Defending Airports from UAS: A Survey on Cyber-Attacks and Counter-Drone Sensing Technologies
Abstract
1. Introduction
- Spying and tracking points of interest, conducting unauthorized mapping and surveillance.
- Carrying CRBNE payloads (chemical, radiological, biological, nuclear and explosive materials) towards fixed installations or moving targets.
- Intercepting wireless networks, breaching computer systems and conducting cyberattacks by hovering or landing on buildings.
2. Worldwide Incidents with UAS
- UK: A serious incident happened between 19–21 December 2018 in London, when Gatwick Airport stopped its operations due to a drone attack. Police investigators said that it was a planned attack, involving someone with inside knowledge of the airport’s operational procedures. It is estimated that 140,000 passengers were affected, with around 1000 flights either diverted or cancelled [19]. The attack cost the airport approx. £1.4 m, but airlines were hit even harder, with EasyJet is said to have lost £15 m through the 3-day attack. A similar disruption took place one month later at Heathrow Airport in January 2019, although with limited duration [20].
- Ireland: Flight operations at Dublin airport were suspended for half an hour in February 2019 due to the confirmed sighting of a drone over the airfield, despite a drone prohibition within 5 km (3 m) of Irish airports [21].
- Germany: Frankfurt airport was shut down for an hour on 9 May 2019 as operators halted flights over a drone sighting. Overall, 143 take-offs and landings were cancelled, while 48 aircrafts were diverted to other airports among a total of 1500 scheduled flights [22].
- Singapore: Two incidents occurred where unauthorized drone flying affected flights at Changi Airport twice in one week during June 2019. Overall, 52 flights were delayed and 8 were diverted due to these drone sightings [23].
- UAE: Dubai International Airport (DXB) was closed three times (an accumulated 115-min closing) in 2016 due to illegal drone activities near the airport. The Emirates Authority for Standardization and Metrology estimated the financial losses to be USD 95,368 per minute due to shutdowns caused by drones. The total loss of DXB in 2016 was approx. USD 11M due to drones [24].
- Japan: A drone spotted flying near Osaka’s Kansai International Airport in October 2019 led to the temporary closure of the major hub, despite the fact that flying drones near Kansai Airport and bringing drones inside the airport is prohibited [25].
- Canada: A Beech King Air A100 of Skyjet Aviation collided with a UAV in October 2017 while approaching Jean Lesage Airport near Quebec City. The aircraft landed safely despite being hit on the wing. Neither the UAV nor the operator have been found. The UAV had been flying at 1500 ft, i.e., five times the maximum altitude that UAVs are permitted to fly at in Canada [26].
- New Jersey, USA: Newark Airport was closed due to a drone spotted in the vicinity for 90 min in January 2019. Estimating a cost of USD 1M per minute for the airport closure, the incident caused USD 90M of economic loss. Airplanes were diverted to other airports using extra fuel consumption and adding to the economic loss for the airlines [27].
- New York, USA: A civilian UAV collided with a Black Hawk helicopter over the eastern shore of Staten Island in September 2017. The helicopter was able to continue flying and landed at Linden Airport. Nobody was hurt, but part of the UAV was found at the bottom of the main rotor system [28].
- South Carolina, USA: A helicopter crash was triggered by a civilian drone in February 2018. This was the first drone-linked aircraft crash. The helicopter’s tail struck a tree while trying to evade a small drone, triggering a crash landing. The student and instructor pilots were uninjured, according to a Charleston Police Department Report [29].
3. Literature Review on Counter-Drone (C-UAS) Technologies
3.1. Preventing Actions
3.2. Detection Sensors and Technologies
3.3. Mitigation Countermeasures
- Net capturing is the attempt to physically capture a drone. An enforced and hardened UAV flies toward the intruding drone and carries attack nets in order to seize and bring back the targeted UAS. Such systems work at relatively short distances and are effective when the nefarious drone navigates with a low speed or does not maneuver.
- Birds of prey are trained birds with protective gear, which are used to attack and grab UAS, when entering into a restricted area. However, birds are also restricted and pose hazards when flying around airport areas due to possible conflicts with arriving or landing aircraft.
- High-power microwave (HPM) or laser fire: using high-power electromagnetic pulse or laser weapons, security teams are able to target and shoot down UAVs. HPM or high-energy lasers destroy electronic circuits and other vital segments of the drone’s airframe. It often causes UAVs to crash to the ground.
3.4. Counter-UAS Applied Techologies in Commercial Systems
4. Attacks with Drones in Airport Critical Infrastructures: Scenario Analysis
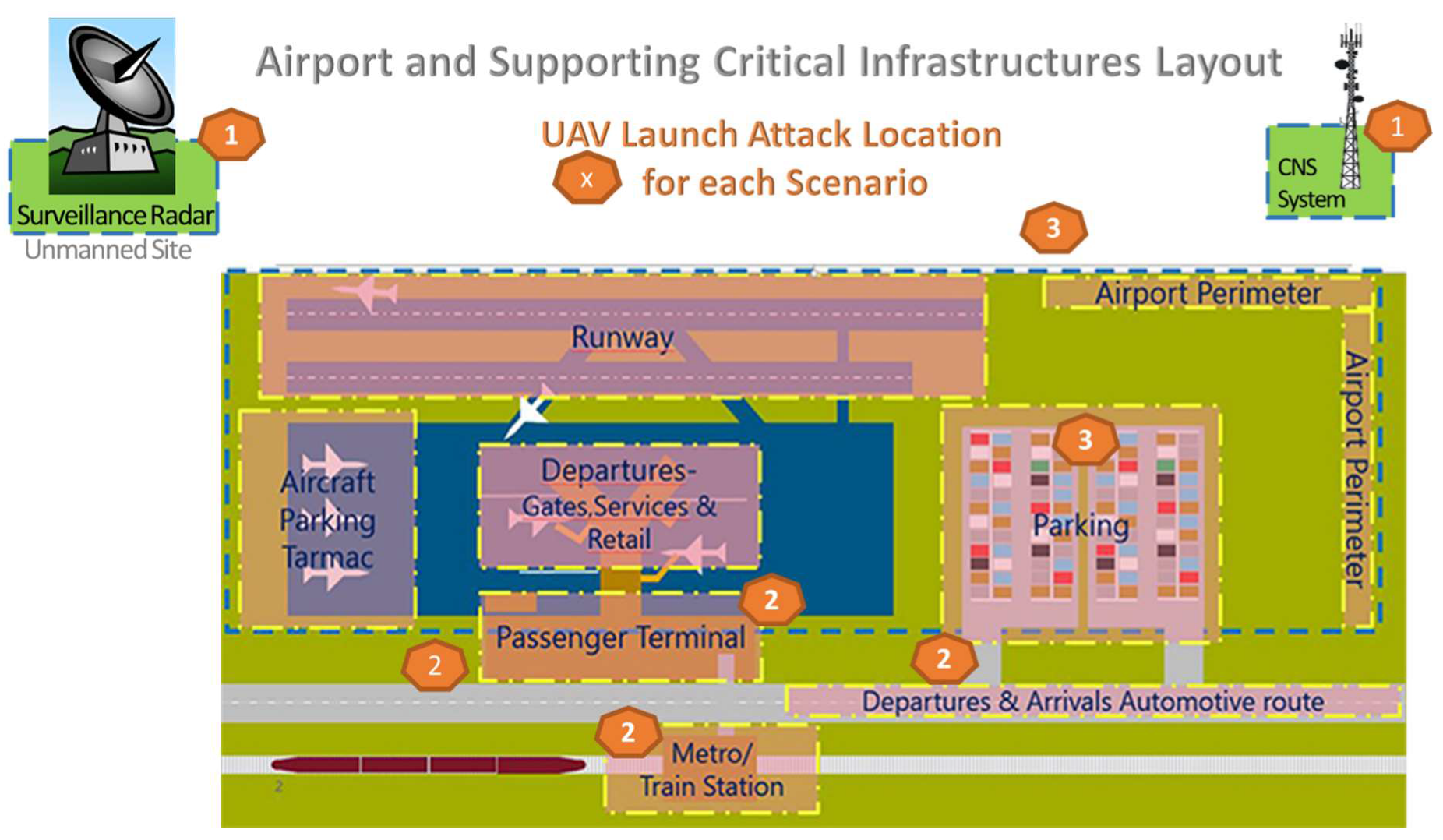
- Scenario (1): Drone attack to remotely located or unmanned sites near airports that support air traffic management (ATM) critical infrastructures;
- Scenario (2): UAS attack against airport wireless systems, information systems and data links;
- Scenario (3): Drone attack to ATM Systems, jeopardizing flight safety of manned aviation.
