An Ontology-Based Cybersecurity Framework for the Internet of Things
Abstract
1. Introduction
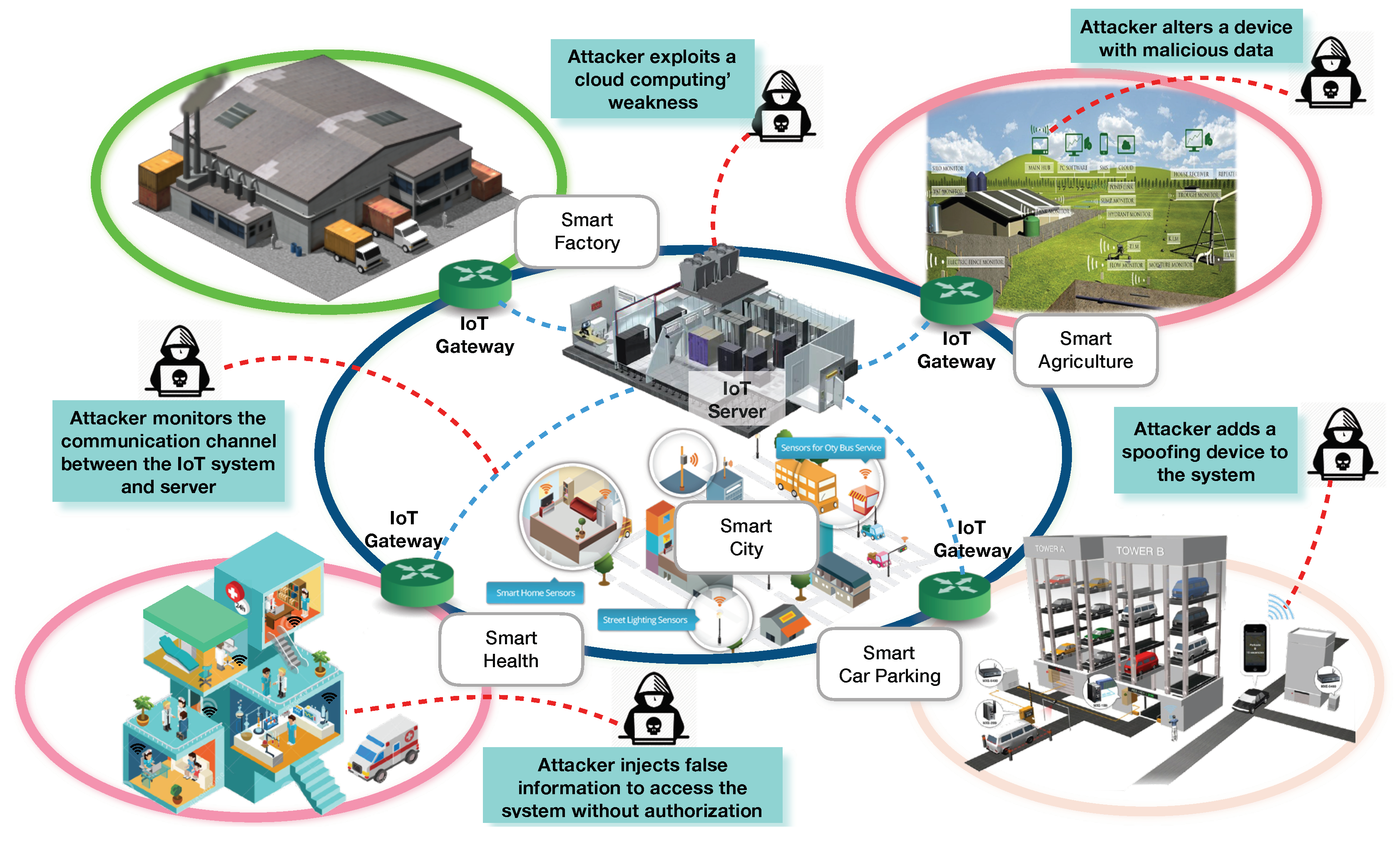
1.1. The Central Challenge: IoT Cybersecurity
1.2. Hypothesis and Main Results
- The cybersecurity framework itself: an integrated technical framework using ontology and knowledge reasoning to address the security aspect of the Internet of Things within industrial environments. The framework focuses on the enterprise (company-side) monitoring, security analysis and the subsequent security service design and provisioning to improve business processes and technology assets;
- The IoTSec ontology, which is a core-component of the framework and a continued work of the authors (see [16]), gathering cybersecurity knowledge about alerts and possible threats and providing reasoning capabilities to discover implicit data from the contextual information of security issues;
- Design and orchestration method to implement and provide suitable security services in the IoT environments through the application of the Model-Driven Service Engineering Architecture (MDSEA) methodology (see [17]);
- Runtime security monitoring and actuation services integrated with the IDMEF standard (see [18]).
