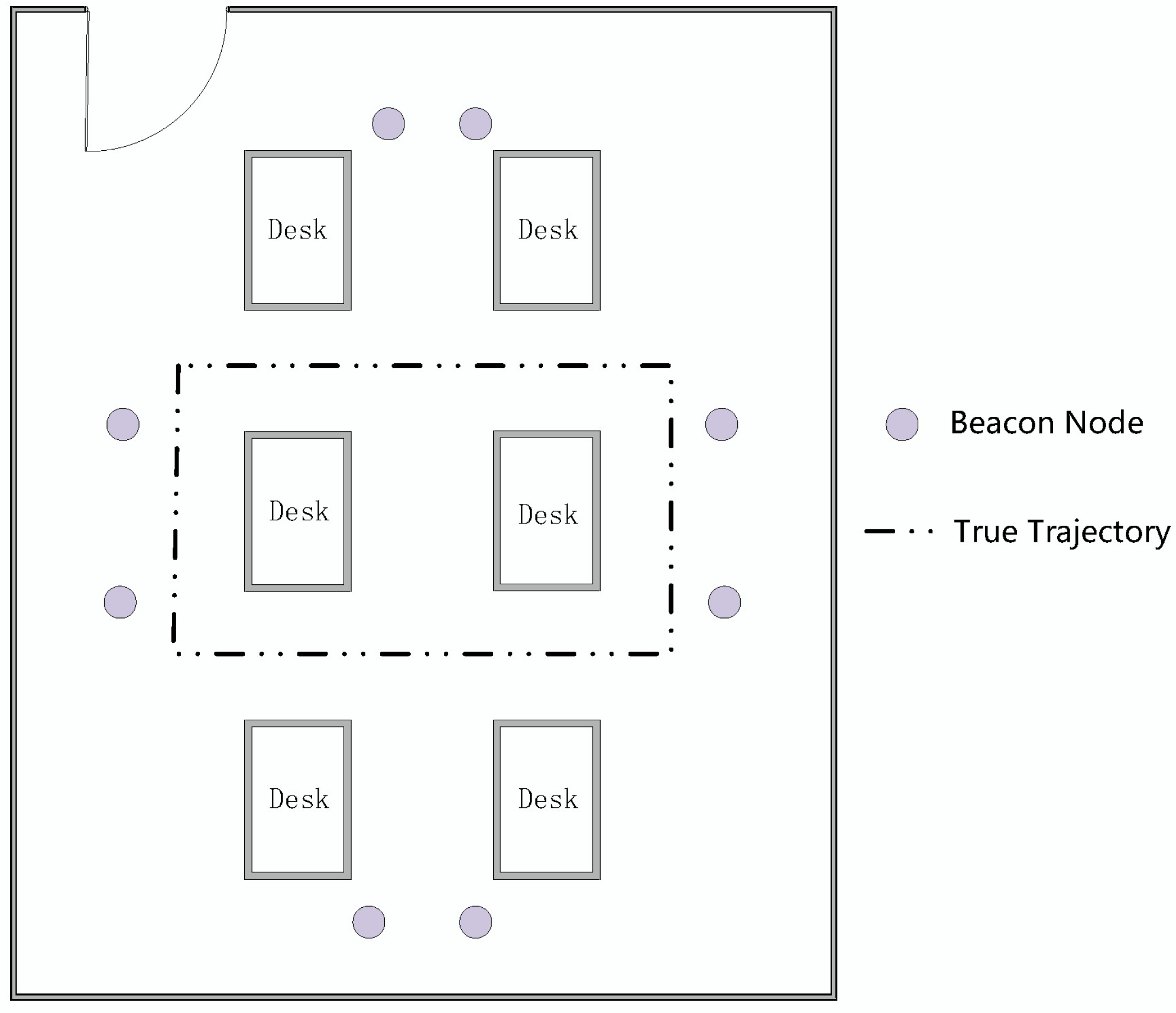
1. Introduction
The most popular worldwide localization is the Global Positioning System (GPS) which is used to tackle outdoor positioning problems, but its accuracy cannot meet requirements in some areas especially in indoor environments. Therefore, Wireless Sensor Network (WSN) based on indoor localization has attracted attention in recent years.
As a research hotspot, WSN has been widely applied in military applications, environmental monitoring, medical care and space exploration. Moreover, the localization techniques based on a mobile node’s location has vital research significance [
1]. Because of the influence of Non-Line-of-Sight (NLOS) propagation, and other factors such as insufficient position signal strength, electromagnetic interference noise and mobile beacon node, the accuracy of localization has become a critical research direction.
According to measuring the distance between nodes, localization algorithms are normally divided into two categories: range-based algorithms and range-free algorithms, and there are many conventional methods in range-based algorithms; for example, time difference of arrival (TDoA), time of arrival (ToA), received signal strength (RSS), direction-of-arrival (DoA) and space-division multiple-access (SDMA) exploiting rich multi-path environment (i.e., NLOS) [
2]. There are two categories of nodes in WSN: beacon nodes and mobile nodes. The coordinate information of beacon nodes can be acquired, while the position of mobile nodes is unknown. The position of a mobile node can be estimated by using the algorithms mentioned above.
The biggest challenge of indoor localization is NLOS propagation. The obstacles between beacon nodes and mobile nodes are the major factors generating NLOS errors, mostly because the obstacles block or reflect the spread of the signal. Therefore, in range-based indoor localization, the mitigation of NLOS errors is profoundly critical to improve the indoor localization accuracy. Many strategies have been proposed in order to mitigate NLOS effects [
3,
4,
5,
6,
7,
8,
9,
10,
11,
12,
13].
In order to tackle the fluctuation problem of range information, many researchers have proposed various filtering algorithms: Average Filtering algorithm (AF), Gauss Filter (GF), Kalman Filter (KF), Extended Kalman Filter (EKF), Unscented Kalman Filter (UKF), Particle Filtering (PF) and so on. This paper proposes a triple filter algorithm based on KF and UKF. Most papers divide measurements into two categories: LOS and NLOS. Actually, the measurements with NLOS errors can be classified more meticulously so as to better cope with the NLOS problem. Considering that KF has limitations in dealing with nonlinear noise, UKF is used to cope with non-linear noise. The main contributions of this paper are as follows:
- (1)
A residual analysis based on the NLOS identification algorithm is proposed to identify NLOS errors. A method of mixed UKF and KF is proposed to filter out measurements noise, and no prior information is required in this mixed algorithm, which can better mitigate NLOS errors.
- (2)
The NLOS correction algorithm based on voting is proposed to restrict NLOS errors and correct the NLOS measurements, which are used to preprocess the NLOS measurements that need to be classified.
- (3)
NLOS measurements are classified into two categories: hard NLOS measurements and soft ones by Fuzzy-C-Means (FCM), which can be extended into more filters to tackle complicated NLOS errors, and it is flexible and robust as well.
