Blockchain Tree as Solution for Distributed Storage of Personal ID Data and Document Access Control
Abstract
1. Introduction
- It is a decentralized system.Since Blockchain data is often stored in thousands of devices on a distributed network of nodes, the system and the data are highly resistant to technical failures and malicious attacks. Each network node is able to replicate and store a copy of the database and, because of this, there is no single point of failure: a single node going offline does not affect the availability or security of the network [18].
- The transparency.
- The high security of the BlockchainThe highly secure nature of the Blockchain technology is achieved on the individual entry into the network because each person who enters the Blockchain is provided with the unique identity that is linked to his/her account. Another reason of the Blockchain security is the reliable chain of the cryptographic hash. When a new block is created, it is necessary to calculate a hash value for the new block. The new hash surely includes the previous hash’s value. This hash is generated automatically by the node key. In this case, it is impossible to change any information in the hash value [19].
- Faster and cost-effective.Traditionally, the transaction takes a lot of time in processing and initialing into banking organization. The use of Blockchain technology helps to reduce the time for processing and initialing—from approximately 3 days to several minutes or even seconds [19,20]. This advantage is the same when speaking about using Blockchain in a bank’s system.
- Stability.Confirmed blocks are very unlikely to be reversed, meaning that once data has been registered into the Blockchain, it is extremely difficult to remove or change it. This makes Blockchain a great technology for storing critical data where an audit trail is required because every change is tracked and permanently recorded on a distributed and public ledger [18].