2. Related Works
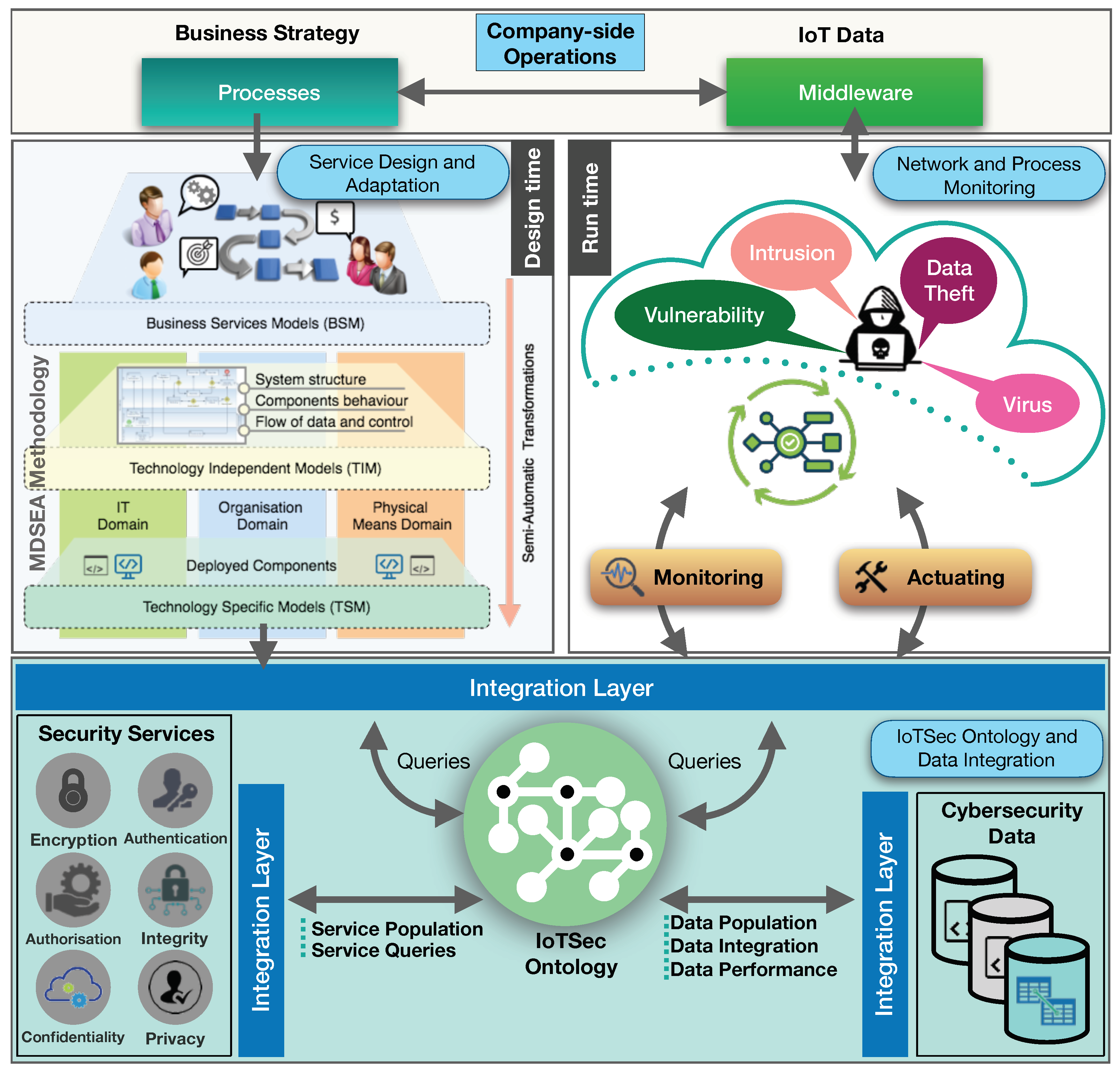
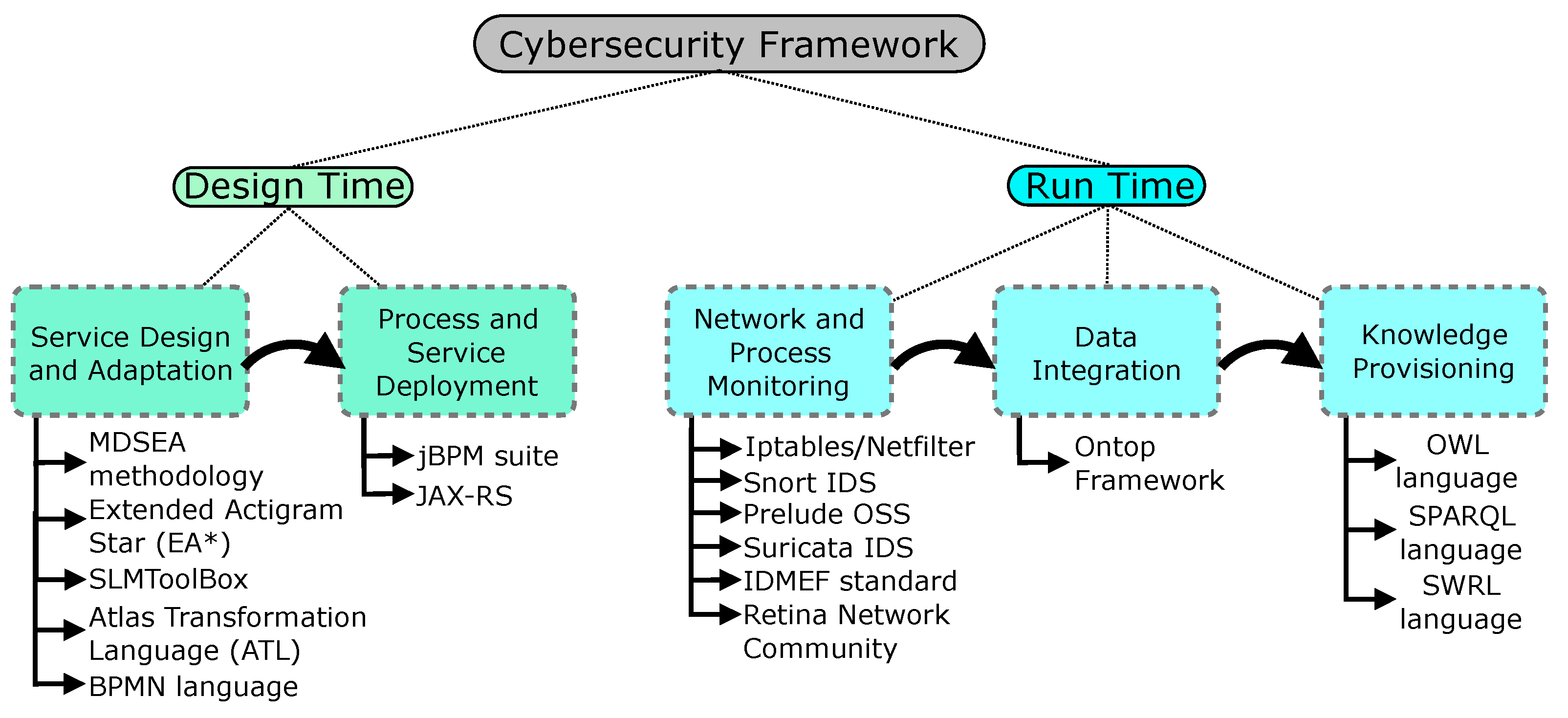
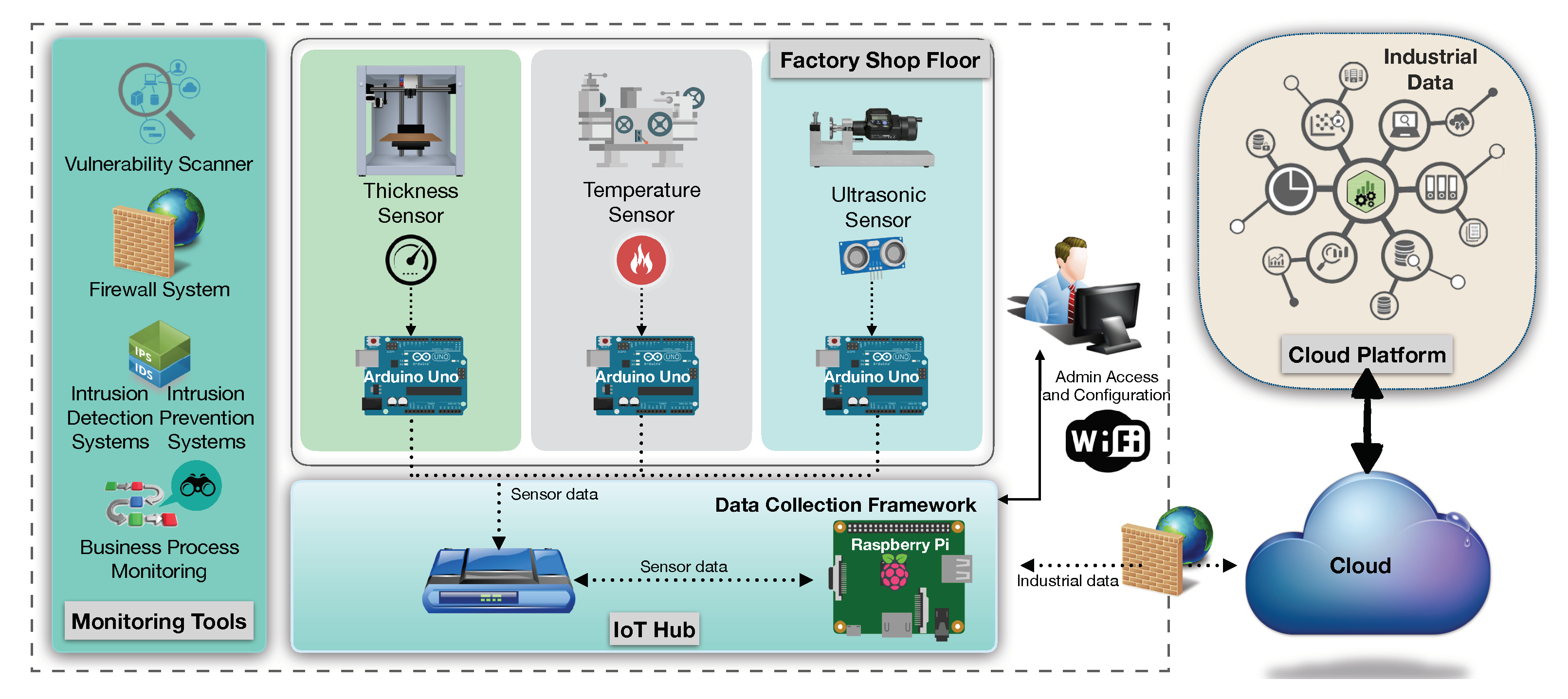
3. Proposed Cybersecurity Framework
3.1. Service Design and Adaptation: Design Time Layer
3.2. Network and Process Monitoring: Run Time Layer
3.3. IoTSec Ontology and Data Integration Layer
3.4. Design Time Usage
3.5. Run Time Usage
3.6. Implementation Considerations
4. Validation and Proof of Concept
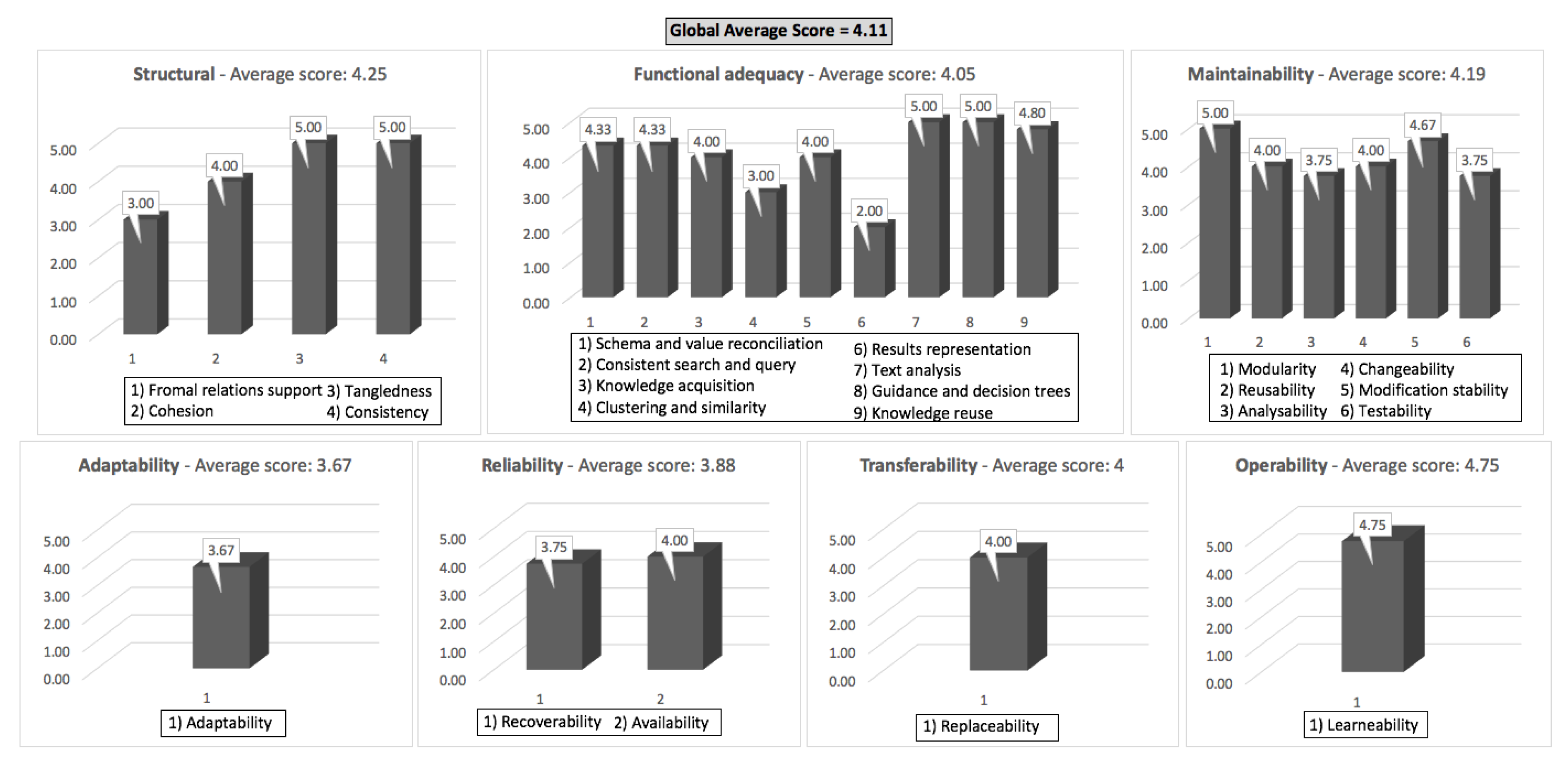
4.1. Ontology Assessment
- The structural characteristic consists of the formal and semantic ontological properties that are widely used in state-of-the-art evaluation approaches. It represents a complete cohesion with a good domain coverage. This helps to verify areas that are more closely connected. It reflects in the knowledge base as a result of extracting data from separate sources. Under structural characteristics, the relation of the number of properties and relationships presents a relatively low value to the formal relations support, which can be improved using inference rules to ensure better formal relations.
- The functional adequacy characteristic follows certain criteria according to the degree of accomplishment of functional requirements over different purposes. As its strengths, the evaluation showed consistent search and query and knowledge reuse considering the mean number