Towards Security Joint Trust and Game Theory for Maximizing Utility: Challenges and Countermeasures
Abstract
1. Introduction
2. Relate Summarized Works
3. Game Theory in Networks
4. Trust Model, Trust Mechanism, and Trust Framework in Networks
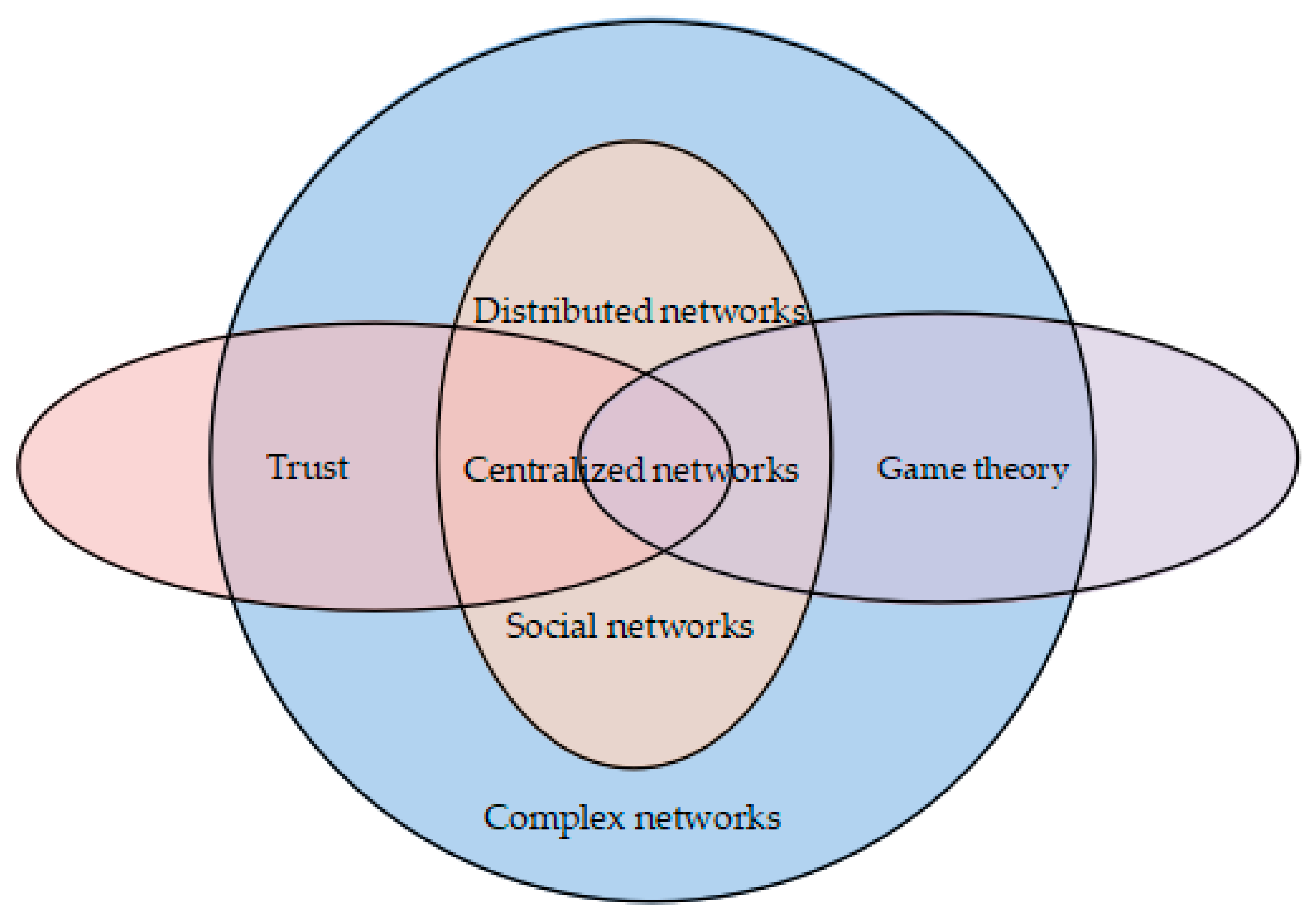
5. Analysis and Comparison Based on Application Scenarios
5.1. Application Scenarios
5.2. Differences in Applying Game Theory in Different Networks
6. Future Research Direction
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Zhu, C.S.; Shu, L.; Leung, V.C.M.; Guo, S.; Zhang, Y.; Yang, L.T. Secure Multimedia Big Data in Trust-Assisted Sensor-Cloud for Smart City. IEEE Commun. Mag. 2017, 55, 24–30. [Google Scholar] [CrossRef]
- Zhu, C.S.; Leung, V.C.M.; Rodrigues, J.J.P.C.; Shu, L.; Wang, L.; Zhou, H. Social Sensor Cloud: Framework, Greenness, Issues, and Outlook. IEEE Netw. 2018, 32, 100–105. [Google Scholar] [CrossRef]
- John, L.; McCormick, P.; McCormick, T.; McNeill, G.R.; Boardman, J. Working to Understand Cooperative Forces in Government Extended Enterprises: Concepts and Methodology. IEEE Syst. J. 2012, 6, 675–687. [Google Scholar] [CrossRef]
- Lian, B.; Chen, G.L.; Ma, M.D.; Li, J.H. Periodic K-Times Anonymous Authentication with Efficient Revocation of Violator’s Credential. IEEE Trans. Inf. Foren. Sec. 2015, 10, 543–557. [Google Scholar] [CrossRef]
- Zeng, P.; Choo, K.R. A New Kind of Conditional Proxy Re-Encryption for Secure Cloud Storage. IEEE Access 2018, 6, 70017–70024. [Google Scholar] [CrossRef]
- Hu, H.; Liu, Y.L.; Zhang, H.Q.; Pan, R.X. Optimal Network Defense Strategy Selection Based on Incomplete Information Evolutionary Game. IEEE Acess 2018, 6, 29806–29821. [Google Scholar] [CrossRef]
- Wu, Y.W.; Tang, S.J.; Xu, P.; Li, X.Y. Dealing with Selfishness and Moral Hazard in Noncooperative Wireless Networks. IEEE Trans. Mob. Comput. 2010, 9, 420–434. [Google Scholar]
- Haruna, K.; Ismail, M.A.; Suyanto, M.; Gabralla, L.A.; Bichi, A.B.; Danjuma, S.; Kakudi, H.A.; Haruna, M.S.; Zerdoumi, S.; Abawajy, J.H.; et al. A Soft Set Approach for Handling Conflict Situation on Movie Selection. IEEE Access 2019, 7, 116179–116194. [Google Scholar] [CrossRef]
- Pan, H.Y.; Song, F.; Cao, Y.Z.; Qian, J.Y. Fuzzy Pushdown Termination Games. IEEE Trans. Fuzzy Syst. 2019, 27, 760–774. [Google Scholar] [CrossRef]
- Zhu, C.S.; Leung, V.C.M.; Wang, K.; Yang, L.T.; Zhang, Y. Multi-Method Data Delivery for Green Sensor-Cloud. IEEE Commun. Mag. 2017, 55, 176–182. [Google Scholar] [CrossRef]
- Zhu, C.S.; Li, X.H.; Leung, V.C.M.; Yang, L.T.; Ngai, E.C.-H.; Shu, L. Towards Pricing for Sensor-Cloud. IEEE Trans. Cloud. Comput. 2017. [Google Scholar] [CrossRef]
