreed key to be used in the current session.
4.2.1. Setup Phase
4.2.2. Authentication and Key Agreement Phase
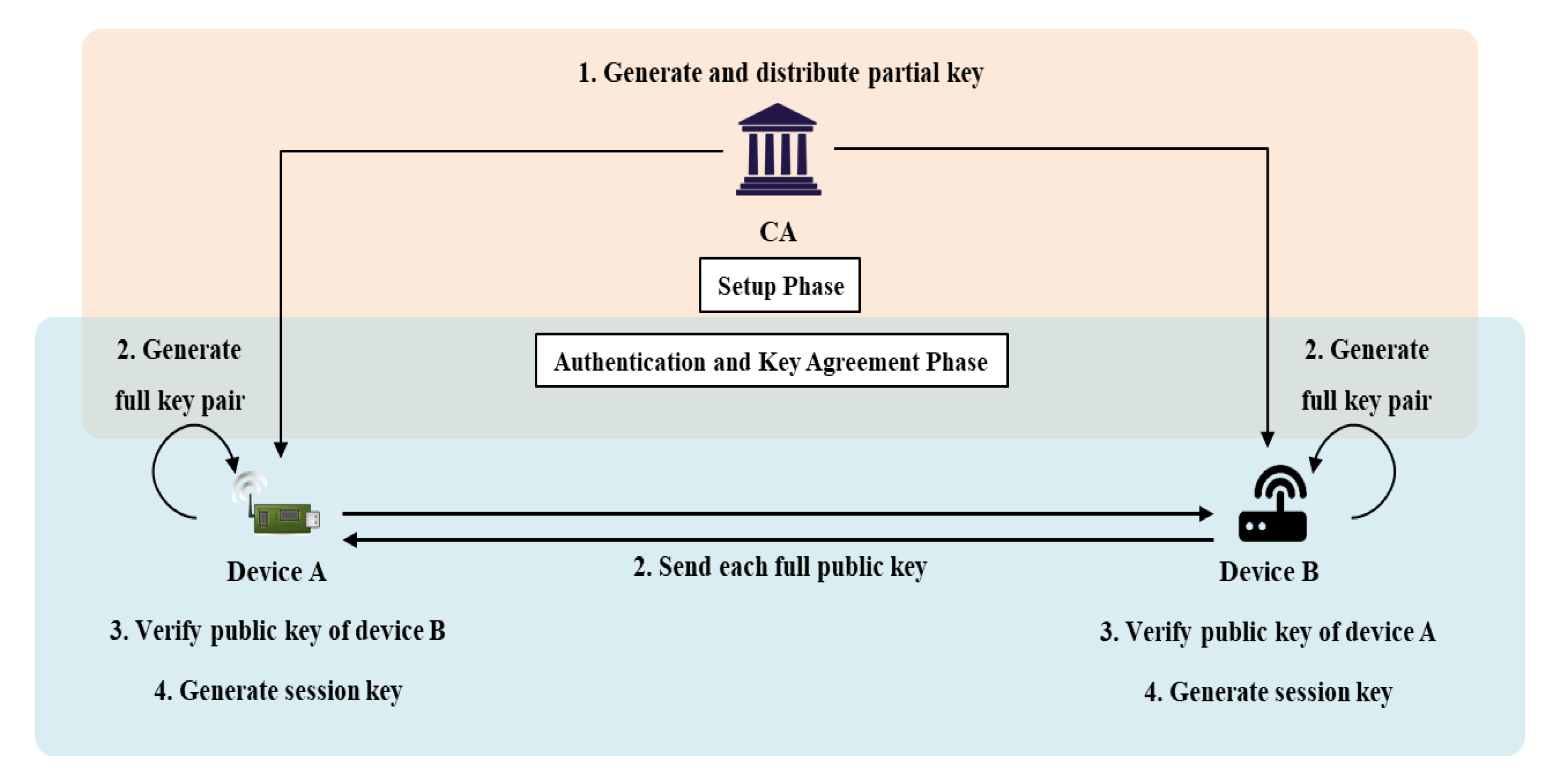
4.3. Proposed AKA with Pairing-Free Certificateless PKC (Scheme 2)
- : A communication participant (CA: certificate authority, A: device A, B: device B).
- : The identifier of an entity;
- : An elliptic curve on group G of prime order q;
- : The generator of cyclic group G;
- : The CA master secret key;
- : The CA master public key;
- : The verification private/public key pair generated by an entity;
- : The partial key of an entity;
- : The full private and public key pair;
- : The mapping hash function ;
- : The mapping hash function
- : The one-way hash function;
- : The session key to be used (generated via agreement).
