CANsec: A Practical in-Vehicle Controller Area Network Security Evaluation Tool
Abstract
1. Introduction
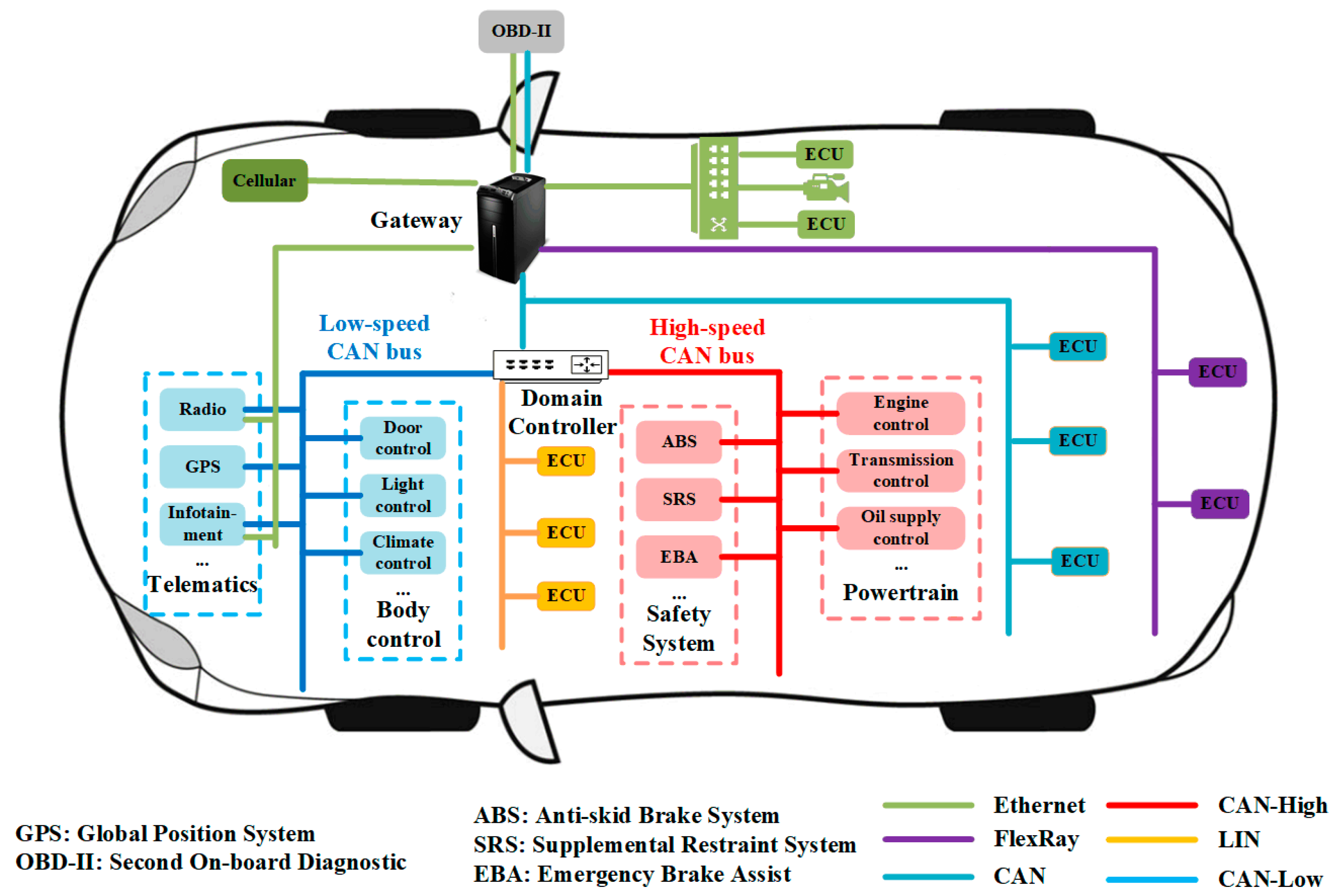
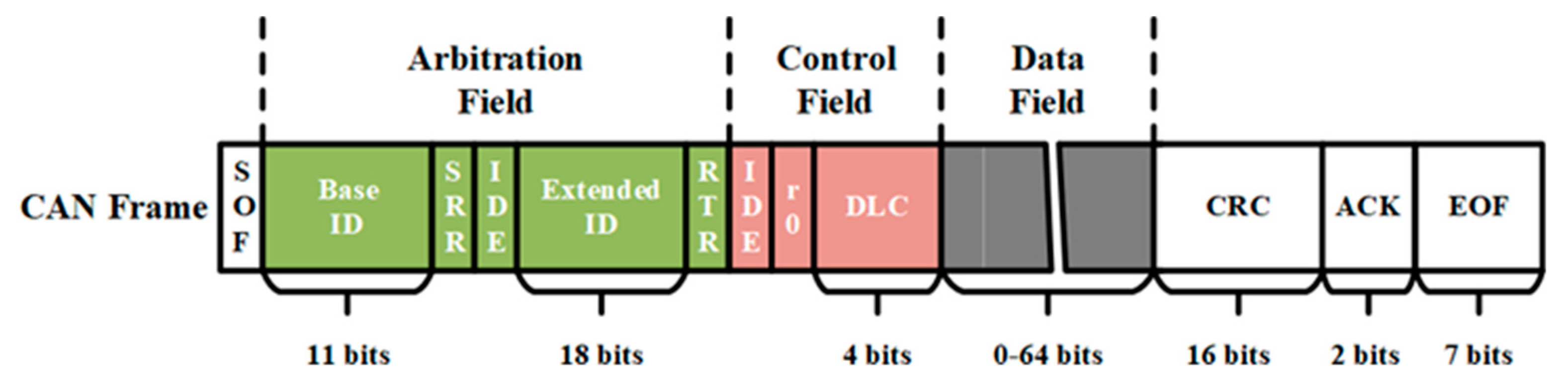
2. In-Vehicle CAN Bus Protocol
3. Vulnerabilities and Attack Vectors
3.1. Vulnerabilities
3.2. Attack Vectors
4. Proposed Security Evaluation Tool
4.1. Evaluation Methodology
4.2. In-depth Knowledge of CANsec
4.2.1. Overview of CANsec
4.2.2. Details of CANsec
- (1)
- CAN Architecture Scan. The purpose of the evaluation vector is obtaining the architecture of the In-Vehicle CAN. Users initiate the vehicle and connect the evaluation hardware device to the OBD-II port of the target vehicle. Users then eavesdrop on the CAN bus frames and record the CAN IDs that helps to indicate the architecture of the In-Vehicle CAN.
- (2)
- ECU Drop-Off. The evaluation vector tries to deny the services of the ECU. After initiating the vehicle and connecting the evaluation hardware device to the OBD-II port of the target vehicle, users eavesdrop on the CAN bus frames and record the CAN IDs. Users send the CAN frames based on the target CAN ID at a certain frequency and record the CAN IDs again. If the CAN IDs in two records change, the attack is valid, and the CAN communication is not secure.
- (3)
- Normal packets Reverse based on the frame frequency. The asset of the evaluation vector is the mapping between CAN IDs and vehicular actions. After initiating the vehicle and connecting the evaluation hardware device to the OBD-II port of the target vehicle, users eavesdrop on and record the CAN bus frames. After manipulating the target vehicle to trigger the vehicular action, users eavesdrop on the CAN bus communication and record the CAN frames again. By comparing the two records, users can find the CAN ID that occurs more frequently and replay the CAN frame related to the CAN ID. If the vehicular action occurs again, the CAN ID is related to the vehicular action.