- (4)
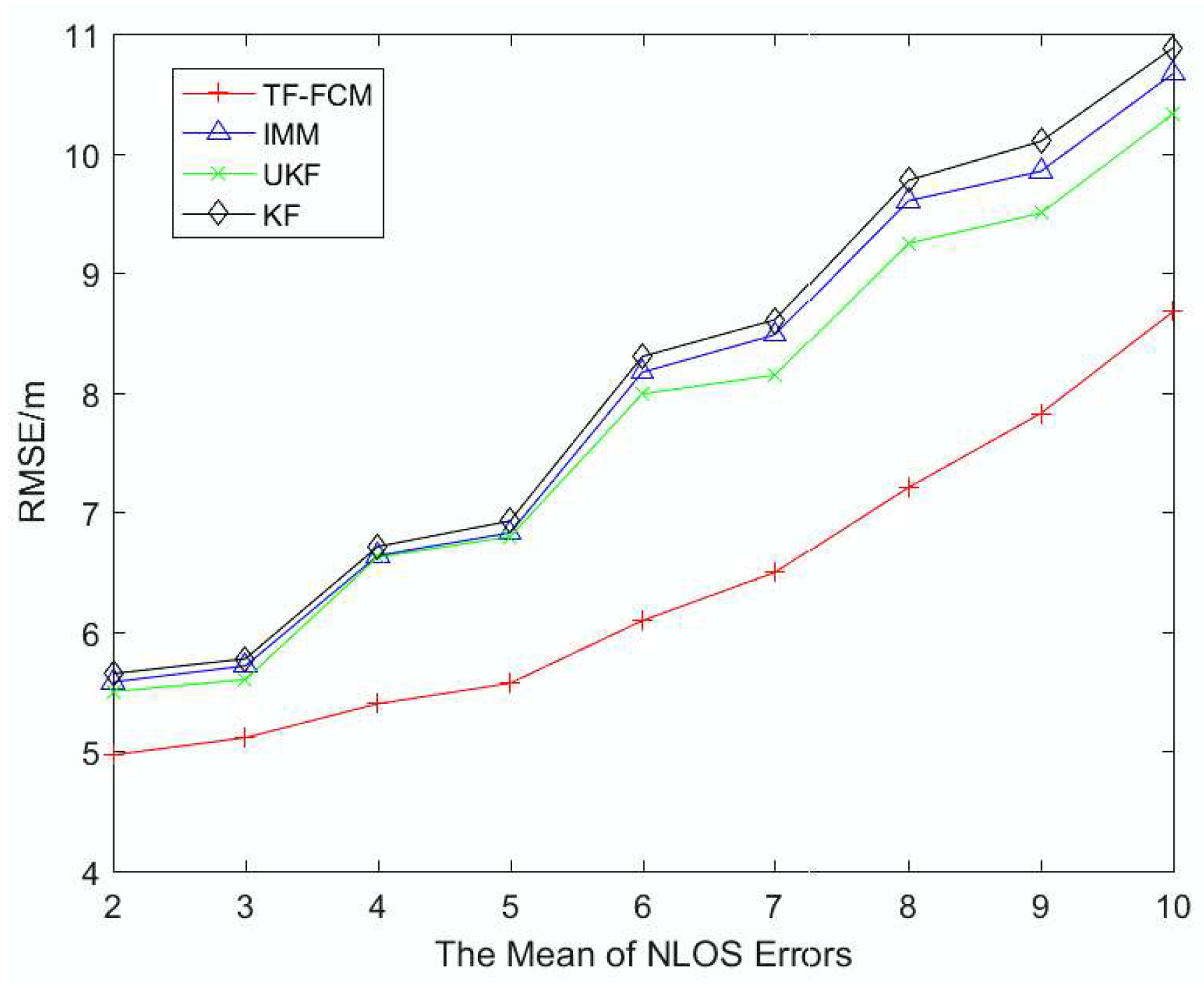
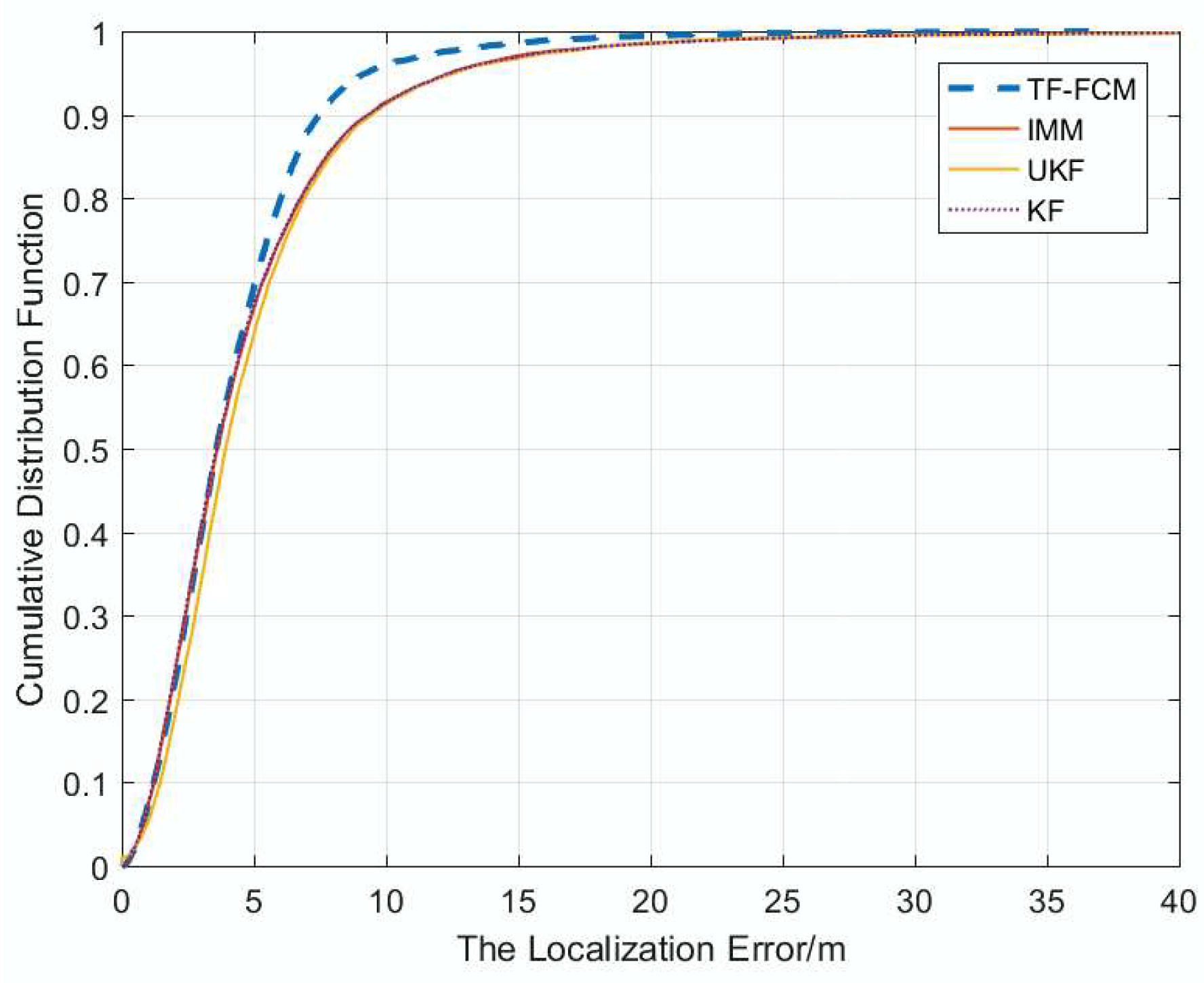
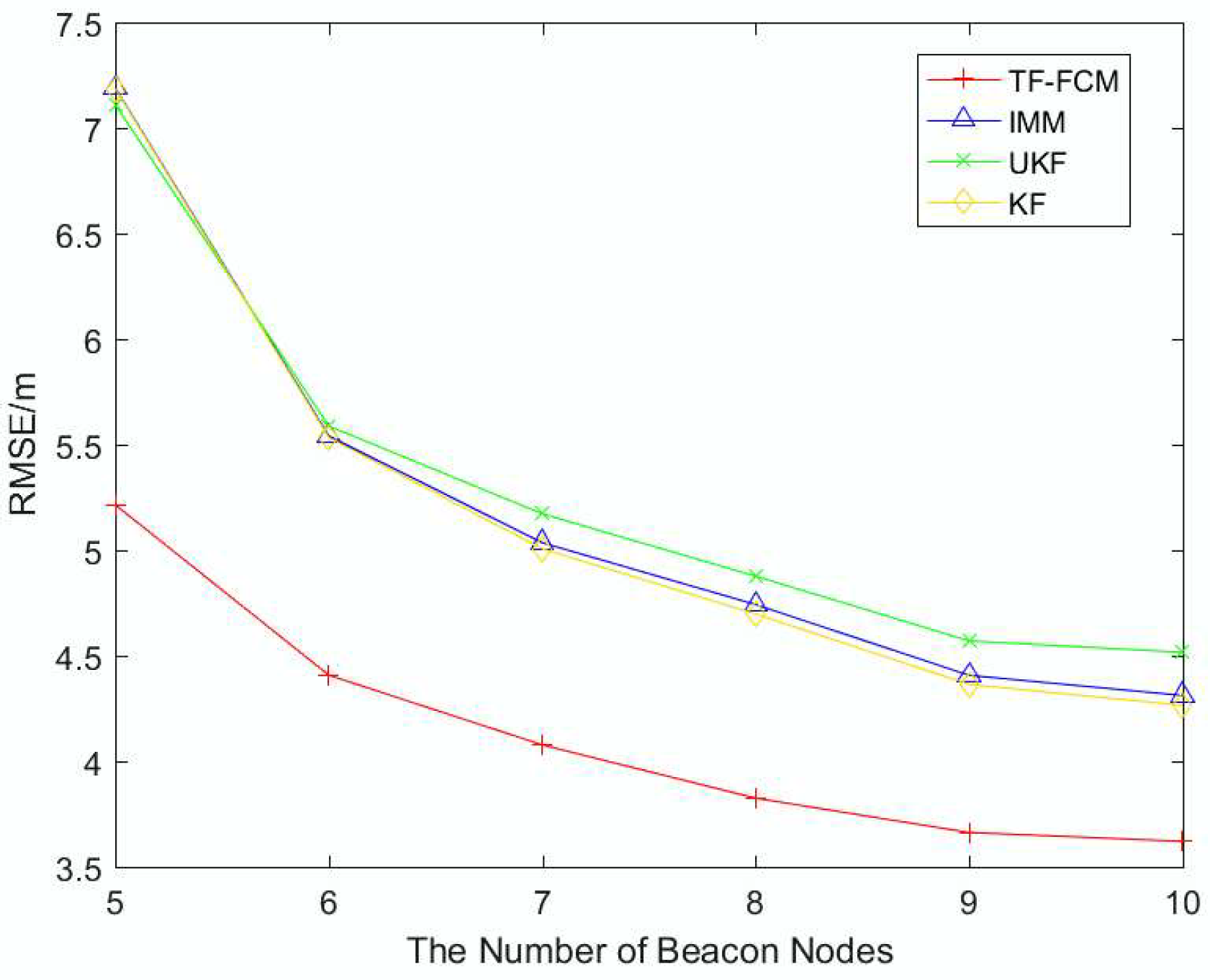
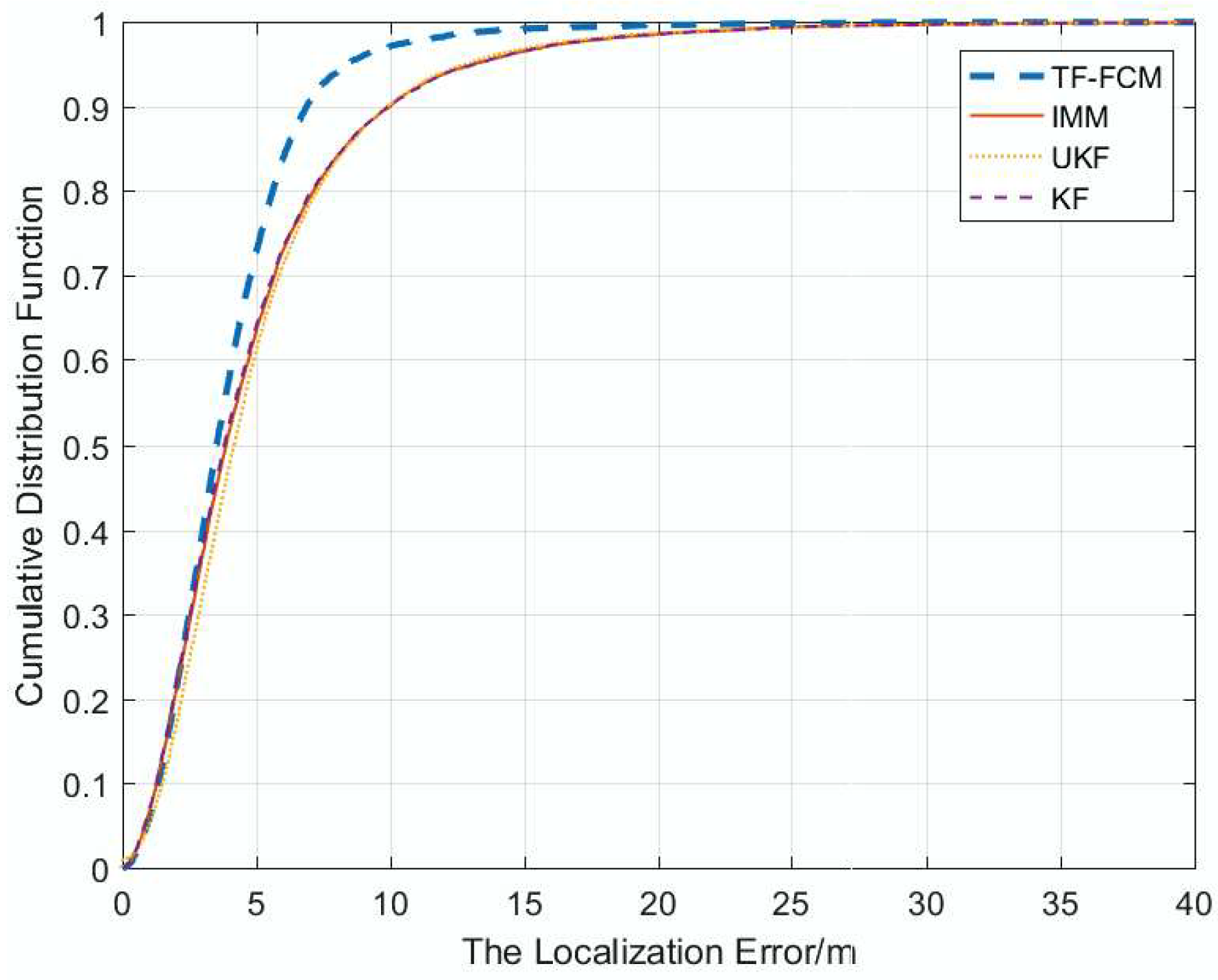
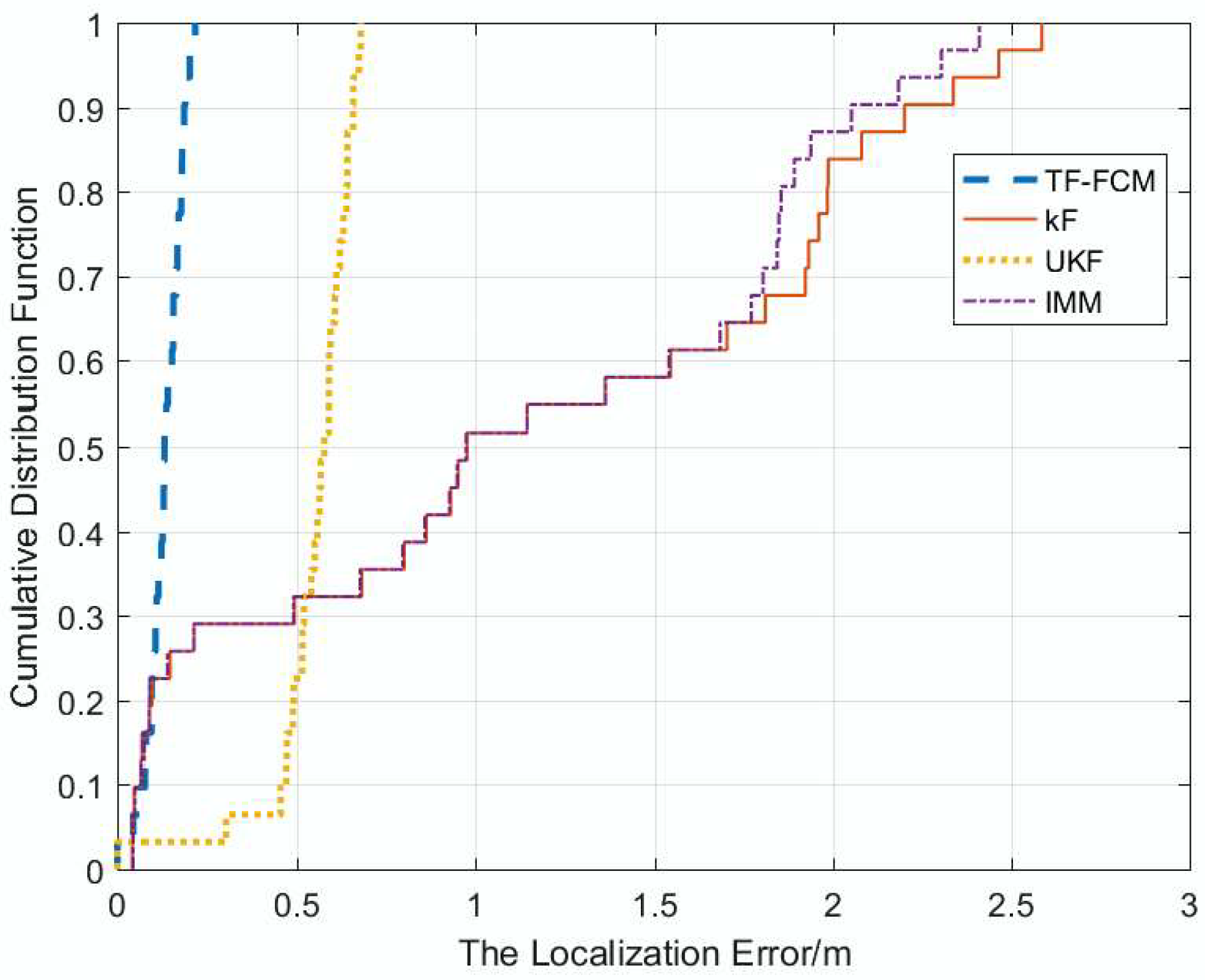
The algorithm is applied to different NLOS conditions, such as Gaussian Distribution, Exponential Distribution, and Uniform Distribution, which make our algorithm robust to a complex environment. An experiment has been conducted, and the result shows that our algorithm has better performance compared with KF, IMM and UKF.
This paper is organized as follows. Firstly, the symbol description will be given in
Section 2. The related works are described in
Section 3. Then, some descriptions about problem statement and a brief introduction of UKF and KF are described in
Section 4. Next, our algorithm is presented in detail in
Section 5, and
Section 6 will show the simulation and experiment results of contrast in the midst of our algorithm and other methods. Finally, the conclusions are made in
Section 7.
3. Related Works
With the extensive research on WSN, many researchers have proposed algorithms to deal with the NLOS condition. Among most methods, LOS and NLOS measurements are classified to mitigate the influence of NLOS errors and improve the accuracy of positioning. These methods are mainly range-based algorithms, which need point to point distance or angle information to estimate the location. In [
3], Liao proposed the classic Interacting Multiple Model (IMM), which is regarded as the classical algorithm to tackle NLOS problems. The significant contribution of [
3] is a two-state Markov switching model, which is used to measure the switching probability of NLOS and LOS measurements. In addition, the combination probability of IMM is updated by Markov switching probability. However, the NLOS identification method of IMM is fuzzy, which is not accurate enough to distinguish between NLOS and LOS errors. Furthermore, more NLOS parameter information and prior information is needed when filtering, which represents a lack of strong robustness. In [
