An Enhanced Lightweight IoT-based Authentication Scheme in Cloud Computing Circumstances
Abstract
1. Introduction
1.1. Related Work
1.2. Contribution
2. Review and Security Analysis of Zhou’s Scheme
2.1. Registration Phase
2.1.1. User Registration Sub-Phase
2.1.2. Cloud Server Registration Sub-phase
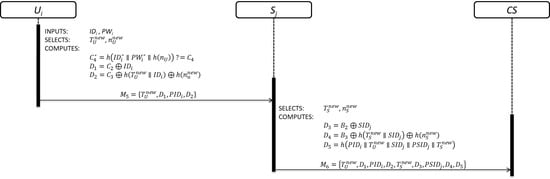
2.2. Authentication Phase
2.3. Security Vulnerabilities
- The attacker is a legal member of the system which means that he/she was registered by CS and he/she has all the security parameters.
- The attacker can control the public communication channel giving him/her the possibility to intercept, insert, store, delete, or modify any message.
- The attacker has high computational power connected to the public communication channel.
2.3.1. Insider Attack
2.3.2. Man-in-the-Middle Attack
2.4. Security Drawbacks
2.4.1. Fails to Provide Mutual Authentication
2.4.2. Fails to Protect Secret Key
3. Proposed Scheme
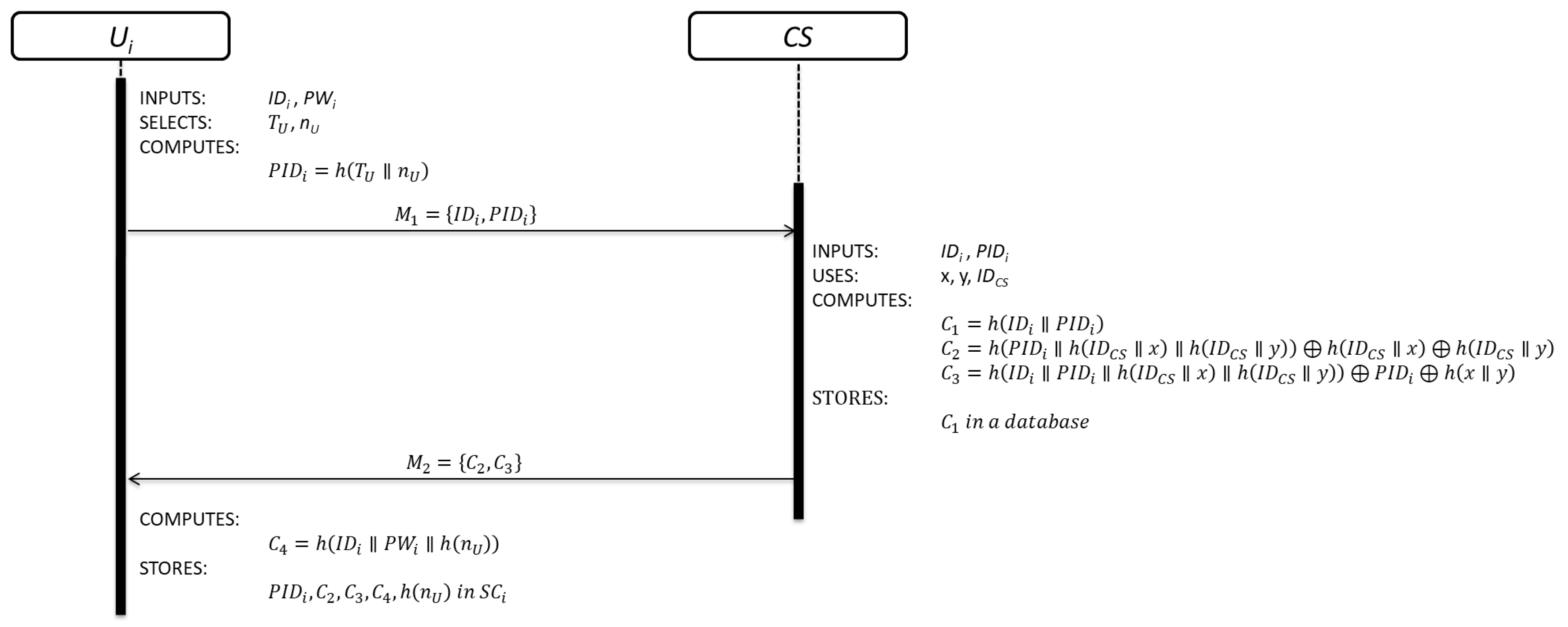
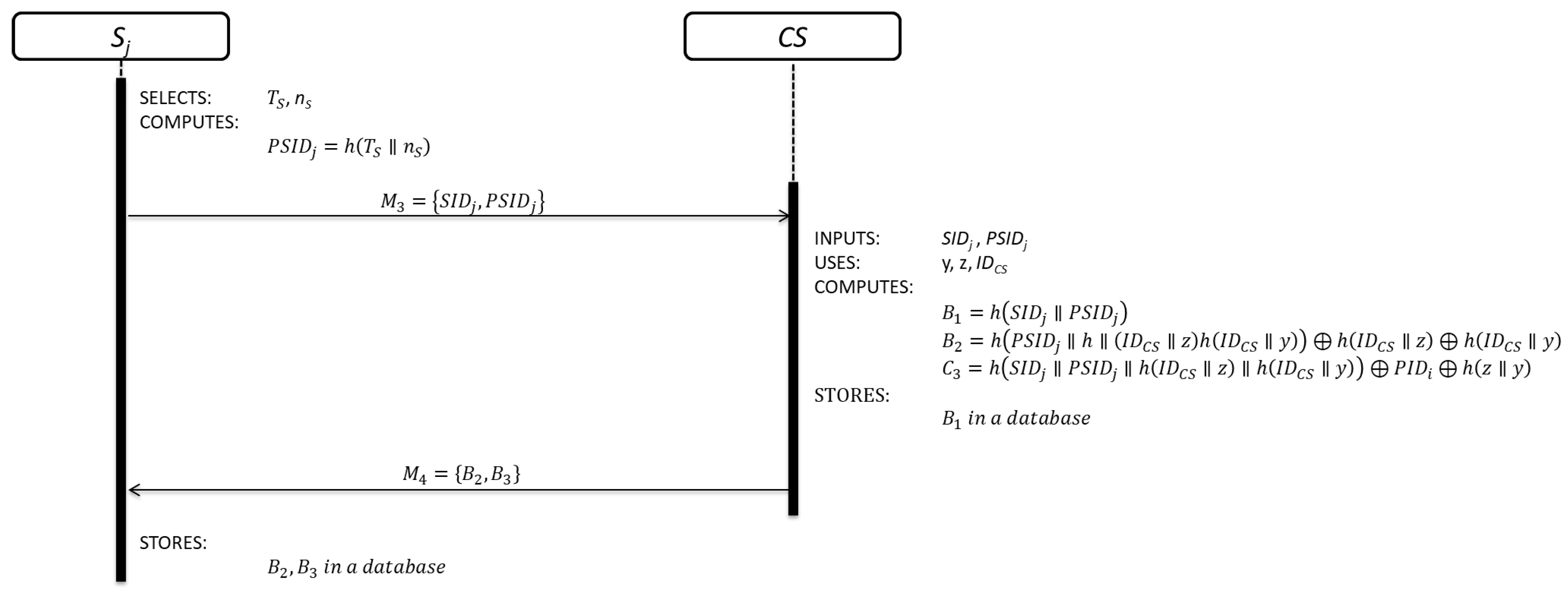
