A Secured Proxy-Based Data Sharing Module in IoT Environments Using Blockchain
Abstract
:1. Introduction
2. Related Works
3. Preliminaries
3.1. Bilinear Maps
- Bilinear: For all , , then can be computed efficiently.
- The map is non-degenerate. That is, if g generates G and h also generates G, then generates . In addition, . The map does not send all pairs in to the identity in .
- It is computable; there exists an efficient algorithm to compute the map for any .
3.2. Inner-Product Encryption (IPE)
3.3. Attribute Based Encryption (ABE)
3.4. Proxy Re-Encryption (PRE)
3.5. Blockchain Network
4. System Model
4.1. Problem Statement
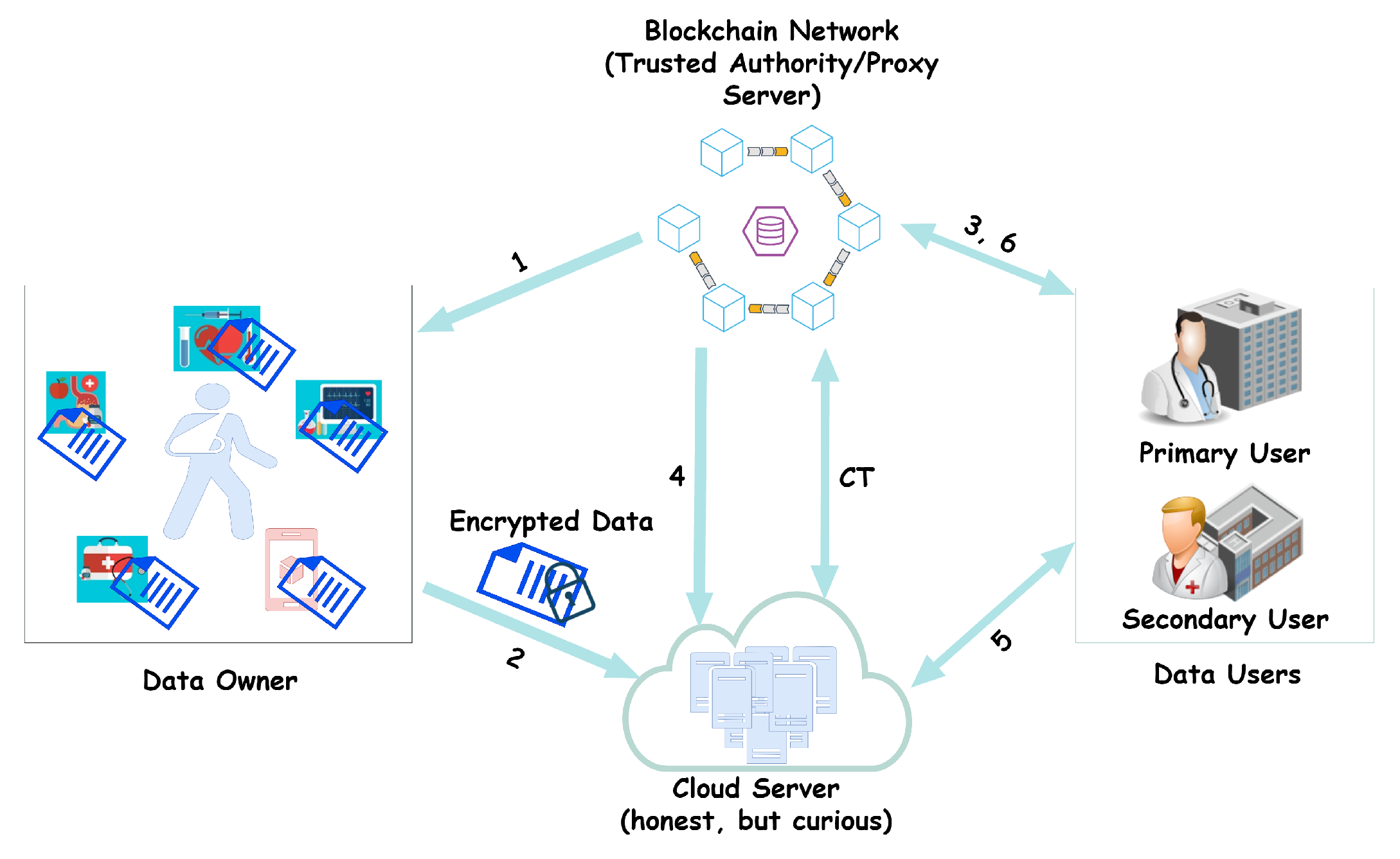
4.2. System Overview
- Data Owner: This is the entity (the patient in this case) whose data are to be accessed. Access is possible if and only if the private key of the data user corresponds to the attribute set specified by the data owner.
