A WSN Layer-Cluster Key Management Scheme Based on Quadratic Polynomial and Lagrange Interpolation Polynomial
Abstract
1. Introduction
1.1. Identity Authentication
1.2. Session Key
- (1)
- The key pre-distribution schemes based on keys pool, such as the key management scheme for distributed sensor networks proposed by Eschenauer-G1igor [21], q-composite random key pre-distribution scheme [22], pair-wise keys in distributed sensor networks [23], etc. In these schemes, each node selects several keys from the key pool randomly and only communicates with the nodes with one or more same keys. Simple application, small computing load and supporting the dynamic changes of the network are the advantages of this type. However, because the key sharing rate between nodes is low and these schemes do not support identity authentication, attackers can easily carry out various malicious attacks by using the obtained key information.
- (2)
- The key pre-distribution schemes based on polynomial keys pool, such as the key pre-distribution in wireless sensor networks using multivariate polynomials [24], the key pre-distribution scheme based on matrix [25,26] and the key pre-distribution scheme based on configuration knowledge [27,28], etc. These schemes are generally able to resist capture attacks and have high security and good network connectivity, but they have large calculation cost and do not support identity authentication of neighbor nodes, and the network scalability is not strong to be good for the new nodes joining.
- (3)
- Other pre-distribution key schemes, such as the grid-based key pre-distribution scheme [29], the key management scheme based on logical key tree, etc. Although these schemes have high network connectivity and small storage cost, they have poor network applicability and security.
1.3. Group Key
1.4. Network Key
1.5. Personal Key
1.6. Layer-Cluster Key
1.7. Motivations
- Since almost all existed encryption technologies rely on keys, and the leakage of the keys will directly lead to the leakage of the plaintexts, so key management is the key part of guaranteeing wireless communication security and how to configure and manage keys effectively and safely has become one of the important parts of WSN security research.
- Key management is one of the most critical issues for security, and it is the basis of other security mechanisms such as secure routing, secure location, secure data fusion, etc. Therefore, it is very important to attach great importance to the key management and introduce appropriate key management schemes for effective control.
- The current key management schemes are mainly designed for static and planar networks and easy to be trapped in the problem of single point failure, which is not very suitable for the layer-cluster wireless sensor network (WSN).
1.8. Main Contributions
- Broadcast authentication. The broadcast authentication protocol based on Fourier series for WSN is used for identity authentication. The authentication key is established by the initial sharing function to realize the broadcast authentication of the group members, and each member can confirm the source and integrity of the broadcast information from BS or cluster heads.
- Session key. Session key information is encrypted by the former authentication key to ensure the security of intermediate interactive information. Using the initial private function , a multiple asymmetric quadratic polynomial, to establish a session key management scheme, which can guarantee the independence of session key and network connectivity.
- Group key. In order to realize the secure broadcast of the sharing information among the group members in a cluster, the group key should be established at the basis of the former session key, in which cluster is the most natural communication group. Since the generation of group keys needs the joint participation of all group nodes or the associated nodes, there is a single point failure problem. According to the former two kinds of key, a group key scheme based on Lagrange interpolation polynomial is established, in which the nodes of the cluster are not directly involved.
- Network key. Network key is the communication key shared by BS and other network nodes and the generation and management scheme of network key is similar with the group key, in which the establishment idea of network key is to regard the BS and all cluster heads as a group, so network keys based on Lagrange interpolation polynomial can also be established.
- Personal key. The key of personal key establishment is to keep the privacy and independence of the key. The generation and management scheme of personal keys is also similar to the situation of group keys, the difference being that personal keys can be obtained by cluster nodes through getting the Lagrange interpolation polynomial coefficients based on their own random key information, in which the coefficients can only be obtained by corresponding nodes. The independent coefficient is defined as the personal key which only can be known by BS and the corresponding node.
- Reverse authentication. Based on the personal key to achieve one-to-one private communication, BS can verify the identity of each node, which is called the reverse authentication.
1.9. Organization
2. Related Work
2.1. Characteristics of the Fourier Series
2.2. Characteristic of Quadratic Polynomial
- Step 1:
- In fields , choosing a multivariate and asymmetric quadratic polynomial randomly and writing out the matrix A.
- Step 2:
- Calculating the all roots of the characteristic equation in fields which are also called eigenvalues.