4.3.1. Setup Phase
4.3.2. Authentication and Key Agreement Phase
5. Analysis of Proposed Schemes
5.1. Mutual Authentication
5.2. Prevent Key Leakage
5.3. Prevent Replay and Masquerade Attacks
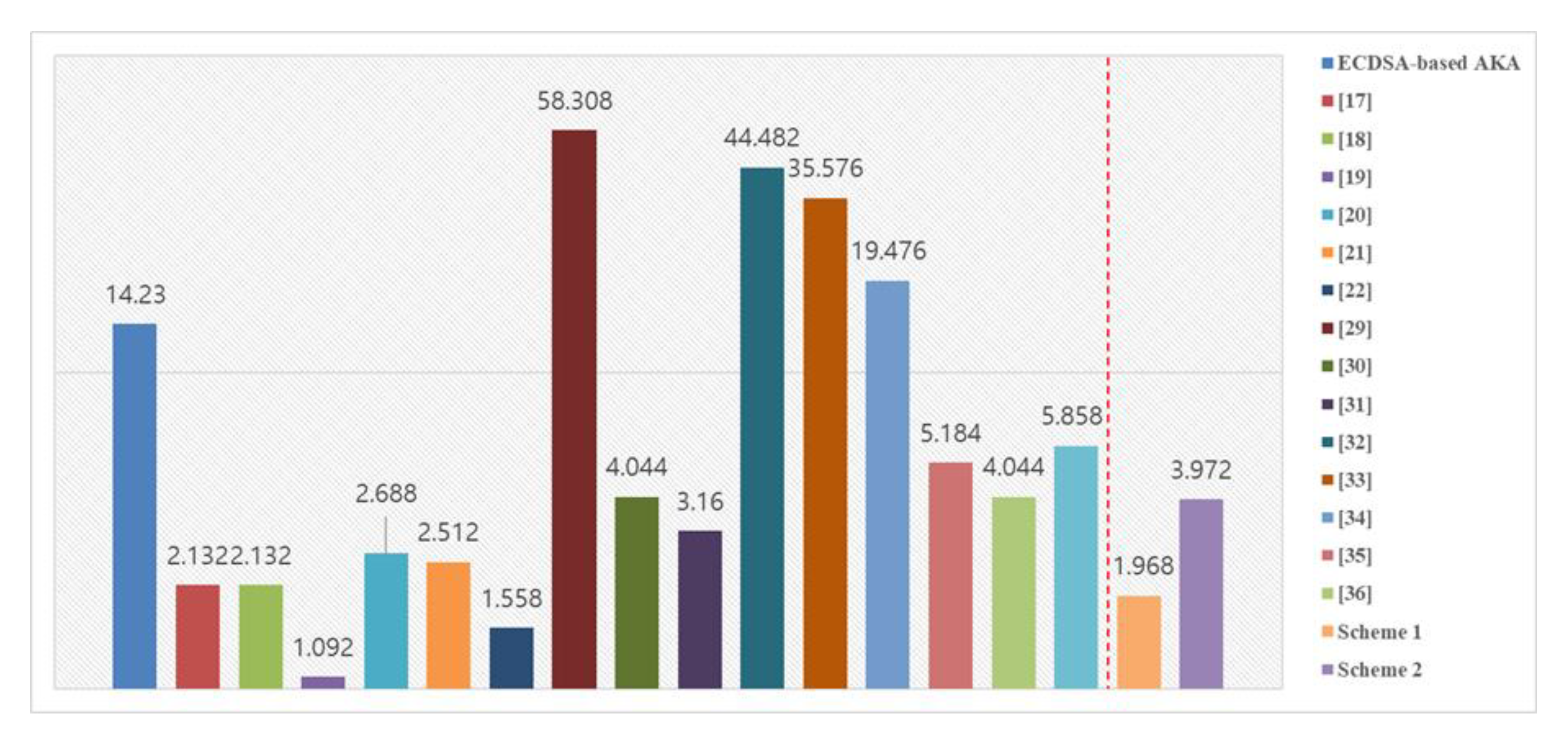
5.4. Efficiency
6. Conclusions and Future Research
Author Contributions
Funding
Conflicts of Interest
References
- Skouby, K.E.; Lynggaard, P. Smart home and smart city solutions enabled by 5G, IoT, AAI and CoT services. In Proceedings of the 2014 International Conference on Contemporary Computing and Informatics (IC3I), Mysore, India, 27–29 November 2014; pp. 874–878. [Google Scholar]
- Li, S.; Xu, L.D.; Zhao, S. 5G Internet of things: A survey. J. Ind. Inf. Integr. 2018, 10, 1–9. [Google Scholar] [CrossRef]
- Yang, H.; Lee, W.; Lee, H. IoT Smart Home Adoption: The Importance of Proper Level Automation. Available online: https://www.hindawi.com/journals/js/2018/6464036/ (accessed on 2 September 2020).
