1. Introduction
With the continuous maturation of intelligence equipment technology, the deepening of swarm intelligence research, and the improvement of distributed multi-sensor fusion technology, more and more unmanned operations are beginning to adopt the collaborative self-organization of multi-vehicle clusters. The collaborative work of multiple unmanned vehicles requires effective decision-making and management. Some groups of unmanned vehicles can be controlled by humans. However, the situation for most groups of unmanned vehicles is that the nature of tasks, communication ability, decision-making time, etc., make it impossible for human beings to participate in decision making. These groups of unmanned vehicles must therefore realize unmanned decision-making and management. Generally, each member of such groups has certain decision-making ability through devices such as embedded processors, however how the whole group makes collaborative decisions is still a difficult problem.
The problem of the generation of formations of multiple unmanned vehicles is a typical group decision-making problem with distributed information fusion. However, the formation generation problem is less studied than popular problems such as target allocation, formation control, and sensor networks. Reference [
1] analyzed the formation structure of multiple UAVs in different numbers and different models. Study [
2] established an adjustable unmanned vehicle formation model according to the environment. Study [
3] analyzed the different characteristics of different unmanned vehicle formations by observing and studying birds. Reference [
4] proposed an unmanned vehicle formation structure that could adapt to large-scale intelligent vehicles. Study [
5] used taxonomy to give a collaborative evaluation method for a UAV group in an unknown confrontation environment. Reference [
6] described an unmanned vehicle formation construction method without communication through relative navigation. Study [
7] described a task-based unmanned vehicle formation construction method of leader-follower. Study [
8] presented a novel approach to a position control problem in rigid formations of nonholonomic UAVs. Reference [
9] described a track guidance method for formation flight of UAVs. Study [
10] presented a multirotor aircraft formation flight control method with collision avoidance capability. Reference [
11] presented a coordinated flight control method for hypersonic glide vehicles with multiple no-fly-zone constraints. Existing researches on formations of unmanned vehicles have paid more attention to formation maintenance and have achieved rich results. Study [
12] proposed a scheme for sharing sensor information among multiple UAVs. Study [
13] proposed a new multi-UAV task allocation method. Reference [
14] designed a network based on multiple UAVs. The above studies conducted an in-depth analysis of the formation of unmanned vehicles. The contents analyzed include: the type of formation, the formation evaluation, the method of the UAVs to reach the formation, the communication method used by the formation, etc. However, formation in many studies is manually specified or determined according to the motion relationship of the formation unmanned vehicles. Little attention was paid to the formation generation methods and algorithms. This paper will supplement studies for the unmanned vehicles formation research in this part.
In essence, the formation generation problem is a decision-making problem. For the problem of unmanned group decision-making, there are two kinds of general schemes: centralized decision-making and distributed decision-making.
In centralized decision-making groups, a member usually acts as the "decision center". The “decision center” determines the actions of all members of the group. This approach is simple and easy to implement, but it has two fatal shortcomings: (1) the huge calculations in the “decision center”; and (2) the group’s requirement of high communication ability requirement. For example, even the members farthest from the “decision center” must communicate directly with the “decision center”. This leads to a high demand for the effective distance of communication equipment. To overcome the above two shortcomings, some researchers have adopted the method of "distributed computing and centralized decision-making", while others have used a method of information communicating step by step among the groups. However, these methods bring difficulties: the former reduced the calculation amount of the "decision center" and increased the communication traffic, and the latter increased the communication delay.
The fundamental way to overcome the shortcomings of centralized decision-making is distributed decision-making. Distributed decision-making means that every member of a group calculates and makes decisions. Each member only communicates with members within a certain range. On this basis, members act according to certain established rules. With the action of the above process, the group finally achieves a state of good coordination among members and achieves the task requirements together.
The emerging Internet of Things technology provides an effective way to organize UAVs. Study [
15] introduced the basic method of UAV-based IoT taking crowd surveillance as an example. Reference [
16] introduced how to select the appropriate UAVs for a particular IoT task. Study [
17] proposed algorithms for UAV path planning using IoT sensor networks. Study [
18] explained the network architecture for the UAV-based IoT. The above studies proved the feasibility of UAVs group and IoT collaborative application from the adaptation of IoT and UAV, network structure and UAV applications under IoT support. Based on these studies, it is an effective method to apply the distributed decision algorithm of the UAVs group in IoT.
When the group has both centralized decision making and distributed decision making capabilities, a mixed strategy can be used. The mixed strategy has a variety of specific solutions, such as: when a member’s computing performance is high and the communication state is good, the group adopts centralized decision, and when the communication quality is degraded, the distributed decision is adopted. Even groups can allocate decision tasks to members based on events trigger. Mixed strategy is an advanced decision-making form based on a highly intelligent group.