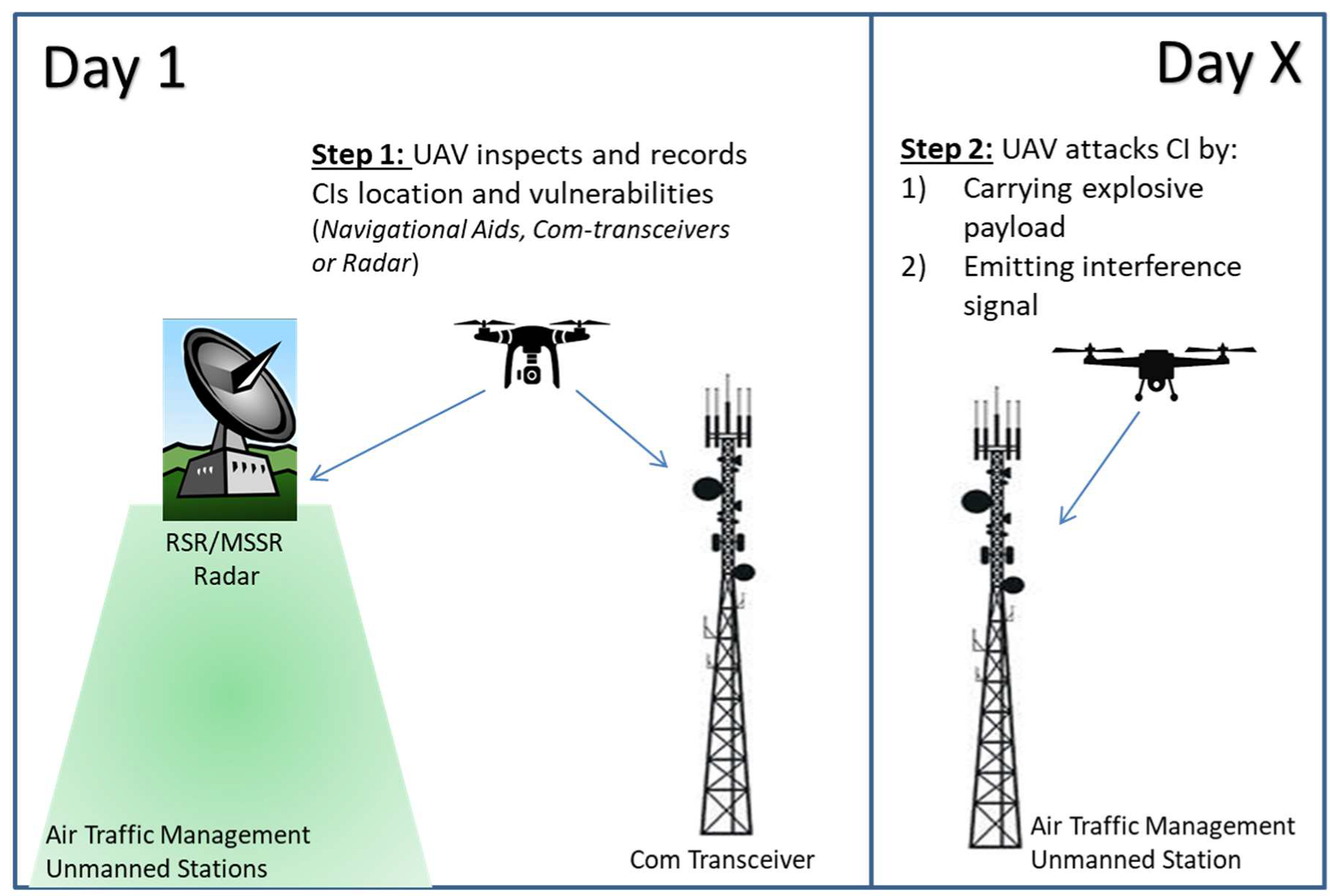
4.1. Scenario 1: Drone Attack to Unmanned Sites, Supporting ATM CIs
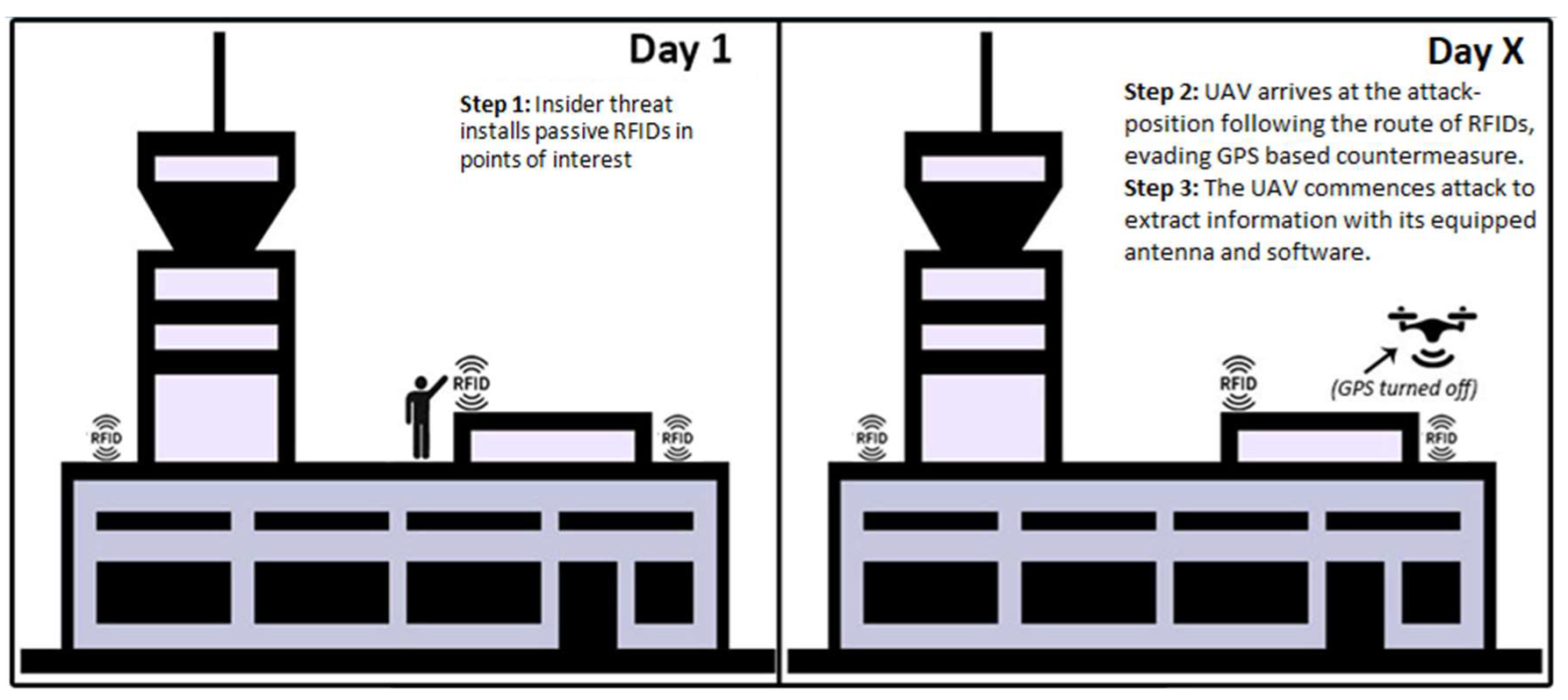
4.2. Scenario 2: UAS attack on an Airport’s Wireless Network and IT Infrastructures
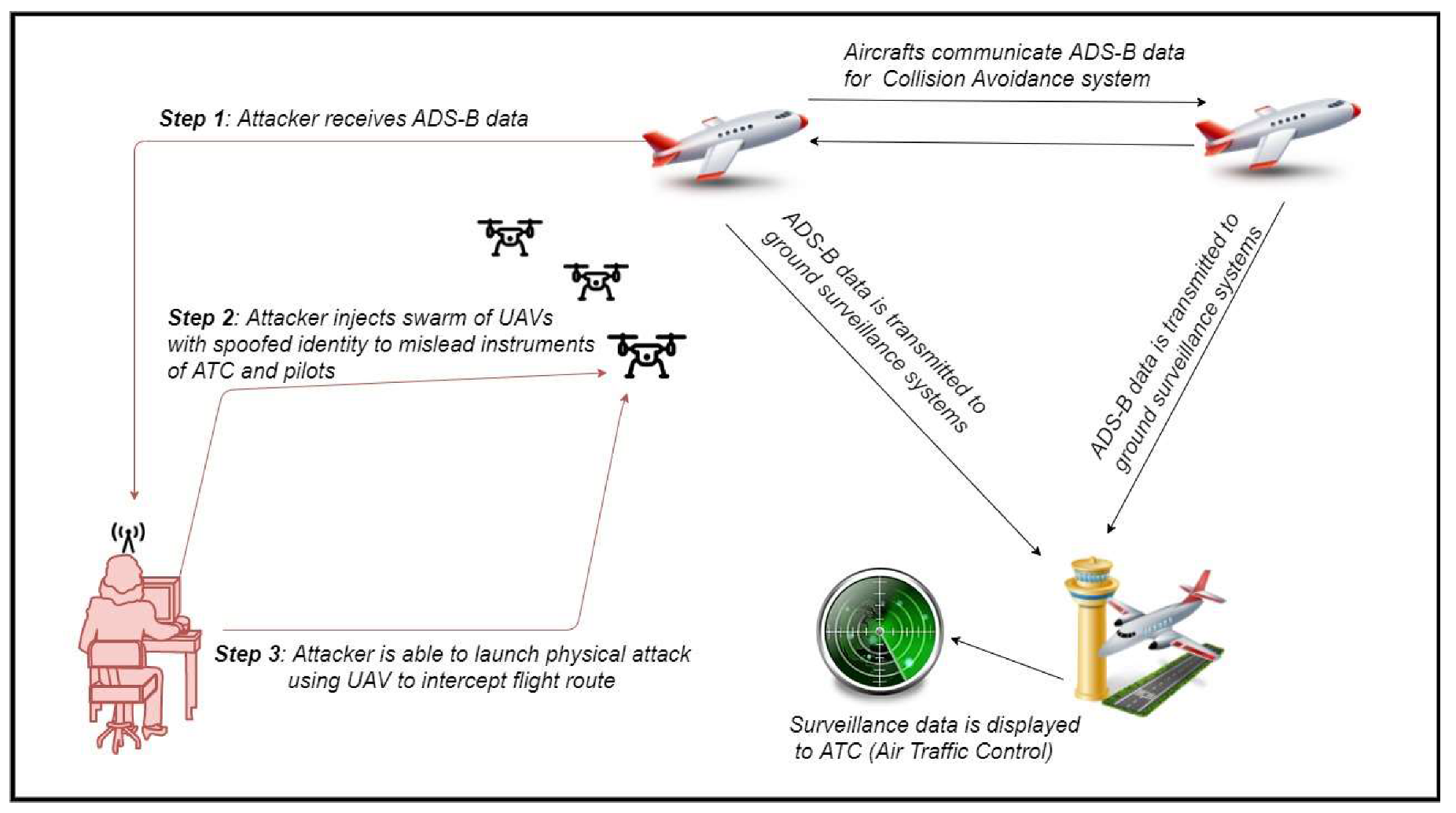
4.3. Scenario 3: Cyber-Physical Attack to Air Traffic Management Systems and Manned Aircrafts
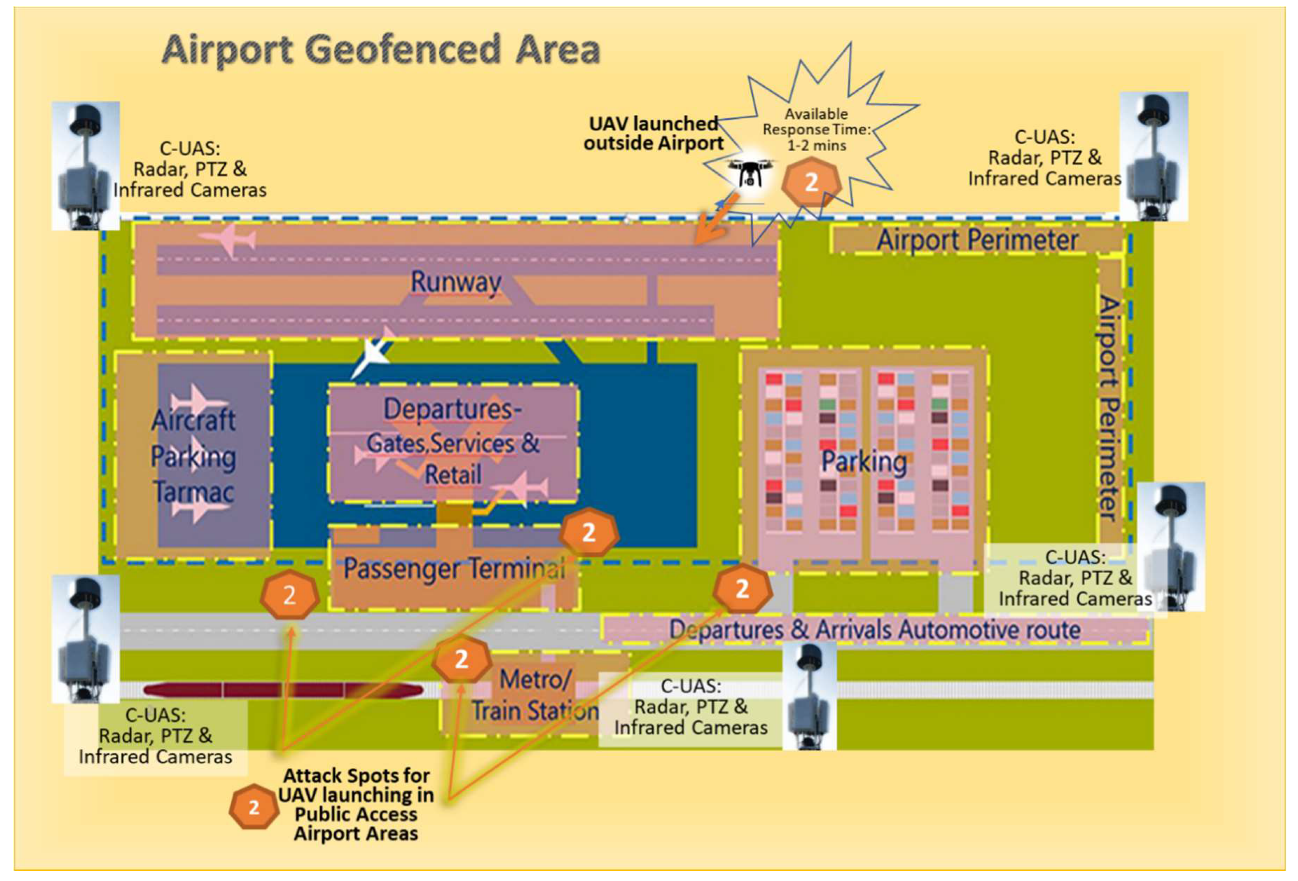
5. Proposed Countermeasures for Airports
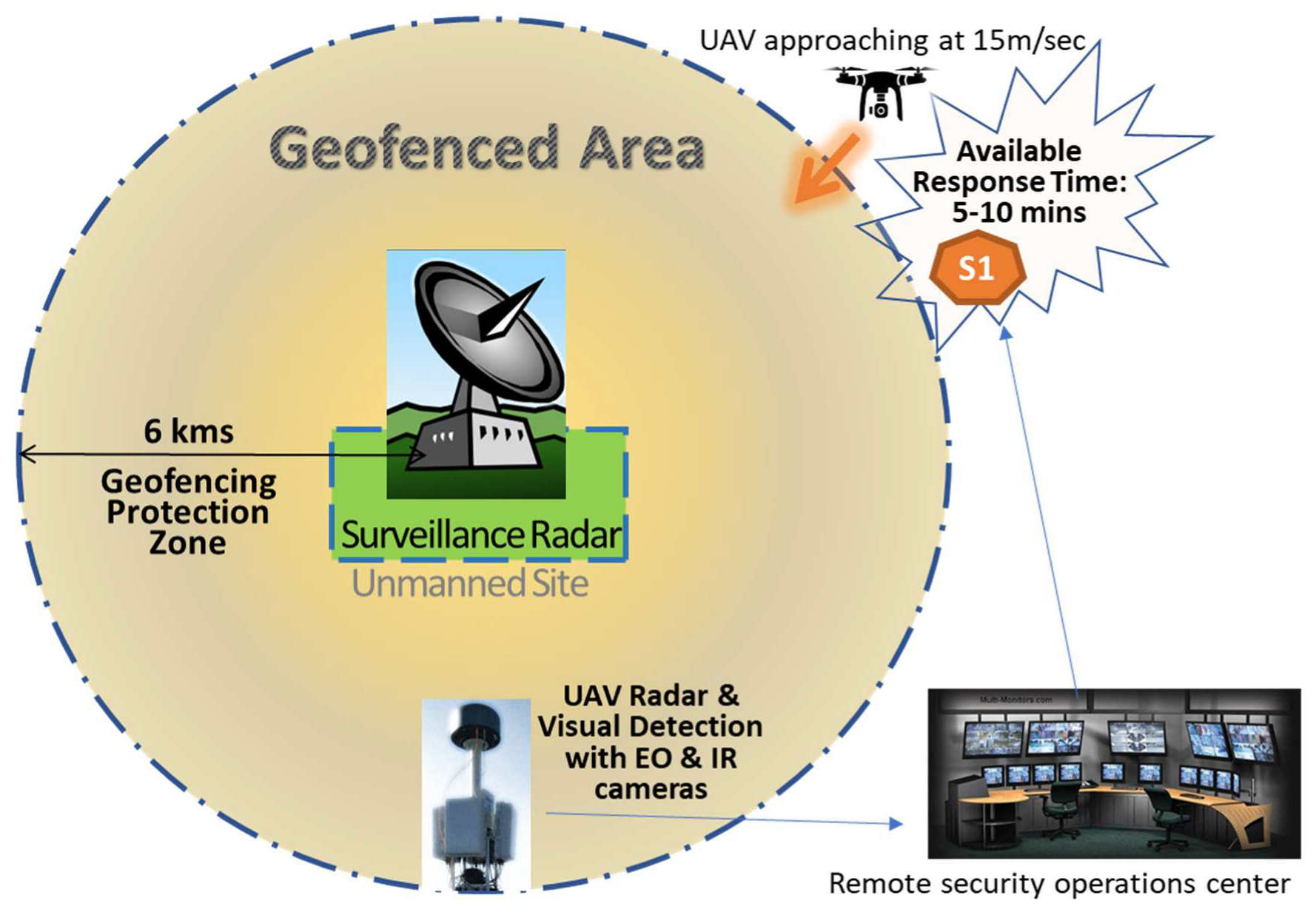
5.1. Scenario 1: Drone Attack to Unmanned Sites Supporting ATM-Critical Infrastructure
5.2. Scenario 2: UAS attack on an Airport’s Wireless Network and IT Infrastructure
5.3. Scenario 3: Cyber-Physical Attack to Air Traffic Management Systems and Manned Aircrafts
6. Discussion on C-UAS Applicability in Airports and Resilience Plans
- (i)
- Implement an effective UAS detection system and create an internal reporting point for drone sightings. It is imperative to understand which part of a facility’s airspace has been infringed upon and locate the drone at all times during the incursion.
- (ii)
- Identify the drone and understand the type of UAV being used, what threat may be posed to the airport operator or airspace management and what mitigation options are available.
- (iii)
- If any mitigation options are adopted, they must be legal, proportionate and properly risk assessed, so as not to create any other hazard to the wider airport community.
- (iv)
- An appropriate liaison with security partners and legal agencies (police, civil protection and civil aviation authorities etc.) should be established, in order to coordinate the response when an incident takes place.
- (v)
- Whenever a drone interrupts an airport’s operation, and before resuming the flight schedule, the operator should confirm that the airspace is clear, the drone is disabled and it is safe for operations to restart.
- (vi)
- Ensure that the business continuity plan, developed for airport operations, has included such types of UAV disruptions, while regularly exercising a preparedness scenario involving all aviation stakeholders.
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- European Union. Artificial Intelligence and Civil Law; Liability Rules for Drones. Available online: https://www.europarl.europa.eu/thinktank/en/document.html?reference=IPOL_STU (accessed on 18 December 2019).
- FAA Aerospace Forecasts. Unmanned Aircraft Systems. Available online: https://www.faa.gov/data_research/aviation/aerospace_forecasts/media/unmanned_aircraft_systems.pdf (accessed on 4 December 2019).