of relationships associated, the number of properties per class and the length of the path from the leaf classes to the thing. Furthermore, the metric “mean number of properties per class” collaborates with the knowledge acquisition because it means that probably this ontology is more useful. However, a sub-characteristic demonstrated weaknesses associated with the number of instances. This aspect has no impact on the evaluation because the ontology requires a complete data population for an application in the real world.
- The adaptability characteristic checks if the ontology can be adapted for different specified environments without conducting other than those were identified for the ontology purpose. The metric “number of properties and relationships” is one essential factor to provide adaptability. This measure consists of a better understanding of how certain focal classes work. Hence, the number of relationships reflects the grouping within a class based on its relationship with other instances. However, a sub-characteristic affects the adaptation purpose of the ontology for distinct environments due to the largest path from the thing to a leaf class.
- The reliability characteristic matches the ontology maintenance of the level of performance under the stated conditions for a given period of time. The metric “maximum depth of the hierarchy tree from thing to a leaf class by the total number of paths” directly influences the availability sub-characteristic.
- The transferability characteristic presents the degree to which the software product can be transferred from one environment to another. The metric “number of properties and direct subclasses” allows one to adapt the ontology easily in another context. However, the metric “length of the largest path” affects the recoverability sub-characteristic because the higher is its score, then lower is the probability to recover.
- The maintainability characteristic provides the ability of ontologies to adapt to changes in the environment, in terms of requirements or functional specifications. The number of properties also impacts on reusability (of maintainability) because having a more precisely-defined ontology makes its knowledge more reusable.
- The operability characteristic harmonizes the knowledge necessary to use an ontology, and in the individual assessment of such use, by a single or a set of users. It is measured through the learnability sub-characteristic. The metric “number of the properties per class” reflects in the schema used at the instances level. This metric is a good indication of how well the use of information in the extraction process is. However, the maximum depth of the hierarchy tree from thing to a leaf class minimizes the effectiveness.