4], Huerta proposed a joint PF and an UKF algorithm (RBPF). In this paper, a Bayesian model is used to fully exploit the LOS and NLOS measurements. PF and UKF are used to estimate the trajectory and kinetic variable (position and speed) of a mobile node. Although the experimental result shows great performance, the complex and comprehensive simulation scenario is needed to illustrate the robustness of the algorithm. Tomic proposed a target localization algorithm utilizing integrated measurements; namely, RSS and AoA in [
5]. Through convex relaxations and derivation of convex problems, global minima and solutions can be obtained. The most important contribution of his work is combined RSS and AoA, which produces a high-precision and -accuracy of localization, but the device complexity is high, and the identification of NLOS and LOS needs to be improved.
In addition, there are several studies based on ToA [
6,
7,
8]. Tomic proposed a bisection-based approach for exact target localization in NLOS environments [
6]. In this paper, he utilized the maximum likelihood (ML) estimator and converted the localization problem into a generalized trust region sub-problem (GTRS) framework. It has the same performance as existing methods, but the computational complexity is better. The great advantage of the proposed algorithm is its linear computational complexity. Nevertheless, its accuracy and precision need to be further improved. Pak proposed distributed hybrid particle/FIR filtering (DHPFF) for mitigating NLOS effects in TOA-based localization using wireless sensor networks in [
7]. In this paper, the hybrid particle finite impulse response filter (HPFF) was adopted in order to cope with the cases that NLOS noises generate. The advantage of this algorithm is that it can achieve self-recovery by detecting failures and resetting the algorithm. However, the computational complexity of DHPFF is too high to be applied to computers with poor computational power. Liu proposed a closed form localization method using AoA and ToA measurements based on WSN in NLOS environments in [
8]. This paper used a two-step weighted least square (WLS) estimator by means of the first-order error analysis. However, an experiment is needed, because the Gaussian distribution of simulation cannot cover all the complex situation in the real world.
NLOS identification is profoundly significant in most range-based algorithms. Hence, some methods have been proposed to address this issue better [