- United Nations Security Council Counter-Terrorism Committee Executive Directorate (CTED) Report, Greater Efforts Needed to Address the Potential Risks Posed by Terrorist Use of UAS. Available online: https://www.un.org/sc/ctc/wp-content/uploads/2019/05/CTED-UAS-Trends-Alert-Final_17_May_2019.pdf (accessed on 18 December 2019).
- Market Forecast, 2020 Counter Drone Market Worth USD 20 Billion. Available online: https://www.unmannedairspace.info/counter-uas-systems-and-policies/2020-counter-drone-market-worth-usd20-billion-says-market-forecast/ (accessed on 20 December 2019).
- Nassi, B.; Shabtai, A.; Masuoka, R.; Elovici, Y. SoK—Security and Privacy in the Age of Drones: Threats, Challenges, Solution Mechanisms and Scientific Gaps. Comput. Sci. Cryptogr. Secur. 2019, arXiv:1903.05155. [Google Scholar]
- Tezza, D.; Andujar, M. The State-of-the-Art of Human–Drone Interaction: A Survey. IEEE Access 2019, 7, 167438–167454. [Google Scholar] [CrossRef]
- Alsamhi, S.H.; Ma, O.; Ansari, M.S.; Almalki, F.A. Survey on Collaborative Smart Drones and Internet of Things for Improving Smartness of Smart Cities. IEEE Access 2019, 7, 128125–128152. [Google Scholar] [CrossRef]
- Calantropio, A. The Use of UAVs for Performing Safety-Related Tasks at Post-Disaster and Non-Critical Construction Sites. Safety 2019, 5, 64. [Google Scholar] [CrossRef]
- Solodov, A.; Williams, A.; Hanaei, S.; Goddard, B. Analyzing the Threat of Unmanned Aerial Vehicles to Nuclear Facilities, SAND 2017-3408J. Available online: https://www.osti.gov/pages/servlets/purl/1356834 (accessed on 18 October 2019).
- PARAS. Guidance for Integrating Unmanned Aircraft Systems (UAS) into Airport Security. May 2019. Available online: https://www.sskies.org/images/uploads/subpage/PARAS_0012.UASAirportSecurityIntegration.FinalGuidebook.pdf (accessed on 1 December 2019).
- U.S. Government Accountability Office (GAO 2018). Unmanned Aircraft Systems. Available online: https://www.gao.gov/key_issues/unmanned_aerial_systems/issue_summary (accessed on 2 December 2019).
- Altawy, R.; Youssef, A. Security, Privacy, and Safety Aspects of Civilian Drones: A Survey. ACM Trans. Cyber-Phys. Syst. 2016, 1, 1–25. [Google Scholar] [CrossRef]
- UK Dep. For Transport, Small Remotely Piloted Aircraft Systems (drones) Mid-Air Collision Study. July 2017. Available online: https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/628092/small-remotely-piloted-aircraft-systems-drones-mid-air-collision-study.pdf (accessed on 2 December 2019).
- Wild, G.; Murray, J.; Baxter, G. Exploring Civil Drone Accidents and Incidents to Help Prevent Potential Air Disasters. Aerospace 2016, 3, 22. [Google Scholar] [CrossRef]
- FAA, UAS Sightings Report, Public Records. 2019. Available online: https://www.faa.gov/uas/resources/public_records/uas_sightings_report/ (accessed on 22 January 2020).