3.1. Registration Phase
3.1.1. User Registration Sub-Phase
3.1.2. Cloud Server Registration
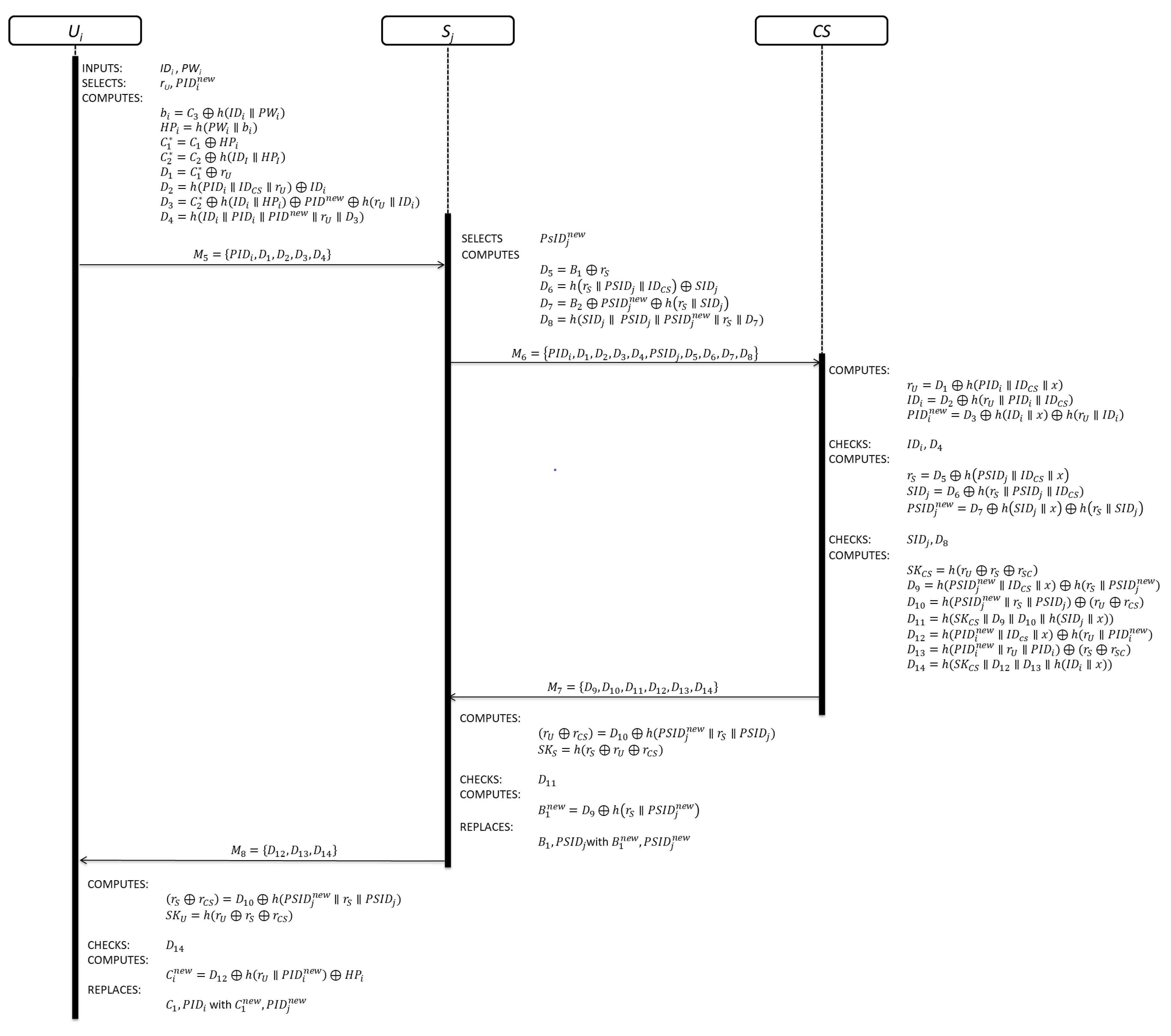
3.2. Login Phase
3.3. Authentication Phase
3.3.1. User Authentication
3.3.2. Server Authentication
3.3.3. Evidence of Connection Attempt
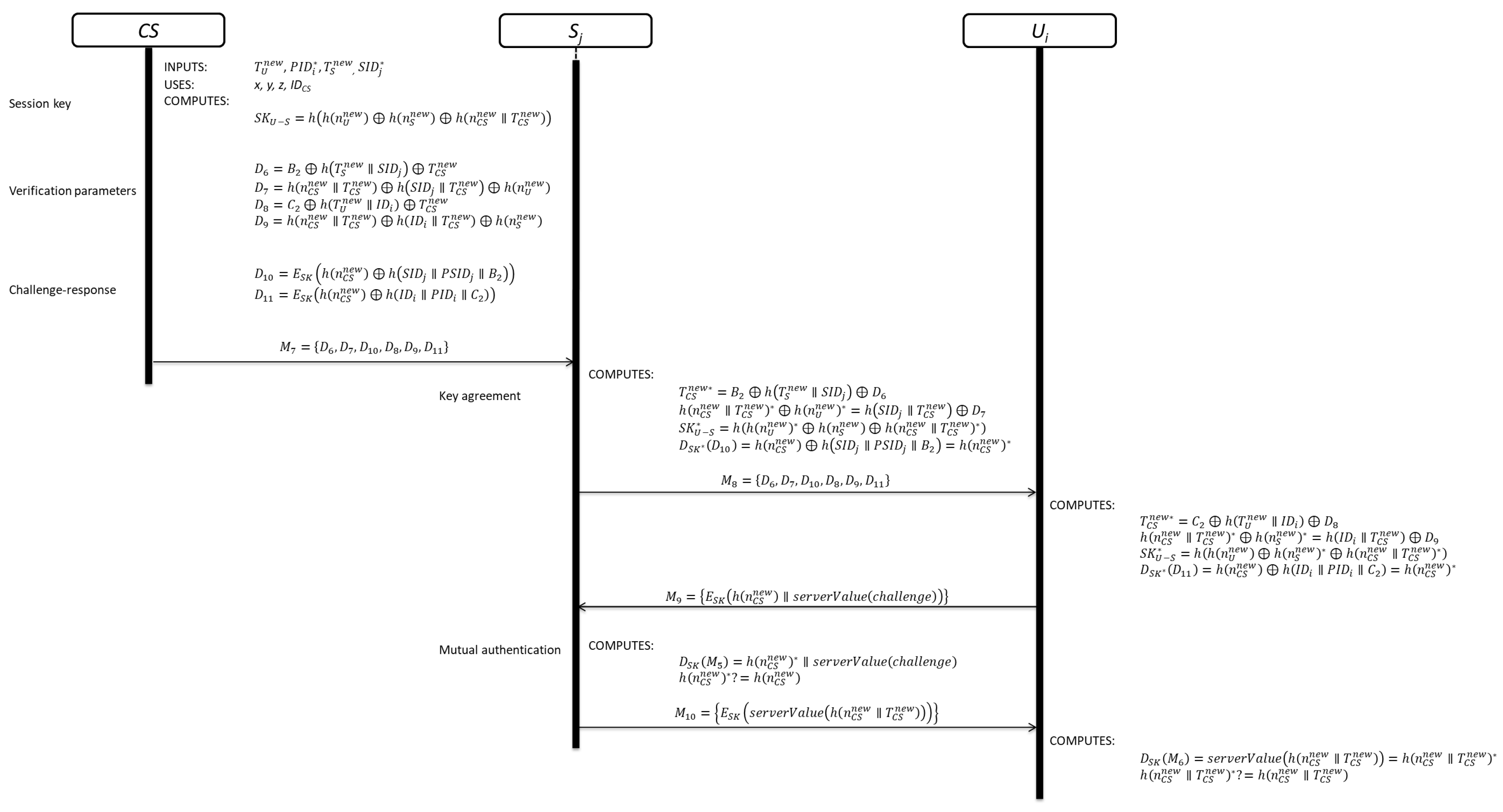
3.4. Key Agreement Phase
3.4.1. Session Key Creation
3.4.2. Server Session Key
3.4.3. User Session Key
3.5. Mutual Authentication
3.6. Password Change Phase
4. Security Analysis and Performance Evaluation
4.1. Informal Cryptanalysis
4.1.1. User Anonymity
4.1.2. Off-line User Identity and Password Guessing Attack
4.1.3. Privileged Insider Attack
4.1.4. Impersonation Attack
4.1.5. Replay Attack
4.2. Security of Session Key
4.2.1. Known-key Security
4.2.2. Forward Secrecy
4.3. Countermeasures
4.3.1. Local Protection against Malicious Users
4.3.2. Mutual Authentication
4.3.3. Evidence of Connection Attempt
4.4. Security Comparison
4.5. Computational-cost Comparison
- Th represents a hash function.