4.2. Industrial Case Study to the Proposal Validation
4.2.1. Process/Environment Monitoring
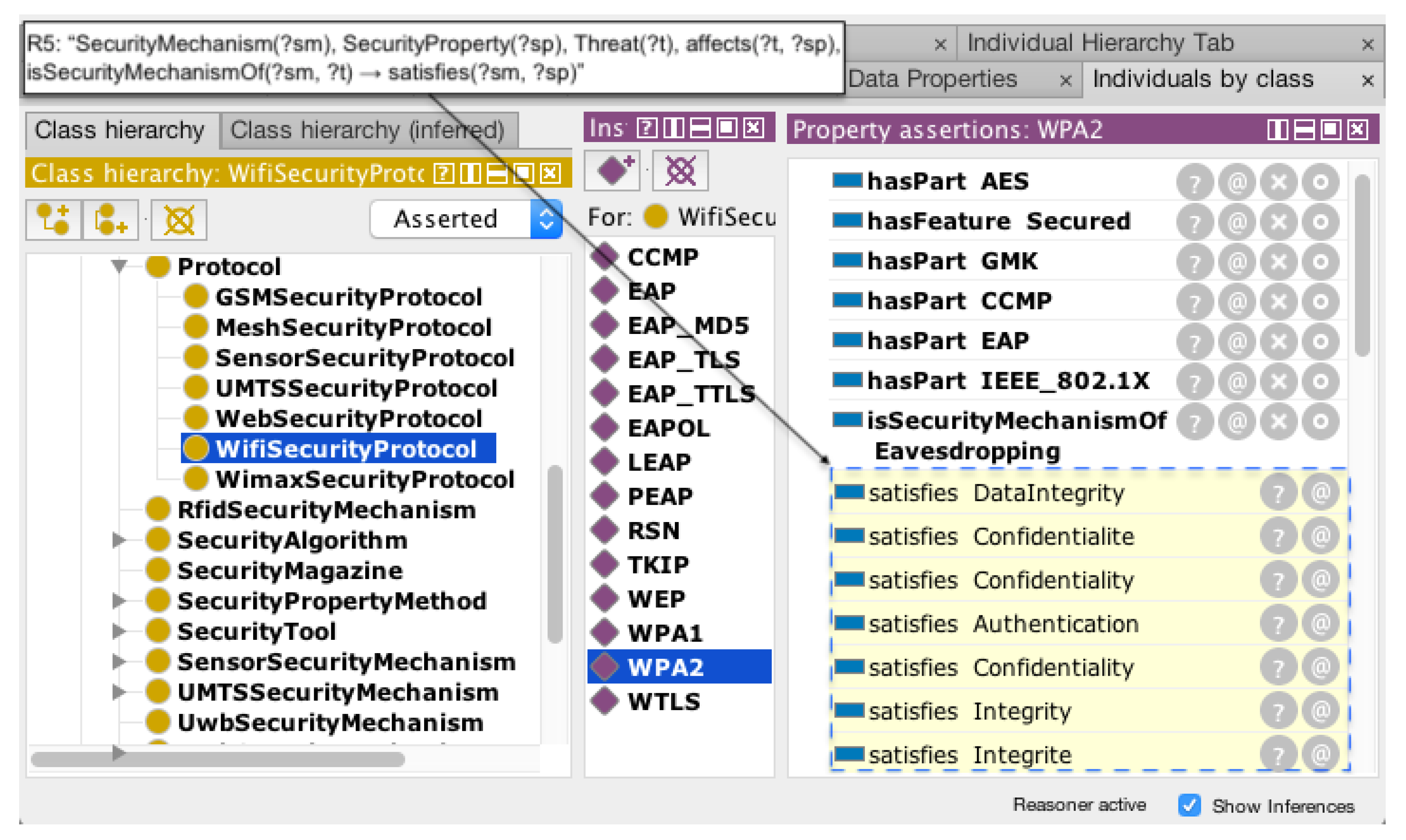
4.2.2. Ontology Usage for Monitoring
- Verifying the consistency of the ontology and knowledge base.
- Verifying the unintended relationship between classes.
- Automatically classifying instances in classes.
- R1:
- hasPart(?x, ?y), hasPart(?y, ?z) → hasPart(?x, ?z)
- R2:
- isSecurityMechanismOf(?sm, ?t), threatens(?t, ?v) → mitigates(?sm, ?v)
- R3:
- protects(?sm, ?a), requires(?a, ?sp) → satisfies(?sm, ?sp)
- R4:
- mitigates(?sm, ?v), threatens(?t, ?v) → isSecurityMechanismOf(?sm, ?t)
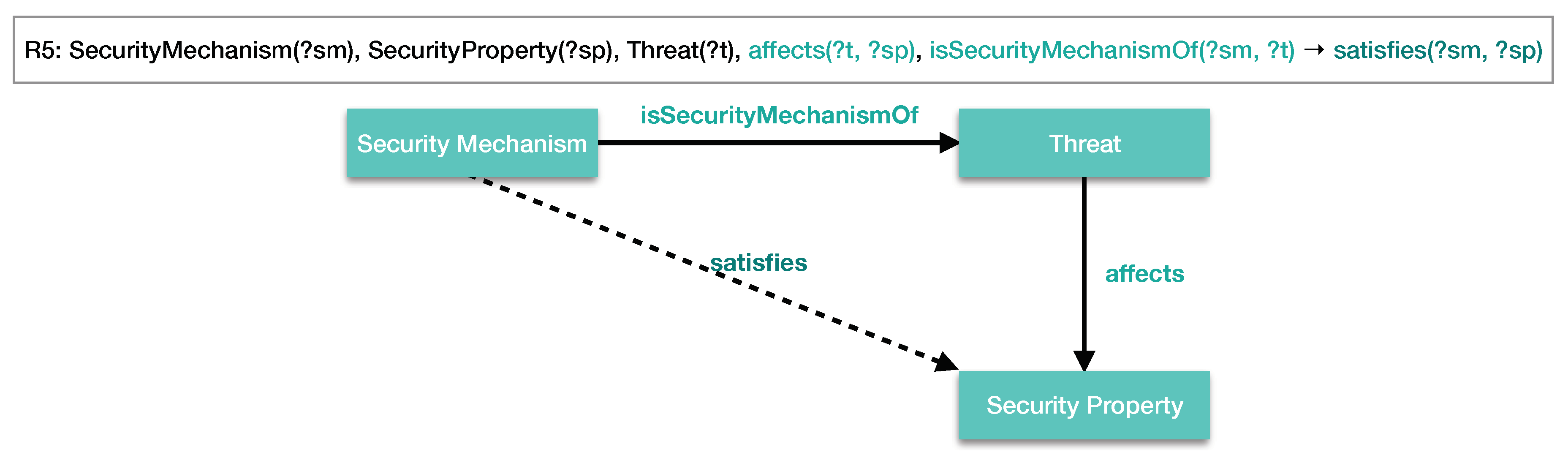
- R5:
- SecurityMechanism(?sm), SecurityProperty(?sp), Threat(?t), affects(?t, ?sp), isSecurityMechanismOf(?sm, ?t) → satisfies(?sm, ?sp)
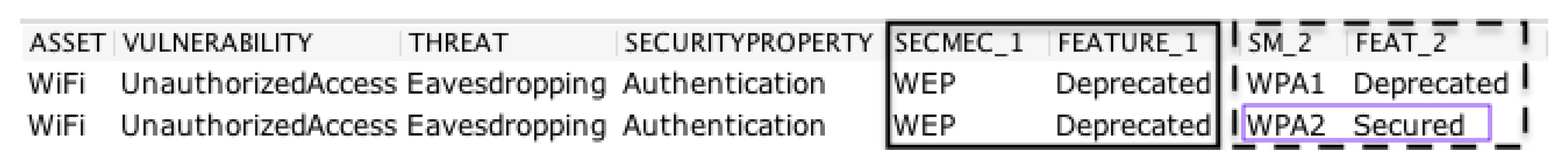
| Listing 1. An example of query of the proposed framework. |
| 1 SELECT ?ASSET ?VULN ?THREAT ?SECPROP ?SECMEC_1 ?FEATURE_1 |
| 2 WHERE { |
| 3 ?VULN iotsec:isVulnerabilityOf ?ASSET . |
| 4 ?VULN iotsec:isThreatensBy ?THREAT . |
| 5 ?THREAT iotsec:affects ?SECPROP . |
| 6 ?SECMEC_1 iotsec:isSecurityMechanismOf ?THREAT . |
| 7 ?SECMEC_1 iotsec:hasFeature ?FEATURE_1 . |
| 8 ?SECMEC_1 rdfs:label ?SMLabel . |
| 9 FILTER regex (?SMLabel, ‘WEP’) |
| 10 } |
4.2.3. Service Adaptation and Actuation on the IoT Network
5. Final Considerations and Discussions
5.1. Contributions of the Work
5.2. Future Research Directions
Author Contributions
Funding
Conflicts of Interest
References
- Ibarra-Esquer, J.E.; González-Navarro, F.F.; Flores-Rios, B.L.; Burtseva, L.; Astorga-Vargas, M.A. Tracking the Evolution of the Internet of Things Concept Across Different Application Domains. Sensors 2017, 17, 1379. [Google Scholar] [CrossRef] [PubMed]
- Delmastro, F. Pervasive communications in healthcare. Comput. Commun. 2012, 35, 1284–1295. [Google Scholar] [CrossRef]
- Polycarpou, E.; Lambrinos, L.; Protopapadakis, E. Smart parking solutions for urban areas. In Proceedings of the 2013 IEEE 14th International Symposium on “A World of Wireless, Mobile and Multimedia Networks” (WoWMoM), Madrid, Spain, 4–7 June 2013; pp. 1–6. [Google Scholar] [CrossRef]
- Ancillotti, E.; Bruno, R.; Conti, M. The role of communication systems in smart grids: Architectures, technical solutions and research challenges. Comput. Commun. 2013, 36, 1665–1697. [Google Scholar] [CrossRef]
- Cai, H.; Xu, L.D.; Xu, B.; Xie, C.; Qin, S.; Jiang, L. IoT-Based Configurable Information Service Platform for Product Lifecycle Management. IEEE Trans. Ind. Inform. 2014, 10, 1558–1567. [Google Scholar] [CrossRef]