- (4)
- Normal packets Reverse based on the data bit feature. The asset of the evaluation vector is the communication matrix. After initiating the vehicle and connecting the evaluation hardware device to the OBD-II port of the target vehicle, users eavesdrop on and record the CAN bus frames. After manipulating the target vehicle to trigger the vehicular action, users eavesdrop on the CAN bus communication and record the CAN frames again. By analyzing the two records, users can figure out the communication matrix. Users then send the CAN frame constructed according to the communication matrix to the vehicle to verify if the communication matrix is correct. If the vehicular status changes as expected, the communication matrix is correct.
- (5)
- Normal packets Replay. The purpose of the evaluation vector is verifying if the replay attack against the In-Vehicle is valid. After initiating the vehicle and connecting the evaluation hardware device to the OBD-II port of the target vehicle, users eavesdrop on and record the CAN bus frames. Users replay the CAN frame recorded to the In-Vehicle and observe the vehicular action. If the vehicle acts as the CAN frame defined, the replay attack is valid.
- (6)
- Normal packets fuzzing. The evaluation vector tries to find unknown vulnerabilities of the In-Vehicle. After initiating the vehicle and connecting the evaluation hardware device to the OBD-II port of the target vehicle, users eavesdrop on and record the CAN bus frames. Users then construct massive fuzzy normal packets based on the mutation of recorded packets, send the fuzzy normal packets, and observe the status of the vehicle. If the vehicle crashes and has another abnormal status, the fuzzy test is valid.
- (7)
- Diagnostic Service Scan. The evaluation vector aims to figure out the diagnostic services of the ECUs. After initiating the vehicle and connecting the evaluation hardware device to the OBD-II port of the target vehicle, users construct the diagnostic request according to the UDS protocol. The request should cover all diagnostic services by configuring the diagnostic frames. Users send the diagnostic frames constructed to the vehicle and record the response from the vehicle and determine if the vehicle opens the corresponding diagnostic service according to the response code from the vehicle and the UDS protocol specification.
- (8)
- Diagnostic packets Reverse. The purpose of the evaluation vector is obtaining the diagnostic command. After initiating the vehicle and connecting the evaluation hardware device to the OBD-II port of the target vehicle, users construct the diagnostic packets according to the UDS protocol by configuring the data field of the diagnostic CAN frame, send the diagnostic packets to the vehicle, and verify whether the vehicle responds with the diagnostic CAN frame correctly. If the vehicle responds with the diagnostic CAN frame correctly, we reverse the diagnostic command correctly.
- (9)
- ECU Access. The asset of the evaluation vector is the access right of the ECU. After initiating the vehicle and connecting the evaluation hardware device to the OBD-II port of the target vehicle, users choose the diagnostic session mode that needs authentication, send the authentication request constructed based on the UDS protocol to the vehicle, and record the seed from the vehicle. Users then calculate the key based on the seed and send the key to the vehicle. If the CANsec can access the ECU in security mode, the attack is valid.
- (10)
- Diagnostic packets Replay. The evaluation vector tries to verify whether the diagnostic replay attack for the In-Vehicle is valid. After initiating the vehicle and connecting the evaluation hardware device to the OBD-II port of the target vehicle, CANsec eavesdrops on and records the session between the diagnostic tool and vehicle. Users then replay the diagnostic packets recorded to the In-Vehicle CAN and observe the vehicular action. If the vehicle response to the diagnostic packets, the replay attack is valid.
- (11)
- Diagnostic packets fuzzing. The evaluation vector tries to find unknown vulnerabilities in the diagnostic services. After initiating the vehicle and connecting the evaluation hardware device to the OBD-II port of the target vehicle, CANsec constructs massive fuzzy normal packets based on the UDS protocol, sends fuzzy normal packets, and observes the status of the vehicle. If the vehicle crashes and has another abnormal status, the fuzzy test is valid.