9,
10,
11,
12,
13]. Hua proposed an NLOS identification and positioning algorithm based on a localization residual in WSN in [
9]. A two-step algorithm to mitigate NLOS errors is proposed, including residual analysis addressing the positioning difference and a threshold hypothesis test. The simulation shows a good performance, but the algorithm needs an experiment based on a real scenario, and the hypothesis based on threshold needs much reliance on people’s subjective experience. Yang proposed NLOS identification for UWB localization based on import vector machine (IVM) in [
10]. In his paper, a novel NLOS identification algorithm with feature selection strategy has been put forward so as to ameliorate the classification accuracy. Besides, a localization algorithm based on IVM with high accuracy and low complexity is also a highlight, which produces higher positioning accuracy than Support Vector Machine (SVM) and Relevance Vector Machine (RVM), but the algorithm needs plenty of training data, and will perform poorly with few training sets. Lei come up with a robust cooperative indoor localization based on reliability evaluation in [
11]. The algorithm combines the advantages of compressive sensing (CS) in the LOS condition and the PF in the NLOS condition, and a reliability evaluation is also proposed to evaluate the estimation results of CS and PF. However, the NLOS identification of this method is based on reliability evaluation, which is not accurate to distinguish the NLOS and LOS measurements. Aghaie presented localization of WSN nodes based on NLOS identification using AoAs statistical information in [
12]. The main idea of this paper is the identification of NLOS nodes based on the statistical model of the measurement and the NLOS errors where they utilized an NP method to judge a threshold. Yu put forward a mean shift-based mobile localization method in mixed LOS/NLOS environments for a wireless sensor network in [
13]. A novel mobile localization method is presented in order to overcome the effects of NLOS errors by utilizing the mean shift-based Kalman filter, but the NLOS identification is based on the hypotheses and alternatives methods. These methods need prior thresholds.