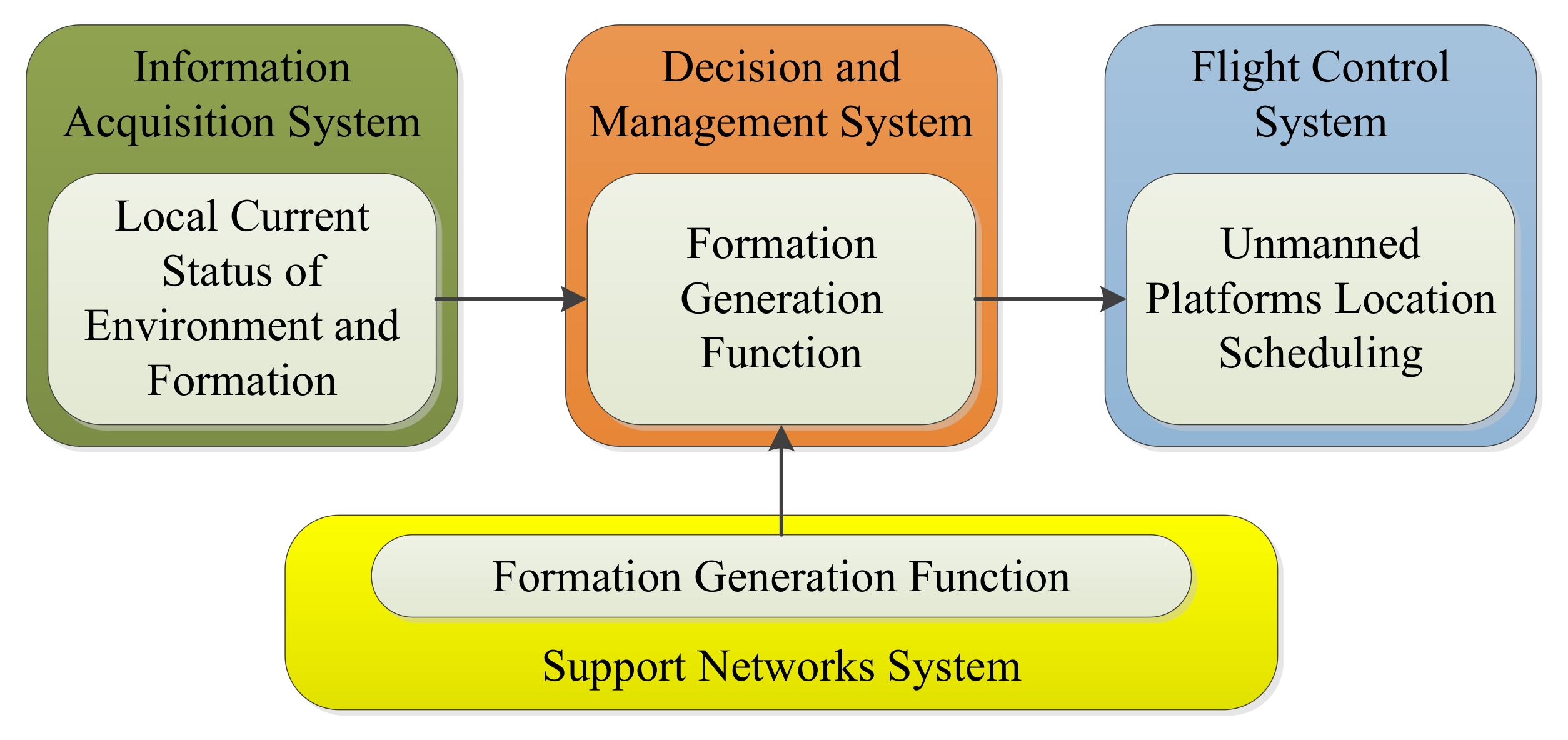
The collaboration of unmanned vehicle groups can be divided into two types: collaboration with formation and collaboration without formation. In a task requiring the collaborative completion of an unmanned vehicle group, unmanned vehicles are often randomly placed in a certain area or start moving toward a concentration area from a certain location at the beginning of the task. For the collaboration problem with formation, whether the unmanned vehicles can gather from the initial position and generate the appropriate formation is the prerequisite for the successful implementation of the task. This paper aims to study this problem.
A typical specific problem can be described as follows: A certain number of unmanned vehicles are randomly located in a certain area. To accomplish a task which requires a variety of functions, they need to adopt an appropriate formation and move to the task area in this formation. Therefore, it is necessary for each member to move into the appropriate formation through distributed decision-making. The Internet of Things (IoT) makes this kind of distributed decision possible. In the IoT, each member can be calculated as part of an algorithm to achieve fast distributed operations.
It should be noted that, in this paper, unmanned vehicles include UAVs, other unmanned vehicles, and other robots with similar characteristics. Most unmanned vehicles move in two dimensions, although others, such as UAVs, move in three dimensions. When the formation needs to be adjusted, three-dimensional moving objects have more room for adjustment. For example, when there is a colliding danger in the formation, members of the two-dimensional formation have to avoid collision by velocity adjustment. However, the members in the three-dimensional formation can easily resolve the crisis by adjusting the height. Moreover, for many tasks, the efficiency of two-dimensional formation is higher than that of three-dimensional formations, such as searching for the ground, spraying plants, and so on. Therefore, this paper focuses on the 2D formation problem. And the formation problem in three-dimensional space can be decomposed into the two-dimensional formation problems of multiple horizontal planes at different levels.