- Data User: This is the entity who wants to make use of the data from the owner. Both the data owner and user(s) should be registered on the blockchain.
- Cloud Server: This is the repository for the data from the owner. All encrypted files are sent to the cloud server (honest, but curious) through a secured communication channel.
- Blockchain Network: This primarily consists of the following entities:
- Issuer: This entity registers the participants (data owner and users) on the blockchain network. It gives out membership keys to them and that serves as their identity (ID).
- Verifier: The verifier, which also serves as an authentication unit, checks whether a user who makes an access request or a data owner who uploads its data onto the cloud, are actually members of the blockchain network.
- Processing node: This is the heartbeat of the blockchain network. All processes (transactions) that ever occur on the network are performed by this entity. In this work, however, it serves as the (trusted) proxy that oversees the re-encryption process.
- Smart contract center: This unit prepares the contract that binds how data are to be used.
- The proxy generates a secret key, , and a public key , and hands the public key and access policy to the data owner. That is, the data owner is given .
- The patient encrypts the data with the attribute set and sends the encrypted data to the cloud through a secured channel. The encrypted data are .
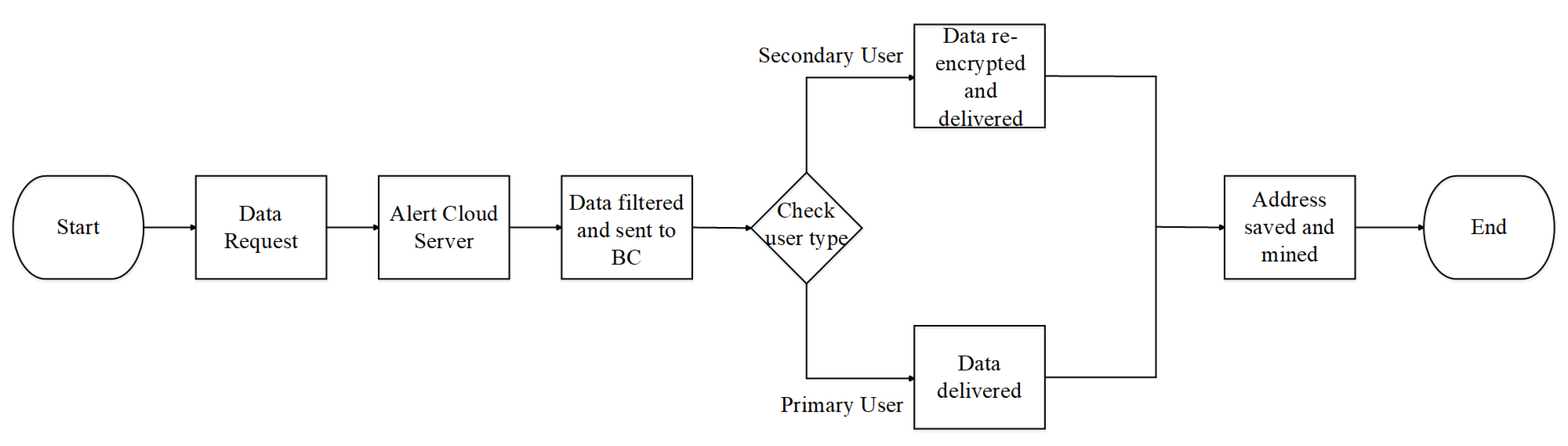
- The data user makes a request for the data.
- The proxy accesses the permission rights of the data users from the cloud server. After accessing it, the blockchain network, which also serves as a trusted authority, gives the private key to the user according to the user’s attributes.
- Users can now access data from the cloud server.
- The primary user is given while the secondary user is given . The proxy generates a re-encryption key and transforms the policy set for the secondary user who wants the shared data from the primary user but holds a different access policy, .