- Javarone, M.A.; Atzeni, A.E. The role of competitiveness in the Prisoner’s Dilemma. Comput. Soc. Netw. 2015. [Google Scholar] [CrossRef]
- Javarone, M.A. Statistical Physics and Computational Methods for Evolutionary Game Theory; Springer: Berlin/Heidelberg, Germany, 2018. [Google Scholar]
- Li, Y.Z.; Quevedo, D.E.; Dey, S.; Shi, L. A Game-Theoretic Approach to Fake-Acknowledgment Attack on Cyber-Physical Systems. IEEE Trans. Signal. Inf. Pr. 2017, 3, 1–11. [Google Scholar] [CrossRef]
- Wang, E.K.; Li, Y.P.; Ye, Y.M.; Yiu, S.M.; Hui, L.C.K. A Dynamic Trust Framework for Opportunistic Mobile Social Networks. IEEE Trans. Netw. Serv. 2018, 15, 319–329. [Google Scholar] [CrossRef]
- Yan, Z.; Wang, H.G.; Yang, L.T.; Niemi, V. IEEE Access Special Section Editorial: Trust Management in Pervasive Social Networking (TruPSN). IEEE Access 2018, 6, 16851–16854. [Google Scholar] [CrossRef]
- Fang, W.D.; Xu, M.; Zhu, C.S.; Han, W.L.; Zhang, W.X.; Rodrigues, J.J.P.C. FETMS: Fast and Efficient Trust Management Scheme for Information-Centric Networking in Internet of Things. IEEE Access 2019, 7, 13476–13485. [Google Scholar] [CrossRef]
- Maharjan, S.; Zhu, Q.Y.; Zhang, Y.; Gjessing, S.; Başar, T. Demand Response Management in the Smart Grid in a Large Population Regime. IEEE Trans. Smart Grid 2016, 7, 189–199. [Google Scholar] [CrossRef]
- Paola, A.D.; Angeli, D.; Strbac, G. Price-Based Schemes for Distributed Coordination of Flexible Demand in the Electricity Market. IEEE Trans. Smart Grid 2017, 8, 3104–3116. [Google Scholar] [CrossRef]
- Paola, A.D.; Papadaskalopoulos, D.; Angeli, D.; Strbac, G. Investigating the Social Efficiency of Merchant Transmission Planning Through a Non-cooperative Game-Theoretic Framework. IEEE Trans. Power Syst. 2018, 33, 4831–4841. [Google Scholar]
- Fang, W.D.; Zhang, W.X.; Chen, W.; Liu, Y.; Tang, C.G. TMSRS: Trust management-based secure routing scheme in industrial wireless sensor network with fog computing. Wirel. Netw. 2019. [Google Scholar] [CrossRef]
- Gong, X.; Paola, A.D.; Angeli, D.; Strbac, G. Distributed Coordination of Flexible Loads Using Locational Marginal Prices. IEEE Trans. Control Netw. 2019, 6, 1097–1110. [Google Scholar] [CrossRef]
- Huang, W.; Zhang, L.; Huang, Y.; Lou, J. Allocating Indivisible Objects with a Parallel Method Insensitive to Identities. IEEE Access 2017, 5, 22880–22891. [Google Scholar] [CrossRef]
- Borjigin, W.; Ota, K.; Dong, M.X. In Broker We Trust: A Double-Auction Approach for Resource Allocation in NFV Markets. IEEE Trans. Netw. Serv. 2018, 15, 1322–1333. [Google Scholar] [CrossRef]
- Zhu, C.S.; Rodrigues, J.J.P.C.; Leung, V.C.M.; Shu, L.; Yang, L.T. Trust-Based Communication for the Industrial Internet of Things. IEEE Commun. Mag. 2018, 56, 16–22. [Google Scholar] [CrossRef]
