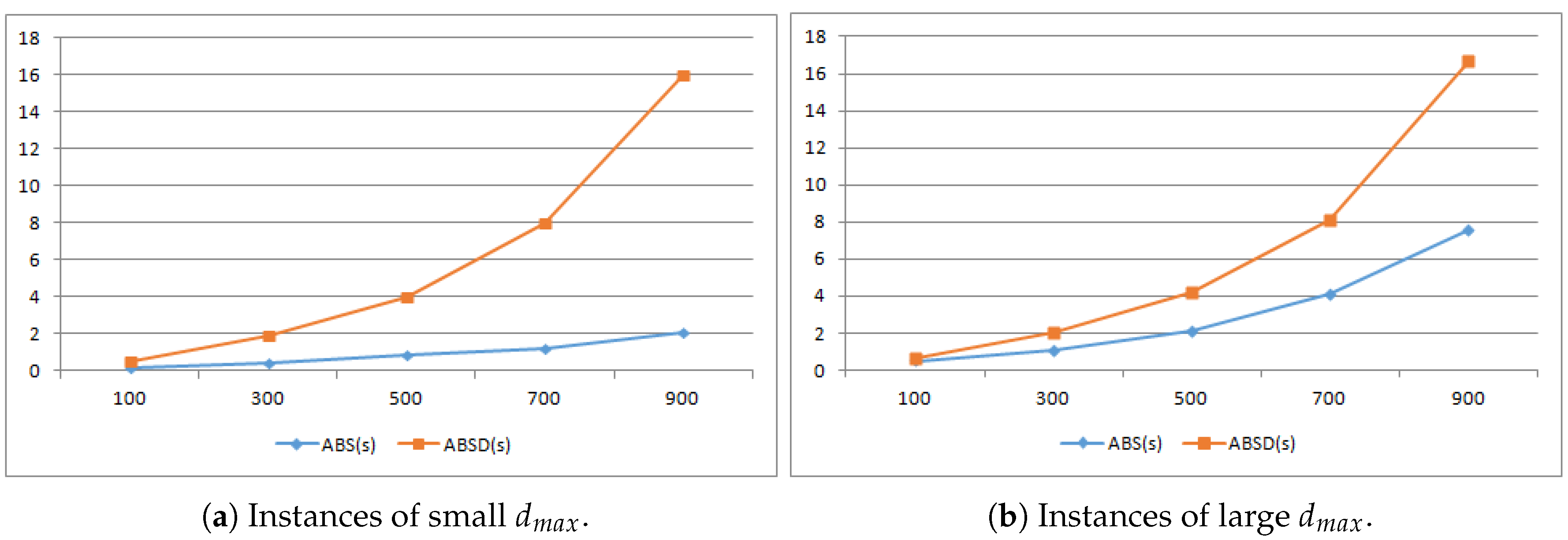
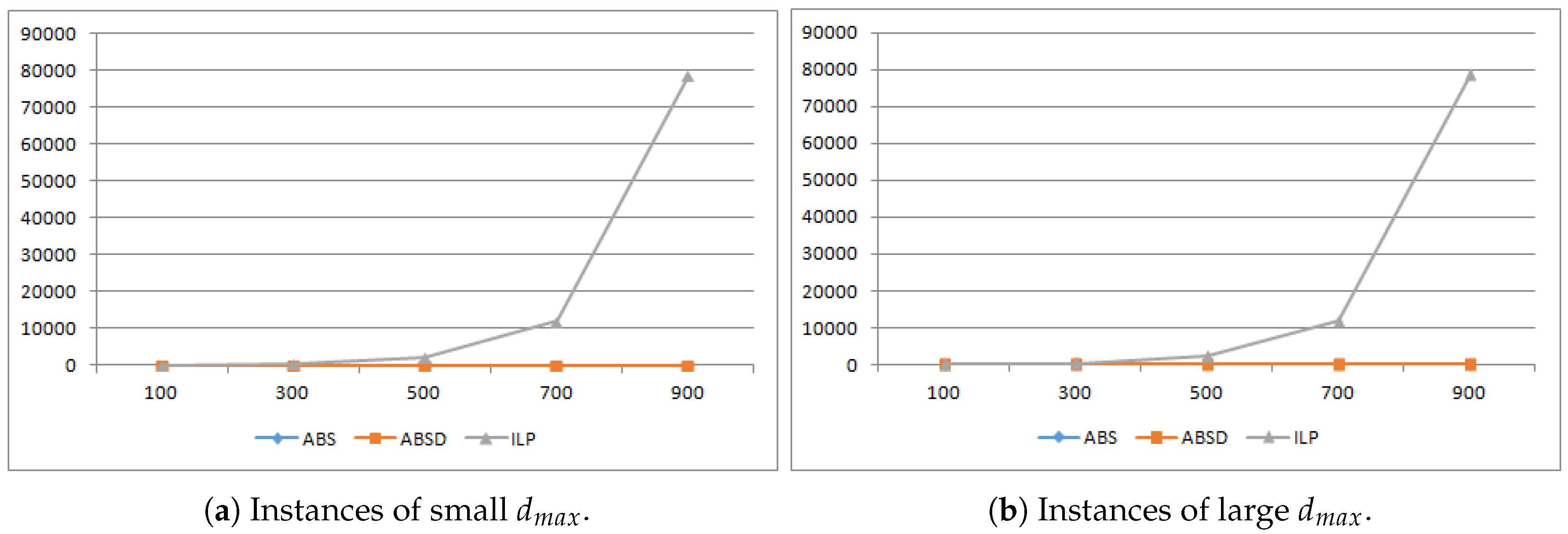
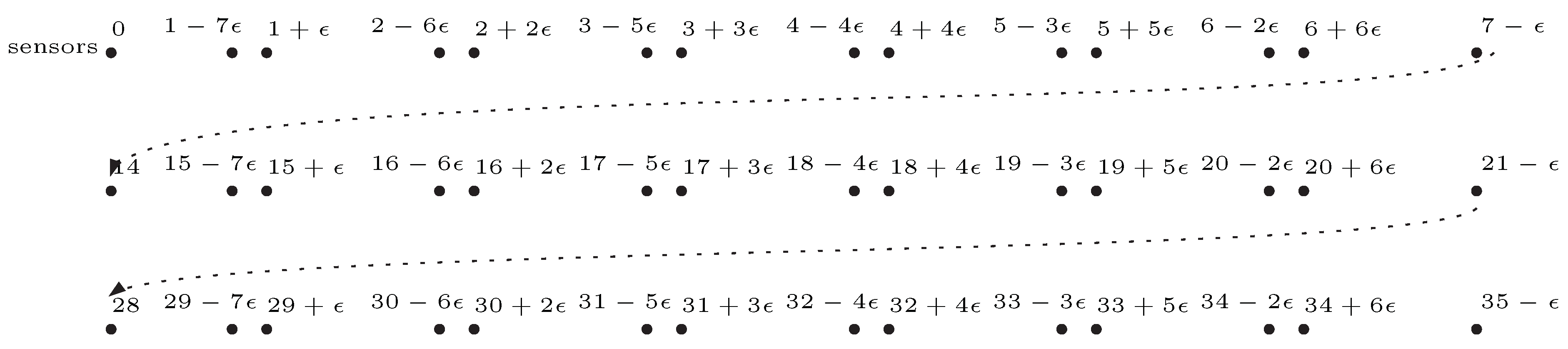1. Introduction
In the past decades, wireless sensor networks have brought tremendous changes to human society and proposed many technique challenges. Among them, the coverage topics including area coverage [
1] and barrier coverage [
2] are among the hop spots that attract lots of research interest. In area coverage, the task is to schedule the new positions of the sensors, such that each point in the given target region is covered by at least one sensor. Differently, in barrier cover the task is to monitor only the boundary of a given region, and the aim is to guarantee that intruders can be detected when they are crossing the barrier. Comparing to area coverage, barrier coverage has an advantage of using significantly less sensors and hence is scalable for large scale wireless sensor networks (WSN). Furthermore, some applications only require a set of Points Of Interest (POIs) along the boundary to be monitored. In the context, a problem arises how to guarantee every POI on the barrier to be covered. The current-state-of-art method is to first cover POIs using the stationary sensors, and then use mobile sensors to cover every not-yet covered POI along the barrier. For the second phase, we traditionally have the following assumptions for the modeling: (1) Sensors are acquired with mobile ability; (2) The initial positions of the sensors are distributed on the plane, and the POIs are distributed along a line segment (Although the shape of the boundary can be various, most researches nonetheless focus on line boundary because curves in other shapes can be considered as a variable of line segments); (3) The aim of sensor networks is to prolong the lifetime. This arises the min-max 2D Line Boundary Target Coverage problem (min-max 2D-LBTC) as follows:
Definition 1. Let P and Γ be respectively a set of POIs distributed in a line segment and a set of mobile sensors distributed on the plane, where has a position while has a position and a positive sensing radius . The min-max 2D-LBTC problem aims to compute a new position for each sensor , such that each POI is covered by at least one sensor, and the maximum movement of the sensors from their original positions to the new positions is minimized that is attained, where is covered means there exists a sensor with position that .
