Privacy-Preserving Vehicular Rogue Node Detection Scheme for Fog Computing
Abstract
1. Introduction
- Providing an authentication scheme to secure communication between fog nodes.
- Employing fog computing to improve security in VANETs.
- Improving vehicle privacy by allowing the exchange of traffic data between vehicles through fog nodes.
- Detecting rogue vehicles and correcting their provided data.
- Protecting vehicles against collusion.
- Improving efficiency by reducing the computational overhead for a vehicle by executing the traffic calculation using fog nodes.
2. Related Work
2.1. Authentication Scheme in VANET
2.2. Rogue Nodes Detection
2.3. Security in Fog Computing
3. Privacy-Preserving Vehicular Rogue Node Detection Scheme for Fog Computing
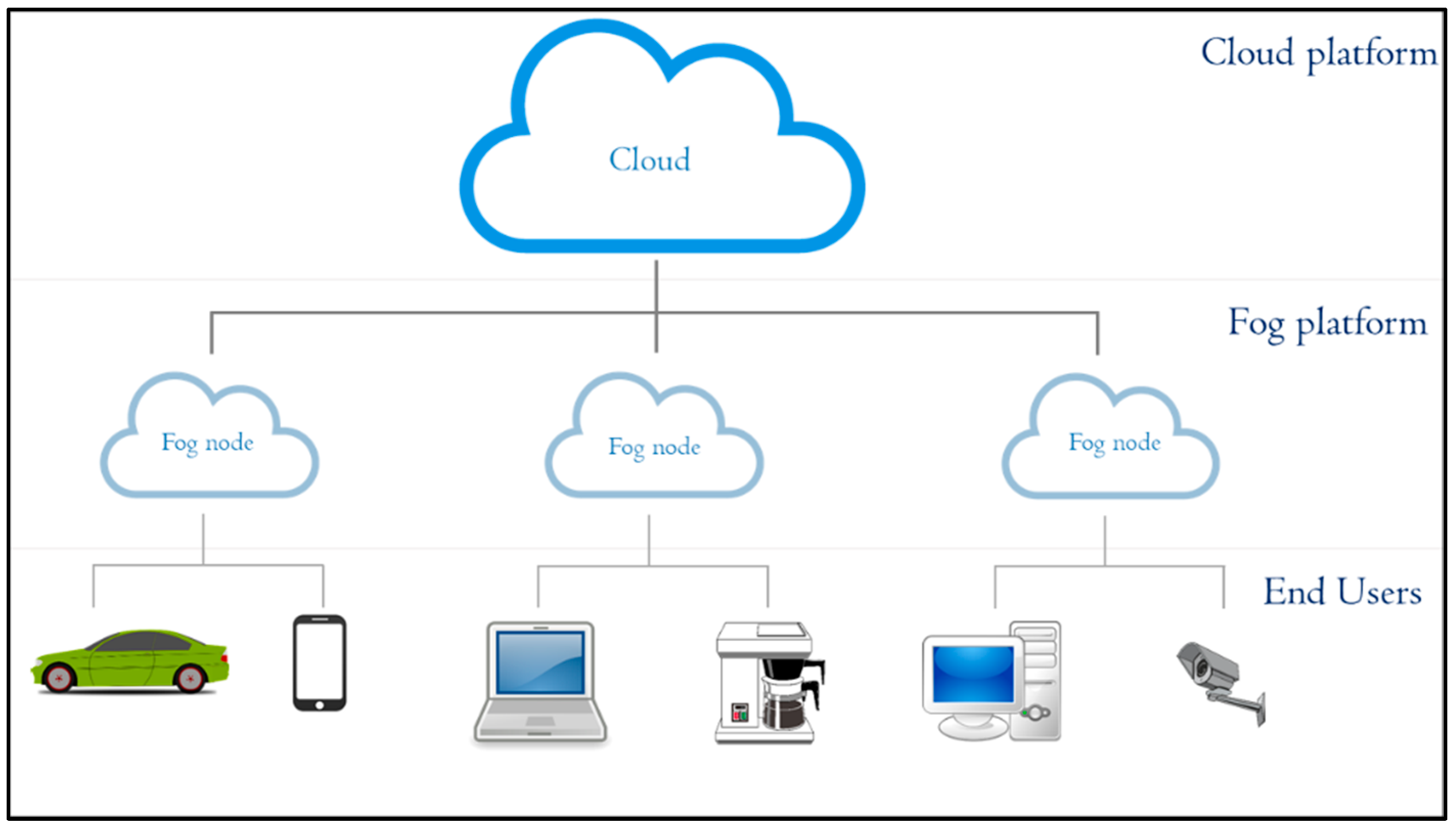
3.1. System Overview
3.2. Attacker Model
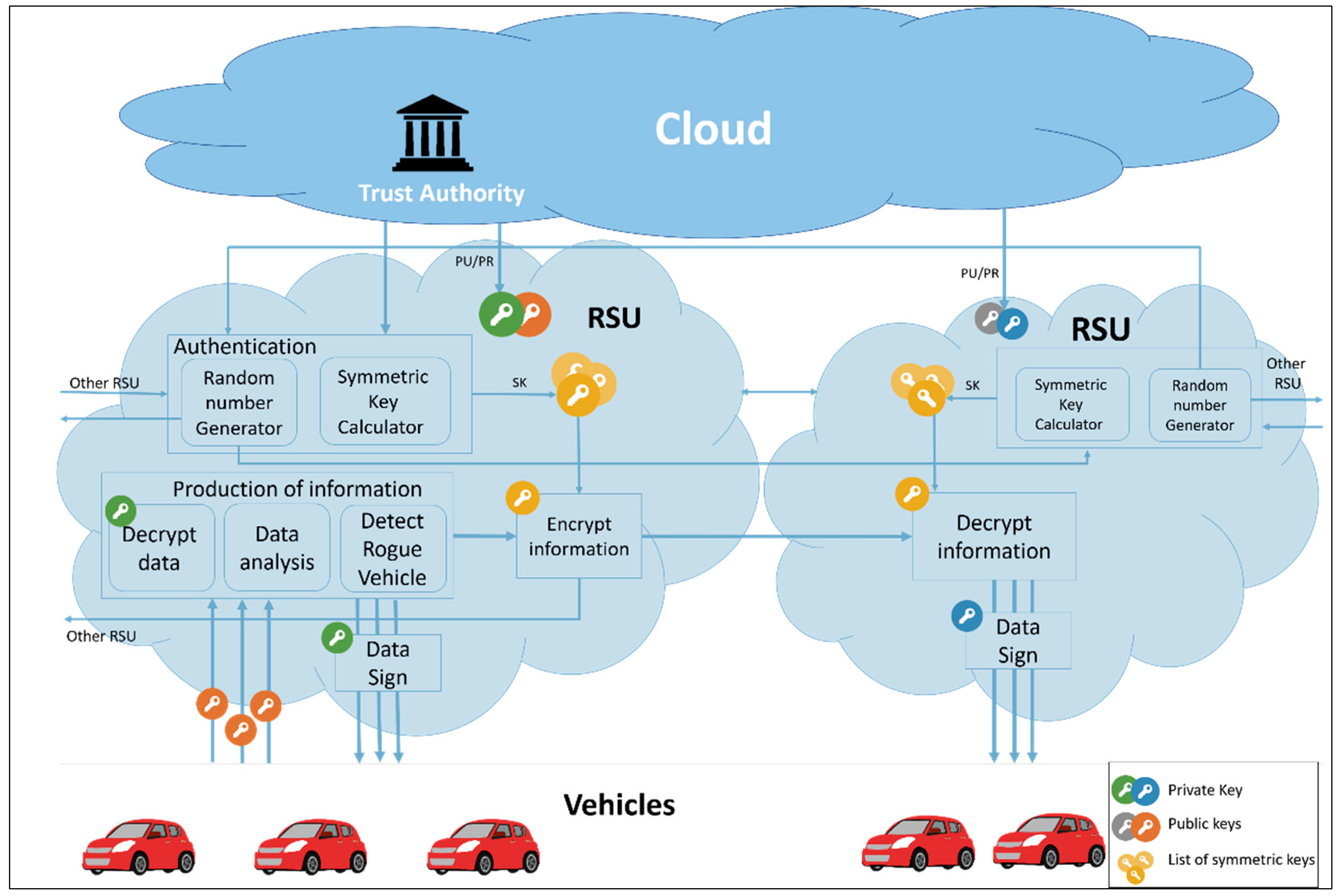
3.3. Methodology Description
- Initial key provided by the trust authority .
- RSU generates a random seed .
- Symmetric key calculated using the authentication key and the random seed generated .
- Each RSU sends its random seed to other RSUs in the network .
- Each RSU will locally calculate for other RSUs.
- Each RSU will store with the calculated .
- The initial key will be hashed and will used in the next cycle .
- After a designated period of time, each RSU will update its symmetric key and the stored list of keys by recalculating the symmetric key using the random seed and the hashed key .
- The hashed key will be hashed again to use it in the next cycle .