- Step 3:
- Taking the obtained eigenvalues into Equation (10) one by one, and then working out a group of basic solutions for each eigenvalue which are called the linearly independent eigenvectors of each eigenvalue. Therefore, based on this method, all linearly independent eigenvectors belonged to each eigenvalue can be obtained.
- Step 1:
- In fields , selecting a quadratic polynomial randomly and building matrix A, calculating all eigenvalues and eigenvectors of the characteristic equation in fields .
- Step 2:
- Using the method of Gram-Schmidt Orthogonalization to orthogonalize the eigenvectors and get the unit orthogonal matrix , where and .
- Step 3:
- Based on orthogonal linear substitution , matrix A can be converted into the diagonal matrix C, where the diagonal values of C are the eigenvalues of the matrix A. At the same time, realizing the linear standardization from .
2.3. Lagrange Interpolation Polynomial
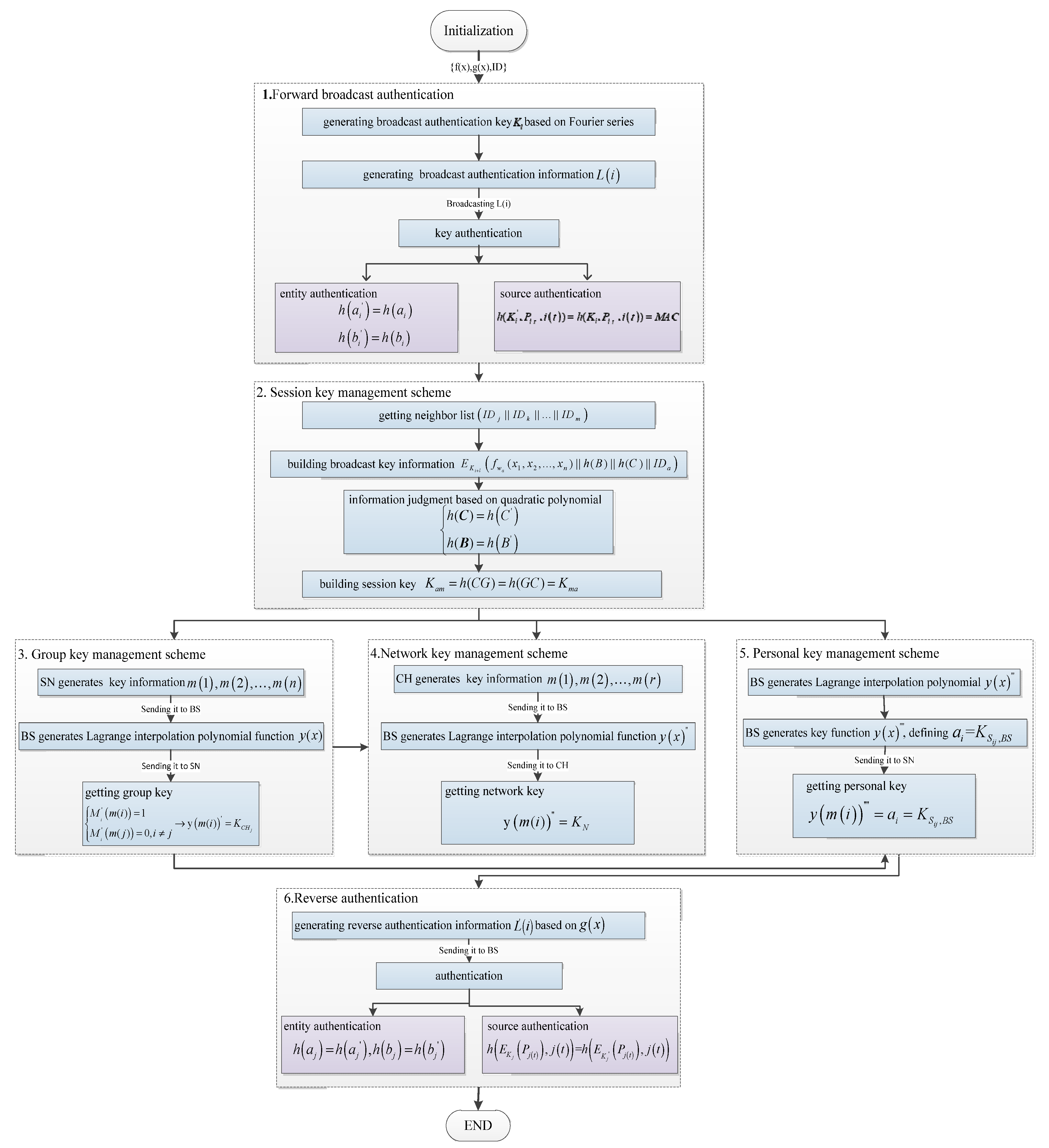
3. LCKMS-QPLIP
3.1. Network Model
- (1)
- It is assumed that the network is homogeneous and static, and each group member is identical in the configuration of hardware and software, where the network size is and there are three types of nodes: base station, cluster head and common sensor node. The layer-cluster network structure of WSN shown in the Figure 1.