When no confusion arises, we shall use LBTC short for the min-max 2D-LBTC problem for briefness. In particular, we use one dimensional min-max Line Boundary Target Coverage problem (1D-LBTC) to denote the special case of LBTC when the initial positions of all the sensors are also distributed on the line boundary. Moreover, the decision version of LBTC (decision LBTC for short) is, for a given movement bound
D, to determine whether there exists a feasible coverage with each sensor’s movement bounded by
D. Besides, when the aim is to cover the line boundary itself instead of the POIs thereon, we respectively have the min-max Line Boundary Coverage (LBC) problem and one-dimensional-LBC (1D-LBC) problem, which have already been well studied and a number of algorithms have been developed. All the notations of this paper are summarized as in
Table 1.
1.1. Related Works
To the best of our knowledge, Kumar et al. [
2] were the first to consider the boundary (barrier) coverage problem using sensors against a closed curve (i.e., a moat), via transforming the coverage problem to the path problem of determining whether there exists a path between two specified nodes, although the research of barrier coverage started from early 90s due to Gage [
3]. The algorithm from Kumar et al. is scalable and can also be extended to solve the
k-coverage problem by transforming to the
k-disjoint path problem. However, the disadvantage is that it can only be used to determine whether a coverage exists using the deployed
stationary sensors. A problem for stationary sensors is that, after deployment there might exist no coverage over all POIs. For the case, a state-of-art solution is to employ mobile sensors to fill the gaps between the stationary sensors. In the scenario, the WSN applications would require to maximize the minimum lifetime of the mobile sensors or to minimize the total energy consumption. For the former, the aim is to schedule new positions for the mobile sensors such that the barrier is completely covered, and that the maximum movement of the sensors is minimized as to prolong the lifetime of the WSN. When the sensors are on the line of the barrier, the 1D-LBC problem is shown optimally solvable in
time for uniform radii in Paper [
4]. The same paper has also proposed an algorithm with
time for uniform radii and
, and with
for the sensor
, where
L is the length of the barrier,
n is the number of the sensors. Later, Chen et al have improved the time complexity to
for uniform sensor radii and proposed an
time algorithm for non-uniform radii in paper [
5]. Besides straight line barrier, circle/simple polygon barriers has been studied and two algorithms have been given developed by Bhattacharya et al. in [
6], which have an
time relative to cycle barriers and an
time relative to polygon barriers, in which
m is the number of the edges on the polygon. The later time complexity was then decreased to
in [
7]. For the more generalized case in which the sensors are distributed on the plane, the LBC problem is known to be strongly
-hard for sensors with general integer sensing radius [
8], while LBC using uniform radius sensors is shown solvable in
time [
9]. Although these elegant algorithms have been developed for LBC for both 1D and 2D setting, none of them is applicable to LBTC since as we shall show in the paper, LBTC is
-complete for non-uniform radius.
Other than the Min-Max case, there are also applications require min-sum coverage that is to minimize the total energy consumption, which is to minimize the total movement of the mobile sensors. For this objective, Min-Sum LBC, which aims to minimize the sum of the movements of all the sensors, were studied in literature. Min-Sum LBC was shown
-complete for arbitrary radii while solvable in time
for uniform radii by Czyzowicz et al. [
10]. The Min-Num relocation problem of minimizing the number of sensors moved, is also proven
-complete for arbitrary radii and polynomial solvable for uniform radii by Mehrandish et al. [
11]. A PTAS has been developed for the Min-Sum relocation problem against circle/simple polygon barriers by Bhattacharya et al. [
6], which was later improved to an
time exact algorithm by Tan and Wu [
7]. For covering a barrier with Min-Sum movement, the most recent result is a factor-
approximation algorithm for covering POIs along a barrier using uniform-radius sensors, aiming to minimize the sum of the movement [
12]. However, it remains open whether the min-sum LBC problem is
-hard. For target coverage task in the plane, Liao et al. have develop algorithms for Min-Sum movement to minimize the total consumed energy [
13].
1.2. Our Results
In this paper, we first show that 1D-LBTC is
-hard when the sensors are with non-uniform integer radii by proposing a reduction from the 3-partition problem that is known strongly
-complete [
14]. This hardness result is interesting, because 1D-LBC, the continuous version of 1D-LBTC, is shown solvable in polynomial time
[
5]. This means LBTC and LBC belong to different classes of computational complexity.