| Algorithm 1. Symmetric key generation at RSUx. |
| , random seed for other RSU = = GenerateRandomSeed() 3. for all RSU in the network 4. = RecievingRandomSeed from RSU i 5. StoreRandomSeed(, ) 6. end 8. for all RSU in the network 9. 10. StoreSymmetricKey(, ); 11. end 12.; 13. if (timeout) 14. Go to step 7 |
3.4. System Implementation
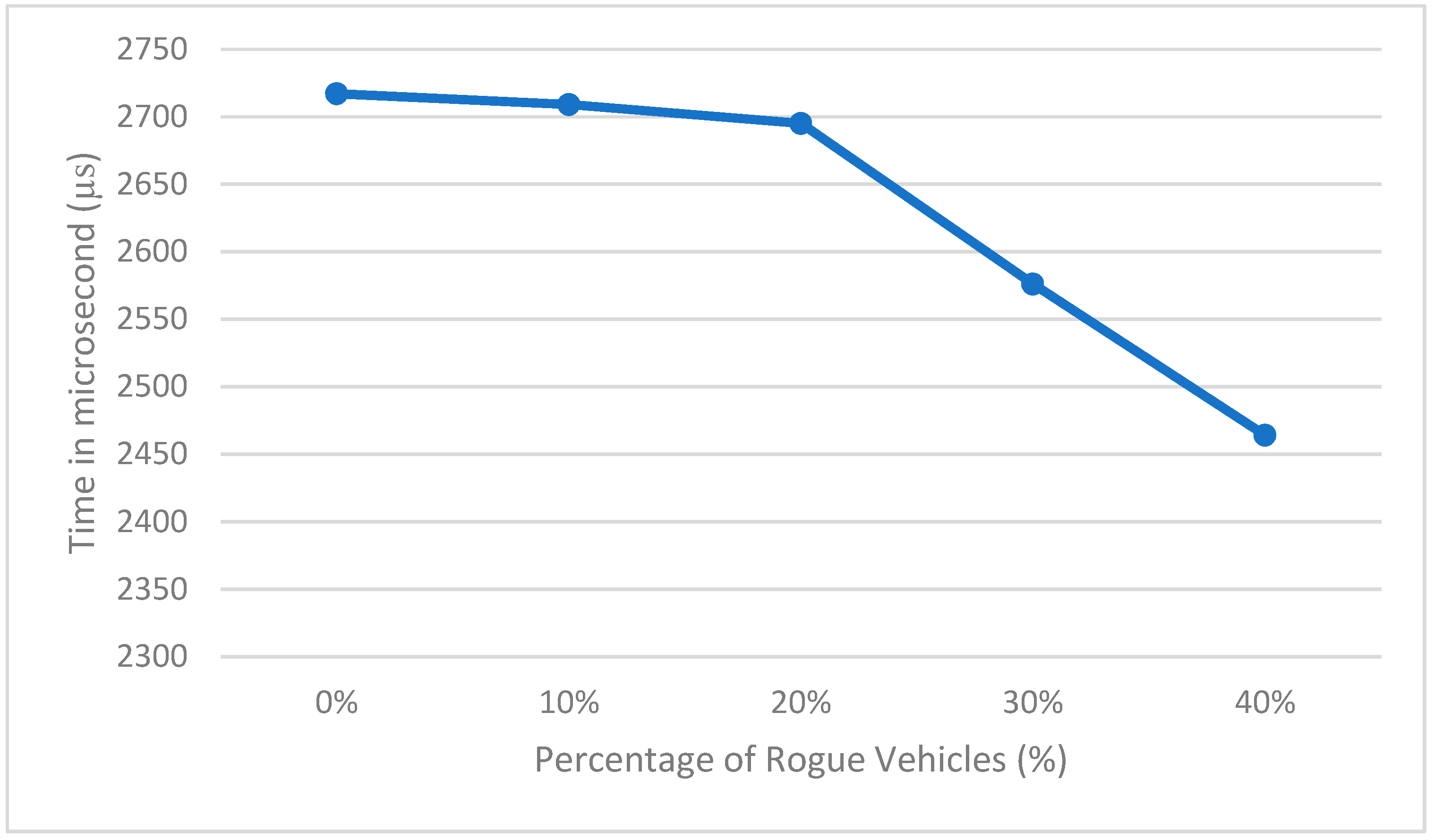
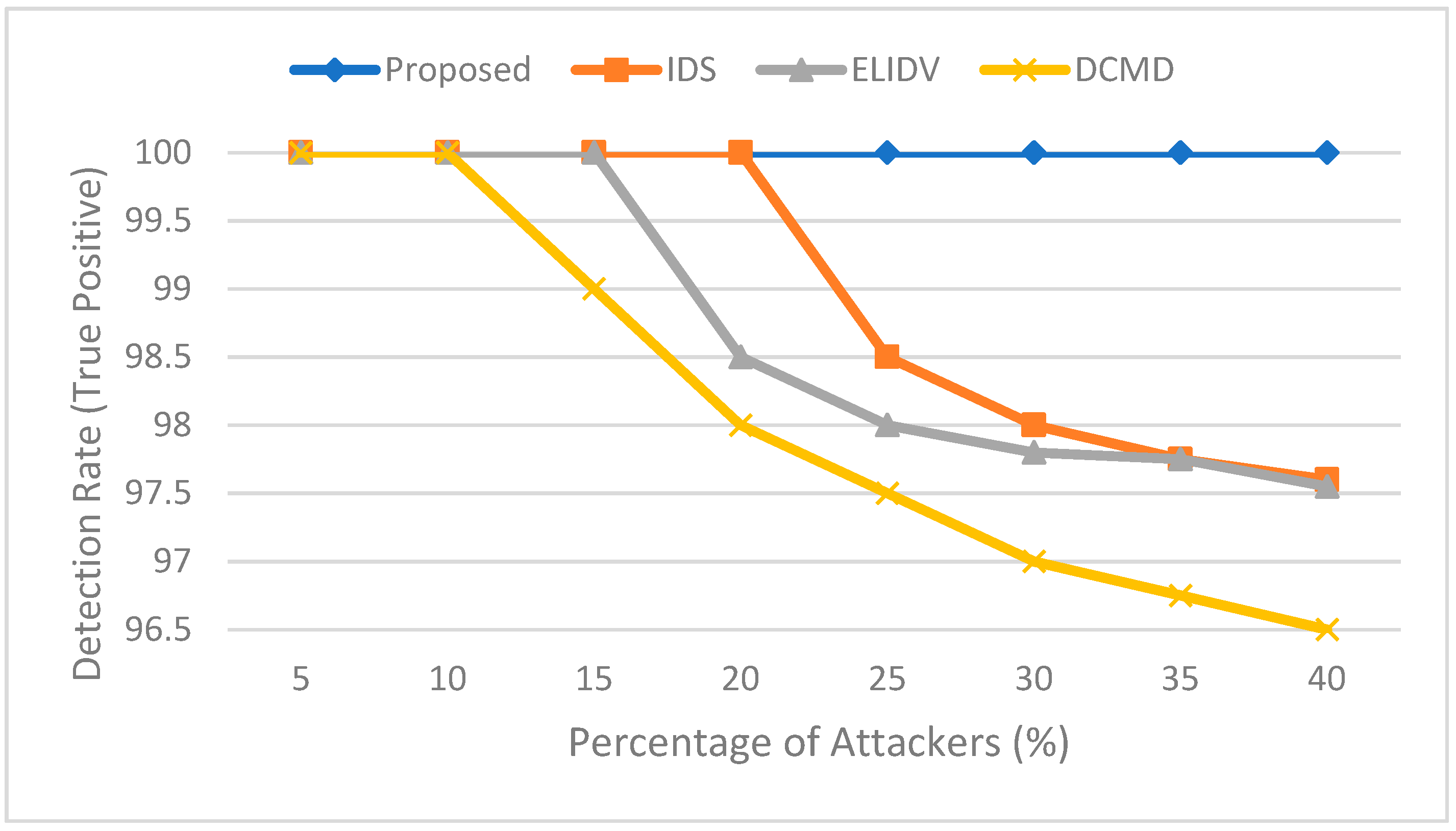
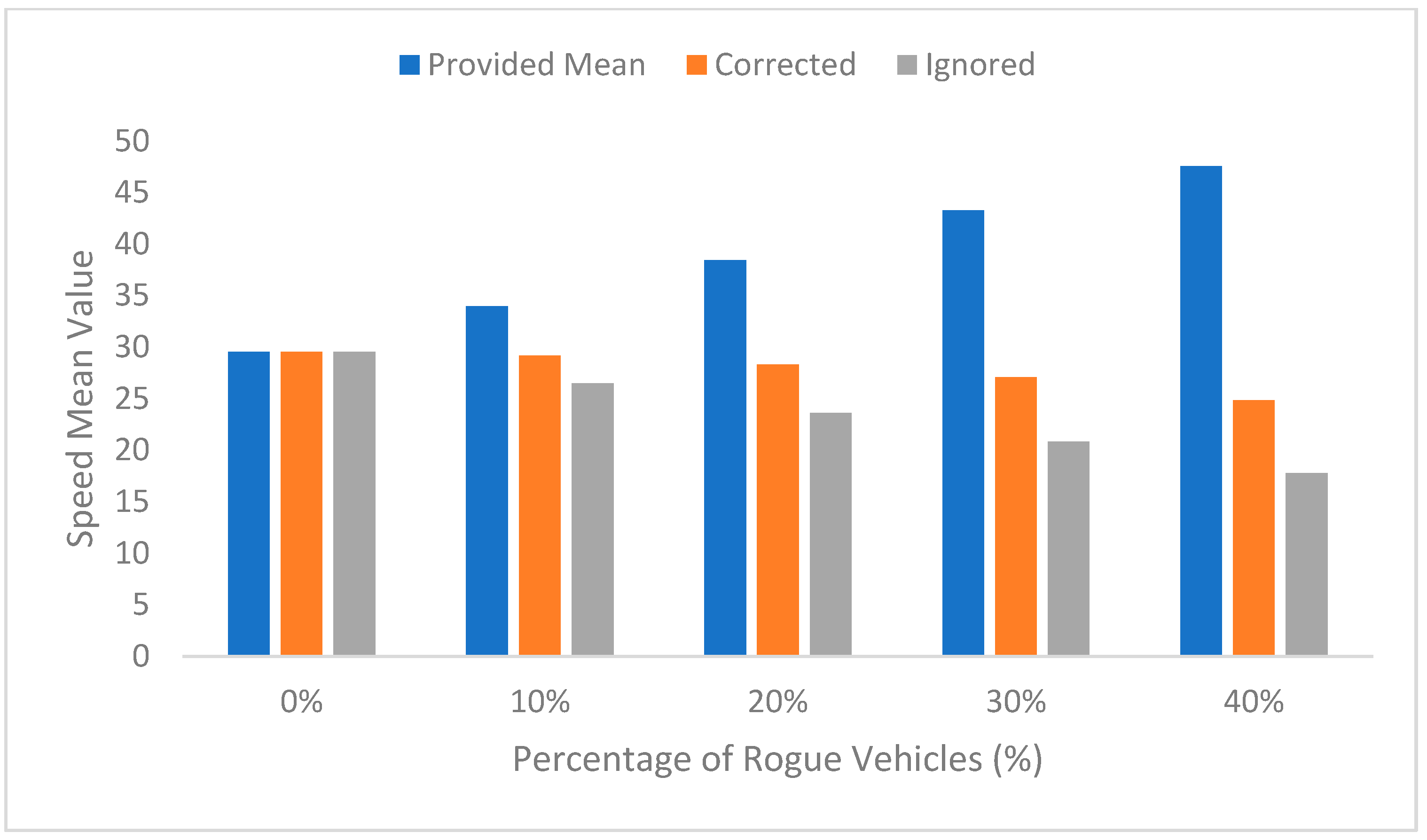
4. Experiment Results and Analysis
- Processing time: This is the time needed to process all the data provided.
