Abstract
With the rapid development of the Internet of Things (IoT), the radio frequency identification (RFID) system becomes increasingly important. Tag identification is a basic problem of the RFID system, whose purpose is to inventory tags. However, in recent years, it requires a very short time for massive tag identification, which brings serious challenges. The traditional Aloha based anti-collision algorithms have disadvantages of either low efficiency or high complexity. Therefore, this article proposes a low complexity dynamic frame slotted Aloha (DFSA) anti-collision algorithm, named LC-DFSA. The reader can estimate the range of tag numbers according to the last frame size, the number of successful slots and the ratio of idle slots. Then the optimal frame size can be calculated. Complexity analysis is deployed in this article, and we validate the correctness of the analysis. Through our simulations, LC-DFSA outperforms other schemes in both the average access efficiency and the algorithm complexity. It also can be conveniently applied to engineering implementations.
1. Introduction
Over the years, with the rapid development of information technology, the Internet of Things (IoT) has begun to penetrate into people’s lives [1]. IoT realizes the Internet of everything through sensor technology, communication technology, network technology and so on [2]. Radio frequency identification (RFID) is an important part of IoT.
Tag identification is a basic and important problem in the RFID system [3]. It is implemented by information exchanged between a reader and many tags, which are attached to different objects [4]. Nowadays, due to the higher demand of logistics [5], warehouse inventory [6], vehicle [7] and other scenarios [8,9,10], tag identification has to face to tricky challenges: to identify massive tags in a very short amount of time. Therefore, high efficient tag identification with low complexity is quite important.
As an important issue of tag identification, response collision needs attentions. In the ISO/IEC 18000 standard, solutions to collision problems are mentioned. Anti-collision techniques can be roughly divided into two types: protocols based on Aloha and protocols based on Binary Tree. For example, in ISO/IEC 18000-6 [11], mode A is a kind of Aloha based protocol, while mode B is a protocol based on Binary Tree. Mode A explicitly proposes the concept of the Dynamic Frame Slotted Aloha (DFSA) algorithm. However, it does not specify how to achieve it.
Some specific DFSA algorithms have been put forward. Mustapha et al. [12] proposed a Tag Estimation Method (TEM) that combined Bayesian and lower bound estimating. Chu et al. [13] estimated tag population through an enhanced Bayesian Method used in the physical layer. Wang et al. [14] used the secant iteration method to estimate the number of tags. Chen [15] performed once early judgment to adjust frame sizes. HajMirzaei [16] proposed a TEM based on Manchester encoding, and Chen [17] used the Maximum a Posteriori (MAP) to estimate the tag number. They are either with low efficiency or with high complexity considering the limited power in passive RFID systems.
In order to reduce the complexity of anti-collision algorithms in the RFID system while maintaining high efficiency, this paper proposes a low complexity anti-collision algorithm based on DFSA, named LC-DFSA. We calculate the demarcation points of different frame sizes through theoretical analyses, and we also analyze the border values of tag numbers in the case of no idle slots, no successful slots and full collision slots. Then the frame size can be kept in an optimizing value according to the demarcation points and border values. Moreover, the above values used in LC-DFSA can be stored in the memory of the reader in advance, which means that the LC-DFSA algorithm only performs some simple calculation and comparison. Thus, it lowers the complexity of the passive RFID system. The results of the analyses and simulations show that the complexity of LC-DFSA is lower than that of Chen [15] and HajMirzaei [16], and the access efficiency of the proposed LC-DFSA achieves 0.345 for the massive tags scenario, which outperforms Chen [15] and HajMirzaei [16].
The contributions of this paper are summarized as follows:
- This paper proposes a low complexity anti-collision algorithm named LC-DFSA, which can be conveniently applied to engineering implementations.
- Meanwhile, the computational and signaling complexity of LC-DFSA is low for a passive RFID system, and the compatibility for the standard framework is good as well.
