A Design Approach to IoT Endpoint Security for Production Machinery Monitoring
Abstract
:1. Introduction
- A novel risk-averse IoT endpoint security design thinking approach for industrial environments.
- An innovative IoT device security implementation of the design thinking approach, motivated by the isolation principle and applied at the interfaces between the key components of an IoT endpoint device and supported by a new lightweight authentication protocol with real-time features.
- Application of the above on a typical industrial case, that of production machinery monitoring.
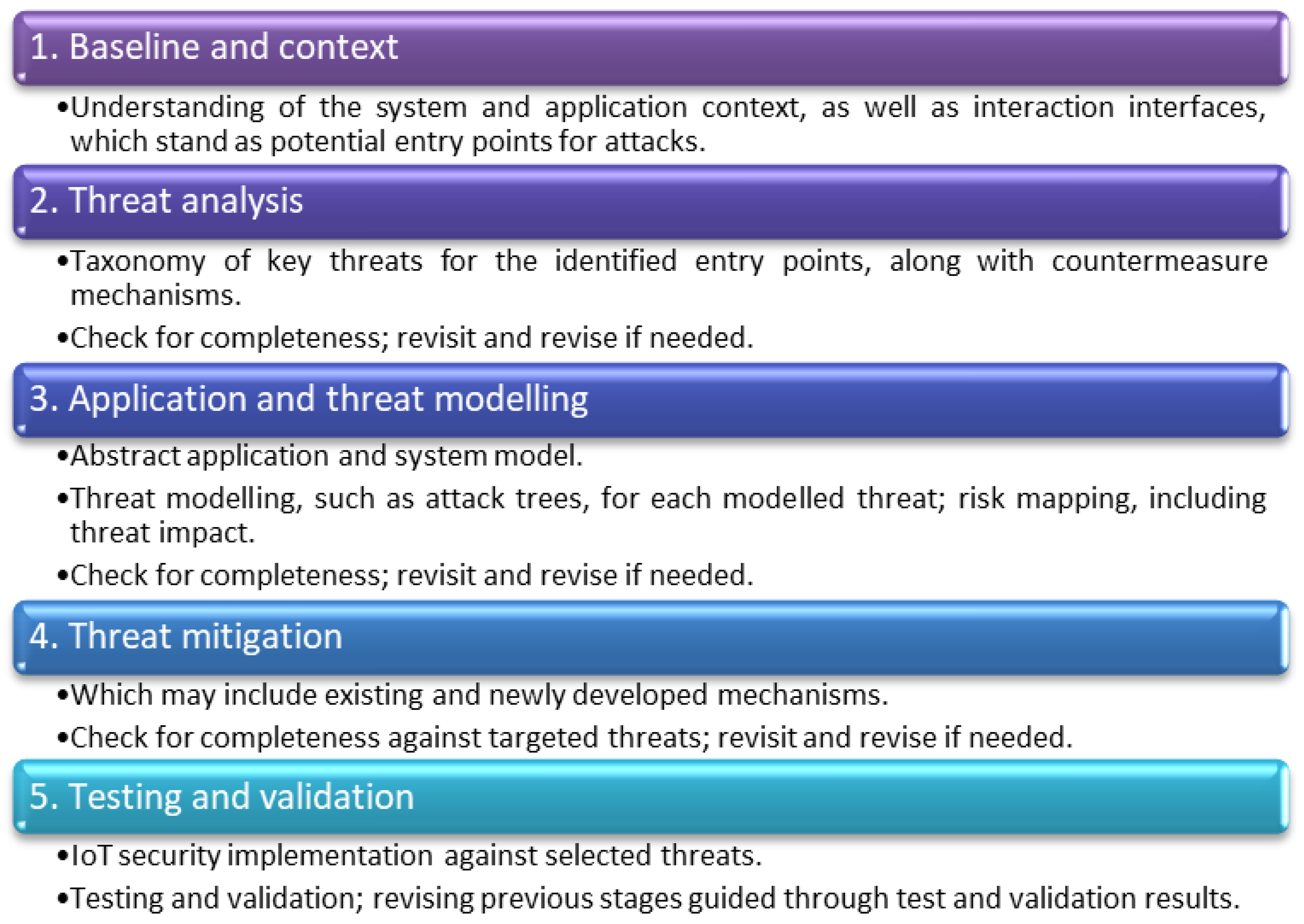
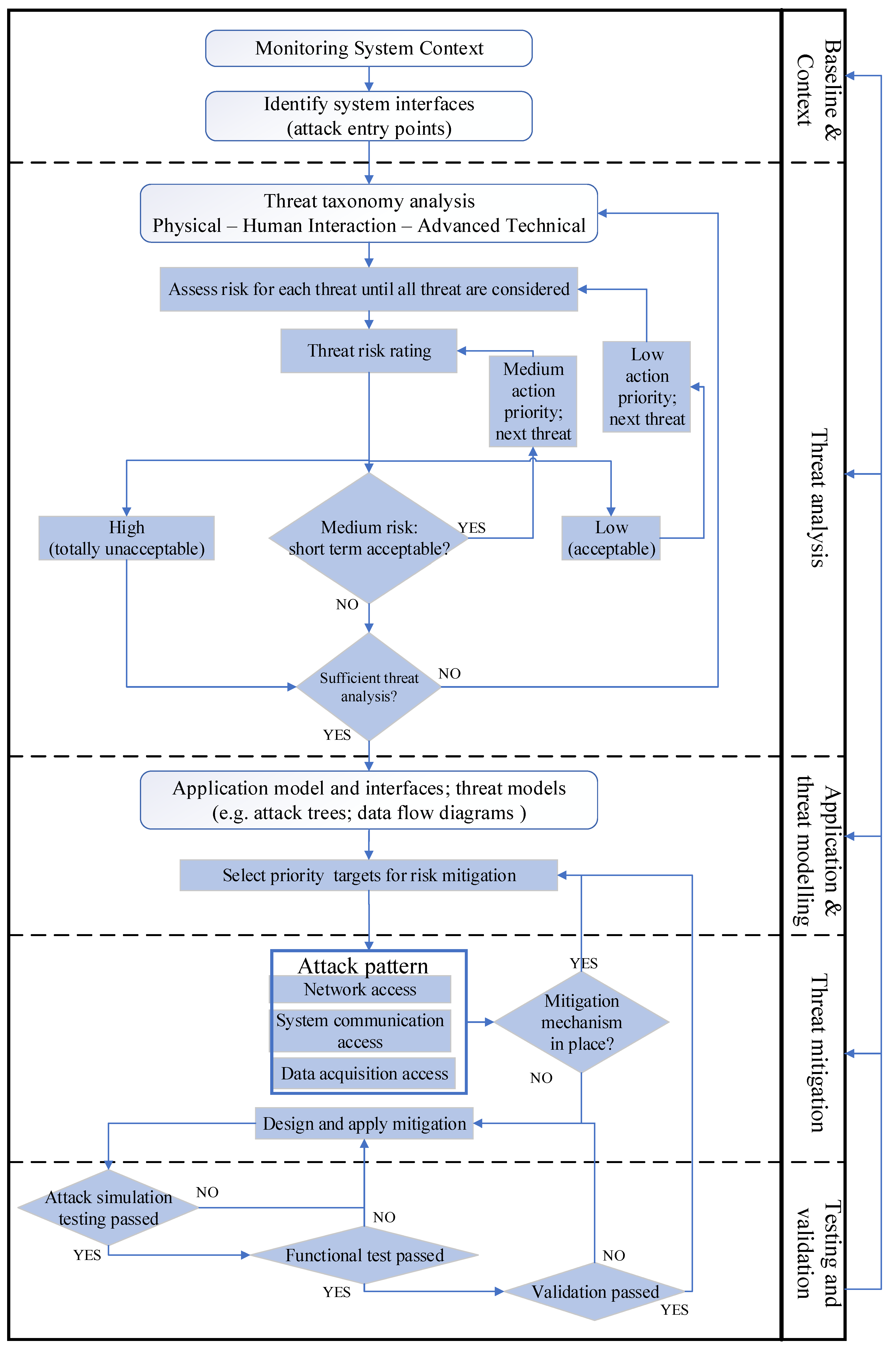
2. Design Thinking for IoT Security in Industrial Environments
- (a)
- Baseline and context: This stage involves analysis of current practices in production environments. An understanding of the application context and system component interfaces, which may be exposed to security threats, is necessary to apply proposed concepts to a specific application target.