- NASA. ASRS Database. Available online: https://asrs.arc.nasa.gov/search/database.html (accessed on 12 January 2020).
- Dedrone, Worldwide Drone Incidents. Available online: https://www.dedrone.com/resources/incidents/all (accessed on 22 December 2019).
- ASN. Aviation Safety Database. Available online: https://aviation-safety.net/database/ (accessed on 25 November 2019).
- UK Telegraph. Gatwick Drone Chaos Continues into a Third Day. Available online: https://www.telegraph.co.uk/news/2018/12/20/gatwick-chaos-drones-cause-flights-cancelled-live-updates/ (accessed on 2 December 2019).
- BBC News. Heathrow Airport: Drone Sighting Halts Departures. Available online: https://www.bbc.com/news/uk-46803713 (accessed on 22 December 2019).
- TheTelegraph. Dublin Airport Forced to Suspend All Flights due to Drone Sighting over Airfield. Available online: https://www.telegraph.co.uk/news/2019/02/21/dublin-airport-drone-sighting-airfield-suspends-flights/ (accessed on 4 December 2019).
- The Local, 143 Flights Cancelled at Frankfurt Airport due to Drone Sighting Incident. Available online: https://www.thelocal.de/20190509/disruption-after-frankfurt-airport-halts-flights-due-to-drone-sighting (accessed on 4 December 2019).
- Yu, E. ZDNet. Singapore Changi Airport Shuts Runway over Drone Sighting. Available online: https://www.zdnet.com/article/singapore-changi-airport-shuts-runway-over-drone-sighting/ (accessed on 2 December 2019).
- UAE. Dubai Airport Airspace Closed due to Unauthorized Drone Activity. Available online: https://www.thenational.ae/uae/dubai-airport-airspace-closed-due-to-unauthorised-drone-activity-1.200601 (accessed on 2 December 2019).
- Possible Drone Sighting Temporarily Closes Kansai International Airport. Available online: https://www.japantimes.co.jp/news/2019/10/19/national/possible-drone-sighting-temporarily-closes-kansai-international-airport/#.XhhCV_4zaUk (accessed on 2 December 2019).
- BBC News. Drone Collides with Commercial Airplane in Canada. Available online: https://www.bbc.com/news/technology-41635518 (accessed on 2 December 2019).
- The NewYork Times. Newark Airport Traffic Halted after Drone is Spotted. Available online: https://www.nytimes.com/2019/01/22/nyregion/drones-newark-airport-ground-stop.html (accessed on 2 December 2019).
- WCBS-TV. Drone Hits Army Helicopter Flying Over Staten Island. Available online: https://newyork.cbslocal.com/2017/09/22/drone-hits-army-helicopter/ (accessed on 2 December 2019).
- Bloomberg. South Carolina Cash Incident. Available online: https://www.bloomberg.com/news/articles/2018-02-16/what-may-be-first-drone-linked-copter-crash-being-investigated (accessed on 2 December 2019).
- FAA. Integration of Civil Unmanned Aircraft Systems (UAS) in the National Airspace System (NAS) Roadmap. Available online: https://www.faa.gov/uas/resources/policy_library/media/Second_Edition_Integration_of_Civil_UAS_NAS_Roadmap_July%202018.pdf (accessed on 1 December 2019).
- Google Scholar Search Engine for Academic Publications Containing “C-UAS” Term since 2014. Available online: https://scholar.google.gr/scholar?q=c-uas&hl=el&as_sdt=1%2C5&as_vis=1&as_ylo=2014&as_yhi=2020 (accessed on 30 April 2020).
- Stevens, M.; Atkins, E. Geofencing in Immediate Reaches Airspace for Unmanned Aircraft System Traffic Management. In Proceedings of the AIAA Information Systems-AIAA Infotech Aerospace, Kissimmee, FL, USA, 8–12 January 2018. [Google Scholar] [CrossRef]
- Hayhurst, K.; Maddalon, J.; Neogi, N.; Verstynen, H. Case Study for Assured Containment. In Proceedings of the International Conference on Unmanned Aircraft Systems (ICUAS), Denver, CO, USA, 9–12 June 2015. [Google Scholar]
- Stevens, M.; Coloe, B.; Atkins, E. Platform-Independent Geofencing for Low Altitude UAS Operations. In Proceedings of the 15th AIAA Aviation Technology, Integration, and Operations Conference, Dallas, TX, USA, 22–26 June 2015; p. 3329. [Google Scholar]
- Stevens, M.; Atkins, E. Multi-Mode Guidance for an Independent Multicopter Geofencing System. In Proceedings of the 16th AIAA Aviation Technology, Integration, and Operations Conference, Washington, DC, USA, 13–17 June 2016; p. 3150. [Google Scholar] [CrossRef]
- Zhu, G.; Wei, P. Low-Altitude UAS Traffic Coordination with Dynamic Geofencing. In Proceedings of the 16th AIAA Aviation Technology, Integration and Operations Conference, Washington, DC, USA, 13–17 June 2016; p. 3453. [Google Scholar] [CrossRef]
- DJI, Home, Online Webpage. 2016, pp. 4–6. Available online: https://www.dji.com/phantom-4/infohttp://www.dji.com/ (accessed on 14 December 2019).
- AISC. What Is Geofencing. Available online: https://www.aisc.aero/what-is-geofencing/ (accessed on 12 December 2019).
- DJI Enhances Geofencing Technology to Protect Airports. Available online: https://www.dji.com/ae/newsroom/news/dji-improves-geofencing-to-enhance-protection-of-european-airports-and-facilities (accessed on 4 December 2019).
- Skolnik, I.M. Radar Handbook, 2nd ed.; McGraw-Hill Education: New York, NY, USA, 1990; Available online: http://www.geo.uzh.ch/microsite/rsl-documents/research/SARlab/GMTILiterature/PDF/Skolnik90.pdf (accessed on 30 April 2020).
- Drozdowicz, J.; Wielgo, M.; Samczynski, P.; Kulpa, K.; Krzonkalla, J.; Mordzonek, M.; Bryl, M.; Jakielaszek, Z. 35GHz FMCW drone detection system, in Radar Symposium (IRS). In Proceedings of the 2016 17th International, Krakow, Poland, 10–12 May 2016; IEEE: Krakow, Poland, 2016; pp. 1–4. Available online: https://www.semanticscholar.org/paper/35-GHz-FMCW-drone-detection-system-Drozdowicz-Wielgo/2bccc966a48db74b3cb73887187dcf5f3ed3ad03 (accessed on 30 April 2020).
- Haag, M.; Bartone, C.; Braasch, M. Flight-test evaluation of small form-factor Lidar and Radar sensors for sUAS detect-and avoid applications. In Proceedings of the Digital Avionics Systems Conference (DASC), 35th IEEE/AIAA, Sacramento, CA, USA, 25–29 September 2016; pp. 1–11. [Google Scholar]
- Samaras, S.; Diamantidou, E.; Ataloglou, D.; Sakellariou, N.; Vafeiadis, A.; Magoulianitis, V.; Lalas, A.; Dimou, A.; Zarpalas, D.; Votis, K.; et al. Deep Learning on Multi Sensor Data for Counter UAV Applications—A Systematic Review. Sensors 2019, 19, 4837. Available online: https://www.mdpi.com/1424-8220/19/22/4837dl40 (accessed on 30 April 2020). [CrossRef]
- Wit, J.M.; Harmanny, R.; Premel-Cabic, G. Micro-Doppler analysis of small UAVs. In Proceedings of the 2012 9th European Radar Conference, Amsterdam, The Netherlands, 31 October–2 November 2012; pp. 210–213. [Google Scholar]
- Harmanny, R.; De Wit, J.; Cabic, G. Radar micro-Doppler feature extraction using the spectrogram and the cepstrogram. In Proceedings of the 2014 11th European Radar Conference, Rome, Italy, 8–10 October 2014; pp. 165–168. [Google Scholar]
- Ritchie, M.; Fioranelli, F.; Griffiths, H.; Torvik, B. Micro-drone RCS analysis. In Proceedings of the 2015 IEEE Radar Conference, Johannesburg, South Africa, 27–30 October 2015; pp. 452–456. [Google Scholar]
- Molchanov, P.; Harmanny, R.I.; de Wit, J.J.; Egiazarian, K.; Astola, J. Classification of small UAVs and birds by micro-Doppler signatures. Int. J. Microw. Wirel. Technol. 2014, 6, 435–444. [Google Scholar] [CrossRef]
- Fioranelli, F.; Ritchie, M.; Griffiths, H.; Borrion, H. Classification of loaded/unloaded micro-drones using multistatic radar. Electron. Lett. 2015, 51, 1813–1815. [Google Scholar] [CrossRef]
- Hoffmann, F.; Ritchie, M.; Fioranelli, F.; Charlish, A.; Griffiths, H. Micro-Doppler based detection and tracking of UAV with multistatic radar. In Proceedings of the 2016 IEEE Radar Conference (RadarConf), Philadelphia, PA, USA, 2–6 May 2016; pp. 1–6. [Google Scholar]
- Zhang, P.; Yang, L.; Chen, G.; Li, G. Classification of drones based on micro-Doppler signatures with dual-band radar sensors. In Proceedings of the 2017 Progress in Electromagnetics Research Symposium-Fall (PIERS-FALL), Singapore, 19–22 November 2017; pp. 638–643. [Google Scholar]
- Knott, E.; Schaeffer, J.; Tulley, M. Radar Cross Section; SciTech Publishing: New York, NY, USA, 2004. [Google Scholar]
- Michel, A. Counter Drone Systems, 2nd ed.; Center for the Study of the Drone at Bard College: New York, NY, USA, 2019; Available online: https://dronecenter.bard.edu/files/2019/12/CSD-CUAS-2nd-Edition-Web.pdf (accessed on 30 April 2020).
- Joint Air Power Competence Centre. A Comprehensive Approach to Countering Unmanned Aircraft Systems. Available online: https://www.japcc.org/portfolio/a-comprehensive-approach-to-countering-unmanned-aircraft-systems/ (accessed on 1 December 2019).
- MyDefence, Communication White Paper, Protecting Airports against Drones. Available online: https://mydefence.dk/2019/02/mydefence-publishes-white-paper-on-airport-drone-protection/ (accessed on 4 December 2019).