- (2)
- It is assumed that BS is equipped with sufficient hardware and software resources and has stored the basic information of all nodes in the network. In addition, BS can detect the broken or captured nodes.
- (3)
- The cluster head is responsible for collecting the data from its members and sending it to BS layer by layer. The clustering protocol LEACH [41] in WSN is chosen to initialize the network topology and select the cluster heads in this paper.
- (4)
- The common sensor nodes are responsible for collecting the surrounding environment data and sending the data to their neighbor nodes or cluster head. Common sensor nodes have not enough storage space and energy to process data. Since the communication radius of common sensor nodes is limited, the communication between nodes that are not within the communication radius needs to rely on the transit of their common neighbor nodes.
3.2. Building Layer-Cluster Key
3.2.1. Forward Broadcast Authentication Key Management
- (1)
- The generation of inner-cluster broadcast authentication key based on a Fourier series
- (2)
- Judging the timeliness of a package
- (3)
- Key authentication
3.2.2. Session Key Management Scheme Based on a Quadratic Polynomial
- (1)
- Initialization
- (2)
- Building session key
- Getting neighbor list
- Building broadcast key information
- Information judgement
- Building session key
3.2.3. Group Key Management Scheme Based on Lagrange Interpolation Polynomial
- (1)
- Sending the key information
- (2)
- Generating Lagrange interpolation polynomial function
- (3)
- Getting the group key
3.2.4. Network Key Management Scheme
- (1)
- Each cluster head generates its own key information randomly named as , and these cluster heads will send the key information encrypted by session keys to BS layer by layer.
- (2)
- BS generates a Lagrange interpolation polynomial function after getting the key information :
- (3)
- Conversely, BS sends encrypted by session key to each cluster head layer by layer, and all cluster heads can obtain the network key independently based on their own key information .
3.2.5. Personal Key Management Scheme
- (1)
- Generating Lagrange interpolation polynomial
- (2)
- Generating key function
- (3)
- Obtaining personal key
4. Key Updating
4.1. Updating
- (1)
- BS generates the updating information .
- (2)
- After verifying, re-encrypts the updating information named by group key .
4.2. Updating
- (1)
- Assume that BS generates the updating information , and is the private function for updating:
- (2)
- decrypts by and judges that is the private information for itself by verifying and . After that, continues to decrypt by the personal key and verifies the integrity of and the timeliness of by hash function.
4.3. Session Key Updating
- (1)
- Node resolves the new private quadratic function and gets the quadratic matrix . In addition, based on Theorem 3, solving the new unit orthogonal matrix , diagonal matrix and eigenvector matrix , where the diagonal values are arranged in the order of eigenvalues from small to large.
- (2)
- Broadcasting key information encrypted by group key to all neighbor nodes:
- (3)
- Information judgement. node resolves the key information by and gets . Based on Theorem 3, solving the unit orthogonal matrix and diagonal matrix . If:
- (4)
- Building the new session key. Node also broadcasts its key information encrypted by group key to all neighbor nodes.
4.4. Group Key Updating
- (1)
- Assume that is the new key information generated by node of cluster , and then encrypts with its own personal key and the session key and sends it to cluster head , and the encrypted information is written as .
- (2)
- decrypts with and finds that it is a private information sent to BS. For facilitating and saving computing resources, will wait for the all key information of the cluster members and send it to BS together (supposing is adjacent to BS here), and the encrypted information is written as: .
- (3)
- BS receives and decrypts the information from by the session key and the personal keys of the members of cluster .