- Yin, F.F.; Wang, A.Y.; Liu, D.P.; Zhang, Z.L. Energy-Aware Joint User Association and Resource Allocation for Coded Cache-Enabled HetNets. IEEE Access 2019, 7, 94128–94142. [Google Scholar] [CrossRef]
- Chen, J.; He, K.; Yuan, Q.; Xue, G.L.; Du, R.Y.; Wang, L. Batch Identification Game Model for Invalid Signatures in Wireless Mobile Networks. IEEE Trans. Mob. Comput. 2017, 16, 1530–1543. [Google Scholar] [CrossRef]
- Cui, Y.; Wang, Z.T.; Yang, Y.; Yang, F.; Ding, L.H.; Qian, L. Joint and Competitive Caching Designs in Large-Scale Multi-Tier Wireless Multicasting Networks. IEEE Trans. Commun. 2018, 66, 3108–3121. [Google Scholar] [CrossRef]
- Zonouz, S.A.; Khurana, H.; Sanders, W.H.; Yardley, T.M. RRE: A Game-Theoretic Intrusion Response and Recovery Engine. IEEE Trans. Parall. Distr. 2014, 25, 395–406. [Google Scholar] [CrossRef]
- Basilico, N.; Gatti, N.; Monga, M.; Sicari, S. Security Games for Node Localization through Verifiable Multilateration. IEEE Trans. Depend. Secure 2014, 11, 72–85. [Google Scholar] [CrossRef]
- Shi, L.Q.; Zhao, L.Q.; Zheng, G.; Han, Z.; Ye, Y.H. Incentive Design for Cache-Enabled D2D Underlaid Cellular Networks Using Stackelberg Game. IEEE Trans. Veh. Technol. 2019, 68, 765–779. [Google Scholar] [CrossRef]
- Kim, S. Reversed Stackelberg bandwidth-sharing game for cognitive multi-hop cellular networks. IET Commun. 2012, 6, 2907–2913. [Google Scholar] [CrossRef]
- Ho, J.; Wright, M.; Das, S.K. ZoneTrust: Fast Zone-Based Node Compromise Detection and Revocation in Wireless Sensor Networks Using Sequential Hypothesis Testing. IEEE Trans. Depend. Secure 2012, 9, 494–511. [Google Scholar] [CrossRef]
- Cho, J. Tradeoffs Between Trust and Survivability for Mission Effectiveness in Tactical Networks. IEEE Trans. Cybern. 2015, 45, 754–766. [Google Scholar] [CrossRef] [PubMed]
- Al-Talabani, A.; Deng, Y.S.; Nallanathan, A.; Nguyen, H.X. Enhancing Secrecy Rate in Cognitive Radio Networks via Multilevel Stackelberg Game. IEEE Commun. Lett. 2016, 20, 1112–1115. [Google Scholar] [CrossRef]
- Muthukumar, V.; Sahai, A. Fundamental Limits onEx-Post Enforcement and Implications for Spectrum Rights. IEEE Trans. Cogn. Commun. Netw. 2017, 3, 491–504. [Google Scholar] [CrossRef]
- Pawlick, J.; Zhu, Q.Y. Strategic Trust in Cloud-Enabled Cyber-Physical Systems with an Application to Glucose Control. IEEE Trans. Inf. Foren. Sec. 2017, 12, 2906–2919. [Google Scholar] [CrossRef]
- Yang, L.; Lu, Y.Z.; Liu, S.; Guo, T.; Liang, Z.F. A Dynamic Behavior Monitoring Game-Based Trust Evaluation Scheme for Clustering in Wireless Sensor Networks. IEEE Access 2018, 6, 71404–71412. [Google Scholar] [CrossRef]