- Kim, T.; Ramos, C.; Mohammed, S. Smart city and IoT. Future Gener. Comput. Syst. 2017, 76, 159–162. [Google Scholar] [CrossRef]
- Jing, Q.; Vasilakos, A.V.; Wan, J.; Lu, J.; Qiu, D. Security of the Internet of Things: Perspectives and challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Shrouf, F.; Ordieres, J.; Miragliotta, G. Smart factories in Industry 4.0: A review of the concept and of energy management approached in production based on the Internet of Things paradigm. In Proceedings of the 2014 IEEE International Conference on Industrial Engineering and Engineering Management, Petaling Jaya, Malaysia, 9–12 December 2014; pp. 697–701. [Google Scholar]
- Chakrabarty, S.; Engels, D.W. A secure IoT architecture for Smart Cities. In Proceedings of the 2016 13th IEEE Annual Consumer Communications Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2016; pp. 812–813. [Google Scholar]
- Diffie, W.; Hellman, M. New directions in cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–654. [Google Scholar] [CrossRef]
- Lu, R.; Cao, Z. Simple three-party key exchange protocol. Comput. Secur. 2007, 26, 94–97. [Google Scholar] [CrossRef]
- Kim, H.-S.; Choi, J.-Y. Enhanced password-based simple three-party key exchange protocol. Comput. Electr. Eng. 2009, 35, 107–114. [Google Scholar] [CrossRef]
- Hummen, R.; Ziegeldorf, J.H.; Shafagh, H.; Raza, S.; Wehrle, K. Towards viable certificate-based authentication for the internet of things. In Proceedings of the 2nd ACM Workshop on Hot Topics on Wireless Network Security and Privacy, Budapest, Hungary, 17–19 April 2013; pp. 37–42. [Google Scholar]
- Lin, C.; He, D.; Huang, X.; Choo, K.-K.R.; Vasilakos, A.V. BSeIn: A blockchain-based secure mutual authentication with fine-grained access control system for industry 4.0. J. Netw. Comput. Appl. 2018, 116, 42–52. [Google Scholar] [CrossRef]
- Jangirala, S.; Das, A.K.; Vasilakos, A.V. Designing secure lightweight blockchain-enabled RFID-based authentication protocol for supply chains in 5G mobile edge computing environment. IEEE Trans. Ind. Inf. 2020, 16, 7081–7093. [Google Scholar] [CrossRef]
- Campagna, M. SEC 4: Elliptic Curve Qu-Vanstone Implicit Certificate Scheme (ECQV). Available online: https://www.secg.org/sec4-1.0.pdf (accessed on 2 June 2020).
- Shamir, A. Identity-based cryptosystems and signature schemes. In Proceedings of the Advances in Cryptology; Blakley, G.R., Chaum, D., Eds.; Springer: Berlin/Heidelberg, Germany, 1985; pp. 47–53. [Google Scholar]
- Al-Riyami, S.S.; Paterson, K.G. Certificateless public key cryptography. In Proceedings of the Advances in Cryptology—ASIACRYPT 2003, Taipei, Taiwan, 30 November–4 December 2003; Laih, C.-S., Ed.; Springer: Berlin/Heidelberg, Germany, 2003; pp. 452–473. [Google Scholar]
- Sciancalepore, S.; Capossele, A.; Piro, G.; Boggia, G.; Bianchi, G. Key management protocol with implicit certificates for IoT systems. In Proceedings of the 2015 Workshop on IoT challenges in Mobile and Industrial Systems, Florence, Italy, 18 May 2015; pp. 37–42. [Google Scholar]
- Sciancalepore, S.; Piro, G.; Boggia, G.; Bianchi, G. Public key authentication and key agreement in IoT devices with minimal airtime consumption. IEEE Embed. Syst. Lett. 2017, 9, 1–4. [Google Scholar] [CrossRef]
- Abdmeziem, M.R.; Tandjaoui, D. An end-to-end secure key management protocol for e-health applications. Comput. Electr. Eng. 2015, 44, 184–197. [Google Scholar] [CrossRef]
