Anomaly Detection Trusted Hardware Sensors for Critical Infrastructure Legacy Devices
Abstract
1. Introduction
2. Critical Infrastructure Security Monitoring System Anomaly Detection Sensors
2.1. Threat Model
3. Introducing Trust on Software Sensors
3.1. Using Trusted Platform Modules
3.2. Using Virtual Environments
4. Proposed Approach for Legacy Systems
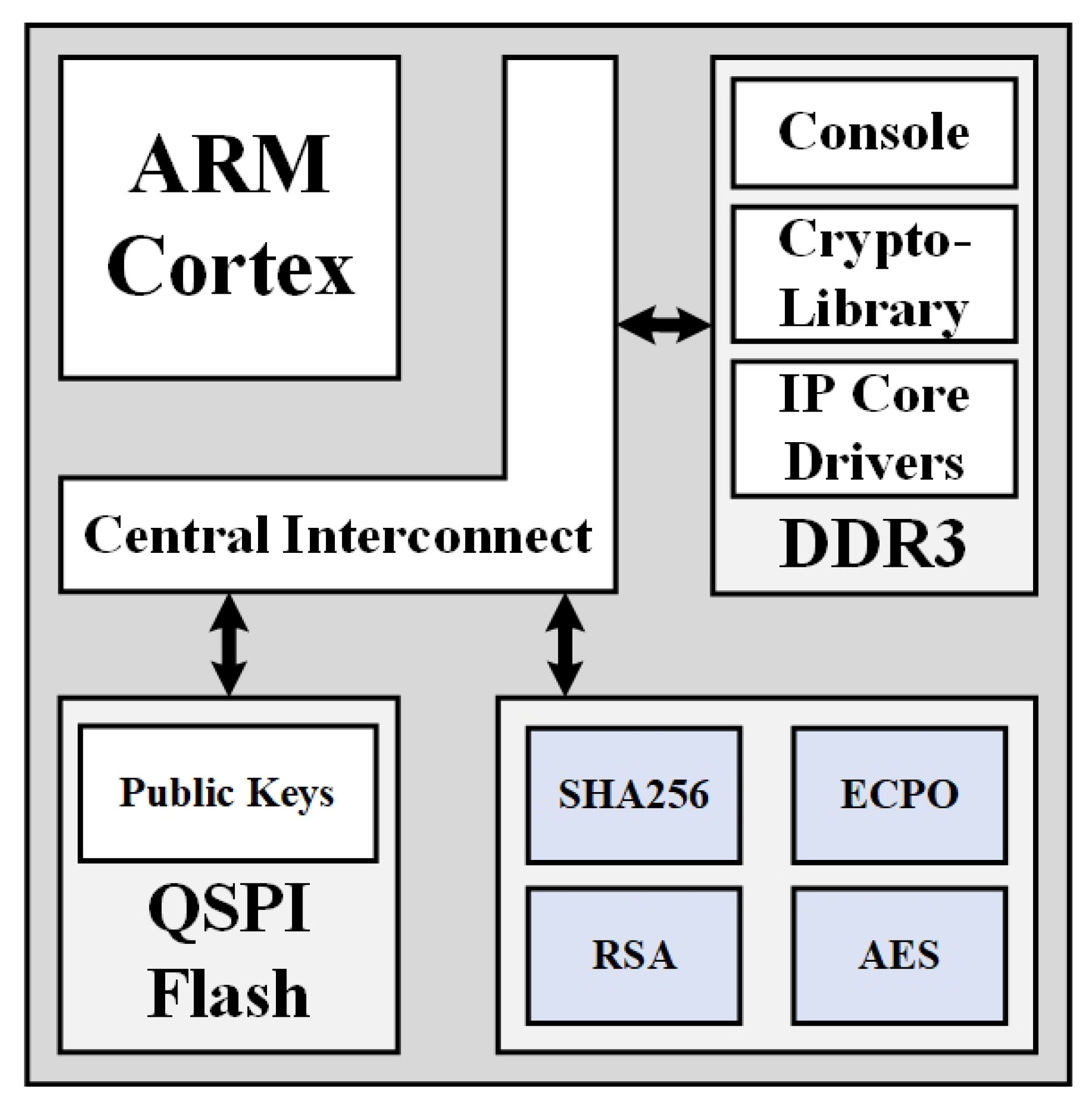
4.1. Hst Architecture
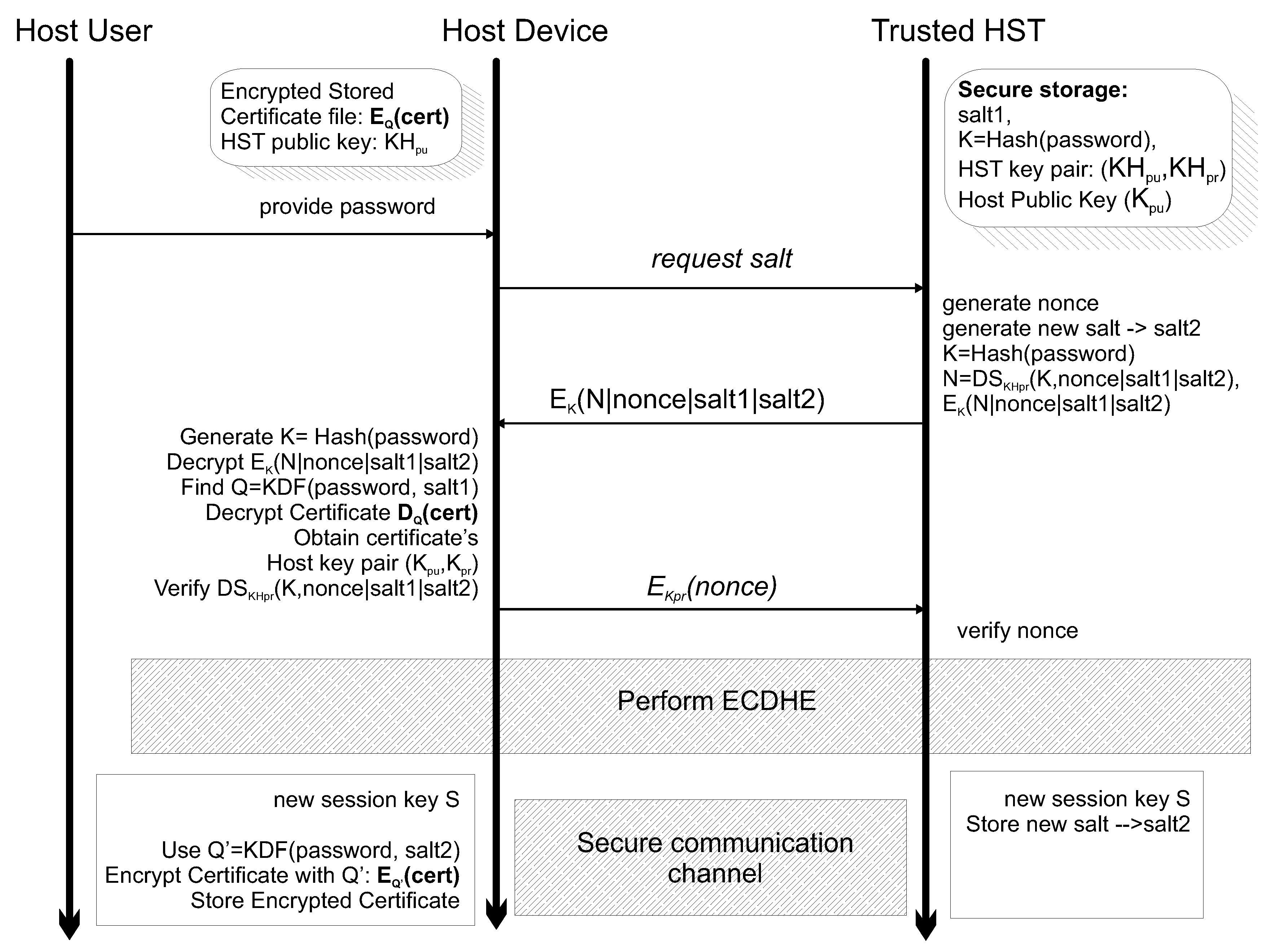