4.2.3. Advantages of CANsec
- (1)
- CANsec allows users to configure the evaluation flexibly after selecting the evaluation vectors.
- (2)
- CANsec supports the 11 evaluation vectors defined above based on four basic attack vectors. And CANsec provides a comprehensive assessment of IVNs, including normal packets assessment and diagnostic packets assessment.
- (3)
- CANsec can monitor the change in vehicular status and log the evaluation activity.
- (4)
- Besides the replay attack, the DoS attack, and the fuzzing attack, CANsec can also reverse CAN traffic to obtain the communication matrix of the manufacturers.
5. Experiments
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Kelarestaghi, K.B.; Foruhandeh, M.; Heaslip, K.; Gerdes, R. Intelligent Transportation System Security: Impact-Oriented Risk Assessment of In-Vehicle Networks. IEEE Intell. Transp. Syst. Mag. 2019, 1. [Google Scholar] [CrossRef]
- Kimm, H.; Ham, H. Integrated fault tolerant system for automotive bus networks. In Proceedings of the 2010 Second International Conference on Computer Engineering and Applications, Bali Island, Indonesia, 19–21 March 2010; Volume 1, pp. 486–490. [Google Scholar]
- Huang, J.; Zhao, M.; Zhou, Y.; Xing, C.-C. In-Vehicle Networking: Protocols, Challenges, and Solutions. IEEE Netw. 2018, 33, 92–98. [Google Scholar] [CrossRef]
- Carnevale, B.; Fanucci, L.; Bisase, S.; Hunjan, H. Macsec-based security for automotive ethernet backbones. J. Circuits Syst. Comput. 2018, 27, 1850082. [Google Scholar] [CrossRef]
- Dvořák, J.; Hanzálek, Z. Using two independent channels with gateway for FlexRay static segment scheduling. IEEE Trans. Ind. Inform. 2016, 12, 1887–1895. [Google Scholar] [CrossRef]
- Koscher, K.; Czeskis, A.; Roesner, F.; Patel, S.; Kohno, T.; Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; et al. Experimental Security Analysis of a Modern Automobile. In Proceedings of the 2010 IEEE Symposium on Security and Privacy, Berkeley/Oakland, CA, USA, 16–19 May 2010; pp. 447–462. [Google Scholar] [CrossRef]
- Bozdal, M.; Samie, M.; Aslam, S.; Jennions, I. Evaluation of CAN Bus Security Challenges. Sensors 2020, 20, 2364. [Google Scholar] [CrossRef] [PubMed]
- Huang, T.; Zhou, J.; Bytes, A. ATG: An attack traffic generation tool for security testing of in-vehicle CAN bus. In Proceedings of the 13th International Conference on Availability, Reliability and Security, Hamburg, Germany, 27–30 August 2018; pp. 1–6. [Google Scholar]
- Park, H.B.; Kim, Y.; Jeon, J.; Moon, H.S.; Woo, S. Practical Methodology for In-Vehicle CAN Security Evaluation. J. Internet Serv. Inf. Secur. (JISIS) 2019, 9, 42–56. [Google Scholar]
- Cho, K.T.; Shin, K.G. Fingerprinting electronic control units for vehicle intrusion detection. In Proceedings of the 25th USENIX Security Symposium (USENIX Security 16), Austin, TX, USA, 10–12 August 2016; pp. 911–927. [Google Scholar]