Apart from the Maximum Likelihood (ML) based on the parameter estimation methods mentioned above, there are also other popular approaches in the family of ML-based parameter estimation. The iterative Space-Alternative Generalized Expectation Maximization Algorithm (SAGE) introduces some hidden data to simplify the ML estimation [
14]. A soft-input soft-output (SISO) version improves robustness, which is applied to joint successive interference cancellation and channel estimation [
15]. The iterative method is called multiple-input multiple-output space division multiple access (MIMO-SDMA), which approaches the maximum likelihood estimate with fast convergence and low complexity [
16].
4. Problem Statement
This section is made up of three parts: signal model and brief introductions of UKF and FCM. In
Section 4.1, some necessary assumptions and important definitions about NLOS are proposed to better describe the algorithm. In
Section 4.2 and
Section 4.3, a brief presentation about the methods is given, including FCM and UKF. In
Section 4.2, a brief description of UKF is made, which is used to cope with NLOS errors. In
Section 4.3, an introduction about FCM is used to classify NLOS measurements into two categories: hard NLOS measurements and soft ones.
4.1. Signal Model
In this section, some technical preparations are introduced to describe the algorithm.
beacon nodes are randomly distributed in field with the coordinates given by
,
The coordinate of unknown node at the time
is
,
Hence, the true distance
between the
-th unknown node and the beacon node at time
[
17,
18,
19] can be expressed as:
Due to the existence of measurement errors, the noise of actual measurement distance
under LOS condition can be approximated by Gaussian white noise. So the LOS measurement distance can be expressed as follows:
where
is the measurement noise obeyed Gaussian Distribution with zero mean and
, i.e.,
The probability density function of
can be expressed as:
In actual scenario, there are obstacles between beacon nodes and mobile node, which result in the propagation distance is longer than true distance. Thus, some NLOS noise
can be added to measurement distance
:
Moreover, the NLOS error
is usually regarded as positive, which obey Gaussian, Uniform, or Exponential Distribution. The probability density function of
obeyed Gaussian Distribution (
) can be described as follows:
And the probability density function of
which obeys to Uniform Distribution (
) is given by:
The probability density function of
which obeys to Exponential Distribution (
) is given by:
4.2. A Brief Introduction to UKF
In our algorithm, UKF is utilized to tackle NLOS measurements including hard NLOS measurements and soft ones. In this section, the advantages of UKF are firstly introduced. Then, an important technique UT transform that is used in UKF will be discussed to better introduce UKF. Finally, the brief implementation steps of UKF will be given.
UKF is an algorithm that uses sampling points to estimate nonlinear distribution and its main frame is based on KF. KF is the most commonly used filter in WSN localization, but KF is proposed to solve problems based on a linear system that the noise is assumed as Gaussian white noise, and it is ineffective when filtering non-linear noise. After that, researchers proposed an algorithm to linearize nonlinear systems, which is known as Extended Kalman Filter (EKF), but the linear processing of EKF causes great calculation errors, even causing the filtering results not to converge. Moreover, EKF needs to calculate Jacobi matrix increasing the amount of calculation. Later, Simon J. Julier introduced Unscented Transformation (UT) to the analysis of KF, which obtained a higher precision and a lower algorithm complexity than EKF.
UT is the most important part of UKF that is different from EKF. UT is a conversion when calculating statistical characteristics of random variables in a nonlinear transformation. UT calculates posterior statistical properties of random vectors by means of weighted statistical linear regression. The selection of the sampling strategy in the UT transform has a vital impact on the estimation results. The sampling strategy of UT includes symmetric sampling, simplex sampling, third-order moment skew sampling, Gaussian distribution fourth-order moment symmetric sampling, etc. The difference between the sigma points produced by the various sampling strategies is the distance and the weight to the center point.
UKF is based on UT, abandoning the traditional method and using KF as its main frame. For one-step prediction equations, UKF uses UT to handle the nonlinear transfer of mean and covariance. More importantly, UKF approximates the probability density distribution of nonlinear function, and uses a series of determined samples to approach the priori probability density of the state, rather than approximating the nonlinear function. UKF does not linearize to ignore high order terms, therefore, the nonlinear distribution statistic has higher calculation accuracy [
20,
21,
22,
23].
Above all, UKF is an iterative estimation algorithm selecting sigma points according to feature distribution of sampling points. These sigma points iterate through a state equation and become the prediction points. The results are constantly corrected by Kalman gain and the errors between the true value and the measurements. Finally, the optimal estimated value can be obtained [
24].
4.3. A Brief Introduction of FCM
FCM is used to classify the NLOS measurements into two categories: hard NLOS measurements and soft ones. In this section, firstly, the main feature of FCM will be discussed. Then, some basic concepts used in FCM will be explained, namely, fuzzy sets and membership function. Finally, the advantages of FCM are given to illustrate that it is appropriate to use FCM in our algorithm.
FCM is a commonly used clustering algorithm. According to a similarity criterion, a set of sample datasets without class identification is divided into several subsets. The Fuzzy C-Means (FCM) algorithm is a partition-based clustering algorithm. Its main idea is to maximize the similarity among objects divided into the same cluster, and minimize the similarity among different clusters. FCM is the improvement of the ordinary C-Means algorithm. The traditional C-Means is Crisp Partition such as K-Means, while the FCM is based on a fuzzy and flexible division according to the membership of each element. FCM clustering is an unsupervised method of gradual optimization based on iterative thinking. This method is to use the least squares principle to iteratively optimize the objective function so as to realize the fuzzy division of the dataset. On one hand, its local convergence property is very good. On the other hand, the algorithm is also effective for high dimensional characteristic space [
25].
Fuzzy sets and membership function are the most important concepts of FCM. The membership function indicates the extent to which an object belongs to the set , which is usually expressed as . Its independent variable range is all objects that may belong to set (which means all points in the space where set A is located), and the value range is [0,1], that is . Thus, means is fully affiliated to set , which is the equivalent of the traditional set concept . A membership function defined in space can be given as a fuzzy set , or can be called as a fuzzy subset defined in space . With the concept of fuzzy sets, it is not hard for an element that belongs to a fuzzy set. In the clustering problem, clusters generated by clusters can be regarded as fuzzy sets. As a result, the membership value of each sample point is in accordance with the following relationship: .
FCM divides n-dimensional vectors into fuzzy groups, and finds the cluster center of each group, so that the value function (or objective function) of the non-similarity index is minimized. The advantages of FCM mainly include the following aspects:
The idea of FCM can objectively reflect the authenticity of things and comply with the characteristics of human cognition of things.
After the given initial parameters, FCM does not need manual intervention in clustering, which is an unsupervised process. It can complete clustering only by dataset, which is more suitable for automatic processing.
FCM is fuzzy, especially suitable for the problems of uncertainty and ambiguity.