- (b)
- Threat analysis: Having identified the high-level system interfaces which pose security risks, this stage involves an analysis of key security issues and vulnerabilities related to the implementation of IoT inside a production environment. Each vulnerability exploited by a threat can create an adverse impact on system integrity. A taxonomy of threats is produced, classifying them under the broader categories of physical, human interaction, and advanced technical ones. For each threat, possible mitigation mechanisms are proposed, and impact risk assessment is performed. Risk is quantified in three categories (High, Medium, and Low), consistent with recommendations [55].
- (c)
- Application and threat modelling: The third phase provides the application context needed for an effective approach. It produces a more detailed model of the targeted system, along with its interfaces and functionality. Modelling tools include data flow diagrams (DFD) [56] to understand the permeation of data trust between components, and systematic threat modelling via attack trees [57], which need to be checked for coverage of security threats.
- (d)
- Threat mitigation: The fourth phase deals with design and implementation of security threats-mitigation mechanisms. In the present work, an instance of the overall process is created and applied to the real-time monitoring application relevant to production environments.
- (e)
- Testing and validation: This includes testing and validation of the mitigation mechanisms against selected threats. Testing may include simulation and functional testing, while validation may be performed in a test or a controlled operational environment. Results from functional and penetration testing can be fed back to improve the mitigation effectiveness. The functional aim of the test in the selected application case is to deliver uninterrupted real-time monitoring.