Then, we propose a sufficient and necessary condition to determine whether there exists a feasible cover for the barrier under the relocation distance bound D. Based on the condition, we propose a simple greedy approach that outputs “infeasible” if , and otherwise computes a feasible solution under the movement bound D, such that the sensors cover all the POIs in their new positions. We show that the decision algorithm is with a runtime . By employing the binary search technique, we propose an algorithm using the decision algorithm as a routine to actually find a minimum integer movement bound , when is integral. The algorithm takes time, where is the maximum distance between the sensors and the POIs.
For instances with being a real number or with large , we propose another algorithm that employs the binary search method against possible values of instead of the continuous value range. The trick is to construct the set of all possible values of and show its size is . This improves the runtime of the algorithm to , which is the time needed to sort the possible values of . The later algorithm remains correct even when D is allowed to be any real number. In contrast, the former algorithm can only work for integer . To the best of our knowledge, our algorithms are the first polynomial algorithms for LBTC.
The following paragraphs will be organized as follows: we shall first give the
-completeness proof in
Section 2; Then present the algorithm for Decision LBTC with uniform sensor radii together with the correctness proof in
Section 3; Next, actually solve the LBTC problem by employing the binary search method first against a continuous range, and then over our proposed discrete set in
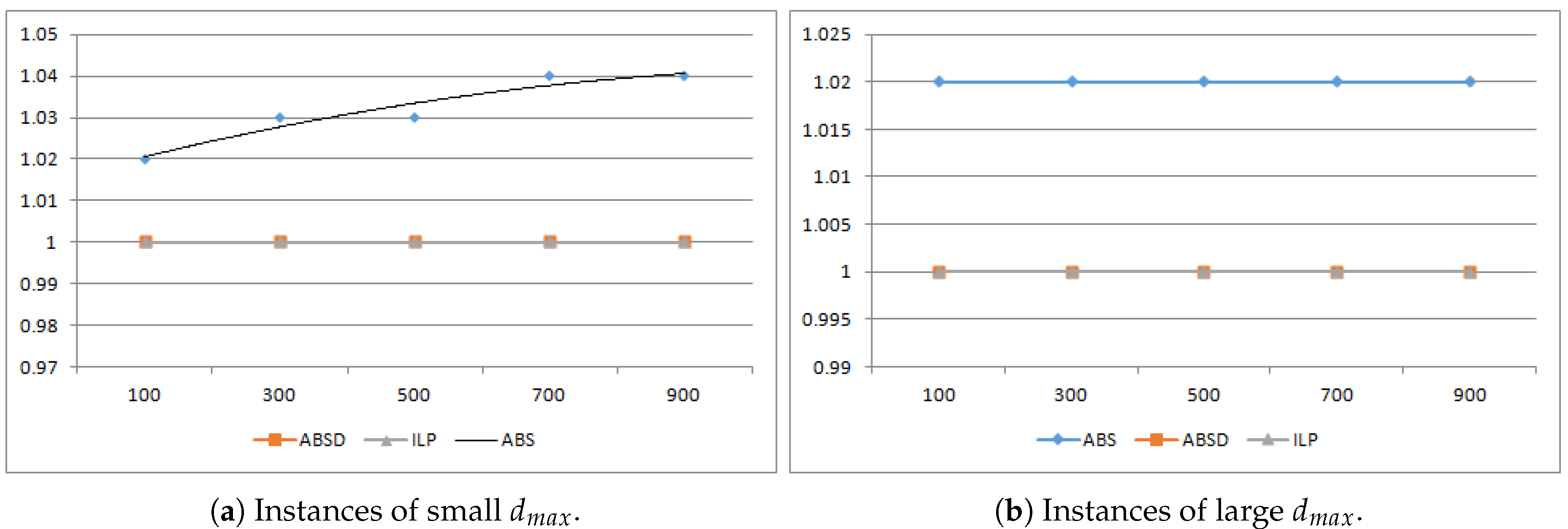
Section 4; After that, evaluate the proposed algorithms via experiments in
Section 5; At last, conclude the paper in
Section 6.
2. -Completeness of Decision 1D-LBTC
In this section, we shall show the decision LBTC problem is
-complete when the sensors are with non-uniform integer radii, by giving a reduction from the 3-partition problem that is known strongly
-complete [
14]. In 3-partition, we are given a set of
integers
with
for an integer
. The aim is to determine whether
can be divided into
n subsets, such that each subset is with an equal sum
B.
Theorem 1. Decision 1D-LBTC is NP-complete when the sensors are with non-uniform integer radii.