5. Proposed Method
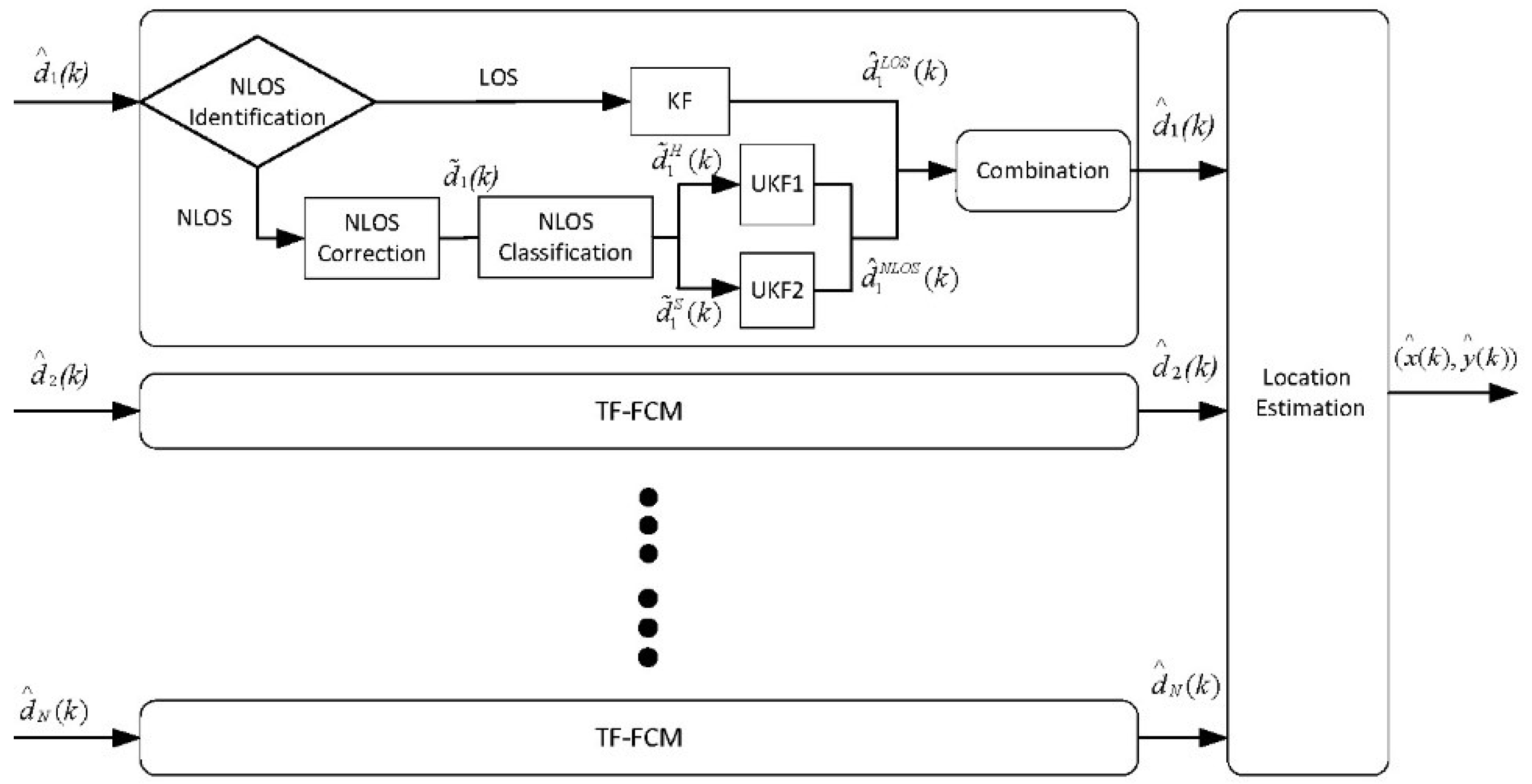
The flow chart of our algorithm is shown as
Figure 1. The input of TF-FCM is
(
).
indicates the measurement at time
, and
indicates the number of the beacon nodes. The output of TF-FCM is the prediction coordinate
. Firstly, the NLOS identification algorithm based on residual analysis is proposed to identify the propagation conditions. Then, if the propagation is NLOS condition, KF is presented to cope with the measurements. For the NLOS situation, NLOS correction algorithm based on voting is proposed to deal with it in advance, and the processed measurements after voting will be classified by NLOS classification based on FCM. Hard NLOS measurements and soft ones will be classified after FCM. Hard NLOS measurements will be processed by UKF1, and the soft NLOS measurements will be processed by UKF2. The NLOS measurements after filtering can be obtained by calculating arithmetic average. Finally, the LOS and NLOS processed measurements will be combined by weights. The processed measurements are used to calculate coordinates of a mobile node by maximum likelihood (ML) localization.
5.1. NLOS Identification Based on Residual Analysis
In case that the NLOS errors data is unknown, this paper assumes that there are
(
) measured distances from
beacon nodes. If each group has no more than three distances,
different combinations can be calculated to group
measurements:
Then, the index of every combination is defined as
. After estimating each node’s coordinate by location estimation, the estimated position
of every combination
and corresponding residual
can be obtained. The residual of
is given by:
And the average residual can be defined as:
Average residual
is utilized to compare with the process noise
to identify the propagation status of the measurements.
where the
indicates the state (1:LOS, 2:NLOS) of the measurements.
The description of residual analysis is as follows (Algorithm 1):
| Algorithm 1. Description of Residual Analysis |
Input:
Output:
begin
for i = 1 : Size of do
end for
for i = 1: do
end for
if then
else
end if
end |
5.2. NLOS Correction Algorithm Based on Voting
If measurement
is identified as NLOS, which means
contains many NLOS errors, a voting algorithm is used to mitigate the influence NLOS errors. The voting matrix is constructed to provide the initial estimated location to obtain the correction distance. To begin with, assume the area of the field is
, and it can be divided into
cells which depend on the estimation accuracy and computational complexity of the algorithm [
22], and the location of each grid can be expressed as
, for
. The resolution of each grid is defined as
. For instance, if the field is
and
, the resolution of cells is equal to:
.
The algorithm consists of the following steps.
Step 1: An
voting matrix
is constructed to estimate the distance, and the elements representing voting results can be expressed by:
where
indicates the number of notes increased at each grid, which can be defined as:
where
represents the Euclidean distance between
-th beacon node and
.
is the measurement distance of the
-th beacon node. The value of
can be adjusted to make estimation more accurate, and here
.
Step 2: The largest value in the voting matrix can be obtained, which is marked as
, and
. The estimated location of mobile node is
, where
is the initial results set and
represents the number of elements in
, and the estimated location of the mobile node is given by:
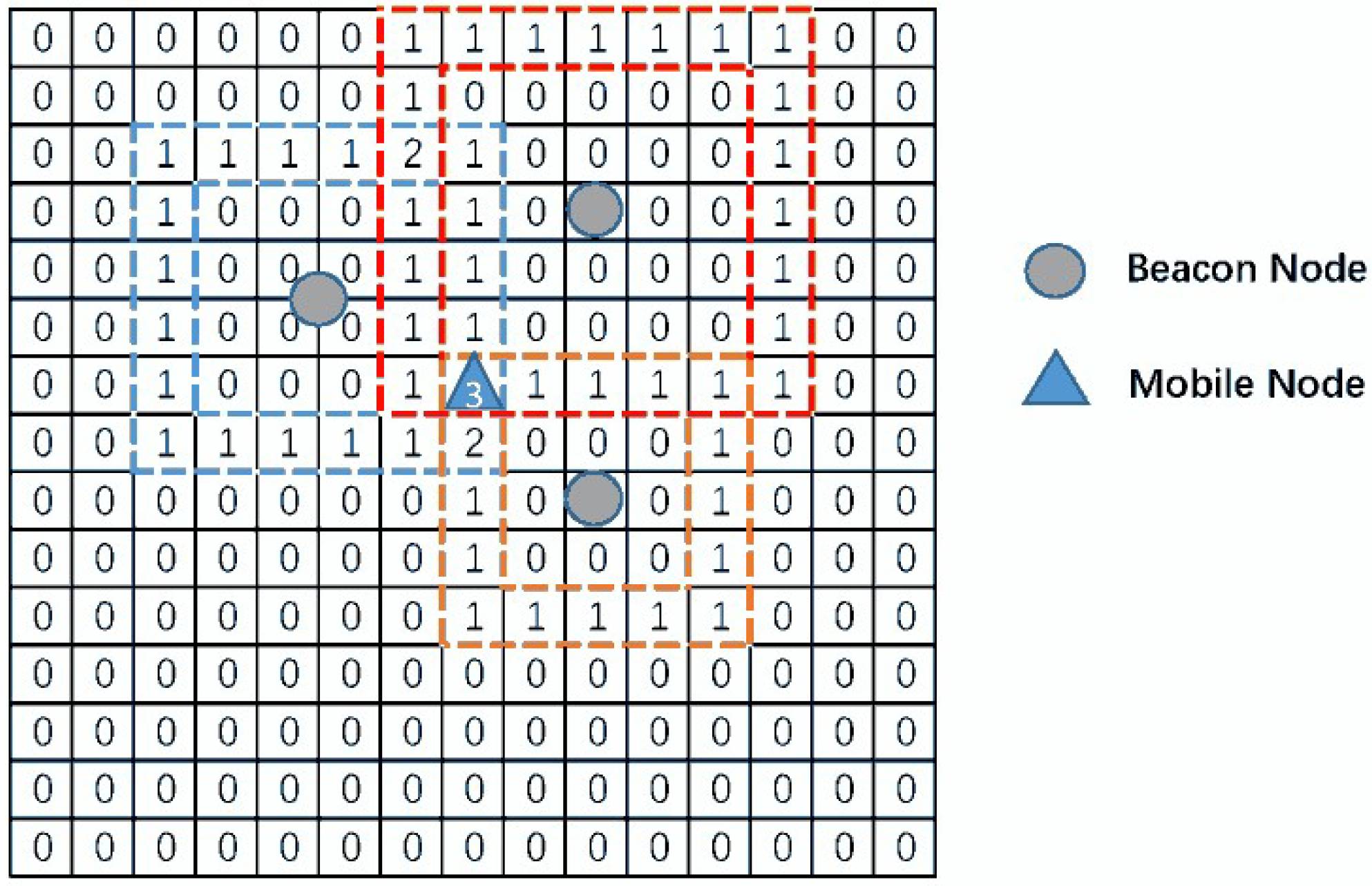
The brief description of
Step 2 is illustrated as
Figure 2. The vote of each grid will increase if the measurement area of beacon nodes is overlapped.