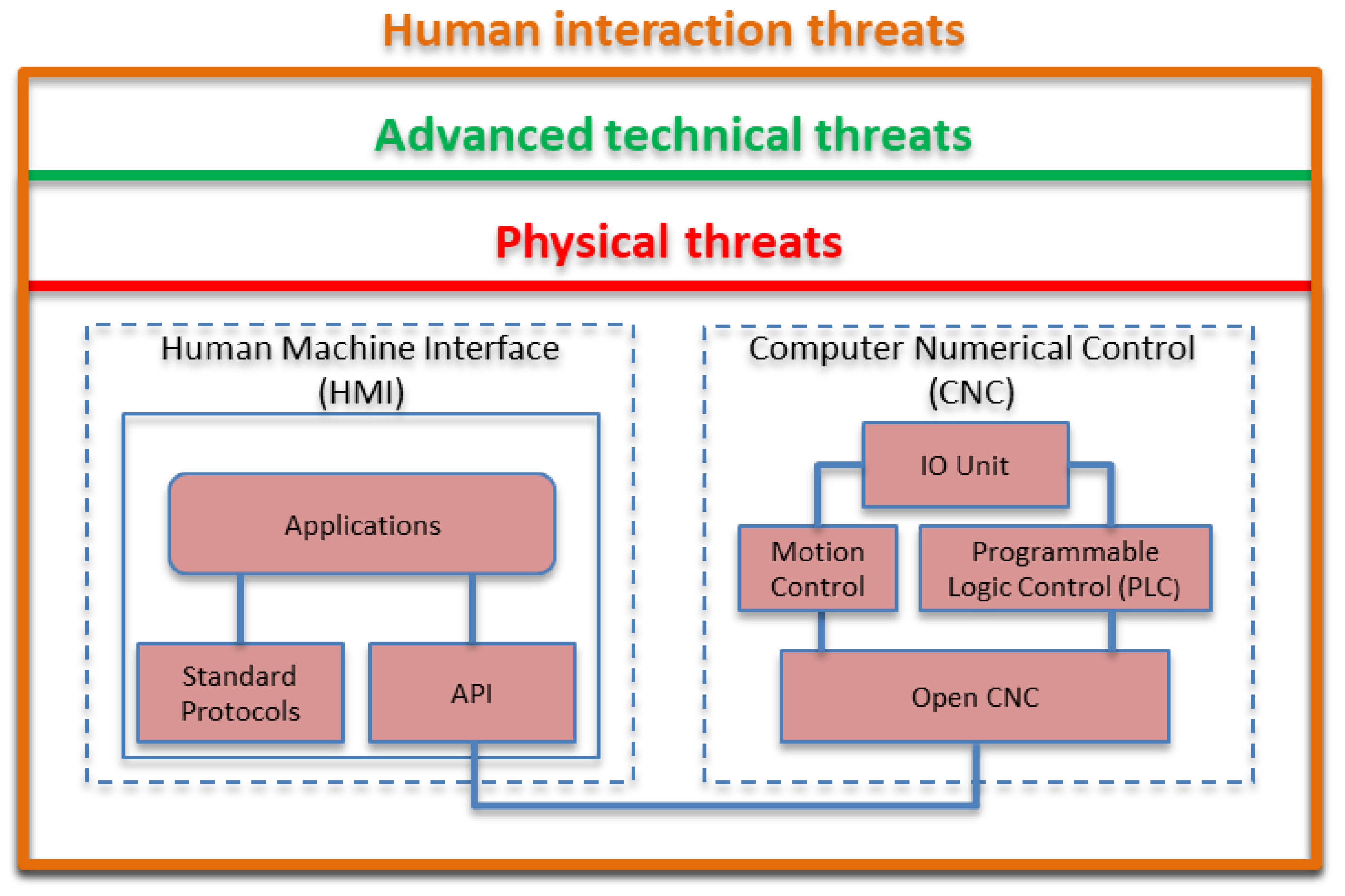
3. Monitoring Systems Security in Industrial Environments
3.1. Baseline and Context
3.2. Threat Analysis
- ✓
- External entities (EE), considered as end-point of a system;
- ✓
- Processes (P), such as system or unit functionality;
- ✓
- Data flows (DF), i.e., ways to transfer data;
- ✓
- Data storage (DS), such as database or files for recorded information.
4. Application and Threat Modelling
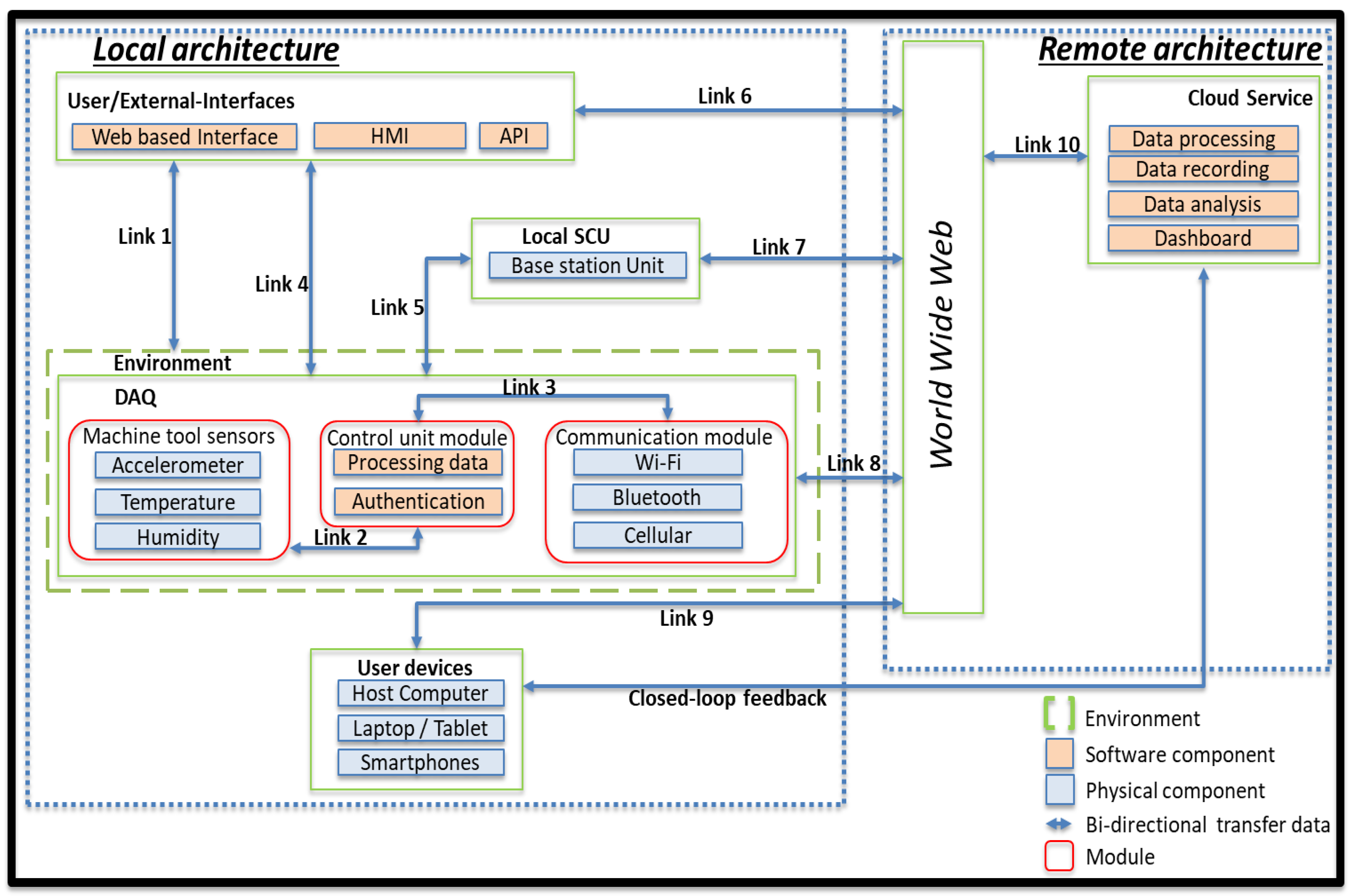
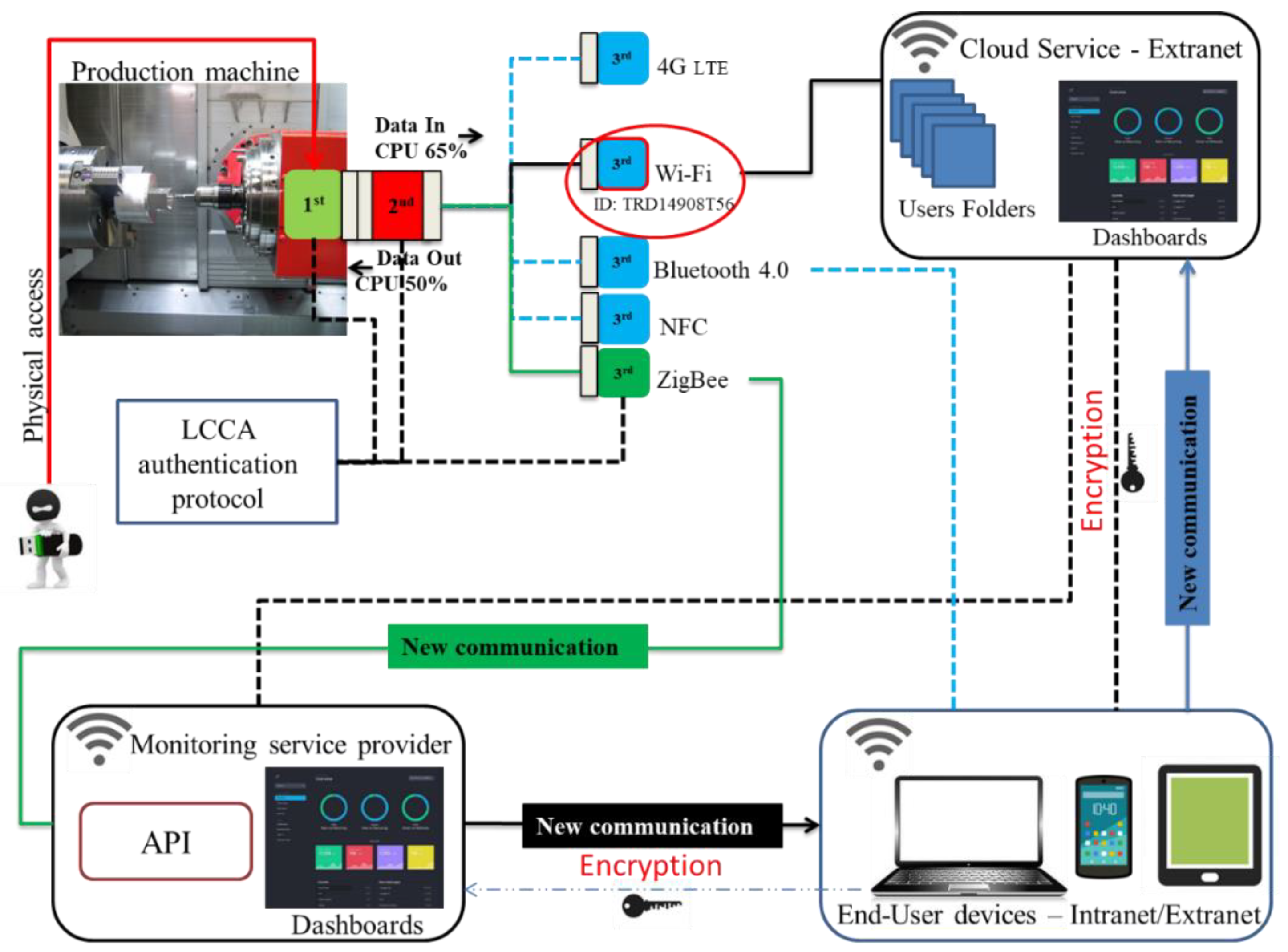
4.1. Application Model and Data Interfaces
- Link 1: The environment includes the legacy production machinery, the DAQ modules, with access to configuration and management web services.
- Link 2: Data acquired from the sensor module are sent to the control module.
- Link 3: The control module manages the authentication process and passes data to the communication module.
- Link 4: The DAQ provides a user-interface to manage and visualise the data acquisition in real-time, residing within the monitored facility.
- Link 5: The DAQ and the SCU exchange data between the sensors and the local architecture.
- Link 6: Interfaces offer data visualisation and support or trigger appropriate actions.
- Link 7: The SCU employs cloud access to offer machine data management to users.
- Link 8: The DAQ communicates with cloud services via the internet.
- Link 9: User devices are communicating with the cloud or server through the internet, exchanging information relevant monitoring information.
- Link 10: Data management and visualisation services are made available to the user.
4.2. Threat Goals Modelling
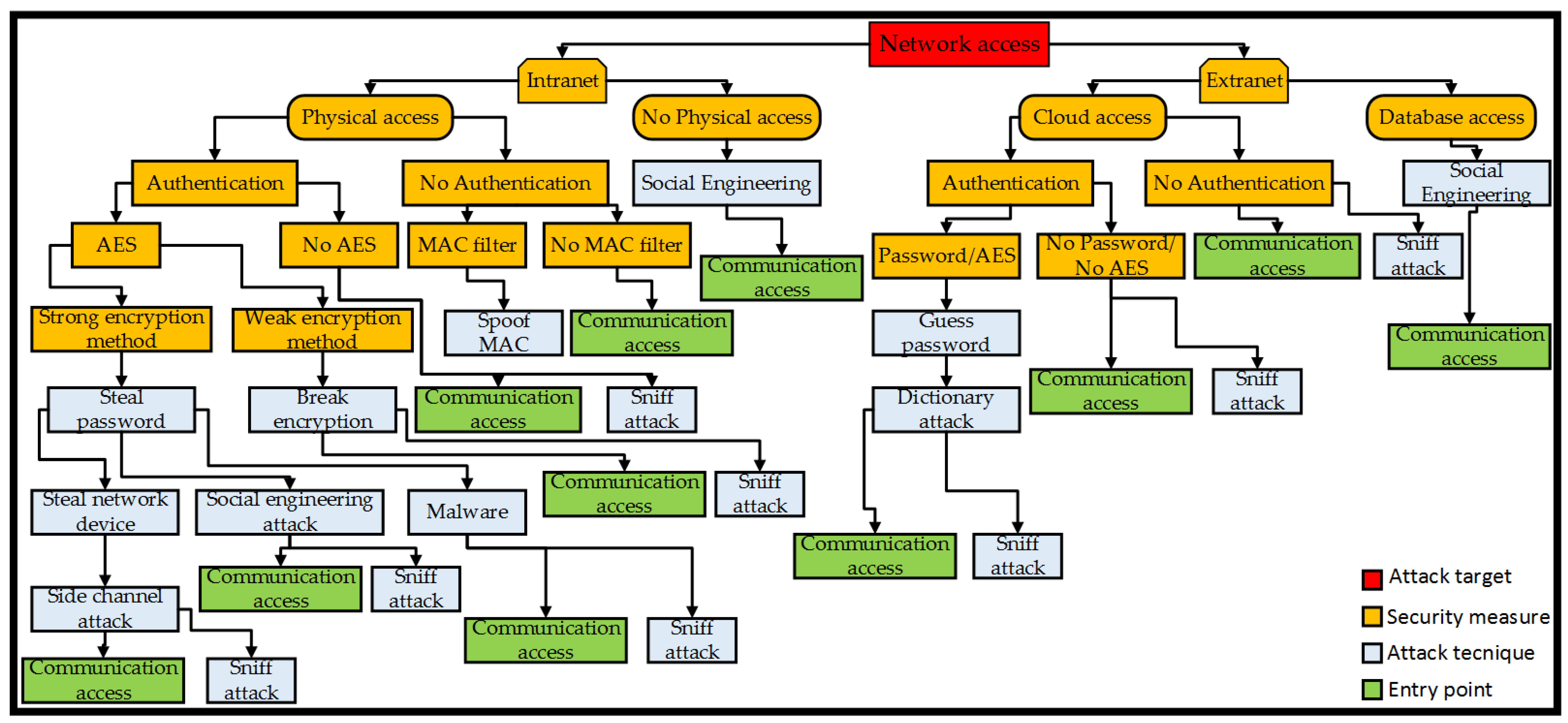
4.2.1. Network Access
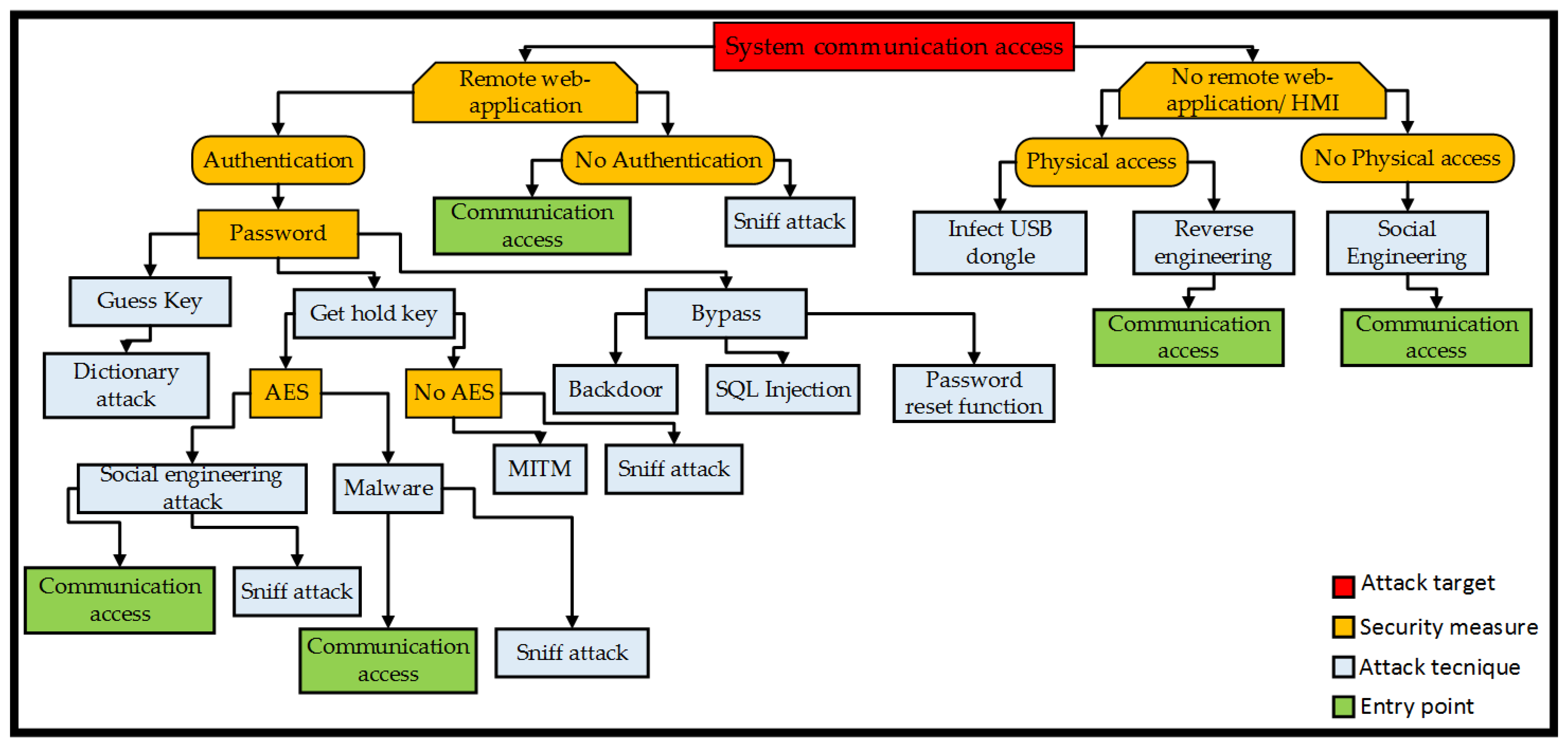
4.2.2. System Communication Access