- Challa, S.; Das, A.K.; Gope, P.; Kumar, N.; Wu, F.; Vasilakos, A.V. Design and analysis of authenticated key agreement scheme in cloud-assisted cyber–physical systems. Future Gener. Comput. Syst. 2020, 108, 1267–1286. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Conti, M.; Jo, M. Design of secure user authenticated key management protocol for generic IoT networks. IEEE Internet Things J. 2018, 5, 269–282. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Vasilakos, A.V. Authenticated key management protocol for cloud-assisted body area sensor networks. J. Netw. Comput. Appl. 2018, 123, 112–126. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Bhat, K.V.; Vasilakos, A.V. LAM-CIoT: Lightweight authentication mechanism in cloud-based IoT environment. J. Netw. Comput. Appl. 2020, 150, 102496. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V. Design of secure key management and user authentication scheme for fog computing services. Future Gener. Comput. Syst. 2019, 91, 475–492. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V.; Rodrigues, J.J.P.C. Design and analysis of secure lightweight remote user authentication and key agreement scheme in internet of drones deployment. IEEE Internet Things J. 2019, 6, 3572–3584. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Conti, M.; Vasilakos, A.V. A novel authentication and key agreement scheme for implantable medical devices deployment. IEEE J. Biomed. Health Inform. 2018, 22, 1299–1309. [Google Scholar] [CrossRef]
- Geng, M.; Zhang, F. Provably secure certificateless two-party authenticated key agreement protocol without pairing. In Proceedings of the 2009 International Conference on Computational Intelligence and Security, Beijing, China, 11–14 December 2009; Volume 2, pp. 208–212. [Google Scholar]
- Hou, M.; Xu, Q. A Two-party certificateless authenticated key agreement protocol without pairing. In Proceedings of the 2009 2nd IEEE International Conference on Computer Science and Information Technology, Beijing, China, 8–11 August 2009; pp. 412–416. [Google Scholar]
- Yang, G.; Tan, C.-H. Strongly secure certificateless key exchange without pairing. In Proceedings of the 6th ACM Symposium on Information, Computer and Communications Security, Hong Kong, China, 22–24 March 2011; Association for Computing Machinery: New York, NY, USA, 2011; pp. 71–79. [Google Scholar]
- Kim, Y.-J.; Kim, Y.-M.; Choe, Y.-J.; O Chol, H. An efficient bilinear pairing-free certificateless two-party authenticated key agreement protocol in the eCK model. arXiv 2013, arXiv:1304.0383. [Google Scholar]
- Farouk, A.; Miri, A.; Fouad, M.M.; Abdelhafez, A.A. Efficient pairing-free, certificateless two-party authenticated key agreement protocol for grid computing. In Proceedings of the 2014 Fourth International Conference on Digital Information and Communication Technology and its Applications (DICTAP), Bangkok, Thailand, 6–8 May 2014; pp. 279–284. [Google Scholar]
- Xie, Y.; Wu, L.; Zhang, Y.; Xu, Z. Strongly secure two-party certificateless key agreement protocol with short message. In Proceedings of the Provable Security; Chen, L., Han, J., Eds.; Springer International Publishing: Cham, Switzerland, 2016; pp. 244–254. [Google Scholar]
- Park, J.S.; Ha, J.C. Certificateless-based Authenticated Key Agreement (AKA) protocol without pairings. J. Secur. Eng. 2016, 13, 451–466. [Google Scholar] [CrossRef]
- Sun, H.; Wen, Q.; Li, W. A strongly secure pairing-free certificateless authenticated key agreement protocol under the CDH assumption. Sci. China Inf. Sci. 2016, 59, 32109. [Google Scholar] [CrossRef]
- Simplicio, M.A., Jr.; Silva, M.V.M.; Alves, R.C.A.; Shibata, T.K.C. Lightweight and escrow-less authenticated key agreement for the internet of things. Comput. Commun. 2017, 98, 43–51. [Google Scholar] [CrossRef]
- Xie, Y.; Wu, L.; Shen, J.; Li, L. Efficient two-party certificateless authenticated key agreement protocol under GDH assumption. Int. J. Ad Hoc Ubiquitous Comput. 2018, 30, 11–25. [Google Scholar] [CrossRef]
- Daniel, R.M.; Rajsingh, E.B.; Silas, S. An efficient eCK secure certificateless authenticated key agreement scheme with security against public key replacement attacks. J. Inf. Secur. Appl. 2019, 47, 156–172. [Google Scholar] [CrossRef]
- Kayes, A.S.M.; Kalaria, R.; Sarker, I.H.; Islam, M.S.; Watters, P.A.; Ng, A.; Hammoudeh, M.; Badsha, S.; Kumara, I. A survey of context-aware access control mechanisms for cloud and fog networks: Taxonomy and open research issues. Sensors 2020, 20, 2464. [Google Scholar] [CrossRef] [PubMed]