3. Multi-Agent Hybrid Social Cognitive Optimization Based on the Internet of Things (IoT)
After a comprehensive analysis of the formation generation problem described above, we propose an algorithm that combines group intelligence and multi-agent technology: multi-agent hybrid social cognitive optimization (MAHSCO).
3.1. Basic Introduction to MAHSCO
The basis of MAHSCO is the social cognitive optimization (SCO) algorithm proposed by Xie [
21]. SCO is an advanced swarm intelligence optimization algorithm. Unlike traditional swarm intelligence algorithms such as the ant colony algorithm and the particle swarm optimization algorithm, the SCO algorithm refers to the learning process of members of human society; the ant colony algorithm and the particle swarm algorithm mimic less intelligent insects and flocks, while the SCO algorithm simulates the cognitive process of human society, which has higher intelligence and stronger sociality. Therefore, the SCO algorithm is expected to have stronger intelligence and better complex problem-solving ability.
The basic principle of the SCO algorithm is to set the solution to the problem as a knowledge library and set the members to solve the problem as learning agents. Learning agents constantly seek a better solution to a problem by imitation learning and observation learning. Through continuous cognition and learning, learning agents finally obtain the best solution to the problem. It can be seen that this process is highly similar to the process of a human learning new knowledge.
Early swarm intelligence optimization algorithms [
22,
23,
24] mostly simulated natural phenomena. Compared with these, SCO methods, which simulate human cognitive processes, are likely to have better comprehensive performance. The SCO algorithm has been applied to solve the following problems: system of nonlinear equations, nonlinear complementarity problem, reliability allocation problem, and composition web service selection problem [
25]. According to the application of the above problems, SCO has the prominent advantage of high stability. According to [
26], although SCO is a centralized algorithm, it has the potential to be distributed.
Considering the social attributes of human cognition allowed the SCO algorithm to be improved by adding chaos learning and elite learning into the basic SCO algorithm [
27,
28]. In the SCO algorithm, each learning agent occupies the same status. However, in human society, the cognitive abilities of each member are very different, and different members adopt different cognitive and learning strategies to maximize the efficiency of the entire group. Therefore, study [
29] added this feature to the traditional SCO algorithm, dividing the learning agents into elite agents, ordinary agents, and low-level agents. The elite agents adopt an elite learning strategy, the ordinary agents adopt an imitation learning and observation learning strategy in the basic SCO algorithm, and the low-level agents adopt a chaotic learning strategy. The improved algorithm is called the hybrid social cognitive optimization (HSCO).
In order to adapt to the characteristics of multiple unmanned vehicle formation and distribute the HSCO algorithm, this paper introduces a multi-agent system into the HSCO algorithm.
Due to the openness and flexibility of the multi-agent system, it is easy to combine with other artificial intelligence algorithms and to demonstrate its structural advantages and interaction capabilities in the new algorithm. Studies [
30,
31] have given the method of distributed multi-agent system. Therefore, the combination of the HSCO algorithm and a multi-agent system is logical.
The addition of the IoT solves the only problem: distributed computing and communication. Therefore, in this paper, distributed computing and communication are combined to propose the MAHSCO algorithm, and the multiple unmanned vehicles can achieve better collaboration and quick solution to the formation generation problem by exchanging information about their respective knowledge libraries.