- Xu, L.D.; He, W.; Li, S. Internet of Things in Industries: A Survey. IEEE Trans. Ind. Inform. 2014, 10, 2233–2243. [Google Scholar] [CrossRef]
- Manyika, J. The Internet of Things: Mapping the Value Beyond the Hype; McKinsey Global Institute: New York, NY, USA, 2015. [Google Scholar]
- Conti, M.; Das, S.K.; Bisdikian, C.; Kumar, M.; Ni, L.M.; Passarella, A.; Roussos, G.; Tröster, G.; Tsudik, G.; Zambonelli, F. Looking ahead in pervasive computing: Challenges and opportunities in the era of cyber–physical convergence. Pervasive Mob. Comput. 2012, 8, 2–21. [Google Scholar] [CrossRef]
- Ashton, K. That ‘internet of things’ thing. RFID J. 2009, 22, 97–114. [Google Scholar]
- Chase, J. The Evolution of the Internet of Things; Texas Instruments: Dallas, TX, USA, 2013. [Google Scholar]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Wolf, M.; Serpanos, D. Safety and Security in Cyber-Physical Systems and Internet-of-Things Systems. Proc. IEEE 2018, 106, 9–20. [Google Scholar] [CrossRef]
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A Survey on Internet of Things: Architecture, Enabling Technologies, Security and Privacy, and Applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Dell Data Security Survey Finds that a Lack of Security Knowledge Limits Business Initiatives. Available online: http://www.dell.com/learn/us/en/uscorp1/press-releases/dell-data-security-survey/ (accessed on 16 January 2018).
- Sharma, S.; Mishra, R.; Singh, K. A Review on Wireless Network Security. In Quality, Reliability, Security and Robustness in Heterogeneous Networks; Singh, K., Awasthi, A.K., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; pp. 668–681. [Google Scholar]
- Mozzaquatro, B.A.; Jardim-Goncalves, R.; Agostinho, C. Towards a reference ontology for security in the Internet of Things. In Proceedings of the 2015 IEEE International Workshop on Measurements Networking (M&N), Coimbra, Portugal, 12–13 October 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Ducq, Y.; Agostinho, C.; Chen, D.; Zacharewicz, G.; Goncalves, R. Generic methodology for service engineering based on service modelling and model transformation. Manufacturing Service Ecosystem. Achievements of the European 7th FP FoF-ICT Project MSEE: Manufacturing SErvice Ecosystem (Grant No. 284860). Weisner, S., Guglielmina, C., Gusmeroli, S., Doumeingts, G., Eds.; FInES Future Internet Enterprise Systems (FInES) Cluster—Cluster Book—ICT2010. June 2010, pp. 41–49. Available online: http://cordis.europa.eu/fp7/ict/enet/documents (accessed on 16 January 2018).