The key idea of the construction of a reduction from 3-Partition to the decision LBTC problem is to model as the diameter of the sensors, and place POIs on the line segment in a way that a coverage of the POIs is actually a partition of the numbers in . More detailed, for a given instance of 3-Partition, the construction of the corresponding instance of decision LBTC is simply as below:
Construct a line segment with length ;
Place POIs on the line barrier as below:
- (a)
Decompose the line segment into subsegments with equal length;
- (b)
Select n sections from the subsegments, where the ith section is the th subsegment;
- (c)
For the ith section, , do
For do
Put two POIs respectively to the two positions and , where is a small positive number;
End for
End for
Place sensors on position , where sensor i is with radii ;
The maximum movement is set as .
An example of the above construction is as depicted in
Figure 1. Note that, the instance of decision 1D-LBTC constructed above contains
POIs and
sensors. Anyhow, 3-Partition is known strongly
-complete, which means, 3-Partition remains
-complete even when
B is polynomial to
n. Therefore, the construction can be done in polynomial time for
B being polynomial to
n.
The main idea behind the construction is to construct a relationship between the number of covered POIs and the diameters of the sensors that are actually the integers in . More precisely, the property on the relationship is as in the following:
Proposition 1. Against a 1D-LBTC instance produced by the above construction, a sensor with diameter can cover at most POIs.
Proof. When a sensor is with a diameter 2, apparently it can cover at most 4 POIs. Suppose the proposition is true for sensors with diameter smaller than . Then, let be two positive integers smaller than r. By induction, we have that sensors with diameters and can cover upto and POIs, respectively. In addition, the two sensors with radii and can cover as many POIs as a sensor with a radii does. Therefore, the sensor with diameter can cover no more than POIs. This completes the proof. □
Lemma 1. An instance of 3-Partition is feasible if and only if the corresponding 1D-LBTC instance is feasible.
Proof. Suppose the instance of 3-Partition is feasible. Without loss of generality, we assume that is a solution to the 3-Partition instance which divides to a collection of n sets, among which and . Since equals the length of the barrier and the original position of each sensor is , each sensor can be moved any point of the barrier. Then we need only to use the sensors in , which are with radius and with a sum exactly B, to cover the segment from to . That apparently results in a coverage for all the POIs in the ith section.
Conversely, suppose the corresponding LBTC instance is feasible. Then since sensor j with radii can at most cover continuous POIs, and each section contains exactly POIs, so the diameter sum of the sensors for each section is at least B. Then because the diameter sum of all the sensors is , and there are n sections, the diameter sum of the sensors for each section is exactly B. Therefore, the diameters for the sensors for the sections is a solution to the corresponding instance of 3-Partition. □
From the fact that 3-Partition is strongly -complete, and following a similar idea of the above proof for Theorem 1, we immediately have the following hardness for LBTC:
Corollary 1. Decision 1D-LBTC is strongly NP-complete.
3. A Greedy Algorithm for 2D-LBTC with Uniform Sensors
The basic idea of the algorithm is to cover the POI from left to right, preferably using sensors that are likely less useful for later coverage. More precisely, let be the possible coverage range of sensor i, where and are respectively the positions of the leftmost and the rightmost POIs, with respect to the given distance D. That is, and are the leftmost and the rightmost positions of POIs sensor i can cover within movement D. Then the key idea of our algorithm is to cover the POIs from left to right, using the sensor that can cover the leftmost uncovered POI within movement D and is with minimum .
The algorithm is first to compute its possible coverage range for each sensor i with respect to the movement constraint D. Apparently, is the projective point of sensor i on the line, so we have and = for each sensor i. Then, the algorithm starts from point , to cover the line from left to right. The algorithm prefers using the sensor with a small , since a sensor with a large would has a better potential to cover the POIs on the right part of the line.
Let s be the position the uncovered leftmost POI on the line barrier. Then among the set of sensors , the algorithm repeats selecting the sensor with minimum to cover the uncovered POIs of the line barrier starting at s. Note that is exactly the set of sensors that can monitor a set of uncovered POIs starting at s by relocating at most D distance. The algorithm terminates either the set of POIs are completely covered, or the instance is found infeasible (i.e., there exists no unused sensor i with while the coverage is not yet done). The algorithm is formally as in Algorithm 1.
Note that Algorithm 1 takes time to compute and for all the sensors in Steps 2–3, and takes time to assign the sensors to cover the targets on the line barrier in Steps 4–15. Therefore, we have the time complexity of the algorithm:
Lemma 2. Algorithm 1 runs in time .
Before proving the correctness of Algorithm 1, we need the following lemma stating the existence of a special coverage for a feasible LBTC instance.