4.2. Host to Hst Functionality
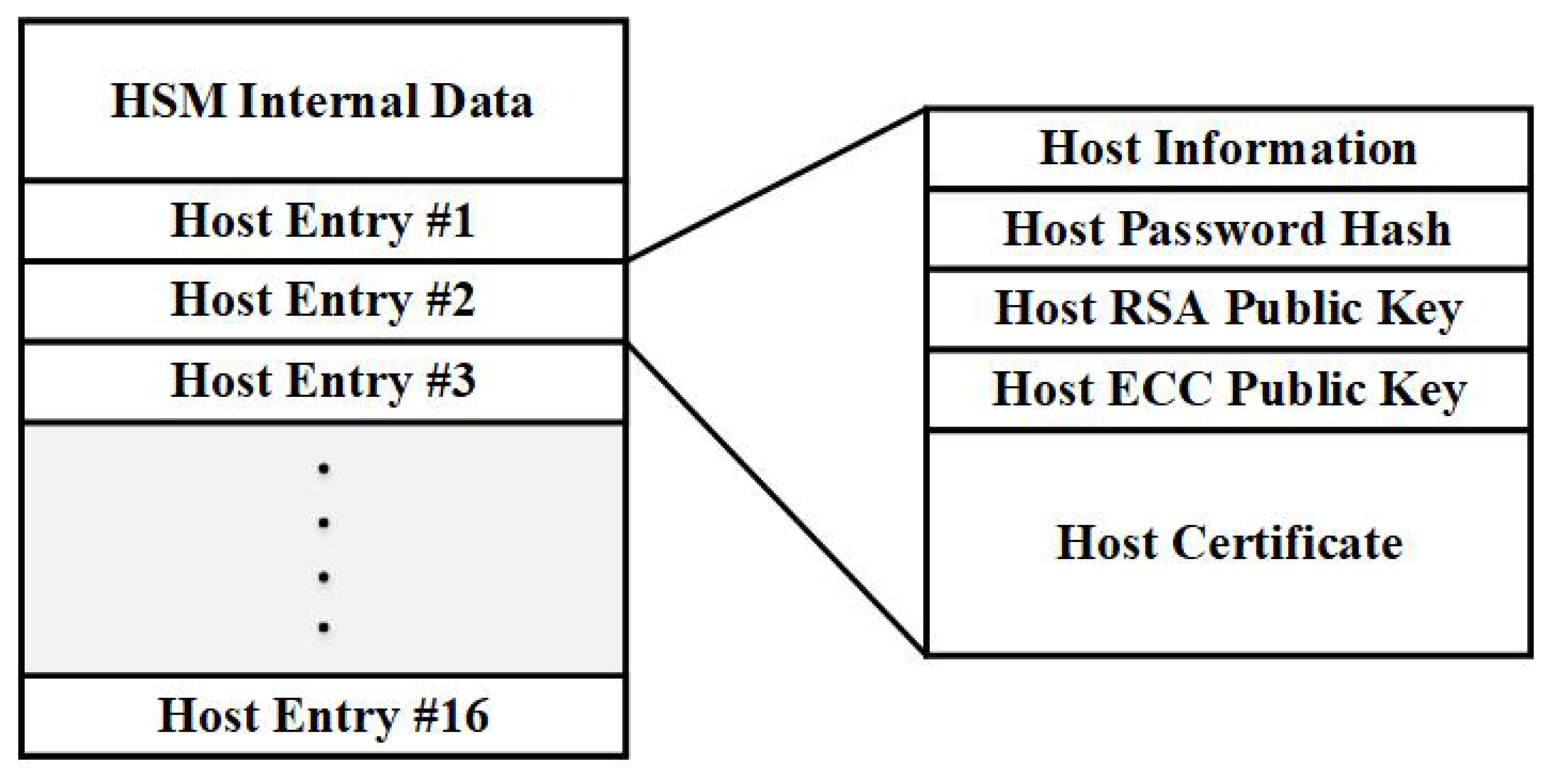
4.3. Host-Hsm Logging Mechanism
- 0: Message integrity validation event.
- 1: Password based host to HST session initiation.
- 2: HST availability.
- 3: Security channel failure.