- Debar, H.; Curry, D.A.; Feinstein, B.S. The intrusion detection message exchange format (IDMEF). Available online: https://tools.ietf.org/html/rfc4765 (accessed on 16 January 2018).
- Ficco, M. Security event correlation approach for cloud computing. Int. J. High Perform. Comput. Netw. 2013, 7, 173–185. [Google Scholar] [CrossRef]
- Ficco, M.; Tasquier, L.; Aversa, R. Intrusion detection in federated clouds. Int. J. Comput. Sci. Eng. 2016, 13, 219–232. [Google Scholar] [CrossRef]
- Alam, S.; Chowdhury, M.M.R.; Noll, J. Interoperability of Security-Enabled Internet of Things. Wirel. Pers. Commun. 2011, 61, 567–586. [Google Scholar] [CrossRef]
- Tao, M.; Zuo, J.; Liu, Z.; Castiglione, A.; Palmieri, F. Multi-layer cloud architectural model and ontology-based security service framework for IoT-based smart homes. Future Gener. Comput. Syst. 2018, 78, 1040–1051. [Google Scholar] [CrossRef]
- Ekelhart, A.; Fenz, S.; Neubauer, T. AURUM: A Framework for Information Security Risk Management. In Proceedings of the 2009 42nd Hawaii International Conference on System Sciences, Waikoloa, HI, USA, 5–8 January 2009; IEEE Computer Society: Washington, DC, USA, 2009; pp. 1–10. [Google Scholar] [CrossRef]
- Marotta, A.; Martinelli, F.; Nanni, S.; Orlando, A.; Yautsiukhin, A. Cyber-insurance survey. Comput. Sci. Rev. 2017, 24, 35–61. [Google Scholar] [CrossRef]
- Shahid, R.; Simon, D.; Joel, H.; Utz, R.; Thiemo, V. Secure communication for the Internet of Things—A comparison of link-layer security and IPsec for 6LoWPAN. Secur. Commun. Netw. 2014, 7, 2654–2668. [Google Scholar] [CrossRef]
- Mozzaquatro, B.A.; Agostinho, C.; Melo, R.; Jardim-Goncalves, R. A Model-Driven Adaptive Approach for IoT Security. In Model-Driven Engineering and Software Development: 4th International Conference, MODELSWARD 2016, Rome, Italy, February 19–21, 2016, Revised Selected Papers; Springer International Publishing: Cham, Switzerland, 2017; pp. 194–215. [Google Scholar] [CrossRef]
- Mozzaquatro, B.A. IoTSec Ontology. Available online: http://iotsec.brunomozza.com/ (accessed on 20 May 2018).
- Bagosi, T.; Calvanese, D.; Hardi, J.; Komla-Ebri, S.; Lanti, D.; Rezk, M.; Rodríguez-Muro, M.; Slusnys, M.; Xiao, G. The Ontop Framework for Ontology Based Data Access. In The Semantic Web and Web Science: 8th Chinese Conference, CSWS 2014, Wuhan, China, August 8–12, 2014, Revised Selected Papers; Springer: Berlin/Heidelberg, Germany, 2014; pp. 67–77. [Google Scholar]
- Prud’hommeaux, E.; Seaborne, A. SPARQL Query Language for RDF. World Wide Web Consortium. Available online: www.w3.org/TR/rdf-sparql-query/ (accessed on 19 March 2018).
- Gennari, J.H.; Musen, M.A.; Fergerson, R.W.; Grosso, W.E.; Crubézy, M.; Eriksson, H.; Noy, N.F.; Tu, S.W. The evolution of Protégé: An environment for knowledge-based systems development. Int. J. Hum. Comput. Stud. 2003, 58, 89–123. [Google Scholar] [CrossRef]
- Bazoun, H.; Zacharewicz, G.; Ducq, Y.; Boyé, H. SLMToolBox: An Implementation of MDSEA for Servitisation and Enterprise Interoperability. In Enterprise Interoperability VI; Proceedings of the I-ESA Conferences; Springer: Cham, Switzerland, 2014; Volume 7, pp. 101–111. [Google Scholar] [CrossRef]
- Koenig, J. Jboss jBPM. White Paper. Available online: http://ftp.vdel.com/files/jboss/jbpm_white paper.pdf (accessed on 16 January 2018).
- Ayuso, P. Netfilter’s connection tracking system. LOGIN USENIX Mag. 2006, 31, 34–39. [Google Scholar]
- Zhou, Z.; Chen, Z.; Zhou, T.; Guan, X. The study on network intrusion detection system of Snort. In Proceedings of the 2010 International Conference on Networking and Digital Society, Wenzhou, China, 30–31 May 2010; Volume 2, pp. 194–196. [Google Scholar] [CrossRef]
- OSS, P. Prelude OSS. Available online: http://www.prelude-siem.com/en/products/prelude-os/ (accessed on 16 January 2018).
- Kasinathan, P.; Costamagna, G.; Khaleel, H.; Pastrone, C.; Spirito, M.A. An IDS Framework for Internet of Things Empowered by 6LoWPAN. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; ACM: New York, NY, USA, 2013; pp. 1337–1340. [Google Scholar] [CrossRef]
- BeyondTrust. Retina Network Security Scanner. Available online: https://www.beyondtrust.com/products/retina-network-security-scanner/ (accessed on 16 January 2018).
- Suryn, W.; Abran, A.; April, A. ISO/IEC SQuaRE. The Second Generation of Standards for Software Product Quality. 2003. Available online: https://www.semanticscholar.org/paper/ISO-%2F-IEC-SQuaRE-.-The-second-generation-of-for-Suryn-Abran/348575d1cc283f04e2a1695ccc6e0a221442653b (accessed on 16 January 2018).