2. Motivation
2.1. Brief Introduction to Aloha Based Anti-Collision Algorithm
Anti-collision algorithms based on Aloha can be roughly divided into five categories [18]: Pure Aloha (PA), Slotted Aloha (SA), Frame Slotted Aloha (FSA), DFSA and Enhanced Dynamic Frame Slotted Aloha (EDFSA).
Pure Aloha (PA): When tags are in the communication range of a reader, they will automatically reply their ID to the reader immediately. Then it will result in three situations: successful identification, complete collision and partial collision. If current identification is failed, the tag will respond again after a random interval of time, and the above steps repeat until all tags are identified by the reader successfully.
Slotted Aloha (SA): Continuous time is split into discrete slots. All tags can only respond at the beginning of the slot. Since the slot duration is longer than that of response, SA avoids partial collisions and improves the efficiency of RFID.
Frame Slotted Aloha (FSA): Several slots make up one frame. Each tag can only respond once in one frame, which can alleviate the problem of frequent response of some tags.
DFSA: After a frame, the reader can dynamically adjust the size of next frame according to the current situation. Therefore, it can improve the efficiency of the RFID system no matter how many tags there are.
Enhanced Dynamic Frame Slotted Aloha (EDFSA): Because the maximum frame size in mode A is 256 [11], when the tag population is larger, the efficiency of the RFID system decreases rapidly. Therefore, tags can be grouped and identified in turn when the tag amount is larger. EDFSA has greatly improved the efficiency of large-scale tag identification.
2.2. Motivation
It is always the case in tag identification that the tag population is unknown. As shown in Figure 1 and Figure 2, when the tag number is much larger than the frame size, collisions will be serious. It will spend more frames to identify all tags. But when the tag number is much smaller than the frame size, plenty of idle slots will be wasted. It will also lead to the reduction of overall efficiency. Therefore, we need an algorithm that can adjust the frame size dynamically. In this way, no matter what the tag number is, tag identification can maintain high efficiency all the time.
Figure 1.
Large Amount of Tags.
Figure 2.
Small amount of tags.
3. Proposed LC-DFSA Algorithm
3.1. Key Idea
If the tag number is known, we can calculate the appropriate frame size to maximize access efficiency. Since frame sizes may not be continuous natural numbers, different tag numbers may correspond to the same optimal frame size. Therefore, even if the number of tags is unknown, if the approximate range of tag numbers can be estimated, the optimal frame size also can be determined. Figure 3 shows the process of tag identification.
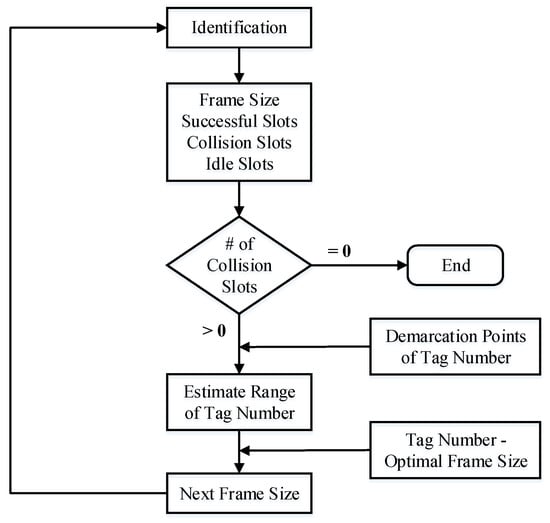
Figure 3.
Tag identification process.
In this paper, the corresponding relationship between tag numbers and optimal frame sizes is obtained through access efficiency. Then, the optimal size of next frame can be calculated by the last frame size, successful slots number and the ratio of idle slots.
3.2. Optimal Frame Size
Assuming that the tag number is fixed, it is obvious that the frame size can be neither too large nor too small. Therefore, in the case of a fixed tag number, it is necessary to determine the optimal frame size, so as to reach the highest efficiency. Table 1 shows some notations which will be used in the theoretical analysis.

Table 1.
Notations.