- (4)
- Generating the new group key based on the group key scheme and the steps are as follows:
- Step 1:
- BS generates a new Lagrange interpolation polynomial , where is the new group key;
- Step 2:
- BS encrypts , it is written as and sends it to ;
- Step 3:
- decrypts and re-encrypts it with old group key, it is written as ;
- Step 4:
- every cluster member receives the broadcast information from and gets by ;
- Step 5:
- every cluster member obtains the new group key by putting into ;
- Step 6:
- all members delete the old group key and enable the new group key .
- (1)
- is encrypted by personal key and the intermediate transfer nodes or cluster nodes cannot obtain .
- (2)
- is encrypted by old group key when it is broadcasted by cluster head, where the advantage is that the cluster members can receive the broadcast information once time and save the computing resources heavily.
4.5. Network Key Updating
- (1)
- Assume that the key information are generated respectively by cluster heads and the transmitted information is encrypted by session key. In addition, for easy to discuss, it is supposed that is adjacent to BS and encrypted information is written as .
- (2)
- BS receives and decrypts the information from all cluster heads and generates a new Lagrange interpolation polynomial function :where, is the new updating network key.
- (3)
- BS sends to each cluster heads. The difference compared with former building scheme of network key is that is not encrypted by session key and not transmitted layer by layer, it is encrypted as by the old network key and only broadcasted once time.
- (4)
- Each cluster head obtains by after receiving and then obtains the new network key by putting into , where the old network key will be deleted when enabling .
4.6. Personal Key Updating
- (1)
- According to the group key updating scheme, BS has obtained the random key information of cluster and cannot decrypt these information. So, BS generates a new Lagrange interpolation polynomial same as the former personal scheme procedure:where , is the new updating personal key.
- (2)
- BS sends the encrypted information to (supposing is adjacent to BS), where is the session key. And then, decrypts and gets , where cannot get any useful information from because of the lack of .
- (3)
- sends the encrypted information to each cluster member of cluster , where is the new updating group key.
- (4)
- Obtaining new personal key. receives and obtains by . If assuming and putting into , then and the old personal key will be deleted when enabling .
5. Security Analysis
5.1. Network Connectivity Analysis
- (1)
- Address query. node encrypts the information and sends it to the cluster head , where is the session key between and .
- (2)
- decrypts the information and get the communication request between node and node . If it is queried from the neighbor list by that node is the common neighbor node of and , will send and to and respectively which means that is their intermediate communication node. Meanwhile, sending to which means that and need its help to finish the non-adjacent communication. The advantage of the above two steps is that they can reduce the probability of a cluster head acting as the intermediate node. Actually, according to the traditional scheme, if the neighbor list of doesn’t contain , has to act as the intermediate node which will increase the communication cost of . It is known that the cluster size is the one hop range of the cluster head according to de definition of layer-cluster network and the communication distance of each pair nodes in the cluster usually does not exceed 2 hops. Therefore, it is better to query and select the communication route of non-adjacent nodes by cluster head.
- (3)
- Building the non-adjacent session key . Node sends the encrypted information to node , where is the key information of node . Node sends the encrypted information to node . Node decrypts and obtains and also sends to node , where is the key information of node . Node also sends the encrypted information to node . Node decrypts and obtains . After sending the key information, node and node can build the non-adjacent session key based on the former session key scheme, and then node deletes and .
- (4)
- Non-adjacent communication. Based on the non-adjacent session key , node sends the encrypted information to node , where is the plaintext. Node decrypts the information and gets that it is the information sent to , and then re-encrypts the information and sends it to .
- The cluster head query and select the communication route of non-adjacent nodes which can reduce the communication cost.
- The intermediate node is only responsible for forwarding the encrypted information and cannot get the plaintext, which can ensure the security of the forwarding process.
- The routing cooperation by cluster head nodes can ensure the 100% connectivity between nodes of the cluster, which is the most prominent advantage and feature of the scheme.