Proposition 2. Let be the position of sensor j in the plane. Assume , and are three points on a line segment. If , then holds. That is, the distance between the sensor and the middle point is not larger than the larger distance between the sensor and the other two points.
Lemma 3. If an instance of LBTC is feasible, then there must exist a coverage in which the sensors are s-ordered.
| Algorithm 1 A greedy algorithm for decision LBTC |
Input: A bound on maximum movement, a set of sensors with original
positions and r being the sensing radii, a set of POIs with
positions , where is the position for ; |
| Output: New positions for the sensors or return “infeasible”. |
| 1: Set and , where s is the leftmost point of the uncovered part of the barrier. |
| 2: For each sensor i do |
| 3: Compute the leftmost position and the rightmost position that sensor i can monitor; |
| 4: EndFor |
| 5: While do |
| 6: If there exists , such that then |
7: Select the sensor with minimum among all the sensors , which is to find
sensor that ; |
| 8: Set and ; |
| 9: Set and ; |
| 10: Else |
| 11: Return “infeasible”; |
| 12: End if |
| 13: If then /*All POIs have been covered. */ |
| 14: Return “feasible” together with the new positions ; |
| 15: Endif |
| 16: Endwhile |
Proof. The key idea of the proof is that, any coverage of LBTC that is not s-ordered, can be converted to an s-ordered coverage by re-scheduling the sensors of covering the POIs.
Suppose there exist two sensors i and j, such that but . Then we need only to swap the final positions of i and j, i.e., to simply set the new final positions and of sensor i and j as below:
Ifthen
Set and then ;
Else
Set and .
EndIf
Apparently, the POIs exclusively covered by
i are now covered by sensor
j, and
vice versa. So after the swap the sensors will remains a coverage for the POIs on the line. It remains to show the swap will not increase the maximum movement. Recall that the leftmost and the rightmost points sensor
j can cover are respectively
and
. Because sensor
j can move to
under the movement bound
D, we have
On the other hand, in either case of the swap, we have
. So combining Inequality (1), we have
That means
Then following Proposition 2, the distance between sensor i and its new position is bounded by . The case for the new position of sensor j is similar except that the distance between sensor j and its new position is bounded by . This completes the proof. □
Based on Lemma 3, given a feasible instance of LBTC, we can assume there exists an s-ordered coverage, say which is the set of sensors used to compose the coverage with being the rightmost POI covered by . Then we have the following lemma, which leads to the correctness of the algorithm:
Lemma 4. When running against a feasible LBTC instance, Algorithm 1 covers the POIs without using any sensor in .
Proof. We shall prove this claim by induction. When , the lemma is obviously true, as we need only to cover the POIs . Suppose the lemma holds for , then it remains only to show the case for . By induction, Algorithm 1 covers the POIs without using any sensor in . Then Algorithm 1 can simply cover POIs by using sensor . Combining with the induction, we covers without using any sensor in . This completes the proof. □
We can now prove the following theorem and have the correctness of Algorithm 1:
Theorem 2. Algorithm 1 returns “feasible” iff the POIs can be completely covered by the sensors within relocation distance D.
Proof. Suppose Algorithm 1 returns “feasible”, then obviously the produced solution is truly a coverage, because in the solution the movement of each sensor is bounded by D and all the POIs are covered by at least one sensor.
Conversely, suppose there is a coverage for the instance. Then by Lemma 3, there must exist an s-ordered coverage, say which is the set of sensors used to compose the coverage. Following Lemma 4, Algorithm 1 covers POIs without using any sensor in for every . So the algorithm can always find sensors for further coverage, and in the worst case use to cover the POIs . Therefore, the algorithm will eventually find a feasible coverage. This completes the proof. □
4. The Complete Algorithms
In this section, we will show how to employ Algorithm 1 to really compute the minimum movement bound for LBTC. Firstly, when only considering integer , we can find it simply by employing the binary search method against a large range that contains ; Secondly, for real number , we construct a set of size which arguably contains , and then eventually finds in the set again by the binary search method.
4.1. A Simple Binary Search Based Algorithm
The algorithm is simply applying the binary search method to find within the range of , where is the maximum distance between the POIs and the sensors. The main observation is as the following proposition whose correctness is easy to prove:
Proposition 3. If LBTC is feasible, then holds.