For a particular slot, the probability that each tag chooses the slot is and the probability of selecting other slots is . So, the probability of a successful slot is given by:
and the probability that a tag is successful in a frame is:
Then we can get the expected successful tags number in a frame, which is:
Therefore, the expected value of access efficiency can be calculated as:
As we can see from Equation (4), is a function of and . When is fixed, will be a unary function of . In order to maximize , perform:
Then we get:
As shown in Figure 4, the maximum access efficiency will be realized if the frame size is equal to the tag number.
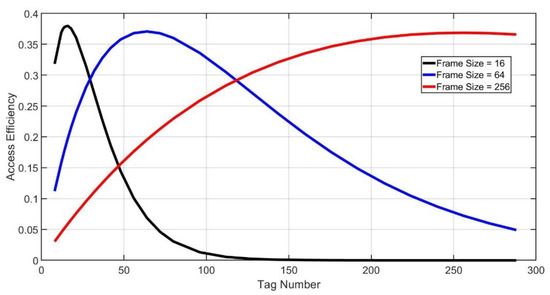
Figure 4.
Access efficiency.
3.3. Tag Number—Optimal Frame Size Table
In ISO/IEC 18000-6, the frame size can only be taken from the several discrete values [11], assuming that frame sizes are the values from a discrete integer sequence . However, the range of tag numbers belongs to positive integers. It is almost impossible that the frame size is exactly the same as the tag number all of the time. Therefore, when the tag number is fixed, we need to confirm the available optimal frame size to maximize access efficiency. Eventually, we can get the relationship between optimal frame sizes and tag numbers.
For a fixed tag number , there are many frame sizes that can be chosen. Through , we can calculate the maximum access efficiency and determine the optimal frame size.
As we can see from Equation (4), is a function of tag number and frame size , and the demarcation points of tag numbers between and can be calculated through the following equation:
The demarcation points are the solution of Equation (7):
Demarcation points are the boundary values of the ranges of tag numbers. If the actual tag number is between and , then will become the optimal size of next frame. When frame sizes are restricted to the power of 2, the demarcation points are shown, as in Table 2.

Table 2.
Values of demarcation points.
The tag number—optimal frame size table is shown in Table 3. For example, if the tag number is 70, the RFID system will get the highest efficiency when the frame size is 64. Efficiency will be lower if the frame size is 32 or any other number.

Table 3.
Tag number—optimal frame size.
3.4. LC-DFSA Algorithm
The size of the last frame, the successful slots number and the ratio of idle slots are used in LC-DFSA to estimate the range of the tag number and to calculate the optimal next frame size.
The probability of appearance of an idle slot is given by:
Then the expected idle slots number in a frame is:
Therefore, the expected ratio of idle slots can be calculated as:
Figure 5 shows the relationship between tag numbers and idle slot ratios when frame sizes are fixed. Idle slot ratio is a monotonic minus function of tag number . Therefore, we can estimate the range of tag numbers by due to its monotonicity. Through Equation (8), we can calculate tag number demarcation points, which are . In order to determine the optimal size of next frame, the demarcation points that we actually use are:
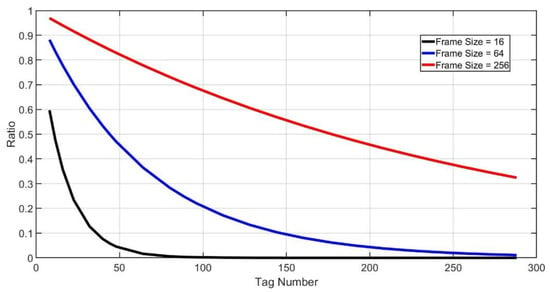
Figure 5.
Idle slot ratio.
is the actual successful slot number of the last frame. According to the size of the last frame, the reader can get for each demarcation point. Then the reader can calculate the actual idle slot ratio . Therefore, the range of current tag number can be estimated by comparing and of the demarcation points.
For instance, assume that the last frame size is 32 and is between and . will be estimated as . Then, the size of next frame will be , which is 16. Figure 6 shows the demarcation points when the last frame size is small, assuming .