- Duque-Ramos, A.; Boeker, M.; Jansen, L.; Schulz, S.; Iniesta, M.; Fernández-Breis, J.T. Evaluating the Good Ontology Design Guideline (GoodOD) with the Ontology Quality Requirements and Evaluation Method and Metrics (OQuaRE). PLoS ONE 2014, 9, 1–14. [Google Scholar] [CrossRef] [PubMed]
- Horrocks, I.; Patel-Schneider, P.F.; Boley, H.; Tabet, S.; Grosof, B.; Dean, M. SWRL: A Semantic Web Rule Language Combining OWL and RuleML. Available online: http://www.daml.org/rules/proposal/ (accessed on 16 January 2018).
- Sirin, E.; Parsia, B.; Grau, B.C.; Kalyanpur, A.; Katz, Y. Pellet: A practical OWL-DL reasoner. Web Semant. Sci. Serv. Agents World Wide Web 2007, 5, 51–53. [Google Scholar] [CrossRef]
- Bröring, A.; Schmid, S.; Schindhelm, C.K.; Khelil, A.; Käbisch, S.; Kramer, D.; Phuoc, D.L.; Mitic, J.; Anicic, D.; Teniente, E. Enabling IoT Ecosystems through Platform Interoperability. IEEE Softw. 2017, 34, 54–61. [Google Scholar] [CrossRef]
- Skouby, K.E.; Lynggaard, P. Smart home and smart city solutions enabled by 5G, IoT, AAI and CoT services. In 2014 International Conference on Contemporary Computing and Informatics (IC3I); IEEE: Piscataway, NJ, USA, 2014; pp. 874–878. [Google Scholar]
- Veeramachaneni, K.; Arnaldo, I.; Korrapati, V.; Bassias, C.; Li, K. AI^2: Training a Big Data Machine to Defend. In Proceedings of the 2016 IEEE 2nd International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing (HPSC), and IEEE International Conference on Intelligent Data and Security (IDS), New York, NY, USA, 9–10 April 2016; pp. 49–54. [Google Scholar] [CrossRef]
- Mikroyannidis, A.; Theodoulidis, B. Ontology management and evolution for business intelligence. Int. J. Inf. Manag. 2010, 30, 559–566. [Google Scholar] [CrossRef]
- Forbes, D.E.; Wongthongtham, P.; Terblanche, C.; Pakdeetrakulwong, U. Ontology Engineering. In Ontology Engineering Applications in Healthcare and Workforce Management Systems; Springer International Publishing: Cham, Switzerland, 2018; pp. 27–40. [Google Scholar] [CrossRef]
- Mavroeidis, V.; Bromander, S. Cyber Threat Intelligence Model: An Evaluation of Taxonomies, Sharing Standards, and Ontologies within Cyber Threat Intelligence. In Proceedings of the 2017 European Intelligence and Security Informatics Conference (EISIC), Athens, Greece, 11–13 September 2017; pp. 91–98. [Google Scholar] [CrossRef]
- Jones, C.L.; Bridges, R.A.; Huffer, K.M.T.; Goodall, J.R. Towards a Relation Extraction Framework for Cyber-Security Concepts. In Proceedings of the 10th Annual Cyber and Information Security Research Conference, Oak Ridge, TN, USA, 7–9 April 2015; ACM: New York, NY, USA, 2015; pp. 11:1–11:4. [Google Scholar] [CrossRef]
- Abie, H.; Balasingham, I. Risk-based Adaptive Security for Smart IoT in eHealth. In Proceedings of the 7th International Conference on Body Area Networks, Oslo, Norway, 24–26 February 2012; ICST (Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering): Brussels, Belgium, 2012; pp. 269–275. [Google Scholar]
- Caraguay, A.L.V.; Peral, A.B.; López, L.I.B.; Villalba, L.J.G. SDN: Evolution and Opportunities in the Development IoT Applications. Int. J. Distrib. Sens. Netw. 2014, 10, 735142. [Google Scholar] [CrossRef]
- Salahuddin, M.A.; Al-Fuqaha, A.; Guizani, M.; Shuaib, K.; Sallabi, F. Softwarization of Internet of Things Infrastructure for Secure and Smart Healthcare. Computer 2017, 50, 74–79. [Google Scholar] [CrossRef]
- Liyanage, M.; Ahmad, I.; Okwuibe, J.; de Oca, E.M.; Mai, H.L.; López, O.; Uriarte, M. Software Defined Security Monitoring in 5G Networks. In A Comprehensive Guide to 5G Security; John Wiley & Sons: Hoboken, NJ, USA, 2018; p. 231. [Google Scholar]
- Nobre, J.C.; Mozzaquatro, B.A.; Granville, L.Z. Network-Wide Initiatives to Control Measurement Mechanisms: A Survey. IEEE Commun. Surv. Tutor. 2018. [Google Scholar] [CrossRef]

| Ontology Metric | # | Ontology Metric | # |
|---|---|---|---|
| Classes | 228 | Logical Axioms | 1895 |
| Object Properties | 24 | Annotations | 1418 |
| Data Properties | 7 | Individuals | 607 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mozzaquatro, B.A.; Agostinho, C.; Goncalves, D.; Martins, J.; Jardim-Goncalves, R. An Ontology-Based Cybersecurity Framework for the Internet of Things. Sensors 2018, 18, 3053. https://doi.org/10.3390/s18093053
Mozzaquatro BA, Agostinho C, Goncalves D, Martins J, Jardim-Goncalves R. An Ontology-Based Cybersecurity Framework for the Internet of Things. Sensors. 2018; 18(9):3053. https://doi.org/10.3390/s18093053
Chicago/Turabian StyleMozzaquatro, Bruno Augusti, Carlos Agostinho, Diogo Goncalves, João Martins, and Ricardo Jardim-Goncalves. 2018. "An Ontology-Based Cybersecurity Framework for the Internet of Things" Sensors 18, no. 9: 3053. https://doi.org/10.3390/s18093053
APA StyleMozzaquatro, B. A., Agostinho, C., Goncalves, D., Martins, J., & Jardim-Goncalves, R. (2018). An Ontology-Based Cybersecurity Framework for the Internet of Things. Sensors, 18(9), 3053. https://doi.org/10.3390/s18093053