- Scalability: This is the capability of the system to process data as the number of vehicles increases.
- Overhead: This indicates the additional messages exchanged on the network in order to detect the rogue vehicle.
- Detection rate: This is the percentage of rogue vehicles detected and classified as rogue vehicles.
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| AP | Access Point |
| CAN | Controller Area Network |
| CDH | Computational Diffie–Hellman |
| DCMD | Data centric misbehavior detection |
| DoS | Denial of Service |
| ELIDV | Efficient and Light-weight Intrusion Detection mechanism for the Vehicular network |
| FOCUS | Fog computing based security |
| ID | Identity |
| IDS | Intrusion Detection System |
| IoT | Internet of Thing |
| LBE | Location-based encryption |
| MAC | Message Authentication Code |
| OBU | On-Board Unit |
| PK | Public Key |
| PKI | Public Key Infrastructure |
| REST-Net | Rule-Enforced Security Technique for VANETs |
| RSU | Road Side Unit |
| SK | Private key |
| TESLA | Timed Efficient Stream Loss-tolerant Authentication |
| V2I | Vehicle to Infrastructure |
| V2V | Vehicle to Vehicle |
| VANET | Vehicle Ad hoc Network |
Appendix A. System Implementation Data Details
| 1 | MFswDQYJKoZIhvcNAQEBBQADSgAwRwJAVxrbiSEL5Sf1EcUHQkhU34LNCl4zqXZq j4MQ2E8sJuizmJLnAOdyEq/yIlDOOVYPMgbt5s4f95/oWCnzZyUQFQIDAQAB | MIIBOQIBAAJAVxrbiSEL5Sf1EcUHQkhU34LNCl4zqXZqj4MQ2E8sJuizmJLnAOdy Eq/yIlDOOVYPMgbt5s4f95/oWCnzZyUQFQIDAQABAkAiqgSOCQGz23fy72cZILHu FR7GLoD+wqpbnHw6qR9YCDJw6PA08zu+02Kmsy85+eGFeNz2D+sM3LmsGXdT4DfN AiEAmcoWls0nbt0eypnuRPWKHEZzy0X4vLJjSVhKByNQmpcCIQCQ/v2Nxr5n4JAW 9BK8faEFQJLnvs++Iqii4N2uRrhcMwIhAIa+js4wEAXNzaW7+w0Giay+ecQ3mXlT XzSrG6lnYr8fAiAdt6VQAYPU1nmxuqR8bWMrKGjzhnAdkAzwFRZaObRfcQIgM6h5 EUkax05llb8IGNhMFWokdDIenpdm1F/B0Sknl8I= | 33 |
| 2 | MFswDQYJKoZIhvcNAQEBBQADSgAwRwJAWWxbte1ThfwfcuQwf6lG7B504fPfSwCp wjnA7iAi7a+MSyIglooy/v8SZZpz7hmPP9Fw2FAWJaLSwXbeNBbyEwIDAQAB | MIIBOQIBAAJAWWxbte1ThfwfcuQwf6lG7B504fPfSwCpwjnA7iAi7a+MSyIglooy /v8SZZpz7hmPP9Fw2FAWJaLSwXbeNBbyEwIDAQABAkBGa5jFagHub5/sgFrZDdt2 Mn3lOoHLtNf6xjRy0gfvmPK1nJilOC+ZYL1FC+QDYYY9zQIg1H8FFXs5+0rRAhrR AiEAnK/LzUO0cxMSmA5kSMZ9YF2Sq4bBxc9oph+kI/MK/J0CIQCSGk3P92SfG0Xb 4XLloAm83DebxacyAHixMXrtOXPybwIgGUmh+bnQmLXeTV4dP0WRnIjdkANKqLMl r5Hxur+R6V0CID9Zun2/ltjKmZsDAbABmddTYaVgqeOrgqnKe7PbIqRvAiEAgvBi zVjHaH9MZKR/RCXsJlAzeKPR//uEeJfQnat+Ja4= | 33 |
| 3 | MFwwDQYJKoZIhvcNAQEBBQADSwAwSAJBAO4zKT34b1MRSoFeyaOmPo6yOFS8n88K Fehb6Ac27P+Ff7Ru3KXV5Scr4yDEO+tsP36Oj/poIPJQFA4gExe0GzUCAwEAAQ== | MIIBPQIBAAJBAO4zKT34b1MRSoFeyaOmPo6yOFS8n88KFehb6Ac27P+Ff7Ru3KXV 5Scr4yDEO+tsP36Oj/poIPJQFA4gExe0GzUCAwEAAQJBAKStAgoxwuTuw0+FNGnK +Ny2IXOTo/gCxPqK73JtapOLZizEbDbGgNZmNkivYU2yKS4OrdawBdAU6/62lYsO 41ECIQD7LxO22yyyQpyR8ciOrZgyFAwKC+/L0yQ9f/Ju6Ir8mwIhAPLEWkK5rB3S 3mTI4rbRddAqnjW2nOASQC2vDEfw2PxvAiEAjWtJ7C+mEI8UW88HHd16zOcgiB+E WPt9ceqxceQXLHUCIQDrBmr3xDc8HESPv+e04+2x3UCTcbpIN4MIdzplf2ciYwIh AKk9Vn9MnEmeAnJXxSI1hN2Xs20L9Wt3pM4eFE2v/cWa | 33 |
| Vehicle | M = Speed | |
|---|---|---|
| 1 | 40 | S7r99OjaxGi9G78qyGSRnhzVnEubv4FCBvAmg0lZ07ljRlVj6aD3wxLI79FgV0yoeguMktQeo+QUnPacF3Evqw== |
| 2 | 44 | J3ZUSkJ0hoj+tZTMDHuVWWcoNTPRUszBTwufydCM7J/3mLGp1otbT8tgV0yUiV40Ps+uUTxplAm6AmT/5/tKWA== |
| 3 | 80 | Kv9Xs3Me7RvhFWqeqd4W9I+AVJ4syLo4FYq9n/59Csfv5GTSiFnOe24fM/yvM9mGz3VSBI0k73bsljzQCYz5Bg== |