4.2.3. Data Acquisition (DAQ) Access
5. Threat Mitigation for IoT-Enabled Production Machinery
The Authentication Protocol
6. Pilot Implementation and Testing
6.1. DoS Attack
- The machine tool equipped with the sensor module on the spindle;
- A hub for a monitoring service provider equipped with an API to make available, through the local network, the machine tool state and performance;
- End-user devices used to monitor the machine tool anywhere and anytime;
- The cloud service for processing, analysing, and planning maintenance interventions.
- Phase 1: The real-time operating clock (RTOC) is used to estimate CPU/core utilization. The scheduler system tick is used for this purpose, as it is based on timer interrupt, which is considered as a relatively accurately measure of elapsed time.
- Phase 2: Counting maximum idle count; an estimation is obtained through observing idle counts during a measurement period. If no task is performed (besides the timer interrupt) this represents the maximum number of idle counts and corresponds to 0% utilisation. Estimation accuracy errors tend to become insignificant when the CPU utilization measurement period is sufficiently large. After calculation of maximum idle counts, no code or task can be added to the idle task.
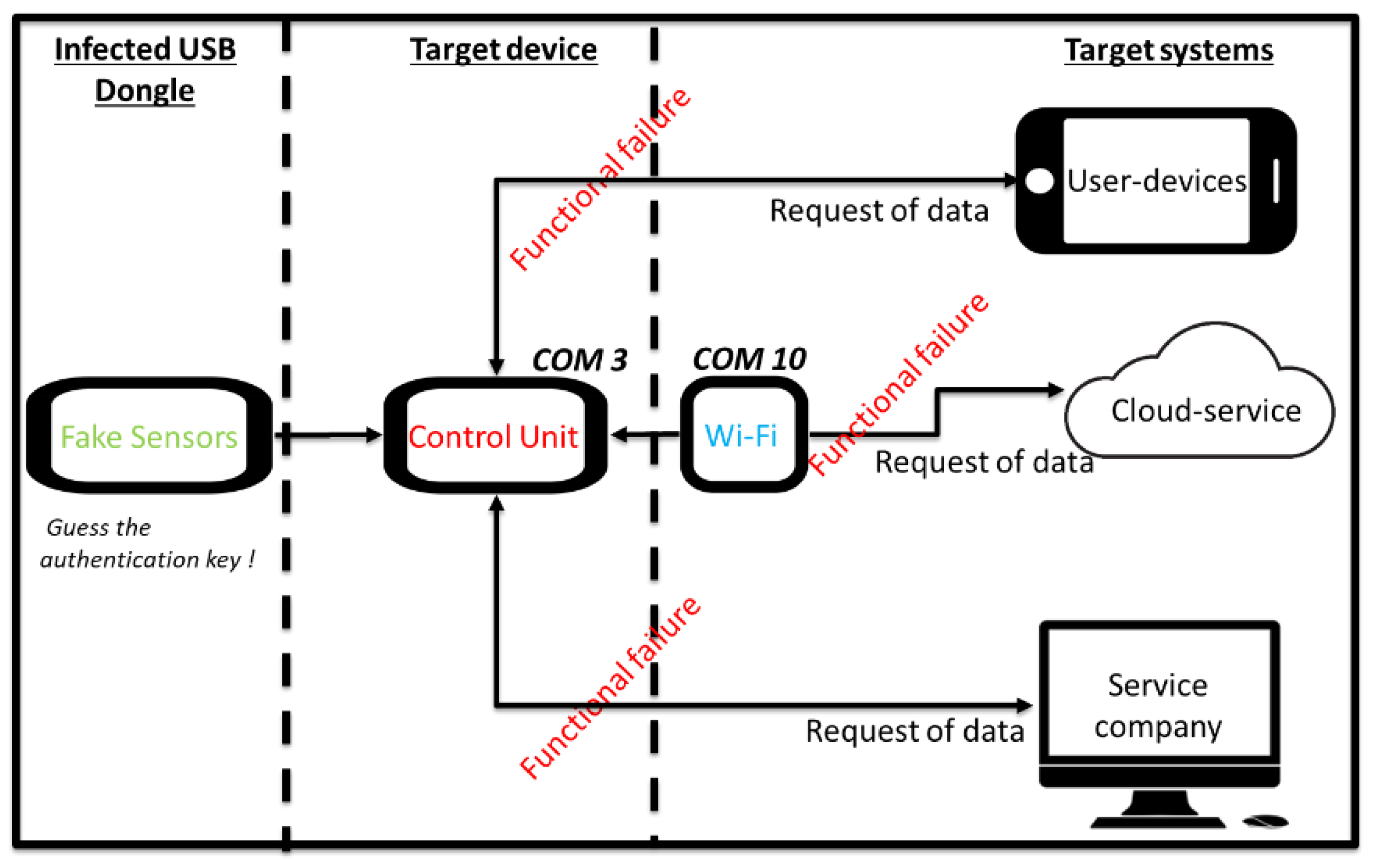
6.2. Cloning Attack
7. Discussion and Related Future Work
- Comprehensive mitigation mechanisms for the range of identified threats. While the reported work presented an implementation example of the design thinking approach, which included specific instances of mitigation mechanisms relevant to preventing DoS and clone attack threats, any alternative and more comprehensive mechanism can be employed instead but would still need to be included within the context of an overall design approach for IoT security.