- TS represents an encryption/decryption operation using AES algorithm.
4.6. Communication-Cost Comparison
- Case 1: any identity, password, pseudo-identity, timestamp, random nonce, and hash output are 128 bits.
- Case 2: any identity, password, pseudo-identity, timestamp, random nonce, and hash output are 256 bits.
- The block length of the symmetric encryption is 128 bits.
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Amin, R.; Kumar, N.; Biswas, G.P.; Iqbal, R.; Chang, V. A light weight authentication protocol for IoT-enabled devices in distributed cloud computing environment. Future Gener. Comput. Syst. 2018, 78, 1005–1019. [Google Scholar] [CrossRef]
- Noura, M.; Atiquzzman, M.; Gaedke, M. Interoperability in internet of things: Taxonomies and open challenges. Mob. Netw. Appl. 2018. [Google Scholar] [CrossRef]
- Foster, I.; Zhao, Y.; Raicu, I.; Lu, S. Cloud computing and grid computing 360-degree compared. In Proceedings of the Workshop on Grid Computing Environments (GCE), Austin, TX, USA, 12–16 November 2008. [Google Scholar] [CrossRef]
- Sova, P. Cloud computing in brief. IOSR J. Comput. Eng. 2016, 18, 101–103. [Google Scholar]
- Ferrag, M.A.; Maglaras, L.A.; Janicke, H.; Jiang, J.; Shu, L. Authentication protocols for internet of things: A comprehensive survey. Secur. Commun. Netw. 2017. [Google Scholar] [CrossRef]
- El-Hajj, M.; Fadlallah, A.; Chamoun, M.; Serhrouchni, A. A survey of internet of things (IoT) Authentication schemes. Sensors 2019, 19, 1141. [Google Scholar] [CrossRef]
- Yu, W.; Liang, F.; He, X.; Grant Hatcher, W.; Lu, C.; Lin, J.; Yang, X. A survey on the edge computing for the internet of things. IEEE Access 2017, 6, 6900–6919. [Google Scholar] [CrossRef]
- Fernández Maimó, L.; Huertas Celdrán, A.; Perales Gómez, A.L.; García Clemente, F.J.; Weimer, J.; Lee, I. Intelligent and dynamic ransomware spread detection and mitigation in integrated clinical environments. Sensors 2019, 19, 1114. [Google Scholar] [CrossRef]
- Baker, S.B.; Xiang, W.; Atkinson, I. Internet of things for smart healthcare: Technologies, challenges, and opportunities. IEEE Access 2017, 5, 26521–26544. [Google Scholar] [CrossRef]
- Jang, Q.; Ma, J.; Yang, C.; Ma, X.; Shen, J.; Chaudhry, S.A. Efficient end-to-end authentication protocol for wearable health monitoring systems. Comput. Electr. Eng. 2017, 63, 182–195. [Google Scholar] [CrossRef]
- Zanella, A.; Bui, N.; Castellani, A.; Vangelista, L.; Zorzi, M. Internet of things for smart cities. IEEE Internet Things J. 2014, 1, 22–32. [Google Scholar] [CrossRef]
- Perera, C.; Harold Liu, C.; Jayawardena, S.; Chen, M. A survey on internet of things from industrial market perspective. IEEE Access 2015, 2, 1660–1679. [Google Scholar] [CrossRef]
- El-Sayed, H.; Sankar, S.; Prasad, M.; Puthal, D.; Gupta, A.; Mohanty, M.; Lin, C.T. Edge of things: The big picture on the integration of edge, IoT and the cloud in a distributed computing environment. IEEE Access 2017, 6, 1706–1717. [Google Scholar] [CrossRef]