3.2. Basic Steps of MAHSCO
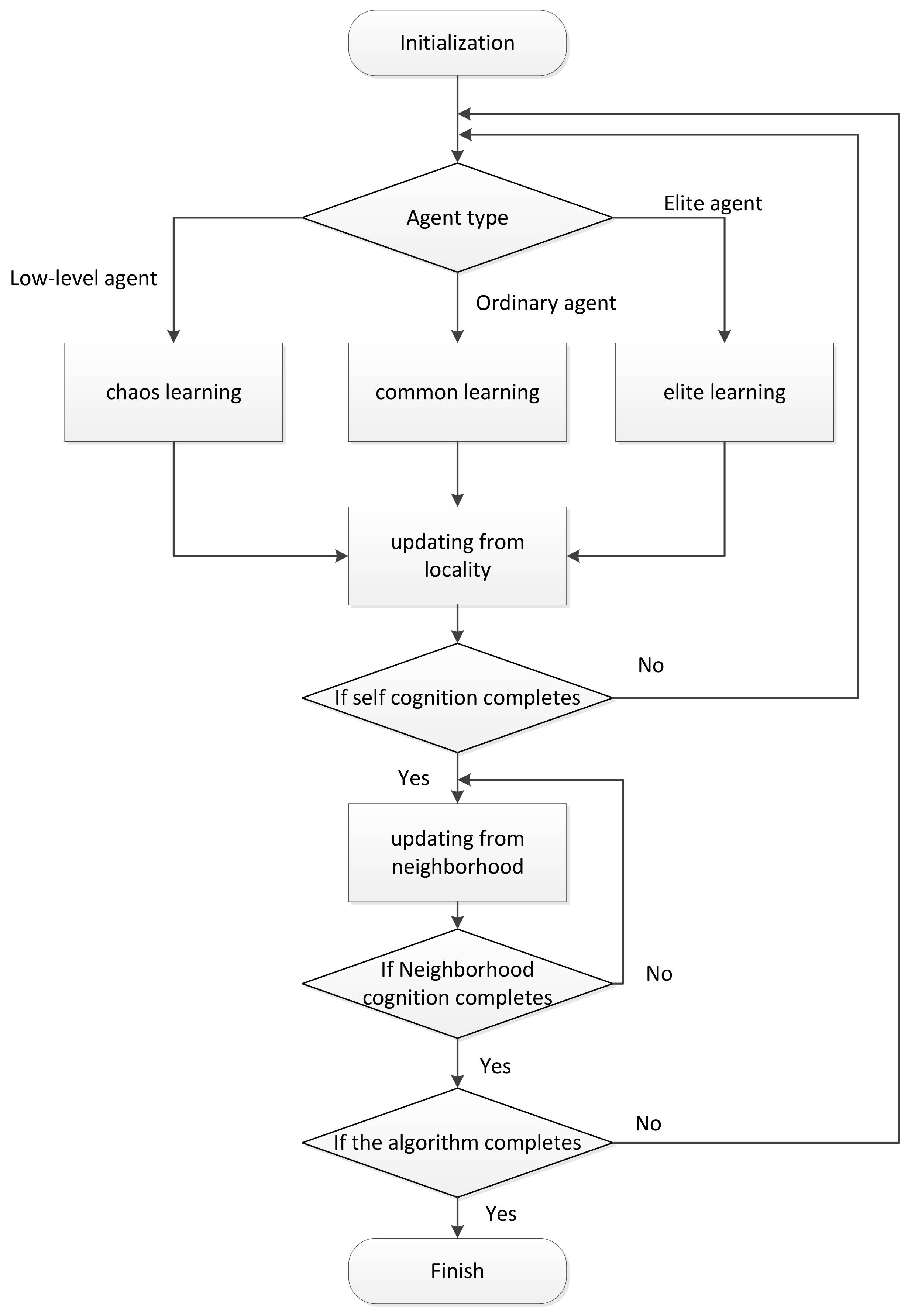
The MAHSCO algorithm is generally divided into the following steps: initialization, self-cognition, neighborhood learning, and conclusion making. The general idea of the algorithm is as follows. At the beginning of the algorithm, each agent randomly generates a solution. As the algorithm proceeds, each agent continuously learns to obtain a better solution, and finally produces a relatively optimal solution. The flow chart of MAHSCO is shown in
Figure 4.
3.2.1. Initialization
Before the MAHSCO begins, it is necessary to abstract the problem to be solved into a mathematical optimization problem, that is, to propose an objective function. The objective function varies with the different problems faced. In this paper, by transforming the form of the objective function, all the problems studied are transformed into the problem of solving the maximum value of the objective function.
After the objective function is determined, each member of the group randomly generates a knowledge library. The knowledge library contains a certain number of solutions that are randomly distributed within the allowable range. The quality of the solution depends on the objective value when it is adopted for the objective function. In this paper, since all the objective functions are transformed to seek the maximum value, the solution which makes the objective function achieve a greater value is a better solution. After that, each member generates a certain number of learning agents. Each learning agent randomly learns one solution in the knowledge library (each agent learns a different solution). The current solution of the learning agent is recorded as .
3.2.2. Self-Cognition
Self-cognition is the process by which learning agents choose better solutions through various learning methods. In this process, the learning agents are divided into three types as described above: elite agents, ordinary agents, and low-level agents. Each agent’s solution produces a value for the objective function. Sort the agents according to the size of the generated value. Usually the top 5% of the agents are defined as elite agents. The last 5% of the agents are defined as low-level agents. The rest are defined as ordinary agents. Different agents use different learning methods:
• Elite agents use elite learning
Let the performance value of the optimal solution in the knowledge library of the current formation member be . The performance value of the agent’s current solution is recorded as . should be compared with . If is better than , center on and use as a reference point for neighborhood search. The new solution obtained is recorded as . If is not better than , make equal to . The neighborhood search method described above is as follows:
Let
be the reference point and
be the center point, then the new solution
is generated by the following equation:
• Ordinary agents use common learning
Common learning is an abstraction and simulation of the conventional learning methods of human beings. In the MAHSCO algorithm, it is used as a self-cognition method for ordinary agents.