- Eventually, any introduced mitigation mechanism needs to be scrutinised for effective protection against attacks. The reported work intention was to present the multistage design thinking approach, with mitigation being a concrete step within this. Any final deployment of adopted solutions needs to be preceded by extensive and systematic testing against attacks. Such a testing will need to consider simulation or indeed emulation of attacks, as well as mechanisms for their systematic generation [90].
- The reported work includes risk assessment and mitigation as part of the five-stage systematic approach. However, risk quantification was only indicative and of qualitative nature. Further work is needed in the direction of systematic risk quantification, including approaches for data- and evidence-driven risk quantification [91]. While this is highly important for IoT endpoint devices, overall IoT network security is only as good as its weakest link and a weak node may have scalable negative impacts to the whole IoT network. Further work needs to put into such a context any risk-based approach to security and duly take into account complexity considerations.
- The isolation principle in IoT is effectively applied through virtualisation and containerisation technologies, as expressed, for example, by the IISF. While such technologies were more applicable to cloud services, they are increasingly expanded and implemented at the edge node level. IoT endpoint device security can strongly benefit via joint physical and virtual isolation, and future research need to align relevant research with such IoT architecture patterns [89,90].
- Organisations seeking to adopt security-by-design approaches would benefit from methodologies and tools that assist in appropriate prioritisation of any upgrades related to security. It is futile to implement the most sophisticated approach for part one aspect of security, when others are left too weak. Maturity assessment methods and tools are helpful to this end. Future work would need to look how to best place a design thinking approach, such as the one presented in this paper, within the context of overall organisational security maturity management [92].
8. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Data Access
Abbreviations
| AES | Advanced Encryption Standard |
| CBM | Condition-Based Maintenance |
| CM | Condition Monitoring |
| CNC | Computer Numerical Control |
| CPS | Cyber-Physical Systems |
| CPPS | Cyber Physical Production Systems |
| CPU | Central Processing Unit |
| DAQ | Data Acquisition |
| DFD | Data Flow Diagram |
| DoS | Denial of Service |
| DTLS | Datagram Transport Layer Security |
| HMI | Human Machine Interface |
| ICS | Industrial Control Systems |
| IT/OT | Information Technology/Operational Technology |
| IoT | Internet of Things |
| MAC | Medium Access Control |
| MITM | Man-in-the-Middle |
| LCCA | Log identity, Communication, Connection, Authentication |
| OT | Operational Technology |
| P2P | Peer-to-Peer |
| PAC | Programmable Automation Controller |
| PLC | Programmable Logic Controller |
| PLM | Product Lifecycle Management |
| RMS | Remote Monitoring System |
| SCADA | Supervisory Control and Data Acquisition |
| SCU | System Control Unit |
| SQL | Structured Query Language |
| WSN | Wireless Sensor Network |
References
- Lee, J.; Kao, H.; Yang, S. Service innovation and smart analytics for Industry 4.0 and big data environment. In Proceedings of the 6th CIRP Conference on Industrial Product Service Systems, Windsor, ON, Canada, 1 May 2014; pp. 3–8. [Google Scholar]
- Deshpande, A.; Pieper, R. Legacy Machine Monitoring using power signal analysis. In Proceedings of the ASME 2011 International Manufacturing Science and Engineering Conference MSEC2011, Corvallis, OR, USA, 13–17 June 2011; pp. 207–214. [Google Scholar]
- Hascoet, J.Y.; Rauch, M. Enabling Advanced CNC Programming with openNC Controllers for HSM Machines Tools. High Speed Mach. 2016, 2, 1–14. [Google Scholar] [CrossRef] [Green Version]
- Elghazel, W.; Bahi, J.; Guyeux, C.; Hakem, M.; Medjaher, K.; Zerhouni, N. Dependability of wireless sensor networks for industrial prognostics and health management. Comput. Ind. 2015, 68, 1–15. [Google Scholar] [CrossRef]
- Sadeghi, A.R.; Wachsmann, C.; Waidner, M. Security and privacy challenges in industrial Internet of Things. In Proceedings of the 52nd ACM/EDAC/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 8–12 June 2015; pp. 1–6. [Google Scholar]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A Survey on Security and Privacy Issues in Internet-of-Things. IEEE Internet Things 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Zhou, L.; Yeh, K.H.; Hancke, G.; Liu, Z.; Su, C. Security and Privacy for the Industrial Internet of Things: An Overview of Approaches to Safeguarding Endpoints. IEEE Signal Proc. Mag. 2018, 35, 76–87. [Google Scholar] [CrossRef]
- Murakami, K.; Suemitsu, H.; Matsuo, T. Classification of repeated replay-attacks and its detection monitor. In Proceedings of the 6th IEEE Global Conference on Consumer Electronics (GCCE), Nagoya, Japan, 24–27 October 2017; pp. 1–2. [Google Scholar]
- Patil, D.S.; Patil, S.C. A Novel Algorithm for Detecting Node Clone Attack in Wireless Sensor Networks. In Proceedings of the International Conference on Computing, Communication, Control and Automation (ICCUBEA), Pune, India, 17–18 August 2017; pp. 1–4. [Google Scholar]
- Fernandez-Carames, T.M.; Fraga-Lamas, P.; Suarez-Albela, M.; Castedo, L. Reverse Engineering and Security Evaluation of Commercial Tags for RFID-Based IoT Applications. Sensors 2017, 17, 28. [Google Scholar] [CrossRef]
- Ogiela, L.; Ogiela, M.R. Insider Threats and Cryptographic Techniques in Secure Information Management. IEEE Syst. J. 2017, 11, 405–414. [Google Scholar] [CrossRef]
- Iqbal, M.A.; Bayoumi, M. A Novel Authentication and Key Agreement Protocol for Internet of Things Based Resource-constrained Body Area Sensors. In Proceedings of the 4th International Conference on Future Internet of Things and Cloud Workshops, W-Fi Cloud 2016, Vienna, Austria, 22–24 August 2016; pp. 315–320. [Google Scholar]
- Abawajy, J. Enhancing RFID tag resistance against cloning attack. In Proceedings of the 3rd International Conference on Network and System Security, Goal Coast, Australia, 19–21 October 2009; pp. 18–23. [Google Scholar]
- Ray, B.; Huda, S.; Chowdhury, M.U. Smart RFID reader protocol for malware detection. In Proceedings of the 12th ACIS International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing, Sydney, Australia, 6–8 July 2011; pp. 64–69. [Google Scholar]
- Desai, A.R.; Hsiao, M.S.; Wang, C.; Nazhandali, L.; Hall, S. Interlocking obfuscation for anti-tamper hardware. In Proceedings of the 8th Annual Cyber Security and Information Intelligence Research Workshop: Federal Cybersecurity R and D Program Thrusts, CSIIRW 2013, Oak Ridge, TN, USA, 8 January 2013; pp. 1–4. [Google Scholar]
- Shostack, A. Threat Modelling: Design for Security; Wiley: Indianapolis, IN, USA, 2014; pp. 29–351. [Google Scholar]
- Khan, R.; McLaughlin, K.; Laverty, D.; Sezer, S. STRIDE-based threat modelling for cyber-physical systems. In Proceedings of the IEEE PES Innovative Smart Grid Technologies Conference Europe (ISGT-Europe), Torino, Italy, 26–29 September 2017; pp. 1–6. [Google Scholar]
- Ucedavelez, T.; Morana, M.M. Risk Centric Threat Modeling: Process for Attack Simulation and Threat Analysis; Wiley: Hoboken, NJ, USA, 2015; pp. 317–342. [Google Scholar]
- Wang, E.K.; Ye, Y.; Xu, X.; Yiu, S.M.; Hui, L.C.K.; Chow, K.P. Security issues and challenges for cyber-physical systems. In Proceedings of the IEEE/ACM Int’l Conference on Green Computing and Communications & Int’l Conference on Cyber, Physical and Social Computing, Washington, DC, USA, 18–20 December 2010; pp. 733–738. [Google Scholar]
- Monostori, L. Cyber-physical production systems: Roots, expectations and R&D challenges. In Proceedings of the 47th CIRP Conference on Manufacturing Systems, Windsor, ON, Canada, 28–30 April 2014; pp. 9–13. [Google Scholar]
- Alexandru, A.M.; De Mauro, A.; Fiasché, M.; Sisca, F.G.; Taisch, M.; Fasanotti, L.; Grasseni, P. A smart web-based maintenance system for a smart manufacturing environment. In Proceedings of the 1st IEEE International Forum on Research and Technologies for Society and Industry Leveraging a Better Tomorrow (RTSI), Torino, Italy, 16–18 September 2015; pp. 1–6. [Google Scholar]
- Weippl, E.; Kirseberg, P. Security in cyber-physical production systems: A roadmap to improving IT-security in the production system lifecycle. In Proceedings of the AEIT International Annual Conference, Cagliari, Italy, 20–22 September 2017; pp. 1–6. [Google Scholar]
- ENISA. Good Practices for Security of Internet of Things in the Context of Smart Manufacturing, November 2018. Available online: https://www.enisa.europa.eu/publications/good-practices-for-security-of-iot (accessed on 13 May 2019).