- Jiang, Q.; Qian, Y.; Ma, J.; Ma, X.; Cheng, Q.; Wei, F. User centric three-factor authentication protocol for cloud-assited wearable devices. Int. J. Commun. Syst. 2009, 9, e3900. [Google Scholar] [CrossRef]
- Madhusudhan, R.; Mittal, R.C. Dynamic id-based remote user password authentication schemes using smart cards: A review. J. Netw. Comput. Appl. 2012, 35, 1235–1248. [Google Scholar] [CrossRef]
- Wang, D.; He, D.; Wang, P.; Chu, C.-H. Anonymous two-factor authentication in distributed systems: Certain goals are beyond attainment. IEEE Trans. Dependable Secur. Comput. 2015, 12, 428–442. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. Two birds with one stone: Two-factor authentication with security beyond conventional bound. IEEE Trans. Dependable Secur. Comput. 2018, 15, 708–722. [Google Scholar] [CrossRef]
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Hwang, T.; Chen, Y.; Laih, C.S. Non-interactive password authentication without password tables. In Proceedings of the 1990 IEEE Region 10 Conference on Computer and Communication Systems, Hong Kong, China, 24–27 September 1990. [Google Scholar]
- Lin, L.C.; Hwang, M.S.; Li, L.H. A new remote user authentication scheme for multi-server architecture. Future Gener. Comput. Syst. 2003, 19, 13–22. [Google Scholar] [CrossRef]
- Li, L.; Lin, L.; Hwang, M.S. A remote password authentication scheme for multi-server architecture using neural networks. IEEE Trans. Neural Netw. 2001, 12, 1498–1504. [Google Scholar] [PubMed]
- Liao, Y.P.; Wang, S.S. A secure dynamic ID based remote user authentication scheme for multi-server environment. Comput. Stand. Interfaces 2009, 31, 24–29. [Google Scholar] [CrossRef]
- Hsiang, C.; Shih, W.K. Improvement of the secure dynamic ID based remote user authentication scheme for multi-server environment. Comput. Stand. Interfaces 2009, 31, 1118–1123. [Google Scholar] [CrossRef]
- Martínez-Peláez, R.; Rico-Novella, F.; Satizábal, C.; Pomykala, J. Efficient and secure dynamic ID-based remote user authentication scheme with session key agreement for multi-server environment. Int. J. Netw. Secur. Its Appl. 2010, 2, 106–116. [Google Scholar] [CrossRef]
- Kim, M.; Park, N.; Won, D. Security Improvement on a Dynamic ID-Based Remote User Authentication Scheme with Session Key Agreement for Multi-server Environment. In Computer Applications for Security, Control and System Engineering; Springer: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Li, X.; Xiong, Y.P.; Ma, J.; Wang, W.D. An efficient and security dynamic identity based authentication protocol for multi-server architecture using smartcards. J. Netw. Comput. Appl. 2012, 35, 763–769. [Google Scholar] [CrossRef]
- Sood, S.K.; Sarje, A.K.; Singh, K. A secure dynamic identity based authentication protocol for multiserver architecture. J. Netw. Comput. Appl. 2011, 34, 609–618. [Google Scholar] [CrossRef]
- Xue, K.; Hong, P.; Ma, C. A lightweight dynamic pseudonym identity based authentication and key agreement protocol without verification tables for multi-server architecture. J. Comput. Syst. Sci. 2014, 80, 195–206. [Google Scholar] [CrossRef]