- Li, Z.T.; Kang, J.W.; Yu, R.; Ye, D.D.; Deng, Q.Y.; Zhang, Y. Consortium Blockchain for Secure Energy Trading in Industrial Internet of Things. IEEE Trans. Ind. Inform. 2018, 14, 3690–3700. [Google Scholar] [CrossRef]
- Wang, Y.T.; Su, Z.; Xu, Q.C.; Yang, T.T.; Zhang, N. A Novel Charging Scheme for Electric Vehicles with Smart Communities in Vehicular Networks. IEEE Trans. Veh. Technol. 2019, 68, 8487–8501. [Google Scholar] [CrossRef]
- Gao, H.M.; Ma, Z.F.; Luo, S.S.; Wang, Z. BFR-MPC: A Blockchain-Based Fair and Robust Multi-Party Computation Scheme. IEEE Access 2019, 7, 110439–110450. [Google Scholar] [CrossRef]
- Xu, Q.C.; Su, Z.; Zheng, Q.H.; Luo, M.N.; Dong, B.; Zhang, K. Game Theoretical Secure Caching Scheme in Multihoming Edge Computing-Enabled Heterogeneous Networks. IEEE Internet Things 2019, 6, 4536–4546. [Google Scholar] [CrossRef]
- Pawlick, J.; Chen, J.T.; Zhu, Q.Y. iSTRICT: An Interdependent Strategic Trust Mechanism for the Cloud-Enabled Internet of Controlled Things. IEEE Trans. Inf. Foren. Sec. 2019, 14, 1654–1669. [Google Scholar] [CrossRef]
- Niu, W.J.; Huang, J.Y.; Xing, Z.; Chen, J.B. Knowledge Spillovers of Medical Big Data Under Hierarchical Medical System and Patients’ Medical Treatment Decisions. IEEE Access 2019, 7, 55770–55779. [Google Scholar] [CrossRef]
- Pawlick, J.; Colbert, E.; Zhu, Q.Y. Modeling and Analysis of Leaky Deception Using Signaling Games with Evidence. IEEE Trans. Inf. Foren. Sec. 2019, 14, 1871–1886. [Google Scholar] [CrossRef]
- Tian, F.Y.; Yan, Z.; Liang, X.Q.; Zhang, P. Trusted Cooperation among Virtual Base Stations in C-RAN. IEEE Access 2018, 6, 57787–57801. [Google Scholar] [CrossRef]
- Zhu, Q.Y.; Fung, C.; Boutaba, R.; Basar, T. GUIDEX: A Game-Theoretic Incentive-Based Mechanism for Intrusion Detection Networks. IEEE J. Sel. Area Comm. 2012, 30, 2220–2230. [Google Scholar] [CrossRef]
- Anand, S.; Subbalakshmi, K.P.; Chandramouli, R. A Quantitative Model and Analysis of Information Confusion in Social Networks. IEEE Trans. Multimed. 2013, 15, 207–223. [Google Scholar] [CrossRef]
- Xu, Q.C.; Su, Z.; Wang, Y.T.; Dai, M.H. A Trustworthy Content Caching and Bandwidth Allocation Scheme with Edge Computing for Smart Campus. IEEE Access 2018, 6, 63868–63879. [Google Scholar] [CrossRef]
- Ahn, S.; Lee, J.; Park, S.; Newaz, S.H.S.; Choi, J.K. Competitive Partial Computation Offloading for Maximizing Energy Efficiency in Mobile Cloud Computing. IEEE Access 2018, 6, 899–912. [Google Scholar] [CrossRef]
- Xu, Q.C.; Su, Z.; Zheng, Q.H.; Luo, M.N.; Dong, B. Secure Content Delivery with Edge Nodes to Save Caching Resources for Mobile Users in Green Cities. IEEE Trans. Ind. Inform. 2018, 14, 2550–2559. [Google Scholar] [CrossRef]