| 4 | 39 | M7eEHp4RO9TQ/xA+mjfEFmRD3edzmRBvxP2I2ShBCiXkDI4w+CFcvNoXdGzB6OsQ9ss0eAtazUTY4vJ0+dg3xw== |
| 5 | 25 | Tkn+G+Wb1O1Y5HdgECh8XvRP2ocLFaCaH9igGWZgixGUM6vF5TFcODnwVWvuJW70hfNCNmOGXwsNmKi11w66dw== |
| 6 | 35 | Rb/ifHWfAdvkAtU+bpgmfcuyIDhYBSkpmORhUCwBfMgGAwW5z7FYEfw+TPb6TQGKUGJNXOJ5hw5B3wKkdK7fLQ== |
| 7 | 120 | HlgqAh2fYHW7++j6MHfAbeccjQxXsSUvg9KwWmmdWVlmE6I6X1XhC1QoIYv0X85fyuH860hVUe4bvrbptK9tFA== |
| 8 | 40 | KCAvJCosWzl/0OsgWczV0aWby1PjjL8jhAbROX6XNXv+clFZOPEcqqRJW6ohdyV/9BQu4kJz9b7kdlGGb8v+hw== |
| 9 | 50 | PKbN2c6V6LgCi2dCXz//ZWgJ+Hw2A7SrtcMSvQ8HH7l3mbX8FWhXsgqdybXdtodKGjP8l4wx2ltY7jm74fbUrQ== |
| 10 | 45 | FpmWe9LQFp9Pas5teIi+YAVdLIPA8WintYtAR7WUOAgnKb8ZeKRB6NtIzKeFe4g+KqL29kFw+PTiV8z8V66JHQ== |
| 11 | 47 | OfLLW6HEGClz2I/D9ZoIOmSeBu2VI4y0sf5YbhMjEzPpOjD0wyf6HdfcT7jpV4qlWUhx7uKiim53os5YMsOiDA== |
| 12 | 39 | J/GXfMcg+rAZff5lgSJhl3St+KxtSVjOFBwDIqI+sbKr0FPNAlV7vrlWPKSAKeTxJQnvho7bOwFhHHJZMZfMMg== |
| 13 | 43 | RFDsPBRdAF+oaa7QIvsaZmrLpXfFhRzL8T7nDF47ha5TNf7voK51CnZIivwJsoNv1K7kBHcfG8jRXFUWVD65Mg== |
| 14 | 29 | LP++KX+ZBi3yZjGhIaUTARHQUi6cg3ZnA1PVFAsynXC3Nc1uKG/Q8y02YEuMEv68/7MrFOZ9HOnCkpb8Cufrxg== |
| 15 | 32 | IMcpySaMUm+/QLFa907slM5uzeFARhRoBPr8awosLGzX/WWzHmBTPDHGrRuMpd3GKbkBNTFziA8Sf7zltm5jcw== |
| 16 | 28 | Pnw4wBBXliV+WKVOEnt3IsG0ivvO0sfgLlp0H51UTgbA31YYxVheGJW9cHuLt60ZHb8mjx36WB7T5ixu7Y9svQ== |
| i | Speed | ||
|---|---|---|---|
| 1 | 25 | 3 | 4 |
| 2 | 28 | 1 | 4 |
| 3 | 29 | 3 | 6 |
| 4 | 32 | 3 | 7 |
| 5 | 35 | 4 | 4 |
| 6 | 39 | 0 | 1 |
| 7 | 39 | 1 | 1 |
| 8 | 40 | 0 | 3 |
| 9 | 40 | 3 | 4 |
| 10 | 43 | 1 | 2 |
| 11 | 44 | 1 | 3 |
| 12 | 45 | 2 | 34 |
| 13 | 47 | 32 | 33 |
| 14 | 79 | 1 | 41 |
| 15 | 80 | 40 | - |
| 16 | 120 | - | - |
References
- Zaidi, K.; Milojevic, M.; Rakocevic, V.; Rajarajan, M. Data Centric Rogue Node Detection in VANETs. In Proceedings of the 2014 IEEE 13th International Conference on Trust Security and Privacy in Computing and Communications, Beijing, China, 24–26 September 2014. [Google Scholar]
- Engoulou, R.G.; Bellaïche, M.; Pierre, S.; Quintero, A. VANET security surveys. Comput. Commun. 2014, 44, 1–13. [Google Scholar] [CrossRef]
- Pathan, A.S.K. Security in Vehicular Ad Hoc Networks. In Security of Self-Organizing Networks: MANET, WSN, WMN, VANET, 1st ed.; CRC Press: Boca Raton, FL, USA, 2011. [Google Scholar]
- Khan, S.; Parkinson, S.; Qin, Y. Fog computing security: A review of current applications and security solutions. J. Cloud Comput. 2017, 6, 19. [Google Scholar] [CrossRef]
- Law, Y.W.; Palaniswami, M.; Kounga, G.; Lo, A. WAKE: Key management scheme for wide-area measurement systems in smart grid. IEEE Commun. Mag. 2013, 51, 34–41. [Google Scholar] [CrossRef]
- Flavio, B.; Rodolfo, M.; Zhu, J.; Addepalli, S. Fog computing and its role in the internet of things. In Proceedings of the first edition of the MCC workshop on Mobile cloud computing, Helsinki, Finland, 17 August 2012. [Google Scholar]
- Riley, M.; Akkaya, K.; Fong, K. A survey of authentication schemes for vehicular ad hoc networks. Secur. Commun. Netw. 2011, 4, 1137–1152. [Google Scholar] [CrossRef]
- Zeadally, S.; Hunt, R.; Chen, Y.-S.; Irwin, A.; Hassan, A. Vehicular ad hoc networks (VANETS): Status, results, and challenges. Telecommun. Syst. 2012, 50, 217–241. [Google Scholar] [CrossRef]