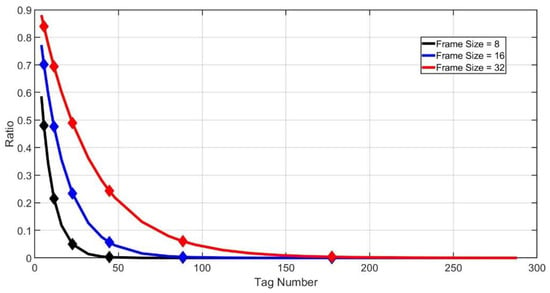
Figure 6.
Demarcation points ().
As we can see from Figure 6, when the frame size is much smaller than the tag number, the idle slot ratio curve descends rapidly. It may not be possible to accurately determine the range of tag numbers. For example, assume that the size of the last frame is 8 and . When , the next frame size will be according to our algorithm above. However, the actual tag number may be only 50. It will waste plenty of slots in this case. To solve the problem, we can analyze the border of successful, idle and collision slot ratios.
Figure 7 shows the ratios of idle, successful and collision slots when the frame size is 32. If the tag number is larger than , the probability of will be very high. is the solution of Equation (12).
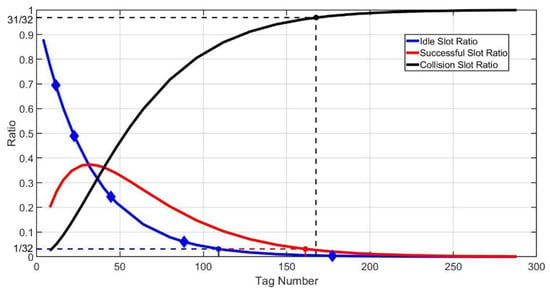
Figure 7.
Border of idle, successful and collision slot ratio.
If the tag number is larger than , the actual number of successful slots will be likely to reduce to 0. is the solution of Equation (13).
In the case of that the tag number is larger than , all slots in the frame will be almost in collision. is the solution of Equation (14).
Therefore, as Algorithm 1 presents, when and , it means that the actual remaining tags may not be so many. The tag number will be estimated as conservatively, and the next frame size can be calculated through the relationship between tag numbers and optimal frame sizes. Meanwhile, when and , the next frame size will be determined through , and if , we can calculate the next frame size according to directly. Then, start a new frame and repeat above steps until all the tags are identified.
| Algorithm 1 LC-DFSA |
| 1: After a frame, get , and . 2: If 3: If 4: If 5: will be calculated by . 6: Else 7: will be calculated by . 8: Else 9: Calculate and . 10: Compare and . And get . 11: will be calculated by directly. 12: Start a new frame with slots. 13: Else 14: Tag inventory completes. |
3.5. Complexity Analysis
As shown in Table 4, the LC-DFSA algorithm performs normal signaling interactions of standard ISO/IEC 18000-6, which leads to its lowest signaling complexity. Chen [15] could achieve low complexity based on the normal signaling interactions of the Q-algorithm. The signaling complexity of Wang and Chen [17] would be a little bit higher due to their continuous frame sizes. However, HajMirzaei increased the signaling overhead a lot to improve the estimation accuracy of tag numbers. Therefore, the signaling complexity of HajMirzaei was the highest.

Table 4.
Complexity comparison.
As for computational complexity, all the demarcation points and border values of LC-DFSA can save in the memory of the reader. Thus, the computational complexity of the LC-DFSA algorithm is low. Chen [15] estimated the tag number as , which needs few computing resources. Chen [17] would calculate the probability of each possible number of tags through the multinomial distribution formula, and then would find the tag number, which has the maximum probability. It costs a lot of resources, so it is unavailable for engineering implementation. Wang solved a transcendental equation by secant iteration and eliminated the pseudo solution, which increased its computational complexity; HajMirzaei only performed some simple calculations and comparisons, which led to its low computational complexity.
Standard compatibility is also important for anti-collision algorithms. Chen [15] could only achieve within the framework of the UHF Class-1 Generation-2 RFID Standard [19], which lowered the compatibility for standards. However, the others can be applied in not only ISO/IEC 18000-6A, but also ISO/IEC 18000-6C, whose framework is the same as UHF Class-1 Generation-2. They have better standard compatibility than Chen [15].