- Duan, J.Q.; Gao, D.Y.; Yang, D.; Foh, C.H.; Chen, H. An Energy-Aware Trust Derivation Scheme with Game Theoretic Approach in Wireless Sensor Networks for IoT Applications. IEEE Internet Things 2014, 1, 58–69. [Google Scholar] [CrossRef]
- Chen, X.; Proulx, B.; Gong, X.W.; Zhang, J.S. Exploiting Social Ties for Cooperative D2D Communications: A Mobile Social Networking Case. IEEE ACM Trans. Netw. 2015, 23, 1471–1484. [Google Scholar] [CrossRef]
- Cao, Y.; Jiang, T.; Chen, X.; Zhang, J.S. Social-Aware Video Multicast Based on Device-to-Device Communications. IEEE Trans. Mob. Comput. 2016, 15, 1528–1539. [Google Scholar] [CrossRef]
- Cho, J.; Wang, Y.T.; Chen, I.; Chan, K.S.; Swami, A. A Survey on Modeling and Optimizing Multi-Objective Systems. IEEE Commun. Surv. Tut. 2017, 19, 1867–1901. [Google Scholar] [CrossRef]
- Waqas, M.; Ahmed, M.; Li, Y.; Jin, D.P.; Chen, S. Social-Aware Secret Key Generation for Secure Device-to-Device Communication via Trusted and Non-Trusted Relays. IEEE Trans. Wirel. Commun. 2018, 17, 3918–3930. [Google Scholar] [CrossRef]
- Wahab, O.A.; Bentahar, J.; Otrok, H.; Mourad, A. Towards Trustworthy Multi-Cloud Services Communities: A Trust-Based Hedonic Coalitional Game. IEEE Trans. Serv. Comput. 2018, 11, 184–201. [Google Scholar] [CrossRef]
- Abdalzaher, M.S.; Samy, L.; Muta, O. Non-zero-sum game-based trust model to enhance wireless sensor networks security for IoT applications. IET Wirel. Sens. Syst. 2019, 9, 218–226. [Google Scholar] [CrossRef]
- Rani, R.; Kumar, S.; Dohare, U. Trust Evaluation for Light Weight Security in Sensor Enabled Internet of Things: Game Theory Oriented Approach. IEEE Internet Things 2019, 6, 8421–8432. [Google Scholar] [CrossRef]
- Wu, Q.H.; Qin, B.; Zhang, L.; Domingo-Ferrer, J.; Farràs, O.; Manjón, J.A. Contributory Broadcast Encryption with Efficient Encryption and Short Ciphertexts. IEEE Trans. Comput. 2016, 65, 466–479. [Google Scholar] [CrossRef]
- Ruan, O.; Chen, J.; Zhang, M.W. Provably Leakage-Resilient Password-Based Authenticated Key Exchange in the Standard Model. IEEE Access 2017, 5, 26832–26841. [Google Scholar] [CrossRef]
- John, L.; John, G.B.; Parker, M.; Sauser, B.J.; Wade, J.P. Self-Organizing Cooperative Dynamics in Government Extended Enterprises. IEEE Syst. J. 2018, 12, 2905–2916. [Google Scholar] [CrossRef]
- Wu, Y.Z.; Lyu, Y.Q.; Shi, Y.C. Cloud storage security assessment through equilibrium analysis. Tsinghua Sci. Technol. 2019, 24, 6. [Google Scholar] [CrossRef]
- Jin, C.L.; Dijk, M.V. Secure and Efficient Initialization and Authentication Protocols for SHIELD. IEEE Trans. Depend. Secure 2019, 16, 156–173. [Google Scholar] [CrossRef]