5. Hst Practical Conceptualization–Realization
5.1. Case Study Hst Cli for Cryptographic Application Programming
5.2. Hst as a Certificate Authority
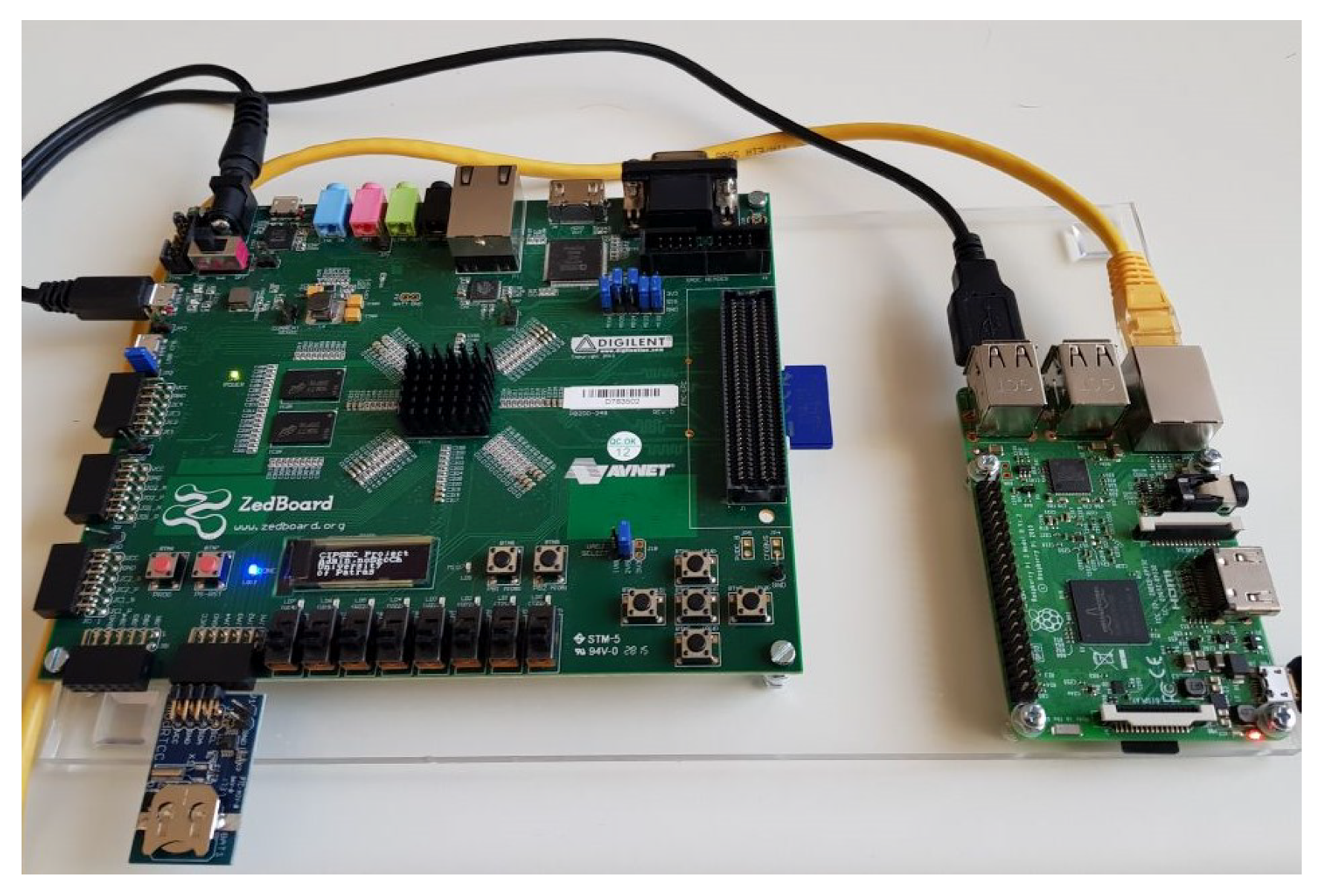
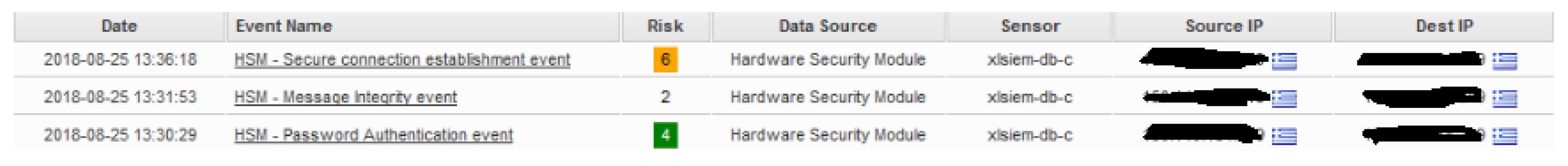
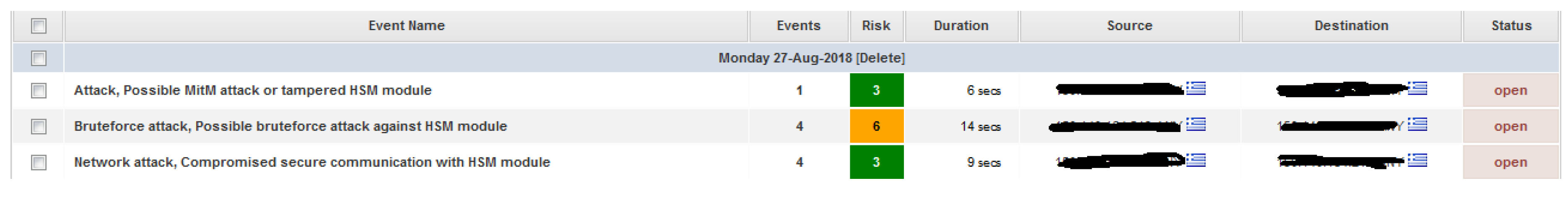
5.3. Real-World Test Case Hst Validation
5.3.1. Test Case A
5.3.2. Test Case B
5.4. Results and Discussion
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Ten, C.W.; Yamashita, K.; Yang, Z.; Vasilakos, A.V.; Ginter, A. Impact assessment of hypothesized cyberattacks on interconnected bulk power systems. IEEE Trans. Smart Grid 2017, 9, 4405–4425. [Google Scholar] [CrossRef]
- Fournaris, A.P.; Lampropoulos, K.; Koufopavlou, O. Trusted hardware sensors for anomaly detection in critical infrastructure systems. In Proceedings of the 2018 7th International Conference on Modern Circuits and Systems Technologies (MOCAST), Thessaloniki, Greece, 9 May 2018; pp. 1–4. [Google Scholar]
- Baggett, R.K.; Simpkins, B.K. Homeland Security and Critical Infrastructure Protection; ABC-CLIO: Santa Barbara, CA, USA, 2018. [Google Scholar]
- Shackleford, D. Who’s using Cyberthreat Intelligence and how? SANS Inst. 2015, 24, 2018. [Google Scholar]
- Lewis, T.G. Critical Infrastructure Protection in Homeland Security: Defending a Networked Nation; John Wiley & Sons: Hoboken, NJ, USA, 2019. [Google Scholar]
- Mitchell, R.; Chen, I.R. A Survey of Intrusion Detection Techniques for Cyber-physical Systems. ACM Comput. Surv. 2014, 46, 55:1–55:29. [Google Scholar] [CrossRef]
- Rathi, M.M.; Jain, V.K.; Merchant, S.T.; Lin, V.C. Method and System for Detecting and Preventing Access Intrusion in a Network, 2014. U.S. Patent 8,707,432, 22 April 2014. [Google Scholar]
- Manandhar, K.; Cao, X.; Hu, F.; Liu, Y. Detection of faults and attacks including false data injection attack in smart grid using Kalman filter. IEEE Trans. Control. Netw. Syst. 2014, 1, 370–379. [Google Scholar] [CrossRef]