- Data modification.Another downside of Blockchain systems is that once data has been added to the Blockchain, it is very difficult to modify or delete it. While stability is one of Blockchain’s advantages, it is not always good. For instance, this problem may actually be to fulfill the requirements of GDPR to use the right to oblivion.
- Storage.Blockchain ledgers can grow very large over time. The Bitcoin Blockchain currently requires around 200 GB of storage. The current growth in Blockchain size appears to be outstripping the growth in hard drives and the network risks losing nodes if the ledger becomes too large for individuals to download and store [18].
- Human errors.As mentioned, Blockchain is immutable, therefore information going into the database needs to be 100% sure and correct; if any mistake happens with data, it cannot be altered [18].
- High power consumption.The main disadvantage of the most-used Blockchain consensus algorithm, Proof of Work (POW), is the high energy consumption and, as a result, the high cost of a support Blockchain in general [19].
- The opportunity to split the chain.The next problem of the Blockchain is the opportunity to split the chain. The nodes, which are operating to the old software, will not accept the transactions in the new chain. This chain is created with the same history as the chain, which is based on the old software. It is named the fork [19].
2. Background
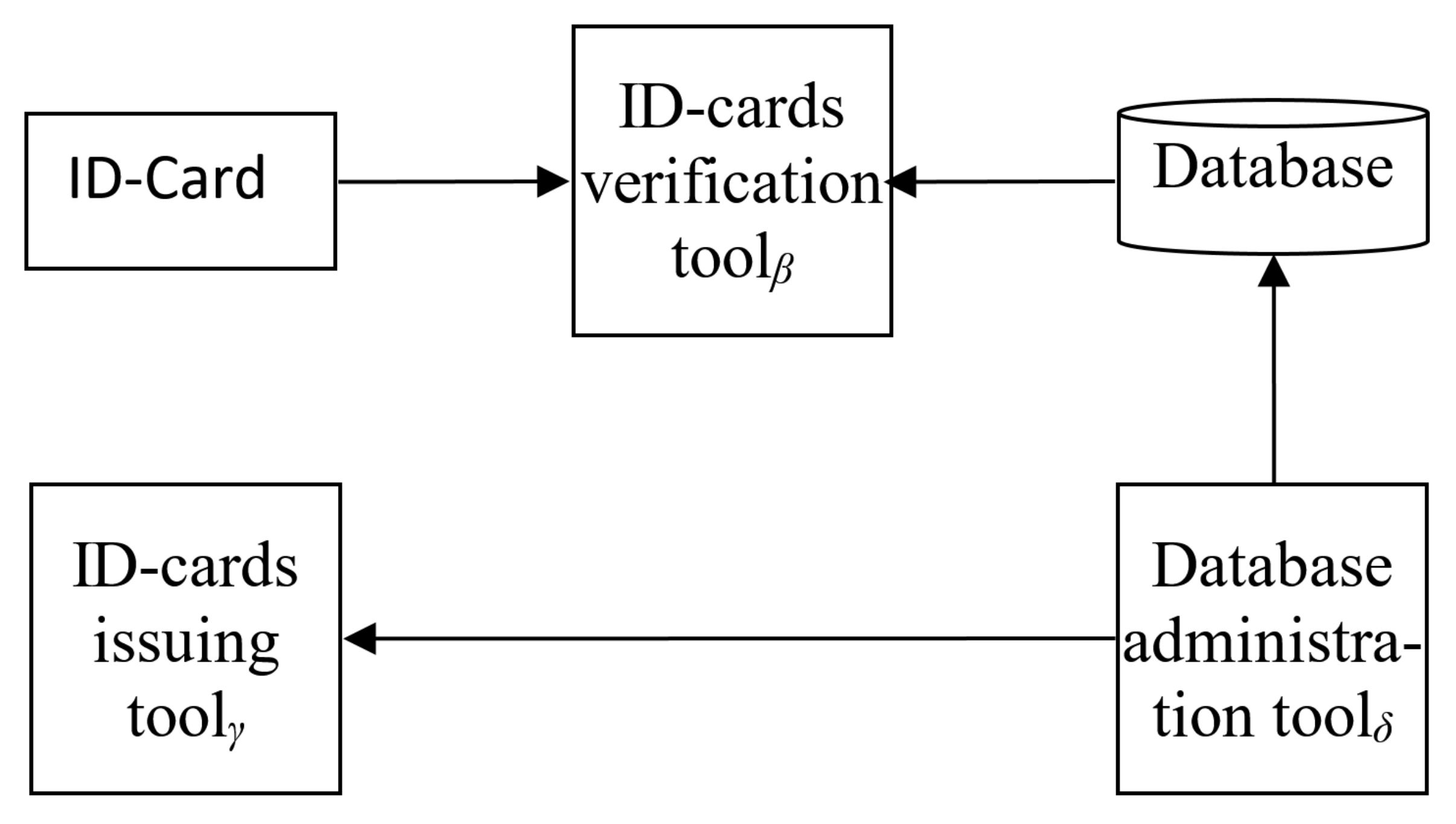
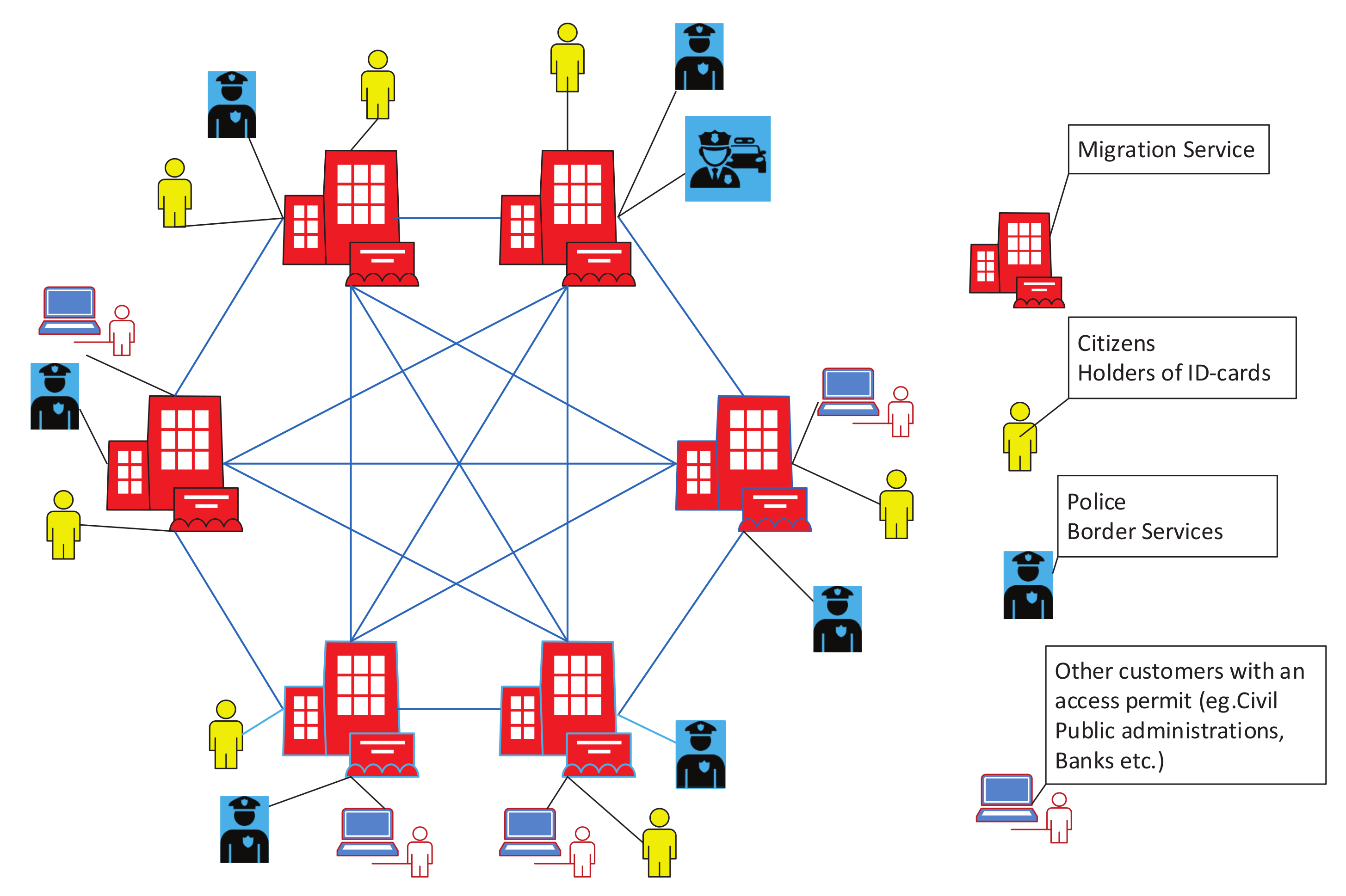
2.1. Information System Model
- Citizen ID-cards;
- Data of registered citizens (database in a wide sense);
- Tools for ID-card verification;
- Tools for database administration;
- Tools for new ID-card issuing.