- Kang, M.J.; Kang, J.W. Intrusion detection system using deep neural network for in-vehicle network security. PLoS ONE 2016, 11, e0155781. [Google Scholar] [CrossRef] [PubMed]
- Taylor, A.; Leblanc, S.P.; Japkowicz, N. Anomaly Detection in Automobile Control Network Data with Long Short-Term Memory Networks. In Proceedings of the 2016 IEEE International Conference on Data Science and Advanced Analytics (DSAA), Montreal, QC, Canada, 17–19 October 2016; pp. 130–139. [Google Scholar]
- Di Natale, M.; Zeng, H.; Giusto, P.; Ghosal, A. Understanding and Using the Controller Area Network Communication Protocol: Theory and Practice; Springer-Verlag: New York, NY, USA, 2012. [Google Scholar]
- Avatefipour, O.; Malik, H. State-of-the-art survey on in-vehicle network communication (CAN-Bus) security and vulnerabilities. arXiv 2018, arXiv:1802.01725. [Google Scholar]
- Liu, J.; Zhang, S.; Sun, W.; Shi, Y. In-Vehicle Network Attacks and Countermeasures: Challenges and Future Directions. IEEE Netw. 2017, 31, 50–58. [Google Scholar] [CrossRef]
- Ying, X.; Bernieri, G.; Conti, M.; Poovendran, R. TACAN: Transmitter authentication through covert channels in controller area networks. In Proceedings of the 10th ACM/IEEE International Conference on Cyber-Physical Systems, Montreal, QC, Canada, 16–18 April 2019; pp. 23–34. [Google Scholar]
- Hazem, A.; Fahmy, H.A. Lcap-a lightweight can authentication protocol for securing in-vehicle networks. In Proceedings of the 10th escar Embedded Security in Cars Conference, Berlin, Germany, 28–29 November 2012; p. 6. [Google Scholar]
- Noureldeen, P.; Azer, M.A.; Refaat, A.; Alam, M. Replay attack on lightweight CAN authentication protocol. In Proceedings of the 2017 12th International Conference on Computer Engineering and Systems (ICCES), Cairo, Egypt, 19–20 December 2017; pp. 600–606. [Google Scholar]
- Lin, C.-W.; Sangiovanni-Vincentelli, A. Cyber-Security for the Controller Area Network (CAN) Communication Protocol. In Proceedings of the 2012 International Conference on Cyber Security, Washington, DC, USA, 14–16 December 2012; pp. 1–7. [Google Scholar]
- Takahashi, J.; Tanaka, M.; Fuji, H.; Narita, T.; Matsumoto, S.; Sato, H. Automotive Security on Abnormal Vehicle Behavior Using Only Fabricated Informative CAN Messages. J. Inf. Process. 2019, 27, 159–167. [Google Scholar] [CrossRef]




| Attack Vectors | No Encryption | No Authentication | No Integrity Checking | Broadcast Transmission | Priority-based Arbitration | Limited Bandwidth and Payload |
|---|---|---|---|---|---|---|
| Eavesdropping Attack | ● | ● | ● | |||
| Replay Attack | ● | ● | ● | |||
| Impersonation Attack | ● | ● | ● | ● | ||
| Injection Attack | ● | ● | ● | ● | ● | ● |
| Evaluation Vectors | Eavesdropping Attack | Replay Attack | Impersonation Attack | Injection Attack |
| CAN Architecture Scan | ● | |||
| ECU Drop-Off | ● | ● | ● | |
| Normal packets Reverse: Based on frame frequency | ● | ● | ||
| Normal packets Reverse: Based on data bit feature | ● | ● | ||
| Normal packets Replay | ● | ● | ||