- Sun, Y.; Luo, H.; Das, S.K. A trust-based framework for fault-tolerant data aggregation in wireless multimedia sensor networks. IEEE Trans. Dependable Secur. Comput. 2012, 9, 785–797. [Google Scholar] [CrossRef]
- Khan, M.T.; Serpanos, D.; Shrobe, H. A rigorous and efficient run-time security monitor for real-time critical embedded system applications. In Proceedings of the 2016 IEEE 3rd World Forum on Internet of Things (WF-IoT), Reston, VA, USA, 14 December 2016; pp. 100–105. [Google Scholar]
- Watterson, C.; Heffernan, D. Runtime verification and monitoring of embedded systems. IET Softw. 2007, 1, 172–179. [Google Scholar] [CrossRef]
- Fadlullah, Z.M.; Taleb, T.; Ansari, N.; Hashimoto, K.; Miyake, Y.; Nemoto, Y.; Kato, N. Combating against attacks on encrypted protocols. In Proceedings of the 2007 IEEE International Conference on Communications, Glasgow, UK, 28 June 2007; pp. 1211–1216. [Google Scholar]
- Jing, Q.; Vasilakos, A.V.; Wan, J.; Lu, J.; Qiu, D. Security of the Internet of Things: Perspectives and challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Niu, Z.; Shi, S.; Sun, J.; He, X. A survey of outlier detection methodologies and their applications. In Proceedings of the International Conference on Artificial Intelligence and Computational Intelligence, Taiyuan, China, 25 September 2011; pp. 380–387. [Google Scholar]
- Coppolino, L.; D’Antonio, S.; Formicola, V.; Romano, L. Enhancing SIEM technology to protect critical infrastructures. In Critical Information Infrastructures Security; Springer: Berlin, Germany, 2013; pp. 10–21. [Google Scholar]
- Hu, F.; Lu, Y.; Vasilakos, A.V.; Hao, Q.; Ma, R.; Patil, Y.; Zhang, T.; Lu, J.; Li, X.; Xiong, N.N. Robust cyber–physical systems: Concept, models, and implementation. Future Gener. Comput. Syst. 2016, 56, 449–475. [Google Scholar] [CrossRef]
- Coppolino, L.; Kuntze, N.; Rieke, R. A Trusted Information Agent for Security Information and Event Management. Secur. Anal. Syst. Behav. 2012, 6–12. [Google Scholar]