Step 3: The corrected distance
of the
-th beacon node can be updated as:
where
represents the location of the
-th beacon node.
Based on the aforementioned descriptions, the pseudo code of Voting can be summarized as Algorithm 2:
| Algorithm 2. Description of NLOS Correction Algorithm based on Voting |
Input:
Output:
begin
for i = 1 : N do
for m = 1 : W do
for n = 1 : W do
end for
end for
end for
for i = 1:N do
end for
end |
5.3. NLOS Errors Classification Based on FCM
Because the real distribution of NLOS is complex, it is impractical to know the parameters of NLOS errors. In order to tackle this problem, FCM is used to approximate the arbitrary probability density by adjusting its parameters.
Let
denote the range from
-th beacon node at time
after voting.
measurements from the
-th beacon node can be obtained over a time slot
. In order to make our statement simpler, time interval
is introduced to indicate the time slot, for example,
. Let
denote the number of cluster centers (
). Here, we set
. Let
indicate cluster centers set. Let
indicate the membership between the
-th distance
at time k and the
-th cluster center
, and the membership matrix is given by
whose size is
.
indicates the Euclidean distance between
and
:
, and FCM can be expressed as a mathematical planning problem:
where
m represents the fuzzy weights factor and
meets the following formula:
Cluster center can be derived as follows to calculate the minimum value of the objective function based on the Lagrange multiplier method.
The sorted cluster center
can be obtained. Since the NLOS error is of a positive bias and the largest value contains many NLOS errors, so the final result is given by:
Hence, the classified distance can be described as follows, and the measurements are divided into two categories: hard NLOS measurements and soft ones.
Based on the aforementioned descriptions, the NLOS error classification algorithm based on FCM can be summarized as the pseudo code shown in Algorithm 3:
| Algorithm 3. Description of NLOS Errors Classification Algorithm based on FCM |
Input:
Output:
begin
while 1 do
for i = 1 : c do
for j = 1 : M do
end for
end for
if then
if then
else
end if
break
end if
end while |
5.4. Kalman Filter
For LOS, KF is used to process LOS measurements. To explain the state more precisely, a state vector of the
-th beacon node is defined as:
where
indicates the distance between the
-th beacon node and the mobile node and
indicates the velocity that
varies.
The state equation of the
-th beacon node under NLOS can be denoted as follows:
where
,
denotes the sample period [
26].
is measurement noise and follows identically distributed Gaussian Distribution with variance
.
Hence, the predicted state and prediction covariance can be expressed as:
The measurement residual is given by , where indicates the measurement state of mobile node and .
And
is defined as:
where
indicates the covariance matrix of measurement errors.
The Kalman gain is described as:
The Kalman update equations can be expressed as:
In the end, the algorithm pseudo code of KF can be expressed as Algorithm 4:
| Algorithm 4. Description of KF |
Input:
Output:
|
5.5. Unscented Kalman Filter
The main algorithm includes three procedures, namely, selection of sigma points, prediction and update [
19]. To begin with, assume that the nonlinear system is:
where
and
represents the Gaussian white noises in state variable
and measurement variable
.
The initial state vector can be denoted as
, which indicates the initial distances of the
-th beacon node [
20], and
indicates the mathematical expectation of
:
For the hard NLOS case, the state can be expressed as ; for the soft NLOS case, the state can be expressed as , and the covariance of the -th beacon node is defined as .
Step 1: Select sigma points. Assume that state vector is an
dimensional random variable, so the sample points (Sigma points) are
, and the estimated sigma points
can be described as:
Step 2: Prediction. The system state equation is used to carry out the
nonlinear transformation for each Sigma point, and the points set after transformation can be expressed as:
where
denotes bounded nonlinear state transfer function which is determined.
Then one-step prediction state value
and covariance matrix
are given by:
Weight coefficient
can be given by:
where
indicates turning parameters to control the spread of the sigma points.
A new Sigma points set can be produced according to a one-step prediction state value:
Nonlinear transformation is performed to Sigma points set
by nonlinear observation equation:
where
denotes non-linear observation equation function.
The system’s predicted observation values
are obtained by weighted sum:
Step 3: Update. The covariance is updated by:
The covariance matrix of system measurement output variables is given by:
where
denotes the covariance of the observation noise.
And the Kalman gain
is expressed as:
The updated state
and a posteriori covariance
are expressed as:
The final NLOS measurements after filtering can be expressed as:
where
and
denote hard NLOS measurements and soft ones after UKF filtering.
5.6. Combination and Location Estimation
Two sorts of estimated distances from KF and UKF can be obtained, respectively, and the final estimated distance
is updated as follows:
A maximum likelihood localization method is utilized to estimate the mobile position according to the distance after filtering. The coordinate of the -th beacon node can be expressed as .