- Birnbach, S.; Baker, R.; Martinovic, I. Wi-fly: Detecting Privacy Invasion Attacks by Consumer Drones; NDSS: New York, NY, USA, 2017. [Google Scholar]
- Nguyen, P.; Truong, H.; Ravindranathan, M.; Nguyen, A.; Han, R.; Vu, T. Matthan: Drone presence detection by identifying physical signatures in the drone’rf communication. In Proceedings of the 15th Annual International Conference on Mobile Systems, Applications, and Services, Niagara Falls, NY, USA, 19–23 June 2017; pp. 211–224. [Google Scholar]
- Nguyen, P.; Truong, H.; Ravindranathan, M.; Nguyen, A.; Han, R.; Vu, T. Cost-effective and passive rf-based drone presence detection and characterization. GetMob. Mob. Comput. Commun. 2018, 21, 30–34. [Google Scholar] [CrossRef]
- Nguyen, P.; Ravindranatha, M.; Nguyen, A.; Han, R.; Vu, T. Investigating cost-effective rf-based detection of drones. In Proceedings of the 2nd Workshop on Micro Aerial Vehicle Networks, Systems, and Applications for Civilian Use, ACM MobiSys 2016, Singapore, 26 June 2016; pp. 17–22. [Google Scholar]
- Scheller, Waylon Dustin, Detecting Drones Using Machine Learning, IOWA Graduate Theses and Dissertations. 2017. Available online: https://lib.dr.iastate.edu/etd/16210 (accessed on 4 December 2019).
- Shi, Z.; Huang, M.; Zhao, C.; Huang, L.; Du, X.; Zhao, F. Detection of LSS UAV using hash fingerprint based SVDD. In Proceedings of the 2017 IEEE International Conference on IEEE, Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–5. [Google Scholar]
- Peacock, M.; Johnstone, M.N. Towards Detection and Control of Civilian Unmanned Aerial Vehicles. 2013. Available online: https://ro.ecu.edu.au/cgi/viewcontent.cgi?article=1051&context=isw (accessed on 30 April 2020).
- Mototolea, D.; Stolk, C. Detection and localization of small drones using commercial off-the-shelf FPGA based software defined radio systems. In Proceedings of the International Conference on Communications (COMM), Bucharest, Romania, 14–16 June 2018; pp. 465–470. [Google Scholar]
- Blue Ribbon Task Force on UAS Mitigation at Airports, Interim Report. July 2019. Available online: https://uasmitigationatairports.org/wp-content/uploads/2019/07/BRTF-Report-New-2.pdf (accessed on 30 April 2020).
- Chang, X.; Yang, C.; Wu, J.; Shi, X.; Shi, Z. A surveillance system for drone localization and tracking using acoustic arrays. In Proceedings of the IEEE 10th Sensor Array and Multichannel Signal Processing Workshop, Sheffield, UK, 8–11 July 2018; 2018; pp. 573–577. [Google Scholar]
- Sedunov, A.; Sutin, A.; Sedunov, N.; Salloum, H.; Yakubovskiy, A.; Masters, D. Passive acoustic system for tracking low-flying aircraft. IET Rada Sonar Navig. 2016, 10, 1561–1568. [Google Scholar] [CrossRef]
- Chowdhury, A. Implementation and Performance Evaluation of Acoustic Denoising Algorithms for UAV. Master’s Thesis, University of Nevada, Reno, NV, USA, 2016. [Google Scholar]
- Mezei, J.; Molnár, A. Drone sound detection by correlation. In Proceedings of the 2016 IEEE 11th International Symposium on Applied Computational Intelligence and Informatics (SACI), Timisoara, Romania, 12–14 May 2016; pp. 509–518. [Google Scholar]
- Bernardini, A.; Mangiatordi, F.; Pallotti, E.; Capodiferro, L. Drone detection by acoustic signature identification. Electron. Imaging 2017, 2017, 60–64. [Google Scholar] [CrossRef]
- Mirelli, V.; Tenney, S.; Bengio, Y.; Chapados, N.; Delalleau, O. Statistical machine learning algorithms for target classification from acoustic signature. Proc. MSS Battlespace Acoust. Magn. Sens. 2009. Available online: http://www.iro.umontreal.ca/~lisa/pointeurs/mss_ml_classif.pdf (accessed on 30 April 2020).
- Kim, J.; Park, C.; Ahn, J.; Ko, Y.; Park, J.; Gallagher, J.C. Real-time UAV sound detection and analysis system. In Proceedings of the 2017 IEEE Sensors Applications Symposium (SAS), Glassboro, NJ, USA, 13–15 March 2017; pp. 1–5. [Google Scholar]
- Salamon, J.; Jacoby, C.; Bello, J.P. A dataset and taxonomy for urban sound research. In Proceedings of the 22nd ACM International Conference on Multimedia, New York, NY, USA, 3–7 November 2014; pp. 1041–1044. [Google Scholar]
- Jeon, S.; Shin, J.; Lee, Y.; Kim, W.; Kwon, Y.; Yang, H. Empirical study of drone sound detection in real-life environment with deep neural networks. In Proceedings of the 2017 25th European Signal Processing Conference (EUSIPCO), Kos, Greece, 28 August–2 September 2017; pp. 1858–1862. [Google Scholar]
- Park, S.; Shin, S.; Kim, Y.; Matson, E.T.; Lee, K.; Kolodzy, P.J.; Slater, J.C.; Scherreik, M.; Sam, M.; Gallagher, J.C.; et al. Combination of radar and audio sensors for identification of rotor-type unmanned aerial vehicles (uavs). In Proceedings of the 2015 IEEE SENSORS, Busan, Korea, 1–4 November 2015; pp. 1–4. [Google Scholar]
- Hu, S.; Goldman, G.; Borel-Donohue, C. Detection of unmanned aerial vehicles using a visible camera system. Appl. Opt. 2017, 56, B214–B221. [Google Scholar] [CrossRef]
- Rozantsev, A.; Lepetit, V.; Fua, P. Flying objects detection from a single moving camera. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Boston, MA, USA, 7–12 June 2015; pp. 4128–4136. [Google Scholar]
- Santana, L.; Brandao, A.; Sarcinelli-Filho, M.; Carelli, R. A trajectory tracking and 3d positioning controller for the ar. Drone quadrotor. In Proceedings of the Unmanned Aircraft Systems (ICUAS), International Conference on IEEE, Orlando, FL, USA, 27–30 May 2014; pp. 756–767. [Google Scholar]
- Unlu, E.; Zenou, E.; Rivière, N. Using shape descriptors for UAV detection. Electron. Imaging 2018, 2018, 1–5. [Google Scholar] [CrossRef]
- Saqib, M.; Khan, S.; Sharma, N.; Blumenstein, M. A study on detecting drones using deep convolutional neural networks. In Proceedings of the 14th IEEE International Conference on Advanced Video and Signal Based Surveillance (AVSS), Lecce, Italy, 29 August–1 September 2017; pp. 1–5. [Google Scholar]
- Aker, C.; Kalkan, S. Using Deep Networks for Drone Detection. arXiv 2017, arXiv:1706.05726. [Google Scholar]
- Unlu, E.; Zenou, E.; Rivière, N. Generic Fourier descriptors for autonomous UAV detection. In Proceedings of the 7th International Conference on Pattern Recognition Applications and Methods (ICPRAM2018), Funchal, Madeira, Portugal, 16–18 January 2018; pp. 550–554. [Google Scholar] [CrossRef]
- Rozantsev, A.; Sinha, S.; Dey, D.; Fua, P. Flight dynamics-based recovery of a UAV trajectory using ground cameras. In Proceedings of the Conference Computer Vision and Pattern Recognition, Honolulu, HI, USA, 21–26 July 2017. [Google Scholar]
- Opromolla, R.; Fasano, G.; Accardo, D. A Vision-Based Approach to UAV Detection and Tracking in Cooperative Applications. Sensors 2018, 18, 3391. [Google Scholar] [CrossRef]
- Gökçe, F.; Üçoluk, G.; ¸Sahin, E.; Kalkan, S. Vision-based detection and distance estimation of micro unmanned aerial vehicles. Sensors 2015, 15, 23805–23846. [Google Scholar] [CrossRef]
- Freitas, S.; Silva, H.; Almeida, J.; Silva, E. Hyperspectral imaging for real-time unmanned aerial vehicle maritime target detection. J. Intell. Robot. Syst. 2018, 90, 551–570. [Google Scholar] [CrossRef]
- Pham, T.; Takalkar, M.; Xu, M.; Hoang, D.; Truong, H.; Dutkiewicz, E.; Perry, S. Airborne Object Detection Using Hyperspectral Imaging: Deep Learning Review. In Proceedings of the International Conference on Computational Science and Its Applications, Saint Petersburg, Russia, 1–4 July 2019; pp. 306–321. [Google Scholar]
- Müller, T. Robust drone detection for day/night counter-UAV with static VIS and SWIR cameras. In Proceedings of the Ground/Air Multisensor Interoperability, Integration, and Networking for Persistent ISR VIII, International Society for Optics and Photonics, Anaheim, CA, USA, 4 May 2017; Volume 10190, p. 1019018. [Google Scholar]
- Birch, G.C.; Woo, B.L. Counter unmanned aerial systems testing: Evaluation of VIS SWIR MWIR and LWIR passive imagers. Sandia Rep. 2017. [Google Scholar] [CrossRef]
- Thomas, A.; Cotinat, A.; Gilber, M. UAV localization using panoramic thermal cameras. In Proceedings of the 12th International Conference on Computer Vision Systems (ICVS), Thessaloniki, Greece, 23–25 September 2019. [Google Scholar]
- Church, P.; Grebe, C.; Matheson, J.; Owens, B. Aerial and surface security applications using Lidar. In Proceedings of the Laser Radar Technology and Applications XXIII, International Society for Optics and Photonics, Orlando, FL, USA, 17–18 April 2018; Volume 10636, p. 1063604. [Google Scholar]
- FAA. Unmanned Aircraft System Traffic Management (UTM). Available online: https://www.faa.gov/uas/research_development/traffic_management/ (accessed on 20 February 2020).
- Luo, A. Drones hijacking—multi-dimensional attack vectors and countermeasures. Presented at the DEF CON 24 Conference, Las Vegas, NV, USA, 4–7 August 2016; Available online: https://www.youtube.com/watch?v=R6RZ5KqSVcg (accessed on 30 April 2019).
- Robinson, M. Knocking My Neighbors Kids Cruddy Drone Offline. DEF CON 23. Available online: https://academic.csuohio.edu/yuc/mobile/GPS-Knocking-My-Neighbors-Kid-Drone-compressed.pdf (accessed on 30 March 2020).
- Rodday, N. Hacking a professional drone. In Proceedings of the Black Hat ASIA 2016, Singapore, 29 March–1 April 2016; Available online: https://www.blackhat.com/docs/asia-16/materials/asia-16-Rodday-Hacking-A-Professional-Drone.pdf (accessed on 30 March 2020).
- Highnam, K.; Angstadt, K.; Leach, K.; Weimer, W.; Paulos, A.; Hurley, P. An uncrewed aerial vehicle attack scenario and trustworthy repair architecture. In Proceedings of the 46th Annual IEEE/IFIP International Conference on Dependable Systems and Networks Workshop (DSN-W), Toulouse, France, 28 June–1 July 2016; pp. 222–225. [Google Scholar]
- Davidson, D.; Wu, H.; Jellinek, R.; Singh, V.; Ristenpart, T. Controlling UAVs with sensor input spoofing attacks. In Proceedings of the 10th USENIX Workshop on Offensive Technologies (WOOT), Austin, TX, USA, 8–9 August 2016; Available online: https://www.usenix.org/system/files/conference/woot16/woot16-paper-davidson.pdf (accessed on 30 March 2020).
