Machine Learning-Based IoT-Botnet Attack Detection with Sequential Architecture †
Abstract
1. Introduction
1.1. Background and Motivation
1.2. Challenging Issues
1.3. Our Contributions
- (1)
- A botnet attacks detection framework with sequential architecture based on machine learning (ML) algorithms is proposed for dealing with attacks in IoT environments.
- (2)
- A correlated-feature selection approach is adopted for reducing the irrelevant features, which makes the system lightweight.
- (3)
- In our proposal, classifiers based on different ML algorithms may be applied in different attack detection sub-engines, which leads to better detection performance and shorter processing times and a lightweight implementation.
1.4. Organization of the Paper
2. Related Works
3. Background Methodologies
3.1. Artificial Neural Network (ANN)
3.2. J48 Algorithm
3.3. Naïve Bayes
3.4. Correlation-Based Feature Selection
4. Our Proposal: Sequential Attack Detection Architecture
5. Experimental Results
5.1. Dataset
- Scan: Scanning the network for vulnerable devices.
- Junk: Sending spam data.
- Udp: UDP flooding.
- Tcp: TCP flooding.
- Combo: Sending spam data and opening a connection to a specified IP address and port.
- Ack: Ack flooding.
- Syn: Syn flooding.
- Udp plain: UDP flooding with fewer options, optimized for higher Packets Per Seconds (PPS).
5.2. The Performance with ANN
5.3. Comparison with Different Learning Algorithms
5.4. Performance of the Proposed Detection Architecture
5.5. Observations