| Normal packets fuzzing | ● | ● | ||
| Diagnostic Service Scan | ● | ● | ||
| Diagnostic packets Reverse | ● | ● | ||
| ECU Access | ● | ● | ||
| Diagnostic packets Replay | ● | ● | ||
| Diagnostic packets fuzzing | ● | ● | ● |
| Tool | Tracing Traffic | Reverse Traffic | Packets Generation | Configuration | Logging | Monitor | System |
|---|---|---|---|---|---|---|---|
| ATG [9] | ✓ | ✓ | ✓ | ✓ | ✓ | Linux, Win | |
| CarShark [7] | ✓ | ✓ | Win | ||||
| CANUtils | ✓ | ✓ | ✓ | Linux | |||
| BusMaster | ✓ | ✓ | ✓ | Win | |||
| CANoe | ✓ | ✓ | ✓ | ✓ | Win | ||
| SavvyCAN | ✓ | ✓ | ✓ | ✓ | Linux, Win | ||
| OCTAN | ✓ | ✓ | ✓ | ✓ | Win | ||
| Tool [10] | ✓ | ✓ | ✓ | ✓ | ✓ | Win | |
| CANsec | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | Linux, Win |
| CAN ID | Data Field | Functionality |
|---|---|---|
| 0x231 | Byte0 = 0xe1, Byte1 = 0x69 | Turn on the back gear |
| 0x235 | Byte0 = 0x00 | Open or close the door |
| 0x265 | Byte0 = 0x20 | Turn on the left turn signal |
| 0x265 | Byte0 = 0x40 | Turn on the right turn signal |
| 0x285 | 0xff 0xff 0xff 0xff 0xff 0xff 0xff 0xff | Air-conditioning heating mode |
| 0x240 | Byte4 = 0x9a | Clutch down |
| 0x60d | Byte1 = 0x01 | Open the fog lamp |
| 0x60d | Byte1 = 0x08 | Turn on high beam |
| 0x358 | Byte0 = 0x40 | Car horns |
| 0x201 | Byte0, Byte1 | The vehicle speed |
| 0x201 | Byte4, Byte5 | The engine speed |
| Diagnostic Request ID | Diagnostic Response ID | The Primary Service ID |
|---|---|---|
| 0x726 | 0x72e | 0x10 0x11 0x14 0x18 0x21 0x22 0x28 0x2f 0x310x32 0x33 0x3b 0x3e 0x3f 0x85 0xb1 |
| 0x737 | 0x73f | 0x14 0x18 0x28 0x31 0x32 0x33 0x3b 0x3e 0x3f 0x85 0xb1 |
| 0x740 | 0x748 | 0x10 0x14 0x18 0x21 0x22 0x27 0x28 0x2f 0x31 0x32 0x33 0x34 0x35 0x36 0x37 0x3b 0x3e 0x3f 0x85 0xb1 |
| 0x741 | 0x749 | 0x10 0x14 0x18 0x21 0x22 0x27 0x28 0x2f 0x31 0x32 0x33 0x34 0x35 0x36 0x37 0x3b 0x3e 0x3f 0x85 0xb1 |
| 0x742 | 0x74a | 0x10 0x14 0x18 0x21 0x22 0x27 0x28 0x2f 0x31 0x32 0x33 0x34 0x35 0x36 0x37 0x3b 0x3e 0x3f 0x85 0xb1 |
| 0x743 | 0x74b | 0x10 0x14 0x18 0x21 0x22 0x27 0x28 0x2f 0x31 0x32 0x33 0x34 0x35 0x36 0x37 0x3b 0x3e 0x3f 0x85 0xb1 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, H.; Meng, X.; Zhang, X.; Liu, Z. CANsec: A Practical in-Vehicle Controller Area Network Security Evaluation Tool. Sensors 2020, 20, 4900. https://doi.org/10.3390/s20174900
Zhang H, Meng X, Zhang X, Liu Z. CANsec: A Practical in-Vehicle Controller Area Network Security Evaluation Tool. Sensors. 2020; 20(17):4900. https://doi.org/10.3390/s20174900
Chicago/Turabian StyleZhang, Haichun, Xu Meng, Xiong Zhang, and Zhenglin Liu. 2020. "CANsec: A Practical in-Vehicle Controller Area Network Security Evaluation Tool" Sensors 20, no. 17: 4900. https://doi.org/10.3390/s20174900
APA StyleZhang, H., Meng, X., Zhang, X., & Liu, Z. (2020). CANsec: A Practical in-Vehicle Controller Area Network Security Evaluation Tool. Sensors, 20(17), 4900. https://doi.org/10.3390/s20174900