- Challa, S.; Das, A.K.; Gope, P.; Kumar, N.; Wu, F.; Vasilakos, A.V. Design and analysis of authenticated key agreement scheme in cloud-assisted cyber-physical systems. Future Gener. Comput. Syst. 2018. [Google Scholar] [CrossRef]
- Zhou, L.; Li, X.; Yeh, K.H.; Su, C.; Chiu, W. Lightweight IoT-based authentication scheme in cloud computing circumstance. Future Gener. Comput. Syst. 2019, 91, 244–251. [Google Scholar] [CrossRef]
- Amin, R.; Biswas, G.P. A secure light weight scheme for user authentication and key agreement in multi-gateway based wireless sensor networks. Ad Hoc Netw. 2016, 36, 58–80. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X.; Shen, J.; Raymond-Choo, K.K.; Wazid, M.; Das, A.K. An efficient authentication and key agreement scheme for multi-gateway wireless sensor networks in IoT deployment. J. Netw. Comput. Appl. 2017, 89, 72–85. [Google Scholar] [CrossRef]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Advances in Cryptology; Wienner, M., Ed.; Springer: Berlin, Germany, 1999; pp. 388–397. [Google Scholar]
- Messerger, T.S.; Dabbish, E.A.; Sloan, R.H. Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 2002, 51, 541–552. [Google Scholar] [CrossRef]



| Symbol | Description |
|---|---|
| User | |
| Cloud server | |
| Control server | |
| Smart card of | |
| Identity of , , , respectively | |
| Pseudo-identity of , , respectively | |
| Password of | |
| Secret keys of Secret keys are long integers | |
| Random nonce of , , , respectively | |
| Timestamp of , , , respectively | |
| Session key between and | |
| Symmetric encryption/decryption using | |
| Collision free one-way hash function | |
| Exclusive-OR operation | |
| Concatenation operation | |
| Secure communication channel | |
| Open communication channel |
| Security Property | Xue et al. | Amin et al. | Zhou et al. | Our Scheme |
|---|---|---|---|---|
| Provide evidence of connection attempt | fails | fails | fails | success |
| Provide mutual authentication | fails | fails | fails | success |
| Provide user anonymity | fails | success | ||
| Resist impersonation attack | fails | fails | fails | success |
| Resist off-line user identity/password attack | fails | success | ||
| Resist privileged-insider attack | fails | fails | success | |
| Resist replay attack | fails | success |
| Phase | Xue et al. | Amin et al. | Zhou et al. | Our Scheme | |
|---|---|---|---|---|---|
| Registration | |||||
| Login | |||||
| Authentication | |||||
| Total |
| Xue et al. | Amin et al. | Zhou et al. | Our | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Op | Case 1 | Case 2 | Op | Case 1 | Case 2 | Op | Case 1 | Case 2 | Op | Case 1 | Case 2 | ||
| R | 3Th | 0.01551 | 0.0000984 | 3Th | 0.01551 | 0.0000984 | 3TH | 0.01551 | 0.0000984 | 2Th | 0.01034 | 0.0000656 | |
| 0Th | 0 | 0 | 0Th | 0 | 0 | 0TH | 0 | 0 | 1Th | 0.00517 | 0.0000328 | ||
| 4Th | 0.02068 | 0.0001312 | 4Th | 0.02068 | 0.0001312 | 4TH | 0.02068 | 0.0001312 | 12Th | 0.06204 | 0.0003936 | ||