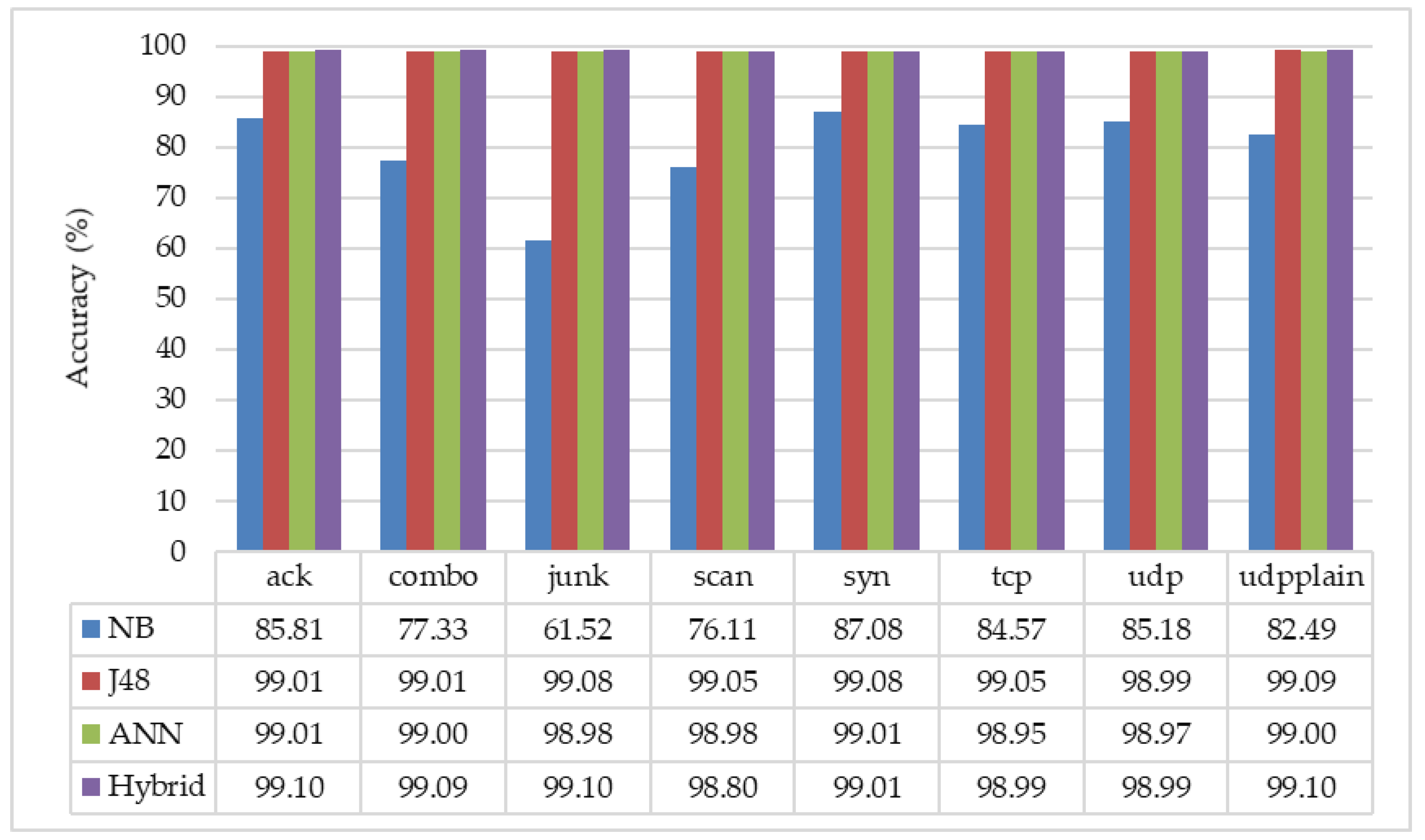
- The proposed architecture, sequential detection scheme with “hybrid” classification, is useful to detect the IoT botnets attacks. In Figure 6, the average detection accuracy of “hybrid” classification is around 99% in each of the sub-engines.
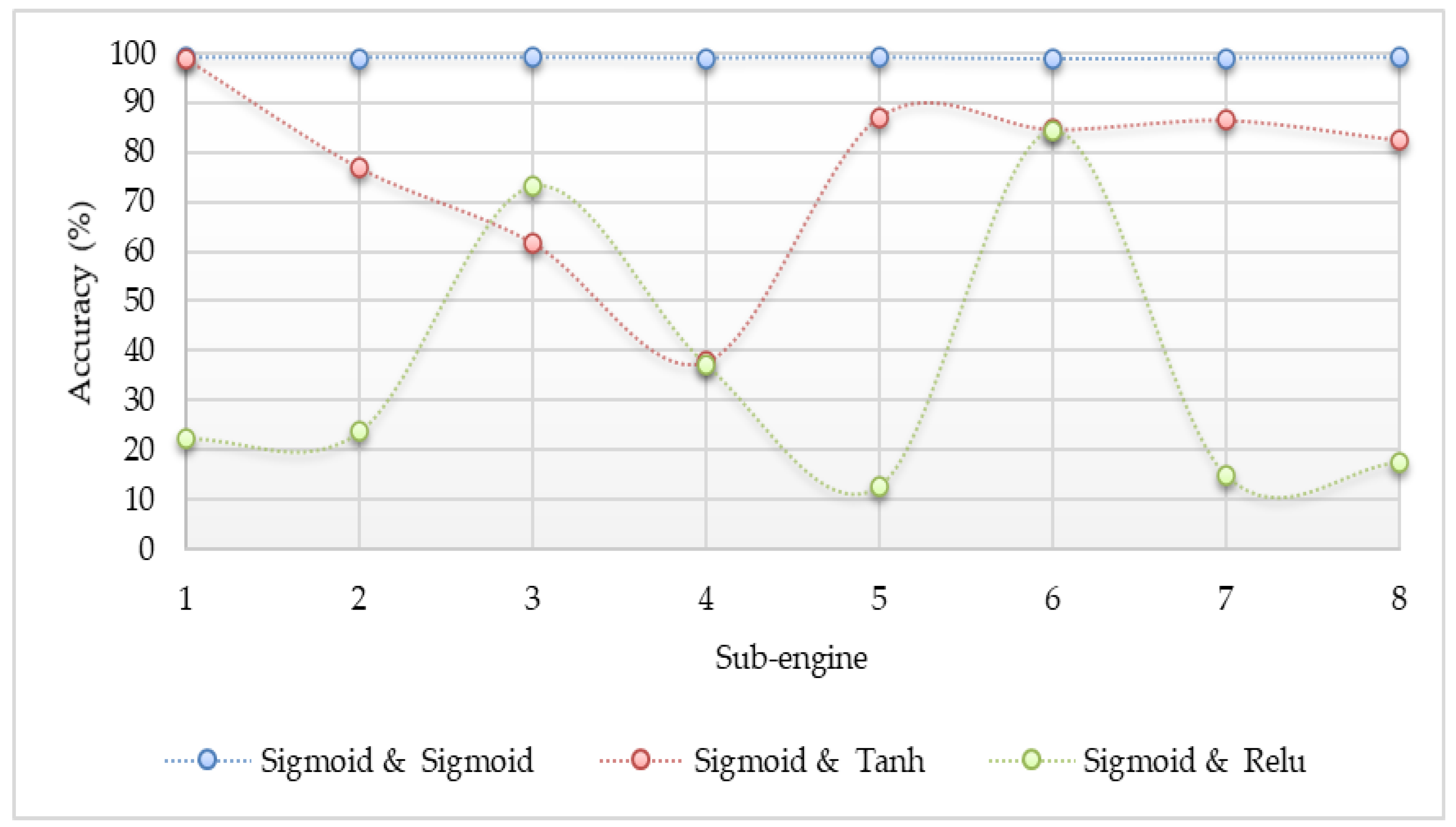
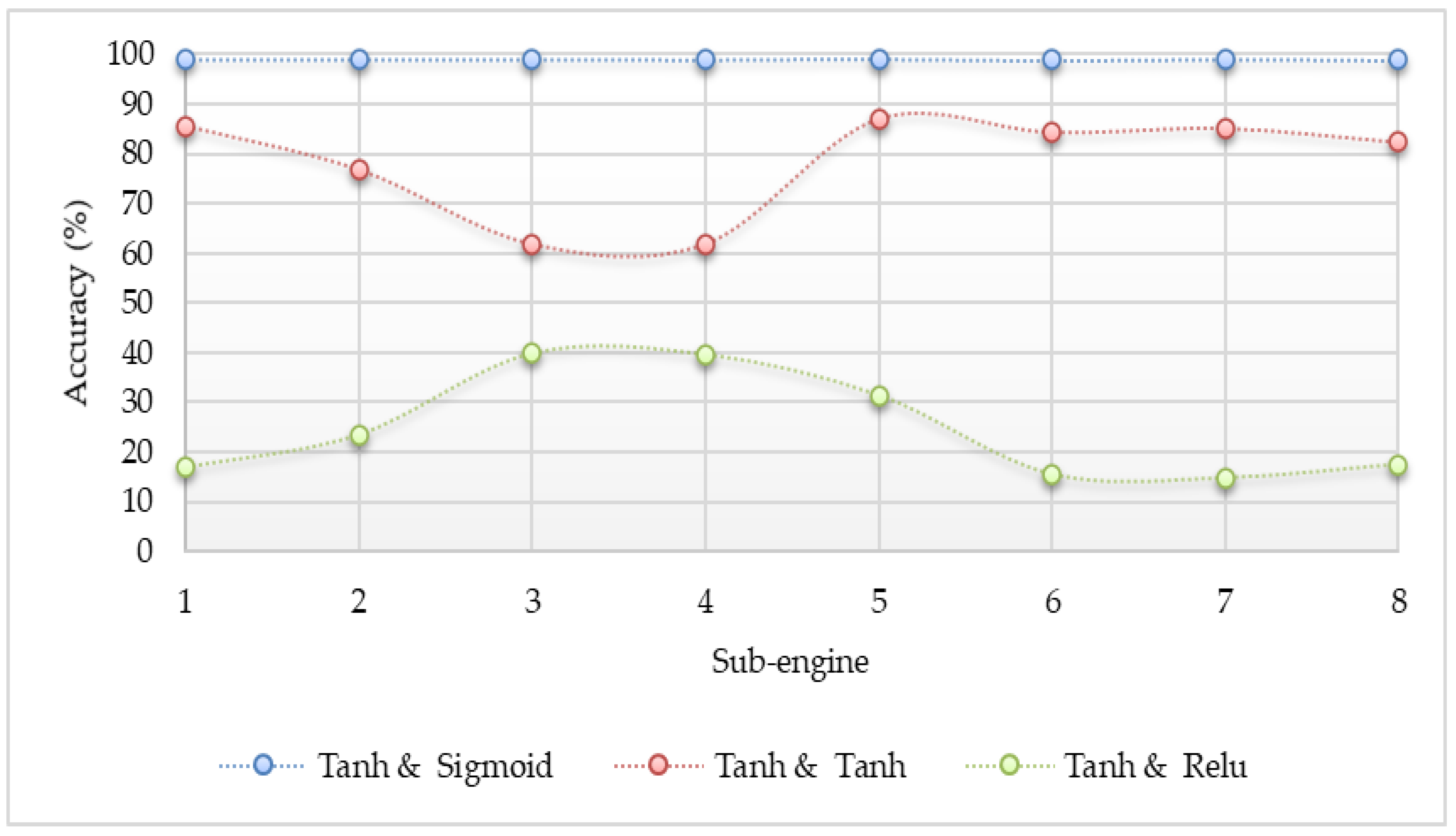
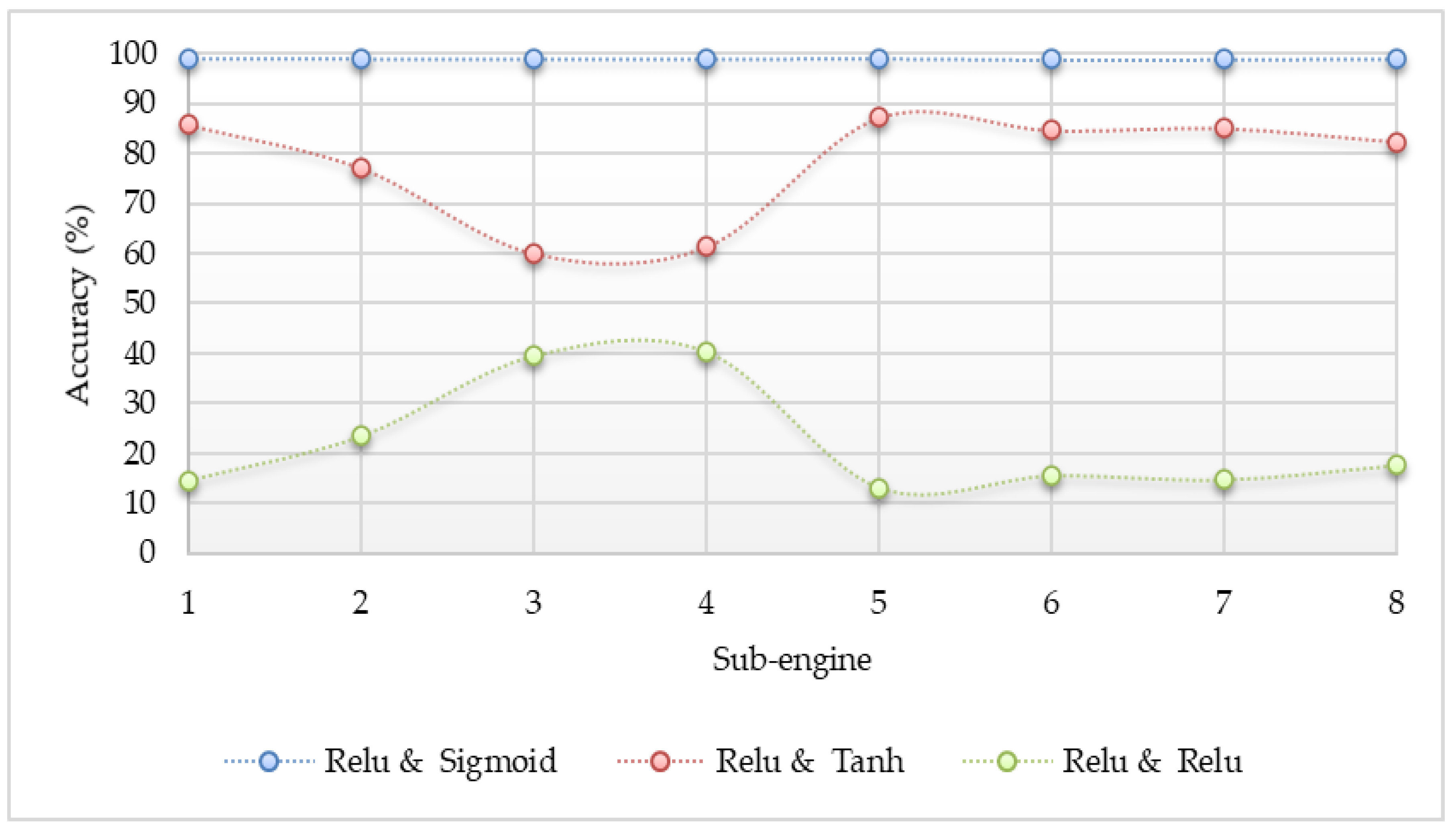
- In the construction of neural network architecture, the sigmoid function at the output layer can generate the most accurate results by our detection scheme. Even though any activation functions can be used at the hidden layer without significantly affecting detection accuracy, the implementation of the ReLU activation function at the hidden layer is more suitable because this function is lighter than the other two functions.