- Kerns, A.; Shepard, D.; Bhatti, J.; Humphreys, T. Unmanned aircraft capture and control via GPS spoofing. J. Field Robot. 2014, 31, 617–636. [Google Scholar] [CrossRef]
- Feng, Z.; Guan, N.; Lv, M.; Liu, W.; Deng, Q.; Liu, X.; Yi, W. Efficient drone hijacking detection using onboard motion sensors. In Proceedings of the Design, Automation & Test in Europe Conference & Exhibition (DATE), Lausanne, Switzerland, 27–31 March 2017; pp. 1414–1419. [Google Scholar]
- Tippenhauer, N.; Pöpper, C.; Rasmussen, K.; Capkun, S. On the requirements for successful GPS spoofing attacks. In Proceedings of the 18th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 17–21 October 2011; pp. 75–86. Available online: https://doi.org/10.1145/2046707.2046719 (accessed on 30 March 2020).
- Vervisch-Picois, A.; Samama, N.; Taillandier-Loize, T. Influence of GNSS spoofing on drone in automatic flight model. In Proceedings of the ITSNT 2017: 4th International Symposium of Navigation and Timing. Ecole Nationale de L’aviation Civile (ENAC), Toulouse, France, 14–17 November 2017; pp. 1–9. [Google Scholar]
- He, D.; Qiao, Y.; Chen, S.; Du, X.; Chen, W.; Zhu, S.; Guizani, M. A friendly and low-cost technique for capturing non-cooperative civilian unmanned aerial vehicles. IEEE Netw. 2018, 33, 146–151. [Google Scholar] [CrossRef]
- Humphreys, T.E. Statement on the Vulnerability of Civil Unmanned Aerial Vehicles and Other Systems to Civil GPS Spoofing. Available online: http://homeland.house.gov/sites/homeland.house.gov/files/Testimony-Humphreys.pdf (accessed on 30 April 2020).
- Mitch, R.; Dougherty, R.; Psiaki, M.; Powell, S.P.; O’Hanlon, B.W. Signal Characteristics of Civil GPS Jammers. Radionavigation Laboratory Conference Proceedings. 2011. Available online: https://repositories.lib.utexas.edu/bitstream/handle/2152/63304/Signal%20Characteristics%20Civil%20GPS%20Jammers_Mitch.pdf?sequence=2 (accessed on 30 April 2020).
- U.S. Dept. of Homeland Security, Science and Technology Directorate; National Urban Security Technology Laboratory (NUSTL). Counter-Unmanned Aircraft Systems Technology Guide. September 2019. Available online: https://www.dhs.gov/sites/default/files/publications/c-uas-tech-guide_final_28feb2020.pdf (accessed on 30 April 2020).
- Michel, A. Counter-Drone Systems, 1st ed.; Center for the Study of the Drone at Bard College: New York, NY, USA, 2018; Available online: https://dronecenter.bard.edu/files/2018/02/CSD-Counter-Drone-Systems-Report.pdf (accessed on 30 April 2020).
- Unmanned Airspace Information Portal, Counter-UAS Industry Directory. Available online: https://www.unmannedairspace.info/counter-uas-industry-directory/ (accessed on 30 April 2020).
- Lykou, G.; Anagnostopoulou, A.; Gritzalis, D. Smart Airports Cybersecurity: Threat Mitigation and Cyber Resilience, SENSORS. 2019. Available online: https://www.mdpi.com/1424-8220/19/1/19 (accessed on 30 April 2020).
- Lykou, G.; Anagnostopoulou, A.; Gritzalis, D. Implementing cyber-security measures in airports to improve cyber-resilience. In Proceedings of the Workshop on Industrial Internet of Things Security (WIIoTS-2018), Bilbao, Spain, 4–7 June 2018. [Google Scholar]
- Lykou, G.; Iakovakis, G.; Gritzalis, D. Aviation Cybersecurity and Cyber-Resilience: Assessing Risk in Air Traffic Management. In Critical Infrastructure Security and Resilience; Advanced Sciences and Technologies for Security Applications; Gritzalis, D., Theoharidou, M., Stergiopoulos, G., Eds.; Springer Nature: Cham, Switzerland, 2019; pp. 245–260. ISBN 978-3-030-00024-0. [Google Scholar]
- Business Standard, Houthi says it targeted Saudi Arabia’s Abha Airport with Drone Attack. Available online: https://www.business-standard.com/article/news-ani/houthi-says-it-targeted-saudi-arabia-s-abha-airport-with-drone-attack-119072900175_1.html (accessed on 2 December 2019).
- The Guardian, Middle East Drones Signal End to era of Fast jet air Supremacy. Available online: https://www.theguardian.com/world/2019/sep/16/middle-east-drones-signal-end-to-era-of-fast-jet-air-supremacy (accessed on 4 December 2019).
- ICAO, Annex 10, Aeronautical Telecommunications. Available online: https://store.icao.int/collections/annex-10-aeronautical-telecommunications (accessed on 30 April 2020).
- SESAR JU, Addressing Airport Cyber-Security. Available online: https://www.sesarju.eu/sites/default/files/documents/news/Addressing_airport_cyber-security_Full_0.pdf (accessed on 4 December 2019).
- Lupu, T.G.; Rudas, I.; Demiralp, M.; Mastorakis, N. Main Types of Attacks in Wireless Sensor Networks. WSEAS International Conference. Recent Advances in Computer Engineering (No. 9). September 2009. Available online: http://www.wseas.us/e-library/conferences/2009/budapest/MIV-SSIP/MIV-SSIP31.pdf (accessed on 4 December 2019).
- Wilkinson, G. Digital Terrestrial Tracking: The Future of Surveillance. DEFCON, 22. Available online: https://pdfs.semanticscholar.org/07a5/08ddd6cc3eadd1f0743e7acf8a38db467703.pdf (accessed on 4 December 2019).
- Gittleson, K. Data-Stealing Snoopy Drone Unveiled at Black Hat. BBC News. Available online: https://www.bbc.com/news/technology-26762198 (accessed on 4 December 2019).
- Karanam, C.; Mostofi, Y. 3D Through-Wall Imaging with Unmanned Aerial Vehicles Using WiFi. Available online: https://www.ece.ucsb.edu/~ymostofi/papers/IPSN17_KaranamMostofi.pdf (accessed on 20 December 2019).
- Guri, M.; Zadov, B.; Elovici, Y. Led-it-Go: LEAKING (a lot of) Data from Air-Gapped Computers via the (Small) Hard Drive Led. In International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment; Springer: Berlin/Heidelberg, Germany, 2017; pp. 161–184. [Google Scholar]
- Kleiner, A.; Prediger, J.; Nebel, B. RFID Technology-based Exploration and SLAM for Search and Rescue. In Proceedings of the RSJ International Conference on Intelligent Robots and Systems, Beijing, China, 9–15 October 2006; pp. 4054–4059. Available online: https://ieeexplore.ieee.org/abstract/document/4059043 (accessed on 15 November 2019).
- Magnabosco, M.; Breckon, T.P. Cross-Spectral Visual Simultaneous Localization And Mapping (SLAM) with Sensor Handover. Rob. Auton. Syst. 2013, 63, 195–208. [Google Scholar] [CrossRef]
- Karlsson, N.; Di Bernardo, E.; Ostrowski, J.; Goncalves, L.; Pirjanian, P.; Munich, M.E. The vSLAM Algorithm for Robust Localization and Mapping. In Proceedings of the 2005 IEEE International Conference on Robotics and Automation, Barcelona, Spain, 18–22 April 2005. [Google Scholar]
- Moore, J. Drone de-Confliction Advances ADS-B for UAS Benefits All Airspace Users, AOPA. May 2019. Available online: https://www.aopa.org/news-and-media/all-news/2019/may/22/drone-deconfliction-advances (accessed on 18 October 2019).
- Costin, A.; Francillon, A. Ghost in the Air(Traffic): On Insecurity of ADS-B Protocol and Practical Attacks on ADS-B Devices. Available online: https://www.researchgate.net/publication/267557712_Ghost_in_the_AirTraffic_On_insecurity_of_ADS-B_protocol_and_practical_attacks_on_ADS-B_devices (accessed on 12 October 2019).
- Mohsen, M.; Kaabouch, N. Analysis of vulnerabilities, attacks, countermeasures and overall risk of the Automatic Dependent Surveillance-Broadcast (ADS-B) system. Int. J. Crit. Infrastruct. Prot. 2017, 19, 16–31. [Google Scholar]
- Santamarta, R. Last Call for SATCOM Security; White Paper; IOActive, Inc.: Seattle, WA, USA, 2018; Available online: https://ioactive.com/wp-content/uploads/2018/08/us-18-Santamarta-Last-Call-For-Satcom-Security-wp.pdf (accessed on 12 October 2019).
- FAA. Letter from FAA Office of Airports on Guidance on Use of Counter UAS Systems at Airports. July 2018. Available online: https://www.faa.gov/airports/airport_safety/media/attachment-1-counter-uas-airport-sponsor-letter-july-2018.pdf (accessed on 10 December 2019).