5.2. Security Analysis of Network Topology Change
5.2.1. New Node Joining
5.2.2. Node Quitting
- Energy Exhaustion Quitting
- Abnormal Node Quitting
5.3. Anti-Capture Analysis
5.3.1. Anti-Capture Analysis of Session Key
5.3.2. Anti-Capture Analysis of Broadcast Authentication Key
5.3.3. Anti-Capture Analysis of Group Key, Network Key and Personal Key
5.4. Efficiency Analysis
- (1)
- Authentication delay cost in [42]
- (2)
- Storage cost in [44]
- (3)
- Computation cost in [44]
5.5. Network Robustness Analysis
- (1)
- Anti-collusion attack capability
- (2)
- Anti-flooding attack capability
- (3)
- Authentication analysis
- (4)
- Scalability analysis
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Chaudhary, R.; Aujla, G.S.; Kumar, N.; Zeadally, S. Lattice-based public key cryptosystem for internet of things environment: Challenges and solutions. IEEE Internet Things J. 2019, 6, 4897–4909. [Google Scholar] [CrossRef]
- Granjal, J.; Monteiro, E.; Silva, J.S. Security for the internet of things: A survey of existing protocols and open research issues. IEEE Commun. Surv. Tutor. 2015, 17, 1294–1312. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, X.X.; Zhai, Z.G.; Chen, R.; Zhang, B.; Jiang, Y. Timely daily activity recognition from headmost sensor events. ISA Trans. 2019, 94, 379–390. [Google Scholar] [CrossRef] [PubMed]
- Tomic, I.; McCann, J.A. A survey of potential security issues in existing wireless sensor network protocols. IEEE Internet Things J. 2017, 4, 1910–1923. [Google Scholar] [CrossRef]
- Perrig, A.; Szewczyk, R.; Tygar, J.D.; Tygar, J.D.; Wen, V.; Culler, D.E. SPINS: Security protocols for sensor networks. Wirel. Netw. 2002, 8, 521–534. [Google Scholar] [CrossRef]
- Moosavi, H.; Bui, F.M. A game-theoretic framework for robust optimal intrusion detection in wireless sensor networks. IEEE Trans. Inf. Forensic Secur. 2014, 9, 1367–1379. [Google Scholar] [CrossRef]
- Zhou, Y.; Fang, Y.G.; Zhang, Y.C. Securing wireless sensor networks: A survey. IEEE Commun. Surv. Tutor. 2008, 10, 6–28. [Google Scholar] [CrossRef]
- Zhu, S.; Setia, S.; Jadojia, S. LEAP: Efficient security mechanisms for large-scale distributed sensor networks. ACM Trans. Sens. Netw. 2004, 2, 500–528. [Google Scholar] [CrossRef]
- Lee, J.C.; Leung, V.C.; Wong, K.H.; Cao, J.N.; Chan, H.C. Key management issues in wireless sensor networks: Current proposals and future developments. IEEE Wirel. Commun. 2007, 14, 76–84. [Google Scholar] [CrossRef]
- Yousefpoor, M.S.; Barati, H. Dynamic key management algorithms in wireless sensor networks: A survey. Comput. Commun. 2018, 134, 52–69. [Google Scholar] [CrossRef]
- Simplicio, M.A., Jr.; Barreto, P.S.; Margi, C.B.; Carvalho, T.C. A survey on key management mechanisms for distributed wireless sensor networks. Comput. Netw. 2010, 54, 2591–2612. [Google Scholar] [CrossRef]
- Zhang, J.Q.; Varadharajan, V. Wireless sensor network key management survey and taxonomy. J. Netw. Comput. Appl. 2010, 33, 63–75. [Google Scholar] [CrossRef]
- Anil Kumar, S.; Ashok Kumar, D.; Neeraj, K.; Alavalapati Goutham, R.; Vasilakos, A.V.; Rodrigues, J.J. On the design of secure user authenticated key management scheme for multigateway-based wireless sensor networks using ECC. Int. J. Commun. Syst. 2018, 31, e3514. [Google Scholar]
- Choi, Y.; Lee, D.; Kim, J.; Jung, J.; Nam, J.; Won, D. Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2014, 14, 10081–10106. [Google Scholar] [CrossRef] [PubMed]
- Shen, L.M.; Ma, J.F.; Liu, X.M.; Wei, F.S.; Miao, M. A secure and efficient ID-based aggregate signature scheme for wireless sensor networks. IEEE Internet Things J. 2017, 4, 546–554. [Google Scholar] [CrossRef]
- Mohammad, W.; Ashok Kumar, D.; Vivekananda, B.K.; Vasilakos, A.V. LAM-CIoT: Lightweight authentication mechanism in cloud-based IoT environment. J. Netw. Comput. Appl. 2020, 150, 102496. [Google Scholar]