- The above-mentioned results show that J48 and NB are lighter than ANN even if the minimum configuration is done with a single hidden layer and a single output node. Moreover, the detection accuracy of these three classifiers is almost the same in our proposed detection scheme with the feature selector. Due to the feature selector module, the system got more accurate results and the lighter processing capability. Especially in the NB classifier, the detection accuracy for junk attack is dramatically increased up to 99.10% from 61.52%.
- Due to the model selector module, we could assign the most suitable classifier as “hybrid classification” in each of the sub-engines. It supports the system to have the most accurate results among different classifiers.
- Our detection can also be extended with additional sub-engines if necessary.
6. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Cisco. Cisco Visual Networking Index (VNI) Global Mobile Data Traffic Forecast Update, 2017–2022 White Paper; Cisco Systems Inc.: San Jose, CA, USA, 2019. [Google Scholar]
- Symantec Internet Security Threat Report 2019. Volume 24. Available online: https://docs.broadcom.com/doc/istr-24-2019-en (accessed on 2 January 2020).
- Kuzin, M.; Shmelev, Y.; Kuskov, V. New Trends in the World of IoT Threats—Securelist Kaspersky Lab. 2018. Available online: https://securelist.com/new-trends-in-the-world-of-iot-threats/87991/ (accessed on 2 January 2020).