- Fang, W.D.; Zhang, W.X.; Yang, Y.; Yang, L.; Wei, C. A resilient trust management scheme for defending against reputation time-varying attacks based on BETA distribution. Sci. China Inform. Sci. 2017, 60. [Google Scholar] [CrossRef]
- Yu, H.; Shen, Z.Q.; Leung, C.; Miao, C.Y.; Lesser, V.R. A Survey of Multi-Agent Trust Management Systems. IEEE Access 2013, 1, 35–50. [Google Scholar]
- Fang, W.D.; Zhang, C.L.; Shi, Z.D.; Zhao, Q.; Shan, L.H. BTRES: Beta-based Trust and Reputation Evaluation System for Wireless Sensor Networks. J. Netw. Comput. Appl. 2016, 59, 88–94. [Google Scholar] [CrossRef]
- Abbass, H.; Greenwood, G.; Petraki, E. The N-Player Trust Game and its Replicator Dynamics. IEEE Trans. Evolut. Comput. 2016, 20, 470–474. [Google Scholar] [CrossRef]
- Chica, M.; Chiong, R.; Kirley, M.; Ishibuchi, H. A Networked N-Player Trust Game and Its Evolutionary Dynamics. IEEE Trans. Evolut. Comput. 2018, 22, 866–878. [Google Scholar] [CrossRef]
- Zhu, H.J.; Du, S.G.; Gao, Z.Y.; Dong, M.X.; Cao, Z.F. A Probabilistic Misbehavior Detection Scheme toward Efficient Trust Establishment in Delay-Tolerant Networks. IEEE Trans. Parall. Distr. 2014, 25, 22–32. [Google Scholar] [CrossRef]
- Ding, W.P.; Wang, J.D.; Guan, Z.J.; Shi, Q. Ensemble feature selection integrating elitist roles and quantum game model. J. Syst. Eng. Electron. 2015, 26, 584–594. [Google Scholar] [CrossRef]
- Zhang, X.; Xue, G.L.; Yu, R.Z.; Yang, D.J.; Tang, J. Keep Your Promise: Mechanism Design against Free-Riding and False-Reporting in Crowdsourcing. IEEE Internet Things 2015, 2, 562–572. [Google Scholar] [CrossRef]
- Fang, W.D.; Zhang, W.X.; Shan, L.H.; Ji, X.H.; Jia, G.Q. DDTMS: Dirichlet-Distribution-Based Trust Management Scheme in Internet of Things. Electronics 2019, 8, 744. [Google Scholar] [CrossRef]
- Aloqaily, M.; Kantarci, B.; Mouftah, H.T. Multiagent/multiobjective interaction game system for service provisioning in vehicular cloud. IEEE Access 2016, 4, 3153–3168. [Google Scholar] [CrossRef]
- Rishwaraj, G.; Ponnambalam, S.G.; Loo, C.K. Heuristics-Based Trust Estimation in Multiagent Systems Using Temporal Difference Learning. IEEE Trans. Cybern. 2017, 47, 1925–1935. [Google Scholar] [CrossRef]
- Pouryazdan, M.; Fiandrino, C.; Kantarci, B.; Soyata, T.; Kliazovich, D.; Bouvry, P. Intelligent Gaming for Mobile Crowd-Sensing Participants to Acquire Trustworthy Big Data in the Internet of Things. IEEE Access 2017, 5, 22209–22223. [Google Scholar] [CrossRef]
- Chen, Y.; Wu, S.N.; Li, J.; Fu, X.M. NCShield: Protecting Decentralized, Matrix Factorization-Based Network Coordinate Systems. IEEE Trans. Serv. Comput. 2017, 10, 244–257. [Google Scholar] [CrossRef]