4. Simulation and Analysis
MATLAB 2018 is used for our simulations. The number of tags ranges from 1000 to 10,000. All simulation results are the average value of 5000 simulations. The initial frame sizes of all the algorithms are set as 1024 in our simulations. The frame sizes in the LC-DFSA algorithm are restricted to the power of 2, and the check point of Chen [15] is .
In Figure 8, the blue line represents the actual frame sizes of the LC-DFSA algorithm, while the red line shows the optimal frame sizes. The tag number is 10,000 and the initial frame size is set as 1024. In this case, 10,000 tags can be identified after 30 frames. According to the simulation results, after the second frame, the actual frame sizes are consistent with the optimal frame sizes, which shows the effectiveness of the LC-DFSA algorithm.
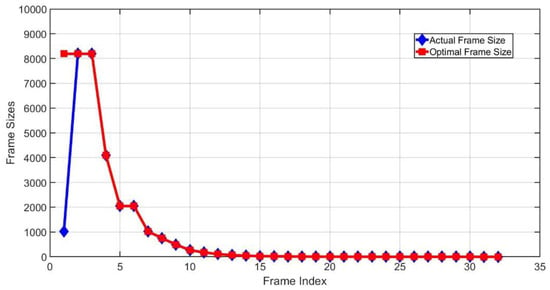
Figure 8.
Actual and optimal frame size.
Figure 9 shows the access efficiency of different algorithms, which is also known as throughput. From the results, HajMirzaei has the worst performance among these three algorithms. When the tag number is smaller than 4000, the difference between Chen’s efficiency and LC-DFSA’s efficiency is small, and as the tag number increases further, the efficiency of Chen decreases. The accuracy of is worse when the tag number and the frame size are mismatched with each other. The average efficiency of Chen is 0.3309 and that of HajMirzaei is 0.3176. The proposed LC-DFSA algorithm is 0.3448, which is the highest. In this way, the LC-DFSA algorithm improves 4.2% when compared with Chen, and it is an improvement of 5.4% when compared with HajMirzaei.
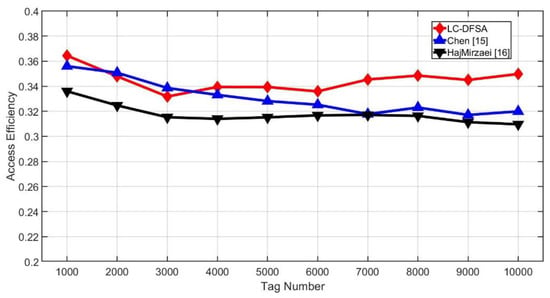
Figure 9.
Access efficiency of different algorithms.
From the view of algorithm complexity, Chen, LC-DFSA and HajMirzaei only perform some fixed calculation and comparison, so the complexity of them are all . Besides, Figure 10 shows the simulation run time of each algorithm. To some extent, it can be proved that the LC-DFSA algorithm has the lowest complexity. Collision analysis by Manchester encoding increases the overhead of HajMirzaei, and Chen performs the examination in the middle of the frame, which will lead to more frames. Moreover, frame sizes of LC-DFSA are discrete while frame sizes of HajMirzaei can be any natural number. It also lowers the complexity of LC-DFSA.
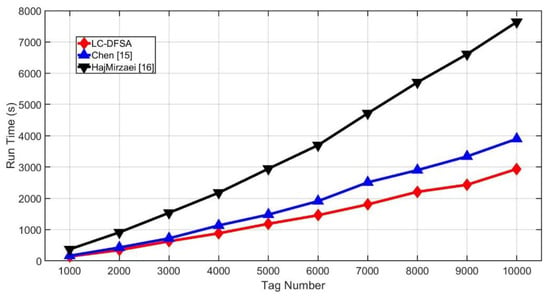
Figure 10.
Simulation run time of different algorithms.