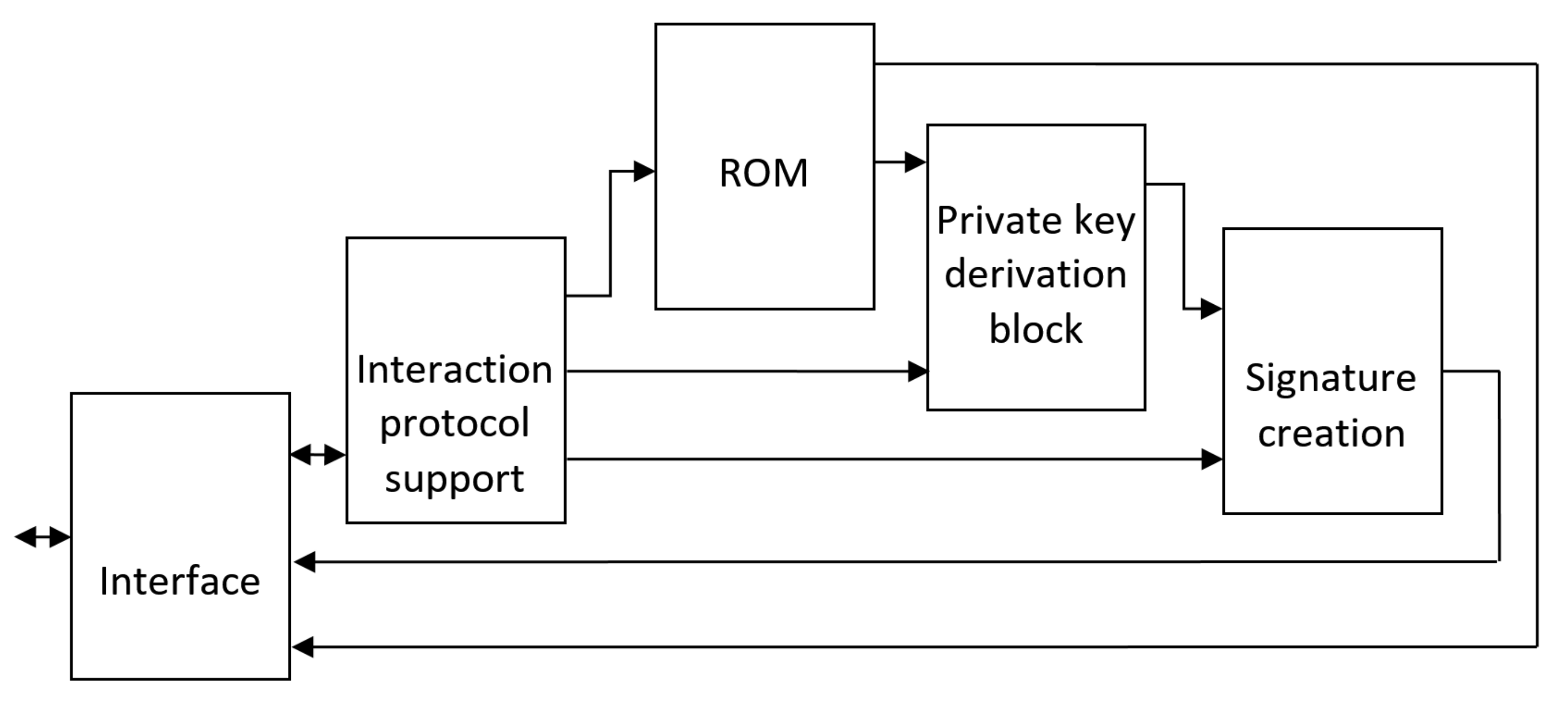
2.2. ID-Card Structure
- Encrypted memory, which contains personal data (i.e., respective block or SubBlockchain’s genesis block);
- Private key derivation block—for avoiding private key leakage;
- Signature creation block for validating changes of personal data, which could be performed when certain personal data is changed;
- Interface—for external interaction.
- Reading interface query and transmitting it to the interaction protocol support block;
- Validating the correctness of the query and determining the data fields of ROM that are to be accessed;
- Sending respective addresses to ROM and transferring them to interface;
- Sending data according to the interface query.
- The receiving respective frame-command interaction protocol support block is to wait for additional personal data input;
- After respective data input is received, the interaction protocol support block transfers it to private key derivation block and sends query to respective fields of ROM for ID-card-specific data;
- Using private key as input, the derivation block yields key and sends it to the signature-creation block;
- Meanwhile, interaction protocol support block sends data to be signed to signature-creation block, where the respective signature is obtained and outputted via interface.
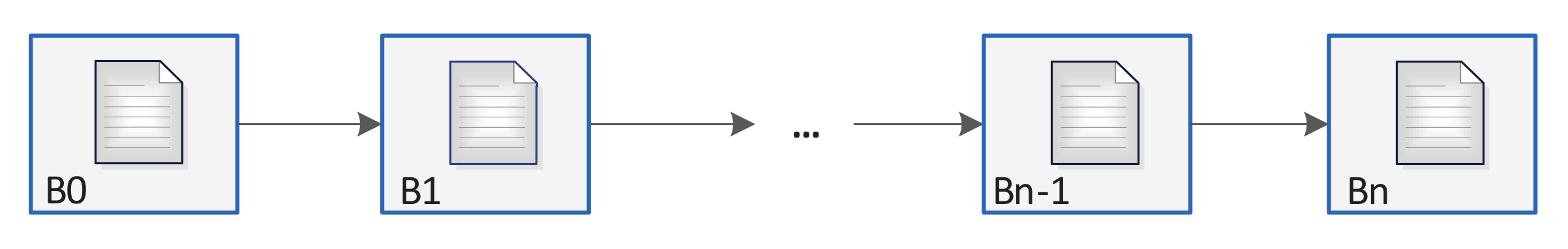
2.3. Block Structure (Information Structure on a Chip)
- Version—contains version of the block, which defines structure of other block’s fields, used consensus protocol peculiarities, presumed forks markers, etc.;
- Hash value of previous block—the integral part of any Blockchain, which provides cryptographic proof of its integrity;
- Hash value of block content—generally used for data integrity protection, but in the considered case it is also essential for rapid Blockchain content search;
- Creation Timestamp—primary intent is to boost protection by limiting potential forger by this field value (its value must be in time window between the blocks preceding and following creation timestamps (Creation Timestamps)), while the field could be used to aid stored data processing;
- Creator identifier of authentication data—is supposed to determine the source of the block (node) because for legal data, all sources, i.e., nodes, are to be determined and authorized by respective government structures.