5. The Scheme
6. Security Model
Security Proof
7. Implementation and Performance Analysis
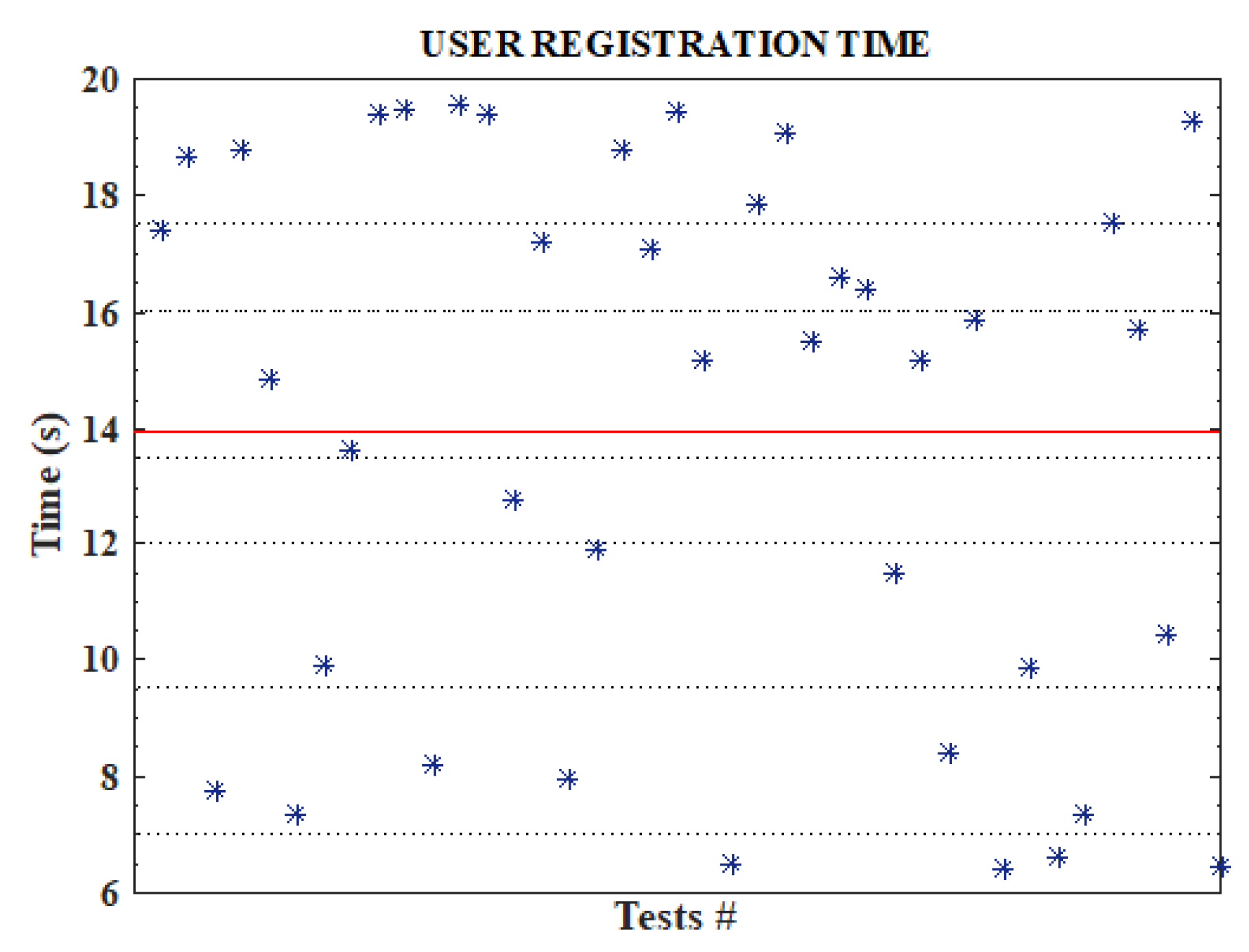
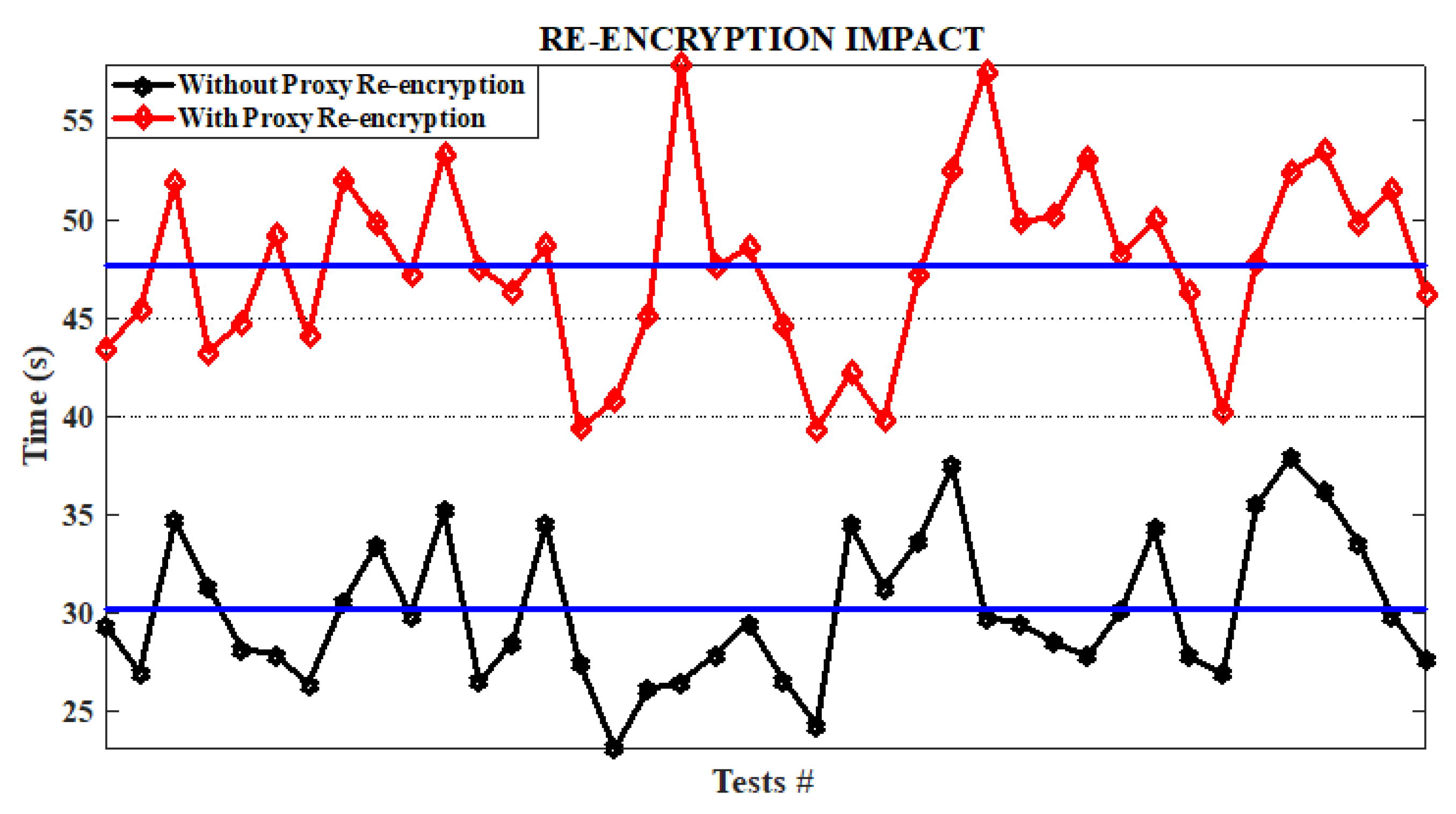
7.1. Experiment 1
7.2. Experiment 2
8. Discussion
- Collusion Resistance: Our proposed scheme prevents collusion attack in the sense that the re-encrypted data are divided into two parts with one part stored on the blockchain network, and the other part stored on the cloud. Because the blockchain network and the cloud server work in tandem, a data user has to first obtain the bit-part data stored on the blockchain before obtaining the other half from the cloud. As a first level security check (usually performed before decryption), a data user must prove to the blockchain networks’ verification unit its membership before gaining access to the data. A revoked user is deprived of this right because its membership keys have been completely removed from the network and therefore the user becomes unknown to the network.However, for a revoked user who still colludes with the cloud server for access to data, the cloud server still has to provide the user’s details to the blockchain processing node for the necessary checks to be made. With collusion attack prevented, the confidentiality of the data is preserved/guaranteed.