Figure 11 and Figure 12 show the effect of different initial frame sizes on the access efficiency. As we can see from Figure 11, the initial frame size has a great impact on efficiency. However, if the tag number is larger, then the influence of the initial frame size will be smaller. From Figure 12, it is found that when the initial frame size is small compared with the tag number, there will be stable access efficiency no matter how large the tag amount is. However, when the initial frame size is larger, the efficiency drops dramatically if the tag number is small. Besides, we can also find that there will be the maximum efficiency when the initial frame size is the same as the number of tags.
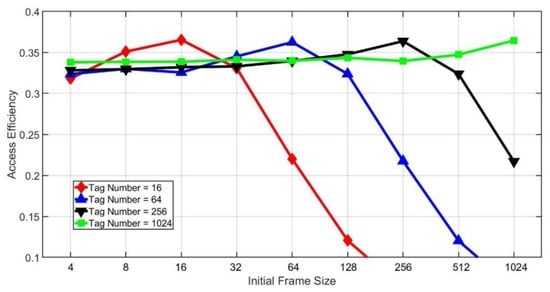
Figure 11.
Access efficiency of different tag numbers.
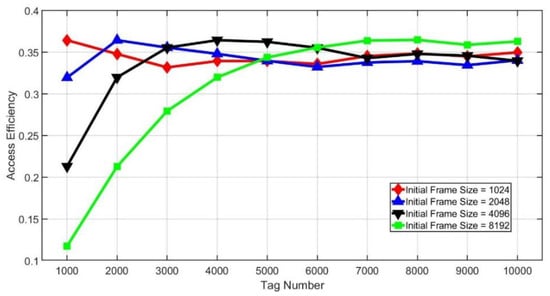
Figure 12.
Access efficiency of different initial frame sizes.
5. Conclusions and Future Work
This article proposes the LC-DFSA algorithm with the purpose of complexity reduction and efficiency improvement for RFID systems. The reader can estimate the range of tag numbers according to the demarcation points and border values, which can be calculated through theoretical analyses. Then the size of next frame can be determined by the relationship between tag numbers and optimal frame sizes. Through our simulations, it is found that the complexity of the LC-DFSA algorithm is lower than that of Chen and HajMirzaei, and LC-DFSA also improves efficiency when compared with Chen and HajMirzaei. Therefore, the proposed LC-DFSA algorithm has the best comprehensive performance.
We still have some work to do in the future. For DFSA algorithms, the initial frame size has an effect on access efficiency. We will try to analyze different initial frame sizes separately so that the frame size can approach the optimal frame size as quickly as possible.
Author Contributions
Conceptualization, Z.J.; Formal analysis, M.Y. and Z.Y.; Funding acquisition, B.L., M.Y. and Z.Y.; Investigation, Z.J.; Methodology, Z.J. and B.L.; Software, Z.J.; Supervision, B.L.; Writing—original draft, Z.J.; Writing—review & editing, B.L., M.Y. and Z.Y. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the National Natural Science Foundations of CHINA (Grant No. 61871322, No. 61771392, No. 61771390, No. 61501373, and No. 61271279), the National Science and Technology Major Project (Grant No. 2016ZX03001018-004), and Science and Technology on Avionics Integration Laboratory (20185553035).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Jayadi, R.; Lai, Y.C.; Lin, C.C. Efficient Time-Oriented Anti-Collision Protocol for RFID Tag Identification. Comput. Commun. 2017, 112, 141–153. [Google Scholar] [CrossRef]
- Su, J.; Sheng, Z.; Leung, V.C.; Chen, Y. Energy Efficient Tag Identification Algorithms for RFID: Survey, Motivation and New Design. IEEE Wirel. Commun. 2019, 26, 118–124. [Google Scholar] [CrossRef]
- Khalil, G.; Doss, R.; Chowdhury, M. A Comparison Survey Study on RFID Based Anti-Counterfeiting Systems. J. Sens. Actuator Netw. 2019, 8, 37. [Google Scholar] [CrossRef]