3. Main Results
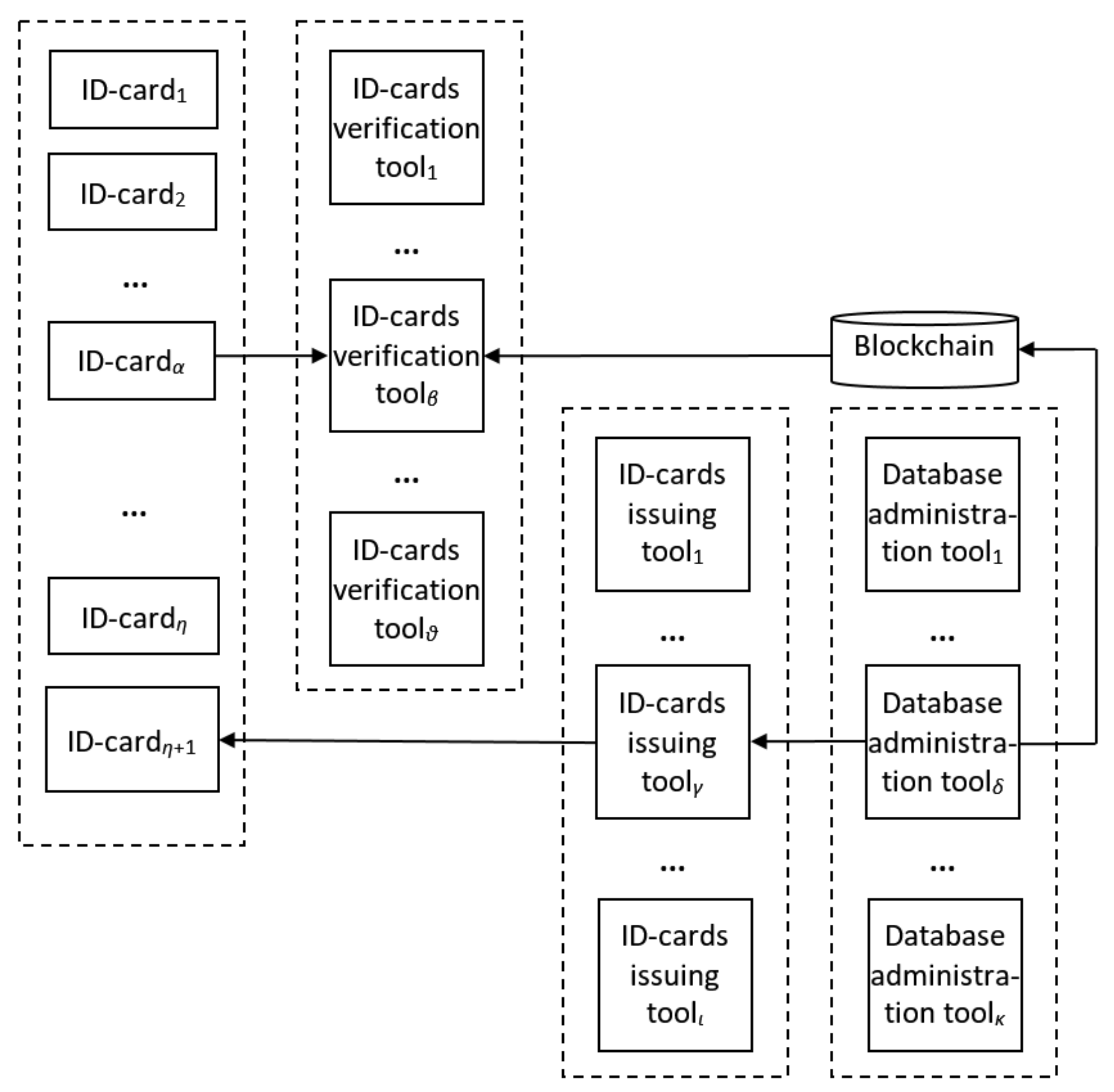
3.1. Blockchain for a Database
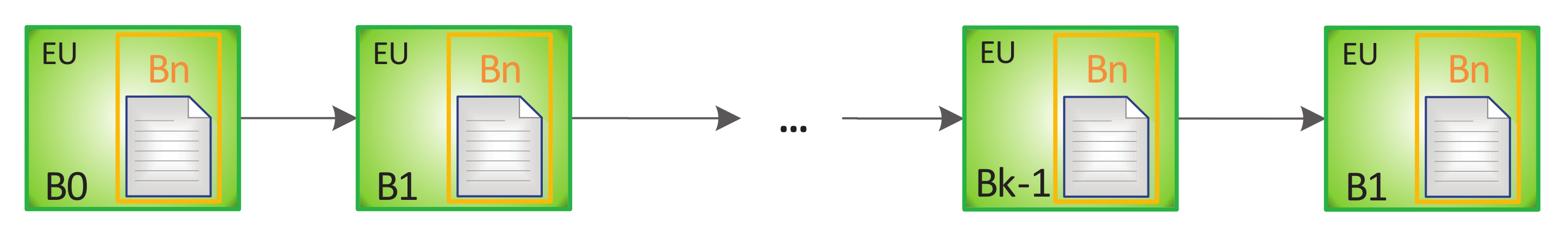
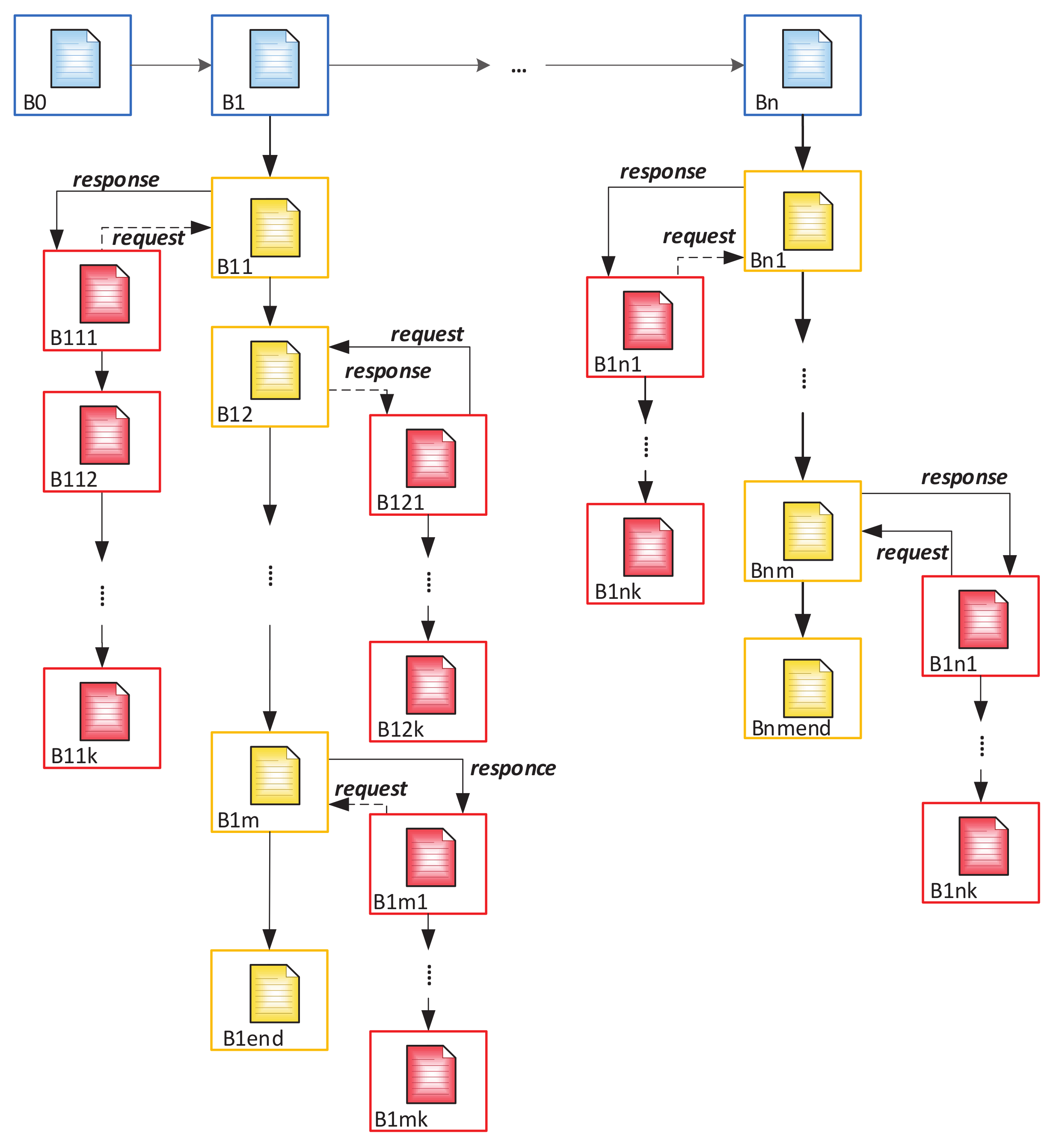
3.2. Blockchain Integration
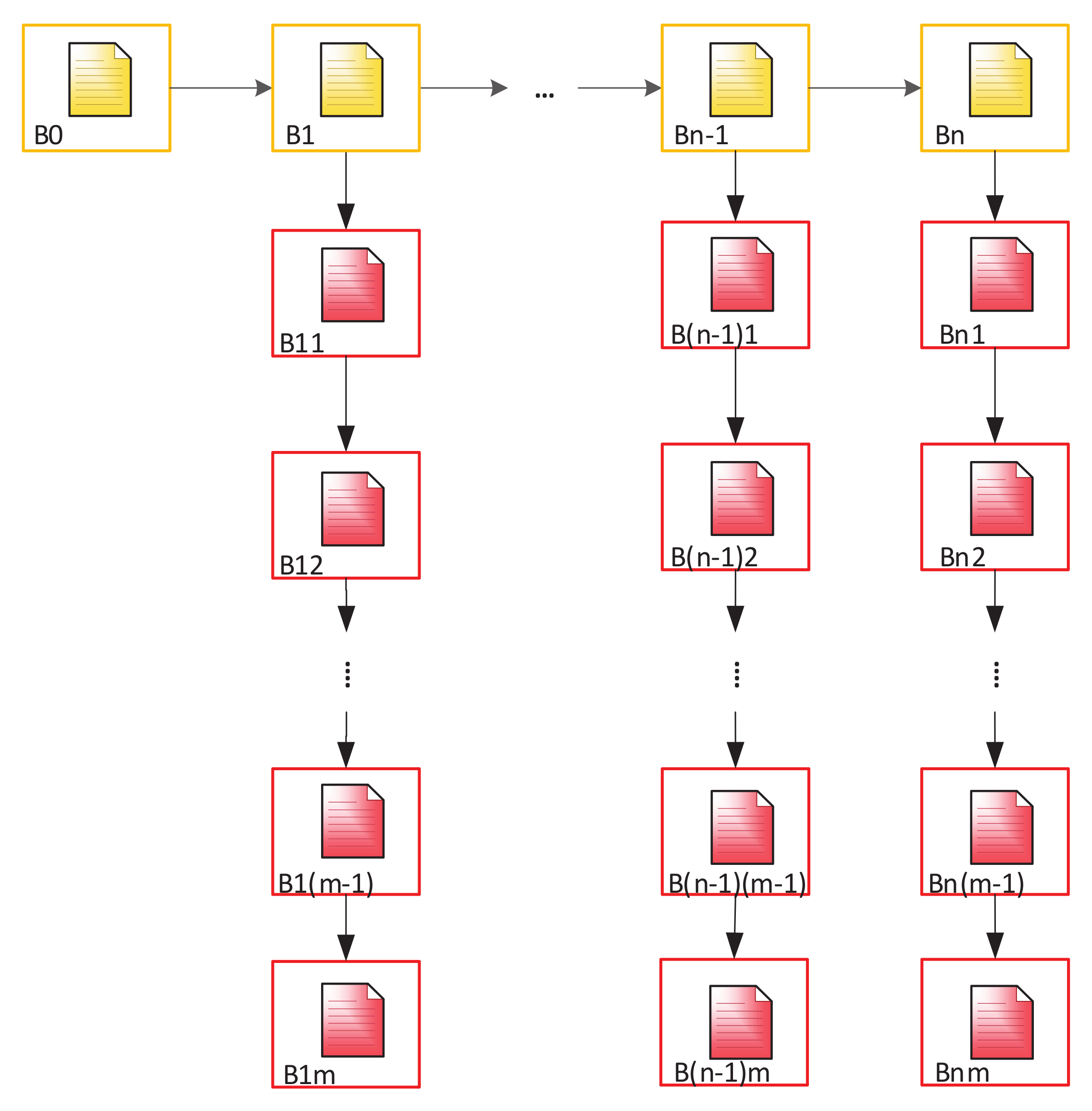
3.3. SubBlockchain for Access Control and Evaluation of ID-Cards
| Algorithm 1: Algorithm of block formation in a multichain. |
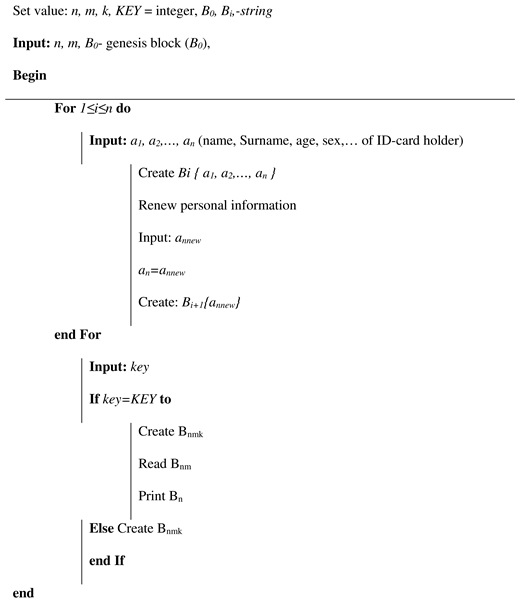 |
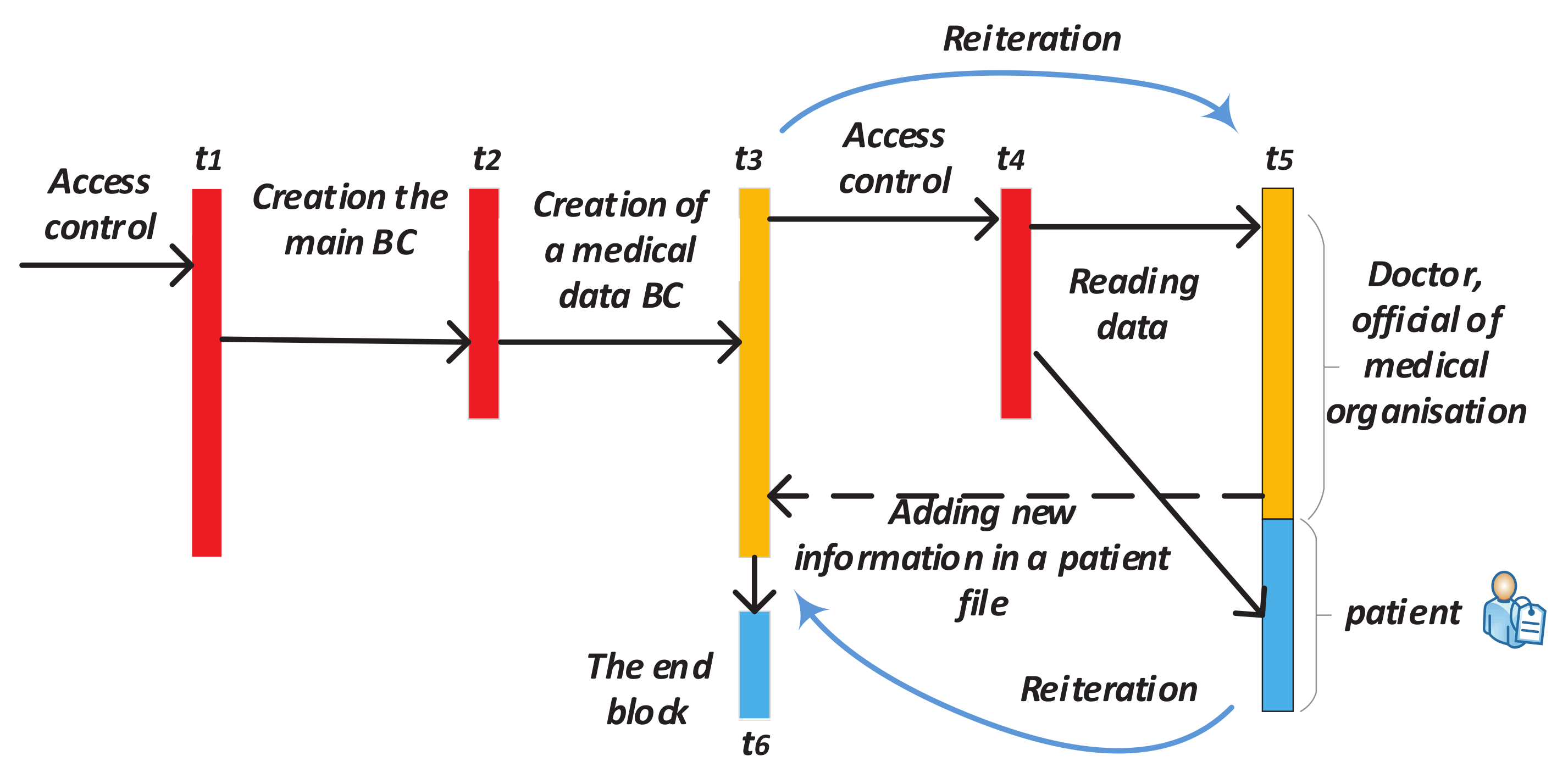
- The appeal of a citizen to authorized department and its registration in it after identity confirmation (before time t1);
- Creating a block which contains personal information of this person in the main BC (time t1–t2);
- Creating Block 1 for recording future records history in Subchain 1 (time t2–t3);
- Creating Block 1 in Subchain 2 for recording access history to Subchain 1;
- After validation of the cardholder and an official, the blocks are automatically added to Subchains 1 and 2 when the person refers to a government service where it is necessary use ID-cards (time t3);
- After checking the access right, the citizen’s or an authorized officer’s access to the person’s personal data in Subchain 1 automatically creates a new block in Subchain 2. This block contains information about password holder (in case of unsuccessful entry—about access attempt), date, local time, place, what information was viewed, etc. (time t4–t6);
- If you need to add new person information, the cycle repeats (new block is created in Subchain 1);
- Closing Subchain 1 (time t6);
- After closing Subchain 1, the information can only be viewed (without a chance of adding new data). Subchain 2 continues to grow with each following access or access attempt.