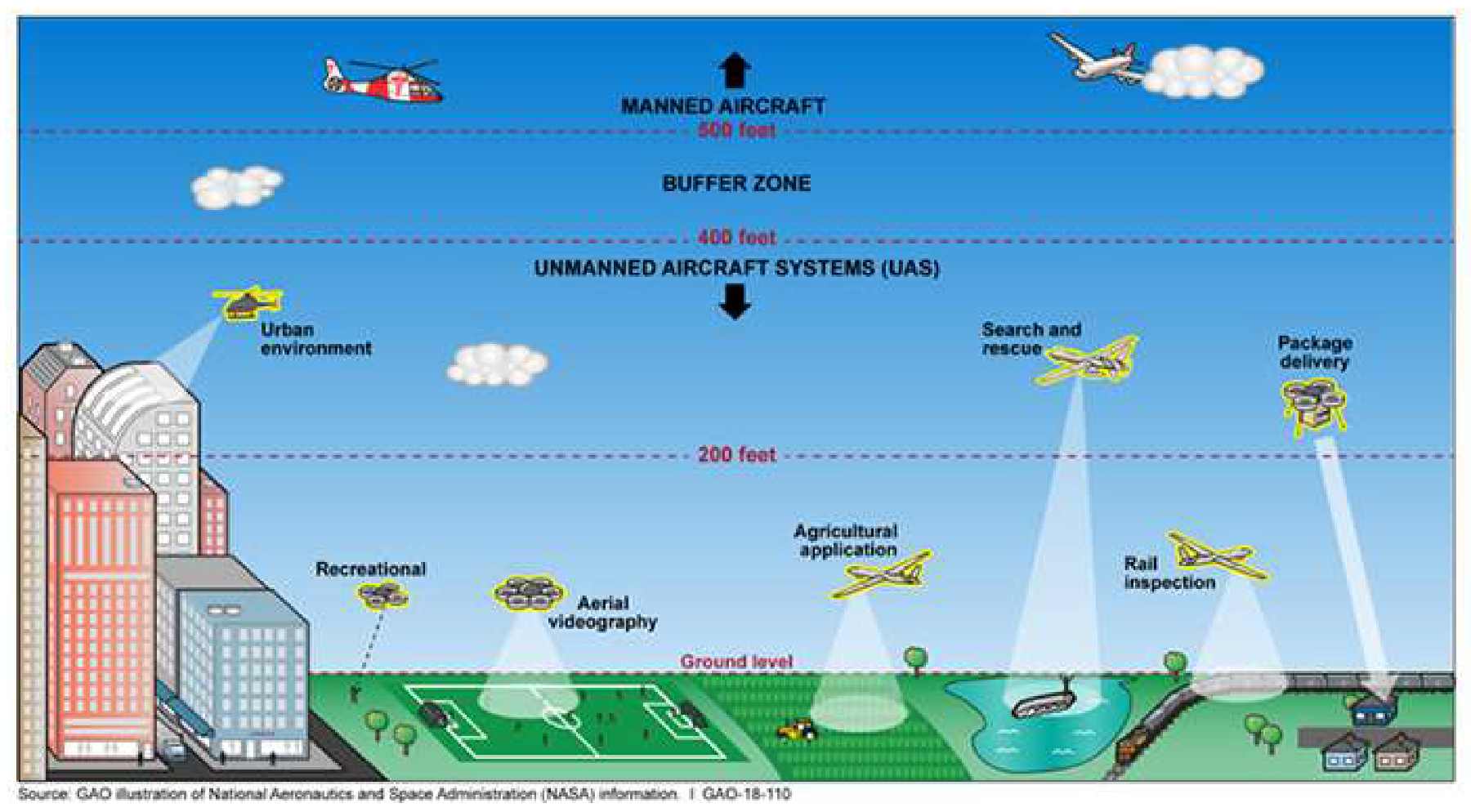
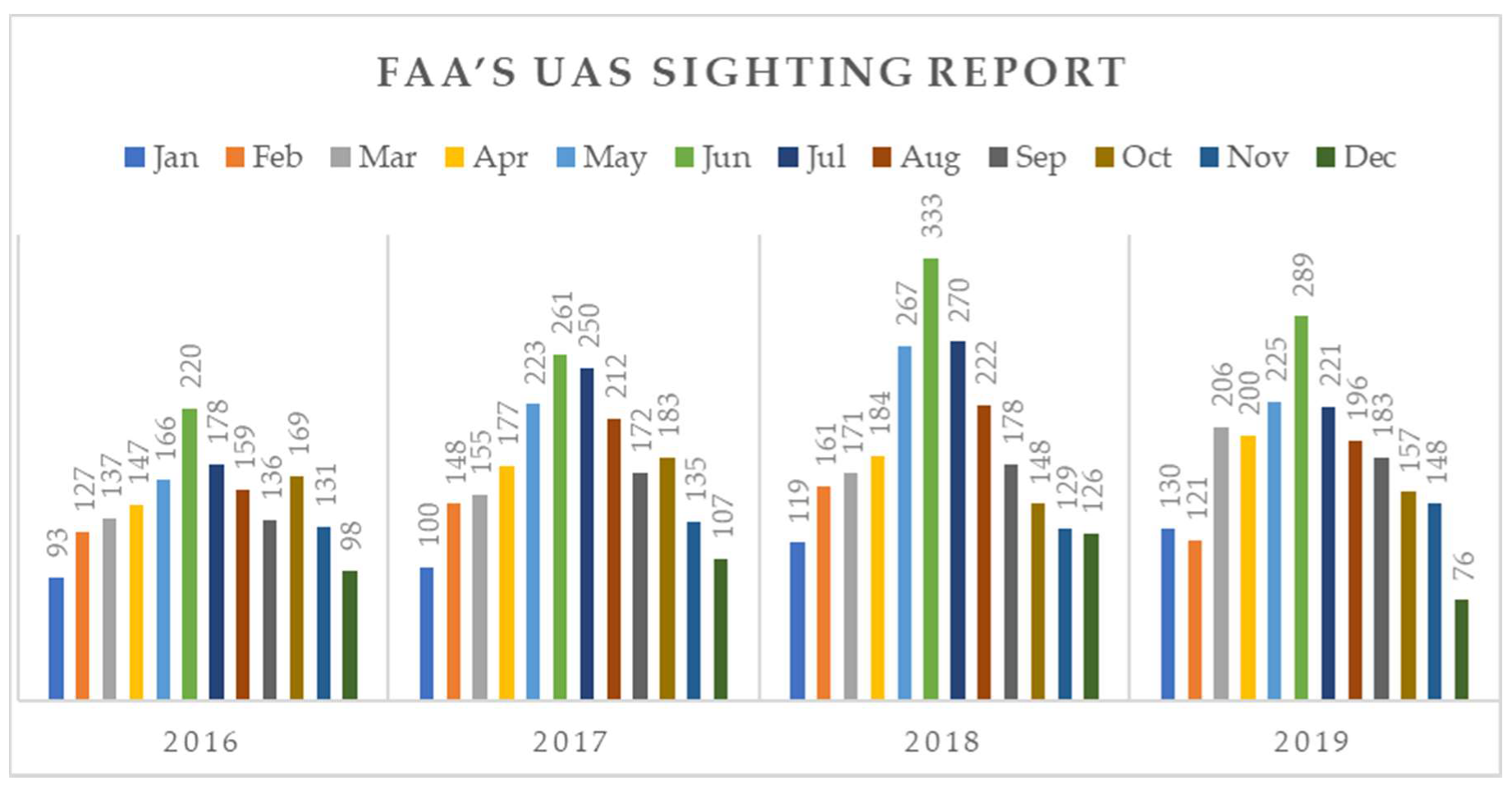
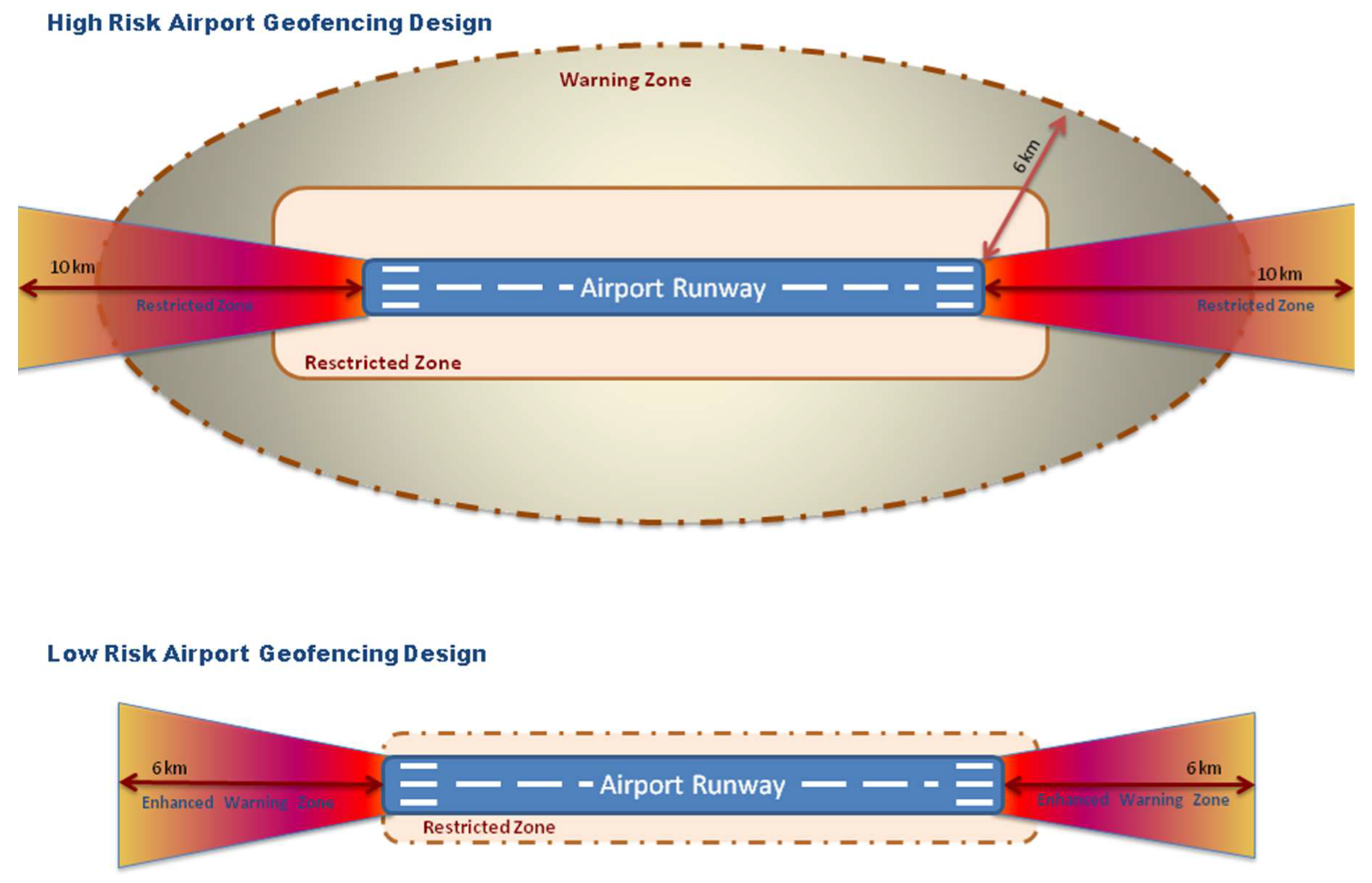




| Category | NASA UAS Class | Weight (in kg) | Normal Operating Altitude (in m) | Mission Radius, Range (in Km) | Typical Endurance (in hrs) | Payload (in kg) | Available UAV Models in Market |
|---|---|---|---|---|---|---|---|
| Micro | sUAS Class I | <2 | <140 | 5 | <1 | <1 | DJI Spark, DJI Mavic, Parrot Bebop2 |
| Mini | 2–25 | <1000 | 25 | 2–8 | <10 | DJI Matrice600, DJI Inspire2, Airborne Vanguard | |
| Small | 25–150 | <1700 | 50 | 4–12 | <50 | AAI Shadow 200, Scorpion 3 Hoverbike | |
| Medium | Class II | 150–600 | <3300 | 200–500 | 8–20 | <200 | Griff 300, Ehang 216 |
| Large/Tactical | Class III | >600 | >3300 | >1000 | >20 | >200 | Boeing X-45A UCAV |
| Year | 2014 | 2015 | 2016 | 2017 | 2018 | 2019 |
|---|---|---|---|---|---|---|
| Num. of Scientific Publications | 99 | 124 | 134 | 182 | 178 | 234 |
| Method | Benefits | Limitations |
|---|---|---|
| Radar | Long-range primary surveillance detection system up to 100 km, depending on RCS and altitude | Detection range dependent on drone size and radar cross-section (RCS) |
| Radar systems designed for manned aviation cannot detect small flying objects | ||
| Can track most drone types, regardless of autonomous flight | High acquisition and installation cost | |
| When combined with machine learning algorithms, can distinguish birds from drones. | Requires a transmission license and frequency check to prevent interference with other RF transmissions | |
| High-accuracy tracking while in angle range of observation | Hard to detect low-altitude-flying, slow-moving or hovering UAVs | |
| Able to track multiple targets simultaneously when using multi- tracking coverage | No pilot tracking capability or ground control geolocation | |
| Bistatic and multi-static radars increase accuracy of UAV detection | Lack of automation and high dependence on trained radar operators | |
| Independent of visual conditions (day, night, overcast weather, etc.) | False positives with similarly shaped objects (birds, clouds, etc.) | |
| No need for RF or acoustic signal | Environmental compatibility study is needed | |
| RF detection | Lower cost than radar sensors with a medium range up to 600 m | RF signal required, cannot detect autonomous flying drones |
| Detects certain radio frequency bands where UAVs and GCS communicate for command and control (C2) | Electromagnetic interference and loss of sight degrades detection capabilities | |
| Can capture RF emitted by UAVs and is able to locate UAVs and controllers | Variable detection accuracy depending on drone type and frequency band | |
| Can capture WiFi-emitting drones | Attacker can spoof MAC addresses | |
| High-accurancy detection | Can detect only a few UAVs at a time | |
| Early warning capability even before UAV takes-off (when turned on) | Less effective in heavy-RF environments with a range less than 100 m | |
| Triangulation is possible with multiple RF sensors | Detection limitations for swarm of drones | |
| Machine learning algorithms can classify drone transmissions | Some passive systems may emit RF signals, despite being characterized as passive systems | |
| Passive detection, no license required | ||
| Acoustic | Classification based on acoustic signature | Depends on an available library of already-captured sound signatures |
| Can differentiate between authorized and unauthorized UAS | Higher false positives due to the increasing number of drone models | |
| No need for RF signal for detection. Can detect autonomous flying UAVs | Unreliable detection at range >300 m | |
| UAV detection can extend beyond line of sight | Does not work as well in noisy environments | |
| Classification based on UAVs’ acoustic signatures | Detection limitations for swarms of drones | |
| Time difference of arrival (TDOA) technique is used for UAV localization while triangulation is possible with an array of distributed sensors | Detection performance is affected by wind direction, temperature, line of sight and signal reflections due to obstacles | |
| Low-cost sensors | Not used as a primary detection source | |
| Can provide drone direction or rough estimation | No pilot tracking capability or ground control geolocation | |
| Visual | Detects visual signature for electro-optical (EO) cameras to classify UAVs | Need for human interference or artificial intelligence to efficiently detect UAVs |
| Detects heat signature infrared spectrum for thermal (IR) cameras | Not used as a primary detection source (both EO and IR cameras) | |
| Can distinguish drones from birds, especially with IR sensors | Both have detection limitations based on resolution capabilities Hard to capture swarms of drones | |
| No need for an RF signal emitted by UAVs to capture | IR and EO cameras need a direct line of sight to detect UAVs | |
| IR cameras visualize surrounding environments, regardless of the external lighting or weather conditions and even in total darkness | EO Cameras depend on daylight and outdoor illuminance conditions (overcast, darkness, etc.) | |
| Can record sightings and use for further investigation | May confuse UAV with a bird or similarly shaped small airplane | |
| Can record incidents as forensic evidence for legal actions | Range limitations depending on weather conditions (clouds, rain, fog, mist, etc.) |
| Method | Benefits | Limitations | |
|---|---|---|---|
| Electronic Interdiction/Signal Jamming | RF Jamming | Use RF transmission to block signals and disrupt C2 between the GSC operator and UAV | RF interference in crowded RF areas. May also jam and interrupt other communication signals |
| Medium range up to a few kilometers, depending on emitting power | Cannot affect autonomous driven drones (without an active RF link) | ||
| Static, mobile, or handheld device | Illegal use in many countries | ||
| Programmable based on RF sensor scanning | May cause uncontrolled UAV flights and crashes | ||
| Disrupts radio-frequency (RF) communication link sCan include WiFi links | Needs special licensing for approved use, based on electromagnetic compatibility regulations | ||
| Use of directional jamming to minimize interfering | A jammer’s ability relies on the strength of its radio transmitter | ||