- Marzano, A.; Alexander, D.; Fonseca, O.; Fazzion, E.; Hoepers, C.; Steding-Jessen, K.; Chaves, M.H.; Cunha, I.; Guedes, D.; Meira, W. The Evolution of Bashlite and Mirai IoT Botnets. In Proceedings of the IEEE Symposium on Computers and Communications, Natal, Brazil, 25–28 June 2018; pp. 813–818. [Google Scholar]
- Baker, A.R.; Esler, J. Snort IDS, IPS Toolkit; 30 Corporate, Dr.; Elsevier Inc.: Burlington, MA, USA, 2007; ISBN 9783540449119. [Google Scholar]
- Shah, S.A.R.; Issac, B. Performance comparison of intrusion detection systems and application of machine learning to Snort system. Futur. Gener. Comput. Syst. 2018, 80, 157–170. [Google Scholar] [CrossRef]
- Aho, A.V.; Corasick, M.J. Efficient String Matching: An Aid to Bibliographic Search Commun. ACM 1975, 18, 333–340. [Google Scholar] [CrossRef]
- OISF. Suricata User Guide; Open Information Security Foundation: Boston, MA, USA, 2019. [Google Scholar]
- Zitta, T.; Neruda, M.; Vojtech, L. The security of RFID readers with IDS/IPS solution using Raspberry Pi. In Proceedings of the 2017 18th International Carpathian Control Conference (ICCC), Sinaia, Romania, 28–31 May 2017; pp. 316–320. [Google Scholar]
- Da Silva Cardoso, A.M.; Lopes, R.F.; Teles, A.S.; Magalhaes, F.B.V. Real-time DDoS detection based on complex event processing for IoT. In Proceedings of the 2018 IEEE/ACM Third International Conference on Internet-of-Things Design and Implementation (IoTDI), Orlando, FL, USA, 17–20 April 2018; pp. 273–274. [Google Scholar]
- von Sperling, T.L.; de Caldas Filho, F.L.; de Sousa, R.T.; e Martins, L.M.C.; Rocha, R.L. Tracking intruders in IoT networks by means of DNS traffic analysis. In Proceedings of the 2017 Workshop on Communication Networks and Power Systems (WCNPS), Brasilia, Brazil, 16–17 November 2017; pp. 1–4. [Google Scholar]
- Zhao, H.; Feng, Y.; Koide, H.; Sakurai, K. An ANN Based Sequential Detection Method for Balancing Performance Indicators of IDS. In Proceedings of the 2019 Seventh International Symposium on Computing and Networking (CANDAR), Negasaki, Japan, 25–28 November 2019; pp. 239–244. [Google Scholar]
- Shafiq, M.; Tian, Z.; Sun, Y.; Du, X.; Guizani, M. Selection of effective machine learning algorithm and Bot-IoT attacks traffic identification for internet of things in smart city. Futur. Gener. Comput. Syst. 2020, 107, 433–442. [Google Scholar] [CrossRef]
- Cervantes, C.; Poplade, D.; Nogueira, M.; Santos, A. Detection of sinkhole attacks for supporting secure routing on 6LoWPAN for Internet of Things. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; pp. 606–611. [Google Scholar]
- Guo, Z.; Harris, I.G.; Jiang, Y.; Tsaur, L.F. An efficient approach to prevent battery exhaustion attack on BLE-based mesh networks. In Proceedings of the 2017 International Conference on Computing, Networking and Communications (ICNC), Santa Clara, CA, USA, 26–29 January 2017; pp. 1–5. [Google Scholar]
- Jia, B.; Ma, Y.; Huang, X.; Lin, Z.; Sun, Y. A Novel Real-Time DDoS Attack Detection Mechanism Based on MDRA Algorithm in Big Data. Math. Probl. Eng. 2016, 2016, 1467051. [Google Scholar] [CrossRef]
- Singh, K.J.; Thongam, K.; De, T. Entropy-based application layer DDoS attack detection using artificial neural networks. Entropy 2016, 18, 350. [Google Scholar] [CrossRef]
- Xu, Y.; Liu, Y. DDoS attack detection under SDN context. In Proceedings of the IEEE INFOCOM 2016-the 35th annual IEEE international conference on computer communications, San Francisco, CA, USA, 10–14 April 2016; pp. 1–9. [Google Scholar]
- Khater, B.S.; Wahid, A.; Abdul, B.; Yamani, M.; Bin, I.; Hussain, M.A.; Ibrahim, A.A. A Lightweight Perceptron-Based Intrusion Detection System for Fog Computing. Appl. Sci. 2019, 9, 178. [Google Scholar] [CrossRef]