- Wolf, M.; Serpanos, D. Safety and Security in Cyber-Physical Systems and Internet-of-Things Systems. Proc. IEEE 2018, 106, 9–20. [Google Scholar] [CrossRef]
- Koopman, P.; Wagner, M. Transportation CPS Safety Challenges. In Proceedings of the NSF workshop Transportation Cyber-Physical Systems, Pittsburgh, PA, USA, 23–24 January 2014; pp. 1–3. [Google Scholar]
- Fidler, D.P. Was Stuxnet an Act of War? Decoding a Cyberattack. IEEE Secur. Priv. 2011, 9, 56–59. [Google Scholar] [CrossRef]
- Johnson, C. Securing the participation of safety-critical SCADA systems in the industrial internet of things. In Proceedings of the 11th International Conference on System Safety and Cyber Security (SSCS), London, UK, 11–13 October 2016; pp. 11–13. [Google Scholar]
- Hehenberger, P.; Vogel-Heuser, B.; Bradley, D.; Eynard, B.; Tomiyama, T.; Achiche, S. Design, modelling, simulation and integration of cyber physical systems: Methods and applications. Comput. Ind. 2016, 82, 273–289. [Google Scholar] [CrossRef] [Green Version]
- DeSmita, Z.; Elhabashy, A.E.; Wells, J.L.; Jaime, A.C. An approach to cyber-physical vulnerability assessment for intelligent manufacturing systems. J. Manuf. Syst. 2017, 43, 339–351. [Google Scholar] [CrossRef]
- Hutchins, M.J.; Bhinge, R.; Maxwell, K.M.; Robinson, S.L.; Sutherland, J.W.; Dornfeld, D. Framework for Identifying Cybersecurity Risks in Manufacturing. Procedia Manuf. 2015, 1, 47–63. [Google Scholar] [CrossRef] [Green Version]
- Finogeev, A.G.; Finogeev, A.A. Information attacks and security in wireless sensor networks of industrial SCADA systems. J. Ind. Inf. Integr. 2017, 5, 6–16. [Google Scholar] [CrossRef]
- Conklin, A.W. IT vs. OT Security: A Time to Consider a Change in CIA to Include Resilience. In Proceedings of the 49th Hawaii International Conference System Sciences (HICSS), Koloa, HI, USA, 5–8 January 2016; pp. 2642–2647. [Google Scholar]
- Global Cyber Executive Briefing-Manufacturing. Available online: https://www2.deloitte.com/global/en/pages/risk/articles/Manufacturing.html (accessed on 13 May 2019).
- ISTR Internet Security Threat Report 2018; Volume 23. Available online: https://www.symantec.com/content/dam/symantec/docs/reports/istr-23-2018-en.pdf (accessed on 13 May 2019).
- The Verge. Available online: https://www.theverge.com/2017/5/14/15637472/renault-nissan-shut-down-french-uk-factories-wannacry-cyberattack (accessed on 13 May 2019).
- Ylmaz, E.N.; Ciylan, B.; Gönen, S.; Sindiren, E.; Karacayılmaz, G. Cyber security in industrial control systems: Analysis of DoS attacks against PLCs and the insider effect. In Proceedings of the 6th International Istanbul Smart Grids and Cities Congress and Fair (ICSG), Istanbul, Turkey, 25–26 April 2018; pp. 81–85. [Google Scholar]
- Langner, R. Stuxnet: Dissecting a Cyberwarfare Weapon. IEEE Secur. Priv. 2011, 9, 49–51. [Google Scholar] [CrossRef]
- Chen, T.M.; Abu-Nimeh, S. Lessons from Stuxnet. Computer 2011, 44, 91–93. [Google Scholar] [CrossRef]
- Elhabashy, A.; Lee, J.W.; Camelio, J.; Woodall, W.H. A Cyber-physical Attack Taxonomy for Production Systems: A Quality Control Perspective. J. Intell. Manuf. 2016, 1–16. [Google Scholar] [CrossRef]
- Krotofil, M.; Gollmann, D. Industrial control systems security: What is happening. In Proceedings of the 11th IEEE International Conference on Industrial Informatics (INDIN), Bochum, Germany, 29–31 July 2013; pp. 664–669. [Google Scholar]
- Kim, H.; Kang, E.; Broman, D.; Lee, E.A. An architectural mechanism for resilient IoT services. In Proceedings of the 1st ACM Workshop on Internet of Safe Things, Delft, The Netherlands, 5 November 2017; pp. 8–13. [Google Scholar]
- Do, Q.; Martini, B.; Choo, K.-K.R. Is the data on your wearable device secure? An Android Wear smartwatch case study. Softw. Pract. Exp. 2016, 47, 391–403. [Google Scholar] [CrossRef]
- Ibrahim, A.; Sadeghi, A.R.; Tsudik, G.; Zeitouni, S. DARPA: Device Attestation Resilient to Physical Attacks. In Proceedings of the 9th ACM Conference on Security & Privacy in Wireless and Mobile Networks, Darmstadt, Germany, 18–20 July 2016; pp. 171–182. [Google Scholar]
- Salmam, O.; Abdallah, S.; Elhaji, H.I.; Chehab, A.; Kayssi, A. Identity-based authentication scheme for the internet of things. In Proceedings of the Symposium on Computers and Communication (ISCC), Messina, Italy, 27–30 June 2016; pp. 1109–1111. [Google Scholar]
- Porambage, P.; Schmitt, C.; Kumar, P.; Gurton, A.; Ylianttila, M. Pauthkey: A pervasive authentication protocol and key establishment scheme for wireless sensor networks in distributed applications. Int. J. Distrib. Sens. Netw. 2014, 10, 1–14. [Google Scholar] [CrossRef]
- Haythem Ahmad, B.S.; Mohammed, F.D. Event-driven hybrid MAC protocol for a two-tier cognitive wireless sensor network: Design and implementation. Int. J. High Perform. Comput. Netw. 2016, 9, 271–280. [Google Scholar] [CrossRef]
- Sharaf-Dabbagh, Y.; Saad, W. On the authentication of devices in the internet of things. In Proceedings of the 17th IEEE Symposium on A World of Wireless, Mobile and Multimedia Networks (WoWMoM), Coimbra, Portugal, 21–24 June 2016; pp. 1–3. [Google Scholar]
- Zhang, C.; Green, R. Communication security in internet of things: Preventive measure and avoid ddos attack over iot network. In Proceedings of the 18th Symposium on Communication & Networking, Alexandria, VA, USA, 12–15 April 2015; pp. 8–15. [Google Scholar]
- Dos Santos, L.G.; Guimaraes, T.V.; Da Cunha, R.G.; Granville, Z.L.; Tarouco, R.M. A dtls-based security architecture for the internet of things. In Proceedings of the IEEE Symposium on Computers and Communication (ISCC), Larnaca, Cyprus, 6–9 July 2015; pp. 809–815. [Google Scholar]
- Jebri, S.; Abis, M.; Bouallegue, A. An Efficient scheme for anonymous communication in iot. In Proceedings of the 11th International Conference on Information Assurance and Security (IAS), Marrakech, Morocco, 14–16 December 2015; pp. 7–12. [Google Scholar]
- Yoshigoe, K.; Dai, W.; Abramson, M.; Jacobs, A. Overcoming invasion of privacy in smart home environment with synthetic packet injection. In Proceedings of the TRON Symposium (TRONSHOW), Tokyo, Japan, 9–10 December 2014; pp. 1–7. [Google Scholar]
- Mehnen, J.; He, H.; Tedeschi, S.; Tapoglou, N. Practical Security Aspects of the Internet of Things. Cybersecurity for Industry 4.0; Thames, L., Schaefer, D., Eds.; Springer Nature: Birmingham, UK, 2017; pp. 225–242. [Google Scholar]
- Industrial Internet Security Framework Technical Report. Available online: https://www.iiconsortium.org/IISF.htm (accessed on 13 May 2019).