- Fine-grained access control: There is an effective management of user access by the implementation of the ABE scheme. The utilization of the inner product encryption scheme enables a fine-grained access control to data. The data owner specifies which attribute set or right a data user enjoys and therefore, to access data, there should be a match-up between the attribute set and the private key set. There is also the possibility of selective delegation due to the weight (information type) set by the data owner. Furthermore, depending on the level of trust between the data owner and the user(s), decryption of either all or some data can be delegated selectively to the user(s).
9. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| ABE | Attribute Based Encryption |
| IoT | Internet of Things |
| IPE | Inner Product Encryption |
| PRE | Proxy Re-Encryption |
| ECC | Elliptic Curve Cryptography |
| WSN | Wireless Sensor Network |
| HIPAA | Health Insurance Portability and Accountability Act |
| EMR | Electronic Medical Record |
| EHR | Electronic Health Records |
References
- Zheng, J.; Simplot-Ryl, D.; Bisdikian, C.; Mouftah, H. The internet of things. IEEE Commun. Mag. 2011, 49, 30–31. [Google Scholar] [CrossRef]
- Miorandi, D.; Sicari, S.; De Pellegrini, F.; Chlamtac, I. Internet of things: Vision applications and research challenges. Ad Hoc Netw. 2012, 10, 1497–1516. [Google Scholar] [CrossRef]
- Casadei, R.; Fortino, G.; Pianini, D.; Russo, W.; Savaglio, C.; Viroli, M. Modelling and simulation of opportunistic IoT services with aggregate computing. Future Gener. Comput. Syst. 2019, 91, 252–262. [Google Scholar] [CrossRef]
- Bennett, T.R.; Savaglio, C.; Lu, D.; Massey, H.; Wang, X.; Wu, J.; Jafari, R. MotionSynthesis toolset (MoST): A toolset for human motion data synthesis and validation. In Proceedings of the 4th ACM MobiHoc Workshop on Pervasive Wireless Healthcare, Philadelphia, PA, USA, 11–14 August 2014. [Google Scholar] [CrossRef]
- Leavitt, N. Is cloud computing really ready for prime time? Computer 2009, 42, 15–20. [Google Scholar] [CrossRef]
- Brodkin, J. Gartner: Seven cloud-computing security risks. Netw. World 2008, 2008, 1–3. [Google Scholar]
- Chow, R.; Golle, P.; Jakobsson, M.; Shi, E.; Staddon, J.; Masuoka, R.; Molina, J. Controlling data in the cloud: outsourcing computation without outsourcing control. In Proceedings of the IEEE 3rd International Conference on Cloud Computing, Chicago, IL, USA, 13–13 November 2009; pp. 85–90. [Google Scholar]
- Sahai, A.; Waters, B. Fuzzy identity-based encryption. In Proceedings of the 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; Springer: Berlin/Heidelberg, Germany; Volume 3494, pp. 457–473. [Google Scholar]
- Wang, G.; Liu, Q.; Wu, J. Hierarchical attribute-based encryption for fine-grained access control in cloud storage services. In Proceedings of the ACM conference on Computer and Communications Security CCS’10, Chicago, IL, USA, 4–8 October 2010. [Google Scholar]
- Zhao, G.; Rong, C.; Li, J.; Zhang, F.; Tang, Y. Trusted data sharing over untrusted cloud storage providers. In Proceedings of the 2nd IEEE International Conference on Cloud Computing Technology and Sciene, Indianapolis, IN, USA, 30 Novemebr–3 December 2011; pp. 96–103. [Google Scholar]
- Yu, S.; Wang, C.; Ren, K.; Lou, W. Achieving secure, scalable, and fine-grained data access control in cloud computing. In Proceedings of the IEEE International Conference on Computer Communications INFOCOM’10, San Diego, CA, USA, 14–19 March 2010. [Google Scholar]
- Park, J.H. Inner-product encryption under standard assumptions. Des. Codes Cryptogr. 2011, 58, 235–257. [Google Scholar] [CrossRef]