| L | 6Th | 0.03102 | 0.0001968 | 6Th | 0.03102 | 0.0001968 | 6Th | 0.03102 | 0.0001968 | 3Th | 0.01551 | 0.0000984 | |
| 3Th | 0.01551 | 0.0000984 | 1Th | 0.00517 | 0.0000328 | 3Th | 0.01551 | 0.0000984 | 3Th | 0.01551 | 0.0000984 | ||
| 0Th | 0 | 0 | 0Th | 0 | 0 | 0Th | 0 | 0 | 0Th | 0 | 0 | ||
| A | 3Th | 0.01551 | 0.0000984 | 3Th | 0.01551 | 0.0000984 | 4Th | 0.02068 | 0.0001312 | 4Th + 3Ts | 0.08512 | 0.0644467 | |
| 3Th | 0.01551 | 0.0000984 | 3Th | 0.01551 | 0.0000984 | 4Th | 0.02068 | 0.0001312 | 2Th + 3Ts | 0.07478 | 0.0643811 | ||
| 14Th | 0.07238 | 0.0004592 | 10Th | 0.0517 | 0.000328 | 19Th | 0.09823 | 0.0006232 | 21Th + 2Ts | 0.15153 | 0.0435658 | ||
| Total | 36Th | 0.18612 | 0.0011808 | 30Th | 0.1551 | 0.000984 | 43Th | 0.22231 | 0.0014104 | 48Th + 8Ts | 0.420000 | 0.173082 | |
| Xue et al. | Amin et al. | Zhou et al. | Our Scheme | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Length | Case 1 | Case 2 | Length | Case 1 | Case 2 | Length | Case 1 | Case 2 | Length | Case 1 | Case 2 | ||
| R | 3 | 384 | 768 | 2 | 256 | 512 | 2 | 256 | 512 | 2 | 256 | 512 | |
| 2 | 256 | 512 | 2 | 256 | 512 | 2 | 256 | 512 | 2 | 256 | 512 | ||
| 2 | 256 | 512 | 3 | 384 | 768 | 6 | 768 | 1536 | 4 | 512 | 1024 | ||
| ST | 896 | 1792 | 896 | 1792 | 1280 | 2560 | 1024 | 2048 | |||||
| L | 6 | 768 | 1536 | 5 | 640 | 1280 | 5 | 640 | 1280 | 4 | 512 | 1024 | |
| 11 | 1408 | 2816 | 9 | 1152 | 2304 | 10 | 1280 | 2560 | 9 | 1152 | 2304 | ||
| 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | ||
| ST | 2176 | 4352 | 1792 | 3584 | 1920 | 3840 | 1664 | 3328 | |||||
| A | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 2 | 256 | 512 | |
| 2 | 256 | 512 | 2 | 256 | 512 | 3 | 384 | 768 | 5 | 640 | 1280 | ||
| 4 | 512 | 1024 | 4 | 512 | 1024 | 6 | 768 | 1536 | 6 | 768 | 1536 | ||
| ST | 768 | 1536 | 768 | 1536 | 1152 | 2304 | 1664 | 3328 | |||||
| T | 30 | 3840 | 7680 | 27 | 3456 | 6912 | 34 | 4352 | 8704 | 34 | 4352 | 8704 | |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Martínez-Peláez, R.; Toral-Cruz, H.; Parra-Michel, J.R.; García, V.; Mena, L.J.; Félix, V.G.; Ochoa-Brust, A. An Enhanced Lightweight IoT-based Authentication Scheme in Cloud Computing Circumstances. Sensors 2019, 19, 2098. https://doi.org/10.3390/s19092098
Martínez-Peláez R, Toral-Cruz H, Parra-Michel JR, García V, Mena LJ, Félix VG, Ochoa-Brust A. An Enhanced Lightweight IoT-based Authentication Scheme in Cloud Computing Circumstances. Sensors. 2019; 19(9):2098. https://doi.org/10.3390/s19092098
Chicago/Turabian StyleMartínez-Peláez, Rafael, Homero Toral-Cruz, Jorge R. Parra-Michel, Vicente García, Luis J. Mena, Vanessa G. Félix, and Alberto Ochoa-Brust. 2019. "An Enhanced Lightweight IoT-based Authentication Scheme in Cloud Computing Circumstances" Sensors 19, no. 9: 2098. https://doi.org/10.3390/s19092098
APA StyleMartínez-Peláez, R., Toral-Cruz, H., Parra-Michel, J. R., García, V., Mena, L. J., Félix, V. G., & Ochoa-Brust, A. (2019). An Enhanced Lightweight IoT-based Authentication Scheme in Cloud Computing Circumstances. Sensors, 19(9), 2098. https://doi.org/10.3390/s19092098