- ISO/IEC 27001. Available online: https://www.iso.org/isoiec-27001-information-security.html (accessed on 13 May 2019).
- Information Security. Guide for Conducting Risk Assessment. NIST Special Publication 800-30. Available online: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-30r1.pdf (accessed on 13 May 2019).
- Schmalenberg, F.; Vandenhouten, R. An advanced data processing environment based on data flow diagrams with a flexible triggering and execution model. In Proceedings of the 14th International Symposium on Applied Machine Intelligence and Informatics (SAMI), Herlany, Slovakia, 21–23 January 2016; pp. 159–164. [Google Scholar]
- Hui, X.; Jun, S.; Xinlu, Z.; Lingyu, Y. Attack identification for software-defined networking based on attack trees and extension innovation methods. In Proceedings of the 9th IEEE International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications (IDAACS), Bucharest, Romania, 21–23 September 2017; pp. 485–489. [Google Scholar]
- Maslina, D.; Rajah, R.; Mary, G.; David, A.; Abdul Fuad, A.R.; Azni, A.H. Denial of service: (DoS) Impact on sensors. In Proceedings of the 4th International Conference on Information Management (ICIM), Oxford, UK, 25–27 May 2018; pp. 270–274. [Google Scholar]
- Georges, A.K.; Niki, P.; Iyengar, S.S.; Beltran, J.; Kamhoua, C.; Hernandez, B.L.; Njilla, L.; Makki, A.P. Preventing Colluding Identity Clone Attacks in Online Social Networks. In Proceedings of the 37th International Conference on Distributed Computing Systems Workshops (ICDCSW), Atlanta, GA, USA, 5–8 June 2017; pp. 187–192. [Google Scholar]
- ISO 13372:2012. Condition Monitoring and Diagnostics of Machines—Vocabulary; ISO: Geneva, Switzerland, 2012. [Google Scholar]
- CEN-EN 13306:2017. Maintenance—Maintenance Terminology; CEN: Brussels, Belgium, 2017. [Google Scholar]
- Crespo-Márquez, A. The Maintenance Management Framework: Models and Methods for Complex Systems Maintenance; Springer: Berlin/Heidelberg, Germany, 2007. [Google Scholar]
- Mori, M.; Fujishima, M.; Komatsu, M.; Zhao, B.; Liu, Y. Development of remote monitoring and maintenance system for machine tools. CIRP Ann. Manuf. Technol. 2008, 57, 433–436. [Google Scholar] [CrossRef]
- Emmanouilidis, C.; Bertoncelj, L.; Bevilacqua, M.; Tedeschi, S.; Ruiz Carcel, C. Internet of Things—Enabled Visual Analytics for Linked Maintenance and Product Lifecycle Management. In Proceedings of the 16th IFAC Symposium on Information Control Problems in Manufacturing, Bergamo, Italy, 11–13 June 2018; pp. 435–440. [Google Scholar]
- Kiritsis, D. Closed-loop PLM for intelligent products in the era of the Internet of things. Comput. Aided Des. 2011, 43, 479–501. [Google Scholar] [CrossRef]
- ISO/IEC 27005:2018. Information Technology—Security Techniques—Information Security Risk Management, 3rd ed.; ISO: Geneva, Switzerland, 2018. [Google Scholar]
- Information Security. National Institute of Standards and Technology (NIST). Available online: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-30r1.pdf (accessed on 13 May 2019).
- Zhang, X.; Wuwong, N.; Li, H.; Zhang, X. Information Security Risk Management Framework for the Cloud Computing Environments. In Proceedings of the 10th International Conference on Computer and Information Technology (CIT 2010), Bradford, UK, 29 June–1 July 2010; pp. 1328–1334. [Google Scholar]
- Risk Assessment Report Based on the 2014 Data Branch. University if Washington, IMT 552. Available online: https://www.slideshare.net/DivyaKothari1/jpmorgan-chase-co-risk-assessment-report-62798131 (accessed on 28 March 2016).
- Cyber Security: Challenges Ahead. Available online: http://www.nexusacademicpublishers.com/uploads/portals/Cyber_Security_Challenged_Ahead.pdf (accessed on 13 May 2019).
- Abhishek, D.; Gokham, M.; Joseph, Z. Detecting/preventing information leakage on the memory bus due to malicious hardware. In Proceedings of the Design, Automation & test in Europe Conference & Exhibition (DATE 2010), Dresden, Germany, 8–12 March 2010; pp. 1–6. [Google Scholar]
- Becher, A.; Benenson, Z.; Dornseif, M. Tampering with Motes: Real-World Physical Attacks on Wireless Sensor Networks. In Proceedings of the Third International Conference, Security in Pervasive Computing (SPC), York, UK, 18–21 April 2006; pp. 104–118. [Google Scholar]
- Fachkha, C.; Bou-Harb, E.; Debbabi, M. Inferring distributed reflection denial of service attacks from darknet. Comput. Commun. 2015, 62, 59–71. [Google Scholar] [CrossRef]
- Meyer, D.; Haase, J.; Eckert, M.; Klauer, B. A Threat-Model for Building and Home Automation. In Proceedings of the IEEE 14th International Conference on Industrial Informatics (INDIN), Poitiers, France, 19–21 July 2016; pp. 860–866. [Google Scholar]
- Kang, D.J.; Lee, J.J.; Kim, S.J.; Park, J.H. Analysis on cyber threats to SCADA systems. In Proceedings of the IEEE Transmission & Distribution Conference & Exposition, Seoul, Korea, 26–30 October 2009. [Google Scholar]
- Young, N. Cyber security for automatic test equipment. In Proceedings of the IEEE AUTOTESTCON, Schaumburg, IL, USA, 9–15 September 2017. [Google Scholar]
- SANS: The Threats of Social Engineering and Your Defense Against It. Available online: https://www.sans.org/reading-room/whitepapers/engineering/threat-social-engineering-defense-1232 (accessed on 13 May 2019).