Stop Adding New Records in Blockchain
3.4. Mathematical Model
4. Summary and Discussion
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- BSI TR-03110 Technical Guideline Advanced Security Mechanisms for Machine Readable Travel Documents and eIDAS Token; Federal Office for Information Security: Bonn, Germany. 2015. Available online: https://www.bsi.bund.de/EN/Publications/TechnicalGuidelines/TR03110/BSITR03110.html (accessed on 24 June 2020).
- MachineReadable TravelDocuments, TechnicalReport, SupplementalAccessControl forMachineReadable TravelDocuments, V.1.01; Authority of the Secretary General for The INTERNATIONAL CIVIL AVIATION ORGANIZATION: Montreal, QC, Canada, 2010; Available online: https://is.gd/rhyjqj (accessed on 24 June 2020).
- Doc 9303, Machine Readable Travel Documents Part 3—Specifications Common to all MRTD, 7th ed.; International Civil Aviation Organization: Montreal, QC, Canada, 2015; Available online: https://is.gd/xyl8vu (accessed on 24 June 2020).
- Ministero Dell’Interno Italia. Carta di Identità Elettronica, Caratteristiche del Documento; Ministero Dell’Interno Italia: Rome, Italy, 2015; Available online: https://www.cartaidentita.interno.gov.it/caratteristiche-deldocumento/ (accessed on 24 June 2020).
- Trub Baltic AS: EstEID v3.4 Card Specification; AS Sertifitseerimiskeskus: Tallinn, Estonia, 2012; Available online: http://www.id.ee/public/TB-SPEC-EstEID-Chip-App-v3.4.pdf (accessed on 24 June 2020).
- A Blockchain Platform for the Enterprise. 2019. Available online: https://hyperledger-fabric.readthedocs.io/en/release-1.4/ (accessed on 24 June 2020).
- Debin, L.; Camp, L.J. The Bitcoin Backbone Protocol: Analysis and Applications. In Proof of Work Can Work, Fifth Workshop on the Economics of Information Security; Springer: Berlin/Heidelberg, Germany, 2006. [Google Scholar]
- Garay, J.A.; Kiayias, A.; Leonardos, N. The Bitcoin Backbone Protocol: Analysis and Applications. In EUROCRYPT—34th Annual International Conference on the Theory and Applications of Cryptographic Techniques; Lecture Notes in Computer Science; Oswald, E., Fischlin, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; Volume 9057, pp. 281–310. [Google Scholar] [CrossRef]
- Matsuo, S.; Miyazaki, K.; Otsuka, A.; Basin, D. How to evaluate the security of real-life cryptographic protocols? the cases of ISO/IEC 29128 and CRYPTREC. Financ. Cryptogr. Data Secur. 2010, 6054, 182–194. [Google Scholar] [CrossRef]
- Bentov, I.; Lee, C.; Mizrahi, A.; Rosenfeld, M. Proof of Activity: Extending Bitcoin’s Proof of Work via Proof of Stake [Extended Abstract]Y. SIGMETRICS Perform. Eval. Rev. 2014, 42, 34–37. [Google Scholar] [CrossRef]
- EOS.IO. EOS.IO Technical White Paper v2. Available online: https://github.com/EOSIO/Documentation/blob/master/TechnicalWhitePaper.md (accessed on 24 June 2020).
- Koles, A. How Blockchain Could Change the Global Remittance Industry. Available online: https://www.bankingtech.com/2018/06/how-blockchain-could-change-the-global-remittance-industry (accessed on 24 June 2020).
- Blockchain in Logistics, Perspectives on the Upcoming Impact of Blockchain Technology and Use Cases for the Logistics Industry; DHL Customer Solutions & Innovation: Troisdorf, Germany, 2018.
- Kushch, S.; Prieto-Castrillo, F. A review of the applications of the Blockchain technology in smart devices and distributed renewable energy grids. Adv. Distrib. Comput. Artif. Intell. J. 2017, 6. [Google Scholar] [CrossRef]
- Prieto-Castrillo, F.; Kushch, S.; Corchado, J.M. Distributed Sequential Consensus in Networks: Analysis of Partially Connected Blockchains with Uncertainty. Complexity 2017, 1–11. [Google Scholar] [CrossRef]
- Kushch, S.; Prieto-Castrillo, F. Blockchain for Dynamic Nodes in a Smart City. In Proceedings of the 2019 IEEE 5th World Forum on Internet of Things (WF-IoT), Limerick, Ireland, 15–18 April 2019; pp. 29–34. [Google Scholar] [CrossRef]
- Kushch, S.; Ranise, S.; Sciarretta, G. Blockchain Tree for eHealth. In Proceedings of the 2019 IEEE Global Conference on Internet of Things (GCIoT), Dubai, UAE, 4–7 December 2019. [Google Scholar]
- Blockchain Advantages and Disadvantages. Available online: https://academy.binance.com/blockchain/positives-and-negatives-of-blockchain (accessed on 24 June 2020).
- Golosova, J.; Romanovs, A. The Advantages and Disadvantages of the Blockchain Technology. In Proceedings of the IEEE 6th Workshop on Advances in Information, Electronic and Electrical Engineering (AIEEE), Vilnius, Lithuania, 8–10 November 2018. [Google Scholar] [CrossRef]
- Blockchain Technology, Advantages & Disadvantages of Blockchain Technology. Available online: https://blockchaintechnologycom.wordpress.com/2016/11/21/advantages-disadvantages (accessed on 24 June 2020).
- Jakobsson, M.; Juels, A. Proofs of Work and Bread Pudding Protocols. In Communications and Multimedia Security; Kluwer Academic Publishers: Dordrecht, The Netherlands, 1999; pp. 258–272. [Google Scholar]
- Laurie, B.; Clayton, R. Proof of Work can Work. In Proceedings of the Third Annual Workshop on Economics and Information Security (WEIS04), Minneapolis, MN, USA, 13–14 May 2004. [Google Scholar]
- Buterin, V. What Proof of Stake Is And Why It Matters. Available online: https://bitcoinmagazine.com/articles/what-proof-of-stake-is-and-why-it-matters-1377531463 (accessed on 24 June 2020).