- Li, C.-T.; Hwang, M.-S.; Chu, Y.-P. A secure and efficient communication scheme with authenticated key establishment and privacy preserving for vehicular ad hoc networks. Comput. Commun. 2008, 31, 2803–2814. [Google Scholar] [CrossRef]
- Lu, R.; Lin, X.; Zhu, H.; Ho, P.-H.; Shen, X. ECPP: Efficient conditional privacy preservation protocol for secure vehicular communications. In Proceedings of the INFOCOM 2008. The 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008. [Google Scholar]
- Perrig, A.; Canetti, R.; Tygar, J.D.; Song, D. The TESLA broadcast authentication protocol. Rsa Cryptobytes 2002, 5, 2–13. [Google Scholar]
- Studer, A.; Bai, F.; Bellur, B.; Perrig, A. Flexible, Extensible, and Efficient VANET Authentication. J. Communic. Netw. 2009, 11, 574–588. [Google Scholar] [CrossRef]
- Vaibhav, A.; Shukla, D.; Das, S.; Sahana, S.; Johri, P. Security Challenges, Authentication, Application and Trust Models for Vehicular Ad Hoc Network—A Survey. IJ Wirel. Microw. Technol. 2017, 3, 36–48. [Google Scholar] [CrossRef]
- Alrawais, A.; Alhothaily, A.; Hu, C.; Cheng, X. Fog Computing for the Internet of Things: Security and Privacy Issues. IEEE Internet Comput. 2017, 21, 34–42. [Google Scholar] [CrossRef]
- Chen, L.; Ng, S.-L.; Wang, G. Threshold anonymous announcement in VANETs. IEEE J. Sel. Areas Commun. 2011, 29, 605–615. [Google Scholar] [CrossRef]
- Tomandl, A.; Fuchs, K.-P.; Federrath, H. REST-Net: A dynamic rule-based IDS for VANETs. In Proceedings of the 2014 7th IFIP Wireless and Mobile Networking Conference (WMNC), Vila Moura, Portugal, 22–24 May 2014. [Google Scholar]
- Kang, M.J.; Kang, J.W. Intrusion detection system using deep neural network for in-vehicle network security. PloS ONE 2016, 11, e0155781. [Google Scholar] [CrossRef] [PubMed]
- Daeinabi, A.; Rahbar, A.G. Detection of malicious vehicles (DMV) through monitoring in Vehicular Ad-Hoc Networks. Multimed. Tools Appl. 2013, 66, 325–338. [Google Scholar] [CrossRef]
- Sushmita, R.; Cavenaghi, M.A.; Huang, Z.; Nayak, A.; Stojmenovic, I. On data-centric misbehavior detection in VANETs. In Proceedings of the 2011 IEEE Vehicular technology conference (VTC Fall), San Francisco, CA, USA, 5–8 September 2011. [Google Scholar]
- Zaidi, K.; Milojevic, M.B.; Rakocevic, V.; Nallanathan, A.; Rajarajan, M. Host-Based Intrusion Detection for VANETs: A Statistical Approach to Rogue Node Detection. IEEE Trans. Vehicular Technol. 2016, 65, 6703–6714. [Google Scholar] [CrossRef]
- Sedjelmaci, H.; Senouci, S.M.; Abu-Rgheff, M.A. An efficient and lightweight intrusion detection mechanism for service-oriented vehicular networks. IEEE Internet Things J. 2014, 1, 570–577. [Google Scholar] [CrossRef]
- Yi, S.; Qin, Z.; Li, Q. Security and Privacy Issues of Fog Computing: A Survey. In Proceedings of the 10th International Conference on Wireless Algorithms, Systems, and Applications, Qufu, China, 10–12 August 2015. [Google Scholar]
- Alrawais, A.; Alhothaily, A.; Hu, C.; Xing, X.; Cheng, X. An attribute-based encryption scheme to secure fog communications. IEEE Access 2017, 5, 9131–9138. [Google Scholar] [CrossRef]
- Huang, Q.; Yang, Y.; Wang, L. Secure Data Access Control with Ciphertext Update and Computation Outsourcing in Fog Computing for Internet of Things. IEEE Access 2017, 5, 12941–12950. [Google Scholar] [CrossRef]