Humans and some other intelligent creatures have the ability to imitate the same kind, which allows the populations of these organisms to share knowledge quickly. When an agent of the population acquires advanced knowledge, imitation can quickly spread this knowledge and increase the overall knowledge level of the population. This is the principle of imitation learning.
And the more advanced aspect of human wisdom is that humans can predict future behavior by constructing predictive models of behaviors by observing others’ behaviors and their consequences. This makes it unnecessary for humans to try every kind of behavior in person, and to gain new knowledge by thinking about the behaviors that have already been done. This method is called observation learning.
Based on the above analysis, the common learning in MAHSCO is also divided into two parts: imitation learning and observation learning. In imitation learning, the agent selects some existing knowledge points in the knowledge base to imitate, so as to obtain new knowledge. In observational learning, the agent analyzes the results of the imitation learning and the knowledge that it has mastered before, so as to obtain new knowledge. The implementation details of the method are as follows.
Imitation learning: Randomly choose solutions in the knowledge library ( is the competition width, usually chosen as 2). The solution chosen cannot be the same as the current solution of the learning agent. Then, choose the best among the solutions, denoted as .
Observation learning: Compare the best solution generated in imitation learning with the current solution of the learning agent. Take the better solution in and as the center point and use another point as the reference point for neighborhood search. The specific method of neighborhood search in common learning is consistent with the neighborhood search in elite learning described above. The updated equation is shown in Equation (1). The newly generated point is recorded as . If the generated is better than the previous global optimal solution , the value of is given to .
• Low-level agents use chaos learning
The main purpose of chaos learning of low-level agents is to ensure the randomness and ubiquity of the algorithm. The low-level agent does not observe, and only generates a chaotic solution through the Tent map. The specific method is as follows:
Step 1: randomly generate initial value , ();
Step 2: Iterative calculation should be performed by the following equation:
The number of iterations is chosen as 300. The iteration result is recorded as
. In the iterative calculation process, if
or
,
should add a small amount:
. This is to avoid the iterative process falling into small cycles or unstable points [
32];
Step 3: Calculate the chaos solution by the following equation:
where
are the upper and lower bounds of the interval. The newly generated chaos solution is recorded as
.
3.2.3. Agent’s Solution and Knowledge Library Updating from Locality
If the new solution calculated in Step 2 is better than the current solution of the agent, the agent chooses the new solution as its own solution.
Then select solutions from the knowledge base ( is usually chosen as 4), remove the worst solution , and replace it with the point generated in the previous self cognition.
Since there are multiple learning agents in each member, process 4 can only be performed after each agent has performed processes 2 and 3 once.
3.2.4. Knowledge Library Updating from Neighborhood Members
Select worst solutions from the knowledge library ( is usually chosen as 4) and replace them with the solutions generated in the neighborhood member. If there are multiple neighborhood members, repeat the above replacement. The neighborhood members are derived from the current communication topology.
After each member has completed processes 3.2.2, 3.2.3, and 3.2.4, the entire group finishes a complete social cognition.
In theory, MAHSCO must be able to get a convergent solution. In practical applications, due to time constraints, the following two conditions are often used as the end of the algorithm:
- (1)
The value of the objective function corresponding to the optimal solution obtained by the algorithm reaches the given requirement.
- (2)
Specify a maximum number of loops, the algorithm ends when the number of algorithm loops reaches this maximum number.
3.3. Proof of MAHSCO Convergence
Definition 1. Suppose there is a non-empty class, and its elements are sets. If the following three conditions are met,is afield:
- (1)
;
- (2)
If,;
- (3)
If,
whereis the universal set, andis the complementary set of.
Definition 2. Ifis a set function defined in the non-empty classand meets the following three conditions simultaneously:
- (1)
For any, there is: - (2)
If,;
- (3)
If,when, then.
The set function
is called the measure on the non-empty class
. When Equation (4) is replaced by Equation (5), the set function
is called the probability measure on the non-empty class
.
Suppose there is an optional set , is the field consisting of subsets of , is the probability measure on , then the triple is called the probability space.
The process of using a random algorithm to give convergence criteria is as follows:
- (1)
Randomly select the initial point , let ;
- (2)
Generate a vector on the sample space ;
- (3)
Calculate , choose , let and implement iterative calculations,
where refers to the probability space of the algorithm at the generation, refers to the field of a certain subset of , refers to the probability measure on , and refers to the Iterative approach of the algorithm.
Definition 3. Suppose there is a subset ofbeing. If it satisfies the following three conditions, it is called the support set of probability measure:
- (1)
;
- (2)
Randomly select the point sequence, for any converged subsequence, there is;
- (3)
Ifsatisfies 1 and 2,.
Only by ensuring that the new individuals produced by are superior to the previous individuals can the effectiveness of the random algorithm be ensured. Therefore, make the following assumptions for random algorithms:
Assumption 1. and if, then.
The global convergence of the random algorithm means that the sequenceshould converge to. .