The detailed algorithm is as in Algorithm 2.
| Algorithm 2 The whole algorithm for optimal LBTC. |
Input: A movement bound , a set of sensors with positions ,
the sensing radii r, a set of POIs with positions , where is
the position for ; |
| Output: The minimized maximum movement of the sensors together with new positions |
| 1: Set and , where is the maximum distance between the sensors and the POIs; |
| 2: If there exists no coverage returned from calling Algorithm 1 wrt then |
| 3: Return “infeasible”; |
| 4: EndIf |
| 5: Set ; |
| 6: While do |
| 7: If there exists no coverage returned from calling Algorithm 1 wrt then |
| 8: Set and ; |
| 9: Else |
| 10: Set and then ; |
| 11: EndIf |
| 12: End While |
| 13: Return the result of call Algorithm 1 wrt .
|
For the correctness and time complexity of Algorithm 2, we immediately have the following lemma:
Lemma 5. Using binary search and employing Algorithm 1 for times, Algorithm 2 will compute the optimum movement within time complexity .
4.2. An Improved Algorithm via Discrete Binary Search
In this subsection, we shall show the time complexity of our algorithm can be further improved via a more sophisticated implementation over the binary search. The key observation is that, we need only to apply a binary search over a set of discrete values which arguably contain the optimum min-max movement
. Let
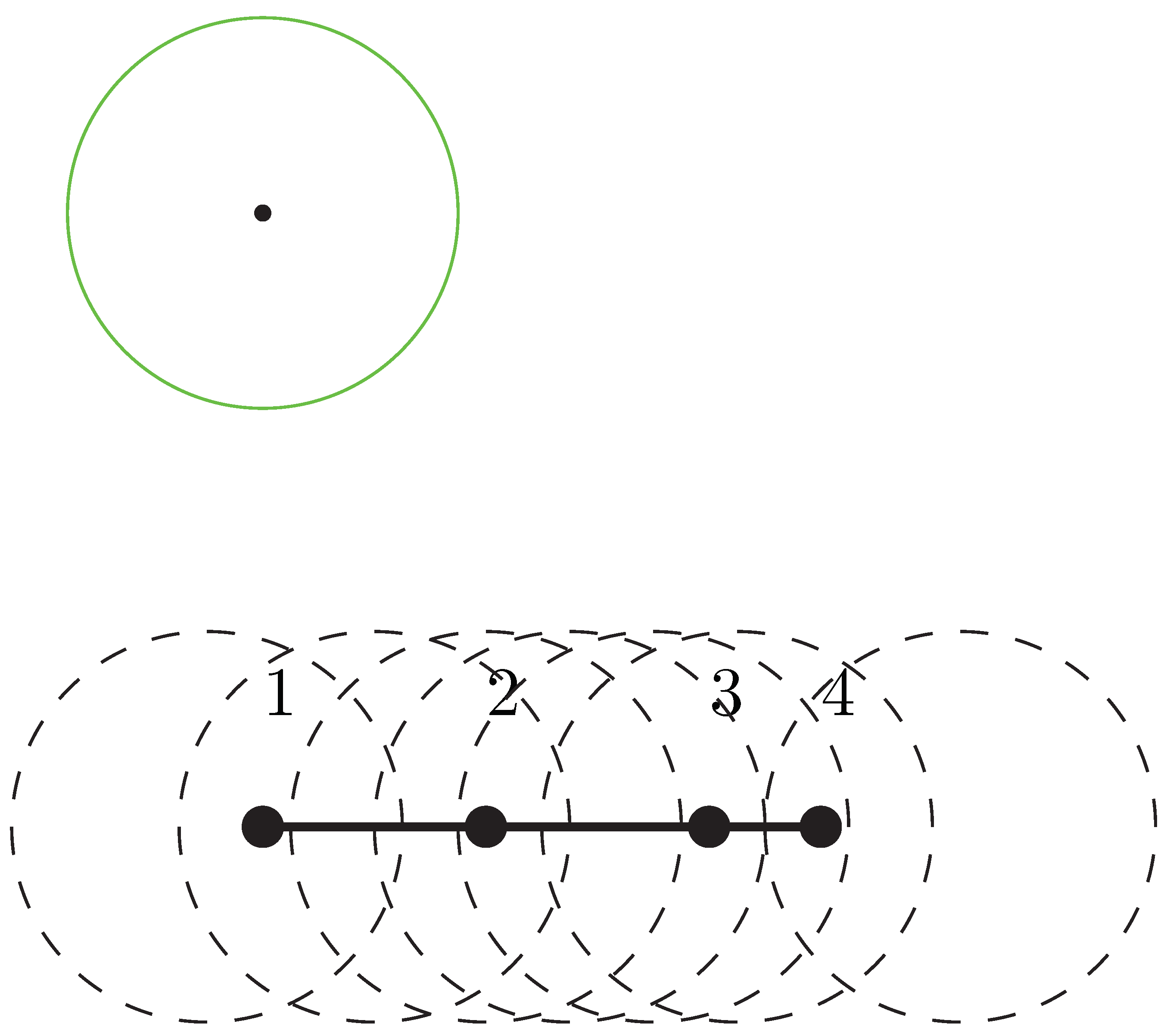
be the set of possible combinations, that is, all possible different combinations covered by a sensor (An example of combinations is as depicted in
Figure 2). Let
be the minimum movement using sensor
i to cover combination
. Then we have the following lemma:
Lemma 6. Let be an optimal solution to the uniform 2D-LBTC problem. Then .