- Rai, K.K.; Asawa, K. Impact analysis of rank attack with spoofed IP on routing in 6LoWPAN network. In Proceedings of the 10th International Conference on Contemporary Computing (IC3), Noida, India, 10–12 August 2017; pp. 1–5. [Google Scholar]
- Nakhila, O.; Zou, C. Parallel Active Dictionary Attack on IEEE 802.11 Enterprise Networks. In Proceedings of the Military Communications Conference, MILCOM 2016-IEEE, Baltimore, MD, USA, 1–3 November 2016; pp. 1–6. [Google Scholar]
- Maraj, A.; Rogova, E.; Jakupi, G.; Grajqevci, X. Testing techniques and analysis of SQL injection attack. In Proceedings of the 2nd International Conference on Knowledge Engineering and Applications, London, UK, 21–23 October 2017; pp. 1–5. [Google Scholar]
- Khanna, S.; Verma, A.K. Classification of SQL Injection Attacks Using Fuzzy Tainting. In Progress in Intelligent Computing Techniques: Theory, Practice, and Applications; Springer: Singapore, 2018; pp. 463–469. [Google Scholar]
- Tedeschi, S.; Emmanouilidis, C.; Farnsworth, M.; Mehnen, J.; Roy, R. New threats for old manufacturing problems: Secure IoT-Enabled monitoring of legacy production machinery. In Proceedings of the APMS 2017: IFIP International Conference on Advances in Production Management Systems: The Path to Intelligent, Collaborative, and Sustainable Manufacturing, Hamburg, Germany, 3–7 September 2017; pp. 391–398. [Google Scholar]
- Oliveira, J.; Frade, M.; Pinto, P. System Protection Agent Against Unauthorized Activities via USB Devices. In Proceedings of the 3rd International Conference on Internet of Things, Big Data and Security (IoTBDS) Funchal, Madeira, Portugal, 19–21 March 2018; pp. 237–243. [Google Scholar]
- Bertino, E.; Islam, N. Botnets and internet of things security. Computer. 2017, 50, 76–79. [Google Scholar] [CrossRef]
- Aansari, H.M.; Vakili, T.V. Detection of clone node attack in mobile wireless sensor network with optimised cost function. Int. J. Sens. Netw. 2017, 24, 149–159. [Google Scholar] [CrossRef]
- Quirke, J. Security in the GSM System. Available online: https://pdfs.semanticscholar.org/b0c8/493e0c6b6e5e08d870a1b318401236e07e82.pdf (accessed on 13 May 2019).
- Helfmeier, C.; Boit, C.; Nedospasov, D.; Seifert, J.P. Cloning Physically Unclonable Functions. In Proceedings of the IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Austin, TX, USA, 2–3 June 2013; pp. 1–6. [Google Scholar]
- Großmann, M.; Illig, S.; Matějka, C.L. SensIoT: An Extensible and General Internet of Things Monitoring Framework. Wirel. Commun. Mob. Comput. 2019, 1–15. [Google Scholar] [CrossRef]
- Morabito, R.; Petrolo, R.; Loscrì, V.; Mitton, N. Reprint of: LEGIoT: A Lightweight Edge Gateway for the Internet of Things. Futur. Gener. Comput. Syst. 2019, 92, 1157–1171. [Google Scholar] [CrossRef]
- Teixeira, F.A.; Pereira, F.M.Q.; Wong, H.; Nogueira, J.M.S.; Oliveira, L.B. SIoT: Securing Internet of Things through distributed systems analysis. Futur. Gener. Comput. Syst. 2019, 92, 1172–1186. [Google Scholar] [CrossRef]
- Matheu-García, S.N.; Hernández-Ramos, J.L.; Skarmeta, A.F.; Baldini, G. Risk-based automated assessment and testing for the cybersecurity certification and labelling of IoT devices. Comput. Stand. Interfaces 2019, 62, 64–83. [Google Scholar] [CrossRef]
- ENISA, Threat Landscape Report 2018, ETL 2018|1.0, January 2019. Available online: https://www.enisa.europa.eu/publications/enisa-threat-landscape-report-2018 (accessed on 13 May 2019).











| Activity Description | Impact Examples | Countermeasure Mechanisms | Threat Types | ||
|---|---|---|---|---|---|
| HIT | ATT | PT | |||
| 1. Negligence Errors and vulnerabilities linked to the launch of a new network within a production environment. | Network delays or errors lead to poor control or loss of control over certain production processes | Operations procedures to be followed by personnel installing or using the network | x | ||
| 2. Social Engineering Uses the human behaviour to gain security access without the victim realising the manipulation. | Could cause system integrity loss (e.g., data loss or tampering, system process malfunctions, poor product quality, health and safety issues). | Training about the social engineering threat, company policy, and procedures. | x | ||
| 3. Denial of service (DoS) Channel is flooded with data, exhausting bandwidth. | Breakdown of network control, causing loss of production monitoring and control capabilities | Network traffic analysis and detection systems | x | ||
| High (H) | The Threat Is Unacceptable and Immediate Measures Are Needed to Reduce It to Preserve Data or System Integrity. |
| Medium (M) | The threat may be acceptable over the short term but countermeasures to reduce the risk should be implemented. |
| Low (L) | The risks are acceptable. Measures to reduce risk can be taken in conjunction with other actions, for example, during upgrades. |
| High (H) | A Highly Motivated and Sufficiently Capable Threat-Source; Protection Countermeasures Are Ineffective. |
| Moderate (M) | The source of the threat is motivated and capable, but some countermeasures in the short term could hinder the success of attacks. |
| Low (L) | Limited motivation and capability of threat-source; the countermeasures are sufficient to prevent the hazard. |
| Impact → → | ||||
|---|---|---|---|---|
| Chance →→ | Low (L) | Moderate (M) | High (H) | |
| High (H) | L × H = M | M × H = H | H × H = H | |
| Moderate (M) | L × M = L | M × M = M | H × M = H | |
| Low (L) | L × L = L | M × L = L | H × L = M | |
| Activity | Threat Types | External Entity (EE) | Data Flow (DF) | Data Store (DS) | Process (P) | Impact Rating | Chance Rating | Score Rating | ||
|---|---|---|---|---|---|---|---|---|---|---|
| HIT | ATT | PT | ||||||||
| Negligence | X | X | M | M | M | |||||
| Social Engineering | X | X | X | H | L | M | ||||
| Tampering | X | X | X | X | H | L | M | |||
| Physical Intrusions | X | X | X | X | X | H | L | M | ||
| User Misuse | X | X | X | H | L | M | ||||
| Unauthorised remote accesses | X | X | H | L | M | |||||
| External hardware | X | X | H | L | M | |||||
| Physical destruction | X | X | X | H | L | M | ||||
| Command injection | X | X | X | M | L | L | ||||
| Denial of Service (DoS) | X | X | X | X | H | M | H | |||
| Signal replaying | X | X | X | X | M | L | L | |||
| Cloning | X | X | X | X | H | M | H | |||
| Remote switch off | X | X | X | H | L | M | ||||
| Signal blocking or jamming | X | X | X | H | L | M | ||||
| Reverse engineering | X | X | X | X | X | H | L | M | ||
| Side-channel | X | X | X | X | X | H | L | M | ||
| Wireless zapping | X | X | X | M | L | L | ||||
| Software compromise | X | X | X | X | X | H | L | M | ||
| Electromagnetic interference | X | X | M | L | L | |||||
| Cable cuts | X | X | X | H | L | M | ||||
| Power fluctuation | X | X | M | M | M | |||||
| Voltage spikes | X | X | H | L | M | |||||
| Installation errors | X | X | M | L | L | |||||
| Takeover of an authorised session | X | X | X | X | X | H | L | M | ||
| Attack Goal | Impact Description | Function Code |
|---|---|---|
| Network access | Inability to communicate with the DAQ | I, U |
| Inability to communicate with the Cloud | U | |
| Inability to communicate with the SCU | C, U | |
| Inability to communicate with User Devices | I, U | |
| Inability to upgrade firmware | I | |
| System communication access | Inability to use the HMI | I, U, P |
| Inability to use the DAQ modules | I, C | |
| Inability to use the legacy production machinery | P, S | |
| DAQ access | Inability to collect correct sensor data | C, I |
| Inability to protect sensor data | C, I | |
| Inability to send data correctly | C, I, U |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tedeschi, S.; Emmanouilidis, C.; Mehnen, J.; Roy, R. A Design Approach to IoT Endpoint Security for Production Machinery Monitoring. Sensors 2019, 19, 2355. https://doi.org/10.3390/s19102355
Tedeschi S, Emmanouilidis C, Mehnen J, Roy R. A Design Approach to IoT Endpoint Security for Production Machinery Monitoring. Sensors. 2019; 19(10):2355. https://doi.org/10.3390/s19102355
Chicago/Turabian StyleTedeschi, Stefano, Christos Emmanouilidis, Jörn Mehnen, and Rajkumar Roy. 2019. "A Design Approach to IoT Endpoint Security for Production Machinery Monitoring" Sensors 19, no. 10: 2355. https://doi.org/10.3390/s19102355
APA StyleTedeschi, S., Emmanouilidis, C., Mehnen, J., & Roy, R. (2019). A Design Approach to IoT Endpoint Security for Production Machinery Monitoring. Sensors, 19(10), 2355. https://doi.org/10.3390/s19102355