- King, D.; Orlando, G.; Kohler, J. A case for trusted sensors: Encryptors with Deep Packet Inspection capabilities. In Proceedings of the MILCOM 2012 IEEE Military Communications Conference, Orlando, FL, USA, 1 November 2012; pp. 1–6. [Google Scholar] [CrossRef]
- Zuech, R.; Khoshgoftaar, T.M.; Wald, R. Intrusion detection and Big Heterogeneous Data: A Survey. J. Big Data 2015, 2, 3. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Bhat K, V.; Vasilakos, A.V. LAM-CIoT: Lightweight authentication mechanism in cloud-based IoT environment. J. Netw. Comput. Appl. 2020, 150, 102496. [Google Scholar] [CrossRef]
- Fraile, L.P.; Fournaris, A.P.; Koufopavlou, O. Revisiting Rowhammer Attacks in Embedded Systems. In Proceedings of the 2019 14th International Conference on Design Technology of Integrated Systems in Nanoscale Era (DTIS), Mykonos, Greece, 16 April 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Fournaris, A.P.; Pocero Fraile, L.; Koufopavlou, O. Exploiting hardware vulnerabilities to attack embedded system devices: A survey of potent microarchitectural attacks. Electronics 2017, 6, 52. [Google Scholar] [CrossRef]
- Fournaris, A.P.; Keramidas, G. From hardware security tokens to trusted computing and trusted systems. In System-Level Design Methodologies for Telecommunication; Springer: Cham, Switzerland, 2014; Volume 9783319006, pp. 99–117. [Google Scholar] [CrossRef]
- Trusted Computing Group. TCG TPM Specification Version 1.2. 2007. Available online: https:/www.trustedcomputinggroup.org/specs/TPM/ (accessed on 29 May 2020).
- Challener, D.; Yoder, K.; Catherman, R.; Safford, D.; Van Doorn, L. A Practical Guide to Trusted Computing; IBM Press: Armonk, NY, USA, 2007. [Google Scholar]
- Intel. Intel® Trusted Execution Technology (Intel® TXT). 2011. Available online: https://www.intel.com/content/www/us/en/architecture-and-technology/trusted-execution-technology/trusted-execution-technology-security-paper.html (accessed on 29 May 2020).
- ARM. ARMTrustZone. Available online: http://www.arm.com/products/processors/technologies/trustzone.php (accessed on 29 May 2020).