Proof. Suppose the lemma is not true. Then let . First we show that under maximum distance and , every sensor i covers an identical collection of combinations. That is because every POI, which sensor i can cover under movement bound , can also be covered by sensor i under movement bound ( as iff ), and conversely every POI, which cannot be covered by sensor i under , can not be covered by the same sensor within the movement bound ( iff ). Therefore, a feasible coverage solution under maximum movement would also remain feasible under . This together with contradicts with the fact that is an optimal solution to the problem. □
Following the above lemma, our algorithm will first compute the set of possible combinations; Then compute all the distances between each sensor in and each combination in , which is ; Later sort the distance in in non-decreasing order and apply the binary search method to by using Algorithm 1 as a subroutine. Eventually, the algorithm finds a minimum , such that by setting the bound the maximum movement there exists a relocation of the sensors to cover all the POIs.
According to the main structure of the complete algorithm above, we shall first compute . The key idea of the computation is to find all the pairs of POIs which can be the first and the final POIs covered by a sensor. The most important part of the computation is to exclude those pairs of POIs, say i and j, for which and are too close, i.e., . In the case, to cover i and j, either or will be also covered, and hence i and j can not respectively be the first and the final POIs covered by a sensor. The detailed algorithm for computing and the complete algorithm are formally stated in Algorithms 3 and 4.
| Algorithm 3 A fast algorithm for constructing combinations. |
Input: A set of POIs on the line segment with positions ,
where is the position for , and a real number r that is the radii of the sensors; |
| Output: The set of combinations . |
| 1: Set , and ; |
| 2: For POI to do |
| 3: For to do |
| 4: If and then |
| 5: ; |
| 6: EndIf |
| 7: EndFor |
| 8: EndFor |
| 9: Return and terminate.
|
| Algorithm 4 A fast algorithm for LBTC. |
Input: A set of sensors with original positions and an identical
sensing radii r, a set of POIs with positions on the line
segment, where is the position for ; |
| Output: A minimum movement D under which the sensors can be relocated to covered all POIs in P. |
| 1: Set and compute the collection of combinations by Algorithm 3; |
| 2: For each sensor i do |
| 3: For each combination do |
| 4: Compute , the minimum movement needed when using sensor i to cover ; |
| 5: Set ; |
| 6: EndFor |
| 7: EndFor |
| 8: Sort in a non-decreasing order and set and , to prepare for binary search. |
| 9: Use as the movement bound (i.e., D) and call Algorithm 1; |
| /*Note that is the smallest element in . */ |
| 10: If there exists a feasible coverage under movement bound then |
| 11: Return as the optimum movement bound; |
| 12: End if |
| 13: While do |
| 14: Set ; |
15: Use as the movement bound (i.e., D) and call Algorithm 1;
/* is the th smallest element in . */ |
| 16: If there exists a feasible coverage under movement bound then |
| 17: Set ; |
| 18: Else |
| 19: Set ; |
| 20: End if |
| 21: Endwhile |
| 22: Return as the optimum movement bound.
|
Lemma 7. Algorithm 3 returns with .
Proof. W.l.o.g. assume the combinations in are sorted, such that for each and , and , where and are respectively the leftmost and rightmost POIs in . Then, following the construction of the combinations as in Algorithm 3, if a POI j appears in and , then for any , . That is, a POI can result in at most two different combinations, one when the POI is added and the other when the POI is removed. Therefore, there are at most combinations in . □
Lemma 8. The time complexity of Algorithm 4 is .
Proof. From Lemma 7,
holds, so we apparently have
. Then, it takes
time to sort the elements in
, provided merge sort is used [
15]. Besides, the while-loop from Step 12 to Step 20 will be repeated for at most
times, each of which takes
time to run Algorithm 1. Therefore, the total time complexity of the algorithm is
. □
Following Lemma 6, we immediately have the correctness of Algorithm 4 as below:
Theorem 3. Algorithm 4 produces an optimum solution to the LBTC problem.