- Creech, G.; Hu, J. Generation of a new IDS test dataset: Time to retire the KDD collection. In Proceedings of the 2013 IEEE Wireless Communications and Networking Conference (WCNC), Shanghai, China, 7–10 April 2013; pp. 4487–4492. [Google Scholar]
- Haider, W.; Creech, G.; Xie, Y.; Hu, J. Windows based data sets for evaluation of robustness of Host based Intrusion Detection Systems (IDS) to zero-day and stealth attacks. Futur. Internet 2016, 8, 29. [Google Scholar] [CrossRef]
- Soe, Y.N.; Feng, Y.; Santosa, P.I.; Hartanto, R.; Sakurai, K. A sequential scheme for detecting cyber attacks in IoT environment. In Proceedings of the 2019 IEEE Intl Conf on Dependable, Autonomic and Secure Computing, Intl Conf on Pervasive Intelligence and Computing, Intl Conf on Cloud and Big Data Computing, Intl Conf on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech), Fukuoka, Japan, 5–8 August 2019; pp. 238–244. [Google Scholar]
- Mitchell, T.M. Machine Learning; McGraw-Hill: New York, NY, USA, 1997; ISBN 978-0-07-042807-2. [Google Scholar]
- Ashari, A.; Paryudi, I.; Min, A. Performance Comparison between Naïve Bayes, Decision Tree and k-Nearest Neighbor in Searching Alternative Design in an Energy Simulation Tool. Int. J. Adv. Comput. Sci. Appl. 2013, 4, 33–39. [Google Scholar] [CrossRef]
- Kuhn, M.; Johnson, K. Applied Predictive Modeling; Springer: New York, NY, USA, 2013; ISBN 978-1-4614-6848-6. [Google Scholar]
- Hall, M. Correlation-based Feature Selection for Machine Learning. Ph.D. Thesis, University of Waikato, Hamilton, New Zealand, 1999. [Google Scholar]
- Kohavi, R.; John, G.H. Wrappers for Feature Subset Selection. Artif. Intell. 1997, 19, 273–324. [Google Scholar] [CrossRef]
- Kohavi, R.; Sommerfield, D. Feature Subset Selection Using the Wrapper Method: Overfitting and Dynamic Search Space Topology. In Proceedings of the First International Conference on Knowledge Discovery and Data Mining (KDD’95); 1995; pp. 192–197. Available online: https://openreview.net/forum?id=B1W_OEb_WH (accessed on 5 August 2020).
- Soe, Y.N.; Feng, Y.; Santosa, P.I.; Hartanto, R.; Sakurai, K. Implementing Lightweight IoT-IDS on Raspberry Pi Using Correlation-Based Feature Selection and Its Performance Evaluation Advanced Information Networking and Applications. In Proceedings of the 33rd International Conference on Advanced Information Networking and Applications AINA-2019 (Advances in Intelligent Systems and Computing), Kunibiki Messe, Matsue, Japan, 27–29 March 2019; Volume 926, pp. 458–469. [Google Scholar]
- Amini, P.; Araghizadeh, M.A.; Azmi, R. A survey on Botnet: Classification, detection and defense. In Proceedings of the 2015 International Electronics Symposium (IES), Surabaya, Indonesia, 29–30 September 2015; pp. 233–238. [Google Scholar]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Meidan, Y.; Bohadana, M.; Mathov, Y.; Mirsky, Y.; Breitenbacher, D.; Shabtai, A.; Elovici, Y. N-BaIoT: Network-based Detection of IoT Botnet Attacks Using Deep Autoencoders. IEEE Pervasive Comput. 2018, 17, 12–22. [Google Scholar] [CrossRef]
- Mirsky, Y.; Doitshman, T.; Elovici, Y.; Shabtai, A. Kitsune: An Ensemble of Autoencoders for Online Network Intrusion Detection. arXiv 2018, arXiv:1802.09089. [Google Scholar]
- Ogasawara, E.; Martinez, L.C.; Oliveira DDe Zimbrão, G.; Pappa, G.L.; Mattoso, M. Adaptive Normalization: A Novel Data Normalization Approach for Non-Stationary Time Series. In Proceedings of the 2010 International Joint Conference on Neural Networks (IJCNN), Barcelona, Spain, 18–23 July 2010; pp. 1–8. [Google Scholar]
- Pedregosa, F.; Varoquaux, G.; Gramfort, A.; Michel, V.; Thirion, B.; Grisel, O.; Blondel, M.; Prettenhofer, P.; Weiss, R.; Dubourg, V.; et al. Scikit-learn: Machine learning in Python. J. Mach. Learn. Res. 2011, 12, 2825–2830. [Google Scholar]
- Chollet, F. Keras 2015 Github Repository. Available online: https://github.com/keras-team/keras (accessed on 1 February 2020).