- Qin, Z.; Xiong, H.; Wu, S.; Batamuliza, J. A survey of proxy re-encryption for secure data sharing in cloud computing. IEEE Trans. Serv. Comput. 2017, 99. [Google Scholar] [CrossRef]
- Sepehri, M.; Cimato, S.; Damiani, E. Efficient implementation of a proxy-based protocol for data sharing on the cloud. In Proceedings of the Fifth ACM International Workshop on Security in Cloud Computing, SCC@AsiaCCS 2017, Abu Dhabi, UAE, 2 April 2017; pp. 67–74. [Google Scholar]
- Sepehri, M.; Cimato, S.; Damiani, E.; Yeuny, C.Y. Data Ssharing on the cloud: A scalable proxy-based protocol for privacy-preserving queries. In Proceedings of the 7th IEEE International Symposium on Ubisafe Computing in Conjunction with 14th IEEE Conference on Trust, Security and Privacy in Computing and Communications, TrustCom/BigDataSE/ISPA, Helsinki, Finland, 20–22 August 2015; pp. 1357–1362. [Google Scholar]
- Mambo, M.; Okamoto, E. Proxy cryptosystems: Delegation of the power to decrypt ciphertexts. IICE Trans. Fundam. Electr. Commun. Comput. Sci. 1997, 80A, 54–63. [Google Scholar]
- Blaze, M.; Bleumer, G.; Strauss, M. Divertible Protocols and Atomic Proxy Cryptography; Springer: Berlin/Heidelberg, Germany, 1998; pp. 127–144. [Google Scholar]
- El Gamal, T. A public key cryptosystem and a signature scheme based on discrete logarithms. In Proceedings of the CRYPTO 84 on Advances in Cryptology, Santa Barbara, CA, USA, 18–22 August 1985; Springer: New York, NY, USA, 1985; pp. 10–18. [Google Scholar]
- Do, J.-M.; Song, Y.-J.; Park, N. Attribute based proxy re-encryption for data confidentiality in cloud computing environments. In Proceedings of the 2011 First ACIS/JNU International Conference on Computers, Networks, Systems and Industrial Engineering (CNSI ’11), Jeju Island, Korea, 23–25 May 2001; IEEE Computer Society: Washington, DC, USA, 2001; pp. 248–251. [Google Scholar]
- Guo, S.; Zeng, Y.; Wei, J.; Xu, Q. Attribute-based re-encryption scheme in the standard model. Wuhan Univ. J. Nat. Sci. 2008, 13, 621–625. [Google Scholar] [CrossRef]
- Liang, X.; Cao, Z.; Lin, H.; Shao, J. Attribute based proxy re-encryption with delegating capabilities. In Proceedings of the 4th International Symposium on Information, Computer, and Communications Security (ASIACCS’09), Sydney, Australia, 10–12 March 2009; ACM: New York, NY, USA, 2009; pp. 276–286. [Google Scholar]
- Luo, S.; Hu, J.; Chen, Z. Ciphertext policy attribute-based proxy re-encryption. In Proceedings of the 12th International Conference on Information and Communications Security (ICICS’10), Barcelona, Spain, 15–17 December 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 401–415. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP ’07), Berkeley, CA, USA, 20–23 May 2007; IEEE Computer Society: Washington, DC, USA, 2007; pp. 321–334. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security (CCS’06), Alexandria, VA, USA, 30 October–3 November 2006; ACM: New York, NY, USA, 2006; pp. 89–98. [Google Scholar]
- Katz, J.; Sahai, A.; Waters, B. Predicate Encryption Supporting Disjunctions, Polynomial Equations, and Inner Products; Springer: Berlin/Heidelberg, Germany, 2008; pp. 146–162. [Google Scholar]
- Okamoto, T.; Takashima, K. Hierarchical Predicate Encryption for Inner-Products; Springer: Berlin/Heidelberg, Germany, 2009; pp. 214–231. [Google Scholar]
- Du, X.; Guizani, M.; Xiao, Y.; Chen, H.H. A routing-driven elliptic curve cryptography based key management scheme for heterogeneous sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1223–1229. [Google Scholar] [CrossRef]