- Mbacke, A.A.; Mitton, N.; Rivano, H. A Survey of RFID Readers Anticollision Protocols. IEEE J. Radio Freq. Identif. 2018, 2, 38–48. [Google Scholar] [CrossRef]
- Zhou, W.; Jiang, N.; Yan, C. Research on Anti-Collision Algorithm of RFID Tags in Logistics System. Procedia Comput. Sci. 2019, 154, 460–467. [Google Scholar] [CrossRef]
- Biswal, A.K.; Jenamani, M.; Kumar, S.K. Warehouse efficiency improvement using RFID in a humanitarian supply chain: Implications for Indian food security system. Transp. Res. Part E Logist. Transp. Rev. 2018, 109, 205–224. [Google Scholar] [CrossRef]
- Ravi, S.; David, A.; Imaduddin, M. Controlling & Calibrating Vehicle-Related Issues Using RFID Technology. SSRN Electron. J. 2018, 8, 1125–1132. [Google Scholar]
- Amato, F.; Torun, H.M.; Durgin, G.D. RFID Backscattering in Long-Range Scenarios. IEEE Trans. Wirel. Commun. 2018, 17, 2718–2725. [Google Scholar] [CrossRef]
- Parada, R.; Melià-Seguí, J.; Pous, R. Anomaly Detection Using RFID-Based Information Management in an IoT Context. J. Organ. End User Comput. 2018, 30, 1–23. [Google Scholar] [CrossRef]
- Yan, L.; Xiong, D. Mobile motion robot indoor passive RFID location research. Int. J. RF Technol. Res. Appl. 2018, 9, 113–129. [Google Scholar] [CrossRef]
- ISO/IEC CD 18000-6. Information Technology—Radio Frequency Identification (RFID) for Item management—Part 6: Parameters for Air Interface Communications at 860–930 MHz. 2004. Available online: http://www.youwokeji.com.cn/down/18000-6.pdf (accessed on 22 November 2018).
- Benssalah, M.; Djeddou, M.; Dahou, B.; Drouiche, K.; Maali, A. A cooperative Bayesian and lower bound estimation in dynamic framed slotted ALOHA algorithm for RFID systems. Int. J. Commun. Syst. 2018, 31, e3723. [Google Scholar] [CrossRef]
- Chu, C.; Wen, G.; Huang, Z.; Su, J.; Han, Y. Improved Bayesian Method with Collision Recovery for RFID Anti-collision. In Proceedings of the International Conference on Artificial Intelligence and Security, New York, NY, USA, 26–28 July 2019; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Wang, Z.; Huang, S.; Fan, L.; Zhang, T.; Wang, L.; Wang, Y. Adaptive and dynamic RFID tag anti-collision based on secant iteration. PLoS ONE 2018, 13, e0206741. [Google Scholar] [CrossRef] [PubMed]
- Chen, W. A Fast Anticollision Algorithm for the EPCglobal UHF Class-1 Generation-2 RFID Standard. IEEE Commun. Lett. 2014, 18, 1519–1522. [Google Scholar] [CrossRef]
- HajMirzaei, M. Novel tag estimation method by use of Manchester coding in RFID systems. Int. J. Commun. Syst. 2019, 32, e4101. [Google Scholar] [CrossRef]
- Chen, W.T. An Accurate Tag Estimate Method for Improving the Performance of an RFID Anticollision Algorithm Based on Dynamic Frame Length ALOHA. IEEE Trans. Autom. Sci. Eng. 2009, 6, 9–15. [Google Scholar] [CrossRef]
- Klair, D.K.; Chin, K.W.; Raad, R. A Survey and Tutorial of RFID Anti-Collision Protocols. IEEE Commun. Surv. Tutor. 2010, 12, 400–421. [Google Scholar] [CrossRef]
- EPCglobal. EPC Radio-Frequency Identity Protocols Class-1 Generation-2 UHF RFID Protocol for Communications at 860 MHz–960 MHz; Version 1.2.0; EPCglobal: Brussels, Belgium, 2008. [Google Scholar]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).