- Sravani, C.; Ashok Kumar, D.; Prosanta, G.; Neeraj, K.; Wu, F.; Vasilakos, A.V. Design and analysis of authenticated key agreement scheme in cloud-assisted cyber-physical systems. Future Gener. Comput. Syst. 2020, 108, 1267–1286. [Google Scholar]
- Thevar, G.K.C.; Rohini, G. Energy efficient geographical key management scheme for authentication in mobile wireless sensor networks. Wirel. Netw. 2017, 23, 1479–1489. [Google Scholar] [CrossRef]
- Ghani, A.; Mansoor, K.; Mehmood, S.; Chaudhry, S.A.; Rahman, A.U.; Saqib, M.N. Security and key management in IoT-based wireless sensor networks: An authentication protocol using symmetric key. Int. J. Commun. Syst. 2019, 32, e4139. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.K.H.; Biswas, G.P.; Khan, M.K.; Leng, L.; Kumar, N. Design of an anonymity-preserving three-factor authenticated key exchange protocol for wireless sensor networks. Comput. Netw. 2016, 101, 42–62. [Google Scholar] [CrossRef]
- Eschenauer, L.; Gligor, V.D. A key management scheme for distributed sensor networks. In Proceedings of the 9th ACM Conference on Computer and Communications Security, Washington, DC, USA, 18–22 November 2002; pp. 41–47. [Google Scholar]
- Chan, H.W.; Perrig, A.; Song, D. Random key predistribution schemes for sensor networks. In Proceedings of the 2003 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 11–14 May 2003; pp. 197–213. [Google Scholar]
- Liu, D.G.; Ning, P.; Li, R.F. Establishing pairwise keys in distributed sensor networks. ACM Trans. Inf. Syst. Secur. 2005, 8, 41–77. [Google Scholar] [CrossRef]
- Delgosha, F.; Fekri, F. Key pre-distribution in wireless sensor networks using multivariate polynomials. In Proceedings of the 2nd Annual IEEE Communications Society Conference on Sensor and Ad Hoc Communications and Networks, Santa Clara, CA, USA, 26–29 September 2005; pp. 118–129. [Google Scholar]
- Yuan, T.; Zhang, S.Y.; Zhong, Y.P. A matrix-based random key pre-distribution scheme for wireless sensor networks. In Proceedings of the 7th IEEE International Conference on Computer and Information Technology, Aizu-Wakamatsu City, Japan, 16–19 October 2007; pp. 991–996. [Google Scholar]
- Liu, J.C.; Huang, Y.L.; Leu, F.Y.; Chiang, F.C.; Yang, C.T.; Chu, W.C.C. Square key matrix management scheme in wireless sensor neteorks. Comput. Inform. 2017, 36, 169–185. [Google Scholar] [CrossRef]
- Ben Amira, M.; Bouraoui, M.; Boulajfen, N. Performance evaluation of polynomial pool-based key pre-distribution protocol for wireless sensor network applications. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 147–152. [Google Scholar]
- Premamayudu, B.; Rao, K.V.; Varma, P.S. Dynamic session key based pairwise key management scheme for wireless sensor networks. KSII Trans. Internet Inf. Syst. 2016, 10, 5596–5615. [Google Scholar]
- Mohaisen, A.; Nyang, D.; Maeng, Y.; Lee, K.; Hong, D. Grid-based key pre-distribution in wireless sensor networks. KSII Trans. Internet Inf. Syst. 2009, 3, 195–208. [Google Scholar] [CrossRef][Green Version]
- Lo, C.C.; Huang, C.C.; Chen, S.W. An efficient and scalable EBS-based batch rekeying scheme for secure group communications. In Proceedings of the IEEE Military Communications Conference (MILCOM 2009), Boston, MA, USA, 18–21 October 2009; pp. 1343–1349. [Google Scholar]
- Chen, Y.L.; Yang, G. Efficient and secure group key management based on EBS and attribute encryption. In Proceedings of the 2011 IEEE International Conference on Computer Science and Automation Engineering (CSAE), Shanghai, China, 10–12 June 2011; pp. 661–665. [Google Scholar]
- Liu, Z.H.; Lai, Y.X.; Ren, X.B.; Bu, S.P. An efficient LKH tree balancing algorithm for group key management. In Proceedings of the 2012 International Conference on Control Engineering and Communication Technology (ICCECT), Shenyang, China, 7–9 December 2012; pp. 1003–1005. [Google Scholar]