- Gulli, A.; Pal, S. Deep Learning with Keras; Packt Publishing Ltd.: Birmingham, UK, 2017; ISBN 978-1-78712-842-2. [Google Scholar]
- Abadi, M. 2015 {TensorFlow}: Large-Scale Machine Learning on Heterogeneous Systems Tensorflow2015-Whitepaper. Available online: https://www.tensorflow.org/ (accessed on 1 February 2020).


| Classifier | Ack | Combo | Junk | Scan | Syn | Tcp | Udp | Udpplain |
|---|---|---|---|---|---|---|---|---|
| NB | 85.81 | 77.33 | 61.52 | 76.11 | 87.08 | 84.57 | 85.18 | 82.49 |
| J48 | 99.01 | 99.01 | 99.08 | 99.05 | 99.08 | 99.05 | 98.99 | 99.09 |
| ANN | 99.01 | 99.00 | 98.98 | 98.98 | 99.01 | 98.95 | 98.97 | 99.00 |
| Classifier | Ack | Combo | Junk | Scan | Syn | Tcp | Udp | Udpplain |
|---|---|---|---|---|---|---|---|---|
| NB | 99.09 | 99.09 | 99.10 | 97.34 | 99.01 | 98.99 | 98.97 | 99.10 |
| J48 | 99.10 | 99.07 | 99.08 | 98.80 | 98.99 | 98.98 | 98.99 | 99.09 |
| ANN | 99.01 | 98.98 | 98.99 | 98.71 | 98.90 | 98.89 | 98.90 | 99.00 |
| Classifier | Training | Testing |
|---|---|---|
| NB | 16.06 | 0.44 |
| J48 | 15.05 | 0.07 |
| ANN | 151.32 | 9.71 |
| Hybrid (serial) | 1.56 | 0.03 |
| Hybrid (parallel) | 0.46 | 0.02 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Soe, Y.N.; Feng, Y.; Santosa, P.I.; Hartanto, R.; Sakurai, K. Machine Learning-Based IoT-Botnet Attack Detection with Sequential Architecture. Sensors 2020, 20, 4372. https://doi.org/10.3390/s20164372
Soe YN, Feng Y, Santosa PI, Hartanto R, Sakurai K. Machine Learning-Based IoT-Botnet Attack Detection with Sequential Architecture. Sensors. 2020; 20(16):4372. https://doi.org/10.3390/s20164372
Chicago/Turabian StyleSoe, Yan Naung, Yaokai Feng, Paulus Insap Santosa, Rudy Hartanto, and Kouichi Sakurai. 2020. "Machine Learning-Based IoT-Botnet Attack Detection with Sequential Architecture" Sensors 20, no. 16: 4372. https://doi.org/10.3390/s20164372
APA StyleSoe, Y. N., Feng, Y., Santosa, P. I., Hartanto, R., & Sakurai, K. (2020). Machine Learning-Based IoT-Botnet Attack Detection with Sequential Architecture. Sensors, 20(16), 4372. https://doi.org/10.3390/s20164372