| GPS Jamming | Replaces GPS communication, increases difficulty to control the drone | Cannot work if UAVs disable GPS or use encrypted GPS (military mission) | |
| Medium to short range, depending on satellite constellation | Dangerous when used near airports, because airplanes also use satellite navigation | ||
| Disrupts Global Positioning Satellite communication link | Illegal procedure in many countries. Needs special licensing for approved use | ||
| Prevents the return-to-home functionality | May cause uncontrolled UAV flights and crashes | ||
| Protocol Manupulation | Replaces the communication link and takes control of drone operation | Illegal procedure for civilian use, acts against computer fraud and abuse | |
| Employs algorithms enhanced with artificial intelligence | Not always successful, especially when encryption is used for C2 links | ||
| Can drive a malicious UAV to a designated area | Complicated method, not always successful | ||
| Low-cost technique, based on attackers’ ability | Cannot affect autonomous driven UAVs not using GPS | ||
| Kinetic Physical | UAV Net Capturing or Birds of Prey | Active and aggressive countermeasures | May cause collateral fatalities to other aircrafts. Not appropriate for airports |
| Net capturing: enforced and hardened UAVs physically capture a drone | Net capturing efficiency depends on UAVs’ flight behavior, reaction time etc. | ||
| Birds of prey are used to attack and grab UAS | Birds also pose hazards when flying around airports | ||
| Captures and drives UAVs in a specific area. | Depends on speed or maneuvering capabilities of rogue UAVs | ||
| Kinetic Electronic | High Power Microwave or Laser Guns | Aggressive and long-range countermeasures | Can have negative effects on other passing aircrafts with fatal consequences |
| Destroys electronic systems of UAVs | May cause uncontrolled UAV flights and crashes | ||
| Disables drone flight | Illegal in civil aviation contexts. Violates aviation security laws | ||
| Number of C-UAS Products | 545 | % |
|---|---|---|
| Systems Capable of Detection | 178 | 33% |
| Systems Capable of Mitigation (Interdiction) | 218 | 40% |
| Systems Capable of Both Detection and Mitigation | 149 | 27% |
| Threat/Hazard | Impacted Assets | Impact Analysis | ||
|---|---|---|---|---|
| Description and Impact Areas (*) | on CIA (**) | |||
| Spying aeronautical CNS systems for vulnerabilities and information gathering | Air traffic management, communication, surveillance and navigation (CNS) systems, such as:
| Site and system vulnerabilities exposure | R, L | C |
| Drone equipped with a radio-frequency (RF) analyzer detects wireless communication and RF signals. | RF signals exposure | R, L | C | |
| UAVs carry RF jamming equipment to interfere with existing RF signals’ communication systems | CI operation interference, signal jamming and communication loss. Airspace capacity limitations | E, M, R, L | I, A | |
| UAVs carry explosive payloads against physical integrity of CI facilities | CI physical damage. Loss of operational efficiency. Air traffic flow slowdown for safety precautions. Human injuries | E, H, M, R, L | I, A | |
| Threat/Hazard | Impacted Assets | Impact Analysis | ||
|---|---|---|---|---|
| Description and Impact Areas (*) | on CIA (**) | |||
| An insider installs passive RFID in the location above a server room, router, array of integrated sensors or data center | Airport operations centre, the central network which handles all the decisions and processes from flight control to ground handlers. such assets include:
| Airport sensitive information and critical infrastructure exposed | R, L | C |
| A UAV equipped with a wireless antenna accesses communication links and captures data packages sent between Wi-Fi-connected devices and wireless sensors to extract information towards a malicious center of command. | Confidentiality breach, data exposure. Passengers’ and personnel’s personal information can be stolen | E, R, L | C, I | |
| A UAV performs an acoustic attack recording valuable private information. | Confidentiality breach | R, L | C | |
| A UAV performs a physical attack against CIs, if carrying an explosive payload | CI physical damage. Human injuries or loss of life. Air traffic flow and airport stops for safety precautions | E, H, M, R, L | I, A | |
| Threat/Hazard | Impacted Assets | Impact Analysis | ||
|---|---|---|---|---|
| Description and Impact Areas (*) | on CIA (**) | |||
| Attacker is equipped with an ADS-B tracing system and receives traffic data from passing aircraft | Air traffic control, secondary surveillance system (ADS-B data), aircraft safety during take-off and landing phases, separation minima, aviation safety rules | Surveillance and ATM systems’ confidentiality is compromised | L | C |
| Attacker injects a single UAV into the airspace, with ADS-B spoofed identity to create confusion in airport’s surveillance system and ATM | Surveillance integrity is compromised and air traffic can be disrupted or downgraded for safety reasons | E, H, M, R, L | I, A | |
| Attacker injects a SWARM of drones equipped with ADS-B systems to create confusion in the airport’s surveillance system and ATM | Aircraft safety is jeopardized and separation minima are violated. A serious accident with aircraft may cause fatalities and serious destruction of airport’s CI | E, H, M, R, L | I, A | |
| Attacker launches a physical attack against passing aircraft during take-off or landing | E, H, M, R, L | |||
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lykou, G.; Moustakas, D.; Gritzalis, D. Defending Airports from UAS: A Survey on Cyber-Attacks and Counter-Drone Sensing Technologies. Sensors 2020, 20, 3537. https://doi.org/10.3390/s20123537
Lykou G, Moustakas D, Gritzalis D. Defending Airports from UAS: A Survey on Cyber-Attacks and Counter-Drone Sensing Technologies. Sensors. 2020; 20(12):3537. https://doi.org/10.3390/s20123537
Chicago/Turabian StyleLykou, Georgia, Dimitrios Moustakas, and Dimitris Gritzalis. 2020. "Defending Airports from UAS: A Survey on Cyber-Attacks and Counter-Drone Sensing Technologies" Sensors 20, no. 12: 3537. https://doi.org/10.3390/s20123537
APA StyleLykou, G., Moustakas, D., & Gritzalis, D. (2020). Defending Airports from UAS: A Survey on Cyber-Attacks and Counter-Drone Sensing Technologies. Sensors, 20(12), 3537. https://doi.org/10.3390/s20123537