- Xu, J.; Li, L.K.; Lu, S.B.; Yin, H.Y. A novel batch-based LKH tree balanced algorithm for group key management. Sci. China-Inf. Sci. 2017, 60, 108301. [Google Scholar] [CrossRef]
- Albakri, A.; Harn, L. Non-interactive group key pre-distribution scheme (GKPS) for end-to-end routing in wireless sensor networks. IEEE Access 2019, 7, 31615–31623. [Google Scholar] [CrossRef]
- Son, J.H.; Lee, J.S.; Seo, S.W. Topological key hierarchy for energy-efficient group key management in wireless sensor networks. Wirel. Pers. Commun. 2010, 52, 359–382. [Google Scholar] [CrossRef]
- Albakri, A.; Harn, L.; Song, S. Hierarchical key management scheme with probabilistic security in a wireless sensor network (WSN). Secur. Commun. Netw. 2019, 4, 1–11. [Google Scholar]
- Sun, B.W.; Li, Q.; Tian, B. Local dynamic key management scheme based on layer-cluster topology in WSN. Wirel. Pers. Commun. 2018, 103, 699–714. [Google Scholar] [CrossRef]
- Gandino, F.; Ferrero, R.; Montrucchio, B.; Rebaudengo, M. Fast hierarchical key management scheme with transitory master key for wireless sensor networks. IEEE Internet Things J. 2016, 3, 1334–1345. [Google Scholar] [CrossRef]
- Tsitsipis, D.; Tzes, A.; Koubias, S. CHAT: Clustered hierarchical key management for wireless sensor networks using network topology. Int. J. Distrib. Sens. Netw. 2017, 13, 1550147717741570. [Google Scholar] [CrossRef][Green Version]
- Jia, X.X.; Song, Y.X.; Wang, D.S.; Nie, D.X.; Wu, J.Z. A collaborative secret sharing scheme based on the Chinese Remainder Theorem. Math. Biosci. Eng. 2019, 16, 1280–1299. [Google Scholar] [CrossRef]
- Ahmed, S.; Walid, O.; Ahmed, M.K. IBLEACH: Intra-balanced LEACH protocol for wireless sensor networks. Wirel. Netw. 2014, 20, 1515–1525. [Google Scholar]
- Wang, X.G.; Shi, W.R. A mutual broadcast authentication protocol for wireless sensor networks based on Fourier series. Int. J. Distrib. Sens. Netw. 2015, 11, 397130. [Google Scholar] [CrossRef]
- Wang, X.G.; Shi, W.R. Secure time synchronization protocol for wireless sensor network based on µTESLA protocol. In. J. Netw. Secur. 2018, 20, 536–546. [Google Scholar]
- Wang, X.G.; Shi, W.R.; Liu, D. A group key management scheme for WSN based on Lagrange interpolation polynomial characteristic. KSII Trans. Internet Inf. Syst. 2019, 13, 3690–3713. [Google Scholar]



| Symbols | Explanation |
|---|---|
| base station/key distribution center | |
| node of cluster | |
| cluster head | |
| hash function | |
| key information of node | |
| identity symbol of node | |
| sharing function | |
| private function | |
| session key between node and node | |
| session key between cluster and BS | |
| session key between node and cluster head | |
| group key of cluster | |
| personal key of node | |
| network key | |
| broadcast authentication information |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, X.; Yang, Z.; Feng, Z.; Zhao, J. A WSN Layer-Cluster Key Management Scheme Based on Quadratic Polynomial and Lagrange Interpolation Polynomial. Sensors 2020, 20, 4388. https://doi.org/10.3390/s20164388
Wang X, Yang Z, Feng Z, Zhao J. A WSN Layer-Cluster Key Management Scheme Based on Quadratic Polynomial and Lagrange Interpolation Polynomial. Sensors. 2020; 20(16):4388. https://doi.org/10.3390/s20164388
Chicago/Turabian StyleWang, Xiaogang, Zhongfan Yang, Zhiqiang Feng, and Jun Zhao. 2020. "A WSN Layer-Cluster Key Management Scheme Based on Quadratic Polynomial and Lagrange Interpolation Polynomial" Sensors 20, no. 16: 4388. https://doi.org/10.3390/s20164388
APA StyleWang, X., Yang, Z., Feng, Z., & Zhao, J. (2020). A WSN Layer-Cluster Key Management Scheme Based on Quadratic Polynomial and Lagrange Interpolation Polynomial. Sensors, 20(16), 4388. https://doi.org/10.3390/s20164388