- Hein, D.; Toegl, R. An Autonomous Attestation Token to Secure Mobile Agents in Disaster Response. In Proceedings of the First International ICST Conference on Security and Privacy in Mobile Information and Communication Systems (MobiSec 2009), Torino, Italy, 3–5 June 2009. [Google Scholar]
- Fournaris, A.; Lampropoulos, K.; Koufopavlou, O. Hardware Security for Critical Infrastructures—The CIPSEC Project Approach. In Proceedings of the 2017 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Bochum, Germany, 3 July 2017. [Google Scholar] [CrossRef]
- Heiser, G.; Andronick, J.; Elphinstone, K.; Klein, G.; Kuz, I.; Ryzhyk, L. The road to trustworthy systems. In Proceedings of the Fifth ACM Workshop on Scalable Trusted Computing, Chicago, IL, USA, 18 July 2010; pp. 3–10. [Google Scholar]
- Fournaris, A.P.; Koufopavlou, O. Protecting CRT RSA against Fault and Power Side Channel Attacks. In Proceedings of the 2012 IEEE Computer Society Annual Symposium on VLSI, Amherst, MA, USA, 19 August 2012; pp. 159–164. [Google Scholar] [CrossRef]
- Fournaris, A.P.; Zafeirakis, I.; Koulamas, C.; Sklavos, N.; Koufopavlou, O. Designing efficient elliptic Curve Diffie-Hellman accelerators for embedded systems. In Proceedings of the 2015 IEEE International Symposium on Circuits and Systems (ISCAS), Lisabon, Portugal, 27 May 2015; pp. 2025–2028. [Google Scholar] [CrossRef]
- EU H2020 Project CONCORDIA: ACybersecurity Competence Network with Leading Research, Technology, Industrial and Public Competences. Available online: https://www.concordia-h2020.eu/ (accessed on 29 May 2020).
- EU H2020 Project CPSoSaware: Cross-Layer Cognitive Optimization Tools & Methods for the Lifecycle Support of Dependable CPSoS. Available online: http://cpsosaware.eu/ (accessed on 29 May 2020).
- Pimoroni. Enviro pHAT. Available online: https://github.com/pimoroni/enviro-phat (accessed on 29 May 2020).
- Ornaghi, A.; Valleri, M. Ettercap Project. Available online: https://www.ettercap-project.org/index.html (accessed on 29 May 2020).

| HSM Log Entry JSON Structure |
|---|
| { |
| “HostID”:<integer>, |
| “HostIP”:<integer>, |
| “HostState”:<string>, |
| “HSTid”:<integer>, |
| “timestamp”:<integer>, |
| “event”:{ |
| “type”:<integer>, |
| “failure”:<integer>, |
| “severity”:<integer> |
| } |
| “comments”: <string> |
| Runtime Benchmark | ||||
|---|---|---|---|---|
| 16B | 64B | 128B | 256B | |
| HMAC | 0.049 s | 0.061 s | 0.071 s | 0.092 s |
| AES | 0.052 s | 0.067 s | 0.089 s | 0.135 s |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fournaris, A.P.; Dimopoulos, C.; Lampropoulos, K.; Koufopavlou, O. Anomaly Detection Trusted Hardware Sensors for Critical Infrastructure Legacy Devices. Sensors 2020, 20, 3092. https://doi.org/10.3390/s20113092
Fournaris AP, Dimopoulos C, Lampropoulos K, Koufopavlou O. Anomaly Detection Trusted Hardware Sensors for Critical Infrastructure Legacy Devices. Sensors. 2020; 20(11):3092. https://doi.org/10.3390/s20113092
Chicago/Turabian StyleFournaris, Apostolos P., Charis Dimopoulos, Konstantinos Lampropoulos, and Odysseas Koufopavlou. 2020. "Anomaly Detection Trusted Hardware Sensors for Critical Infrastructure Legacy Devices" Sensors 20, no. 11: 3092. https://doi.org/10.3390/s20113092
APA StyleFournaris, A. P., Dimopoulos, C., Lampropoulos, K., & Koufopavlou, O. (2020). Anomaly Detection Trusted Hardware Sensors for Critical Infrastructure Legacy Devices. Sensors, 20(11), 3092. https://doi.org/10.3390/s20113092