At time
, the position of a mobile node is
. The relation between coordinates of the mobile node and the coordinate of the
-th of beacon node can be modeled as [
27]:
The equation above can be represented by linear equation
, where
and
are expressed as follows:
Finally, the simplified estimated coordinate
of a mobile node at time
can be derived as:
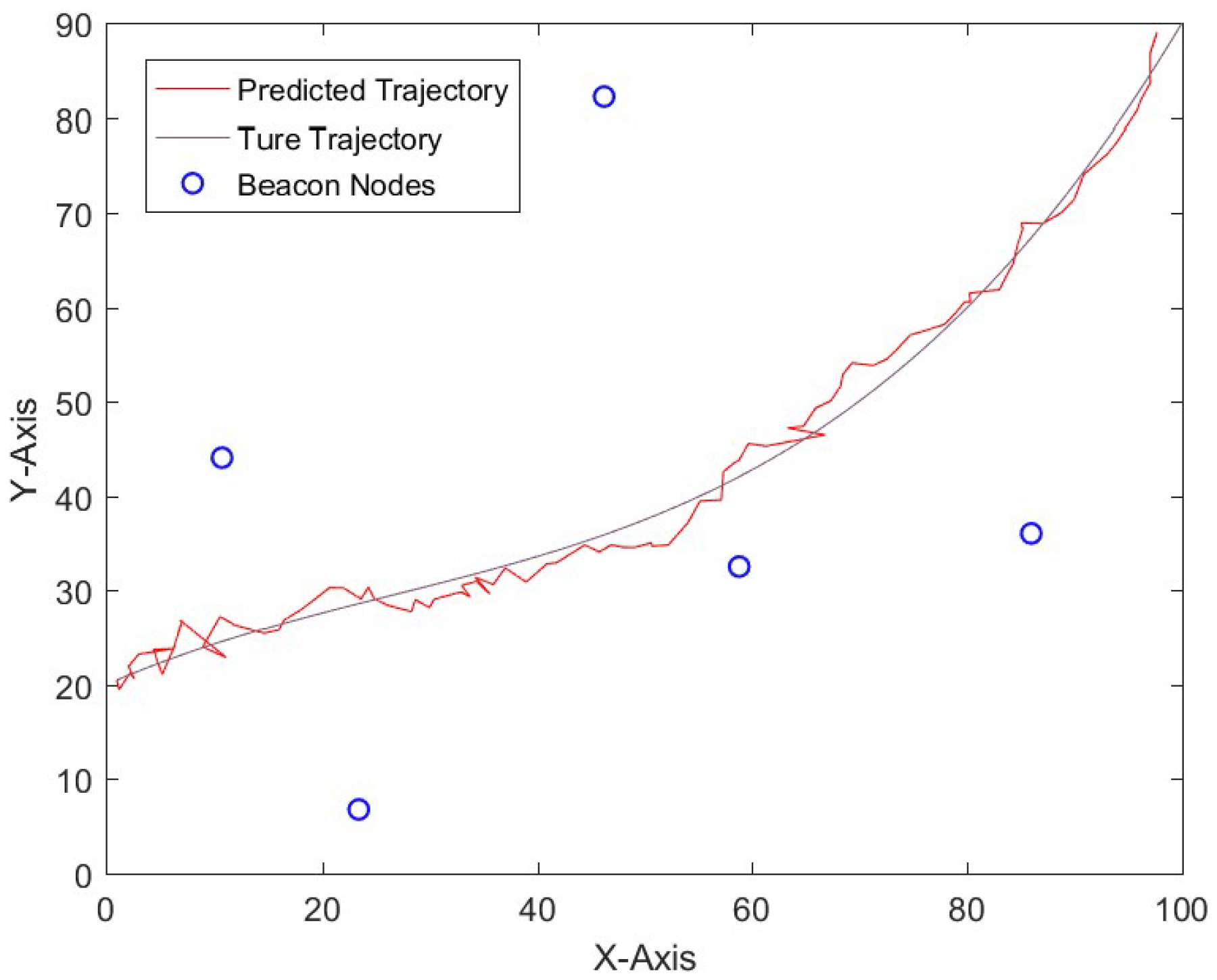
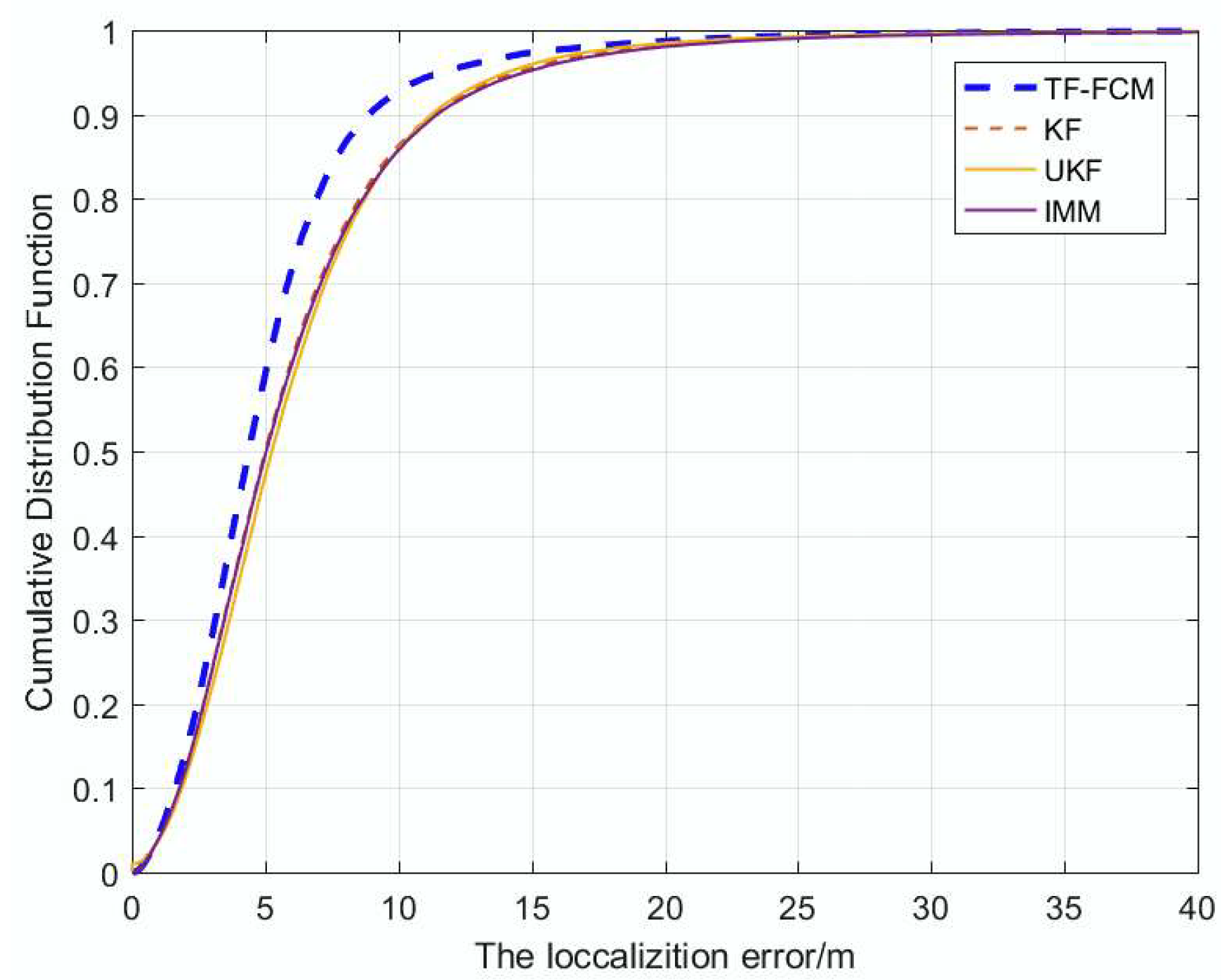
7. Conclusions
In this paper, an algorithm based on triple-filter mixed KF and UKF, using residual analysis, voting and FCM is proposed, which is utilized to mitigate NLOS errors and enhance the accuracy of localization in mixed LOS and NLOS environments. Residual analysis is employed to identify if the propagation condition is NLOS or not. For LOS case, KF is adopted to process. For NLOS case, firstly NLOS correction algorithm based on voting is used to restrict the NLOS errors and correct the measurements. Then, the NLOS error classification method based on FCM is proposed to classify the NLOS errors into two categories: hard NLOS measurements and soft ones. The simulation result shows great advantage when processing the situation with complicated NLOS errors, including Gaussian distribution, exponential distribution and uniform distribution compared with IMM, UKF and KF. The performance of TF-FCM has significantly improved in accuracy and robustness when dealing with rough wireless environments. Furthermore, TF-FCM could efficiently mitigate the NLOS effects compared with other classical methods. An experiment is conducted to verify our algorithm, and the result shows the high accuracy and strong robustness of TF-FCM.