- Chohan, U.W. Proof-of-Stake Algorithmic Methods: A Comparative Summary; TNotes on the 21 st Century; University of New South Wales: Canberra, Australia, 2018; p. 8. [Google Scholar] [CrossRef]
- Beikverdi, A. Proof-of-Importance: How NEM is Going to Add Reputations to the Blockchain. Available online: https://cointelegraph.com/news/proof-of-importance-nem-is-going-to-add-reputations-to-the-blockchain (accessed on 24 June 2020).
- Bentov, I.; Gabizon, A.; Mizrahi, A. Cryptocurrencies Without Proof of Work. In Financial Cryptography and Data Security; Clark, J., Meiklejohn, S., Ryan, P.Y., Wallach, D., Brenner, M., Rohloff, K., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; pp. 142–157. [Google Scholar] [CrossRef]
- Lim, S.Y.; Fotsing, P.; Almasri, A.; Musa, O.; Mat Kiah, M.L.; Ang, T.; Ismail, R. Blockchain Technology the Identity Management and Authentication Service Disruptor: A Survey. Int. J. Adv. Sci. Eng. Inf. Technol. 2018, 8, 1735. [Google Scholar] [CrossRef]
- Jacobovitz, O. Blockchain for Identity Management; Ben-Gurion University: Beer Sheva, Israel, 2016. [Google Scholar]
- Estonian eID Scheme: E-Residency Digi-ID. Technical Specifications and Procedures for Assurance Level High for Electronic Identification; Police and Border Guard Board: Tallinn, Estonia, 2018.
- Khovratovich, D.; Law, J. Sovrin: Digital Identities in the Blockchain Era. 2016, p. 5. Available online: https://sovrin.org/wp-content/uploads/AnonCred-RWC.pdf (accessed on 14 June 2020).
- Reed, D.; Sporny, M.; Longley, D.; Allen, C.; Grant, R.; Sabadello, M. Decentralized Identifiers (DIDs) v1.0. Available online: https://www.w3.org/TR/2020/WD-did-core-20200608/ (accessed on 14 June 2020).
- Konashevych, O. Advantages and Current Issues of Blockchain Use in Microgrids. Èlektronnoe Model. 2016, 38, 93–104. [Google Scholar] [CrossRef]

| N | Content | Example | Length (Bits) |
|---|---|---|---|
| 1 | Surname | Smith | Max 28 |
| 2 | First name line 1 | John | Max 15 |
| 3 | First name line 2 | Max 15 | |
| 4 | Sex | M | 1 |
| 5 | Nationality | POL | 3 |
| 6 | Date of birth | 01.01.1971 | 10 |
| 7 | Personal ID code | 37101010021 | 11 |
| 8 | Document number | X0010536 | 8 or 9 |
| 9 | Expiry date | 13.08.2019 | 10 |
| 10 | Place of birth | POOL/POL | Max 35 |
| 11 | Date of issuance | 13.08.2014 | 10 |
| 12 | Permit type | PERMANENT | Max 50 |
| 13 | Notes line 1 | EL KODANIK/EU CITIZEN | Max 50 |
| 14 | Notes line 2 | ALALINE ELAMISOIGUS | Max 50 |
| 15 | Notes line 3 | PERMANENT RIGHT OF RESIDENCE | Max 50 |
| 16 | Notes line 4 | LUBATUD TOOTAD | Max 50 |
| N | Content | Example | Length (Bits) |
|---|---|---|---|
| 1 | Community of issue | Milano | Max 28 |
| 2 | Serial number | AA00000BB | Max 15 |
| 3 | First name line 1 | John | Max 15 |
| 4 | First name line 2 | Max 15 | |
| 5 | Surname | Smith | Max 15 |
| 6 | Place of birth | Milano | Max 35 |
| 7 | Sex | M | 1 |
| 8 | Nationality | ITA | 3 |
| 9 | Date of birth | 01.01.1971 | 10 |
| 10 | Stature | 186 | 3 |
| 11 | Citizenship | ITA | 3 |
| 12 | Image of the holder’s signature | “digital scan” | 50 |
| 13 | Validity for expatriation | 13.08.2014 | 10 |
| 14 | Photography | “Digital photo” | Max 50 |
| 15 | Images of 2 fingerprints (one finger of the right hand and one finger of the left hand) | “Digital photo” | Max 50 |
| 16 | Parents (in the case of a minor’s card) | Max 50 | |
| 17 | Fiscal Code (Personal ID code) | ABCDEF00B00A111W | 16 |
| 18 | Address of residence | Verona str., 1, Rome | Max 50 |
| 19 | Tax code in the form of a barcode | Barcode | Max 100 |
| 20 | Information about the documents on the basis of which the ID-card was issued | - | Max 50 |
| 21 | The number of the block storing information about the previous ID-card (in case of renewal or update of the card). This parameter = 0 if the card is being issued for the first time | - | Max 50 |
| 22 | ID of migration police officer who created personal file of a citizen | - | Max 50 |
| 23 | Notes line 4 | Permanent residence | Max 50 |
| 24 | Notes line 4 | - | Max 50 |
| 25 | Notes line 4 | - | Max 50 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kushch, S.; Baryshev, Y.; Ranise, S. Blockchain Tree as Solution for Distributed Storage of Personal ID Data and Document Access Control. Sensors 2020, 20, 3621. https://doi.org/10.3390/s20133621
Kushch S, Baryshev Y, Ranise S. Blockchain Tree as Solution for Distributed Storage of Personal ID Data and Document Access Control. Sensors. 2020; 20(13):3621. https://doi.org/10.3390/s20133621
Chicago/Turabian StyleKushch, Sergii, Yurii Baryshev, and Silvio Ranise. 2020. "Blockchain Tree as Solution for Distributed Storage of Personal ID Data and Document Access Control" Sensors 20, no. 13: 3621. https://doi.org/10.3390/s20133621
APA StyleKushch, S., Baryshev, Y., & Ranise, S. (2020). Blockchain Tree as Solution for Distributed Storage of Personal ID Data and Document Access Control. Sensors, 20(13), 3621. https://doi.org/10.3390/s20133621