- Lorenzo, B.; Shafigh, A.S.; Liu, J.Q.; González-Castaño, F.J.; Fang, Y.G. Data and Spectrum Trading Policies in a Trusted Cognitive Dynamic Network Architecture. IEEE ACM Trans. Netw. 2018, 26, 1502–1516. [Google Scholar] [CrossRef]
- Li, Y.; Zhang, Z.F.; Wang, H.G.; Yang, Q. SERS: Social-Aware Energy-Efficient Relay Selection in D2D Communications. IEEE Trans. Veh. Technol. 2018, 67, 5331–5345. [Google Scholar] [CrossRef]
- Aroyo, A.M.; Rea, F.; Sandini, G.; Sciutti, A. Trust and Social Engineering in Human Robot Interaction: Will a Robot Make You Disclose Sensitive Information, Conform to Its Recommendations or Gamble? IEEE Robot. Autom. Lett. 2018, 3, 3701–3708. [Google Scholar] [CrossRef]
- Moghadam, R.; Modares, H. Resilient Autonomous Control of Distributed Multiagent Systems in Contested Environments. IEEE Trans. Cybern. 2019, 49, 3957–3967. [Google Scholar] [CrossRef]
- Wu, X.; He, J.S.; Xu, F.; Zhang, X. A distributed decision-making mechanism for wireless P2P networks. J. Commun. Netw. 2009, 11, 359–367. [Google Scholar] [CrossRef]
- Xu, J.L.; Wang, S.G.; Bhargava, B.K.; Yang, F.C. A Blockchain-Enabled Trustless Crowd-Intelligence Ecosystem on Mobile Edge Computing. IEEE Trans. Ind. Inform. 2019, 15, 3538–3547. [Google Scholar] [CrossRef]
- Kang, J.W.; Xiong, Z.H.; Niyato, D.; Ye, D.D.; Kim, D.I.; Zhao, J. Toward Secure Blockchain-Enabled Internet of Vehicles: Optimizing Consensus Management Using Reputation and Contract Theory. IEEE Trans. Veh. Technol. 2019, 68, 2906–2920. [Google Scholar] [CrossRef]
- Zhang, Q.P.; DiFranzo, D.; Gloria, M.J.K.; Makni, B.; Hendler, J.A. Analyzing the Flow of Trust in the Virtual World with Semantic Web Technologies. IEEE Trans. Comput. Soc. Syst. 2018, 5, 807–815. [Google Scholar] [CrossRef]
- Wang, P.W.; Meng, J.; Chen, J.C.; Liu, T.; Zhan, Y.; Tsai, W.; Jin, Z. Smart Contract-Based Negotiation for Adaptive QoS-Aware Service Composition. IEEE Trans. Parall. Distr. 2019, 30, 1403–1420. [Google Scholar] [CrossRef]
- Zhang, L.; Wu, Q.H.; Domingo-Ferrer, J.; Qin, B.; Dong, Z.M. Round-Efficient and Sender-Unrestricted Dynamic Group Key Agreement Protocol for Secure Group Communications. IEEE Trans. Inf. Foren. Sec. 2015, 10, 2352–2364. [Google Scholar] [CrossRef]

| Dynamic Game | Static Game | Non-Cooperative Game | Cooperative Game |
| Kim [32] Ho et al. [33] Cho [34] Al-Talabani et al. [35] Muthukumar and Sahai [36] Pawlick and Zhu [37] Yang et al. [38] Li et al. [39] Wang et al. [40] Gao et al. [41] Xu et al. [42] Pawlick et al. [43] Niu et al. [44] Pawlick et al. [45] Shi et al. [31] Maharjan et al. [18] Zonouz et al. [29] | Tian et al. [46] De Paola et al. [19] | Zhu et al. [47] Anand et al. [48] Xu et al. [49] Ahn et al. [50] Xu et al. [51] Borjigin et al. [24] De Paola et al. [20] Gong et al. [22] Basilico et al. [30] | Duan et al. [52] Chen et al. [53] Cao et al. [54] Cho et al. [55] Waqas et al. [56] Wahab et al. [57] Abdalzaher et al. [58] Rani et al. [59] |