- Wang, Q.; Chen, D.; Zhang, N.; Qin, Z.; Qin, Z. LACS: A Lightweight Label-Based Access Control Scheme in IoT-Based 5G Caching Context. IEEE Access 2017, 5, 4018–4027. [Google Scholar] [CrossRef]
- Imine, Y.; Kouicem, D.E.; Lounis, A.; Bouabdallah, A. MASFOG: An Efficient Mutual Authentication Scheme for Fog Computing Architecture. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018. [Google Scholar]
- Alharbi, S.; Rodriguez, P.; Maharaja, R.; Iyer, P.; Bose, N.; Ye, Z. FOCUS: A fog computing-based security system for the Internet of Things. In Proceedings of the 2018 15th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 12–15 January 2018. [Google Scholar]
- Liu, J.; Li, J.; Zhang, L.; Dai, F.; Zhang, Y.; Meng, X.; Shen, J. Secure intelligent traffic light control using fog computing. Future Gener. Comput. Syst. 2018, 78, 817–824. [Google Scholar] [CrossRef]
- Wei, J.; Wang, X.; Li, N.; Yang, G.; Mu, L. A Privacy-Preserving Fog Computing Framework for Vehicular Crowdsensing Networks. IEEE Access 2018, 6, 43776–43784. [Google Scholar] [CrossRef]

| Symbol | Description |
|---|---|
| Encryption key for RSU i | |
| Signed message | |
| Hash of authentication key | |
| Authentication key used in round j | |
| Initial key provided by the trust authority | |
| Random seed for RSU i | |
| Public key |
| (a) | (b) | (c) | ||||||
|---|---|---|---|---|---|---|---|---|
| 1 | 783,346 | 25 | 2 | 368,263 | 16 | 3 | 294,958 | 4 |
| 2 | 368,263 | 16 | 1 | 783,346 | 25 | 1 | 783,346 | 25 |
| 3 | 294,958 | 4 | 3 | 294,958 | 4 | 2 | 368,263 | 16 |
| (a) | (b) | (c) | ||||||
|---|---|---|---|---|---|---|---|---|
| i | ||||||||
| 1 | 783,346 | 10,3278 | 2 | 368,263 | 28,229 | 3 | 294,958 | 294,958 |
| 2 | 368,263 | 28,229 | 1 | 783,346 | 103,278 | 1 | 783,346 | 103,278 |
| 3 | 294,958 | 294,958 | 3 | 294,958 | 294,958 | 2 | 368,263 | 28,229 |
| i | Speed | i | Speed |
|---|---|---|---|
| 1 | 25 | 9 | 40 |
| 2 | 28 | 10 | 43 |
| 3 | 29 | 11 | 44 |
| 4 | 32 | 12 | 45 |
| 5 | 35 | 13 | 47 |
| 6 | 39 | 14 | 37.38462 |
| 7 | 39 | 15 | 37.38462 |
| 8 | 40 | 16 | 37.38462 |
| Scheme | Immune from Collude | Overhead | Infrastructure | Response Mechanism | Fog |
|---|---|---|---|---|---|
| DCMD 1 [19] | No | Yes | Hybrid | Fine Imposition | No |
| IDS 2 [20] | No | Yes | OBU-based (cooperative) | Isolation | No |
| ELIDV 3 [21] | No | Yes | Hybrid | Ignore | No |
| Our Work | Yes | No | RSU-based | Correction | yes |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Al-Otaibi, B.; Al-Nabhan, N.; Tian, Y. Privacy-Preserving Vehicular Rogue Node Detection Scheme for Fog Computing. Sensors 2019, 19, 965. https://doi.org/10.3390/s19040965
Al-Otaibi B, Al-Nabhan N, Tian Y. Privacy-Preserving Vehicular Rogue Node Detection Scheme for Fog Computing. Sensors. 2019; 19(4):965. https://doi.org/10.3390/s19040965
Chicago/Turabian StyleAl-Otaibi, Basmah, Najla Al-Nabhan, and Yuan Tian. 2019. "Privacy-Preserving Vehicular Rogue Node Detection Scheme for Fog Computing" Sensors 19, no. 4: 965. https://doi.org/10.3390/s19040965
APA StyleAl-Otaibi, B., Al-Nabhan, N., & Tian, Y. (2019). Privacy-Preserving Vehicular Rogue Node Detection Scheme for Fog Computing. Sensors, 19(4), 965. https://doi.org/10.3390/s19040965