| Explicit Certificate | Implicit Certificate | |
|---|---|---|
| Key Derivation | Included in the certificate | Must be calculated using certificates and signatures |
| Public Key Verification | Signature verification using a public key | No verification process |
| Structure | Identifier, public key, electronic signature | Identifier, public key recovery data |
| Comparison | The key and certificate sizes are relatively large (PKI); slow | The key and certificate sizes are relatively small (ECC); fast |
| Strength | Key Length (Bits) | Certificate Size (Bits) | |||
|---|---|---|---|---|---|
| ECC | RSA | ECQV | ECDSA | RSA | |
| 80 | 192 | 1024 | 193 | 577 | 2048 |
| 112 | 224 | 2048 | 225 | 673 | 4096 |
| 128 | 256 | 3072 | 257 | 769 | 6144 |
| 192 | 384 | 7680 | 358 | 1153 | 15,360 |
| 256 | 521 | 15,360 | 522 | 1564 | 30,720 |
| [17] | [18] | [19] | [20] | [21] | [22] | Proposed Scheme 1 | |
|---|---|---|---|---|---|---|---|
| Prevent Key Leakage Attack | O | O | X Possible to steal key during connection | O | X The key of the node is leaked to the user | O | O |
| Prevent Masquerade | X Possible to masquerade as a result of replay | X Possible to masquerade as a result of replay | X Possible session hijacking during connection | X Possible to masquerade without key agreement | X Possible to masquerade via node’s key | X Cannot provide non-repudiation of sender | O |
| Prevent Replay Attack | X No nonce in MAC | X Reuse of published values | O | X Reuse of published values | O | O | O |
| Public Key Verifiability | ∆ Only implicit authentication | ∆ Only implicit authentication | ∆ Only implicit authentication | X Only use pre-shared symmetric key | X Only use pre-shared symmetric key | X Only use pre-shared value | ∆ Only implicit authentication |
| Operation | 2EA + 4EM + 4h | 2EA + 4EM + 4h | 4SE + 6h | 4EM + 22h | 8SE + 16h | 19h | 2EA + 4EM + 2h |
| [29] | [30] | [31] | [32] | [33] | [34] | [35] | [36] | [37] | Proposed Scheme 2 | |
|---|---|---|---|---|---|---|---|---|---|---|
| Prevent Key Leakage Attack | X Possible to leakage as a result of replay | O | X Possible to leakage as a result of masquerade | O | O | O | O | X Possible to replay with leaked temporary key | O | O |
| Prevent Masquerade | X Possible to masquerade by replay | X Possible to masquerade by replay | X Possible to masquerade by key replace | X Possible key replaces and masquerade | X Possible key replaces and masquerade | X Possible key replaces and masquerade | X Cannot verify public key | X Possible to masquerade by replay | X Possible to masquerade by replay | O |
| Prevent Replay Attack | X Possible to replay | X Possible to replay | X Possible to join session with masquerade | O | O | X Possible man-in-the-middle attack | O | O | O | O |
| Public Key Verifiability | X Possible to public key replacement | O | O | X Cannot verify public key | X Cannot verify public key | X Cannot verify public key | X Cannot verify public key | O | X Cannot verify public key | O |
| Operation | 12E + 11EM + 7h | 10EA + 8EM + 4h | 10EA + 6EM + 4h | 2P + 8EA + 8EM + 4h | 8E + 4h | 36EA + 40EM + 14h | 6EA + 10EM + 8h | 10EA + 8EM + 4h | 8EA + 12EM + 5h | 6EA + 8EM + 4h |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, D.-H.; Lee, I.-Y. A Lightweight Authentication and Key Agreement Schemes for IoT Environments. Sensors 2020, 20, 5350. https://doi.org/10.3390/s20185350
Lee D-H, Lee I-Y. A Lightweight Authentication and Key Agreement Schemes for IoT Environments. Sensors. 2020; 20(18):5350. https://doi.org/10.3390/s20185350
Chicago/Turabian StyleLee, Dae-Hwi, and Im-Yeong Lee. 2020. "A Lightweight Authentication and Key Agreement Schemes for IoT Environments" Sensors 20, no. 18: 5350. https://doi.org/10.3390/s20185350
APA StyleLee, D.-H., & Lee, I.-Y. (2020). A Lightweight Authentication and Key Agreement Schemes for IoT Environments. Sensors, 20(18), 5350. https://doi.org/10.3390/s20185350