Definition 4. Suppose thein the algorithm makes sense in the following areas: In Equation (6), . If the algorithm finds a point in , the algorithm is considered to have found an acceptable point. The error at this point is ;
Assumption 2. Suppose thathas any Borel subset, if its measure satisfies the conditionthen:whereis calculated by the probability measure.
Theorem 1 [33]. Assume that the objective functionis measurable,is a measurable subset within the field and satisfies Assumptions 1 and 2. Let the solution sequence of the algorithm iteration be, then:
whereis the probability of the solutiongenerated by thestep of the algorithm. Theorem 1 gives the necessary and sufficient conditions for the stochastic optimization algorithm to globally converge with probability 1. Define the function
as follows:
where
refers to the global best of step
,
refers to the updating of the
agent, and
refers to the location of the agent
at the
step. Since the MAHSCO algorithm retains the optimal solution in the learning process in the knowledge library, according to the definition of function
, it can be shown that the MAHSCO algorithm satisfies Assumption 1.
For the learning agent group, the establishment of Assumption 2 is equivalent to the algorithm satisfying Equation (10):
where
is the support set of point
of the algorithm at step
.
For the MAHSCO algorithm, in all learning iteration points, some points are updated according to chaos learning. Chaotic sequences have global ergodicity. For the points with chaos learning, . Therefore, the MAHSCO algorithm satisfies , and also satisfies Assumption 2.
In summary, the MAHSCO algorithm converges globally to the global optimal solution with a probability of 1.
5. Simulations and Results
5.1. Algorithm Parameter
When using the MAHSCO algorithm to optimize the formation of six UAVs, each UAV member generates a knowledge library containing 350 solutions. Each UAV member chooses 35 agents for cognitive learning. After selecting a certain UAV as the reference point, the 2D plane rectangular coordinate system is adopted, and the position of each of the other UAVs is determined by the distance in the x and y directions. Therefore, one solution group contains 10 solutions. In the algorithm, the ratios of elite agents, ordinary agents, and low-level agents are 5, 90, and 5%, respectively. The competition width is selected as 2, the local update width is selected as 4, and the neighbor update width is selected as 4.