| Security Game | Trust Game | Others | |
| Wu et al. [60] Ruan et al. [61] John et al. [62] Wu et al. [63] Jin and van Dijk [64] | Yu et al. [66] Abbass et al. [68] Chica et al. [69] Hu et al. [6] | Zhu et al. [70] Ding et al. [71] Zhang et al. [72] Aloqaily et al. [74] Rishwaraj et al. [75] Pouryazdan et al. [76] Chen et al. [77] Lorenzo et al. [78] Li et al. [79] Aroyo et al. [80] Moghadam and Modares [81] Cui et al. [28] Yin et al. [26] Chen et al. [27] Li et al. [14] |
| Trust Model | Trust Mechanism | Trust Framework |
|---|---|---|
| Duan et al. [52] Chen et al. [53] Cho et al. [34] Rishwaraj et al. [75] Chica et al. [69] Xu et al. [49] Li et al. [79] Wang et al. [40] Abdalzaher et al. [58] Jin and Van Dijk [64] Rani et al. [59] | Wu et al. [82] Kim [32] Lorenzo et al. [78] Xu et al. [42] Pawlick et al. [43] | Wahab et al. [57] Wang et al. [15] |
| Distributed Network | Centralized Network | Social Network |
|---|---|---|
| Wu et al. [82] Zhu et al. [47] Ho et al. [33] Duan et al. [52] Cho et al. [56] Yang et al. [38] Li et al. [39] Gao et al. [41] Abdalzaher et al. [58] Wang et al. [86] Kang et al. [84] Rani et al. [59] | Kim [32] Yu et al. [66] Zhu et al. [70] Aloqaily et al. [74] Cao et al. [54] Abbass et al. [68] Rishwaraj et al. [75] Pawlick and Zhu [37] Xu et al. [49] Ahn et al. [50] Lorenzo et al. [78] Xu et al. [51] Tian et al. [46] Xu et al. [83] Xu et al. [42] Pawlick et al. [43] Moghadam and Modares [81] | Anand et al. [48] Chen et al. [53] Chica et al. [69] Zhang et al. [85] Li et al. [79] Wahab et al. [57] Wang et al. [15] Yan et al. [16] |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Huang, L.; Jia, G.; Fang, W.; Chen, W.; Zhang, W. Towards Security Joint Trust and Game Theory for Maximizing Utility: Challenges and Countermeasures. Sensors 2020, 20, 221. https://doi.org/10.3390/s20010221
Huang L, Jia G, Fang W, Chen W, Zhang W. Towards Security Joint Trust and Game Theory for Maximizing Utility: Challenges and Countermeasures. Sensors. 2020; 20(1):221. https://doi.org/10.3390/s20010221
Chicago/Turabian StyleHuang, Libingyi, Guoqing Jia, Weidong Fang, Wei Chen, and Wuxiong Zhang. 2020. "Towards Security Joint Trust and Game Theory for Maximizing Utility: Challenges and Countermeasures" Sensors 20, no. 1: 221. https://doi.org/10.3390/s20010221
APA StyleHuang, L., Jia, G., Fang, W., Chen, W., & Zhang, W. (2020). Towards Security Joint Trust and Game Theory for Maximizing Utility: Challenges and Countermeasures. Sensors, 20(1), 221. https://doi.org/10.3390/s20010221