- Xiao, Y.; Rayib, V.K.; Sunc, B.; Du, X.; Hue, F.; Gallowaya, M. A survey of key management schemes in wireless sensor networks. J. Comput. Commun. 2007, 30, 2314–2341. [Google Scholar] [CrossRef]
- Du, X.; Xiao, Y.; Guizani, M.; Chen, H.H. An effective key management scheme for heterogeneous sensor networks. Ad Hoc Netw. 2007, 5, 24–34. [Google Scholar] [CrossRef]
- Du, X.; Chen, H.H. Security in wireless sensor networks. IEEE Wirel. Commun. Mag. 2008, 15, 60–66. [Google Scholar]
- Griggs, K.N.; Ossipova, O.; Kohlios, C.P.; Baccarini, A.N.; Howson, E.A.; Hayajneh, T. Healthcare Blockchain System Using Smart Contracts for Secure Automated Remote Patient Monitoring. J. Med. Syst. 2018, 42, 130. [Google Scholar] [CrossRef] [PubMed]
- Kamau, G.; Boore, C.; Maina, E.; Njenga, S. Blockchain technology: Is this the solution to EMR interoperability and security issues in developing countries? In Proceedings of the 2018 IST-Africa Week Conference (IST-Africa), Gaborone, Botswana, 9–11 May 2018; pp. 1–8. [Google Scholar]
- Ekblaw, A.; Azaria, A.; Halamka, J.D.; Lippman, A. A case study for blockchain in healthcare: “Medrec” prototype for electronic health records and medical research data. In Proceedings of the IEEE Open and Big Data Conference, Vienna, Austria, 22–24 August 2016; p. 13. [Google Scholar]
- Xia, Q.; Sifah, E.B.; Smahi, A.; Amofa, S.; Zhang, X. BBDS: Blockchain-based data sharing for electronic medical records in cloud environments. Information 2017, 8, 44. [Google Scholar] [CrossRef]
- Yue, X.; Wang, H.; Jin, D.; Li, M.; Jiang, W. Healthcare data gateways: found healthcare intelligence on blockchain with novel privacy risk control. J. Med. Syst. 2016, 40, 218. [Google Scholar] [CrossRef] [PubMed]
- Badr, S.; Gomaa, I.; Abd-Elrahman, E. Multi-tier blockchain framework for IoT-EHRs systems. Procedia Comput. Sci. 2018, 141, 159–166. [Google Scholar] [CrossRef]
- Boneh, D.; Franklin, M. Identity-based encryption from the Weil Pairing. SIAM J. Comput. 2003, 32, 586–615. [Google Scholar] [CrossRef]
- Park, N.; Kwak, J.; Kim, H.; Kim, S.; Won, D. WIPI mobile platform with secure service for mobile RFID network environment. In Proceedings of the ICSE 2006 International Workshop on Web-based Internet Computing for Science and Engineering (In Conjunction with APWeb 2006), Harbin, China, 16–18 Janury 2006; Springer-Verlag: Berlin/Heidelberg, Germany, 2006; pp. 741–748. [Google Scholar]
- Ateniese, G.; Fu, K.; Green, M.; Hohenberger, S. Improved proxy re-encryption schemes with applications to secure distributed storage. In Proceedings of the 12th Annual Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 2–4 February 2005. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 11 March 2019).
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Obour Agyekum, K.O.-B.; Xia, Q.; Sifah, E.B.; Gao, J.; Xia, H.; Du, X.; Guizani, M. A Secured Proxy-Based Data Sharing Module in IoT Environments Using Blockchain. Sensors 2019, 19, 1235. https://doi.org/10.3390/s19051235
Obour Agyekum KO-B, Xia Q, Sifah EB, Gao J, Xia H, Du X, Guizani M. A Secured Proxy-Based Data Sharing Module in IoT Environments Using Blockchain. Sensors. 2019; 19(5):1235. https://doi.org/10.3390/s19051235
Chicago/Turabian StyleObour Agyekum, Kwame Opuni-Boachie, Qi Xia, Emmanuel Boateng Sifah, Jianbin Gao, Hu Xia, Xiaojiang Du, and Moshen Guizani. 2019. "A Secured Proxy-Based Data Sharing Module in IoT Environments Using Blockchain" Sensors 19, no. 5: 1235. https://doi.org/10.3390/s19051235
APA StyleObour Agyekum, K. O.-B., Xia, Q., Sifah, E. B., Gao, J., Xia, H., Du, X., & Guizani, M. (2019). A Secured Proxy-Based Data Sharing Module in IoT Environments Using Blockchain. Sensors, 19(5), 1235. https://doi.org/10.3390/s19051235