5.2. Conditional Parameter
According to the actual flight experience, the safety distance of a certain kind of small UAV could be approximated to 8 m. In this condition, the two UAVs with the largest distance among the six must be kept at a distance of at least 40 m to ensure a solution to the formation problem. After appropriately expanding this range, the solution range for each solution is −100 to 100.
5.3. Simulation Result in Each Optimizing Indicator
In order to verify the effectiveness of the algorithm, the following indicators were used:
(1) Minimum formation horizontal distance
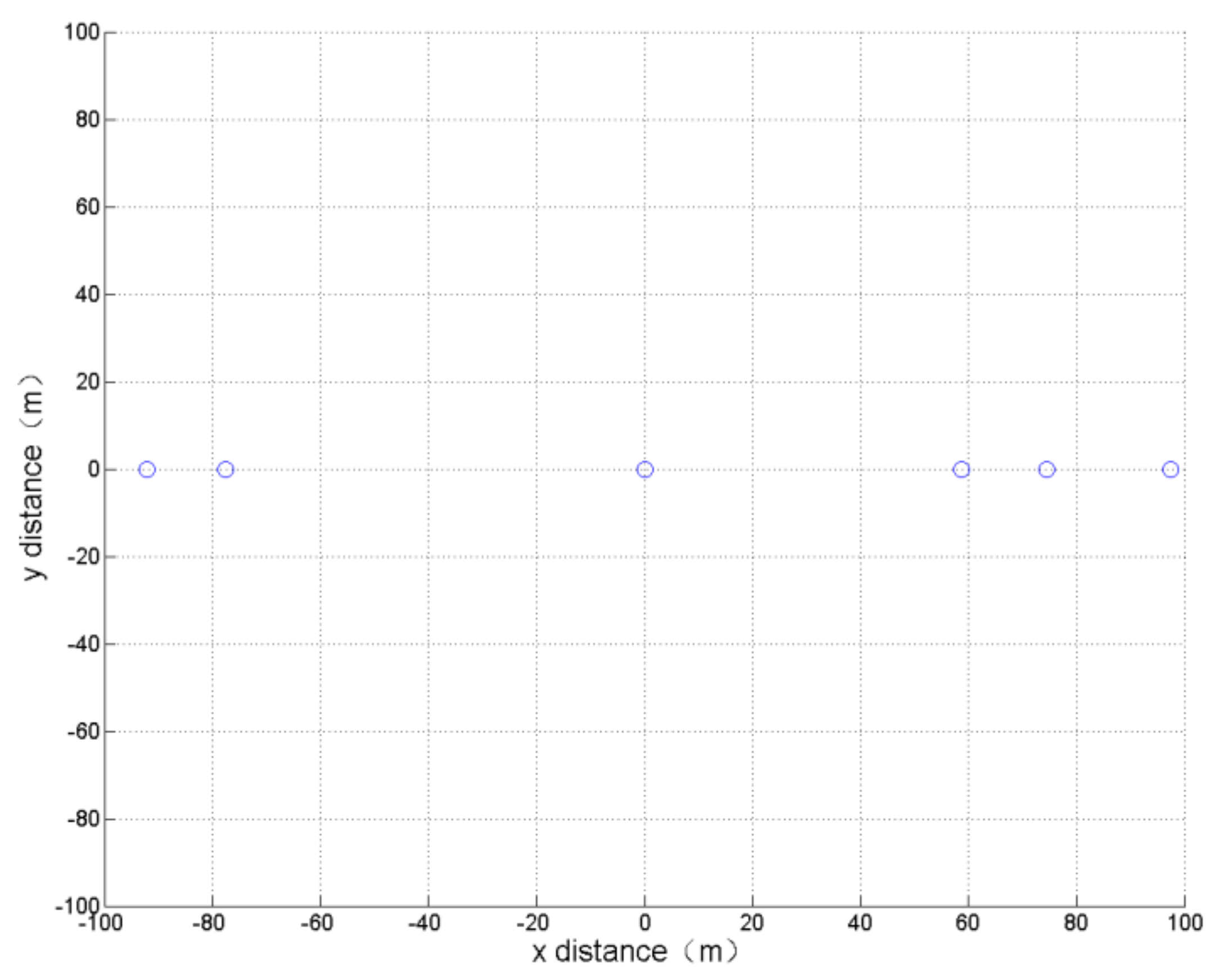
In this simulation, only the formation horizontal distance is optimized in order to obtain the smallest formation horizontal distance without paying attention to other parameters. After 800 cycles of learning calculation, the optimization results and the formation obtained are shown in
Table 1 and
Figure 6.
It can be seen that the result of the optimization is consistent with the actual experience, resulting in a single vertical formation.
(2) Minimum formation vertical distance
In this simulation, only the formation vertical distance is optimized in order to obtain the smallest formation vertical distance without paying attention to other parameters. The optimization results and the formation obtained after 800 cycles of learning calculation are shown in
Table 2 and
Figure 7.
It can be seen that the result of the optimization is consistent with the actual experience, resulting in a single horizontal formation.
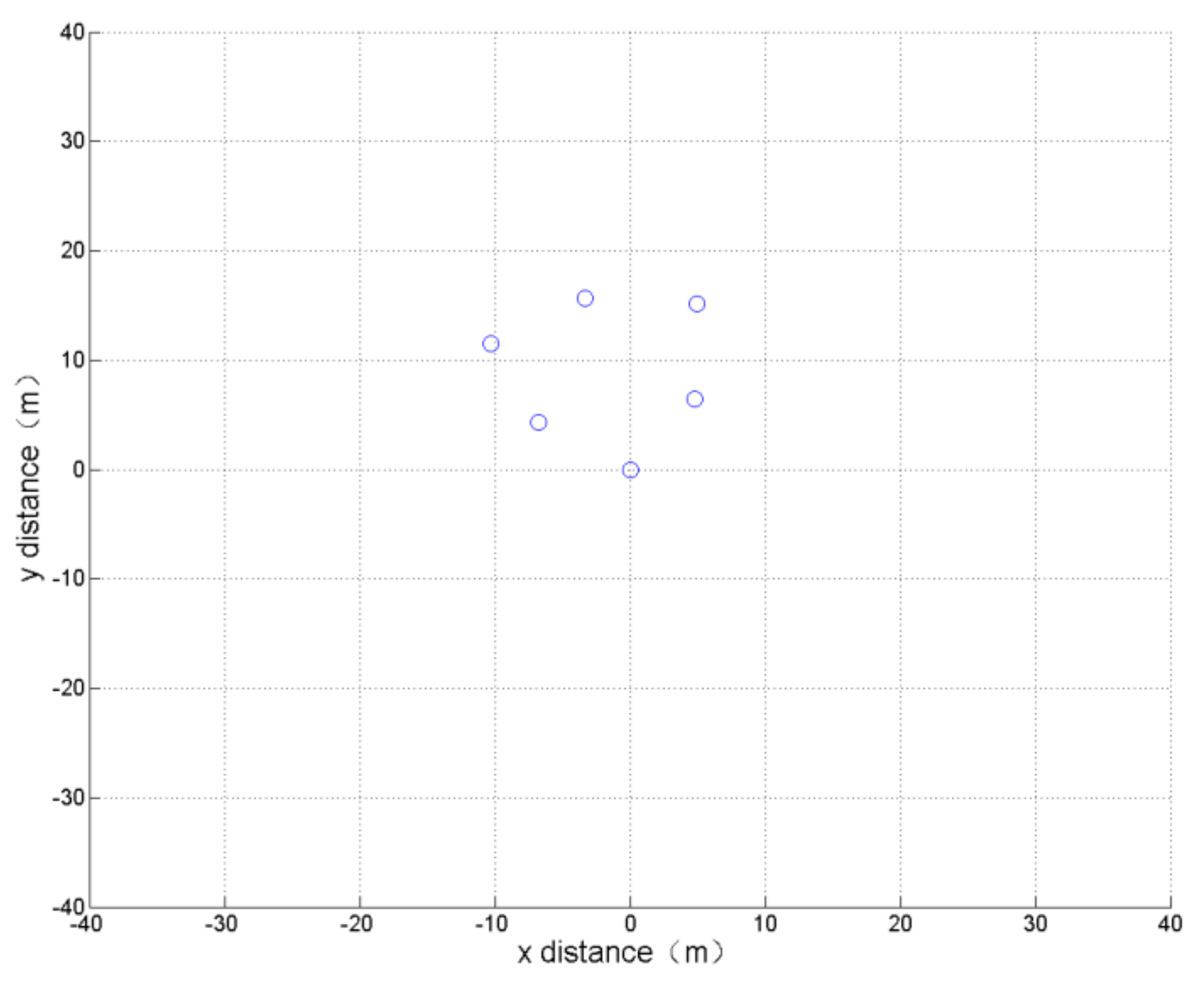
(3) Minimum span
The optimization indicator of this simulation is: the span of the UAV formation is the smallest. This means that the two UAVs that are farthest apart in the formation maintain a small distance. The optimization results and the formation obtained after 800 cycles of learning calculation are shown in
Table 3 and
Figure 8.
The simulation results show that all the UAVs in the generated formation are closely clustered, which is consistent with the actual experience.
(4) Minimum average distance
The optimization indicator of this simulation is: the root mean square (rms) value of the distance between all UAVs and the reference UAV is the smallest. This means that the formation of the UAVs should be relatively tight. The optimization results and the formation obtained after 800 cycles of learning calculation are shown in
Table 4 and
Figure 9.
The simulation results show that all the UAVs in the generated formation are closely clustered, which is consistent with the actual experience.
5.4. Analysis Results
In the simulation experiment of the above four formations, the formation generated by the MAHSCO algorithm is consistent with the theoretical optimal formation. Moreover, the distance between the unmanned aerial vehicles in the generated formation is less deviated from the theoretical value, and the precision is high.
5.5. Comparison of MAHSCO and HSCO
As described above, the main difference between MAHSCO and HSCO is whether the neighborhood recognition is performed or not. The HSCO only needs one unmanned platform to calculate, while MAHSCO needs to calculate on each platform. However, due to the mutual communication between platforms, the computation amount of each platform in the MAHSCO algorithm can be much less than the total computation amount in the HSCO algorithm. The corresponding disadvantage is that MAHSCO needs more cycles to achieve the same precision as HSCO if the amount of computation in each learning cycle is equal. Taking the first optimization in
Section 5.3. as an example, the number of cycles required for both algorithms to achieve the same precision result is shown below. (The minimum formation horizontal distance below −1 × 10
−10 was taken as the end condition of optimization. In order to keep the computation amount of each cycle equal to that of MAHSCO, the agent amount in the HSCO for comparison was taken as 210.)
It can be seen from the data in
Table 5 that MAHSCO requires more cycles than HSCO under similar conditions. However, the increase in the number of cycles is not much, considering that the computation amount of each unmanned platform is only 1/6 of the original. Also, since all the calculations in the HSCO are performed in one unmanned platform, the entire formation cannot be implemented once it fails. Therefore, MAHSCO is a better algorithm for the generation of UAV formations.
5.6. Robustness and Fault-Tolerant Analysis of MAHSCO
In MAHSCO, the operation of the algorithm relies on the transfer of information between members. In practical applications, information transmission is achieved through radio stations. Therefore, under actual circumstances, MAHSCO will face errors caused by transmission delay, packet loss and bit error.
In engineering applications, we add transmission feedback and verification. When a member needs to send a message, it will continue to send until it receives feedback from all neighboring members or reaches the upper limit of the sending time. In this case, the probability of a message being erroneously transmitted is low, but more information is lost. Although it turns out that the final algorithm will still reach convergence, it will reduce the optimization efficiency of MAHSCO. In order to verify the operational efficiency of MAHSCO in the case of partial information loss, we added 5%, 10% and 20% of the packet loss in the algorithm information transmission. Still taking the first optimization in
Section 5.3 and the same condition in
Section 5.5 as an example, the comparison that the number of cycles required achieving the same operational precision of no packet loss, 5% packets loss, 10% packets loss and 20% packets loss are shown in
Table 6.
It can be seen from the data in
Table 6 that MAHSCO’s efficiency has dropped when information is lost. However, even if the packet loss rate reaches 20%, it can converge faster to the specified accuracy. And, by comparing with
Section 5.3, the distributed decision is proved still better than the centralized decision. (The total number of cycles is less than 2 times, but the calculation amount of each member is 1/6 of the original.) The main reason is that MAHSCO retains the characteristics of member self-learning.